Hedging and Strategic Stability
The concept of strategic stability emerged during the Cold War, but today it is still unclear what the term exactly means and how its different interpretations influence strategic decisions. After the late 1950s, the Cold War superpowers based many of their arguments and decisions on their own understanding of strategic stability1 and it still seems to be a driving factor in the arms control negotiations of today. However, in absence of a common understanding of strategic stability, using this argument to explain certain decisions or threat perceptions linked to the different aspects of nuclear policy tend to create more confusion than clarity.
In the 2010 Nuclear Posture Review (NPR) report,2 the Obama administration used the term strategic stability as a central concept of U.S. nuclear policy vis-à-vis Russia and China. Altogether it appeared 29 times in the report, in reference to issues mostly related to nuclear weapons capabilities. In the U.S.-Russian bilateral relationship, strategic stability was associated with continued dialogue between the two states to further reduce U.S.-Russian nuclear arsenals, to limit the role of nuclear weapons in national security strategies, and to enhance transparency and confidence-building measures. At the same time, the United States pledged to sustain a safe, secure, and effective nuclear arsenal by modernizing its nuclear forces, retaining the triad, and “hedging against potential technical problems or vulnerabilities.”
On the other hand, Russia seems to use the term strategic stability in a broader context, claiming that the question of ballistic missile defense, conventional prompt global strike, and the militarization of outer space all affect strategic stability between Moscow and Washington. U.S. modernization efforts in these areas are seen as attempts to undermine the survivability of the Russian nuclear arsenal and steps to gain strategic advantage over Russia. Therefore, Moscow has been repeatedly arguing that any future arms control agreement should address all factors which affect strategic stability.3
Although these are the issues which Russia explicitly mentions in reference to strategic stability, there is another “hidden” issue which might also have a counterproductive impact on long term stability because of its potential to undermine strategic parity (which seems to be the basis of Russian interpretation of strategic stability).4 This issue is the non-deployed nuclear arsenal of the United States or the so-called “hedge.”
During the Cold War, both superpowers tried to deploy the majority of their nuclear weapons inventories. Reserve nuclear forces were small as a result of the continuous development and production of new nuclear weapons, which guaranteed the rapid exchange of the entire stockpile in a few years. The United States started to create a permanent reserve or hedge force in the early 1990s. The role of the hedge was twofold: first, to guarantee an up-build capability in case of a reemerging confrontation with Russia, and second, a technical insurance to secure against the potential failure of a warhead type or a delivery system. Despite the dissolution of the Soviet Union, during the first years of the 1990s, the United States was skeptical about the democratic transition of the previous Eastern Block and the commitment of the Russian Federation to arms control measures in general. Therefore, the Clinton administration’s 1994 NPR officially codified – for the first time – the concept of a hedge force against the uncertainties and the potential risks of the security environment.5 This concept gradually lost importance as the number of deployed strategic and non-strategic nuclear weapons kept shrinking on both sides and relations improved between Washington and Moscow. By the end of the 1990s, the main rationale for upholding the hedge force shifted towards the necessity of maintaining a back-up against technical failures. Although the nuclear arsenal was aging, a moratorium was declared on nuclear weapons testing, and several production facilities were closed. Therefore, it seemed imperative to retain fully functional nuclear warheads in reserve as an insurance policy.6
While the Clinton administration’s NPR was not too explicit about what the hedge really was, both the Bush and the Obama administrations made the specific role of the hedge clearer. Although technical considerations remained important, the Bush administration’s 2001 NPR refocused U.S. hedging policy on safeguarding against geopolitical surprises. The administration tried to abandon Cold War “threat-based” force planning and implemented a “capabilities-based” force structure which was no longer focused on Russia as an imminent threat but broadened planning against a wider range of adversaries and contingencies: to assure allies, deter aggressors, dissuade competitors and defeat enemies.7 This shift in planning meant that the force structure was designed for a post-Cold War environment with a more cooperative Russia. Therefore, the primary goal of the hedge was to provide guarantees in case this environment changed and U.S.-Russian relations significantly deteriorated.
Regardless of the main focus of the acting administration, the hedge has always served two different roles which belong to two separate institutions: the military considers the hedge a responsive force against the uncertainties of the international geopolitical environment, while the National Nuclear Security Administration (NNSA) views the hedge as a repository to safeguard the aging U.S. nuclear arsenal. These two institutions advise the administration on the required size of the hedge. Since the end of the Cold War, both the United States and Russia considerably reduced their deployed nuclear warheads, but Washington retained many of these weapons in the hedge. By now there are more non-deployed nuclear weapons than deployed nuclear weapons in its military stockpile.
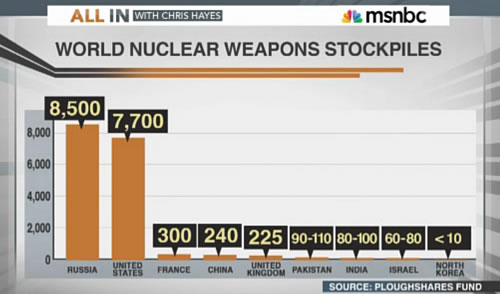
According to the Federation of American Scientists,8 the United States has a military stockpile of 4,650 nuclear weapons, of which roughly 1,900 strategic nuclear weapons are deployed (this includes bomber weapons on bomber bases as deployed) and another approximately 200 non-strategic nuclear weapons are deployed in Europe. Altogether this leaves around 2,500 non-deployed nuclear weapons in reserve – approximately 2,200 strategic and 300 non-strategic.9 This hedge force10 provides the United States with a capability to increase its deployed nuclear arsenal to more than 4000 nuclear weapons within three years.11 In the long run, this capability might feed into Russian paranoia over anything that can potentially undermine strategic parity and it could become a serious roadblock on the way toward further reductions in deployed strategic as well as non-strategic nuclear arsenals.
The Obama administration has already indicated in the 2010 NPR that it is considering reductions in the nuclear hedge. According to the document, the “non-deployed stockpile currently includes more warheads than required” and the “implementation of the Stockpile Stewardship Program and the nuclear infrastructure investments” could set the ground for “major reductions” in the hedge. However, in parallel to these significant reductions, the United States “will retain the ability to ‘upload’ some nuclear warheads as a technical hedge against any future problems with U.S. delivery systems or warheads, or as a result of a fundamental deterioration of the security environment.” In line with the 2010 NPR, the 2013 Presidential Employment Guidance also envisions reductions in the deployed strategic nuclear arsenal and reaffirms the intention to reduce the hedge as well. The Pentagon report on the guidance12 discusses an “alternative approach to hedging” which would allow the United States to provide the necessary back-up capabilities “with fewer nuclear weapons.” This alternative approach puts the main emphasis on the technical role of the hedge, claiming that “a non-deployed hedge that is sized and ready to address these technical risks will also provide the United States the capability to upload additional weapons in response to geopolitical developments.” According to Hans Kristensen, Director of the Nuclear Information Project at the Federation of American Scientists, this might imply that the hedge will no longer contain two categories of warheads – as there will be enough reserve warheads to protect against technical failures and potential geopolitical challenges.13 However, at this point it is still unclear if (and when) this new approach will lead to actual force reductions in the non-deployed nuclear arsenal.
In the meantime, the United States could achieve several benefits by reducing the hedge. First, reducing the number of warheads (which require constant maintenance and periodic life extension) could save a few hundred million dollars in the federal budget. Second, it could send a positive signal to Russia about U.S. long-term intentions. In his 2013 Berlin address, President Obama indicated that his administration would seek “negotiated cuts with Russia” to reduce the number of deployed strategic nuclear weapons below the ceilings of the New START Treaty.14 In terms of deployed strategic nuclear weapons, Moscow has already met the limits of the Treaty and seems to be reluctant to negotiate any further cuts until the 2018 New START implementation deadline or until the United States also meets the Treaty limits15 (which – in light of the current trends – is probably not going to happen earlier than 2018). In addition, the deeper the two sides reduce their deployed strategic nuclear arsenals, the harder Russia tries to press the United States to include all other issues which affect strategic stability (especially ballistic missile defense). The United States has tried to alleviate Russian concerns over missile defense by offering some cooperative and transparency measures but Moscow insists that a legally binding treaty is necessary, which would put serious limits on the deployment of the system (a condition that is unacceptable to the United States Congress at the moment). Therefore, the future of further reductions seems to be blocked by disagreements over missile defense. But the proposed reduction of the hedge could signal U.S. willingness to reduce its strategic advantage against Russia.
Despite the potential benefits, U.S. government documents16 have been setting up a number of preconditions for reducing the size of the hedge. Beyond “geopolitical stability,” the two most important preconditions are the establishment of a responsive infrastructure by constructing new warhead production facilities and the successful completion of the warhead modernization programs. The Department of Energy’s FY 2014 Stockpile Stewardship and Management Plan (SSMP) proposes a so-called 3+2 warhead plan that would create three interoperable warheads for ballistic missiles and two for long-range bombers.17 The transition to interoperable warheads could, according to the plan, permit a reduction of the number of warheads in the hedge. In light of the current budget constraints, it is still unclear if the program will start as planned and even if completed according to schedule, the gradual reduction of the technical hedge would not begin until the mid-2030s. Similar challenges will arise if the administration wishes to link the reduction of the hedge to the construction of new warhead production facilities – some of which have already been delayed due to budget considerations, and the exact dates and technical details of their future completion are still unclear.
The preconditions would mean that significant reductions in the hedge18 are unlikely to materialize for at least another 15 years. Meanwhile, the deployed arsenal faces two scenarios in the coming decades: the number of warheads and delivery platforms could keep shrinking or arms control negotiations might fail to produce further reductions as a result of strategic inequalities (partly caused by the huge U.S. non-deployed arsenal). Under the first scenario, keeping the hedge in its current size would be illogical because a smaller deployed arsenal would require fewer replacement warheads19 in case of technical failures, and because fewer delivery platforms would require fewer up-load warheads in case of geopolitical surprises. Maintaining the current non-deployed arsenal would not make any more sense under the second scenario either. If future arms control negotiations get stuck based on arguments over strategic parity, maintaining a large hedge force will be part of the problem, not a solution. Therefore, insisting on the “modernization precondition” and keeping the current hedge for another 15 years would not bring any benefits for the United States.
On the other hand, President Obama could use his executive power to start gradual reductions in the hedge. Although opponents in Congress have been trying to limit his flexibility in future nuclear reductions (which could happen in a non-treaty framework), current legislative language does not explicitly limit cuts in the non-deployed nuclear arsenal. After the successful vote on the New START Treaty, the Senate adopted a resolution on the treaty ratification which declares that “further arms reduction agreements obligating the United States to reduce or limit the Armed Forces or armaments of the United States in any militarily significant manner may be made only pursuant to the treaty-making power of the President.”20 However, if gradual cuts in the hedge would not be part of any “further arms reduction agreement” but instead implemented unilaterally, it would not be subject to a new legally binding treaty (and the necessary Senate approval which comes with it). Similarly, the FY2014 National Defense Authorization Act (NDAA), which was adopted in December 2013, does not use explicit language against unilateral reductions in the hedge.21 The NDAA only talks about preconditions to further nuclear arms reductions with Russia below the New START Treaty levels and it does not propose any limitations on cutting the non-deployed arsenal. In fact, the NDAA encourages taking into account “the full range of nuclear weapons capabilities,” especially the non-strategic arsenals – and this is exactly where reducing the United States hedge force could send a positive message and prove beneficial.
The 2013 Presidential Employment Guidance appears to move towards an alternative approach to hedging. This new strategy implies less reliance on non-deployed nuclear weapons which is a promising first step towards their reduction. However, the FY 2014 Stockpile Stewardship and Management Plan links this reduction to the successful completion of the ongoing nuclear modernization programs, anticipating that the number of warheads in the hedge force will not change significantly in the near future. Its fate will mainly depend on congressional budget fights.
