Rebuilding Environmental Governance: Understanding the Foundations
Today we are facing persistent, complex, and accelerating environmental challenges that require adding new approaches to existing environmental governance frameworks. The scale of some of them, such as climate change, require rethinking our regulatory tools, while diffuse sources of pollutants present additional difficulties. At the same time, effective governance systems must accommodate the addition of new infrastructure, housing, and energy delivery to support communities. Our legal framework must be sufficiently stable to enable regulation, investment, and innovation to proceed without the discontinuities and gridlock of the past few decades.
In an increasingly divided atmosphere, it will take candid, multiperspective dialogue to identify paths toward such a framework. This discussion paper explores the baseline that we’re building on and some key dynamics to consider as we think about the durable systems, approaches, and capacity needed to achieve today’s multiple societal goals.
The early 20th Century saw the emergence of our first national laws regulating public resources— the Federal Power Act in the 1930s, the precursor to the Clean Water Act in the 1940s, and the first version of the Clean Air Act in the 1950s. Then, in a concentrated decade of new laws and massive amendments to existing ones, the 1970s saw a focus on assessing, controlling, and reducing pollution, while setting ambitious goals for human and ecosystem health. These statutes generally were constructed around specific resources—airsheds, watersheds, public lands, and wildlife habitat—and articulated specific roles for federal agencies and other levels of government. State efforts were incorporated into a nationwide system of cooperative federalism, while many states undertook their own initiatives to address environmental problems.
For half a century these laws—enacted with overwhelming, bipartisan congressional support— produced a great deal of success, with conventional pollution decreasing across many resources and regions and some species and habitats recovering. But we have plateaued in terms of broad improvements, and meanwhile novel pollutants and more diffuse, global threats have emerged. Political shifts, legacy economic interests, and a changing information landscape have played an important role, as amply recounted elsewhere.
The bipartisan legislation of the 1970s arose from both idealism and necessity, during an Earth Day moment that embraced ecological thinking in response to tangible harms to humans and the environment. The laws enjoyed massive public support and got many things right. Some were aspirational and holistic, such as the Clean Water Act’s “zero-discharge” target or NEPA’s vision “to create and maintain conditions under which man and nature can exist in productive harmony, and fulfill the social, economic, and other requirements of present and future generations of Americans.” The latter Act established the Council on Environmental Quality to coordinate this policy across the entire federal government.
Other advances came piecemeal, focused on specific resources. The U.S. Environmental Protection Agency (EPA) was cobbled together by an executive plan to reorganize several existing agencies and offices, then granted authority in a series of media-specific statutes that began with the Clean Air Act, Clean Water Act, and Safe Drinking Water Act, and later the Toxic Substances Control Act and Federal Insecticide, Fungicide, and Rodenticide Act. The Resource Conservation and Recovery Act, Superfund, and Oil Pollution Act addressed hazardous substances affecting the nation’s health and ecosystems. Implementation of all these laws required the Agency to develop in-house scientific expertise and detailed regulations that fleshed out statutory standards and applied them to specific sectors—an approach upheld for decades by the Supreme Court.
These laws made unquestionable progress on conventional pollution and waste, the visible, toxic byproducts of industrial production and consumer culture that had spurred the environmental movement and drawn a generation of lawyers to the new profession. But with specialization came fragmentation of environmental law into a plethora of subtopics, and a managerial, permit-centric legal culture that risked losing sight of ecological goals. Nor were the benefits distributed equally by race or class, as demonstrated by pioneering studies in the field of environmental justice.
As the field matured, it slowed, with congressional interventions becoming less frequent and more technical. Some of the last major amendments to a bedrock environmental statute were the Clean Air Act Amendments of 1990, enacted by a bipartisan Congress and signed by President George H.W. Bush. (The other prominent example is the Frank R. Lautenberg Chemical Safety for the 21st Century Act (Lautenberg Chemical Safety Act), a major amendment to TSCA in 2016.) Absent updated legislation, EPA regulations became paramount, but these had to run a gauntlet of shifting policy priorities, complex rulemaking procedures, litigation, and a transformed and often skeptical Supreme Court.
Critiques of this system date back almost as far as the statutes themselves. One ELI study listed 34 major “rethinking” efforts emanating from academia, blue-ribbon commissions, and NGOs between 1985 and 2014, across the political spectrum and ranging from incremental reforms to radical reinvention. One highly touted initiative, led by sitting Vice President Al Gore, resulted in some modest administrative streamlining. Most remained paper exercises, appealing to good-government advocates but lacking political support.
The stakes grew higher with increasing awareness of climate change. In June 1988, NASA and book-length treatments followed, sparking broad discussion of what was then a fully bipartisan issue. Vice President Bush campaigned on addressing it, and as President in 1992, he traveled to Rio de Janeiro to sign the U.N. Framework Convention on Climate Change. With successes like the 1987 Montreal Protocol on the ozone layer or EPA’s 1990 Acid Rain Program doubtless in mind, the Senate ratified the Framework Convention 92-0.
But climate change implicates much larger portions of the U.S. economy—energy, transportation, agriculture—at individual as well as industrial scales. While NEPA embodied the 1960s slogan that “everything is connected,” the lesson of climate change is that many things emit greenhouse gases, and all things will be affected by global warming. The need for systemic change proved to be an uneasy fit with existing site-specific, media-specific environmental laws.
Growing awareness of climate change and the scale of action needed to address it also generated a backlash from entrenched economic interests. By the mid-2000s, the Bush/Cheney administration had reversed course on federal climate commitments. It contested and lost Massachusetts v. EPA, a landmark ruling in which a narrowly divided Supreme Court held that the Clean Air Act applies to greenhouse gas emissions that affect the climate.
The Administration’s argument was captured by Justice Antonin Scalia’s flippant remark in dissent that “everything airborne, from Frisbees to flatulence, [would] qualif[y] as an ‘air pollutant.’” In Scalia’s opinion, real pollution must be visible, earthbound, toxic, inhaled, not a matter of colorless molecules interacting in the stratosphere. Even in dissent, this view set the stage for subsequent legal battles, right up to the present effort to revoke EPA’s 2009 “endangerment finding” that is now the underpinning of federal greenhouse gas regulation.
Climate change likewise laid bare the long-standing divide between environmental law, which historically regulated the power sector in terms of its fuel inputs and combustion byproducts, and energy and utility law, which focused more on transmission and distribution of the resulting power. (Both fields are further divided among federal, state, and local authorities, as discussed below.) Vehicle emissions similarly are regulated via both EPA tailpipe standards and National Highway Transportation and Safety Administration mileage standards, with California authorized to propose more stringent ones. When coordinated, this multi-headed structure produces steady advances, but in deregulatory moments it has become fertile ground for opportunism, retrenchment, and delay.
At the federal level, these questions have been exacerbated by massive shifts in administrative law, long the building block of environmental law and climate action, and in federal court rulings on the separation of powers, implicating the authority of federal agencies to issue and enforce rules. Successive administrations have run afoul of the current Supreme Court majority, whose “major questions doctrine” casts a shadow both on attempts to fit new problems into once-expansive environmental statutes, and on “whole of government” approaches that attempt to address climate change’s sources and impacts across the entire economy.
Tentative attempts by presidents to leverage executive power and emergency authority have been curtailed when invoked for regulatory purposes, but are running strong in deregulatory efforts and executive actions in the service of “energy dominance.” Whether the Supreme Court will articulate some principled limits, and whether those will be even-handedly applied to future administrations, remains to be seen. Meanwhile, the past year has seen a large-scale push to reduce environmental regulation, in parallel with abrupt reorganizations and steep reductions in the federal workforce and agency budgets. These actions were joined by sharp declines in environmental enforcement and U.S. withdrawal from environmental and climate-related international instruments and bodies.
In this uncertain atmosphere, attention has turned to new technologies and building the necessary infrastructure to effect growth in low- and zero-carbon energy. As clean energy alternatives have matured and become economically competitive, the climate imperative is pushing against long-standing environmental review and permitting procedures. That may well include NEPA, which is now attracting attention from all three branches of government and a robust debate about whether, or how much, its procedures might be slowing energy deployment.
Environmental issues were federalized for a reason: to counter pollution that crosses state borders and to prevent a race to the bottom. But decades of implementation have seen the blunting of some tools, expansion of others, and identification of gaps. Moving forward requires reaffirming that the environment is inseparable from societal health and well-being, economic stability, and energy systems. Any serious response must orient governance toward decarbonization, while embedding accountability, equity, and justice from the outset rather than inconsistently and often inadequately after the fact. Doing all this without sacrificing hard-won environmental gains will not be easy.
To meet the challenge of the worldwide crises of biodiversity loss, pollution overload, and climate change, creation of any new structure must be rooted in understanding the existing baseline for environmental governance.
- Cross-Cutting Objectives: Effective governance paths must overcome the persistent false dichotomy between the environment and the economy, making clear that energy production, economic prosperity, ecosystem health, and societal well-being are inextricably linked. Improved trust and participation are essential to sustaining and accelerating progress across these interconnected goals.
- Democracy, Expertise, and Regulatory Certainty: Our legacy environmental laws have seen many successes, but their media- and site-specific tendencies are in tension with the scale of action needed to decarbonize our economy, conserve biodiversity, and control pollution. Eroded trust, accreted layers of process, and increasingly extreme political actions and reactions hamstring progress. At the same time, rapidly advancing scientific knowledge and technology have greatly expanded our ability to anticipate environmental challenges and understand and react to the impacts of our actions. Harnessing these tools effectively can help us improve and accelerate our decisionmaking processes.
- Building a Structure Fit for Purpose: Environmental law necessarily operates at multiple scales: global, national, tribal, regional, state, and local. Our system of cooperative federalism centers authority around the federal and state governments, backstopped by treaty obligations, interstate compacts, and traditional state and local authority over land use and public safety and welfare. A strong cooperative federalism framework can foster collaboration across subnational jurisdictions, including by leaning into data collection, analysis, and dissemination to support decisionmaking. In addition, understanding the effects and drivers of private sector environmental actions can help to identify ways to leverage those actions to augment and fill gaps in public governance.
Cross-Cutting Objectives
Inseparable: Environment, Energy, Economy, and Society
The past half-century has demonstrated the impossibility of severing the environment from the economy, energy production, and social well-being. We must ensure the false dichotomy between environmental protection and economic development, characterized by an oversimplified idea that the two are in a zero-sum competition, also fades. The decades-old concept of sustainability (or triple bottom line) has not yet made its way into many of our foundational laws and governance structures.
Ignoring the complex relationships among environment, energy, the economy, and society favors short-term decisions that externalize impacts. This underlies the longstanding debate over the accuracy and efficacy of cost-benefit analyses, throughout their 40-plus year federal history, including questions about scope and how they handle uncertainty. For any project or program, system designers that consider an integrated suite of factors that move beyond basic environmental parameters or economic indicators (from public health to workforce development, from the supply chain to community well-being) have a greater chance of cross-sector success.
These governance challenges are also inseparable from shifts in how finance flows. Public and private financial tools—from subsidies and tax credits to loans, grants, and community-based financing—are increasingly shaping market behavior and determining whether policy objectives translate into real-world outcomes. Who controls these tools, how they are deployed, and when capital is made available all play a central role in driving or constraining environmental progress.
Bridging these gaps is, of course, easier said than done. But widening the aperture of considerations can connect decisionmaking to holistic industrial policies that account for a wider range of economic, social, and environmental factors. Accounting for this wider range isn’t just a nice-to-have, but essential to shared prosperity.
Foundational: Trust and Participation
A process, project, or program will move at the speed of trust—no faster and no slower. This refers to trust in institutions, in science, and in process.
Trust is earned through consistent transparency, clear accountability, and demonstrated responsiveness. For governance systems to function at the scale and pace required today, these principles must be embedded in decisionmaking in ways that are coherent and durable, rather than fragmented across a series of disparate steps and entities. Our traditional frameworks contain mechanisms to solicit and incorporate public input. But those mechanisms have limitations for all involved, both those trying to make their voice heard and those proposing the action and receiving input. (These range from when and how often participation occurs in the decisionmaking process to how the input is incorporated and decisions communicated.) Participation is foundational to our regulatory democracy and must occur early enough and in meaningful ways to improve decisions.
Effective participation also depends on clarity. People must be able to understand how decisions are made, what tradeoffs are being weighed, and where and how engagement can influence outcomes. But our frameworks still reflect reliance on elite and professional representation rather than widespread engagement. Trust—and the durability of outcomes—will increase when our processes have clearly articulated principles, transparently and rapidly weigh tradeoffs, and come to decisions through open and informed consideration.
The Concurrent Risk and Promise of Technology
Mechanization and industrialization created both unprecedented wealth and the pollutants that were the target of the 1970s wave of environmental laws. Emerging technologies likewise offer great promise, but also place familiar stresses—greenhouse gas emissions, water consumption, land use, waste—on the ecosystem and on human health and well-being. Our existing laws will need to respond and adapt to these problems as data centers and other novel demands reach greater scale, even as we evolve new ways of balancing those technologies’ potential against their up-front impacts and opportunity costs.
Technology also offers a potential path through the climate crisis, as solar and wind energy have become scalable and cost-competitive with traditional fossil fuels. Other clean technologies on the horizon, such as geothermal or fusion energy, retain bipartisan support and will require legal and regulatory guardrails if they mature and are integrated into the system. Battery storage and energy efficiency advances will help manage and reduce energy demand, and carbon removal and sequestration technologies may also play a role in curbing emissions. And at the outer limits of our knowledge, various geoengineering concepts are raising difficult questions about feasibility, decisionmaking procedures, unintended consequences, and accountability.
New technologies are also helping shape the implementation of environmental law in important ways. Existing tools such as satellite imaging, GPS location and geographic information systems, remote monitoring and sensing, and drones have fundamentally altered the way we view and record data from the physical world, in close to real time. Computer modeling and simulations have been a mainstay of climate science and policy, and other software innovations may improve environmental governance, including addressing long-standing issues of government transparency and public participation.
Effective messaging is essential to enhancing public understanding of interconnected issues and support for responses. It should be tailored to specific jurisdictions and informed by advances in research (e.g., behavioral science), learn from those thriving in today’s information ecosystem, and embrace strategies for reducing polarization.
How can we identify and address barriers to the development and equitable deployment of technologies that advance environmental protection while limiting their negative impacts.
Democracy, Expertise, and Regulatory Certainty
In a healthy democracy, public policy is guided by evidence, and truth is the shared foundation for collective decisionmaking, whatever the chosen outcome. When facts and scientific expertise are dismissed or minimized in favor of ideology, however, it becomes harder for citizens to deliberate, solve problems, and hold leaders accountable. The diminution and marginalization of science contribute to the erosion of democracy itself.
In the United States, our ability to build necessary infrastructure and take action has been slowed by the long timelines and sometimes overlapping requirements of our regulatory processes. This is exacerbated by the increasingly extreme policy swings we have been experiencing between administrations. The result is the twin challenge of how to increase the pace of our processes without lessening their protections, while also making our decisions more stable and durable.
Aligning Regulatory Certainty and Timelines
Regulatory certainty is not the same thing as rigidity. When done correctly, it can be the backdrop against which communities are able to plan for the future and companies can make informed decisions about where and how to invest. Regulation that is sufficiently clear on stable objectives does not have as much space in which to swing.
Long horizons with clear milestones matter: think of a national clean electricity standard, or the emissions-based equivalent, set on a 15- to 20-year glidepath. Confidence in long-term decisions, however, stems from effective inclusion, holistic analysis, and transparent decisions. The perspectives of subject-matter experts (in-house and external), and of those who manage and care about the resources or land in question, should be considered essential and actively pursued by policymakers.
Program-level thinking can help inform decisions at the project level. The energy transition will be remembered for feats of engineering—the thousands of miles of transmission lines, the buildout of battery storage—but its success will be determined by whether our framework listens, incorporates needed expertise, and produces rules that last long enough for people to plan their lives.
Evidence-Based Decisionmaking
For decades, the principle that good decisions require a good evidence base has been axiomatic. Dating back to 1945, the federal government has invested in science as a discipline and an idea, with government supporting the research to be conducted by public institutions and delivered as socially useful goods by the private sector.
Incorporating meaningful, often complex, evidence—including scientific data, traditional knowledge, and the needs, concerns, and priorities of potentially affected individuals—into decisionmaking is increasingly fraught. Climate change illustrates these challenges: despite decades of understanding by government officials and private sector decisionmakers about its causes and the need to act, economic and social interests have prevented effective policy and legislative response. Decisions are as good as the information they are based on. Emissions reductions ultimately depend not just on technical knowledge, but on institutions and governments capable of acting on that knowledge independently, transparently, and free from corruption and clientelism.
In a study assessing the effectiveness of the federal government’s efforts to improve evidence-based decisionmaking, the U.S. Government Accountability Office found mixed progress in: (1) developing relevant and high-quality evidence; (2) employing it in decisionmaking; and (3) ensuring adequate capacity to undertake those activities. These are foundational problems.
Compounding our challenges in making legislative and policy decisions based on accurate and pertinent evidence is the siren song of AI. Artificial intelligence promises many tools, ranging in complexity and autonomy from providing clerical tasks to generating substantive recommendations. (AI Clerical Assistive Systems automate certain administrative and procedural tasks, such as document classification and automatic transcription, and AI Recommendation Systems can contribute to judicial decision-making, for example, by analyzing legal codes and case precedents. Paul Grimm et al.)
AI is already being used across jurisdictions and agencies for environmental regulation, including planning, reviewing proposals, drafting environmental reviews, public participation and engagement, monitoring compliance, and enforcement. Recent federal policy has fueled the AI flame, with a 2025 AI action plan and multiple Executive Orders that offer the power to expedite permitting processes.
Enormous governance questions around AI have yet to be resolved. Technologies built by people reflect the values and assumptions of those who built them, and their use shifts power in decisionmaking processes. If a judge were called upon to review a decision made by such a tool, how could she determine the finding was reasonable under existing standards of administrative law? Can machine-generated analysis satisfy NEPA’s “hard look” review? These types of governance concerns dog AI tools wherever they are deployed but become particularly critical when they have the potential to become the decisionmaker in our legal and regulatory system.
The importance of having rigorous systems for identifying and considering trusted information to ground collective and democratic decisionmaking cannot be overstated. Until recently, dozens of scientific advisory committees routinely advised federal agencies to help bridge information gaps. Staggering recent losses of federal research funding and government programs and scrubbing of essential data sets means any path forward will likely require significant investments of both financial and human capital. When we rebuild, priority should be placed on ensuring all participants in decisionmaking have access to the same evidence, supported by the same systems.
Frontloading Regulatory Decisionmaking
Even as we work to improve how evidence informs decisionmaking, we face growing risks, uncertainties, and tradeoffs. The challenge is not simply to generate more information, but to make better use of what we already know through regulatory systems that reflect the integrated nature of the problems we face—without mistaking uncertainty for an absence of evidence.
Many conflicts arise because decisions are fragmented across regulatory silos and institutions. Consider a proposed electrical transmission line crossing a wetland. Decisionmakers must balance the imperatives of the energy transition, the conservation of biodiversity, the protection of water resources, and local economic opportunities. Yet these factors may be evaluated at different times, at different scales, and by different agencies. As a result, environmental permitting decisions can be made in isolation, long after foundational choices about the project’s purpose and design have already been locked in.
By the time site-specific questions arise, such as whether a particular wetland falls within the narrowed jurisdiction of the Clean Water Act, many broader tradeoffs have already been foreclosed.
A holistic approach would entail identifying the priority of certain projects and a system for weighing their impacts. For example, infrastructure decisions could happen at a systemic scale such as nationwide grid needs, providing context for decisions about individual projects and resources. Our decisionmaking processes need systems for weighing tradeoffs, and making them transparent, to enable systems-level planning and prioritization and effective engagement.
Hard decisions will have to be made regarding prioritized (and thus deprioritized) objectives. But frontloading data gathering, assessment, and decisionmaking on a national scale—through meaningful scenario planning, for example—could reduce the number of decisions made much further down the line in a project lifecycle and temper the uncertainty that can stem from permitting officials’ discretion.
We will be facing these types of tradeoffs with increasing frequency as needs mount to build infrastructure and housing, retreat from our coasts, manage and conserve species and ecosystems, and respond to and prepare for increasingly frequent and severe emergencies. In addition to an integrated approach for assessing impacts and making tradeoffs transparent, the system will need certain decisions to be made earlier in the decisionmaking processes and with a broader scope.
Acting (and Adapting) Amidst Uncertainty
Core tenets of administrative law structure decisionmaking with up front analysis and assume that we have full—or at least sufficient—information about circumstances and potential impacts to support a decision. But this is not always the case. When there are substantial uncertainties about conditions or the possible impacts of an action or rulemaking, adaptive management can improve outcomes by taking an iterative, systematic approach.
The uncertainties brought on by changing conditions due to climate impacts and unknowns about the consequences of proposed actions may call for an adaptive approach. And there are other situations where establishing sufficient evidence before taking irreversible action is appropriate. For example, we currently have limited understanding of the potential local and global impacts of geoengineering proposals to release aerosols into the atmosphere to block the sun’s rays, nor are there governing mechanisms in place to address them.
There are also situations where it is important to ensure that we do not indefinitely postpone action due to a desire to have all the answers before acting, such as infrastructure for transitioning away from fossil fuel combustion. When appropriate, effective adaptive management plans include procedural and substantive safeguards such as clear goals to set an agenda and provide transparency, an accurate assessment of baseline conditions to compare future monitoring data against, an outline of the thresholds at which management actions should be taken to promote certainty and assist with judicial enforcement, and is linked to response action.
Learning as we go and making appropriate adjustments may be justified in some contexts, and even essential when we do not have the luxury of time and must move ahead without critical information. Adaptive management can increase an agency’s ability to make decisions and allow managers to experiment, learn, and adjust based on data. But adaptive management’s flexibility comes at the cost of more resources and less certainty, which may also invite controversy. The sweet spot for adaptive management may be when managing a dynamic system for which uncertainty and controllability are high and risk is low. While uncertainties are proliferating, situations that meet those conditions are not the norm.
It would be beneficial for our environmental governance systems to explicitly identify conditions under which adaptive management may and may not be used, and to provide clear accountability mechanisms. The approach must fit with the practical realities of the working environment. For example, even if uncertainty and controllability are high and risk is relatively low, tinkering with large-scale energy infrastructure is not practical. Adaptive management may not be suited to regulatory contexts (1) in which long-term stability of decisions is important; (2) where decisions simply can’t easily be adjusted once implemented; or (3) where it is essential that an agency retain firm authority to say “yes” or “no” and leave it at that. It is a valuable tool to be invoked when truly necessary.
The interconnectedness of today’s global environmental challenges is in tension with the accreted framework of media-specific, site-specific laws and siloed agencies. Adjustments that help to align objectives, processes, and structures could scale impact.
Our framework should reflect commitment to and investment in gathering and analyzing information, from intricate science to the concerns of impacted communities; and be designed to incorporate and respond to changing information, such as through judicial review or other checks.
In part because of impacts already set in motion, we must consider when we cannot wait for more information before taking action on environmental and climate challenges. By their nature, some of those actions can be adapted on an ongoing basis, while others cannot. Clear parameters for differentiating will help ensure clear timelines and appropriate, effective processes.
Building a Structure Fit for Purpose
The triple planetary crises, a term coined by the UN Environment Programme, refers to the challenges of biodiversity loss, pollution overload, and climate change. They require large-scale mobilization and societal level adjustments. This magnitude of action requires a multifaceted system that can support and move myriad levers in a coordinated and balanced manner. The year she received the Nobel Prize in Economics, Elinor Ostrom published a paper capturing the tension but also necessity of this layered system, calling for a “polycentric approach” to addressing climate change.
The following discussion focuses largely on federal and state government action. In addition, Tribal Nations are vital sovereign authorities, partners, and voices in governance, including natural resource management, and their needs and knowledge are critical to effective, sustainable, just results. And as Ostrom recognized, private entities will also be instrumental in addressing climate change and other complex challenges; this includes not only corporations, as discussed below, but philanthropic organizations and a variety of other nongovernmental actors.
The Scale Challenge
Environmental regulation occurs at multiple levels: local ordinances, state laws and policies, interstate agreements, tribal laws, federal regulations, and international laws and norms. It also works at different resource scales, from managing a subspecies to protecting regional drinking water to setting nationwide air standards.
Jurisdictional nesting can provide comparative benefits at various levels for specific resources or pollutants. For example, working at the local level may allow for tailoring to specific circumstances to maximize benefits and the building of trust, while working at the state level can allow for the cumulative benefits of collective local action while also allowing for the testing of different approaches to federal implementation. Meanwhile, working at the federal and larger scale allows, among other things, the balancing of voices, and the establishment of shared objectives, standards, or requirements.
However, tiered systems can also be subject to gaps in implementation, such as when there is no mechanism to trigger enforcement of an international mandate at a national level. This may inadvertently impede interoperability and shared learning, such as by using different data standards, tools, or systems, and slow action due to competing or otherwise unaligned priorities. In addition, rarely do jurisdictional boundaries align with resource definitions, whether it be a hydrogeographic basin, extent of an air pollutant, or natural hazard vulnerability zone. Further complexity is added by questions around preemption, with changes occurring in longstanding understandings of federal versus state authorities under key statutes and regulatory structures.
Federal, tribal, state, and local governments must navigate these challenging dynamics as they work to effectively implement existing environmental laws and creatively address new environmental problems.
Cooperative Federalism
Federalism—whereby the federal government and states share power and responsibilities—is a central tenet of the U.S. governance system. A particular form, cooperative federalism, is embodied in most of the major U.S. environmental laws, including the Clean Air Act and the Clean Water Act. These laws establish a legal framework in which minimum standards are established at the federal level and individual states implement the programs. Today, over 90 percent of the delegable federal environmental programs are run by states. As a general matter, states are responsible for ensuring that federal standards are met but have the flexibility to impose standards that are more stringent than the federal standards.
In practice, the Congressional Research Service observes that the “precise relationship and balance of power between federal and state authorities in cooperative federalism systems is the subject of debate.” This debate has manifested in a variety of ways over the decades, including differences over the appropriate scope of federal oversight and levels of federal funding for state-delegated programs.
Environmental protection has advanced in many respects over time with cooperative federalism as its foundation, but few would argue there is no room for improvement. For example, a 2018 memorandum by the Environmental Council of the States (ECOS) captured a consensus among states that the “current relationship between U.S. EPA and state environmental agencies doesn’t consistently and effectively engage nor fully leverage the capacity and expertise of the implementing state environmental agencies or the U.S. EPA.”
In addition to the leeway that cooperative federalism provides to the states in implementing federal environmental laws, states are free to regulate or otherwise address environmental problems that are not covered by federal laws. As a result, states are often referred to as (in Justice Brandeis’ phrase) “laboratories of democracy” for testing innovative policies. Historically, states have served as testing grounds for environmental policies later adopted by the federal government. Given the current federal governance landscape, discussed below, what happens in the states may stay in the states (at least for quite some time)—making state laboratories one of the few promising options for advancing environmental protection.
Barriers to Optimal Functioning of Cooperative Federalism
In addition to the inherent systemic challenges outlined above with respect to multi-tiered jurisdiction and resource scale, there are broad societal barriers to maximizing the efficacy of cooperative federalism. The numerous overarching problems contributing to democratic dysfunction (e.g., channelized communication, primaries that yield extreme candidates who foster dramatic pendulum swings, lack of public trust) will contribute to impeding the optimal functioning of cooperative federalism for the foreseeable future.
The multitude of environmental governance-specific challenges identified earlier also significantly affect the functioning of cooperative federalism. These include, for example, long-standing congressional gridlock; new and emerging environmental harms that cannot be easily addressed within the existing, siloed framework; a Supreme Court changing its review of regulation; and regulatory pendulum swings that make consistency and stability difficult and hinder continuous improvement.
In addition, several additional barriers arguably weaken the foundations of cooperative federalism. These include: ineffective federal oversight of state programs (possibly both too stringent and too lenient in some respects); insufficient collection and dissemination of data (e.g., on environmental conditions, performance, pollution impacts), as well as inconsistent tracking of key environmental indicators; lack of state-specific effective risk communication and messaging; limited state resources for filling federal regulatory gaps or experimenting with innovative ways of implementing federal and state regulations; and insufficient federal funding for state programs. Recent critiques also point to the need to build out state administrative law to improve the functioning of cooperative federalism.
Opportunities for Renewing Cooperative Federalism
Recent developments in federal programs are disrupting many aspects of the country’s environmental protection efforts. These developments include drastic regulatory rollbacks, multiplied industry influence, curtailed input from scientists and other experts, rollback of federal grant funds to states and local governments, and sweeping staffing cuts resulting in loss of critical expertise.
Cooperative federalism has been particularly undermined by federal funding cuts (e.g., withdrawal of federal grants, reductions in revolving loan funds) and cuts to the federal programs that collect and analyze environmental data. Moreover, federal interference with independent or “more stringent than” state initiatives is taking a toll (e.g., response to California’s electric vehicle requirements ).
Given the barriers outlined above that make major statutory change infeasible, building an entirely new structure to replace cooperative federalism will be a nonstarter for the foreseeable future. However, ample opportunities exist to strengthen the existing structure in a manner that yields more effective and innovative approaches to environmental protection.
Front and center is building state and local governmental capacity to fill the gaps created by federal inaction and rollbacks as well as to lead on regulatory innovation. In so doing, states and local governments can serve as more effective laboratories of democracy and foster innovative federal action. And because states and local governments are on the frontlines of managing environmental and climate impacts such as floods and wildfires, as well as aging water infrastructure and other environment-related challenges, they are motivated to address the cause and effects of these harms, despite the intensely politicized nature of environmental issues such as climate change.
To be sure, renewing the existing structure is complicated by an uneven political landscape. For example, the level of political and popular support for environmental protection measures in the 26 states led by Republican governors differs from the levels of support in the 24 states led by Democratic governors, and the relative dominance of a particular party (e.g., trifectas or triplexes) is also a factor. These dynamics likewise influence environmental action by local governments when, for example, the potential for state preemption of local authority is a factor.
Nevertheless, the practical reality of increased extreme weather events, aging water infrastructure, and other environment-related challenges provides a strong incentive for all states and local governments to act. State and local efforts, however, are hindered by limited capacity in the form of staffing, funding, expertise, data, and other factors. For example, virtually all states could benefit in their decisionmaking from more robust data on local environmental conditions, and many states lack adequate funding, staff, and other resources.
Private Sector Synergies and Opportunities
Private environmental governance (PEG)—which can take a range of forms including collective standard-setting, certification and labeling systems, corporate carbon commitments, investor and lender initiatives, and supply chain requirements—is already making its mark across industries as diverse as electronics, forestry, apparel, and AI. For example, roughly 20 percent of the fish caught for human consumption worldwide and 15 percent of all temperate forests are subject to private certification standards. In addition, 80 percent of the largest companies in key sectors impose environmental supply chain contract requirements on their suppliers. And investors are increasingly taking environmental, social, and governance (ESG) into account, including risks related to climate change. A 2022 study estimated, for example, that assets invested in U.S. ESG products could double from 2021 to 2026 and reach $10.5 trillion.
As professors Vandenbergh, Light, and Salzman explain in their book Private Environmental Governance: “If you want to understand the future of environmental policy in the 21st century, you need to understand the actors, strategies, and challenges central to private environmental governance.”
Given the scope of PEG activities, it is not surprising that a range of regulatory regimes are implicated, including corporate governance, contract, antitrust, and consumer protection laws. In some cases, these legal regimes place constraints on the forms and scope of PEG initiatives. Many contend, however, that these constraints are inadequate, as reflected in recent efforts to severely curtail ESG initiatives.
Further, some scholars and advocates have criticized PEG from an entirely different perspective, citing concerns that PEG measures constitute greenwashing—that is, that they do not actually change corporate behavior and environmental conditions. Among other concerns is that PEG may undermine support for public governance measures in certain contexts.
Yet federal legislative gridlock, a dramatically swinging environmental regulatory pendulum, unregulated new technologies, and other factors point to needing a better understanding of how PEG can be leveraged to advance environmental protection efforts—including the improved functioning of cooperative federalism.
How can we use innovative approaches for preserving existing data and collecting new data on environmental conditions, regulated entity performance, and pollution impacts to enhance interoperability of local, state, and federal systems, foster consistency among assessments of risk, and help align priorities and approaches?
Problems such as climate change require a whole of government approach to address and could benefit from leveraging adjacent state and local regulatory authorities in areas such as land use (e.g., zoning), infrastructure, and public health.
Bolstering state and local officials’ networks for sharing data, best practices, and regulatory innovations may help align priorities and produce further progress on cross-jurisdictional problems as well as new challenges such as permitting reforms.
For example, asking—what are the effects of PEG (e.g., emissions reductions); what are the drivers of PEG (e.g., brand reputation, shareholder actions, employees, and corporate customers); are there ways to reduce greenwashing and greenhushing; and how can we ensure that PEG complements public governance.
For example, AI and advanced monitoring technologies—if thoughtfully leveraged—could lessen the burden on state and local governments, particularly those that are under-resourced, in their efforts to assess climate risk, develop resilience plans, and monitor regulatory compliance.
Conclusion
The environmental gains of the last half-century demonstrate that governance choices matter. The United States built a system capable of addressing the urgent environmental crises of its time by combining scientific expertise, democratic accountability, and enforceable legal standards.
Today’s urgent challenges—climate change, biodiversity loss, and pervasive pollution—demand a similar alignment under far more complex conditions. The challenge is not merely to regulate more, faster, or differently, but to recommit to decisionmaking that is credible and durable: by restoring confidence that evidence matters, that participation is meaningful, that tradeoffs get confronted honestly, and that rules will persist long enough to justify investment and collective effort.
The path forward lies neither in abandoning the foundations of environmental law, nor in relying solely on technological or private solutions. It will be found by strengthening and adapting existing governance structures—integrating cross-cutting objectives across domains, clarifying roles across jurisdictions, and rebuilding the shared evidentiary base and institutional capacity needed to act amid uncertainty, rather than deferring action in pursuit of unattainable certainty. And it requires clear communication about today’s complex, dispersed challenges that enhances understanding and reduces polarization.
At its core, the triple planetary crisis is a democratic and governance challenge: how societies decide, together, to protect people and places while sharing costs and benefits fairly. Meeting that challenge will require systems capable of carrying both technical complexity and public trust, as well as a sustained commitment to invest in institutions that can decide, act, and endure.
Costs Come First in a Reset Climate Agenda
Key Takeaways
- The costs of climate policy influence whether reforms benefit society, as well as their likelihood of passage and durability. Four ways to categorize climate policy costs are: negative-cost policies (pro-growth policies with climate co-benefits); low-cost policies (costs below domestic climate benefits); medium-cost policies (costs below global climate benefits); and high-cost policies (costs above global climate benefits). Cross-partisan alignment is most evident among pro-abundance progressives and pro-market conservatives.
- Negative- and low-cost policies align with domestic self-interest and comprise a growing share of the abatement curve. For example, market liberalization in permitting, siting, electricity regulation, and certain transportation applications lower energy costs and have profound emissions benefits. A prominent low-cost policy is emissions transparency. Negative- and low-cost policies hold the most potential for durable reforms and are often technocratic in nature.
- Chronic underconsideration of costs has induced an overselection of high-cost policies and underpursuit of low- and negative-cost policies. Legislative policies, such as subsidies and fuel mandates or bans, often receive no ex ante cost-benefit analysis before adoption. Interventions receiving cost-benefit analysis, especially regulation, tend to underestimate costs.
- Innovation policy – namely public support for research, development, and early-stage deployment – can align with domestic self-interest and address legitimate market deficiencies. By contrast, industrial policy for mature technology carries high costs, often erodes social welfare, and is not politically durable. Notably, public support for mature technologies in the Inflation Reduction Act was not durable, but support remained for nascent industry.
- We recommend that a reset climate agenda focus on abatement results over symbolic outcomes, prioritize state capacity for technocratic institutions, and emphasize cost considerations in policy formulation and maintenance. Negative cost policies warrant prioritization, with an emphasis on mobilizing beneficiaries like consumer, non-incumbent supplier, and taxpayer groups to overcome the lobbying clout of entrenched interests. Robust benefit-cost analysis should precede any cost-additive policies and be periodically reconducted to guide adjustments.
Introduction
Public policy involves tradeoffs. The primary tradeoff for climate change mitigation is economic cost. Secondary tradeoffs include commercial freedom, consumer choice, and the quality or reliability of goods and services. Political movements seeking to address a collective action problem, such as climate change, are prone to overlook the consequences of tradeoffs on other parties, like consumers and taxpayers. This paper posits that the cost tradeoffs of climate change mitigation have been underappreciated in the formation of public policy. This has resulted in an overselection of high cost policies that are not politically durable and may erode social welfare. It also results in overlooking low or negative-cost policies that are durable and hold deep abatement potential. These policies can have broad political appeal because they align with the self-interest of the United States, however they typically require dispersed beneficiaries to overcome the concentrated lobby of entrenched interests.
A core, normative objective of public policy is to improve social welfare, which “encourages broadminded attentiveness to all positive and negative effects of policy choices”. Environmental economics determines the welfare effects of climate change mitigation policy by the net of its abatement benefits less the costs. The conventional technique to determine abatement benefits is the social cost of carbon (SCC). The barometer for whether climate policy benefits society is to determine whether abatement benefits exceed costs. Accounting for full social welfare effects requires consideration of co-benefits as well, granted these tend to be conventional air emissions with existing mitigation mechanisms covered under the Clean Air Act. Nevertheless, accounting for costs is essential to ensure climate policy benefits society.
Abatement costs also have a discernable bearing on the likelihood and durability of policy reforms. Climate policies exhibit patterns of passage, mid-course adjustments, and political resilience across election cycles based on the constituency support levels linked to benefit-allocation and cost imposition. This paper develops four policy classifications as a function of their abatement benefit-cost profile, and uses this framework to examine the political economy, abatement effectiveness, and economic performance of select past and potential policy instruments.
Political Economy and Policy Taxonomy
The translation of climate policy concepts into legitimate policy options in the eyes of policymakers can be viewed through the Overton Window. That is, politicians tend to support policies when they do not unduly risk their electoral support. The Overton Window for climate policy is constantly shifting within and across political movements with the foremost factor being cost.
In a 2024 survey of voters, the most valued characteristics of energy consumption were 37% for energy cost, 36% for power availability, 19% for climate effect, 6% for U.S. energy security effect, and 1% for something else. Democrats slightly valued energy cost and power availability more than climate effects. Independents and Republicans heavily valued energy cost and power availability more than climate effect.
Progressives have long exhibited greater prioritization of climate change policy, but cost concerns are driving an overhaul of the progressive Overton Window on climate change. In California, which contains perhaps the most climate-concerned electorate in the U.S., progressives have begun a “climate retreat” to recalibrate policy as “[e]lected officials are warning that ambitious laws and mandates are driving up the state’s onerous cost of living”. Nationally, a new progressive thought leadership think tank is encouraging Democrats to downplay climate change for electoral benefit. Importantly, they find that 61% of battleground voters acknowledge that “climate change is at least a very serious problem,” but that “it is far less important than issues like affordability.”
Similarly, veteran progressive thought leaders, such as the Progressive Policy Institute, now stress that “energy costs come first” in a new approach to environmental justice. While emphasising the continued importance of GHG emissions reductions, those policy leaders are making energy affordability the top priority, amid a broader Democratic messaging pivot from climate to the “cheap energy” agenda. The rise of cost-conscious progressives is particularly notable because the progressive electorate has expressed a higher willingness to pay to mitigate climate change than moderate and conservative electoral segments.
Economic tradeoffs, namely costs and more government control, has long been the central concern on climate policy for the conservative movement. The conventional climate movement messaged on fear and the need for economic sacrifice, which is the antithesis of the conservative electoral mantra: economic opportunity. Yet the conservative climate Overton Window emerged with a series of state and federal policy reforms when climate change mitigation aligned with expanded economic opportunity. However, pro-climate conservative thought leaders remain opposed to high cost policies, such as calling to phase out Inflation Reduction Act (IRA) subsidies for mature technologies.
Many leading conservative thought leaders continue to challenge the climate agenda writ large because of its association with high cost policies. For example, President Trump’s 2025 Climate Working Group report was expressly motivated by concerns over “access to reliable, affordable energy” while acknowledging that climate change is a real challenge. Similarly, a 2025 American Enterprise Institute report finds that the public is most interested in energy cost and reliability and unwilling to sacrifice much financially to address climate change. Meanwhile, climate-conscious conservative thought leaders like the Conservative Coalition for Climate Solutions and the R Street Institute continue to emphasize a market-driven, innovation-focused policy agenda that prioritizes American economic interests and drives a cleaner, more prosperous future. Altogether, it indicates a conservative Overton Window on negative and low-cost climate change mitigation.
While cost is driving the Overton Window within each political movement, it also buoys the potential for alignment across political movements. Political movements are not monoliths, but rather exhibit major subsets within each movement. The progressive movement has seen gains in popularity among its populist left flank, often identified as the “democratic socialist” wing, which contributes to ongoing debate about Democrats’ ideological direction. Climate policy initiated by this wing, however, is associated with high economic tradeoffs (e.g., degrowth) and has prompted a backlash within the progressive movement. By contrast, a subset of the progressive movement, sometimes labelled “abundance progressives,” has emerged to support a more pro-market, pro-development posture. This movement is especially responsive to energy cost concerns, and is an emerging substitute for the anti-development traditions of the progressive environmental movement. Overall, variances in the progressive movement are fairly straightforward to categorize linearly on the economic policy spectrum.
The Republican electorate views capitalism far more favorably than Democrats, but with modest decline in recent years. Republicans have trended away from consistently conservative positions associated with limited government, which historically emphasized the rule of law and a strict cost-benefit justification for government intervention in the market economy. They have migrated towards right-wing populism associated with the Make America Great Again (MAGA) movement. Right-wing populism is hard to operationalize for economic policy because it is not a standalone ideology, but a movement vaguely attached to conservative ideology. Generally, the “America First” orientation of MAGA implies positions based on the self-interest of the U.S., with the Trump administration prioritizing cost reductions in energy policy.
MAGA is further to the right of conventional conservatives on environmental regulation and general government reform. For example, conservatives have noted the contrast between conservative “limited, effective government” and the Department of Government Efficiency’s “gutted, ineffective government” reform approach. On the other hand, MAGA will occasionally back leftist policy instruments, such as coal subsidies, wind restrictions, executive orders to override state policies, and emergency authorities for fossil power plants. These are often justified to counteract the leftist policies passed by progressives (e.g., renewables subsidies, fossil restrictions, emergency authorities for renewables), resulting in dueling versions of industrial policy. In other words, ostensible overlap between MAGA and progressives on policy instrument choice actually reflects the use of similar tools used for conflicting purposes (e.g., restrictive permitting or subsidies for opposing resources; i.e. picking different “winners and losers”). Nevertheless, the disciplinary agent for right-wing energy populism has been cost concerns, which have influenced the Trump administration to pursue more traditionally conservative energy policies like permitting reform and lowering electric transmission costs.
This political economy identifies the broadest cross-movement Overton Window between moderate or “abundance progressives” and traditional conservatives. Regardless, both broad movements exhibit cost sensitivity and growing prioritization of U.S. self–interest. Distinguishing the domestic SCC from global SCC is essential to determine what policies are consistent with the self-interest of the U.S. versus the world as a whole. Traditionally, the U.S. government only considers domestic effects in cost-benefit analysis, yet the vast majority of domestic climate change abatement benefits accrue globally.
The first SCC, developed under the Obama administration, relied solely on a global SCC. Leading conservative scholars, including the former regulatory leads for President George W. Bush, criticized the use of the global SCC only to set federal regulations. They argued for a “domestic duty” to refocus regulatory analysis on domestic costs and benefits. Similarly, the first Trump administration used a domestic SCC. Although the second Trump administration moved to discard the SCC outright, this appears to be part of a regulatory containment strategy, not a reflection of the conservative movement’s dismissal of the negative effects of climate change. In other words, even if the SCC is not the explicit basis for policymaking, it is a useful heuristic for policymakers.
The proper value of the SCC is the subject of intense scholarly and political debate. It has fluctuated between $42/ton under President Obama, $1-$8/ton under President Trump, and $190/ton under the Biden administration (all values for 2020). The main methodological disagreement has been over whether to use a domestic or global SCC, with the Trump administration position guided by “domestic self-interest.” This suggests the original domestic and global SCC values may approximate the Overton Window parameters the best. This underscores the following policy taxonomy that characterizes climate abatement policies by cost relative to domestic and global SCC levels:
- Class I policy: negative abatement costs. Such policies are widely viewed as “no regrets” by scholars and political actors across the spectrum because they constitute sound economic policy that happens to carry climate co-benefits. The Overton Window is most robust for Class I policy. It typically takes the form of fixing government failure, such as permitting reform.
- Class II policy: positive abatement costs below the domestic SCC. These low-cost policies often fall within the Overton Window, because they advance U.S. self-interest (i.e., positive domestic net benefits). Class II policies have a small abatement cost range (e.g., up to $8/ton). One estimate puts them at 4-14 times smaller than the global SCC.
- Class III policy: abatement costs between the domestic SCC and global SCC. These medium-cost policies improve global social welfare, but are not in the self-interest of the U.S., excluding co-benefits. Most cost-additive policies that pass a global SCC test fall in this range, underscoring why climate change is an especially challenging strategic problem; those incurring abatement costs do not accrue most abatement benefits. Class III policies face inconsistent domestic support and often require international reciprocation to be in the self-interest of the U.S.
- Class IV policy: abatement costs exceeding the global SCC. These high-cost policies fail a climate-only cost-benefit test. In other words, Class IV policies erode social welfare, excluding co-benefits. Class IV policies may be effective at reducing emissions, but often leave society worse off. Class IV policies are challenging to pass and are hardest to sustain.
Policy Applications
There are myriad policies across the abatement cost spectrum. This analysis applies to particularly popular domestic policies already pursued or readily considered. This includes policies targeting the environmental market failure via direct abatement (GHG regulation) and indirect abatement (public spending, clean technology mandates, and fuel bans). It also includes policies targeting non-climate market failure, yet hold deep climate co-benefits (innovation policy). The analysis also examines policies that correct government failure and have major climate co-benefits (permitting, siting, and electric regulation reform).
Fuel Mandates and Bans
For the last two decades, the most prevalent climate policy type in the U.S. has been state level fuel mandates and bans. Last decade, the environmental movement came to prefer policies that explicitly promote or remove fuels or technologies, not emissions. This is despite ample evidence in the economics literature that market-based policies are more effective and carry far lower abatement costs. Nevertheless, the most common domestic climate policy instrument this century has been state renewable portfolio standards (RPS). The literature notes several key findings from RPS:
- RPS has substantial but diminishing abatement efficacy. RPS compliance drove the bulk of initial renewables deployment, but declined to 35% of U.S. renewables capacity additions in 2023. This reflects the improved economics of renewable energy, which went from an infant industry in the 2000s to a mature technology and the preferred choice of voluntary markets by the 2020s. Renewables also exhibit declining marginal abatement as penetration levels grow. This underscores the environmental underperformance of policies promoting fuel, not emissions reductions.