This might send a bad signal to Russia, where U.S. missile defense developments and its alleged impact on strategic stability are already a primary source of concern to the Kremlin. As a result of aging technologies and necessary retirements, Russian nuclear forces have been constantly decreasing, and despite all modernization efforts,[ref]Russian has an ongoing modernization program, in the framework of which it has already begun to build a new heavy ICBM and a multiple-warhead Bulava SLBM.[/ref] it is expected that by the early 2020s the ICBM arsenal will shrink to 220 missiles.22 Russia already deploys 40 percent less strategic delivery systems than the United States and tries to keep the balance of deployed weapons by higher warhead loadings. This does not give Russia the ability to significantly increase the deployed number of warheads – not just because of the lower number of delivery vehicles but also because of the lack of reserve warheads comparable in number to the United States hedge force. In this regard there is an important asymmetry between Russia and the United States – while Washington keeps a hedge for technical and geopolitical challenges, Moscow maintains an active production infrastructure, which – if necessary – enables the production of hundreds of new weapons every year. It definitely has its implications for the long term (10-15 years) status of strategic parity, but certainly less impact on short term prospects.
In the meantime, the United States loads only 4-5 warheads on its SLBMs (instead of their maximum capacity of 8 warheads) and keeps downloading all of its ICBMs to a single warhead configuration.23 Taken into account the upload potential of the delivery vehicles and the number of warheads in the hedge force, in case of a dramatic deterioration of the international security environment the United States could increase its strategic nuclear arsenal to above 4000 deployed warheads in about three years.
Whether one uses a narrow or a broader interpretation of strategic stability, these tendencies definitely work against the mere logic of strategic parity and might have a negative effect on the chances of further bilateral reductions as well. Cutting the hedge unilaterally would definitely upset Congress and it could endanger other foreign policy priorities of the United States (such as the CTBT ratification or negotiations with Iran), but it would still be worth the effort as it could also indicate good faith and contribute to the establishment of a more favorable geopolitical environment. It could signal President Obama’s serious commitment to further disarmament, send a positive message to Russian military planners and ease some of their paranoia about U.S. force structure trends.
Anna Péczeli is a Fulbright Scholar and Nuclear Research Fellow at the Federation of American Scientists. Additionally, Péczeli is an adjunct fellow at the Hungarian Institute of International Affairs, where she works on nuclear arms control. Péczeli earned a master’s degree in international relations from Corvinus University of Budapest, and is currently working on her doctoral dissertation, which focuses on the Obama administration’s nuclear strategy.
President’s Message: Legitimizing Iran’s Nuclear Program

Be careful of self-fulfilling prophecies about the intentions for Iran’s nuclear program. Often, Western analysts view this program through the lens of realist political science theory such that Iranian leaders seek nuclear weapons to counteract threats made to overthrow their regime or to exert dominance in the Middle East. To lend support to the former argument, Iranian leaders can point to certain political leaders in the United States, Israel, Saudi Arabia, or other governments that desire, if not actively pursue, the downfall of the Islamic Republic of Iran. To back up the latter rationale for nuclear weapons, Iran has a strong case to make to become the dominant regional political power: it has the largest population of any of its neighbors, has a well-educated and relatively technically advanced country, and can shut off the vital flow of oil and gas from the Strait of Hormuz. If Iran did block the Strait, its leaders could view nuclear weapons as a means to protect Iran against attack from powers seeking to reopen the Strait. (Probably the best deterrent from shutting the Strait is that Iran would harm itself economically as well as others. But if Iran was subject to crippling sanctions on its oil and gas exports, it might feel compelled to shut down the Strait knowing that it is already suffering economically.) These counteracting external threats and exerting political power arguments provide support for the realist model of Iran’s desire for nuclear bombs.
But viewed through another lens, one can forecast continual hedging by Iran to have a latent nuclear weapons capability, but still keeping barriers to proliferation in place such as inspections by the International Atomic Energy Agency (IAEA). In particular, Iranian leaders have arguably gained considerable political leverage over neighbors by just having a latent capability and have maintained some legitimacy for their nuclear program by remaining part of the IAEA’s safeguards system.
If Iran crosses the threshold to make its own nuclear weapons, it could stimulate neighbors to build or acquire their own nuclear weapons. For example, Saudi leaders have dropped several hints recently that they will not stand idly by as Iran develops nuclear weapons. The speculation is that Saudi Arabia could call on Pakistan to transfer some nuclear weapons or even help Saudi Arabia develop the infrastructure to eventually make its own fissile material for such weapons. Pakistan is the alleged potential supplier state because of stories that Saudi Arabia had helped finance Pakistan’s nuclear weapons program and thus, Islamabad owes Riyadh for this assistance. Moreover, Pakistan remains outside the Non-Proliferation Treaty and therefore would not have the treaty constraint as a brake on nuclear weapons transfer. Furthermore, one could imagine a possible nuclear cascade involving the United Arab Emirates, Jordan, and Egypt, all states that are developing or considering developing nuclear power programs. This proliferation chain reaction would likely then undermine Iran’s security and make the Middle East further prone to potential nuclear weapons use.
I would propose for the West to act optimistically and trust but verify Iran’s claim that its nuclear program is purely for peaceful purposes. The interim deal that was recently reached between Iran and the P5+1 (the United States, Russia, France, China, United Kingdom, and the European Union) is encouraging in that it places a temporary halt on some Iranian activities such as construction of the 40 MW reactor at Arak, the further enrichment of uranium to 20 percent uranium-235 (which is about 70 percent of the work needed to reach the weapons-grade level of 90 percent uranium-235), and continued expansion of the enrichment facilities. Iran also has become more open to the IAEA’s inspections. But these are measures that can be readily reversed if the next deal cannot be negotiated within the next several months. Iran is taking these actions in order to get relief from some economic sanctions.
Without getting into the complexities of the U.S. and Iranian domestic politics as well as international political considerations, I want to outline in the remaining part of this president’s message a research agenda for engineers and scientists. I offer FAS as a platform for these technical experts to publish their analyses and communicate their findings. Specifically, FAS will create a network of experts to assess the Iranian nuclear issues, publish their work on FAS.org, and convene roundtables and briefings for executive and legislative branch officials.
Let’s look at the rich research agenda, which is intended to provide Iran with access to a suite of peaceful nuclear activities while still putting limits on the latent weapons capacity of the peaceful program. By doing so, we can engender trust with Iranians, but this will hinge on adequate means to detect breakout into a nuclear weapons program.
First, consider the scale of Iran’s uranium enrichment program. It is still relatively small, only about a tenth of the capacity needed to make enough low enriched uranium for even the one commercial nuclear plant at Bushehr. Russia has a contract with Iran for ten years of fuel supply to Bushehr. If both sides can extend that agreement over the 40 or more years of the life of the plant, then Iran would not have the rationale for a large enrichment capacity based on that one nuclear plant. However, Iran has plans for a major expansion of nuclear power. Would it be cost effective for Iran to enrich its own uranium for these power plants? The short answer is no, but because of Iranian concerns about being shut out of the international enrichment market and because of Iranian pride in having achieved even a modestly sized enrichment capacity, Iranian leaders will not give up enrichment. I would suggest that a research task for technical experts is to work with Iran to develop effective multi-layer assurances for nuclear fuel. Another task is to assess what capacity of enrichment is appropriate for the existing and under construction research and isotope production reactors or for smaller power reactors. These reactors require far less enrichment capacity than a large nuclear power plant. A first order estimate is that Iran already has the right amount of enrichment capacity to fuel the current and planned for research reactors. But nuclear engineers and physicists can and should perform more detailed calculations.
One reactor under construction has posed a vexing challenge; this is the 40 MW reactor being built at Arak. The concern is that Iran has planned to use heavy water as the moderator and natural uranium as the fuel for this reactor. (Heavy water is composed of deuterium, a heavy form of hydrogen with a proton and neutron in its nucleus, rather than the more abundant “normal” hydrogen, with a proton in its nucleus, which composes the hydrogen atoms in “light” or ordinary water.) A heavy water reactor can produce more plutonium per unit of power than a light water reactor because there are more neutrons available during reactor operations to be absorbed by uranium-238 to produce plutonium-239, a fissile material. The research task is to develop reactor core designs that either use light water or use heavy water with enriched uranium. The light water reactor would have to use enriched uranium in order to operate. A heavy water reactor could also make use of enriched uranium in order to reduce the available neutrons. Another consideration for nuclear engineers who are researching how to reduce the proliferation potential of this reactor is to determine how to lower the power rating, while still providing enough power for Iran to carry out necessary isotope production services and scientific research with the reactor. The 40 MW thermal power rating implies that if operated at near full power for a year, this reactor can make one to two bombs’ worth of plutonium annually. Another research problem is to design the reactor so that it is very difficult to use in an operational mode to produce weapons-grade plutonium. Safeguards and monitoring are essential mechanisms to forestall such production but might not be adequate. Here again, research into proliferation-resistant reactor designs would shed light on this problem.
Regarding isotope production, further research and development would be useful to figure out if non-reactor alternative technologies such as particle accelerators can produce the needed isotopes at a reasonable cost. Derek Updegraff and Pierce Corden of the American Association of the Advanced of Science have been investigating alternative production methods. Science progresses faster when additional researchers investigate similar issues. Thus, this research task could bear considerable fruit if teams can develop cost effective non-reactor means to produce medical and other industrial isotopes in bulk (or whatever quantity is required). If such development is successful, Iran and other countries could retire isotope production reactors that could pose latent proliferation concerns.
Finally, I will underscore perhaps the biggest research challenge: how to ensure that the Iranian nuclear program is adequately safeguarded and monitored. One of the next important steps for Iran is to apply a more rigorous safeguards system called the Additional Protocol and for a period of time, perhaps from five to ten years, apply inspection measures that go beyond the requirements of the Additional Protocol in order to instill confidence in the peaceful nature of Iran’s nuclear program. Dozens of states have ratified the Additional Protocol, which requires the IAEA to assess whether there are any undeclared nuclear material and facilities in the country being inspected. The Additional Protocol was formed in response to the finding in 1991 in Iraq that Saddam Hussein’s nuclear technicians were getting close to producing fissile material for nuclear weapons, despite the fact that Iraq was subject to regular IAEA inspections of its declared nuclear material and facilities. The undeclared facilities were often physically near declared facilities. There are concerns that given the large land area of Iran, clandestine nuclear facilities might go unnoticed by the IAEA or other means of detection and thus pose a significant risk for proliferation. The research task is to find out if there are effective means to find such clandestine facilities and to provide enough warning before Iran would be able to make enough fissile material and form it into bombs.
A key consideration of any part of this research agenda is how to cooperate with Iranian counterparts. For this plan to be acceptable and achievable, Iranian engineers, scientists, and leaders must own these concepts and believe that the plan supports their objectives to have a legitimate nuclear program that can generate electricity, produce isotopes for medical and industrial purposes, and provide other peaceful benefits including scientific research. Thus, we will need to leverage earlier and ongoing outreach to Iran by organizations such as the Pugwash Conferences on Science and World Affairs, the U.S. National Academy of Sciences, the American Association for the Advance of Science, and the Richard M. Lounsbery Foundation. Future workshops with Iranian counterparts are essential and companion studies by these counterparts would further advance the cause of legitimizing the Iranian nuclear program.
Several scientists and other technically trained experts in the United States have already been assessing aspects of this agenda as I indicated above with the mention of Updegraff and Corden’s research. Also, without meaning to slight anyone I may not know of or forget to mention, I would call out David Albright and his team at the Institute for Science and International Security, Richard Garwin of IBM, Frank von Hippel and colleagues at Princeton University, and Scott Kemp of MIT. This group is doing insightful work, but I believe that getting more engineers and scientists involved would bring more diverse ideas and more technical expertise to bear on this challenge to international security.