- Binding RPS increases costs, with large state variances based on target stringency and carveouts. RPS compliance costs average 4% of retail electricity bills in RPS states and reach 11-12% of retail bills in states with solar carve-outs. Stringency is a key factor, as some RPS are not binding due to strong market forces, whereas binding RPS increases costs. Abatement cost estimates of RPS vary widely, with one prominent study placing compliance with RPS from 1990-2015 at $60-$200/ton. Within the Mid-Atlantic region alone, implied states’ RPS compliance costs in 2025 ranged from $11/tonne to $66/tonne, with solar carveout compliance clocking in at $70/tonne to $831/tonne. The future abatement cost of renewables integration is highly sensitive to RPS stringency and technology cost assumptions, with one estimate of implied abatement costs ranging from zero (nonbinding) to $63/tonne at 90% requirement in 2050. This evidence qualifies RPS as a class II to class IV policy, depending on its design.
- States with stringent RPS face challenging compliance targets, prompting calls for reforms to mitigate cost. Compliance with interim targets has generally been strong but stringent RPS states are beginning to fall behind on their targets. For example, renewable energy credit (REC) costs are nearing alternative compliance payment levels. To reduce costs, popular reform ideas have included delaying compliance timelines, adopting a clean energy standard to capture broader resource eligibility, or making RECs emissions weighted.
- Modest RPS exists in some conservative states but aggressive RPS policy has, generally, only proven popular in progressive states. As of late 2024, 15 states plus the District of Columbia had RPS targets of at least 50% retail sales, and four have 100% RPS. Sixteen (16) states have adopted a broader 100% clean electricity standard, though the broad definition of clean energy dilutes expected abatement performance in some states. Overall, renewable or clean portfolio standards do not appear to hold broad Overton Window alignment potential beyond modest applications.
Micro-mandates have also sprung up, primarily in progressive states. These have often targeted the promotion of nascent or symbolic energy sources that the market would not otherwise provide, with the costs obscured from public view (e.g., rolled into non-bypassable electric customer charges). A good example is offshore wind requirements in the Northeast, which carries a high abatement cost (over $100/ton).
Fuel bans have become increasingly popular climate policy in progressive states and municipalities. Beginning in 2016, a handful of progressive states began banning coal. However, this does not appear to have created much cost or abatement benefit, as evidenced by a lack of commercial interest in coal expansion in areas without such restrictions. In fact, neither federal nor state regulation was responsible for steep emissions declines from coal retirements. Coal retirements were mostly driven by market forces, especially breakthroughs in low-cost natural gas production and high efficiency power plants. Policy factors, like the Mercury and Air Toxics Rule, were secondary drivers of coal plant retirement.
Around 2020, California, New York, and most New England states began adopting partial natural gas bans or de facto bans on new gas infrastructure through highly restrictive permitting and siting practices. Unlike coal restrictions, these laws have markedly decreased commercial activity, namely gas pipeline and power plant development, and in some cases caused economically premature retirements. This has caused “pronounced economic costs and reliability risk.” Resulting pipeline constraints drive steep gas price premiums in these states, which translate into a core driver of elevated electricity prices.
Insufficient pipeline service in the Northeast is especially problematic, as demonstrated by a December 2022 winter storm event that nearly led to an unprecedented loss of the Con Edison gas system in New York City that would have taken weeks or months to restore. Further, preventing gas infrastructure development does not provide a clear abatement benefit, because more infrastructure is needed to meet peak conditions even if gas burn declines. A prominent study found a 130 gigawatt increase in gas generation capacity by 2050 was compatible with a 95% decarbonization scenario.
Progressive states and municipalities have also pursued natural gas consumption bans. This policy may carry exceptional cost, especially for existing buildings, with potentially well over $1 trillion in investment cost to replace gas with electric infrastructure. One estimate put the cost of natural gas bans at over $25,600 per New York City household. A Stanford study projected a 56% electric residential rate increase in California from a natural gas appliance ban. Generally, conservative thought leaders and elected officials have opposed natural gas bans for cost as well as non-pecuniary reasons, including security concerns and the erosion of consumer choice. This applies even for prominent members of the Conservative Climate Caucus. Altogether, gas bans are considered class IV policy with virtually no Overton Window alignment.
GHG Transparency
GHG regulation takes various forms. The least stringent is GHG transparency, which addresses an information deficiency and lowers transaction costs in voluntary markets. This begins with reporting and accounting requirements on emitters (Scope 1 emissions). Public policy can help resolve measurement and verification problems that have eroded confidence in voluntary carbon markets. GHG transparency policy can also standardize terminology and provide indirect emissions platforms. For example, making locational marginal emissions rates on power systems publicly available lets market participants identify the indirect power emissions of power consumption (Scope 2 emissions). Progressives have consistently favored GHG transparency policy, while conservatives have typically supported light-touch versions of it like the Growing Climate Solutions Act.
The second Trump administration recently pursued removal of basic GHG reporting requirements on ideological grounds, specifically repeal of the GHG Reporting Program (GHGRP). This appears to reflect an optical deregulatory agenda over an effective one. Conservative groups have warned of the downsides of GHGRP repeal. Pressure to course correct may prove fruitful, given that the industry the Trump administration aims to assist – oil and natural gas – maintain that the U.S. Environmental Protection Agency (EPA) should retain the GHGRP. A recent analysis found that if states replace the GHGRP, new programs will be more expensive (Figure 2).
Many regulated industry and conservative groups instead support a low compliance cost GHG reporting regime with durability across future administrations. This not only applies to direct emissions reporting but indirect emissions reporting, as in the absence of federal policy industry faces a patchwork of compliance requirements across states and foreign governments. The same economic self-interest rationale justifies a role for limited government in emissions accounting, with an emphasis on the capital market appeal of showcasing the “carbon advantage” of the U.S. in emissions-intensive industries. An example is liquified natural gas, whose export market is enhanced by showcasing its lifecycle emissions advantage over foreign gas and coal.
The abatement effectiveness of GHG transparency has grown appreciably in the 2020s, as voluntary industry initiatives have sharply increased. This policy set enables an efficient “greening of the invisible hand” with staying power, as corporate environmental sustainability efforts appear resilient regardless of political sentiment, unlike corporate social endeavors. In fact, the aggregate willingness to pay for voluntary abatement from producers, consumers, and investors suggests that well-informed domestic markets go a long way towards self-correcting the externality of GHGs (e.g., convergence of the private and social cost curves). Certain voluntary corporate behaviors may even exceed the global SCC, especially commitments to nuclear, carbon capture, and other higher cost abatement generation financed by the largest sources of power demand growth. Well-functioning voluntary carbon markets could yield roughly one billion metric tons of domestic carbon dioxide abatement by 2030. Providing locational marginal emissions data can slash abatement costs from $19-$47/ton down to $8-$9/ton while doubling abatement levels from some power generation sources.
Overall, efficient GHG transparency policy described above is a low-cost mitigation strategy consistent with class II designation. Basic, federal GHG transparency policy may even constitute class I policy, because it avoids the higher compliance cost alternative of a patchwork of state and international standards that would manifest in the absence of federal policy. However, stringent GHG transparency policy may constitute class III or IV policy. Prominent examples include a recent California climate disclosure law and a former Securities and Exchange Commission proposed rule to require emissions disclosure related to assets a firm does not own or control (Scope 3). Such efforts may obfuscate material information on climate-related risk and worsen private-sector led emission mitigation efforts.
Direct GHG Regulation
Classic environmental regulation takes the form of a command-and-control approach. These instruments include applying emissions performance standards or technology-forcing mechanisms, typically for power plants or mobile sources. These policies vary widely in stringency and cost. Overall, command-and-control is widely considered in the economics literature to be an unnecessarily costly approach to reducing GHGs relative to market-based alternatives. It can also result in freezing innovation, by discouraging adoption of new technologies.
Federal command-and-control GHG programs have not been particularly environmentally effective, cost-effective, or demonstrated legal or political durability. The first power plant program was the Clean Power Plan, which was struck down in court, and yet its emissions target was achieved a decade early from favorable market forces and subnational climate policy. The most recent federal command-and-control approaches for GHG regulation were 2024 EPA rules for vehicles and power plants. A 2025 review of these and other federal climate regulations over the last two decades of federal climate regulations found:
- EPA’s cost estimates to be “extraordinarily conservative” with suspect methodology that was prone to error and inconsistent with economic theory;
- Assessed costs of $696 billion compared to regulators’ estimate of $171 billion, or an increase in abatement cost from $122/tonne to $487/tonne; and
- EPA is too optimistic in its assumptions of benefits.
The 2025 review study implies that past federal command-and-control had very high cost – well into class IV range. It has also been a top priority of conservatives to undercut. However, it is possible for modest command-and-control policy with class II or III costs.
Some conservatives, noting EPA’s legal obligation to regulate GHGs and the cost of regulatory uncertainty from decades of EPA policy oscillations between administrations, suggested modest requirements as a better option to replace high cost rules in order to mitigate legal risk and provide industry a predictable, low-cost compliance pathway. For example, conservatives argued that replacing high cost requirements for power plants to adopt carbon capture and storage (CCS) with low cost requirements for heat rate improvements may lower compliance costs more than attempting to repeal the Biden era rule for CCS outright. Similarly, the oil and gas industry opposed stringent GHG regulations on power plants and mobile sources, but often validated alternative low cost compliance requirements.
The first Trump administration pursued modest replace-and-repeal GHG regulation. The second Trump administration has opted for repeal policies and to eliminate the endangerment finding via executive rulemaking. However, regulated industry and many conservative thought leaders believe this is a strategic blunder, given the low odds of legal success, resulting in the perpetuation of “regulatory ping-pong that has plagued Washington, D.C., for decades.” If the courts uphold Massachusetts v. EPA and the associated endangerment finding, this implies that modest command-and-control policy may have durable political alignment potential. Yet this does not hold much abatement potential. In the absence of a legal requirement to regulate GHGs, there is unlikely to be broad political alignment for even modest command-and-control policy. Conservatives tend to view this as a gateway to more costly policies that will probably not meaningfully affect global GHG trajectories.
The 2025 review study understates the full cost of U.S. climate regulations because they exclude state and local levels. Although no comprehensive study of state climate regulation is known, command-and-control state regulations often raise major cost concerns as well. The cost and environmental performance of such state programs varies immensely, often owing to differences in the accuracy of abatement technology costs that regulatory decisions are based upon (e.g., the failure of California’s zero-emission vehicle program compared to success with its low-emission vehicle program). A recent example is California’s rail locomotive mandate, which projected to impose tens of billions of dollars in costs before being withdrawn. State command-and-control regulation is commonplace in progressive states, but not beyond, implying meager Overton Window alignment.
A more economical version of GHG regulation is a system of marketable allowances, or cap-and-trade (C&T). Over three decades of experience with C&T programs reveals two things. First, C&T is environmentally effective and economically cost effective relative to command-and-control policy. Second, C&T performance depends on its design quality and interaction with other policies. Abatement costs depend on stringency and other design features, but C&T in a backstop role is generally close to the domestic SCC, rendering it class II policy. Robust C&T generally falls in the class III policy range. C&T is an example of abatement policy that can be cost-effective on a per unit basis, but given the breadth of its coverage its total costs can be substantial. Recent developments in Pennsylvania indicate a possible preference for policies with higher per-unit abatement costs than C&T, which may reflect a political preference for policies with less cost transparency and lower aggregate costs.
Some environmental C&T complaints are valid, such as emissions leakage, but C&T effectiveness concerns are generally readily fixable design flaws. C&T effectiveness complaints are often the result of interference from other government interventions like fuel mandates, relegating C&T to a backstop role and suppressing allowance prices. Such state interventions triggered anti-competitive concerns in wholesale power markets overseen by the Federal Energy Regulatory Commission (FERC). This prompted conservative state electric regulators to call for a conference to validate mechanisms like C&T as a market-compatible alternative to high cost interventions. Conservative expert testimony at that conference, invited by conservative FERC leadership, explained that interventions layered on top of C&T merely reallocate emissions reduction under a binding cap, which raises costs, creates no additional abatement, and undermines innovation. This implies that such states might increase abatement and lower aggregate costs by upgrading the role of C&T and downgrading the role of costlier interventions.
In the 2000s, bipartisan interest in federal C&T policy arose, but it failed and has not resurfaced. In its absence, states have supplanted federal policy with subnational C&T programs. However, the durability of C&T beyond progressive states is unclear. Moderate states have sometimes joined a regional C&T program under Democratic leadership, but sometimes departed them under Republican leadership. Conservative state groups typically challenge C&T adoption and seek repeal of C&T programs like the Regional Greenhouse Gas Initiative. This suggests that C&T is at the fringe, but typically outside, an Overton Window across political movements.
Permitting and Siting
Permitting policy can base decisions explicitly on GHG criteria, or they can be based on non-GHG factors but hold indirect GHG consequences. Generally, only progressive states and presidents have pursued the former. Federally, these include the Obama administration’s “coal study” and Biden administration’s “pause” on liquified natural gas (LNG). The LNG pause did not provide any apparent emissions benefit, yet carried substantial foregone economic opportunity and strategic value to U.S. allies. Pragmatic progressive thought leaders expressed concern with the pause, noting the creation of economic and security risks, and suggested lifting the pause in exchange for companies to commit to strict, third-party verified methane emissions standards. Relatedly, some conservative thought leaders have supported policy that enables voluntary participation in certified programs that provide market clarity and confidence to harness private willingness to pay for lower GHG products. This has been buttressed by support from an industry-led effort to advance a market for environmentally differentiated natural gas based on a standard, secure certification process.
Permitting constraints on clean technology supply chains can have perverse economic and emissions effects. A prime example is critical minerals, which are essential components to clean energy technologies. A net-zero emission energy transition, relative to current consumption, would increase U.S. annual mineral demand by 121% for copper, 504% for nickel, 2,007% for cobalt, and 13,267% for lithium. Market forces, unsubsidized, are poised to produce a sufficient amount of domestic copper and lithium supply to satiate a large share of domestic demand, but face undue barriers to entry that restrict production far below its potential. To meet net-zero objectives, permitting reform allowing all currently proposed projects to enter the market would lower U.S. import reliance for copper from 74% to 41%, while dropping lithium import reliance from 100% to 51%.
Expanding domestic mining no doubt carries local environmental tradeoffs. However, the U.S. has some of the most stringent and comprehensive mining safeguards in the world. Thus, foregoing development domestically is likely to push mining toward foreign countries with inferior environmental, safety, and child labor protections. It is therefore critical that domestic permitting decisions account for the unintended effects of denying permits, not merely the direct consequences of approving a project.
Permitting and siting constraints on energy infrastructure also impose major costs and foregone abatement. These entry barriers largely exist as environmental safeguards, yet almost always inhibit projects with a superior emissions profile to the legacy resources they replace. In fact, 90% of planned and in progress energy projects on the federal dashboard were clean energy related as of July 2023. In 2023, the ratio of clean energy to fossil projects requiring an environmental impact statement to comply with the National Environmental Policy Act (NEPA) was 2:1 for the Department of Energy and nearly 4:1 for the Bureau of Land Management. A 2025 study estimated that bringing down permitting timelines from 60 months to 24 months would reduce 13% of U.S. electric power emissions.
Permitting has proven to be a litmus test for the progressive environmental movement, as the movement bifurcates between anti-development symbolists and pragmatic pro-abundance progressives. While a minority of mainstream environmental groups have become amenable to permitting reform, such as The Nature Conservancy and Audubon Society, the core of progressive environmental groups have not. Instead, new progressive groups like Clean Tomorrow and the Institute for Progress filled the pro-abundance void alongside traditional market-friendly progressive groups like the Progressive Policy Institute. This progressive subset has helped influence moderate Democrats to support permitting reform in a collaborative way with conservatives.
Permitting reform has long been championed by conservatives for its economic benefits, with climate considerations typically a secondary-at-best rationale. Yet permitting reform has become a priority for the newer climate-minded conservative movement. However, permitting has also proven to be a differentiator between conservatives and right-wing populists. The latter engages in forms of government intervention that sometimes contradict conservative principles. For example, the Trump administration enacted an offshore wind energy pause that followed the same problematic blueprint as the Biden administration’s LNG pause. This elevates the importance of technology-neutral permitting reforms with an emphasis on permitting permanence safeguards.
In recent years, a coalition of Republicans, centrist Democrats, and clean energy and abundance advocates have pressed for reform to NEPA. A broad suite of federal permitting reforms with bipartisan appeal was identified in a 2024 report by the Bipartisan Policy Center. Bipartisan alignment led to the passage of the Fiscal Responsibility Act of 2023 into law and the Senate passage of the Energy Permitting Reform Act of 2024 (EPRA). Although a 2025 Supreme Court decision suggests executive actions alone may substantially reduce NEPA obstacles, plenty of NEPA and other federal statutory reforms remain of high value and hold considerable bipartisan potential.
The positions of leading progressive, conservative, and centrist thought leadership organizations highlight alignment on various federal permitting and siting reforms. These include statutory changes to NEPA, the Endangered Species Act, the Clean Water Act, the Clean Air Act and the National Historic Preservation Act. Substantive alignment includes reforms that reduce litigation risk (e.g., judicial review reform), limit executive power to stop project approvals and undermine permitting permanence, maintain technology neutrality, strengthen federal backstop siting authority for interstate infrastructure, codify the Seven County decision, and streamline agency practices while ensuring sufficient state capacity.
Despite considerable positive momentum at the federal level, the greatest permitting and siting barriers generally reside at the state and local levels and trending sharply in a more restrictive direction. Wind and solar ordinances have grown by over 1,500% since the late 2000s. Oil and gas pipelines and power plants face mounting permitting and siting restrictions in progressive states, which not only raise costs but do not necessarily reduce emissions. In fact, the New England Independent System Operator said that a lack of natural gas infrastructure in the region has raised prices and pollution by forcing reliance on higher-cost resources like oil-fired power plants. The only major power generation resource with a less restrictive trend is nuclear, as six states recently modified or repealed nuclear moratoria to ease siting.
Motivation for opposing energy infrastructure permitting has included the well-known “not in my backyard” concerns, such as noise, construction disruptions, or land use conflicts. Interestingly, much opposition appears to come from perception, as much as substantiated negative effects. Relatedly, permitting resistance rationales increasingly appear to result from ideological opposition to particular energy sources. Finally, much opposition and most litigation of energy projects comes from non-governmental organizations, not the land owners directly affected. Altogether, this underscores the importance of permitting and siting reform that improves the quality of information to agencies and parties, ties decisionmaking to specific harms not speculative claims, limits standing to affected parties, and creates appeals processes for landowners to challenge obstructive local government laws and decisions. A key tension to overcome is that technology-agnostic legislation has been more likely to advance in states with one or more Republican chamber, yet environmental advocates resist “all-of-the-above” reforms.
Policies that reduce permitting and siting burdens are class I: they boost economic output and are increasingly key to emissions reductions. Permitting and siting policies that are restrictive on fossil development are not particularly effective at reducing emissions and often add considerable cost, granted costs vary widely depending on the nature of the policies and implementation. Effective fossil restrictions can range from class II to class IV policy, while ineffective ones actually increase emissions. The political economy of permitting and siting must overcome the lobby of entrenched suppliers, who seek to maintain competitive moats. An ironic example was incumbent asset owners funding environmental groups to oppose transmission infrastructure in the Northeast that would import emissions-free hydropower.
Electric Regulation
The power industry is at the forefront of energy cost concerns and decarbonization objectives. In the early 2020s, electric rates have risen most in Democratic states. These concerns reoriented progressives towards cost containment, even at the expense of climate objectives. In the 2024 election, cost of living concerns propelled Republicans to widespread victories as President Trump vowed to halve electricity prices. A year later, voter concerns over rising electricity rates in Georgia, New Jersey, and Virginia boosted Democrats in gubernatorial and public service commission (PSC) elections.
At the same time, electricity is arguably the most important sector for climate abatement given its emissions share and the indirect effects of electrifying other sectors, namely transportation and manufacturing. Ample pathways exist to reduce electric costs and emissions simultaneously, primarily by fixing profound government failure embedded in legacy regulation. Electric industrial organization shapes economic and climate outcomes, with market liberalization an advantage for both.
Electric regulation falls into two basic formats. The first is cost-of-service (CoS) regulation, where the role of government is to substitute for the role of competition in overseeing a monopoly utility. The alternative is for regulation to facilitate competition by using the “visible hand” of market rules to enable the “invisible hand” to go to work.
CoS regulation historically applied to power generation, though about a third of states enacted restructuring to introduce competition into power generation and retail services, in response to rising rates and the recognition that these are not natural monopoly services. Nearly all transmission and distribution (T&D) historically and today remains under CoS regulation. Importantly, CoS regulation motivates a utility to expand the regulated rate base upon which it earns a state-approved return. Generally, the main sources of cost discipline problems in the power industry stem from its CoS regulation segments: transmission, distribution, and the portion of generation that remains on CoS rates.
Generally, restructured jurisdictions see greater innovation and downward pressure on the supply portion of customer bills. The economic performance of restructuring is highly sensitive to the quality of implementation. This includes the quality of wholesale energy price formation and capacity market design. It also includes various elements of retail choice implementation. They have also seen improved governance, whereas CoS utilities are prone to cronyism and corruption given the inherent incentives of their business model. Competitive wholesale and retail power markets hold cost and emissions advantages through several mechanisms:
- Markets accelerate capital stock turnover when it is economic. With the brief exception of nuclear retirements, new entry is dominated by zero emission resources or high efficiency gas plants that displace legacy plants with higher emissions rates. Markets usher in new entry and induce retirements in response to economic conditions. Last decade saw markets outperform in the coal-to-gas transition, and this decade with advances in wind, solar, and storage economics. Texas, the most thoroughly restructured state, leads the country in solar, wind, and energy storage additions while placing second in gas additions. A review of restructuring found that competition worked as intended, facilitating new, low-cost entry while “driving inefficient, high-cost generation out of the market.” A new paper evaluating generator-level data found that from 2010–2023, regulated units were 45% less likely to retire than unregulated units.
- Markets encourage power plant operating efficiencies. Competitive generators adopt technologies and practices that use fuel more efficiently and improve environmental performance. The introduction of competition caused nuclear generators to adopt innovative practices to reduce refueling outage times, boosting operating efficiency by 10%. One study found 9% higher operating efficiencies in the thermal power fleet in restructured states. By contrast, CoS utilities sometimes engage in uneconomic operations because they are financially indifferent to market signals, resulting in overoperation of the fossil fleet.
- Markets reflect customer preferences, including clean power. Footprints with retail choice have seen much higher popularity of voluntary clean power programs. Competition lowers the “green premium” and customer choice allocates it equitably. This is critical as the willingness to pay for clean power varies enormously across customers. Notably, most growing power customers are large companies with ambitious corporate emissions reductions targets, which explains their commercial interest in advancing consumer choice.
- Markets better integrate unconventional resources, namely storage, wind, solar, and demand flexibility. The central planning of monopoly utilities struggles to account for the profile of variable (e.g., wind and solar) and use-limited (e.g., storage) resources. Demand flexibility is valuable to integrate more variable supply sources. Wholesale and retail competition are the only structural pairings that have elicited substantial shifts in demand in response to price signals, because they align the incentives of retailers and end-users to reduce consumption during high price periods.
- Markets induce lower-cost environmental compliance and better environmental lobbying behavior. Restructuring reoriented the incentives to influence and comply with public policy. Notably, competitive enterprises pursue more innovative, lower-cost compliance pathways that tend to deepen abatement. Monopoly utilities have a track record of lobbying for higher cost environmental laws. For example, monopolies have a preference for command-and-control regulation that pads their rate base, and have opposed market-based policies like the 1990 Clean Air Act amendments.