Engineers and scientists have a fundamental role to play in explaining the technical options to policy makers. For FAS, in particular, such work will help revitalize the organization as a true federation of scientists and engineers dedicated to devoting their talents to a more secure and safer world. FAS invites you to contact us if you have skills and knowledge you want to contribute to this proposal to help ensure Iran’s nuclear program remains peaceful.
Charles D. Ferguson, Ph.D.
President, Federation of American Scientists
A Citizen Approach to Nonproliferation
Have you ever watched a football match where thousands of attendees witness an event that the officials missed? Sometimes there is wisdom in the crowd, especially a crowd who understand the rules of the game. Officials, no matter how dedicated and hardworking they may be, cannot be everywhere or look everywhere at every moment. Indeed, sometimes just one set of eyes can call attention to what should have been obvious or would have been missed.
Consider the individual with administrative responsibilities working for an import/export company who has been told that the company works on the acquisition of farming equipment. Invoices and shipment information cross their desk for large diameter carbon fiber tubes or those made from maraging steel or high-speed electronics, potential items for a gas centrifuge uranium enrichment facility or nuclear weapons detonation fire sets. Maybe they are laborers in the company’s receiving facility and are responsible for uncrating and repackaging these purchases. They are witnesses to illegal activities and, if they remain uninformed, these individuals would simply go about their everyday tasks.
Shouldn’t we consider a way to reach the citizens of the world to make the world a safer place? Shouldn’t we explore how the power of the web and crowdsourcing might have a profound impact in the area of nonproliferation? Part of the power of the web is how inexpensive it is to explore concepts and allow users to vote with their participation and support.
This article describes the concept of Citizen Sensor1, which aims at leveraging citizens around the world to further strengthen the nonproliferation and international safeguard regime. Start by imagining a world with new and inexpensive methods of vigilance against the spread of nuclear weapons by producing as many knowledgeable citizens as possible – using the observations of crowds and attentive individuals through the power of the web.
The detection of undeclared nuclear facilities and nuclear weapons programs is unequivocally the greatest challenge facing the International Atomic Energy Agency. The common theme for all nuclear nonproliferation challenges is the exposure of people to information, but they are often unaware of the actual application or nature of their work or of the items and activities they see. Or, even if they are aware, they are not sure where to turn to or how to safely inform others. By using the web as both an education tool and a reporting platform, Citizen Sensor aims to alert them to this type of threat, instruct them on how they can help with early detection through education and vigilance and share their knowledge to try to deter those who seek to create a nuclear weapon or other weapons of mass destruction. From the proposed website: “The problem of nuclear proliferation is much like a puzzle – one piece of the puzzle may not show you much, but a collection of pieces will. By combining even seemingly innocuous pieces of information we can help deter nuclear threats and provide nuclear security for the world at large.”
Elements of the Internet-based Citizen Sensor Culture
A variety of potential elements could influence the creation of the Citizen Sensor. These include:
- Proliferation indicator training – What are the most important signs that might indicate proliferation is happening and how do you watch for them? Citizen Sensor would educate the web-based community as a formidable mechanism for early detection of the construction of clandestine nuclear facilities and discovery of weaponization activities. The website would allow education through words and pictures.
- “Neighborhood Watch” as a sharing platform – Post your evidence/suspicions anonymously or signed for discussion and analysis by the crowd.
- “Amber” or “911” type alert for urgent real-time events – If nuclear or radiological material or sensitive information goes missing, mobilize people to help law enforcement find them.
- “Suggestion” box – What are your ideas on how to improve a Citizen Sensor website?
- Testimonials – What supporting activities can be shared with the general public in order to encourage this work?
The concept of Citizen Sensor reaches beyond its website; it would leverage information and capabilities on other websites (such as the IAEA, Google Earth, and Wikipedia) and it will develop an international culture of informed training, watchfulness, and reflection regarding proliferation, coupled with statistical and social science analysis of the information exchanges and discussions that transpire.
Citizen Sensor would include tools for education, information discovery, and anonymous reporting, and could serve as a test bed for other researchers to experiment with specific data processing and social science techniques. These include incentives for the public to participate and methods to screen for incorrect information.
Training modules on all elements of the nuclear fuel cycle, single/dual use items, and aspects of weaponization would be developed, along with search tools to allow users to discover any linkages/matches from their “found” information to be translated into written and/or visual knowledge.

A successful Citizen Sensor website would catalyze a watchful and credible culture of citizen sensors – a worldwide community that produces potential actionable threats and concerns that those with authority and power would consider and act upon. It could be a significant deterrent to proliferators, as it targets the very human resources they count on.
As smart phones continue to grow in computational and sensor capability, new applications continue to arise. GammaPix™ works with the camera of iPhones2 and Android-based3 smart phones to detect radioactivity. The app allows you to measure radioactivity levels wherever you are and determine if your local environment is safe. The app can be used for the detection of radioactivity in everyday life such as exposure on airplanes, from medical patients, or from contaminated products. GammaPix™ can also be used to detect hazards resulting from unusual events like nuclear accidents (such as Fukushima), a terrorist attack by a dirty bomb, or quietly placed and potentially dangerous radioactive sources. As this technology becomes more widespread, a way to gather, process, and post the information is needed. Educating the public on its limitations is just as important as its capabilities, and Citizen Sensor website could potentially accomplish both aspects.
If Citizen Sensor had already been operational, perhaps it could have helped during the 2013 theft in Mexico of a cobalt-60 radioactive source. The thieves apparently had not been aware of what they had stolen, but what if they had been interested in making a radiological dispersal device? Just as an Amber Alert aims to help officials find a missing child or a 911 call is used for emergencies in the United States, perhaps a Citizen Sensor alert could help find missing radioactive materials.
Through the Comprehensive Test Ban Treaty Organization, the world is building a surveillance network to detect nuclear tests. According to an article in the Washington Post, “the nearly-completed International Monitoring System is proving adept at tasks its inventors never imagined. The system’s scores of listening stations continuously eavesdrop on Earth itself, offering clues about man-made and natural disasters as well as a window into some of nature’s most mysterious processes.”4 What might thousands of people, educated observers, and radioactivity-detecting smart phones find?
Requirements
Citizen Sensor must be as open as possible, without any government affiliation, by hosting through a non-governmental organization. It must be unencumbered by government policy and/or regulations. It must be responsive to current events and actively maintain updated information. Knowledgeable developers of websites and training modules for nuclear fuel cycle facilities, proliferation indicators, and sustained funding are all key factors for any chance of success.
The effort must be international and multi-lingual with capabilities that evolve over time as experience and suggestions drive its future. Contributions can be either public posts or private messages and can be either anonymous or signed. It is certain there will be false positives, and issues and concerns that do not point to proliferation activity. Both the culture and software must be structured to minimize false positives and protect it and contributors from the ramifications of false positives. It will also act as a nexus for discovery tools at other websites offering maps, images, knowledge, and analysis tools.
The challenge that is faced is the support (financial and skills) to make this concept a reality. This includes recruiting scientific talent to populate educational modules, website creation and operators and methods to promote the Citizen Sensor and its potential to educate citizens about the nature of nuclear materials and proliferation.
Editor’s Note
If interested, please send feedback and ideas to citizensensor@inl.gov.
Mark Schanfein joined Idaho National Laboratory (INL) in September 2008, as their Senior Nonproliferation Advisor, after a 20-year career at Los Alamos National Laboratory where, in his last role, he served as Program Manager for Nonproliferation and Security Technology. He served as a technical expert on the ground in the DPRK during the disablement activities resulting from the 6-Party Talks. Mark has eight years of experience working at the International Atomic Energy Agency in Vienna, Austria, in the Department of Safeguards where he served four years as a safeguards inspector and as Inspection Group Leader in Operations C, and four years as the Unit Head for Unattended Monitoring Systems (UMS) in Technical Support. In this position he was responsible for the installation of all IAEA unattended systems in nuclear fuel cycle facilities worldwide.
With over 30 years of experience in international and domestic safeguards, his current focus is on conducting R&D to develop the foundation for effective international safeguards on pyroprocessing facilities and solutions to other novel safeguards challenges.
Steven Piet has worked 31 years at Idaho National Laboratory. He earned the Bachelors, Masters, and Doctor of Science degrees in nuclear engineering from the Massachusetts Institute of Technology (MIT). He has 57 peer-reviewed journal articles and is author or co-author of 3 book chapters – in the fields of nuclear fuel cycles, fusion safety and technology, environmental science and decision making, and stakeholder assessment and decision making. For the nuclear fuel cycle program, he framed questions, searched for broadly acceptable and flexible solutions, promoted consensus on criteria, evaluated trade-offs, and identified R&D needs and possibilities to improve concepts; and was responsible for development of the world-leading multi-institution fuel cycle system dynamic model VISION. For the Generation IV advanced nuclear power program, his lab-university team diagnosed public/stakeholder issues and heuristics.
He has also been a Toastmaster for almost 9 years and has attained the educational achievement level of “Distinguished Toastmaster,” which less than 1% of Toastmasters achieve. As Club President, his club achieved President’s Distinguished Status. He was recognized as Area Governor of the year (2011-2012) and Division Governor of the year (2012-2013) and now serves as District Lt Governor of Marketing.
President’s Message: Rights and Responsibilities
The election of Hassan Rouhani as the president of Iran has breathed new life into the negotiations over Iran’s nuclear program. In recent months, a flurry of meetings has raised hopes that this program can remain peaceful and that war with Iran can be averted. But barriers still block progress. Among the major sticking points is Iranian leaders’ insistence that Iran’s “right” to enrichment be explicitly and formally acknowledged by the United States and the other nations in the so-called P5+1 (China, France, Russia, the United Kingdom, the United States, and Germany). While it is a fact that Iran has enrichment facilities, it is not a foregone conclusion that Iran has earned a right or should be given a right to enrichment without meeting its obligations. Enrichment is a dual-use technology: capable of being used to make low enriched uranium for nuclear fuel for reactors or highly enriched uranium for nuclear weapons.
Iran has consistently pointed to the Non-Proliferation Treaty (NPT) itself as using the word “right.” Indeed, the beginning of Article IV of the NPT states, “Nothing in this Treaty shall be interpreted as affecting the inalienable right of all the Parties to the Treaty to develop research, production and use of nuclear energy for peaceful purposes.” [Emphasis added.] But rights come with responsibilities. In particular, the remaining part of the first sentence of Article IV concludes: “without discrimination and in conformity with articles I and II of this Treaty.” Article I puts responsibility on the nuclear weapon states not to transfer nuclear explosives or assist a non-nuclear weapon state in manufacturing such explosives. Article II places responsibility on the non-nuclear weapon states to not receive nuclear explosives or to manufacture such explosives. Article IV is also linked with Article III, in which non-nuclear weapon states have the obligation to apply comprehensive safeguards to their nuclear programs to ensure that those programs are peaceful. Nuclear weapon states can accept voluntary safeguards on the parts of their nuclear programs designated for peaceful purposes.
Iranian leaders have also often said that they want to be treated like Japan, which has enrichment and reprocessing facilities. But Japan has made the extra effort to apply advanced safeguards to these facilities. Specifically, it enacted the Additional Protocol to the Comprehensive Safeguards Agreement, which gives the International Atomic Energy Agency (IAEA) access to a country’s entire nuclear program and requires the IAEA to assess whether there are any undeclared nuclear materials or facilities in that country. In effect, the IAEA must act like Sherlock Holmes investigating whether there is anything amiss throughout a nuclear program rather than acting like a green-eye shade wearing accountant who just checks the books. Iran had been voluntarily applying the Additional Protocol before early 2006 when its nuclear file was taken to the UN Security Council. Then Iran suspended application of these enhanced safeguards.
While the deal announced on November 11 between the IAEA and Iran to allow the IAEA additional access and information on selected facilities and activities, it does not go far enough. Iran has left out the Arak heavy water research reactor and the Parchin site, in particular. The Arak reactor, which could start operations next year, has the type of design well suited to being able to produce weapons-grade plutonium. If Iran had a covert hot cell to reprocess irradiated fuel from this reactor, it could extract at least one bomb’s worth of plutonium per year depending on the level of operations. The Parchin site has been suspected of previously being used for testing of high explosives that might be relevant for nuclear weapons design work. Iran has stated that this is a military site not related to nuclear work and thus off limits to IAEA inspectors. Arak and Parchin are just two outstanding examples of sites that raise concern about Iran’s intentions and potential capabilities.
Without a doubt, Iran has the right to pursue and use peaceful nuclear energy. But before it is given a formal right to continue with enrichment, it has to take adequate efforts to ensure that its nuclear program is fully transparent and well safeguarded. The United States and its allies would concomitantly have the obligation to help Iran meet its energy needs and remove sanctions that have been in place against Iran’s nuclear program.
New START Data Shows Russia Reducing, US Increasing Nuclear Forces
By Hans M. Kristensen
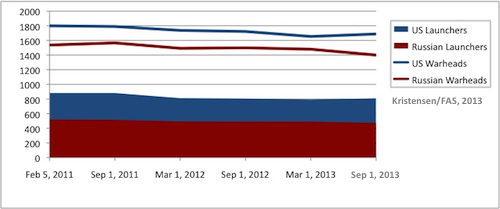
While arms control opponents in Congress have been busy criticizing the Obama administration’s proposal to reduce nuclear forces further, the latest data from the New START Treaty shows that Russia has reduced its deployed strategic nuclear forces while the United States has increased its force over the past six months.
Yes, you read that right. Over the past six months, the U.S. deployed strategic nuclear forces counted under the New START Treaty have increased by 34 warheads and 17 launchers.
It is the first time since the treaty entered into effect in February 2011 that the United States has been increasing its deployed forces during a six-month counting period.
We will have to wait a few months for the full aggregate data set to be declassified to see the details of what has happened. But it probably reflects fluctuations mainly in the number of missiles onboard ballistic missile submarines at the time of the count.
Slooow Implementation
The increase in counted deployed forces does not mean that the United States has begun to build up is nuclear forces; it’s an anomaly. But it helps illustrate how slow the U.S. implementation of the treaty has been so far.
Two and a half years into the New START Treaty, the United States has still not begun reducing its operational nuclear forces. Instead, it has worked on reducing so-called phantom weapons that have been retired from the nuclear mission but are still counted under the treaty.
For reasons that are unclear (but probably have to do with opposition in Congress), the administration has chosen to reduce its operational nuclear forces later rather than sooner. Not until 2015-2016 is the navy scheduled to reduce the number of missiles on its submarines. The air force still hasn’t been told where and when to reduce the ICBM force or which of its B-52 bombers will be denuclearized.
Moreover, even though the navy has already decided to reduce the missile tubes on its submarine force by more than 30 percent from 280 in 2016 to 192 on its next-generation ballistic missile submarine, it plans to continue to operate the larger force into the 2030s even though it is in excess of targeting and employment guidance.
Destabilizing Disparity
But even when the reductions finally get underway, the New START Treaty data illustrates an enduring problem: the growing disparity between U.S. and Russian strategic nuclear forces. The United States now is counted with 336 deployed nuclear launchers more than Russia.
Russia is already 227 deployed missiles and bombers below the 700 limit established by the treaty for 2018, and might well drop by another 40 by then to about 430 deployed strategic launchers. The United States plans to keep the full 700 launchers.
Put in another way: unless the United States significantly reduces its ICBM force beyond the 400 or so planned under the New START Treaty, and unless Russia significantly increases deployment of new missiles beyond what it is currently doing, the United States could end up having nearly as many launchers in the ICBM-leg of its Triad as Russia will have in its entire Triad.
Strange Bedfellows
For most people this might not matter much and even sound a little Cold War’ish. But for military planners who have to entertain potential worst-case threat scenarios, the growing missile-warhead disparity between the two countries is of increasing concern.
For the rest of us, it should be of concern too, because the disparity can complicate arms reductions and be used to justify retaining excessively large expensive nuclear force structures.
For the Russian military-industrial complex, the disparity is good for business. It helps them argue for budgets and missiles to keep up with the United States. But since Russia is retiring its old Soviet-era missiles and can’t build enough new missiles to keep some degree of parity with the United States, it instead maximizes the number of warheads it deploys on each new missile.
As a result, the Russian Strategic Rocket Forces has begun a program to deploy modified SS-27 ICBMs with multiple warheads (the modified SS-27 is known in Russia as RS-24 or Yars) with six missile divisions over the next decade and a half (more about that in a later blog). And a new “heavy” ICBM with up to ten warheads per missile is said to be under development.
So in a truly bizarre twist, U.S. lawmakers and others opposing additional nuclear reductions by the Obama administration could end up help providing the excuse for the very Russia nuclear modernization they warn against.
Granted, the Putin government may not be the easiest to deal with these days. But that only makes it more important to continue with initiatives that can take some of the wind out of the Russian military’s modernization plans. Slow implementation of the New START Treaty and retention of a large nuclear force structure certainly won’t help.
See also blog on previous New START data.
This publication was made possible by grants from the New-Land Foundation and Ploughshares Fund. The statements made and views expressed are solely the responsibility of the author.
B61-12 Nuclear Bomb Triggers Debate in the Netherlands

In a few years, US Air Force C-17 aircraft will begin airlifting new B61-12 nuclear bombs into six air bases in five NATO countries, including Volkel Air Base in the Netherlands (seen above).
By Hans M. Kristensen
The issue of the improved military capabilities of the new B61-12 nuclear bomb entered the Dutch debate today with a news story on KRO Brandpunt (video here) describing NATO’s approval in 2010 of the military characteristics of the weapon.
Dutch approval to introduce the enhanced bomb later this decade is controversial because the Dutch parliament wants the government to work for a withdrawal of nuclear weapons from the Netherlands and Europe. The Dutch government apparently supports a withdrawal.
Bram Stemerdink, who was Dutch defense minister in 1977 and deputy defense minister in 1973-1976 and 1981-1982, said that the Dutch government would have been consulted about the B61-12 capabilities. “Because we have those bombs at the moment. Was the Netherlands therefore consulted, yes,” Stemerdink reportedly said.

Former Dutch defense minister Bram Stemerdink said the Netherlands would have been consulted about the military capabilities of the enhanced B61-12 bomb.
NATO approved the military characteristics of the B61-12 in April 2010, according to the U.S. Government Accountability Office, “including the yield, that it be capable of freefall (rather than parachute-retarded) delivery, its accuracy requirements when used on modern aircraft and that it employ a guided tailkit section, and that it have both midair and ground detonation options.”
Dutch approval is also controversial because the improved military capabilities of the B61-12 compared with the weapons currently deployed in Europe (addition of a guidance tail kit to increase accuracy and provide a standoff capability) contradict the U.S. pledge from 2010 that nuclear weapon life-extension programs “will not…provide for new military capabilities.” The U.S. currently does not have a guided standoff nuclear bomb in its stockpile. The improved military capabilities also contradict NATO’s promise from 2012 to seek to “create the conditions and considering options for further reductions of non-strategic nuclear weapons assigned to NATO…”
Last month Dutch TV disclosed a dispute between the U.S. and Dutch governments over how to discuss potential financial compensation in case of an accident involving U.S. nuclear weapons in the Netherlands.
The B61-12 is currently being designed for production with a price tag of more than $10 billion for approximately 400 bombs – possibly the most expensive U.S. nuclear bomb ever.
Nuclear weapons are unlikely to remain in Europe for long, so instead of wasting more than $10 billion on the controversial enhanced B61-12 for a mission that has expired, the United States should instead do a more basic and cheaper life extension of an existing version. Instead of wasting money on modernizing a nuclear weapon for Europe, the United States should focus its efforts on changing the views of eastern European NATO countries by providing extended deterrence in a form that actually contributes to their security.
This publication was made possible by grants from the New-Land Foundation and Ploughshares Fund. The statements made and views expressed are solely the responsibility of the author.
Dispute Over US Nuke in the Netherlands: Who Pays For An Accident?

Who pays for a crash of a nuclear weapons airlift from Volkel Air Base?
By Hans M. Kristensen
Only a few years before U.S. nuclear bombs deployed at Volkel Air Base in the Netherlands are scheduled to be airlifted back to the United States and replaced with an improved bomb with greater accuracy, the U.S. and Dutch governments are in a dispute over how to deal with the environmental consequences of a potential accident.
The Dutch government wants environmental remediation to be discussed in the Netherlands United States Operational Group (NUSOG), a special bilateral group established in 2003 to discuss matters relating to the U.S. deployment of nuclear weapons in the Netherlands.
But the United States has refused, arguing that NUSOG is the wrong forum to discuss the issue and that environmental remediation is covered by the standard Status of Forces Agreement from 1951.
The disagreement at one point got so heated that a Dutch officials threatened that his government might have to consider reviewing US Air Force nuclear overflight rights of the Netherlands if the United States continue to block the issue from being discussed within the NUSOG.
The dispute was uncovered by the Brandpunt Reporter of the TV station KRO (see video and also this report), who discovered three secret documents previously released by WikiLeaks (document 1, document 2, and document 3).
The documents not only describe the Dutch government’s attempts to discuss – and U.S. efforts to block – the issue within NUSOG, but also confirm what is officially secret but everyone knows: that the United States stores nuclear weapons at Volkel Air Base.
Michael Gallagher, the U.S. Charge d’Affaires at the U.S. Embassy in Hague, informed the U.S. State Department that environmental remediation is “primarily an issue of financial liability” and discussing it “potentially a slippery slope.” During on e NUSOG meeting, Dutch civilian and military participants were visibly agitated about the U.S. refusal to discuss the issue, and Gallagher warned that “a policy of absolute non-engagement is untenable, and will negatively impact our bilateral relationship with a strong ally.”
Gallagher predicted that the Dutch would continue to raise the issue, and said the Netherlands was ahead of the other European countries that host U.S. nuclear weapons on their territories in having signed and implemented the NUSOG. Unlike Germany, Belgium, Italy and Turkey, the Netherlands was the only country that had raised the issue of remediation in a forum such as NUSOG, but Gallagher warned that the other countries would raise the issue of remediation in the future as similar nuclear weapons operational groups are established.

Charge d’Affaires Michael Gallagher shakes hands with Dutch foreign minister Frans Timmermans, who wants U.S. nuclear weapons removed from the Netherlands.
The United States has deployed nuclear weapons in the Netherlands since April 1960 and currently deploys an estimated 10-20 nuclear B61 bombs in underground vaults inside 11 aircraft shelters at Volkel Air Base. The weapons are under the custody of the US Air Force’s 703rd Munitions Support Squadron (MUNSS), a 140-personnel unit that secures and maintains the weapons at Volkel.
In a war, the U.S. nuclear bombs at Volkel would be handed over to the Dutch Air Force for delivery by Dutch F-16 fighter-bombers of the 1st Fighter Wing. The Netherlands is one of five non-nuclear NATO countries (Belgium, Germany, Italy, the Netherlands, and Turkey) that have this nuclear strike mission, which clearly violates the spirit of the nuclear Non-Proliferation Treaty.

A B61 nuclear bomb is loaded onto a C-17 cargo plane. Improved B61-12 bombs are scheduled to be deployed to Volkel at the end of the decade.
From 2019 (although delays are expected), the U.S. Air Force would begin to deploy the new B61-12 nuclear bomb to Volkel and the five other bases in Europe that currently store the old B61 types. The B61-12, which is scheduled for production under a $10 billion-plus program, will have improved military capabilities compared with the weapons currently stored at the bases.
The U.S.-Dutch dispute over remediation is but the latest political irritant in the deployment of U.S. nuclear weapons in Europe, a deployment nearly 200 B61 bombs at five bases in six countries that costs about $100 million a year but with few benefits. President Obama has promised “bold reductions” in U.S. and Russian tactical nuclear weapons in Europe. Volkel Air Base would be a good place to start.