Electric cost increases are multifaceted, prompting many misdiagnoses that blame markets for non-market problems. Utilities have begun pushing campaigns in restructured states to revert back to CoS regulation, whereas the growing consumer segment – namely data centers and industrials – are organizing campaigns to expand consumer choice. Independent economic assessments warn against a return to CoS regulation, and instead encourage state regulators to implement restructuring better. This includes better market design, consumer exposure to wholesale prices, and effective coordination with transmission investment.
T&D costs, generally, are the core driver of electricity cost pressures nationwide. Over the last two decades, utility capital spending on distribution has increased 2.5 times while nearly tripling for transmission. This reflects profound flaws in CoS regulation of T&D, resulting in overinvestment in inefficient infrastructure and underinvestment in cost-effective infrastructure. This projects to worsen, given T&D expansion needed to meet grid reliability criteria as a result of aging infrastructure, turnover in the generation fleet, and load growth.
T&D expansion is also central to abatement. Even partial transmission reforms can reduce carbon dioxide emissions by hundreds of million of tons per year. This explains why progressives have made reforms that expand transmission a top priority. This needs to be reconciled with the cost concerns of consumers and conservatives to result in durable policy. Consumers and conservatives have a budding transmission agenda rooted in upgrading the existing system, removing barriers to voluntary transmission development, using sound economic practices for mandatorily planned transmission, streamlined permitting and siting, and improved governance. A particularly promising frontier is reforms to enhance the existing system, given the expedience of their cost relief and consistency with a Trump administration directive.
Recent federal regulatory actions have demonstrated bipartisan willingness to improve transmission policy and the related issue of interconnection, which has emerged as a major cost and emissions issue. In 2023, FERC passed Order 2023 on a bipartisan basis to reduce barriers to new power plants trying to interconnect to regional transmission systems. Subsequent reforms were motivated by a coalition of consumer groups and the center-right R Street Institute. In 2024, FERC passed Order 1920-A on a bipartisan basis to improve economic practices in regional transmission development. EPRA, a gamechanger for interregional transmission development, passed the Senate with bipartisan support in 2024.
Demand growth has sparked reliability concerns over tight supply margins and recently put upward pressure on wholesale market prices. However, states with the greatest price decreases typically had increasing demand from 2019 to 2024 (Figure 3). This shows the importance of infrastructure utilization on electric rate pressures, as many areas had supply slack previously. The past may not be prologue. Emerging conditions show supply-constrained scenarios where marginal generation and T&D costs increase steeply to meet new load increase. The Energy Information Administration observes steady retail price increases and projects further rises to exceed inflation.
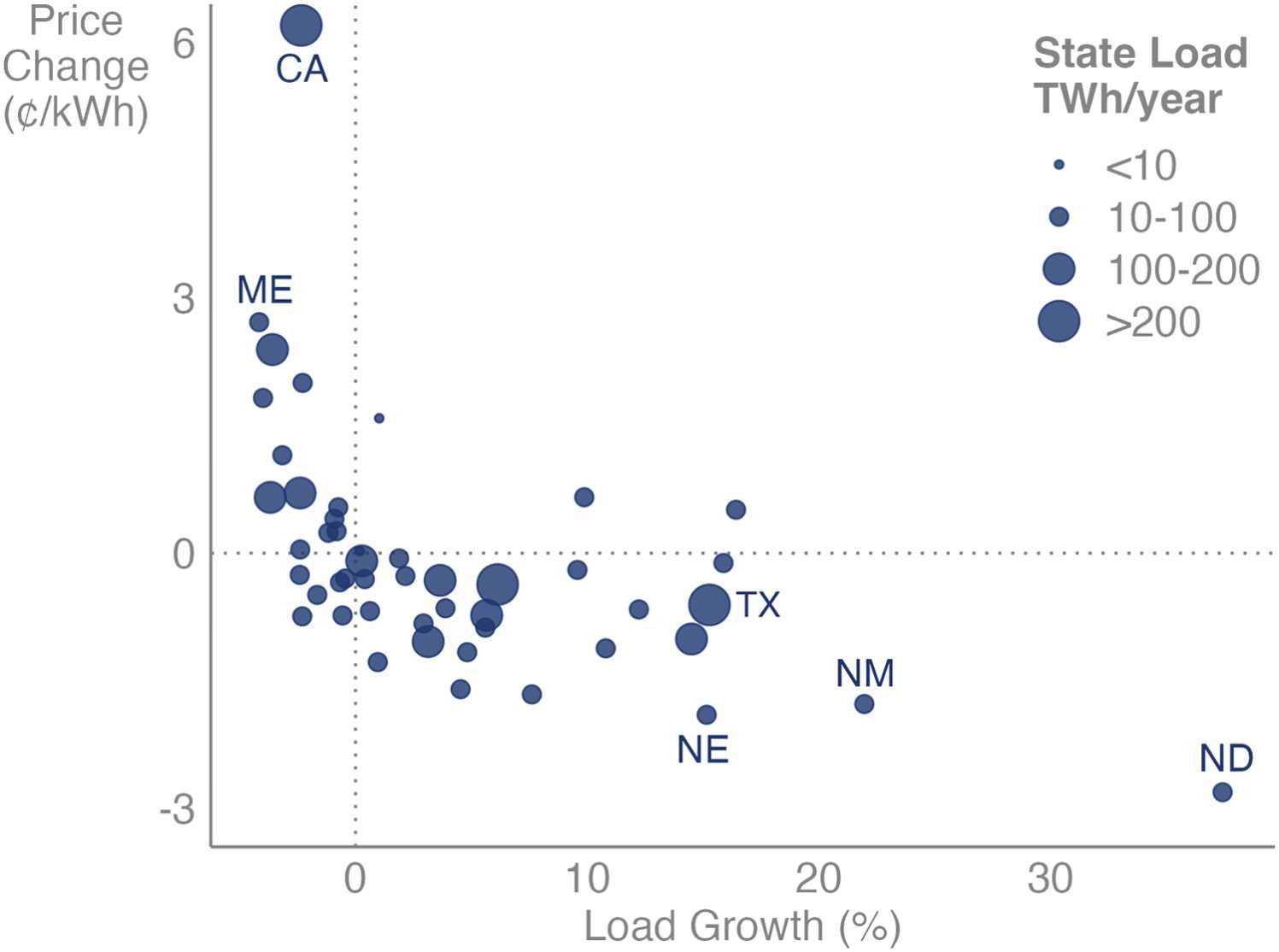
Source: Wiser et al., 2025.
In an era of resurgent power demand growth, the states poised to keep rates and emissions down have wholesale competition, retail competition, efficient generator interconnection processes, economical T&D practices, and low permitting and siting barriers. The only state that reasonably accomplishes all of these is Texas, which is experiencing the most commercial interest among competitive suppliers and growing power consumers. Texas has experienced industry-leading clean energy investment and earned the distinction of Newsweek’s “greenest state” in 2024.
All aforementioned electric reforms are considered class I policy. Despite cost-reduction appeal, power industry reforms have proven challenging for two reasons. First, reforms are highly technical in nature and face limited state capacity among legislative advisors and technocratic agencies, namely PSCs and FERC. For example, recent FERC and PSC activities reveal that these entities do not have the bandwidth or expertise to properly implement existing transmission policy, much less reform it. Secondly, reforms face strong resistance from incumbent utilities who hold concentrated interests in the status quo, creating a strong lobbying incentive. By contrast, the beneficiaries of reform, especially consumers, are dispersed interests that do not organize as effectively as a lobbying force.
Although the Texas electricity experiment and associated federal power market reforms under President George W. Bush is a conservative legacy, most restructured states are progressive. This reflects significant bipartisan historic appeal. However, traditional conservatives have sometimes conflated pro-utility positions as the “pro-business” position, while it is unclear whether right-wing populist influences will catalyze pro-market reforms by challenging the status quo or retrench monopoly utility interests based on technocratic market skepticism (e.g., Project 2025). CoS utilities also commonly oppose cost-effective T&D reform, especially vertically-integrated utilities, which is consistent with their financial incentives to expand rate base and deter lower-cost imports from third parties. Nonetheless, the political economy of bipartisan electric regulatory reform remains promising, given voters’ prioritization of reducing electricity costs.
Public Spending
Government spending occurs through direct spending outlays or indirect spending through tax expenditures. Spending takes the form of industrial policy or innovation policy. The economics literature is historically critical of industrial policy, while positive literature on industrial policy usually conflates it with innovation policy. A distinguishing element is that innovation policy selects policy instruments suited to specific market failures, namely the positive externalities of knowledge spillovers and learning-by-doing. These generally apply to research and development (R&D) and early stage technologies, including those in demonstration stage and infant industries that have not achieved economies of scale.
Predictably, progressives have been consistent backers of robust innovation policy, while conservatives typically scrutinize such expenses closely. Although differences of opinion exist on optimal funding levels, historically conservatives and progressives have agreed on a role for the government in supporting R&D. There is also a history of good governance agreement, such as a joint project between the Center for American Progress and the Heritage Foundation in 2013 on improving the performance of the national lab system. Improving outcomes-based Department of Energy program performance may have broad appeal, including better performance metrics, stronger linkages to private sector needs, and program reevaluation to determine government investment phase-out. Improvements to state capacity are paramount in this regard.
Conservatives are often critical of public spending on infant industry, where government failure can outweigh market failure. For example, policymakers often struggle to identify when to end industry support, while industry engages in rent-maintenance behavior even after it has achieved maturity. Historic evidence indicates that direct subsidies and tax exemptions for infant energy industry continue well after the targeted technologies mature. Conservative and progressive scholars have historically framed the merits over subsidies for infant industry as a debate over government versus market failure.
Since innovation policy targets non-climate market failures (e.g., knowledge spillovers) it may have a high static abatement cost. However, it is an inexpensive abatement policy when accounting for dynamic effects, because of induced innovation and learning-by-doing. Importantly, innovation policy holds massive climate benefits, because achieving abatement cost parity between clean and emitting resources is central to clean technology market adoption. Efficient R&D policy can be classified as class I policy, because the upfront cost of the policy is outweighed by long-term cost savings. Demonstration and infant industry support falls into class II-III range, depending on its implementation, and often exhibits substantial durability.
In recent years, climate-minded conservatives have shown stronger inclinations of public spending for innovation policy. However, there is a stark difference between conservatives and right-wing populism on innovation policy. Conservatives note that the adverse consequences of Department of Government Efficiency’s “gutted, ineffective government” approach to the Department of Energy is inconsistent with limited, effective government practice. The economic self-interest benefits of innovation policy may induce a course-correction with MAGA, which has not deliberately targeted innovation policy insomuch as sacrificing it amid a rash government downsizing exercise.
In contrast to innovation policy, industrial policy aims to directly promote a given industry, typically using mature technology, with interventions untethered to any underlying market failure (e.g., negative emissions externality). This generally takes the form of public spending on mature industries. For decades, traditional conservatives and climate-minded conservative scholars have been critical of green industrial policy for carrying high costs with modest emissions reductions.
The most relevant case study in climate industrial policy versus innovation policy is the Inflation Reduction Act (IRA) of 2022. IRA represented the “largest federal response to climate change to date.” It consisted mostly of subsidies for mature technologies, especially wind, solar, and electric vehicles (EVs). It also contained subsidies for infant industry. IRA was passed exclusively by Democrats, with Republicans voicing concerns over its cost. Republicans then passed the One Big Beautiful Big Act (OBBBA) in 2025, which phased-out subsidies for mature technologies, but generally retained those for infant industry. This underscores the political durability of innovation policy and the fragility of industrial policy.
A broader debrief on IRA and OBBBA reveals:
- Disregard for cost considerations preceded passage of the IRA. All known ex ante modeling of IRA’s abatement benefits before it passed ignored costs. This left Congress unequipped to weigh the merits and tradeoffs of the policy. A simplistic abatement cost technique in 2022 yielded a cost of $72/tonne for the renewable energy subsidies. A more sophisticated modeling exercise in 2023 projected an average abatement cost of $83/tonne. IRA could have been identified as a high abatement cost policy (class IV) before it passed. Before passage, R Street Institute analysis suggested meager additionality from subsidies and identified permitting and electric regulation flaws as the determining factors of energy emissions trajectories, yet Congress neglected those reforms.
- IRA abatement cost estimates escalated sharply after passage. The total abatement cost of IRA subsidies to taxpayers rose from $336/tonne in 2024 to $600/tonne in 2025. The initial 2022 IRA renewables subsidy cost estimate of $72/tonne rose to $142/tonne in 2024 and $208/tonne in 2025. The EV subsidy came in at $1,626/tonne. It is possible that this is understated, since the direction of the emissions effect of EV subsidies may depend on recipient qualifications, especially when accounting for the behavioral tendencies of EV adopters. The subsidies also undermined developer cost reduction in two ways: 1) motivated development in the least efficient areas and 2) weakened incentives for innovation that lowers costs, which translates into long-term cost increases relative to an unsubsidized baseline.
- Government failure precluded most of the anticipated climate benefits of the IRA. IRA abatement was overstated in 2022, because models understated artificial constraints on the core abatement driver: wind and solar deployment. The Energy Information Administration’s renewables projections in 2025, which reflected IRA subsidies, were close to their no-IRA estimates from 2022. Risk, not cost, has consistently been the barrier to wind and solar. A Brookings Institution analysis found that artificial barriers to entry were the leading causes of wind and solar project cancellations from 2016-2023, whereas the lowest cause was “lack of funding.” Renewables subsidies primarily constituted a wealth transfer from taxpayers to suppliers. One analysis suggested 80-90 percent of clean energy backed by the IRA would have occurred anyways. An S&P Global forecast projected OBBBA to cause a 15 percent decline in wind, solar, and battery storage capacity by 2035.
- Wind, solar, and EV tax credit phaseouts should lower costs and increase economic productivity, despite increasing electricity prices. Price and cost are related, but not the same thing. The phase-out of subsidies under OBBBA will put upward pressure on electricity prices. However, it will likely lower costs by restoring dynamic cost management incentives and removing distortions so investment reflects economic fundamentals. Electricity subsidies shift cost burdens from power generators and ratepayers to taxpayers. Because taxpayer funding is expensive – tax collection imposes considerable deadweight loss on the economy – the net effect of taxpayer subsidies tends to shrink economic output. The Tax Foundation projected that IRA would reduce U.S. gross domestic product by 0.2 percent, while OBBBA would increase long-run GDP by 1.2 percent, granted energy tax credits were only one factor in these analyses.
The takeaway from IRA and OBBBA is that subsidies for mature technologies are high cost, likely to erode social welfare, and not politically durable. Efficient public spending for RD&D, however, enhances social welfare and falls in the Overton Window due to its value for economic self-interest. Late-stage infant industry is at the fringe of the Overton Window. It is the area where conservative and progressive scholars have historically had contrasting views on whether market failure outweighs government failure, yet political outcomes have largely supported infant industry.
Generally, the literature finds strong evidence of opportunity cost neglect in public policy, which “creates artificially high demand for public spending.” The IRA was a case-in-point. Meanwhile, the opportunity cost of public spending is rapidly rising given the dire fiscal trajectory of the United States. In 2025, moderate experts emphasized a pivot away from unsustainable and ineffective “Green New Deal thinking” for clean technology subsidies in favor of an innovation-driven strategy.
Takeaways
This analysis finds chronic flaws of cost considerations in ex ante policy analysis. Many medium and high-cost policies have passed without any robust accounting of costs at all (e.g., IRA, fuel bans). Interventions with cost-benefit analysis have had a tendency to underestimate costs (e.g., regulation). These flaws contribute to public misconception and play into political economy dynamics that tend to incent policies with hidden costs over those with transparent ones.
High-cost policies have typically only been enacted by progressive governments and have come under greater scrutiny as energy costs escalate. This calls their social welfare effects and durability into question. It has cast climate action in the public eye as requiring deep economic sacrifice.
Conservatives have been hesitant to engage on climate policy outright, largely over dire economic tradeoff perceptions. Such concerns have instigated a conservative backlash to climate policy, including to policies that are compatible with U.S. economic interests. This has been exacerbated by right-wing populism, which often strays from limited government conservatism in pursuit of cultural identity objectives. For example, in a 2024 piece promoting energy affordability, the Heritage Foundation correctly attributed cost increases to renewable energy mandates, but incorrectly presumed that a broad shift towards renewable energy and away from fossil fuels would always increase costs.
High abatement cost policies not only risk reducing aggregate social welfare, but they create distributional concerns. Policies that raise energy costs tend to be regressive. This has challenged the social justice narrative of progressives, prompting a rethink by progressive leaders to take a “cost-first approach to [the] clean energy transition.” Although subsidies are a common response to lower burdens on low-income households, the most popular green subsidies pursued have exacerbated distributional concerns. Specifically, renewables subsidies favored by progressives have been challenged by conservatives as “green corporate welfare.” Progressives have also faced criticism for EV tax credits for disproportionately benefiting wealthy households.
Encouragingly, negative- and low-cost policies comprise a rising share of the abatement curve. The Overton Window for pursuing such policies has grown remarkably for “abundance progressives” and conventional conservatives. However, populist subsets within both movements challenge the potential for political alignment. Enacting negative-cost policies also faces the collection active problem of dispersed beneficiaries versus a concentrated incumbent supplier lobby favoring the status quo. Mobilizing consumer and taxpayer groups is an underappreciated strategy to enact these policies.
This analysis is far from comprehensive. A notable omission from this paper is transportation policy, the largest GHG sector in the U.S. A scan of the transportation literature underscores major abatement potential for negative and low-cost policies, including reducing government barriers to efficient heavy-duty transportation like railways, shipping, and heavier trucking. Further, the electrification of transportation requires extensive fixes to government failure, such as liberalizing markets to enable competitive charging infrastructure, which lowers costs. The merits of innovation and GHG transparency policy, previously discussed, also appear to hold promise for transportation applications such as aviation fuel. The transportation sector has also been the target of GHG regulation, mostly in progressive states, which warrants close assessment of costs. For example, one study identified a vast abatement cost range for fuel standards ($60-$2,272/tonne).
A shortcoming of this analysis is that it only characterizes costs by their efficiency (i.e., $/ton). Political decisions are highly sensitive to aggregate cost and its visibility to the public, which our taxonomy does not characterize. It is possible that efficient, transparent, and higher aggregate cost policies (e.g., C&T) fare less favorably in some political settings than inefficient, opaque, and sometimes lower aggregate cost policies (e.g., RPS solar carveouts).
Despite the limitations of this analysis, the sample of policies evaluated is sufficient to support the thesis. That is, a retooled climate policy agenda that prioritizes cost considerations should elevate social welfare and achieve greater abatement by selecting more durable policies.
Conclusion
Abatement costs have huge bearing on whether climate policies benefit society, their likelihood of passage, and whether they prove politically durable. Most abatement need not come from dedicated climate policy, per se, but rather sound economic policy that carries deep climate co-benefits. Chronic disregard for cost considerations has led to an overselection of high-cost policies and underpursuit of low- and negative-cost policies. This has undermined policy durability and exacerbated political polarization over climate change abatement.
This paper finds extensive abatement opportunities within negative-cost policies. These largely constitute fixes to government failure and include permitting, siting, and power regulation reforms. This analysis also finds considerable low-cost policies that are compatible with U.S. economic self-interests. These policies primarily spur voluntary private sector abatement through efficient innovation policy and GHG transparency.
We offer three sets of recommendations moving forward for influencers of the climate policy agenda:
- Focus on results. Climate change abatement is a function of global GHG concentrations. Too much attention pursues symbolic objectives, like preventing fossil fuel infrastructure. This tends to undermine abatement goals and impose high costs.
- Emphasize cost considerations in policy agenda setting, formulation, and maintenance. Negative abatement cost policies should take top priority, with an emphasis on mobilizing beneficiaries. Robust cost-benefit analyses should precede all cost-additive policies and be reconducted periodically to guide policy adjustments.
- Prioritize quality state capacity. The net benefits of abatement policies are sensitive to government capacity and performance. Public management is in great jeopardy in an era of institutional decay. Negative-cost policies are often highly technocratic and require sufficient staffing expertise and accountable management at public institutions like DOE, FERC, PSCs, and permitting and siting agencies.
In an era of energy affordability precedence, a reset climate agenda should anchor itself in good policy basics. That is, a sober-minded return to results-driven, net-benefits prioritized policy. This should improve the durability of climate policy and ensure it enhances social welfare. Executing reforms well requires a recommitment to improving the quality of institutions as much as the policy itself.
Bureaucracy as Social Hope: An Argument for Renewing the Administrative State
I. Why Isn’t Government Working?
The “administrative state” is an unlovely bureaucratic term for a bureaucracy that has grown increasingly unloved: the network of government agencies that implements and enforces laws. In the United States, critiques of the administrative state abound. The nativist right pushes back against a purportedly dangerously powerful “deep state” while the left sees a meek state beholden to big corporations and incumbent interests. Libertarians bemoan bureaucratic inefficiency and hubris, while the newer “Abundance” movement describes a state choking on its own procedures. Though different narrators are telling different stories, they are arriving at the same moral that the core mechanics of the world’s greatest democracy just don’t work. From there, it is not too big a jump towards casting a nihilistic eye on democracy itself, and towards reckless deconstruction.
Erosion of faith in government is manifesting acutely in the climate movement. The Inflation Reduction Act (IRA) was by far the largest climate investment the world has ever seen. Biden-era regulations were intended to further spur rapid decarbonization of the world’s largest economy. And yet. If we had a dollar for every word written about the administrative state’s failure to effectively implement the IRA, we’d be shaving truffles on our eggs. Meanwhile, the current administration’s regulatory rollbacks are the latest play in what seems to be a never-ending game of political football around federal climate policy. If the administrative state can’t effectively address challenges it deems an “existential threat”, one might ask, what good is it?
Our answer: the American administrative state, since its modern creation out of the New Deal and the post-WWII order, has proven that it can do great things. Vast bureaucracies now successfully care for the elderly, the sick, the poor. Many communicable diseases are close to elimination. The administrative state, by directing tremendous amounts of public and private effort, built the power grid, the internet, the interstates. Nor are our glory days behind us: The American administrative state played the primary role in ending the Covid pandemic, saving millions of lives.
Even when it comes to climate change, the record simply isn’t one of failure. American bureaucratic regulation, including from the Environmental Protection Agency (EPA) and from the states, and from air pollution standards for cars to carbon trading systems for entire economies, combined with significant incentive investments, has brought us technological transformation. Renewable energy is the dominant source of new energy globally. Electric cars now comprise 20% of sales globally and will replace internal combustion by mid-century. Whole industries are decarbonizing and emissions will shortly be beginning to fall. For all the many dubiously legal rollbacks of the second Trump administration, the United States continues to decarbonize.
And so, we argue, it’s hardly time to abandon the administrative state. But it is time to reinvent it. Our core supposition is that the sense of malaise and stasis characterizing current views of the bureaucracy has a substantial amount to do with mismatches between tools that produced current successes and the next set of tools that will be required to sustain and grow them. In the same way that nations might have a first or a second Republic, with constitutional reforms intervening, it is likely time for the next American administrative state.
Again, grounding in climate illustrates the point. Significant administrative pushes have commercialized the technologies needed to address the climate crisis and substantially pushed them into use. The Inflation Reduction Act supercharged this process in the United States, while China – which has sought to dominate clean energy supply chains via its own administrative state and invested accordingly – did so globally. As we enter 2026, there is no real doubt that many clean technologies are available, profitable, and better than fossil technologies. Every nation, including those that do not substantially produce these clean technologies, benefits from their adoption.