This publication was made possible by grants from the New-Land Foundation and Ploughshares Fund. The statements made and views expressed are solely the responsibility of the author.
The Benefits and Challenges of Active Monitoring in Support of Future Arms Control Initiatives
As the United States remains on a path towards continued reductions of nuclear weapons in concert with Russia, there is a likelihood that future arms control initiatives may include individual warheads – strategic and tactical, deployed and non-deployed. Verification of such an agreement could prove to be challenging and costly under an inspection-oriented regime such as that employed by the New START Treaty. As such, the concept of actively monitoring warheads throughout their lifecycle is proposed as a potential solution. An active monitoring system could reduce the burden of inspection activities to achieve equivalent confidence that treaty obligations are being upheld by increasing transparency of operations. Concerns about the sensitivity of data generated are warranted, and generating sufficient trust in the validity of data produced by this system is challenging, yet they are not insurmountable with a thoughtful design. This article explores the active monitoring concept, in addition to highlighting both the challenges and solutions such a system would provide.
Motivation
The Obama administration has clearly stated an interest in continuing reductions of the United States nuclear weapon stockpile in accordance with Russia and the other nuclear weapons states. The New START treaty1, signed in 2010 and ratified in 2011, limits strategic deployed warheads to 1,550 on 700 deployed delivery vehicles, with a total limit of 800 deployed and non-deployed delivery vehicles. In a 2009 speech in Prague, prior to the New START negotiations, President Obama brought a new focus to nuclear arms control by affirming “… America’s commitment to seek the peace and security of a world without nuclear weapons.”2 While also admitting that this is very much a long-term goal, this statement and others made in the same speech set the policy of the United States as seeking to advance arms control goals beyond New START. After stating his plan to negotiate New START, he said that “… this will set the stage for further cuts, and we will seek to include all nuclear weapons states in this endeavor.” Further cuts may happen in a similar fashion to the START and New START treaties – reductions in the numbers of strategic, deployed delivery vehicles and warheads – though as those numbers continue to drop, the numbers of non-deployed and non-strategic (tactical) weapon systems and warheads become more prominent in the debate.
According to the 2010 Nuclear Posture Review, “… the Administration will pursue discussions with Russia for further reductions and transparency, which could be pursued through formal agreements and/or parallel voluntary measures. These follow-on reductions should be broader in scope than previous bilateral agreements, addressing all the nuclear weapons of the two countries …”3 Under New START, all strategic delivery vehicles (missiles, land-based launch tubes, submarine launch tubes, and bombers) are accountable and limited, whether they are deployed or not. A follow-on agreement to New START that limited nuclear warheads and bombs (whether they are deployed or not), would shift the focus from accounting for the delivery system to accounting for the warhead, whether it is mated to a delivery vehicle or not. In addition, an agreement that limited non-strategic warheads and delivery systems would increase the scope of limitations: mildly for the United States, and significantly for Russia.
The shift in focus from delivery systems to warheads and the inclusion of non-strategic systems will make verification of the treaty terms much more difficult. In general, strategic systems are much easier to see from a distance than non-strategic systems and especially individual warheads. In addition, the set of locations that warrants inspections when including non-strategic systems and warheads (in storage, maintenance, etc.) is much larger than the set of locations under New START. Increasing the scope and number of on-site inspections to account for all nuclear weapons may not be desirable due to the large expense to the inspecting nation and impact to operations of the host nation. Therefore, new technical approaches for verification could become useful to ensure that arms control agreements will be maintained and trusted when the scope extends to all nuclear weapons – deployed and non-deployed, strategic and non-strategic.
The Verification Challenge
The verification methods used for New START are essentially the same as those used under START: (1) national technical means, (2) data exchanges and notifications, and (3) on-site inspections.4 National technical means includes all manner of viewing and sensing the actions of the treaty partner from a distance, relying on national intelligence capabilities. Data exchanges and notifications are declaratory tools used to communicate the numbers and locations of all treaty-accountable items (TAIs) at the beginning of the treaty enforcement, at periodic intervals, and when things change. On-site inspections are used to verify those declarations by sending an in person delegation to a limited number of sites in the treaty partner country to view the TAIs at that site. There are two types of New START on-site inspections: Type One inspections focus on sites with deployed and non-deployed strategic systems, while Type Two inspections focus on sites with only non-deployed strategic systems (sites without warheads). During Type One inspections, inspectors have the opportunity to count the number of deployed strategic delivery systems and verify for a single delivery system (including a bomber at an air base), the number of warheads emplaced on it. The relevant inspections for this discussion are Type One.
The goal of verification is to generate a sufficient amount of confidence that the treaty partner is fulfilling their obligations expressed in the treaty. With effective national technical means, fewer and less intrusive on-site inspections are necessary to gain sufficient confidence. When the focus of reductions, and therefore of verification, shifts from strategic delivery systems to warheads and non-strategic systems, national technical means will be less effective. This result could mean that with more intrusive on-site inspections (and probably more inspections with the expanded set of locations of interest), the same amount of confidence can be generated in a new treaty as is generated by New START verification. However, with more inspections that are increasingly intrusive, costs for both sides rise and the impact to host operations suffers, since operations will likely be suspended at the site being inspected for the duration of the inspection.
Passive tags and seals have been suggested as assisting in verification of warheads: a warhead in a container could be sealed, and if the inspector verifies a seal on inspection the inspecting party has some confidence in the integrity of that particular warhead going back to the time it was sealed. But passive seals can only indicate that a seal was broken or not broken. No additional information about a broken seal is available, such as when or why the seal was broken.
An alternative and more comprehensive approach is to use active tags and seals, along with fixed monitoring devices in facilities of interest to create trustable information about the location and integrity of all TAIs. An active monitoring system in support of a future arms control agreement that includes all warheads – strategic and non-strategic, deployed and non-deployed – could reduce the cost of generating sufficient confidence enough to make the agreement feasible, while providing an unprecedented level of transparency.
Active Monitoring Approach
In lieu of increasing inspection frequency and complexity, an active monitoring system could be used to generate sufficient confidence that treaty declarations are being upheld while lessening the burden associated with inspection costs and the impact on operations at military installations. The approach of active monitoring discussed here uses an active tag with a monitored seal, known as an item monitor, which communicates to a centralized data collection point. After being attached and sealed to a TAI, the item monitor and associated data management system provides an indication of where the TAI is at any given point within the nuclear security enterprise –in storage, staging, maintenance, transportation, or deployment. The seal is designed to monitor when the item is physically removed from its handling gear which can occur during shipment, maintenance, or when deployed on a delivery vehicle. The seal design precludes removal of the warhead from its handling gear without breaking the seal. Additional layers of monitoring such as motion detectors, cameras, and other sensors can be added into the system to gather supplemental data and improve transparency of operations, while providing greater confidence in the information generated by the item monitors.
While all nuclear weapons in each country would be accountable and thus part of the monitoring regime, each TAI might not be actively monitored in every stage of its lifecycle. Figure 1 illustrates the seven generic stages of nuclear weapons in the United States, along with the dispositioning stage, which may be of interest for monitoring to account for latent nuclear weapons beyond dismantlement.
The deployment stage shown in the figure specifically represents warheads deployed on a delivery vehicle, and not those in storage at a deployed base (which are still considered in the storage stage).
Refurbishment of a weapon occurs as part of a Life Extension Program in which many components are replaced, whereas weapon maintenance implies a less significant replacement or access to the weapon without replacement, which can be done at the deployment or storage location.
Staging indicates that a weapon is awaiting refurbishment or dismantlement.
Dispositioning is the stage in which the dismantled weapon components are rendered unusable without an effort equal to production of those components.
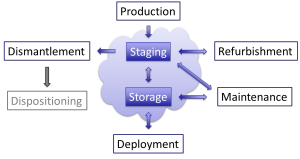
As indicated in Figure 1, TAIs in the staging and storage stages would be continuously and actively monitored. Any integrity breach or movement during these stages would be recorded by the system. The transitions from the production5 and to the dismantlement stages, as well as the transitions to and from the refurbishment, maintenance, and deployment stages would be recorded, though once the TAI is in any of those stages it would not be actively monitored.
Using the United States as a model, there are numerous sites where an active monitoring system would be installed to meet the requirements of a future arms control monitoring regime. Furthermore, within each individual site there could be multiple holding locations for weapons. At each site the information from each holding location would be aggregated and transmitted to a site-wide database. The information from the nation’s weapon sites would then be aggregated at the national level, reviewed, and periodically transferred to the treaty partner who would analyze it to verify declarations as well as discover undeclared activity. Thus, the concept of data exchanges and notifications currently used for New START verification would be retained, albeit with much larger sets of data and potentially more frequent notifications. The treaty partner could then select a sampling of locations and TAIs to inspect to increase confidence and ensure proper system functionality. The concept of on-site inspections would also be retained from New START, though the active monitoring system would limit the number needed to achieve sufficient confidence. A simplified view of this system is shown below in Figure 2 for three separate sites, each with three discrete TAI locations (either storage or maintenance).
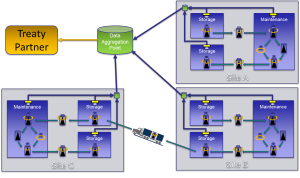
In Figure 2, looking at a particular site there is a single TAI that is sealed and tagged by an item monitor moving from a storage area to a maintenance area and back to a different storage area. While it is in the maintenance area, the seal is broken and the item monitor is removed so that the warhead can be accessed for maintenance. Following the work, the warhead is placed back in its handling gear, which is sealed once again. In each of these locations the item monitor communicates with a data collection unit in the room, sending information during entrance and exit, as well as periodically throughout its existence in the room. In addition, fixed monitoring nodes in each of these locations (such as door switches, motion detectors, and cameras) generate additional information to create layers of evidence. The information generated by the monitoring system in each location – by item monitors as well as fixed monitoring nodes – is passed to a central data aggregation point at the site that combines the information from all locations at the particular site. Each site then passes information to a national data aggregation point, which is then transferred to the treaty partner during periodic data exchanges and more frequently during notifications.
All nuclear weapons that are properly maintained will still require routine maintenance and refurbishment, and these activities will likely occur without inspectors present to avoid releasing weapon design information. In order for the monitoring system to increase the treaty partner’s confidence in the host nation’s declarations of TAI activity, they must first trust that the TAI being monitored is an authentic nuclear weapon – i.e., that the host nation is not playing a shell game. As shown in Figure 3, at the start of a future agreement all TAIs would need to be verified as authentic in what is considered a baseline inspection, and then sealed using the item monitor while the inspecting partner is present. This baseline inspection likely would include measurements of attributes that are agreed upon in negotiations.
Following the baseline inspection at all sites, every nuclear weapon would be entered into the monitoring regime. A TAI with an item monitor attached (and sealed) goes from black to white. In the white (sealed) state, the treaty partner has confidence that that particular TAI is authentic, and thus trusts the information the TAI generated by the monitoring system. The TAI would then continue to move throughout the nuclear security enterprise as required by the host country, with its movements and the status of its seal being continuously monitored. Since nuclear weapons are not static items for the life of a treaty, seals will have to be broken and most likely TAIs will have to be removed from active monitoring for maintenance, refurbishment, and deployment. When performing a maintenance activity on a sealed warhead or preparing a warhead for deployment, the activity would be declared in the same dataset that is transmitted to the treaty partner. Normal operations would not require the presence of an inspector.
Once declared, the seal can be removed and the warhead operation can proceed. After the seal has been opened on a TAI, the authenticity of that item cannot be confirmed until it is inspected by the partner nation, which would likely include the same type of measurements made during a baseline inspection. At that point, the combination of re-establishing the authenticity of the TAI with the record of the TAI being sealed back to a point in the past gives the treaty partner confidence in the TAI from the time of sealing (indicated by the cross-hatched TAI in the figure), even if the treaty partner did not witness that sealing.