But we are now running into a “mid-transition” moment, in which rival technologies, energy systems, and the economic and political systems on which they depend, are in collision. Consider electric vehicles (EVs). It is one thing to call EVs into being by imposing traditional “supply-side” regulations on manufacturers. It is quite another, as gasoline demand begins to sharply decline, to manage knock-on consequences for the entirety of the fossil economy, from refineries to pipelines to gas stations – much less the local and state budgets and jobs that the fossil economy underpins. Though regulatory strategies can be designed to address these economy-wide consequences, we won’t get there by running the same plays harder and faster. We’ve got to seriously interrogate where the most significant bottlenecks are, who is equipped to address them, and what tools they have or will need to deploy.
Now add two further wrinkles.
First, procedural tangles that were created for all the right reasons, but that now hamper problem solving. In the environmental space, laws and processes were put in place decades ago to carefully scrutinize the impacts of potentially polluting infrastructure and factories. These measures have, in many instances, succeeded in preventing harm and protecting communities. But they are also indisputably making it harder to rapidly, massively scale up green technologies. This “Greens’ Dilemma” playing itself out in debates over the national environmental regulatory regime nationally is, in fact, a specific manifestation of broader dynamics. Incumbent systems, and those invested in them, do not particularly like to change. Indeed, the American administrative state generally was designed to move deliberately and deliberatively, including multiple veto points to avoid capture by industry or any particular interests. A worthy goal, but distinct from moving with speed towards the public good. When system inertia makes it too easy to grind the gears, the result, unsurprisingly, is painfully slow progress on building new public infrastructure and harnessing new innovations. If we zoom back in on the environmental space with these broader dynamics in mind, the particular obstacle inhibiting climate progress emerges with startling clarity: a system that was designed to produce cleaner technologies within the fossil economy is simply not set up to replace the fossil economy.
Second, the fact that capacity of the government to navigate these challenging dynamics has been sapped. There are multiple drivers of eroding government capacity. At the state and local level, years of corrosive narrative attacks translated into unwise revenue restrictions that in turn made forward-looking capacity investments all but impossible. At the federal level, a variety of policies and misaligned incentives have led to stasis and overreliance on contractors as opposed to internal expertise. At all levels, well-intentioned good-government and environmental reforms have imposed layers of analytic requirements that, while initially successful, ultimately contributed to “kludgeocracy”, while a highly litigious American society has, unsurprisingly, produced a highly risk-averse American government. Make no mistake: U.S. government at all levels has, and has always had, countless dedicated and talented civil servants who find ways to accomplish great things. But generally, this government is riddled with systems and structures that make it ever-more difficult for even the most effective individual to quickly and creatively deliver, especially when armed with aging legal and regulatory tools.
The upshot? We need not lose faith in the administrative state itself; we would do better to view it as having functioned with its hands tied tighter and tighter. But we are now starting, particularly in the climate and energy space, to hit real limits.
These aren’t issues we can resolve with one-off budget bills or Band-Aid workarounds. The vision, and the fixes, will have to run much deeper. The second Trump administration’s massive federal shake-ups, if nothing else, have opened the field for reconstruction. There is an opening – and, we believe, transpartisan appetite – for a bold, positive vision of a government that is attuned and responsive to the needs of American people and communities, that people can trust to deliver things like cheap, reliable energy; affordable, abundant housing; and fast, safe transportation even as it adeptly manages complex, higher-order challenges like climate change.
To launch its new Center for Regulatory Ingenuity, the Federation of American Scientists (FAS) engaged an ideologically diverse cohort of experts on government capacity and climate to describe how we might realize that vision. This cohort was asked to consider how to advance a paradigm of “regulatory ingenuity” – that is, creativity and cleverness in service of societal objectives alongside basic democratic values – in one or both of the following ways:
- Ingenuity in regulatory design. Looking across the entire regulatory lifecycle – from underlying statutory construction, to rule development, to implementation and (ideally) iterative improvement – to seriously examine how existing regulatory systems in the United States can be improved, and identify where fresh thinking is needed.
- Ingenuity in regulatory application. Considering how regulations can be coupled with other tools (e.g., innovative market designs, financial instruments, contracting mechanisms, etc.) to achieve societal goals quickly, equitably, and durably.
“Bureaucracy as Social Hope: An Argument for Renewing the Administrative State” is a collection of essays capturing the cohort’s insights. Essay authors envision new alignments of regulatory and financial power, new tools to enable multiple levels of government to move fast, to address distributional impacts, to channel capital at scale, to finally build infrastructure, and to, most fundamentally, break free from stasis. They are, eminently, not cynics. Though clear-eyed about the failings they seek to remedy, they understand that these failings are largely the shadows cast by past success.
While these essays are grounded in climate policy, they address cross-cutting themes. They use climate as a lens to evaluate where government is and isn’t working. Indeed, the authors’ commentary with respect to government performance on climate challenges is easily extrapolated to other domains.
In writing, the authors revive an older American tradition of a vital administrative state in service of an equally vital and egalitarian democracy. Our nation used to regularly reorganize its government, and the Congress used to legislate regularly on hard problems. The recent reality of agencies working within aging statutes and confined by outdated structures was not the dominant face of government during the creative ferment of the New Deal or the Great Society or, indeed, of the Reconstruction itself. It is, in fact, deeply odd that we still largely live with the same administrative agencies and processes that we had in the 1970s.
So what should – what could – a modernized administrative state look like? The authors together imagine:
A government that can deliver. It doesn’t need to take a generation to build a railroad, a power grid, or new housing. We can trade a veto-ocracy for the older progressive tradition of governance that rapidly responds to public needs – and secures us the service and infrastructure we need.
A government that can make decisions. The rules of the economy need to stop changing with every election and every major lawsuit. Re-empowering Congress to make big choices, and administrative agencies to deliver without constant swerves, will allow us to stop re-reading the manual and actually play the game.
A government for a modern economy. The future should be innovative and egalitarian. Realizing this future requires the de-risking and direction-setting powers of government to invite bold bets and spur investment, and the distributive powers of government to ensure that benefits are appropriately shared.
A government that listens and responds. We can replace the prevailing procedural labyrinth with a government that asks focused questions on the key issues, acknowledges and addresses real disagreements, and then moves forward thoughtfully yet confidently. That would involve, in part, staffing government fully and organizing it well – reversing decades of attacks on public servants and putting people to work on the right problems.
A government that works on all levels. Federal, state, and local governments each have unique levers and comparative strengths when it comes to serving our communities and society. A modern administrative state should recognize these, and emphasize frameworks that enable them to work well together.
Americans have spent too long living within a slowly failing version of last century’s government. The resulting civic frustration has largely fueled further attacks on government, spiraling us downwards. But an upwards spiral is possible too, in which structural reforms yield a government better equipped to chip away at tough problems in ways that improve daily life and rebuild civic satisfaction. Because while the “administrative state” as a term is about as wonky as you can get, a renewed administrative state in practice is just common sense.
II. New Approaches for Climate and Democracy
As you will discover as you read, the authors do not all agree on every particular; our goal in inviting this collection was good-faith debate, not artificial consensus. Yet a survey of the collection’s component essays reveals common themes.
For instance, the authors generally agree that economic and industrial policy will be central to the next chapter of climate action. Incumbents still heavily invested in mature fossil-linked technologies and supply chains, as well as non-transparent pricing and other barriers to market entry, badly constrain the transition to competitive clean technologies in many sectors. And where promising technologies are still earlier-stage (e.g., as is the case for nuclear, geothermal, or green hydrogen), there are compelling arguments for government involvement to help establish U.S. dominance. Pollution regulators do not typically, though, control fiscal and monetary tools that can (i) correct market distortions, (ii) manage the very considerable distributive impacts of a shift away from fossil fuels that profoundly impacts industries and jobs across regions, and (iii) support a comprehensive strategy for incubating high-potential domestic industries. Nor are these regulators, with little ability to affect trade policy, well positioned to act within the complex geopolitical context of a partial energy transition. To put it frankly, it doesn’t make a lot of sense to run a massive societal transition with substantial global implications through the EPA. But in the absence of purpose-built institutions and statutes, that’s pretty much what we’ve been doing – with politically and legally unstable results.
This problem is compounded by the fact that the Supreme Court’s skepticism of sweeping regulatory mandates based on old statutes has left the administrative state with ever fewer tools to respond to economic transition needs. Regulations are regularly reversed, and the ongoing duel between litigators and executive branch agencies increasingly looks like an unproductive stalemate. The authors generally chart a path towards a reinvigorated role for Congress to settle disputes, for agencies to act more inventively, and for disputes to move away from the courts and back into democratic processes.
The authors further point out that regulatory efforts alone are not sufficient to drive the infrastructure shifts needed to make those efforts last, or to buffer their up-front costs. Big infrastructure projects – including vastly growing the clean power grid, electrifying freight, expanding and upgrading transit systems, building new housing, and dismantling legacy, non-economic fuel systems – are central to regulatory success and stability, as well as to addressing an ongoing cost-of-living crisis and boosting national economic competitiveness. Infrastructure, the authors emphasize, isn’t an afterthought – it’s a core enabler of regulatory policy. Unfortunately, the now decades-long trench warfare over climate and other regulations has been accompanied by attacks on the state itself, stripping away administrative and delivery capacity along with the ability of many subnational governments to collect sufficient revenue to fund even basic services, let alone flagship infrastructure projects. The authors vehemently agree that there is much room to trim bureaucratic bloat, streamline process, and sensibly reorganize agencies. At the same time, they observe that a government that is smaller doesn’t always work better; not infrequently, the opposite is true. The authors therefore favor approaches that fit government agencies with the staffing, structures, and revenue they need to deliver on outcomes. Sometimes, those approaches are tweaks. Other times, they’re radical reforms.
II.A Towards a Shared Affirmative Vision
So how do we tackle these challenges – how do we start the upwards spiral in which effective delivery reinforces faith in democratic governance that in turn unlocks more delivery capacity? The authors develop a shared affirmative vision, one that broadly looks like this:
- Embrace whole-of-government engagement on economic strategy. Driving economic direction has long been viewed as a core role of government in the United States and in many other nations). To achieve climate goals as well as position the United States for success in the next energy era, the authors argue that the United States should embrace whole-of-government engagement on clean technology, regional economic diversification and resilience, regional transitions away from fossil fuels, and inequality reduction. In so doing, the United States would more appropriately leverage the full governmental toolbox (including substantial involvement of trade and economic agencies), with pollution regulations rendered far less politically and legally isolated. New institutions and agencies would be created to facilitate an effective, durable, and broadly beneficial economic transition, while sunsetting laws and structures that are outdated.
- De-gunk infrastructure process. From speeding interconnections to a truly national power grid, to rapidly deploying transit systems, to supporting clean industrial clusters, the authors see substantial opportunities to build our way out of looming climate and economic threats. Rethinking public participation – which today too often amounts to an unhelpful, seemingly endless series of veto points – is essential to realizing these opportunities. Done right, the authors argue, public participation can ensure that what we’re building will work and last, but without making it impossible to build at all.
- Support agile, pro-competitive finance. The authors would move us away from one-time budget bills, subsidies for mature industries, and temporary consumer incentives and towards a model focused on pushing private capital rapidly towards public needs – including strategies to bring competition to markets and systems dominated by pro-fossil incumbents. Again, the authors emphasize the role that government can appropriately play as an economic driver, albeit in this case by “greasing the wheels” of finance by shifting funds rapidly where they are needed, providing backstops and guarantees to de-risk private investment, developing financial metrics and vehicles that can help capital move at scale, and facilitating transactions across jurisdictional and sectoral boundaries.
- Work through problems – not around them. Government needs to insist on democratic decisions, even on hard debates. Those decisions should be made in Congress (or at subnational levels, analogous legislative bodies) and implemented through effective bureaucracies. It’s time to shift from courts as the primary locus of debate for many advocates towards the democratic branches. Relying too heavily on courts to resolve genuine policy debates tends to entrench the debating sides for the long term. Though there will always be a role for judicial oversight, that role is neither as a source of radical new mandates, nor as a referee that functionally provides “permission to ignore the other side”. The authors suggest institutional reforms that can help rebalance the distribution of decision-making authority across branches of government, emphasizing the importance of democratic and legislative voice in this task.
- Build capacity from the ground up. State and local governments are at the frontlines of climate and extreme weather impacts. They’re also closest to people, communities, and their unique needs, and have tools for responding that the federal government doesn’t. While the administrative state is often perceived as almost entirely federal, the truth is – as legal scholar Anthony Derron astutely observes – that many federal programs and schema are implemented through state statutes, regulations, and agencies. In short, Derron writes, “cooperative federalism relies on the capacity of state institutions to function.” We would add that state institutions and schema similarly rely on their local counterparts. The authors emphasize the role of subnational governments as co-equal partners in realizing an agile, effective, and durable administrative state, as well as the many ways in which focusing on state and local capacity can kick-start administrative renewal now, rather than waiting until after the next federal election.
The collective vision is one in which the administrative state starts moving again, returning to the ethic of ongoing systematic revision that once characterized it. Rather than relying on the best ideas and institutions of a half-century ago, we would work towards structures more aligned with current needs – and do so in a way that reaffirms the creativity and vigor that has long powered America’s economy.
II.B Laying Out The Pieces
Each of the essays in this collection lays out particular pieces of the shared vision. Broadly: the collection starts by proposing fundamentally different ways to think about environmental and administrative law, seeing its task as delivering a clean economy at scale, rather than simply cutting pollution, and doing so with stable rules derived in democratically legitimate and procedurally stable ways. It then explores how these legal and regulatory structures could help guide the far larger private sector into configuration with public goals, removing barriers to competition that have insulated stubborn fossil incumbents and creating opportunities to move capital at scale into communities in ways that build a fairer and cleaner economy. From there, wrestling with the dislocations that nonetheless will accompany these changes, the collection describes ways to link participatory democracy with economic change, sharpening the focus of the regulatory state and its engagement with the public. The collection concludes by bringing these issues home, describing how state and local governments can deliver today – and presenting a “policy primer” of innovative ideas that can start moving from ambition to action this year. Below, we discuss each of these pieces in turn.
Jordan Diamond and co-authors at the Environmental Law Institute lays the foundation for this collection with a careful look at what environmental law can do, what it can’t, and how we might rebuild its powerful tools for modern challenges. They argue that the pollution statutes of the Nixon era, crucial though they are to addressing environmental contamination from fossil fuels, are at best limited tools for a whole-of-economy shift away from fossil fuels entirely. Viewing that new challenge as fundamentally one about driving economic innovation and infrastructure growth, they chart out areas ripe for legal development. At the same time, they explain why the next round of environmental progress is more likely to be led by infrastructure and economic agencies than pollution regulators – emphasizing that while pollution regulation will remain critical, we should stop asking pollution regulators to drive a national economic transition with aging environmental statutes alone. Their vision is of treating the energy transition like the economic problem it is, with tools to match. They would expand state capacity, bringing to bear a much wider set of agencies and approaches, and therefore also expand what we think of as “environmental law” to respond to the modern era.
Still working within legal reforms, Kirti Datla takes a close look at the profound challenges modern administrative law poses to the regulatory state. The Supreme Court’s new doctrines, she writes, are making it very difficult for environmental agencies, and regulators generally, to address new problems (and often even old problems) through existing statutes. And they suggest that the Court will impose its deregulatory views on even new statutes. These ever-changing rules strain government capacity, make it difficult for subnational governments and investors to plan a path forward, and prevent progress on policy goals. After acknowledging the need for new regulatory approaches, judicial system reforms, and new statutes, Datla focuses on how Congress can and should engage in the constitutional politics of asserting its role within our federal system, both to constrain the Court and to build its own capacity to address pressing problems like climate.
These two foundational essays, then, help us see the challenge before us. They explain why a kludged-together administrative state running off old statutes and aging structures keeps sputtering to a halt – and start to focus us on an expanded field of play, well beyond re-litigating the environmental policy disputes that have seesawed between the Obama, Biden, and Trump administrations. It is not that the regulatory state is inevitably a “hollow hope” for the shared challenges of climate, democracy, and fair economic growth – but that it has been asked to tackle enormous challenges without a shared theory of action or structures to match. Shifting the economy from its incumbent fossil foundations to a new electrified base, while managing the many linked distributive impacts of that shift under growing climate pressure, simply requires more than pollution regulations or one-time tax policy. If politics is the “slow boring of hard boards,” it helps to have the right tools to drill deep.
But, as Devin Hartman and Neel Brown posit, new tools need not – for durability’s sake, must not – be expensive tools. Nor will another round of mandates succeed without thinking seriously about how to address accompanying costs. Hartman and Brown argue that traditionally conservative lenses that look skeptically at giant fiscal policies and regulatory mandates do, in fact, bring to bear a canny understanding of the interests of incumbent economic system actors. The authors point out that the stuttering progress of the transition to clean technologies comes from the ways in which fossil fuels are deeply intertwined with the interests of powerful economic incumbents, and of existing government. And, having traced the root of the challenge, they conclude that opening these incumbents up to competitive disruption through appropriate reforms will be a potent strategy. For instance, Hartman and Brown contend that the repeal of the IRA may appropriately shift focus of subsidies from mature energy technologies (including clean technologies like solar as well as most fossil technologies) towards earlier-stage technologies (e.g., geothermal). From permitting reform to addressing market problems that deny Americans access to affordable EVs, Hartman and Brown set out a creative array of solutions that, with government backing, can push forward a modern economy at low, or even negative, cost.
Sometimes aligning with these arguments, sometimes complicating them, and always making them concrete, Beth Bafford describes how a focused set of government investments can further shift the economy onto new foundations by using public capital to leverage far greater private investments in the fundamental infrastructure American needs. She outlines how to wed together Hartman and Brown’s pro-competitive policies with the expanded and stable regulatory mission state described by Diamond and Datla. Regulators have often operated on a model in which government grants help underwrite regulatory mandates. Bafford instead starts to outline a structure in which government investments – including simple and accessible loan products – instead help shift the economy towards profitable and self-reinforcing clean new industries. Her model is one in which capital access builds entire businesses that can electrify and modernize core sectors of the economy, from the freight sector to the power grid. Regulations can and should still set the direction of travel in this model – but its engine is broadly shared profitability. Rather than forcing innovation into new channels with politically-exposed regulatory mandates, agencies in Bafford’s model would help convene and channel the economy towards new system states entirely, with regulations conceived as tools operating in concert with economic investments and planning to help crowd in capital to communities across the country.
Nicole Steele explores the role of capital in renewing the administrative state from a different lens. Steele observes that mission-aligned financial institutions (including values-based banks, green banks, CDFIs, and other purpose-driven funds) are increasingly functioning as essential partners in the administrative state’s delivery capacity. Sitting at the intersection of public policy and private markets, these institutions translate legislative and regulatory goals into bankable, scalable projects by absorbing early risk, standardizing structures, and aggregating demand. In practice, this has included mission-aligned banks working alongside state and local governments to deploy catalytic capital – whether as first-loss reserves, flexible operating support, balance-sheet backstops, or credit enhancement – in support of simple, repeatable lending platforms (such as residential and commercial PACE financing) that allow households, small businesses, and local governments to access clean energy, resilience, and efficiency upgrades without relying on bespoke grants or one-off subsidies.
By deploying catalytic capital, Steele continues, these intermediaries unlock funding that would not otherwise reach underserved markets or emerging project types. Critically, investment into mission-driven institutions does not substitute for private capital; it enables it. Strengthening the balance sheets and operating capacity of green banks and CDFIs allows them to originate, warehouse, and scale lending products that meet market standards, crowding in institutional capital while maintaining public purpose. In a period of federal uncertainty and shifting incentive regimes, expanding the availability of catalytic capital will require a diversified approach: drawing on state and local public balance sheets, philanthropy and quasi-philanthropic capital, and mission-aligned institutional investors willing to deploy flexible funds through intermediaries rather than relying on centralized federal programs alone.
Nana Ayensu builds on Bafford and Steele’s insights. As Ayensu points out, we have a transformational economic opportunity to deploy modern, clean energy infrastructure at scale.
Federal and subnational governments have a real chance to catalyze significant capital deployment of mature and emerging clean energy technologies that are primed for growth – both directly and via investment into infrastructure. Widespread social benefits are available if governments use their authorities to assemble the puzzle pieces needed to create more actionable investment environments. Ayensu describes the state’s ability to do so: it can synchronize intra- and intergovernmental policy execution, build high-value foundational infrastructure to provide project stakeholders with the information they need, develop deeper risk and reward sharing partnerships with the private sector, and create the market forces that close align with economic & societal benefits. Making this type of consistent, efficient multi-pronged effort will be critical to garner the scale of investment needed to expand and update critical energy infrastructure systems and deliver lasting value to communities and industries across the nation.
Ali Zaidi makes the case for bringing this ingenuity to the arena of critical minerals and materials, what he calls “the atomic foundation for reindustrialization and any shot at lasting prosperity and security.” Zaidi draws moral inspiration from America’s post-oil shock response, a crisis moment that authored a broad policy playbook with a spine for experimentation. New laws and regulatory authorities, institutions and infrastructure, and moonshot moves on research…that moment, he writes, gave life to policy to solve a problem. It was “policy with helmets and pads”: playing offense, not defense. Zaidi urges bringing that same positioning to minerals and materials security policy today. In his conception, that policy should entail three pillars – production, partnership, and a drive for increasing productivity – that together support the shared goal of strengthening American competitiveness.
The third pillar is where Zaidi spends the most time. The oil shock of the 1970s propelled domestic standards designed to achieve greater fuel economy and appliance efficiency. Such standards have been weighed down over time by clunky test procedures, multi-year rulemakings, and heavy hand of government auditors. Zaidi proposes a framework for materials productivity that adopts the same solutions-oriented spirit of the 1970s energy policy environment, but is characterized by standards that bind instead of burden. To unlock minerals and materials security, Zaidi writes, “we should replace red tape with rubber bands, just enough structure to allow us to slingshot forward new production, processing, and partnerships — and increased productivity.” Zaidi details a framework that is digital, dynamic, and data-driven: where enforcement is algorithmic, not bureaucratic; and the work is easily federated and easily staffed. This light, flexible scaffolding will accelerate capital formation and technological innovation.
Indeed, Jennifer DeCesaro, Jennifer Pahlka and Hannah Safford add, we’d do well to apply a similar mindset to planning: a standard feature, and all-too-common bug, of climate policy. Environmental statutes are rife with planning mandates, from Clean Air Act implementation plans to natural hazard mitigation plans required by the Stafford Act to all things NEPA. Look beyond pure statute and become quickly overwhelmed: climate-related plans are mandated by public utilities commissions, developed by task forces, produced as a precondition for grant eligibility, and on and on. Though plans are easy to ask for, they’re often expensive and time-consuming to develop; moreover, lack of coordination among overlapping plans can lead to duplication or even contradictions. DeCesaro, Pahlka, and Safford therefore ask a simple question: “What are all these plans getting us?” They argue that climate policy too often falls into the trap of “planning primacy”, where planning becomes the end goal instead of an intermediate step towards progress. Put another way, it’s rarely the case that a plan is developed and its directions are then followed to the letter. Rather, the process of thinking through scenarios, understanding constraints, building mental models, and developing relationships with other plan stakeholders is what really matters. DeCesaro, Pahlka, and Safford draw from both the climate space and other domains to illustrate how treating plans as compasses, not maps, can improve efficiency and outcomes. Because to quote Eisenhower: “In preparing for battle I have always found that plans are useless, but planning is indispensable.”