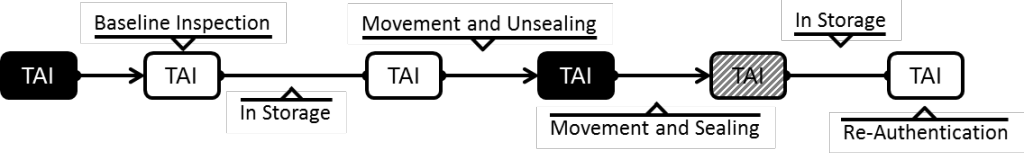
A monitoring system that accounts for individual weapons under a new arms control regime must have two basic characteristics: reliability and trustworthiness. Reliability implies that the system will work as intended with little or no downtime and without generating false information. While reliability is an important attribute of any engineered system, it is especially important in an arms control monitoring system. Any unexpected system behavior or relatively long downtime is likely to raise suspicion in the treaty partner, and would likely require a host country explanation. Trustworthiness is more complex. A system can be trusted by the host if the individual components and software can be shown to not interfere with the safety, security, and reliability of the nuclear weapons or the facilities that house the nuclear weapons (the process of certification). The system can be trusted by the treaty partner if the data it generates can be authenticated, it is hard (i.e. expensive) to forge false data, and the hardware and software used can be verified to not have hidden functionality (the process of authentication). Hardware and software authentication is challenging due to the complexity of integrated circuits and modern programming languages. Authentication concerns could be eased through either a jointly designed system or random sampling of the active monitoring system’s components by the treaty partner to inspect, possibly destructively. Data authentication requires the ability to digitally sign and verify the signature of the data generated by individual item monitors and fixed monitoring nodes, which necessitates the use of cryptographic algorithms to greatly increase the difficulty in forging messages. The system must also take into consideration the usability of the data from the perspectives of both the host and treaty partner to ensure that it is easy to sort and analyze the large quantity of data that will inevitably be collected.
The extent to which each side will assess the system equipment during certification and authentication also depends on who designs and produces the equipment. With host-designed and produced equipment, certification will likely be easier but authentication may be harder. With inspector-designed and produced equipment, authentication will be easier, but certification will be much harder, maybe impossible. A third option (which needs more study), is joint design and third-party (monitored) production. For our analysis, we have assumed host-designed and produced equipment.
The level of transparency associated with the active monitoring approach described here goes beyond any previous sharing of information under former treaties and agreements. Achieving concurrence and buy-in from stakeholders will be challenging – particularly the military services whose base operations may be affected – though the impact of a monitoring system may be less than the impact of the number of on-site inspections necessary in its absence. Additionally, many sensitive and potentially classified characteristics of the nuclear security enterprise could be revealed through the data aggregation and analysis process. To maintain the high level of transparency required for such an arms control regime, it may be necessary to redact portions of the data prior to transmitting it to the partner country. This could be done without degrading the integrity of the remaining data, but still providing enough information to account for warheads in the regime.
Conclusions
Potential arms control initiatives that include limits on total nuclear warhead stockpiles (including non-strategic and non-deployed weapons) and monitoring of warheads awaiting dismantlement may require technical accountability measures that are distinct from the technical measures used in previous treaties. Accountability measures could include active monitoring systems that provide trustable information and assurances of the location and the integrity of nuclear weapons and its components throughout the nuclear weapons lifecycle. Better understanding of active monitoring capability options for declared warheads and potential operational impacts of such a monitoring regime will help prepare for possible future initiatives.
Many challenges to the development and use of a nation-wide monitoring system in the U.S. and its treaty partners in support of a future arms control initiative remain. The scope of technology necessary for this system is much larger than what is used today for New START verification. The sheer complexity will make negotiations long and challenging. Generating trust with this technology may not be easy. Trustable components and information will be a key system attribute to be factored into design. The inspectors must trust the system to generate authentic and correct information, and to be highly resistant to undetected tampering by the host party. In addition, the host must accept the use of this equipment on or near nuclear weapons in their custody, which requires mitigation of concerns about safety, security, and divulging sensitive information. Lastly, no matter how well designed the system, on-site inspections would still be required to verify that the data generated by these systems reflects reality. However, the number of inspections could be minimized while still creating a level of confidence that is statistically significant.
Active monitoring of all nuclear weapons by a system coordinated across all staging, storage, maintenance, and deployment sites may be a key step in building confidence in such an agreement and reducing the need for on-site inspections to the point where the agreement is realizable. While 100% confidence in verification will be difficult, a system can be engineered to increase confidence that an agreement is being upheld by identifying the location and status of each TAI in an assured and trusted way to the monitoring partner, as well as providing layers of evidence of monitoring activities using various sensors and imagers. A flexible system will allow weapons to be accounted for and actively monitored through various phases of their lifecycle, thus enabling verification and increased confidence in weapons reductions. Research into the concept of an active monitoring system, including the operational impacts of such a system – and technology to support the concept – should be an element of a research agenda to support future negotiations for a new bilateral or multilateral arms control agreement.
Jay Kristoffer Brotz is a Senior Systems Engineer in the Nuclear Monitoring and Transparency Department at Sandia National Laboratories in Albuquerque, NM. His work is primarily on the Chain of Custody project, in which he is the Hardware and Operations Design Lead. He is primarily concerned with the development and evaluation of candidate technologies to be used as monitoring nodes at the Chain of Custody Test Bed. Last year, Jay participated in the Next Generation Working Group on U.S.-China Nuclear Relations, a function of the Center for Strategic and International Studies (CSIS) Project on Nuclear Issues (PONI). Jay graduated with a B.S. in Computer Engineering from Rose-Hulman Institute of Technology and an M.S. in Electrical and Computer Engineering from Carnegie Mellon University, where he wrote a Master’s thesis on damping of mechanical resonators fabricated in a CMOS-MEMS process.
Justin Fernandez is a Senior Member of the Technical Staff at Sandia National Laboratories. Justin’s experience and expertise lies at the intersection of technology and policy, with a focus on international nuclear relations and arms control. For the past two years he has led test and evaluation activities between three national laboratories for nuclear monitoring and transparency technologies geared towards supporting future arms control initiatives. Prior to his current position, Justin worked for three years on testing and evaluating the compatibility of Sandia developed technologies with US Air Force and NATO aircraft platforms. Justin obtained his B.S. and M.S. in Mechanical Engineering from Rutgers University and Georgia Institute of Technology respectively.
Dr. Sharon DeLand is a System Analyst in the Nuclear Monitoring and Transparency Department at Sandia National Laboratories. She received her doctorate in experimental condensed matter physics from the University of Illinois in 1991. Sharon’s current research interests include developing and evaluating technical approaches for monitoring arms control agreements, especially approaches focused on item accountability. Her work focuses on systems approaches that integrate technical monitoring objectives with policy perspectives and operational constraints. She also applies systems analysis to the modeling and simulation of international relations, with an emphasis on nonproliferation and arms control.
The opinions expressed in this paper are the authors’ own and do not reflect the opinions or official policy of Sandia National Laboratories, the National Nuclear Security Administration, or the United States Government.
President’s Message: Innovative Ideas to Reduce Nuclear Dangers
We at FAS are always looking for innovative thinking on reducing nuclear dangers. This issue features both emerging leaders in the field and seasoned practitioners who are advancing new ways of looking at nuclear education, arms control monitoring, deterrence, and lessons from historical perspectives. Three of the articles have lead authors from the younger generation.

Erika Suzuki, who leads UC Berkeley’s Nuclear Policy Working Group, has joined with Dr. Bethany Goldblum, a younger faculty member, and Dr. Jasmina Vujic, a senior faculty member who has mentored dozens of Ph.D. and M.S. degree students. They describe a new model for educating students about nuclear technology and security policy. Their goals are to develop and sustain “an enduring nuclear security workforce,” to build bridges among “professionals from technical and social science fields,” and “to generate original policy recommendations and technical working papers.” They want to extend their work to many universities and educational institutions. For PIR readers who are educators in the nuclear security and policy field, we encourage you to contact Erika and her co-authors to find out how you can help advance this important new project.
Ravi Patel, a talented, younger biologist from Stanford, worked last summer at FAS as a security scholar and began researching how to create stability between India and Pakistan. After travel to South Asia and extensive interviews and other research, Mr. Patel wrote the article in this issue on “Using Trade to Build Stability in South Asia.” He discusses four major steps: (1) forming a uniform, jointly developed trade policy, (2) having Pakistan grant Most-Favored-Nation status to India, (3) improving infrastructure linking India and Pakistan, and (4) improving ties between the Indian and Pakistani business communities. He points out that it is often easier to ship goods between the two countries through third party countries such as the United Arab Emirates because of the impediments to direct trade. Although his article does not directly address the nuclear arms race in South Asia, it provides advice on ways to indirectly reduce nuclear tensions.
Recently, I had the pleasure of meeting Jay Brotz at a conference at the University of California’s Washington, DC, Center and was impressed with the work that he and his co-authors Justin Fernandez and Dr. Sharon DeLand are performing at Sandia National Laboratories. As discussed in their article, they are developing and analyzing models for monitoring nuclear warheads in potential future arms control treaties or agreements. Up to now, nuclear arms control agreements between Russia and the United States have primarily focused on inspecting and monitoring strategic weapon systems because of the relative ease of monitoring these objects that are much bigger than individual warheads. When individual warheads are monitored, the inspection system has to provide reliable information to the treaty partner but not reveal sensitive design information about the warhead. Brotz et al. discuss how to achieve that balance.
On FAS’s staff, we are privileged to have senior scholars such as Dr. Robert S. Norris and Hans Kristensen. For many years, they have co-written the Nuclear Notebook in the Bulletin of the Atomic Scientists, which is the most authoritative, unofficial source of information on the status of worldwide nuclear forces. In this issue, they have separate articles. Dr. Norris, a leading historian of nuclear weapons, shines a spotlight on the three factors that stoked the nuclear arms race: (1) inter-service rivalry among the branches of the U.S. armed forces, (2) the tenet that the United States could achieve security through technical superiority in nuclear weaponry, and (3) the “hyperactive definition of deterrence,” which resulted in “very high degrees of readiness” to launch an attack. This historical legacy weighs heavily on contemporary nuclear policy as examined in the final article by Hans Kristensen.
The PIR presents Mr. Kristensen’s invited presentation to the Deterrence and Assurance Working Group at the U.S. Air Force’s Global Strike Command at Barksdale Air Force Base in Louisiana. He raises profound questions about how many nuclear weapons are enough, what are the roles and tasks for nuclear weapons, and whether and how the United States can continue to reduce nuclear targeting and alert levels of nuclear forces. He advises the Air Force Global Strike Command to not resist further reductions but instead “sustain sufficient deterrence and assurance at lower levels.”
We hope you find these articles enlightening. We are grateful for your support of FAS.
Charles D. Ferguson, Ph.D.
President, Federation of American Scientists
Building a Foundation for the Future of Nuclear Security
“The need for understanding of today’s evolving nuclear threats is critical to informing policy decisions and diplomacy that can move the world toward greater nuclear security. The scientific underpinnings for such an understanding are remarkably broad, ranging from nuclear physics and engineering to chemistry, metallurgy and materials science, risk assessment, large-scale computational techniques, modeling and simulation, and detector development, among others. These physical science disciplines must be combined with social science fields such as public policy, political science, international relations, international law, energy policies, economics, history, and regional studies in order to yield a deep understanding of today’s nuclear security challenges.”