Shifting incumbent systems requires not just low-cost solutions, access to capital, and competent, efficient regulatory capacity. It also requires ways to reconcile or resolve competing interests. Our current regulatory system has gotten bogged down with ineffective procedural approaches to dispute resolution, yielding a litigation-driven collection of process fouls and veto points that no one really likes. Our next set of authors observes that improving this system requires more than a simplistic call for deregulation. Moreover, they argue, the solution can’t be to ignore stakeholder input altogether – that runs the risk of policies that are poorly informed, technically unfeasible, and brittle given lack of buy-in by the businesses, communities, and people they serve. Rather, our authors propose a range of reforms to help administrative bodies effectively collect input from stakeholders, weigh hard trade-offs and disputes, and move forward fairly, but expeditiously: thereby using democratically legitimate decisionmaking to strengthen industrial policy.
The first of these authors is James Goodwin, who argues for an “agonistic” view of the regulatory state in which regulators must actively surface and invite input on genuine disputes. Goodwin proposes replacing today’s box-checking engagement exercises and voluminous stacks of public comments with a focused participation process. In this process, administrators would at each state of a project or regulation, identify the core disputes and disagreements that need resolving, and draw in input specifically on these issues. By targeting engagement – and avoiding consensus – in this way, administrators would be able to efficiently advance dialogues with the public that are both quicker and inherently more resistant to status quo bias.
Loren DeJonge Schulman and Shaibya Dalal pick up on this theme. They argue that treating public engagement as a strategic asset, not a box-checking exercise, leads to smarter, more durable policies that reflect real community needs and build trust in government. Participation is not a distraction from governing – it is how government governs well. They argue that the failure of many engagement processes is not that agencies invite too much input, but that they do so too late, too perfunctorily, and in ways that exclude the communities most affected by public decisions. When participation is treated as compliance rather than governance, it fuels distrust, invites procedural obstruction, and produces policies that are fragile and contested. By reflecting the full range of transactional public participation and relational community engagement options, and by applying clear principles (purposeful design, mutual respect, transparency, accessibility, and iteration) agencies can use engagement to surface lived experience, anticipate conflict, improve policy design, and strengthen the legitimacy and durability of their actions. Done well, participation becomes a form of ingenuity that reduces conflict, eases implementation, and reinforces democratic accountability.
Of course, inviting public participation only works when people are interested in participating. Angela Barranco and Kristi Kimball argue that the American climate movement faces a critical public engagement crisis that threatens to undermine decades of progress on clean energy adoption – and explore how advocates can speak to the public to build interest and support for the shifts that government seeks to deliver and legitimize. Despite nearly 70% of Americans expressing concern about climate change, Barranco and Kimball contend that current advocacy strategies fail to tee up paths for politically durable dispute resolution (and eventual support) because those strategies are unduly rooted in fear-based messaging and technical data. Barranco and Kimball make the case for a shift towards a public conversation that approaches Americans as consumers (who must adopt new technologies and cannot be persuaded through regulatory mandates alone) making lifestyle choices rather than political constituents to be mobilized. Drawing on proven strategies from consumer marketing, behavioral psychology, and community-based social marketing research, Barranco and Kimball observe tremendous opportunities for (i) reframing climate engagement around consumer choice, and (ii) leveraging the unprecedented infrastructure investments necessitated by extreme weather impacts to build lasting climate coalitions while simultaneously strengthening democratic institutions and community trust.
Ultimately, these changes and debates occur not in the abstract, and not just in Washington, DC. State and local governments are the theaters in which economic and democratic change play out, mediating federal policy and global geopolitical shifts in the lives of real people. Thus both the climate crisis and the economic transition are inherently “polycentric”. Subnational governments have therefore always been at the core of climate and regulatory policy. It is these governments that are most able to set democratically responsive visions for clean economic growth, climate resilience, and infrastructural change that will concretely change lives. If our future is to be shaped more by ordinary people than by technocrats, it is these governments that must have the capacity and creativity to act.
Louise Bedsworth provides a prospectus for local action. As she argues, a rebuilt regulatory state has to position state and local governments for creative action and response. These governments, she writes, are more than subsidiary partners, and more than replacements for federal regulators during deregulatory periods (important though those roles can be). State and local governments are innovators and leaders in their own right. The task is not just to provide ancillary community benefits from federal grants, or to mandate particular state plans, but for state and local democracies to be engines of national and even global change. By expanding their own capacity, aligning capital and economic plans to build regional prosperity and resilience, and engaging in and leveraging networks across geographies, nationally and globally, subnational governments can reshape climate action and the regulatory state.
Indeed, because of the enormous creativity of subnational governments, and the huge opportunities created by the private sector, in response to past regulatory guidance and government investments, we do not need to wait for a new federal administration to start putting solutions into place. We have already identified a broad network of ideas and actors that can start building these ideas in reality, this year – in a policy primer for that foundational work. The primer, crowd-sourced from leaders across the field, highlights a starting list of policies well within the reach of subnational actors, and focusing strongly on economic and industrial policy interventions that can durably advance clean economic systems while managing real trade-offs with savvy deployment of government capacity. It is a practical point of engagement, allowing for the ideas articulated in these papers to be tested now, not after further electoral cycles.
III. Conclusion
We do not need more stories of American decline. Critics on the left, center and right have already told us that our government doesn’t work. Americans feel underserved, underrepresented, and ripped off. But Americans also know how to do better. We are always rebuilding our democracy; it is time to do it again.
Collectively, our authors have sketched out the beginnings of an administrative state for this era – grounded in the pressing challenge of climate change and its increasingly evident impacts on American lives. This state would enable governments across scales, and stakeholders across sectors, to realize the vision of a nation where:
- Commercial green technologies are matched with coherent economic and industrial policy, creating broadly shared wealth and revitalized, livable communities.
- Government agencies are empowered to resolve disputes and respond creatively and flexibly to changing situations, supported by the courts and guided by Congress.
- State and local governments, staffed at a level that allows delivery, are engines of green innovation and rebuild aging infrastructure in ways resilient to a changing climate.
This sort of “mission state” – a government that sets a clear vision and brings together public and private sectors to execute it – is actually an old American tradition. What else were the New Deal, the Apollo Program, Operation Warp Speed, and the creation of the internet than missions of this sort? Indeed, when it comes to newer challenges like climate change, we have started, a bit haphazardly, to reach for a mission again. The Inflation Reduction Act’s billions in investments, and the Biden administration’s complementary regulations, were an attempt to bring together the public and private sectors around the vision of a clean and prosperous economy, with good-paying jobs and dominance in the technologies increasingly certain to underpin the 21st-century global order. Yet because of obstacles identified above, that mission was…while not entirely a failure, hardly a resounding success.
But the mission remains necessary. America must not remain mired halfway between the old economy and the new, exposed to climate shocks, with a government unable to satisfyingly respond. Clean technologies are advanced enough that retrenchment and retreat to fossil is a doomed strategy; similarly, we’ve seen that taking a chainsaw to government leaves our whole nation bleeding.
The only logical approach is to tap into the creative, determined spirit that is the essence of American identity. Think of the millions of Americans who, in the midst of the Great Depression, spread out to every part of this country to rebuild it. We still live among the lovely parks, trails, and civic architecture called into being by the Civilian Conservation Corps; our power grid was brought to us by rural electrification, the Federal Power Act, and the Tennessee Valley Authority. We know what it looks like when Americans believe in government and the government is worthy of that belief.
It looks, to start, like a conversation. As CRI launches, in partnership with a broad network of partners and contributors, we invite debate, dissent, and experimentation. One of our goals is to bring together people and perspectives that are often in tension to identify where there are some threads of common sentiment – and how we can productively move forward despite the tension that remains. We will be gathering thinkers, exchanging ideas, and mapping out pilot projects with growing momentum across the months and years to come, working not just to theorize around solutions but to bring them to life. To adapt the truism about trees: the best time to renew our administrative state was ten years ago. The second-best time is today.
From Ambition to Action: A Policy Primer
How public leaders can boost climate progress, restore trust in government, and make lives better…starting today.
People across the nation are clamoring for solutions that make their lives better. And they’re frustrated by the responses they’re getting. Confronting massive inequality, Americans watch leaders finger-point on the price of eggs; yearning for security and stability, Americans watch politics lurch between radically different agendas. No wonder, then, that public trust in the U.S. government has been in the basement for decades. Americans are facing both everyday challenges and a deep, growing sense of discontent. But they’ve lost faith in government to resolve either.
That sense of stuckness doesn’t need to last. But change means focusing on outcomes, eliminating bottlenecks, and prioritizing delivery. It means embracing tools and talent that better connect big ideas to real-world results. It means resisting the temptation to chase buzzwords – from “abundance” to “dominance” to “affordability” – and focusing on the method over the message.
One place to start is with the shift to clean technologies, a place where there is powerful momentum. One in five cars globally are already electric, while heat pumps have outsold gas furnaces in the United States for four consecutive years. The vast bulk of new energy generation is renewable: globally, clean energy investment is now double the amount spent on all fossil fuels combined.
While the transition to clean technologies is unstoppably underway, it is also in its messy middle. Rival technologies and energy systems (and the economic and political systems on which they depend) are now colliding. Many counties and cities depend heavily on fossil fuel revenues; meanwhile, job quality and union density in the renewable energy industry leaves much to be desired. And core parts of our infrastructure – from the power grid to gas stations – are complex and expensive to convert to serve renewable and clean industries, even if those industries will ultimately boost affordability.
Put simply, remaining globally competitive on critical clean technologies requires far more than pointing out that individual electric cars and rooftop solar panels might produce consumer savings. But we also can’t afford to cede the space. Internationally, clean energy spending is booming. China’s clean energy industry by itself would be the world’s eighth largest economy if it were a country, and Europe’s investments have almost doubled over the last decade. Even if current estimates hold, fossil fuel demand will peak mid-century. If the U.S. continues to hold fast to existing policies until then, we’ll be 30 years behind the rest of the world’s energy economy, and it will be impossible to catch up. The bottom line? Good climate policy is good economic policy, and vice versa.
Good climate policy is also good politics. Climate-induced disasters are increasing by the day, and are impacting both safety and affordability. Americans generally see climate and energy policy as important as immigration. Most Americans, on both sides of the political aisle, support environmental regulations and clean energy development. Many say electricity costs are just as stressful as grocery bills, and they worry about higher insurance rates and local market problems. And they’re tired of entrenched corporate interests calling the shots.
What’s needed are creative, clever strategies that boost climate progress while delivering everyday benefits. The Federation of American Scientists (FAS), as part of our new Center for Regulatory Ingenuity (CRI), developed this primer to put a bunch of those strategies in one place. Our goal is for this primer to serve as a resource for public-sector leaders at the federal, state, and local levels who believe that government can do great things for our communities and our planet.
The strategies herein are open-sourced from a diverse network of contributors and collaborators, and are shovel-ready. Many of these strategies are already being deployed across the country. They’re designed to make energy, housing, and transportation better this year.
Indeed, we hope that readers see the actionability of these solutions not just as a benefit, but as an imperative. Americans aren’t looking for the magic message or the magic moment. They’re looking to government for leadership. Every day that government is paralyzed by gridlock, indecisiveness, or fear of failure is another day that it fails to realize the potential of the good that it can achieve, and that public trust in government further erodes. That’s a downwards spiral that we’ve got to stop.
Finally, we emphasize that this primer is a starting place. We’re at the precipice of a new era for climate and energy policy in the United States, and the strategies that will form the backbone of this new era – by adeptly fitting together government capacity, private innovation, and democratic decision-making – are just starting to come into view. As they do, CRI and its partners are committed to working hand-in-glove with bold doers and thinkers, sharpening our collective focus, and realizing the vision of a more responsive government, more optimistic society, and more resilient nation.
Getting to Work: Opportunities in Energy, Transportation, and Housing
Solving problems requires framing them accurately. As observed above, the truth is that clean technologies are increasingly dominant, and that the United States is rapidly falling behind. A response predicated on propping up the 20th-century fossil economy is doomed to fail. So too, we’ve learned, is a response that relies on the U.S. federal government to muscle the clean-technology transition forward single-handedly.
Fortunately, because so many clean technologies are now commercial, the opportunity for leadership on multiple levels, and multiple fronts, has never been more available – or more crucial. For example, simple economics will do much to propel wind, solar, and battery technologies if needed supporting infrastructure is in place and clean technologies are given the chance to compete on fair terms. Policymakers can worry less about expending political capital on expensive public subsidies for clean power, and focus instead on transpartisan policies enabling broad market access, streamlined interconnection processes, and swift power grid build-out. In the transportation sector, policies that ensure transparent vehicle pricing or increase market competition for legacy car companies may matter more than traditional regulatory standards.
This new reality also makes thoughtful economic, industrial, and social policy indispensable. The advent of new technology often comes with the promise of broad societal benefits, but making good on that promise is hardly a guarantee (witness the emergent effects of AI). It’s incumbent on government to ensure that the clean-technology transition reduces inequality and improves quality of life at scale, and that the transition doesn’t abandon workers in fossil-dependent regions and industries to the vagaries of the market. And it’s government, working across multiple scales, that can assess regional comparative advantages and figure out where the United States can still compete – as well as where it must innovate and diversify.
Government leaders, in short, have the unique ability to see all the way from the kitchen table to the commanding heights of the global economy, and to mediate between them.
We illustrate below the types of approaches that entrepreneurial policymakers can adopt to secure U.S. leadership on critical clean technologies, in ways that benefit all Americans. We focus on energy, transportation, and housing, which are collectively the largest sources of climate pollution and key elements of household and regional economies nationwide. The list below is not exhaustive, or comprehensive, but exemplary – a demonstration that there are real opportunities for change.
Unleashing Modern Energy
There’s massive untapped potential for clean energy in the United States. To realize it, we’ve got to make room for new energy to move.
This isn’t primarily a project of continued renewable energy subsidies: there’s good evidence that renewable energy can compete on a level playing field when it’s given the chance. Rather, the project is one of clearing away barriers to financing and building projects, fixing broken market incentives that favor existing players over new entrants and distort energy pricing, and accelerating construction of major grid infrastructure.
This project looks a lot like the successful national push towards rural electrification that the United States led a century ago: a serious effort that aligns private and public investments to rethink how and where we deliver energy. In executing this effort, we must grapple with the full set of barriers to building – not just cost and permitting, but also thorny local siting processes, misaligned incentives for electric utilities, and lengthy wait times to connect projects to the grid.
Today, of course, we’ve also got to reckon with the growing threats of cyberattacks and extreme weather to energy infrastructure, as well as the unprecedented, unpredictable energy demands of hyperscalers. Such challenges can only be managed by a mix of climate stabilization policies, economic risk-sharing strategies, and investments in infrastructure modernization. That’s not a cheap or easy proposition, but it is one with major lasting benefits.
At the consumer level, building more clean energy can help stabilize residential electricity prices (though many other factors also contribute to electricity prices and price volatility). More broadly, clean energy could unlock billions of dollars in potential efficiencies, such as by reducing costs associated with redundant natural gas transmission infrastructure. Expanding clean energy, especially distributed energy resources and virtual power plants, can also upgrade outdated grid infrastructure and secure it against cyber threats. But getting to these benefits requires government leadership.
Energy ingenuity could look like:
- Protecting consumer electric bills from data centers. New power-hungry data centers could raise bills for families and small businesses if we aren’t careful. States and public utility commissions (PUCs) can use ratemaking proceedings to protect households and small businesses from the costs of meeting the demand of large new customers like data centers. For instance, Kentucky’s PUC requires utility contracts with these types of large-load customers to include certain protections for other consumers: any extra costs generated by the large-load customer must be covered by that customer and not place undue load or cost on the utility that can be passed on to general consumers.
- Guarding against confusing and opaque bill increases. Utility companies drive the process of setting electricity rates, submitting justifications for rate hikes that are often tens of thousands of pages long. They frequently lobby regulators and other state policymakers to accept these proposals – and in almost all states, they can recover their lobbying and political expenses from customer bills. As a result, customers are paying more for energy, and it’s difficult for any regular person to understand why. States can help by playing a larger role in evaluating utility proposals and finding bill reductions. In Hawai’i, for instance, the PUC reformed its planning process to engage more stakeholders to produce analysis to inform grid investments and provide more transparency on key decisions. New York passed a law that requires PUCs to explain why rate changes are requested and how the proposed revenue would be spent, while California’s recent statute barring utilities from charging customers for their own lobbying helps even the playing field to ensure rates are set in a more balanced way.
- Making government more responsive to clean energy project needs. Many clean energy projects get stuck in clunky, outdated state and local processes, run by understaffed agencies that weren’t designed for speed and dynamism. Most clean energy projects don’t need federal permits, but almost all must secure state and local approvals before getting built. States can engage industry and communities to identify the biggest roadblocks and then make targeted changes to reduce permitting timelines and increase certainty without sacrificing quality of projects. For example, Pennsylvania recently updated its guidance for stormwater permitting for solar projects to provide developers with more clarity on how projects will be modeled to assess their impacts. A New York law sets standard timelines for permitting decisions and creates a centralized team to improve information sharing and help projects get through the approval process. At the local level, the Sol Smart program has helped hundreds of local governments streamline their permitting processes for solar projects.
- Getting more out of existing grid infrastructure. Modernizing transmission and distribution infrastructure is expensive and takes time; it has to happen but isn’t going to all get done at once. Longer-term investments must therefore be complemented with strategies to reduce operating costs and improve performance of the grid infrastructure we have in the near term. States and PUCs can push utilities, through planning and ratemaking processes, to prioritize integration of distributed energy resources, virtual power plants, battery storage, upgrades to existing transmission lines, and other grid-enhancing technologies. Colorado, Nevada, Washington, and South Carolina are examples of states that have adopted this approach.
- Using public finance and ownership to get projects built. Relying solely on private finance raises project costs (and therefore customer bills) and limits the types of projects that get built. Public finance and ownership can help fill the gaps and reduce costs. States and cities can move towards a variety of public utility models that champion clean energy. New York’s Build Public Renewables Act allows the state-owned power authority to build and own clean energy projects. Municipally owned utilities are not a new idea, but unlocking those public dollars for clean energy can help stabilize the investment landscape. But states don’t have to own the infrastructure to make a difference. They can also help finance projects. A 2025 California law, for instance, unlocked several new tools to use public finance to reduce the costs of new transmission projects.
- Empower regular people and small businesses to be part of the solutions. Community power – also known as distributed energy resources (DER) – can complement large-scale power plants to meet demand growth and lower bills. But households and businesses must overcome major hurdles to take advantage of small-scale solar, battery storage, and flexible appliances. In most places, utilities have not made it easy for customers to participate, as community power solutions do not align with their traditional business model. State leaders can change the status quo by creating mechanisms to compensate distributed resources for the value they bring to the grid, requiring utilities to procure a minimum amount of distributed clean energy, and making it easier to connect small-scale projects to the grid. For example, a 2024 Colorado law required the utility to create a mechanism to properly compensate customers for the grid benefits of distributed resources. And New Jersey Governor Sherill directed the PUC to take steps to make it easier to connect community power projects to the grid and allow new customers to register for community solar.
- Improve planning to attract more investment. Many regions with abundant clean energy resources simply do not have enough transmission capacity to deliver that power to population centers. As a result, developers are increasingly unable to move generation projects forward even when other barriers—like siting and permitting—are addressed. Outdated planning processes have led to inefficient decisions and dampened investment, which raises costs for customers and limits clean energy growth. States can address this issue by building out smart planning processes, working with PUCs, utilities, and other stakeholders to conduct integrated planning of new transmission lines and power plants to take advantage of low-cost clean energy resources. New Mexico, for example, created a new state entity to plan and finance transmission lines that can help move electricity from solar- and wind-rich parts of the state to population centers.
- Stop forcing customers to foot the whole bill for natural disasters and cyber attacks. Under the default utility ratemaking model, electricity bills include the costs of preparing for and recovering from disasters and cyber threats. In Western and Gulf Coast states, these costs have driven bills up fast. Disaster recovery is far more expensive than mitigation, so one way for states to take this on is to invest upfront in mitigation and resilience measures. States can increase scrutiny and analysis to ensure that utilities are focusing on the most economic mitigation and resilience measures, use public financing tools to reduce costs, and consider other approaches to paying for these investments outside of customer bills. A bill introduced in California last year, for instance, would shift wildfire recovery costs off of customers and onto fossil fuel companies.
Making Transportation Cleaner and Cheaper
People just want to get to where they’re going safely, efficiently, and affordably. Yet despite record levels of federal transportation spending, traffic, emissions, and pedestrian deaths keep rising. And as the Cato Institute observes, “U.S. policy contributes to an inefficient and costly transportation system that reduces workers’ time and incomes.”
We can do better. This starts by recognizing that in much of the United States, cars are both essential and increasingly unaffordable. There’s opportunity for a suite of policies that break market strangleholds while expanding consumer choice, moving us away from involuntary dependence on expensive cars and towards a future with transit that people actually want to ride – as well as affordable yet excellent, and often zero-emission, personal transportation. Core federal clean transportation programs have supported $4.6 billion in domestic investments and created at least 14,000 jobs in manufacturing, demonstrating the large-scale benefits of such programs and the economic case for continued federal support. Because the tools involved are nearly all within the authorities of state and local governments, and independent of ongoing federal regulatory disputes, they also can go into effect quickly.
On the vehicle side, this agenda includes governmental efforts to address legacy company market power. Incentives and protections for domestic manufacturing are sensible so long as they boost local economies, support American workers, and drive American innovation – but they’ve got to be coupled with policies ensuring price transparency and other oversight mechanisms, to ensure that benefits flow to consumers rather than pad company profits. Unlocking a more affordable, competitive, zero-emission vehicle (ZEV) market – with more options for buyers at lower prices – is also a key political foundation to the next round of vehicle regulatory mandates, by creating a larger constituency for further progress.
On the system side, states and cities can significantly build up regional budgets with savvy transportation investments. The data are clear that transit and walkability investments bring more valuable housing into cities and connect people with jobs, raising economic activity and raising property values. Investments in electric-vehicle charging similarly boost local business revenue and spurs economic vitality. Communities thrive when their members have transportation options (that all work well), instead of being steered towards legacy vehicle technology and wrestling with creaky 20th-century infrastructure.
On the vehicle side, transportation ingenuity could look like:
- Focusing on capital access to drive ZEV technology forward. Clean vehicles are now cheaper to run, in most cases, than fossil vehicles – a success of the initial wave of regulatory ZEV policy. But purchase prices remain high, making it difficult for many consumers and businesses to realize these long-term savings. The traditional way of solving this problem (incentive checks) runs hard into budget realities. The alternative is to focus ever more on lower-cost financial instruments, including loans, that can provide a return on investment and which can draw in private capital. Rather than writing grant checks, states can focus on de-risking ZEV finance, starting with state-backed loans for key consumer classes, and moving rapidly towards de-risking private loans (e.g., by guaranteeing the resale value of EVs – a far smaller investment than new-car subsidies). The goal should be to make a standard consumer or fleet loan for a ZEV as easy to secure as an internal combustion engine car loan is today. That possibility is on the horizon, and available for states that rapidly bring together financiers, consumer groups, and business interests to map out the financial products needed. Unlocking ZEV affordability is also a key foundation for the next round of regulatory progress, in states and at the federal level. States could implement a fee on retail deliveries—like Colorado has done—and put the revenue towards EV charging infrastructure or towards unlocking ZEV affordability. Like California is doing, states could consider an EV incentive program that requires participating OEMs to match state funds dollar-for-dollar.
- Stop legacy companies from jacking up prices. In addition to creating new capital flows, states need to make sure that investments translate into low prices. Especially in the heavy-duty truck and the bus sector, concentrated markets and non-public pricing have given manufacturers far too much power to keep prices high. One straightforward intervention is to use existing sales and pricing data held by state DMVs on every vehicle transaction to publish pricing information across vehicle markets, and then to task state market oversight bodies (including attorneys general) with addressing overconcentrated market power using antitrust and business law tools. State financing mechanisms can also be explicitly tied to lowering prices year over year, driving affordable vehicles into the market.
- Drive competition in the ZEV market. The ZEV market is a big one, and state support through economic development offices for new market entrants can drive down prices and boost options for consumers. States are well-positioned to support new companies – both in-state (as California did by creating Tesla a decade ago) and via working to onshore competitors, with adequate protections, from overseas. These companies can compete on price, onshore overseas companies that are making more affordable electric vehicles, or figure out ways to lower the costs of imports, to lower overall consumer costs and provide healthy competition to incumbent companies that are slow-walking incorporation of new vehicle technologies. Charging state business offices with clearing away red tape for new market entrants, while using convening powers to bring companies together with both public and private capital, is a powerful way forward.
- Normalizing ZEVs through visible MDV and HDV deployment. Expanding the number and diversity of zero-emission medium- and heavy- duty vehicles (MDVs and HDVs) on the road itself is a powerful adoption strategy. When the public regularly sees and interacts with ZEVs, they shift from being perceived as niche or experimental to practical, proven solutions. State leaders can drive this shift by prioritizing ZEV deployment in public, municipal, and contracted fleets like school buses, transit buses, garbage trucks, and last-mile delivery vehicles.
- Supporting secondary infrastructure. States have multiple tools to drive the charging infrastructure build-out. Continued federal funding, unlocked in part by state litigation, can be deployed along key corridors – but broader efforts by the states can accelerate infrastructure independent of federal support. Importantly, federal dollars remain available through NEVI, the Low- or No- Emission Vehicle (Lo-No Program), EPA’s Clean School Bus Program, and other initiatives, and states should move quickly to deploy these funds. Beyond direct funding, states can use their convening authority to coordinate construction and investment (or apply for investments) along key corridors, amending building codes to ensure chargers can be quickly added (especially to apartment buildings), easing permitting approval processes, and providing maps to transportation agencies and the public on locations of existing high-power electricity capacity for use in siting EV charging stations. States also have significant opportunities to design vehicle-to-grid electricity rate programs that leverage the benefits of charging to lower overall electricity rates and to store energy for when it is needed, providing major savings to both drivers and to the general public.
On the system side, transportation ingenuity could look like:
- Using transportation infrastructure to support goals in other sectors. With 48,000 miles of interstate highways and 140,000 miles of freight railroads, the United States has a vast network of transportation rights-of-way (ROWs) that can be leveraged for new infrastructure – such as high-speed EV charging infrastructure and long-distance electrical transmission – without the need for costly land acquisition or major structural change. States including New York and Wisconsin have already constructed several hundred miles of co-located transmission lines along highway/interstate corridors. Not far behind, states like Minnesota have conducted feasibility studies and are currently in the process of removing barriers to transmission construction in its publicly owned ROWs.
- Employing effective land use strategies. States have significant authority to dedicate both state and federal funds towards transportation, which can include bringing additional housing and transit to suburban areas. There is also a major opportunity to avoid ineffective investments in major new highway capacity, which almost always increases traffic congestion and is rarely the highest and best use of urban land.
- Using transportation funds to expand public revenue and public choice. Providing transportation choices – from transit to biking to safe sidewalks for kids – raises property values and quality of life. States can build these design principles into their transportation funding and planning processes. States can also go further by shifting funding to narrow or remove excess roadway capacity, or by swapping costly underused infrastructure for new housing and improved urban fabric (and hence greater public tax revenue that can then again be reinvested in communities). These financing models were once used to support excess highway construction, but now can be used to invest in transportation solutions that also address housing needs and budget crunches. Leaders at all levels can also expand eligibility for micromobility (e.g., walking, biking, and scooters) in federal transit grant programs.
- Improving planning processes. Transportation accounts for a large chunk of most state budgets. Conducting a close review of the existing project pipeline for state-funded transportation, in order to identify and prioritize projects that genuinely expand mobility choices and connect to broader regional and urban development goals, is therefore in state fiscal interests – and can have the happy consequence of also improving air quality and quality of life. Indeed, the California Air Resources Board has determined that the climate impacts of reducing car dependency are on the same scale as its world-leading vehicle electrification rules; meanwhile Minnesota and Colorado have both initiated audits to prioritize funding to reduce car dependency, with good early results. Because these alternate projects are generally much less expensive than major road construction projects, and more likely to raise overall property values, they are an exceptionally good approach for public officials looking to make climate progress.
Building Affordable, Abundant Housing
Housing shouldn’t be a luxury: it’s a prerequisite for a stable, healthy life. Yet Americans – facing prohibitively high (and increasing) rental costs as well as unrealistic down payments and pathways to ownership – are struggling to meet this basic need. And with extreme weather on the rise, renters and owners alike are facing concerns about physical safety and skyrocketing insurance as well as price hurdles. The emissions that the housing sector produces only worsen these problems.
Delivering more affordable, resilient, and climate-friendly housing means making it easier to build housing of all shapes and sizes; tailoring solutions to rural communities, urban communities, and different geographies generally; and striking a better balance between development for housing and development for other purposes. These strategies need to be paired with deep investments in government capacity to facilitate permitting and approval of new housing construction, as well as to facilitate more complex projects – like retrofits, infill development, and office-to-residential conversion – at scale. Also critical is reimagining community and stakeholder engagement on housing questions, aiming to maintain trust, democratic process, and local buy-in without overvaluing the perspectives of existing homeowners, developers, or any other particular constituency. at the expense of the rest of the community.
Housing ingenuity could look like:
- Reforming zoning to support more flexible and mixed-use buildings. Zoning makes sense when it stops a refinery from being built next to a playground. Zoning is a problem when it overprioritizes one kind of development, artificially limiting construction of diverse housing types. Policymakers can prioritize zoning and land use reforms to increase housing supply for a range of budgets and families. Policymakers have been working on creative zoning fixes for years: Houston led the way in reducing minimum lot sizes to encourage denser housing, while Minneapolis got rid of parking requirements, legalized accessory dwelling units (ADUs) to get more out of existing lots, and ended single-family zoning. These changes have helped stabilize rent prices, diversified housing mixes, and given more people an entry point into the housing market.
- Investing in infill housing. Infill developments can often be expensive, restricted by zoning, or face public opposition. Public leaders can get creative with solutions, such as by pre-identifying and providing data on infill development opportunities to help reduce costs for developers, or by reforming zoning laws to allow more flexibility in what type of development can fill in. Leaders can also facilitate retrofits and upgrades of existing buildings to convert those buildings to residential housing, which is effectively another type of infill strategy.
- Limiting incumbent interests. Large institutional investors like private equity firms can drive up rental costs and reduce housing supply when they purchase single-family homes as investment opportunities. State and federal policymakers can make these homes less appealing investments by introducing tax penalties, removing tax breaks, and encouraging firms to offload the homes they currently own over time, as proposed in recent legislation. This is a bipartisan issue: President Trump signed an executive order aiming to prevent firms from buying single-family homes outright; this directive was followed by a similar commitment by Governor Newsom.
- Streamlining permitting. Part of the housing supply issue is related to long permitting processes and high upfront development costs. The solutions are straightforward: invest in human talent and AI tools (in tandem with consistent AI governance and technical support) to clear permitting backlogs; provide limited, clear, and objective standards for rejecting permits; and create pre-approved plans to fast-track permitting of resilient, efficient homes. These actions will get homes on the market faster and cheaper, since every day a lot sits waiting for a permit increases development costs. Form-based zoning codes, for example, are designed around what the physical building form is rather than on what the building will be used for. These codes streamline review processes, but also help enable neighborhoods with good character and safe streets.
- Building safer and more resilient houses. Every year, one in ten homes in the United States are directly impacted by fires, floods, storms, and other types of extreme weather. As extreme weather increases, investments in home resilience are critical to keep people safe and long-term costs low. Policymakers can support safer and more intentional development in high-risk areas, with second-order benefits for energy access, reliability, and cost. Holistic approaches, like combined risk-reduction and pooled insurance “Housing Resilience Agencies” are the types of overhauls needed, but policymakers can also use tools like insurance premium reductions to lower the costs of roof improvements, like in Alabama. Other solutions target the community level, like using shared infrastructure and nature-based solutions to reduce risk for a group of homes.
- Simplifying building codes to allow for more flexibility and innovation. Building codes are responsible for ensuring consumer safety, but are often so complex and restrictive that they can drive up build times and increase construction costs. Policymakers can act to simplify codes without compromising safety by incorporating new research. Codes requiring buildings over three stories to have two staircases in the name of fire safety, for example, are more expensive and less space-efficient than single-stair buildings. Single-stair buildings that exist in much of the rest of the world are not necessarily less safe, and have cost benefits. States are starting to implement changes: Texas, Colorado, Montana, and New Hampshire all legalized single-stair buildings in some form in 2025.
- Stabilizing insurance markets. As extreme weather risks increase, home insurance providers are bumping up premiums and dropping policies for high-risk areas, leaving homeowners with few or no options for coverage. State policymakers can help keep consumers safe, limit additional costs, and improve transparency within the market. Colorado passed a law requiring providers to report on their risk assessment methods when using catastrophe risk models and to account for homeowner mitigation when setting rates. Other states, including Arkansas and Florida, expanded access to mitigation funds for homeowners.
- Supporting technologies that cut home energy costs. Housing policy offers an indirect yet effective way to bring down rising energy bills. For instance, “bring your own device” programs, such as those that have been deployed in Arizona and Vermont, enables homeowners to participate in virtual power plants using solar, batteries, and potentially energy-storing equipment like water heaters. States like Vermont have established on-bill financing programs for weatherization and efficiency upgrades, helping all Americans access the comfort benefits and long-term energy savings of these upgrades.
- Enabling more choices for homeowners. As families change, so do their housing needs. But there are often financial barriers to moving. Policymakers can design policies that allow for flexibility in different stages of life, like tax reforms to lower the barriers for moving into smaller homes. States can also offer tax credits for developers to build more accessible housing that’s more attractive to older homeowners, or implement policies (as in California) that allow older homeowners to maintain their property tax rate if they move into a similarly priced home. Giving people the capacity to live in places and housing types that fit their needs can reduce emissions from extended commutes and overbuilt homes.
- Lowering construction costs to increase supply. High development costs make it difficult to meet housing supply needs quickly. Modular housing, made up of standardized and interchangeable parts and assembled on site, can significantly reduce build times and construction costs – and those savings can ensure housing prices that work for more Americans. Modular homes can often be lower-emission and more energy efficient than traditional homes. Policymakers can direct funds specifically towards modular housing, or reform building codes to make it easier for modular housing to qualify (unlike manufactured housing, modular housing has to adhere to state and local building codes).
Making Solutions Stick: The Cross-Cutting Benefits of Government Capacity, Pro-Democracy Design, and Innovative Financing
Each of the policy solutions above offers a way to boost climate progress while delivering everyday benefits across energy, transportation, and/or housing. But how do we make those solutions stick? With trust in government at historic lows, public-sector leaders must quickly follow ambition with action, investing in both ideas and the building blocks that turn ideas into reality. Below, we outline how public leaders can use three of these core building blocks – government capacity, financing, and pro-democracy design – to get on the scoreboard early…and stay there for the long term.
Government Capacity
Government capacity refers to the ability of government to get things done, whether through efficient processes, effective talent, or fit-for-purpose tools. Americans are frustrated by the slow pace of government, but they don’t want the functions that keep them safe and supported dismantled: they want them improved. Accomplishing this requires more than new programs or new funding streams or new inventions. It requires leaders to seriously (and systematically – not via a “wrecking ball” approach) consider which government functions are working, which need to be overhauled, and which should be retired.
Rebuilding government capacity is inseparable from strengthening democracy itself. Both of these goals are wholly intertwined with climate progress. When government acts competently, transparently, and in partnership across levels, it restores public faith that collective action is possible and worthwhile. When it can’t, even well-designed policies stall under the weight of fragmented authority, procedural burden, risk aversion, and institutional inertia. Treating government capacity as a core investment is therefore much more than administrative housekeeping. It’s a prerequisite for durable climate progress.
To boost government capacity, public leaders can:
- Align on policy outcomes, owners, and indicators. Governments should establish collective, ambitious, and executable goals, not just agency outputs; clear and cross-cutting responsibility, not siloed authority, and collective signals that show when things are getting off track or are moving to success. These shouldn’t be one-off reporting exercises, but valued north stars with relentless attention. And to enable shared outcomes, owners, and indicators, public sector leaders need to consider the full “map” of the climate-oriented transition they are aiming for: how the various puzzle pieces of planning, utilities, transit, infrastructure and more will sequence logically and in resourcing; how tactical actions that are possible now intersect with ambitious long-term planning; how to mitigate barriers in advance of key inflection points; and how to storytell what may be a long transition to residents.
- Shore up linchpin talent. Government delivery often fails at the human bottleneck. No program, however brilliant, will work if it’s not adequately staffed with the people needed to run it. Emphasis on talent growth, talent sharing, and talent strategy can be game-changing for governments if undertaken at the front end, such as:
- Empowering “machinery” expertise. Functional roles like procurement officers, finance specialists, engineers, and lawyers, are the engines of the government capacity needed to drive climate action. Instead of treating people in these roles as workhorses, jurisdictions can treat them as strategic enablers, giving them time, authority, and political cover to redesign how work gets done.
- Sourcing technical talent creatively. Leaders can think outside the box when it comes to talent for high-impact roles and roles that involve specialized, high-demand technical expertise. For instance, leaders can establish shared services and shared delivery teams that enable individuals to contribute across internal departments, or regional implementation offices that support multiple jurisdictions at once. Leaders can also explore pathways to bring in fellows and detailees from external organizations for short-term tours of service.
- Upskilling current workforces. With significant evolutions in technology, funding, and collaboration coming every year, public sector entities can’t pursue new hires every time something new emerges. Investing space, patience, and resources into upskilling current workers and setting a culture where collaborative learning is the norm will pay off far more than relying on expensive consultants.
- Investing in delivery and relational capacity. Understanding local context is a technical skill like any other, and when regional partners trust each other, decisions accelerate. Federal leaders can build regional roles and teams, and invest in intergovernmental capacity for working with states and localities on implementation, not just convening.
- Establish “safe-to-experiment” parameters and expectations. Creating safe-to-experiment space is less about changing statutes and more about leadership setting expectations and guardrails, as well as working collaboratively to shift from risk minimization to risk management. Leaders can consider:
- Testing regulatory sandboxes. A regulatory sandbox is a mechanism that provides a structured environment for testing new technologies and business approaches under modified rules to increase the speed of adoption. The goal of sandboxes is to test, learn, and collect data, not strive for immediate perfection. Once an approach is proven promising, pilots can be set up to be scaled rapidly. In 2023, for instance, the Connecticut Public Utilities Commission established a regulatory sandbox called the Innovative Energy Solutions (IES) Program to pilot innovative technologies to expand its electric grid.
- Collaborating on pathways to scaling. Before beginning an experiment, those involved should collaborate to create milestones and criteria for discontinuing unsuccessful experiments, as well as a clear transition and ownership path for working experiments to get to the next level.
- Using proactive messaging. Leaders should be clear with public sector workforce, media, advocacy, and oversight communities when the objective of a policy experiment is to learn. Such messaging should also emphasize that while successes are valuable outcomes, so too are well-understood setbacks.
- Use collective-action tools. Ambitious policy decisions are often inaccessible for cities, states, and even federal agencies acting alone because of limited capacity, procurement constraints, and fear of litigation from incumbent interests. Collective-action tools let local and state governments pool risk and resources, smoothing out the cost and bumpiness of transitions while helping governments deliver more together, including:
- Coordinated and reinforcing public funding instruments: Government institutions have a range of market shaping tools available to them to facilitate climate innovations, whether demand side (procurement, advanced market commitments) or supply side (grantmaking, loan guarantees). In a resource-limited environment, public sector organizations can work together to share insights and risk, to balance across the stages of innovation they want to drive to (higher risky experiments? near term performance criteria? sustainable supply?), and align the timeline and ROI of their policy levers in order to shape access to the capabilities they need. That might include:
- Pooled procurement. Joint Powers Authorities are agreements or entities created between multiple public-sector organizations to collectively deliver services or exercise authorities. JPAs or lead entity models can aggregate buying power for emerging tech and new clean energy capabilities. JPAs in California have been used to aggregate procurement for clean energy, insurance, and shared services. Standardizing technical specifications for transit procurements across transit districts can similarly help drive down transit costs.
- Build a shared information base: Rebuild the environmental data backbone at the state/local level, including working to preserve and sustain current environmental resources; over time, expand interoperable data collection and make it genuinely usable to support consistent, evidence based state and local action.
- Pooled legal funds. Public sector entities can establish or engage with agile pooled legal funds addressing legal and regulatory barriers that block climate innovations and getting access to specialized regulatory and litigation expertise that would be cost-prohibitive to maintain in-house.
- Reciprocity. States and municipalities can invest in shared permitting, licensing or certification schemes in areas enabling climate action. If a green tech design or contractor is authorized in one jurisdiction, reciprocity would ensure that their eligibility extends to others, helping enable a common market and reducing the burden needed to obtain duplicative certifications.
- Coordination across technical assistance resources. Many TA resources for state and local implementers exist for the multiple phases of clean energy projects. But they tend to be siloed, and few usable maps exist for resource and time-strapped state and local entities to take advantage of.
- Coordinated and reinforcing public funding instruments: Government institutions have a range of market shaping tools available to them to facilitate climate innovations, whether demand side (procurement, advanced market commitments) or supply side (grantmaking, loan guarantees). In a resource-limited environment, public sector organizations can work together to share insights and risk, to balance across the stages of innovation they want to drive to (higher risky experiments? near term performance criteria? sustainable supply?), and align the timeline and ROI of their policy levers in order to shape access to the capabilities they need. That might include:
- Design processes and feedback loops for outcomes, not box-checking. There’s significant value in government consistency and legibility in decision-making, but maximal interpretation of rules for rules sake serves no one. Government agencies should make a regular practice of assessing frustrating process flows for accumulated “kludge,” duplication, and poor user experience (grantmaking and permitting are obvious targets). At the same time, agencies should upgrade how performance measures serve as feedback loops throughout complex processes: are metrics telling you what you need to know about performance when you need it to take action, or months after the fact?
- Design for (sustainable) decisions. Government processes are often over-engineered, lacking clear guidelines for who is ultimately in charge of making a decision. To speed up permitting, deployment, rulemaking, and community engagement, governments should:
- Clarify authority. Speed requires empowering specific decision-makers with cover to say yes, authority to change course, and will to stop a failing experiment.
- Enable collaboration, not duplication. A well designed cross-functional team breaks down silos and acts with fluidity, agility, and overcommunicating focus–not doubling up meetings or reporting, not relying on standalone dashboards, and overcommunicating. Teams can be oriented around common outcome goals rather than teams grouped by administrative departments.
- Build transition resilience. Invest in transition planning across administrations for key initiatives – especially when there are shifts in political ideology.
- Deliver excellent frontline services. Particularly at the state and local level, the front lines of climate action are in day-to-day public services that can get slowed by burdensome processes. Agencies can apply journey-mapping techniques, already used in benefits delivery and permitting reform, to climate-facing services like interconnection approvals or home retrofit permits. Such techniques identify slow-downs and places where residents drop out from frustration.
- Engage the private sector as a partner and source of capacity. Governments can harness external capacity (without giving up oversight) by shifting how responsibility is allocated while remaining clear on outcomes, enforcement, and accountability. Examples of this sort of approach might include adopting self-certification options when strong third-party verification is feasible; using market discipline to reinforce public outcomes, engaging insurers, reinsurers, and lenders to incent safer construction, resilient infrastructure, and better operational practices; or leveraging credible existing private standards instead of reinventing compliance regimes.
Finance
Capital is a powerful tool for policymakers and others working in the public interest to shape the forward course of the economy in a fair and effective way. Very often, the capital needed to achieve major societal goals comes from a blend of sources; this is certainly true with respect to climate action and facilitating the transition to clean technologies.
States, cities, banks, community-driven financial institutions (CDFIs), impact investors, and philanthropies have long worked in partnership with the federal government on clean-technology projects – and are stepping up in a new way now that federal support for such projects has been scaled back. These entities are developing bond-backed financing, joint procurement schemes, and revolving loan funds – not just to fill gaps, but to reimagine what the clean technology economy can look like.
In the near term, opportunities for subnational investments are ripe because the now partially paused boom in potential firms and projects generated by recent U.S. industrial policy has generated a rich set of already underwritten, due-diligenced projects for re-investment. In the longer term, the success of redesigned regulatory approaches will almost certainly depend on creating profitable firms that can carry forward the clean-technology transition. Public sector leaders can assume an entrepreneurial role in ensuring these new entities, to the degree they benefit from public support, advance the public interest: connecting economic growth to shared prosperity.
To be sure, subnational actors generally cannot fund at the scale of the federal government. But they can have a truly catalytic impact on financing availability and capital flows nevertheless.
To boost finance, public leaders can:
- Combine financing and procurement policy. As electrification reaches individual communities and smaller businesses, many face capital-access problems. Subnational actors should consider packaging similar businesses together to provide financing for multiple projects at once. Leaders can also consider complementary public procurement policies to pull forward market demand for projects and products. For instance, grant programs can preference applications that utilize joint procurement, thereby helping public grant dollars go further. This strategy was previously employed in the Federal Transit Agency’s Low or No Emission Grant Program for clean buses.
- Blend public and private capacities. Dollars go further and the funding landscape is easier to navigate when public and private funders work together. Public and private entities can join forces around flexible finance mechanisms (e.g., bond-backed financing, rapid permitting pilot zones, and revolving loan funds) needed to push projects “over the finish line”, particularly in high-demand power markets. One compelling example is the Connecticut Green Bank, which has successfully blended public and private capital to deploy over $2 billion in clean energy investments since its founding. States can similarly support programs like the Municipal Infrastructure Fund (MIF), facilitated by ICLEI USA and the Coalition for Green Capital (CGC), to provide seed grants to local communities for market building and development of clean energy project pipelines. Groups like CGC also develop loan products specifically targeted at municipal energy infrastructure projects that can help cities access larger investment tools.
- Provide project certainty. Uncertainty around federal policy and the likelihood of project completion is constraining available finance as well as increasing costs for both project developers and involved counterparties (e.g., those helping finance a project by purchasing its tax credits). Though the public sector has a key role to play in reducing uncertainty, an emerging strategy for living with uncertainty is the formation of “coalitions of the credible”: i.e., “governments, industrial firms, and financiers who are capable of showing sustained, coordinated commitment to building clean energy systems despite global [and national] discord.” State and local leaders can help kick-start these coalitions.
- Help smaller developers and investors access needed components. Despite optimistic growth prospects, shrinking profit margins and tighter financing conditions in the near term are making it harder for smaller and less liquid developers and community financial institutions to remain solvent. Industry concentration could lead to less innovation and higher prices in the long term. State energy financing institutions can create warehouses to buy key clean-technology components in bulk and then resell these components to smaller developers and investors. As the Center for Public Enterprise observes, “these cooperative purchasing structures are already how some states in the Northeast procure heating oil and fuels, and how Climate United intended to mobilize investment into electric trucks for independent drivers working at the Port of Long Beach.”
- Leverage the power of information. Deep, shared, information architectures and clarity on policy goals are key for institutional investors and patient capital. Shared information on costs, barriers, and rates of return would substantially help facilitate the clean technology transition. Simple RFIs targeted at businesses and developers can function as dual-purpose information-gathering and outreach tools for these investors. By asking basic questions through these RFIs (which can be as short as a page!), investors can build the knowledge base for shaping their clean technology and energy plans while simultaneously drawing more potential participants into their investment networks.