-James Doyle, “Nuclear Security as a Multidisciplinary Field of Study,” Los Alamos National Laboratory, 2008
The future of domestic and global nuclear security depends on today’s university students and young professionals feeding the pipeline to supply the requisite scientific workforce. To develop the next generation of nuclear security experts, universities must not only train students in technical nuclear science but also provide a comprehensive educational platform including nuclear energy and weapons policy in the context of the current political science architecture. Nuclear-related education programs are gaining traction, bolstered by the 2010 Nuclear Forensics and Attribution Act and other government initiatives such as the National Nuclear Security Administration (NNSA)’s Global Threat Reduction Initiative (GTRI).1
However, many of these programs are geared towards training students already engaged in nuclear science graduate programs. To maintain a steady stream of experts in nuclear security, universities must also actively recruit students in the early stages of their academic career by incorporating undergraduate educational initiatives and pre-professional development through both traditional classroom-based and extracurricular programming.
A working group model established at the University of California, Berkeley provides a pathway through which educational institutions with an established nuclear science program can initiate and further enhance nuclear security educational programming targeting students from all academic career stages.
The PRI(M)3E Model
The PRI(M)3E model was developed by the UC Berkeley Nuclear Policy Working Group (NPWG) in October 2012.2The model is derived from the three-fold mission statement of the NPWG. The first focus is to educate undergraduate students on important issues in nuclear security by providing supplementary education on nuclear technology and policy. The second aim is to foster collaboration between students and professionals from technical and social science fields. The third core goal of the NPWG is to generate original policy recommendations and technical working papers to contribute to the nuclear security field. From these primary objectives, the NPWG developed a foundational model to educate the next generation of nuclear scientists and policymakers.
The PRI(M)3E model features seven key components that are essential for developing and sustaining an enduring nuclear security workforce:
- Pioneering
- Group discussions, collaborative research, and open communities facilitate the innovation of novel techniques for strengthening nuclear security through technological advancements and action-oriented policy. This environment allows for the unconstrained development of best practices for the education of undergraduate and graduate students in nuclear security.
- Research
- A research-based working group allows members to collaborate on technical and policy-focused research projects addressing an array of critical nuclear security topics.
- Interdisciplinary
- Interactive workshops draw from both the physical and social sciences, encouraging students to develop a strong foundational knowledge base in nuclear security to best inform research projects and policy recommendations.
- M3
- Mentorship
- Opportunities are made available for undergraduate and graduate students to work closely with senior mentors to share insight, career advice, and guidance on next steps towards a career in the nuclear security field.
- Multi-level
- Students at all stages of their academic career- from freshmen through senior-level undergraduate and graduate students, post-doctoral researchers, staff scientists from the university and the national laboratories, and non-academic professionals engage in collaborative needs- driven research in nuclear security and associated applications.
- Multimedia
- Participants use a variety of media including various audio-visual presentation platforms, workshops, expert panel discussions, student seminars, and digital electronic technology to convey important concepts and foster debate.
- Mentorship
- Education
- Education of working group members, the campus community, and the general public via accurate, timely information on current developments in nuclear security technology and policy is central to the multistage mission.
Implementation of the PRI(M)3E model serves as a framework that enables the NPWG to fuel the nation’s nuclear security workforce pipeline. Each component of the PRI(M)3E model uniquely targets the recognized need for interdisciplinary training of nuclear experts, integrates a research unit into the overall educational platform, and translates multi-level interaction into mentorship to provide undergraduate and graduate students with career guidance in both the scientific and policy fields. The working group is designed to generate a cadre of experts with both well-rounded and in-depth knowledge of the technical and policy-oriented aspects of nuclear security through comprehensive, research-based, educational programming.
The NPWG is a low-cost, high-impact model. The budget for running a successful working group is minimal compared to the potentially substantial financial and institutional investment required to establish a certificate or degree program, while the organizational structure of the PRI(M)3E model allows for the achievement of comparable educational objectives. Should institutional priorities shift to the adoption of more traditional educational models, the PRI(M)3E model lays the foundation for the future development of degree programs. Further, the inclusive nature of the working group makes it accessible to students at all levels as well as to the general public. Student retention represents the primary challenge to the success of the PRI(M)3E model. The informal nature of the working group can result in difficulties maintaining a core group of students, many of whom may juggle numerous responsibilities and commitments, including academics, work, and other extracurricular activities. To reduce attrition, the NPWG strives to actively engage members using a variety of media and activities, and works with members to develop flexible working practices.
Beyond the Foundational Model: Practices and Results
The PRI(M)3E model is particularly instrumental at UC Berkeley, which has a highly divided campus layout like many research-oriented universities. Almost all of the social science departments are located on the southwest side of campus, while the physical sciences are based on the northeast side of campus. As a result, students from different disciplines often do not physically interact with one another, and opportunities for interdepartmental collaboration between the technical and social sciences at the undergraduate level are sparse. The NPWG serves as a bridge between these two spheres on campus, and establishes a space in which students from various disciplines can interact and collaborate on interdisciplinary research projects.
The principal goals of the PRI(M)3E model are institutionalized through the activities of the NPWG. At weekly research meetings, members discuss research progress and future direction, and contribute to colloquia where participants present on a nuclear security topic of their choice. The multidisciplinary nature of the NPWG is one of its greatest strengths, as students from the nuclear engineering, physics, astrophysics, electrical engineering and computer science, political science, and public policy departments share knowledge and draw on their individual strengths to contribute to joint research projects and weekly seminar presentations. This working group series provides students with opportunities to continually develop dynamic working relationships with other students, as well as senior mentors. The development of close, effective mentor relationships is highly beneficial to undergraduate professional development, as advisors encourage students to apply for internships at the national laboratories or other nuclear security institutions, impart career and internship advice, and support the academic growth of students throughout the learning process.
To expand its educational outreach initiative to the general public, the NPWG hosted its first annual Nuclear Security Panel in April 2013, which featured prominent nuclear security experts well versed in both the technical and social science aspects of the field (see Fig. 1). The panel event generated lively debate and educated the broader campus community on current issues in nuclear forensics. This interdisciplinary team of experts provided the UC Berkeley campus and the public with a multifaceted examination of the role of nuclear forensics in combating nuclear terrorism, and also served as a public forum for discussion.

Nuclear Security Panel featuring (from left to right) Ian Hutcheon, Michael Nacht, Jasmina Vujic (moderator), Raymond Jeanloz, Stan Prussin and Jay Davis.
The NPWG also showcased its practices and results at several technical and policy conferences to disseminate the PRI(M)3E methodology for student engagement and communicate contributions to the nuclear security field in the form of original policy recommendations (see Fig. 2). These events provided undergraduate and graduate students with professional development opportunities, occasions to cultivate and hone presentation skills, and networking opportunities with nuclear security professionals from around the globe. Feedback from these colleagues has been vital to the enhancement of working group practices and research project design.
Through these PRI(M)3E-based endeavors, the NPWG has trained a first-year cohort of fifteen members and conducted educational outreach on numerous occasions in both technical and public policy capacities.

Institute on Global Conflict and Cooperation 2013 Winter Public Policy and Nuclear Threats Conference. NPWG Undergraduate Research Assistant Erika Suzuki with Ambassador Linton Brooks.
Institutional support has been critical to the success of the NPWG and is essential for the long-term efficacy of the working group model. The NPWG is currently supported through an educational programming grant provided by the Nuclear Science and Security Consortium (NSSC) through the Institute on Global Conflict and Cooperation. The NSSC is a $25 million grant with UC Berkeley as the lead institution that was awarded by the National Nuclear Security Administration (NNSA) to support its NA-22 Nonproliferation Research and Development mission. The purpose of the NSSC is to train and educate experts in the nuclear security field using “an end-to-end approach, from recruitment of undergraduates to early career phases,” – the SUCCESS PIPELINE (Seven Universities Coordinating Coursework and Experience from Student to Scientist in a Partnership for Identifying and Preparing Educated Laboratory-Integrated Nuclear Experts). The NPWG operates at the foundational level, recruiting and educating undergraduate students, providing them with opportunities to collaborate with and learn from advanced students and professionals actively engaged in the nuclear security field.
SUCCESS PIPELINE NSSC3
At the input end of the pipeline, highly promising undergraduate and graduate students who have shown relevant interests are exposed to nuclear security. The program couples basic science research to technological developments relevant to the nuclear security mission. Student education includes hands-on training in a broad set of experimental disciplines—at university facilities and, as a formally constructed and supported aspect of their education, at the Lawrence Berkeley, Lawrence Livermore, Los Alamos, or Sandia National Laboratories. Between the academic and the national laboratory partners exist an array of facilities including nuclear reactors, cyclotrons and other particle accelerators, as well as detector development and characterization facilities. Summer schools and seminars broaden student exposure to a wide range of topics in the nuclear security mission. This approach is designed to not only recruit but also retain top students by exposing them to a diverse and exciting research portfolio of critical importance to the U.S. nuclear security mission. The graduate will be a well-rounded professional ready to contribute to nuclear security and step into leadership roles in the field.
Future Vision
In an effort to further develop and sustain an enduring expertise pipeline, the NPWG will be launching its Nuclear Security Initiative (NSI) in the coming year. The purpose of the NSI is to extend the NPWG across NSSC partner institutions to engage a larger cross section of students in interdisciplinary nuclear security science, provide foundational knowledge on nuclear science and policy, and train students to work collaboratively on technical research projects and policy recommendations. The NSI is a refined version of the NPWG’s efforts based on the PRI(M)3E model, and expands on the NPWG’s research focus on nuclear forensics to include nuclear terrorism, nuclear material security and nonproliferation. The NPWG thus serves as a feeder for the NSSC’s SUCCESS PIPELINE at a micro-level, and duplication of its practices via the NSI will support the development of a robust national nuclear security network among universities, national laboratories, government agencies, and industrial institutions.
Conclusion
Universities are increasingly impacted by state and federal budget cuts, so the role of institutional support has intensified. Most prominently, the recent sequester cuts will reduce the available pool of research funds by an estimated $1 billion.4This will not only affect the ability of researchers at universities and national laboratories to obtain grants from federal science-based organizations, but will also potentially decrease the number of graduate students admitted to science and engineering programs at universities that rely heavily on federal funding.5 The loss in funding coupled with a reduced number of doctoral students in these fields may hinder scientific progress and shrink the pipeline as fewer students pursue advanced degrees in science and engineering. Cultivating the future scientific workforce is crucial to operations at the national laboratories, which will face a shortage of staff scientists in the coming years due to a combination of scheduled retirements and voluntary early retirement policies stemming from the sequestration budget cuts.
As we enter the new academic and fiscal year this fall, universities and other educational institutions will need to supplement losses in research and graduate programs with lower-cost, extracurricular modes of learning. The PRI(M)3E model is one such pathway to establish a rich environment for the generation of debate and novel direction on critical nuclear security issues while engaging students outside of a traditional classroom setting. This interdisciplinary approach to academic programming is crucial for securing the future of domestic and global nuclear security, as it provides a means for involving students from various disciplines to cooperatively address the multifaceted and vital nuclear issues that permeate the current landscape of national defense. Training future nuclear scientists and policymakers to collaborate on nuclear issues will forge better-informed and better-implemented nuclear policy and practices, and will ultimately result in the maintenance of a strong, sustainable nuclear security infrastructure.
Erika Suzuki leads the University of California, Berkeley’s Nuclear Policy Working Group in support of the Nuclear Science and Security Consortium. Erika has taught three student elective courses on human rights, the politics of genocide, and California/UC labor policy that she developed through the Democratic Education at Cal program. She has also interned for Democratic Leader and Congresswoman Nancy Pelosi, the American Federation of State, County, and Municipal Employees Local 3299, and Berkeley Rent Board Commissioner Igor Tregub. She is an alumna of the 2012 Berkeley Haas School of Business Summer Program: Business for Arts, Science, and Engineering, and is a member of Delta Phi Epsilon, a co-ed, professional Foreign Service and international affairs fraternity. After graduating from UC Berkeley with a Bachelor of Arts degree in Political Science and Public Policy, Erika aspires to work as a nuclear policy analyst focusing on nuclear counterterrorism and nonproliferation efforts, and obtain an advanced degree in international security studies.
Bethany L. Goldblum received a Ph.D. in Nuclear Engineering from the University of California, Berkeley in 2007. She served as a Clare Boothe Luce Chancellor’s Postdoctoral Fellow at Berkeley before joining the nuclear engineering faculty at the University of Tennessee, Knoxville in August 2010. In January 2012, she returned to Berkeley as a member of the research faculty. Her research interests are in the areas of fundamental nuclear physics for nuclear security applications, nuclear-plasma interactions, technical nuclear forensics, and nuclear energy and weapons policy. From 2004-2006 she held the National Science Foundation Public Policy and Nuclear Threats Fellowship. She was a Project on Nuclear Issues Scholar at the Center for Strategic and International Studies and a member of the United States delegation to the China-India-United States Workshop on Science, Technology and Innovation Policy in Bangalore, India. She is the founder of the Nuclear Policy Working Group at UC Berkeley, an interdisciplinary team of undergraduate and graduate students focused on developing policy solutions to strengthen global nuclear security.
Jasmina L. Vujic is Professor of Nuclear Engineering at the University of California, Berkeley. She received her Ph.D. in Nuclear Science from the University of Michigan, Ann Arbor, in 1989. After working at Argonne National Laboratory she joined UC Berkeley faculty in 1992. From 2005 to 2009 she was the Chair of the Department of Nuclear Engineering at UC Berkeley and in 2009/2010 she chaired the Nuclear Engineering Department Heads Organization (NEDHO). Her research interests are in the areas of nuclear reactor analysis and design, neutronics and neutron physics, non-proliferation and nuclear security, and engineering aspects of medical imaging and cancer therapy. She is currently a Principal Investigator for two large research projects (over $30 million): the Nuclear Science and Security Consortium and the Berkeley Nuclear Research Center, involving close to 150 students, faculty and researchers from 7 partner universities and 4 national laboratories. Professor Vujic is the author of three books, the editor of 6 monographs and international conference proceedings, and the holder of one U.S. patent. She authored close to 300 research publications. Under her mentorship 24 students received the Ph.D. degrees and 22 received the M.S. degrees.
This article was prepared as an account of work sponsored by an agency of the United States Government. Neither the United States Government nor any agency thereof, nor any of their employees, makes any warranty, express or implied, or assumes any legal liability or responsibility for the accuracy, completeness, or usefulness of any information, apparatus, product, or process disclosed, or represents that its use would not infringe privately owned rights. Reference herein to any specific commercial product, process, or service by trade name, trademark, manufacturer, or otherwise does not necessarily constitute or imply its endorsement, recommendation, or favoring by the United States Government or any agency there of. The views and opinions of authors expressed herein do not necessarily state or reflect those of the United States Government or any agency thereof.
This material is based upon work supported by the Department of Energy National Nuclear Security Administration under Award Number DENA0000979. We also gratefully acknowledge support from the Nuclear Science and Security Consortium, the Institute on Global Conflict and Cooperation, and the Berkeley Nuclear Research Center.
MSNBC On Nuclear Weapons Reduction Efforts
By Hans M. Kristensen
MSNBC used FAS data on the world nuke arsenals in an interview with Ploughshares Fund president Joe Cirincione about how deteriorating US-Russian relations might affect efforts to reduce nuclear arsenals.
The updated weapons estimates on the FAS web site are here.
Detailed profiles of each nuclear weapon state are published as Nuclear Notebooks in the Bulletin of the Atomic Scientists.
Support our work to produce high-quality estimates of world nuclear forces: Donate here.
Russian Missile Test Creates Confusion and Opposition in Washington
The recent test-launch of a modified Russian ballistic missile has nuclear arms reduction opponents up in arms with claims that Russia is fielding a new missile in violation of arms control agreements and that the United States therefore should not pursue further reductions of nuclear forces.
The fact that the Russian name of the modified missile – Rubezh – sounds a little like rubbish is a coincidence, but it fits some of the complaints pretty well.
Although many of the facts are missing – what the missile is and what the U.S. Intelligence Community has concluded – public information and statements indicate that the missile is a modified RS-24 Yars (SS-27 Mod 2) with intercontinental range.
Whatever the missile is, it is certainly no reason for why the United States should not seek to reduce U.S. and Russian nuclear forces further. On the contrary, the continued modernization of nuclear weapons underscores why it is important that the United States continues its push for reducing the numbers and role of nuclear weapons.
The Accusations
Under the headline “Russian Aggression: Putin violating nuclear missile treaty,” the article on Washington Times Free Beacon web site accuses Russia of being engaged in “a major violation” of the terms of the Intermediate-range Nuclear Forces (INF) Treaty signed with the United States in 1987.
The treaty bans all nuclear ground-launched ballistic and cruise missiles with range between 500 and 5,500 km (about 300-3,400 miles).
Claims of Russian cheating are frequent in the Washington arms control debate – just as claims about U.S. cheating is frequent in the Moscow arms control debate – and the ones in the article are largely consistent with the claims made by Mark Schneider, a former DOD official and now with the National Institute for Public Policy.
The “new” in the article is that it quotes “one official” saying: “The intelligence community believes it’s an intermediate-range missile that [the Russians] have classified as an ICBM because it would violate the INF treaty.” In total, “Two U.S. intelligence officials said the Yars M is not an ICBM,” according to the article.
Two members of Congress, House Armed Services Committee chairman Howard “Buck” McKeon (R-CA) and House Permanent Select Intelligence Committee chairman Mike Rodgers (R-MI), have written President Obama about alleged Russian violations. They complain that they haven’t received a response but the administration says it deals with treaty compliance issue directly with Russia and informs Congress accordingly.
Accusations Disputed
The accusations that the Yars-M is not an ICBM and in violation of the INF Treaty are disputed by Russian officials and, interestingly, previous flight tests of the missile itself.
To its credit, the Washington Times took the trouble of asking Colonel General Victor Yesin about the missile. Yesin is former Chief of Staff of the Russian Strategic Rocket Forces and apparently a consultant to the Chief of the General Staff. But Yesin clearly disputed the claim by the U.S. intelligence officials, saying that the Yars-M is a “Topol-M class ICBM” and that “its range is over 5,500 km.”
That assessment fits the description made by a source in the General Staff in November 2012, following the first Yars-M launch from Kapustin Yar in October 2012 and news media rumors that Russia was developing a “fundamentally new missile.” “There are no fundamentally new missiles ‘on the approach’ for [the Russian Strategic Rocket Forces]. We are talking about modernizing the existing Yars class by improving the warhead,” he told Interfax and explained:
“Take the Layner [modification of the SS-N-23] sea-based intercontinental ballistic missile, reported by some media to be a completely new missile. It is in fact a Sineva. Only the warhead is new. Novelty lies in greater missile defense penetration capabilities, achieved owing to, among other things, a greater number of re-entry vehicles (boyevoy blok) in the warhead. The same applies to the prototype missile that was successfully launched from Kapustin Yar (Astrakhan Region) recently. There is nothing new in the missile itself. Only the ‘head’ is new. Its creators went down the same route as the designers of the Layner.”
Moreover, the claim that the short flight range of the missile test launched from Kaputsin Yar in June 2013 would indicate that the Yars-M is not an ICBM ignores that an earlier flight test of the missile last year flew 5,800 kilometers from Plesetsk north of Moscow to the Kura test range on the Kamchatka Peninsula (see table).
After the May 2012 flight test, Colonel-General Vladimir Zarudnitsky of the General Staff said: “As part of the approved plan of your building the armed forces of the Russian Federation last night made a promising test launch rocket system” Frontier “with an intercontinental ballistic missile high-precision shooting.” (Emphasis added).
Col. Vadim Koval, a Russian defense ministry spokesperson, said “the main goals and tasks of the launch consisted of receiving experimental data on confirming the correctness of the scientific-technical and technological decisions in developing the intercontinental ballistic missile as well as checking the performance and determining the technical characteristics of its systems and components.” (Emphasis added).
Rather than an entirely new missile, Koval explained further, “This missile is being created by using and developing, to the maximum extent, already existing new capacities and technological solutions, which were obtained in the development of fifth generation missile complexes, which substantially reduces the terms and expenditures on its creation.”
After the successful initial launch from Plesetsk, the second test was moved to Kapustin Yar apparently to test the capability of the Yars-M payload to evade ballistic missile defense systems. An industry sources told Interfax that, “The use of new fuel is one of the features of the missile. It reduces boost phase engine operation time. Consequently, the missile’s capabilities to penetrate missile defense will go up.”
It is rare, but not unheard of, that ICBMs are launched from Kapustin Yar into the Sary-Sagan test range. It appears to happen when ICBM payloads are being tested against missile defense systems. In addition to the recent tests of the modified SS-27, an SS-25 was test launched from the site on June 7, 2012. The test flight verified the “extended service life” of the SS-25 and “the latest test of an ICBM combat payload.” During the test “information was received which in future will be used in the interests of developing effective means for overcoming missile defense,” according to the Russian Ministry of Defense.
After the June 2013 test, Deputy Prime Minister Dmitry Rogozin, called the modified SS-27 a “missile defense killer.”
It is not unusual that ballistic missiles with intercontinental range are test-flown in a compressed trajectory with much shorter range. That doesn’t make them less than strategic weapons, however. In March 2006, for example, the U.S. Navy launched a Trident II D5 sea-launched ballistic missile with a range of well over 7,400 kilometer (4,000 miles) in a compressed trajectory of 2,200 kilometers (1,380 miles) – about the same range as the Yars-M test on June 6, 2013. No one has suggested that the Trident II D5 therefore is an INF weapon.

The USS Tennessee (SSBN-734) launches a Trident II D5 SLBM on March 2, 2005, on a compressed trajectory of only 2,200 km – about the same range as the Yars-M test in June 2013.
Conclusions and Recommendations
If there are Russian violations of the INF Treaty, then the United States certainly should raise it directly with Moscow.
But the claim that the Yars-M missile flight-tested on June 6 to a range of 2,050 kilometers is an intermediate-range ballistic missile in violation of the INF treaty seems strange since the same missile apparently was flight tested to an ICBM range of 5,800 kilometers just a year ago.
Of course, we don’t know who the U.S. intelligence officials cited in the Washington Times article are, if what they say is accurate, and to what extent it reflects a coordinated assessment by the U.S. Intelligence Community. We may learn more about the Yars-M in the future.
But several Russian government, military, and industry officials have consistently stated that the Yars-M is not a new missile but a modification of the RS-24 Yars (SS-27 Mod 2) and that it has intercontinental range.
The intension of the allegations in the article seems clear: to create doubts about further reductions of U.S. nuclear forces. One of the “officials” quoted in the article directly questions: “How can President Obama believe [the Russians] are going to live up to any nuclear treaty reductions when he knows they are violating the INF treaty by calling one of their missiles something else?”
The thought that Americans would use INF treaty allegations to argue against reducing the number of strategic nuclear weapons that can hit the United States seems kind of bizarre. After all, under current Russian war plans, many of the 400-500 warheads President Obama has proposed can be offloaded under a new agreement, are most likely currently tasked to hold at risk several hundred targets in the United States – including some in California and Michigan.
Since Russia – unlike the United States – is already below the New START Treaty limit on deployed nuclear weapons and likely to drop further before the treaty enters into force in 2018, it seems like a no-brainer that it is in the U.S. interest to nurture that trend by reducing its own forces further.
This is even more important because the very reason some Russian officials could potentially be tempted to argue that an INF-missile was needed is that China is modernizing of its medium-range missile forces. Ironically, many of those in the United States who make the accusations about Russian INF violations are the same people who also warn about China’s nuclear modernization.
What the article completely seems to miss is that the only way that China and smaller nuclear weapons states may be persuaded to place limits on their nuclear arsenals is if the United States and Russia take bold steps to reduce their still enormous nuclear arsenals. Why then nitpick about dubious INF accusations to block that from happening?
This publication was made possible by grants from the New-Land Foundation and Ploughshares Fund. The statements made and views expressed are solely the responsibility of the author.