- Tapping into new markets. As demand for electricity increases, new markets and business models are opening in the clean economy. General Motors and Redwood Materials, for instance, joined forces to use surplus and used EV batteries to help power data centers and other hyperscalers. There is a surprising but potent opportunity to market and finance clean energy and grid upgrades as a national security imperative, in response to the growing threat of foreign cyberattacks that are exploiting “seams” in fragile legacy energy systems. And as climate-linked disasters grow, so has the market for adaptation and resilience solutions, including many that reduce emissions as a co-benefit. Public leaders can work with the private sector to identify and support these types of innovative strategies, including by working with existing economic development agencies, chambers of commerce, accelerators, and other components in the innovation ecosystem.
- Keep eyes on the long-term prize. Investing with a short-term mindset can hobble state economic strategy before it gets started; moreover, many clean technology projects may have higher upfront costs balanced by long-term savings. States can set themselves up for long-term gains by:
- Helping firms stand on their own. States should design incentive programs with an eye for long-term business growth. States can focus, for instance, on incentives that intentionally partner well with other financing tools, thereby attracting new industries and market players to make durable investments. State strategies outlining multi-year economic plans (such as the one that New Mexico has published) can help businesses develop workable investment and growth strategies.
- Taking active equity stakes. Debt equity, provided through revolving loan funds, can play a large role in accelerating deployment of clean technologies by buying down entry costs and paying back the public investor over time. Moreover, the superior bond ratings of state institutions substantially reduce borrowing costs; sharing these benefits is an important role for public finance. State financial institutions can explore taking equity stakes in some projects they fund that provide substantial public benefits (e.g., mega-charging stations, large-scale battery storage, etc.) and securing an attractive long-term rate of return over time in exchange for buying down upfront risk.
- Adopting portfolio approaches. Diversified subnational institutions can use cash flows from higher-return portions of their portfolios to de-risk lower-return or higher-risk projects that are ultimately in the public interest. States with operating carbon market programs can consider expanding their funding abilities by bonding against some portion of carbon market revenues, converting immediate returns to long-term collateral for the green economy.
Public Participation
Public participation in climate action is often treated as a procedural requirement to be satisfied late in the process, rather than as a core function of governing well. The result is familiar: performative town halls, notice-and-comment processes that invite frustration rather than insight, and transparency tools that are easily weaponized by organized interests. This dynamic erodes trust, slows projects, and fuels the perception that government is both unresponsive and incapable. Yet participation, when designed well and tailored to the moment, is not an obstacle to effective governance: it is how government discovers what will work, where friction will arise, and how to build solutions that communities will defend rather than resist. Treating participation as a functional component of state capacity means seeing it as an input to smarter design, faster implementation, and more durable outcomes.
Upgrading how government listens and engages is vital to upgrading how government delivers. When residents see clearly how their input shapes decisions, participation builds legitimacy and reduces the incentives for obstruction and litigation later in the process. When agencies invest in the infrastructure, tools, roles, and expectations that make participation meaningful, they create a feedback loop that improves policy design and strengthens democratic trust at the same time. And when climate leaders meet the public where they are in terms of how they experience and make consumer choices in the the climate transition, we can strengthen the connective tissue between government action and public trust.The recommendations below are aimed at helping public leaders move beyond compliance-driven engagement toward participation models that are relational, deliberative, and integrated into the machinery of experience and delivery. This approach ensures that climate solutions are not only technically sound, but socially resilient and democratically grounded. These take time, but we encourage recognition that they enable enormous time, risk and failure saved.
To boost public participation, public leaders can:
- Invest in government participation capacity: Engagement fails when it is treated as a public-affairs sideline. To be effective, it must be integrated into the agency’s internal machinery and the community’s external ability to show up. There is no one size fits all toolkit for engagement, and the scope of the topic defines the method, energy, and limits.
- Know the stakeholders: Leaders should have the expectation that program leads know the full set of impacted (near term and long term) stakeholders in their policy area and have early and iterative engagement with them. Likewise, leaders should know, cultivate, and rely on trusted messengers in key communities.
- Have a plan for engagement: Define the purpose, scope, and timeline of participation at the outset of an intervention or change, including how it does and does not shape decisions. When residents see a clear path for their influence and co-design (and staff see it as a core function) it’s easier to become vested stakeholders in a project’s success.
- Participation training and roles for staff: Community engagement, facilitation, listening, and conflict transformation are technical skills that agencies can invest in across the span of a project team, in addition to relational roles.
- Recognize the full range of impacts: Every policy has near and long term winners and losers, and these voices may be unintentionally elevated or muted in design. Leaders should incentivize their staff to recognize and validate that full set of impacts, bring in communities early to understand parameters and co-design solutions, be clear about intentions to weigh or mitigate, and be direct about decision ownership.
- Leadership cover: Leadership needs to set the expectation that surfacing weak signals of concern early is a success, not a failure. Providing political cover for staff to iterate based on early feedback prevents catastrophic delays later in the cycle, as does enabling staff to move to the next phase with informed decisions.
- Feedback loop accountability: Proactively message to the public how community input changes project design or outcomes. People stop engaging when they feel unheard and demonstrating that participation matters build investment in long term success (even if not wholly in line with their feedback).
- Upgrade listening tools: Traditional feedback mechanism (like notice-and-comment) are often overengineered for compliance and late stage. Government agencies should prioritize investing in their listening plumbing.
- Experiment with deliberative models: Move beyond one-way listening sessions toward deliberative democracy models, which have some great pilots in California. These allow residents to grapple with real-world trade-offs (e.g., local land use vs. regional grid stability) alongside experts, leading to more durable mandates that are less vulnerable to litigation.
- Listening at scale tools: Investigate and invest in tools and methods that make taking the pulse of a broad or targeted community possible. Find opportunities where the people are (Reddit? Community Centers? ) rather than expecting them to navigate a govt.exe portal. Utilize tools that lower barriers to entry and analysis, like SMS-based surveys, AI-assisted triage for public comments, and digital town halls.
- User experience toolkits: Agencies should invest in user experience tools to understand how a particular proposal, innovation, or ecosystem works and feels from an immersive resident standpoint. Small tweaks may be barriers that prevent adoption.
- Invest in how people experience and adopt the solutions government is trying to deploy. The clean-energy transition is not implemented solely through permits and public meetings: It is implemented through millions of household decisions about heating systems, vehicles, appliances, and power sources. Too much of the climate movement’s engagement strategy still treats Americans primarily as political constituents to persuade. People are far more likely to embrace clean-energy solutions when they see how those choices improve their daily lives. To strengthen consumer-centered climate engagement, public leaders can:
- Broaden from policy messaging to benefit messaging: Frame clean-energy programs around concrete improvements people care about (like comfort, savings, reliability, and service quality) rather than abstract climate goals or technical policy descriptions.
- Invest in understanding residents as consumers: Use market research, behavioral insights, and segmentation to understand what different communities value, what barriers they face, and what motivates action.
- Elevate trusted messengers: Partner with the people residents already rely on for advice about their homes and services (like neighbors, contractors, utilities, tradespeople, and community organizations) rather than relying solely on government spokespeople.
- Meet people where decisions happen: Integrate or encourage outreach into the places and moments where people make choices: point-of-sale materials, contractor visits, utility communications, home-improvement stores, and neighborhood groups.
- Use social modeling and peer effects: Highlight visible examples of adoption within communities and create opportunities for residents to learn from one another through open houses, neighborhood pilots, and group demonstrations.
- Remove friction through group and guided programs: Support group purchasing models, concierge-style assistance, and personalized coaching that simplify complex decisions and reduce perceived risk.
- Align infrastructure investments with visible benefits: Use the reality of extreme weather and infrastructure upgrades as opportunities to demonstrate how clean-energy improvements strengthen local resilience and service reliability.
- Build the infrastructure for community trust. Effective engagement is not a one-off transaction, it is a relational investment. Because governments often lack the time and personnel for deep localized work, they must build the connective tissue between agencies and the ground, and several models exist to work from:
- Community navigator hubs: To make existing capacity go further, governments can work with civil society and community organizations to leverage non-governmental talent through initiatives like community navigator programs, that use local and state-level expertise to guide policy design and implementation and combine it with government technical assistance – in the process creating public buy-in and trust of a policy. It’s worth it to set up these programs in advance, as it can reduce opposition later on and help design future policies that are better suited for the communities they’re for.
- Community capacity support for participation: Recognize that participation has a cost. While some agencies are able to support compensation models for community participants for their time, there are other ways to reduce the burden of participation, whether scheduling flexibly, providing childcare or transport, offering translation, or simply using plain language rather than technical jargon.
- Implementer partnerships: Work on lowering barriers between the public and program implementers in the private sector, bringing them together early to align on community benefits agreements early.
About The Primer
Ambition to Action was authored by Angela Barranco, Zoë Brouns, Megan Husted, Kristi Kimball, Arjun Krishnaswami, Hannah Safford, Loren Schulman, Craig Segall, and Addy Smith.
Many individuals contributed ideas and input to this primer. The authors are grateful to the following individuals and organizations for their time, expertise, and constructive feedback: Patrick Bigger, Laurel Blatchford, Heather Clark, Ted Fertik, Danielle Gagne, Kate Gordon, Betony Jones, Nuin-Tara Key, Alex McDonough, Sara Meyers, Shara Mohtadi, Saharnaz Mirzazad, Beth Osborne, Alexis Pelosi, Sam Ricketts, Bridget Sanderson, Lotte Schlegel, Igor Tregub, Louise White, and Clinton Britt. The content of this primer does not necessarily reflect the views of individuals or organizations acknowledged. Any errors are the sole fault of the authors.
A National AI Laboratory to Support the Administration’s AI Agenda at the Department of Commerce
The United States faces intensifying international competition in Artificial Intelligence (AI). The Trump administration’s AI Action Plan places the Department of Commerce at the center of its agenda to strengthen international standards-setting, protect intellectual property, enforce export controls, and ensure the reliability of advanced AI systems. Yet no existing federal institution combines the flexibility, scale, and technical depth needed to fully support these functions.
To deliver on this agenda, Commerce should expand their AI capability by sponsoring a new Federally Funded Research and Development Center (FFRDC), the National AI Laboratory (NAIL). NAIL would:
- Advance the science of AI,
- Ensure that the United States leads in international AI standards and promotes the trusted adoption of U.S. AI products abroad,
- Identify and mitigate AI security risks,
- Protect U.S. technologies through effective export controls.
While the National Institute of Standards and Technology’s (NIST’s) Center for AI Standards and Innovation (CAISI) within Commerce provides a base of expertise to advance these goals, a dedicated FFRDC offers Commerce the scale, flexibility, and talent recruitment necessary to deliver on this broader commercial and strategic agenda. Together with complementary efforts to strengthen CAISI and expand public-private partnerships, NAIL would serve as the backbone of a more capable AI ecosystem within Commerce. By aligning with Commerce’s broader mission, NAIL will give the Administration a powerful tool to advance exports, protect American leadership, and counter foreign competition.
Challenge
AI’s breakneck pace is having a real-world impact. The Trump administration has made clear that widespread adoption of AI, backed by strong export promotion and international standards leadership, is essential for maintaining America’s position as the world’s technology leader. The Department of Commerce sits at the center of this agenda: advancing AI trade, developing international standards, advancing the science of AI, promoting exports, and ensuring effective export controls on critical technology.
Even as companies and countries race to adopt AI, the U.S. lacks the capacity to fully characterize the behavior and risks of AI systems and ensure leadership across the AI stack. This gap has direct consequences for Commerce’s core missions. First, advances in the science of AI are necessary to ensure that AI systems are sufficiently robust and well understood to be widely adopted at home and abroad. Second, without trusted methods for evaluating AI, the U.S. cannot credibly lead the development of international standards, an area where allies are seeking American leadership and where adversaries are pushing their own approaches. Third, this deep understanding of AI models is needed to identify and mitigate security concerns present in both foreign and domestic models. Fourth, deep technical expertise within the federal government is required to properly create and enforce export controls, ensuring that sensitive AI technologies and underlying hardware are not misused abroad. A deep bench of subject matter experts in AI models and infrastructure is increasingly critical to these efforts.
As AI systems become more capable, the lack of predictable and understandable behavior risks further eroding public trust in AI and inhibiting beneficial AI adoption. Jailbreaking attacks, in which carefully crafted prompts get around Large Language Model (LLM) guardrails, can produce unexpected behavior of models. For example, jailbreaking can prime LLMs for use in cyberattacks, which can cause significant economic harms, or cause them to leak personal information, or produce toxic content, causing legal liability and reputational harm to companies using these models. As companies deploy custom models built on top of LLMs they need to know that medical assistants will not produce harmful recommendations, or that agentic AI systems will not misspend personal funds. Addressing these concerns is an extremely challenging technical problem that requires more effective and consistent methods of evaluating and predicting model performance.
The ability to effectively characterize these models is central to the Trump administration’s AI Action Plan, which highlights widespread adoption of AI as a major policy priority, while also recognizing that the government has a key role to play in managing emerging national security threats. The AI Action Plan gives Commerce a central role in addressing these concerns; nearly two fifths of the plan’s recommendations involve Commerce. Commerce’s responsibilities include:
- Creating methods of AI model evaluation and developing international standards.
- Identifying security risks.
- Promoting research on AI interpretability, control and robustness.
- Recruiting leading AI researchers.
- Promoting exports of AI technology.
For a full list of AI Action Plan recommendations involving Commerce, see Appendix A.
While Commerce has an impressive track record in AI, including through its work at the National Institute of Standards and Technology and CAISI, it will face immense institutional challenges in delivering on the ambitions of the AI Action Plan, which require broad and deep expertise. Like other U.S. government entities, Commerce operates under federal hiring rules that make it difficult to quickly recruit and retain top technical talent. The government also struggles to match AI industry pay scales. For example, fresh PhDs joining AI companies frequently receive total compensation that is twice the cap set for the overwhelming majority of government workers, and senior researchers earn five times this cap or more. In some cases, top researchers may also hold equity in private companies, further complicating their employment by the government. Without a new institutional mechanism designed to attract and deploy world-class expertise, Commerce will struggle to execute on the ambitious goals of the AI Action Plan.
Opportunity
To deliver on the scope of the AI Action Plan, the Department of Commerce needs a dedicated institution with the resources, flexibility, and talent pipeline that existing structures cannot provide. A Federally Funded Research and Development Center (FFRDC) offers this capacity. Unlike traditional government offices, an FFRDC can recruit competitively from the same pools as industry, while remaining mission-driven and independent of commercial interests.
At its core, a new FFRDC, the National AI Laboratory (NAIL), would provide the technical expertise Commerce needs to carry out its central responsibilities. Specifically, NAIL would:
- Advance the science of AI, including the measurement and evaluation of AI models.
- Develop the methods and benchmarks that underpin international standards and ensure U.S. companies remain the trusted source for global AI solutions.
- Identify and mitigate AI security risks, ensuring U.S. technologies are not exploited by adversaries.
- Provide the technical expertise needed to support export promotion, export controls, and international trade negotiations.
NAIL would equip Commerce with the authoritative science and engineering base it needs to advance America’s commercial and strategic AI leadership.
FFRDCs are unique in combining the flexibility of private organizations with the mission focus of federal agencies. Their long-term partnership with a sponsoring agency ensures alignment with government priorities, while their independent status allows them to provide objective analysis and rapid technical response. This hybrid structure is particularly well-suited to the fast-moving and security-relevant domain of frontier AI. More background information on FFRDCs can be found in Appendix C.
The current talent landscape underscores the value of the FFRDC model. While industry salaries are high, many senior researchers are constrained by proprietary agendas and limited opportunities to pursue foundational, publishable work. To obtain greater freedom in their research, many top industry researchers have been seeking positions at universities, despite drastically lower salaries. An FFRDC focused on frontier model understanding, interpretability, and security offers a rare combination: freedom to pursue scientifically important problems, the ability to publish, and a mission anchored in national competitiveness and public service. This environment can attract researchers who would not join the civil service but are motivated by high-impact scientific and policy goals.
FFRDCs have repeatedly demonstrated their ability to deliver large-scale technical capability for federal sponsors. For example, NASA’s Jet Propulsion Laboratory has successfully built and landed multiple rovers on Mars, among many other achievements. The Departments of Energy and Defense have led much of the U.S.’ efforts in science and technology assisted by more than two dozen FFRDCs. Their track record shows that FFRDCs are uniquely suited to problems where neither academia nor industry is structured to meet federal needs—exactly the situation Commerce now faces in AI. Commerce currently supports one FFRDC, the fourth smallest. As advanced AI technology grows even more central to Commerce’s mission, it makes sense to add to this capacity.
Plan of Action
Recommendation 1. Establish an FFRDC to support the AI Mission at Commerce.
Commerce should establish a new FFRDC within two years with a mission to begin important research and timely evaluations. Establishing a new FFRDC requires the sponsoring organization (Commerce in this case) to satisfy the criteria laid out in the Federal Acquisition Regulations (48 CFR 35.017-2) for creating a new FFRDC. Key requirements involve demonstrating needs that are not met by existing sources and that Commerce has sufficient expertise to evaluate the FFRDC. It will require consistent government support through appropriations, and Commerce must identify an appropriate organization to manage it. The rapid pace of AI development makes it an urgent priority to move forward as soon as possible. Recent FFRDCs have taken about 18 months to establish after initial announcement, a significant length of time in the AI field. Further details related to establishing an FFRDC can be found in Appendix D.
Recommendation 2. NAIL should focus on topics that will advance the Administration’s AI Agenda, including recommendations given to Commerce in the AI Action Plan.
These topics should include:
- Development of a standardized federal science of measurement that enables evaluation and comparison of models. These evaluations should be predictive of their performance on real-world tasks. NIST has already laid out how measurement science can advance AI innovation in this report.
- Use of these advances in the science of AI measurement for the development of unified AI standards. This would build greater confidence in models, promoting adoption and U.S. AI exports.
- Development of comprehensive methods to assess security implications of models. This includes security concerns in foreign models and vulnerabilities, such as jailbreaks, backdoors, and leakage of sensitive data, and their susceptibility to data poisoning attacks. Of particular note are attacks that can obtain dangerous information related to topics such as biological weapons. While much of this work can be done without access to classified information, NAIL workers may need security clearances, for example, to determine whether models could leak specific secure data. NAIL should also promote AI security by advancing technical work on AI interpretability, robustness, and control, which was highlighted as a priority in the AI Action Plan.
- Determination of whether AI models or hardware provide capabilities that might warrant export controls.
The proposed FFRDC should pursue activities that range from longer term, fundamental research to rapid response to new developments. Much of the knowledge needed to fulfill Commerce’s mandate lies at the heart of the most significant research questions in AI. This requires deep research, which is also important in attracting top tier talent. On a shorter time scale, it will be important for the FFRDC to provide regular evaluations of models as they progress, including the evaluation of security concerns in foreign models. NAIL can speed up these time critical security evaluations. It will also need to use these evaluations to help create and update procurement guidelines for federal agencies and assess the state of international AI competition. Finally, the FFRDC should be a source of expertise that can support Commerce in a wide range of topics such as export control and development of a workforce trained to appropriately take advantage of AI tools.
The FFRDC will also need to work closely with industry to develop standards for the evaluation of models, and support efforts to create international standards. For example, it may seek to facilitate an industry consensus on the evaluation of new models for security concerns. NIST is well known for similar efforts in many technical areas. Finally, the FFRDC should provide a capacity for rapid response to significant AI developments, including possible urgent security concerns.
Recommendation 3. Provide a sufficient budget to cover the necessary scale of work.
There are different possible scales at which NAIL might be created. It is important to note that creating industry scale models from scratch can cost tens or hundreds of millions of dollars. However, the task of evaluating models may be undertaken without this expense by experimenting on models that have already been trained. Much of the published work on model evaluation takes this course. Such evaluations and experiments still require access to significant computational resources, requiring millions of dollars a year in compute, depending on the size of the effort. The FFRDC’s research might also include experiments in which smaller models are built from scratch at a much smaller expense than what is required to train industry sized models.
We consider two alternatives as to the size and budget of the proposed FFRDC:
- Testbed for AI Competitiveness and Knowledge (TACK): A smaller, prototype effort involving dozens of researchers and support staff, including staff that will facilitate collaborations with industry and other agencies. Such a small-scale effort will not be able to address the full range of problems that Commerce has been tasked with, but will be able to contribute to important missions and demonstrate the value of such an FFRDC on an accelerated timeline. This might cost a few tens of millions of dollars per year, on the scale of Commerce’s current National Cybersecurity FFRDC (NCF).
- Full NAIL: A larger-scale effort could address the full range of tasks outlined above. At this scale, the FFRDC could also take the lead in shaping international standards. For comparison, the Software Engineering Institute (SEI) operates as an FFRDC with a staff of roughly 700 and an annual budget of about $130 million.
The figure in Appendix B lists all current FFRDCs and their annual budget in 2023.
The budget of the FFRDC would need to cover several different costs:
- Research staff. This would consist of experienced researchers who would lead fundamental research and oversee shorter term technical work.
- Research support staff. This would include experienced developers, many with experience in data collection and cleaning, model training and evaluation.
- Administrative support.
- Policy experts skilled in interfacing with industry and other government agencies.
- Computer staff, with experience in supporting large scale computing resources.
- Computing resources, including funds to purchase GPU clusters or to obtain them through cloud services.
- Other expenses such as travel, office space, and miscellaneous overhead.
Recommendation 4. Make NAIL the Backbone of a Broader AI Ecosystem at Commerce.
While an FFRDC offers a unique combination of technical depth and recruiting flexibility, other institutional approaches could also expand Commerce’s AI expertise. One option is to expand the Center for AI Standards and Innovation (CAISI) within NIST, leveraging its standards and measurement mission, though it remains bound by federal hiring and funding rules that slow recruitment and limit pay competitiveness.
A separate proposal envisions a NIST Foundation—a congressionally authorized nonprofit akin to the CDC Foundation or the newly created Foundation for Energy Security and Innovation (FESI)—to mobilize philanthropic and private funding, convene stakeholders, and run fellowships supporting NIST’s mission. Such a foundation could strengthen public-private engagement but would not provide the sustained, large-scale technical capacity needed for Commerce’s AI responsibilities.
Taken together, these models could form a complementary ecosystem: an expanded CAISI to coordinate standards and technical policy within government as well as providing oversight over the FFRDC; a NIST Foundation to channel flexible funding and external partnerships; and an FFRDC to serve as the enduring research and engineering backbone capable of executing large-scale technical work.
Conclusion
The Trump administration has set ambitious goals for advancing U.S. leadership in artificial intelligence, with the Department of Commerce at the center of this effort. Ensuring America’s continued leadership in AI requires technical expertise that existing institutions cannot provide at scale.
NAIL, a new Federally Funded Research and Development Center (FFRDC) offers Commerce the capacity to:
- Push forward our fundamental understanding of frontier AI models along axes that are central to Commerce’s mission, including measurement and evaluation.
- Build the trusted benchmarks and standards that can become the global default.
- Rapidly respond to new technical and security challenges, ensuring the U.S. stays ahead of competitors.
- Provide authoritative analysis for export promotion and control, ensuring U.S. technologies are widely adopted abroad while protected from adversaries, and strengthening America’s hand in international negotiations and trade forums.
By sponsoring this FFRDC, Commerce can secure the talent, flexibility, and independence needed to deliver on the Administration’s commercial AI agenda. While CAISI provides the technical anchor within NIST, the FFRDC will enable Commerce to act at the necessary scale—ensuring the U.S. leads the world in AI innovation, standards, and exports.
Appendix A. References to the Department of Commerce in America’s AI Action Plan
Appendix B. FFRDC Budgets
Appendix C. Further Background on FFRDCs
FFRDCs in Practice: Successes and Pitfalls
FFRDCs have been supporting US government institutions since World War II. Overviews can be found here and here. In this appendix we briefly describe the functioning of FFRDCs and lessons that can be drawn for the current proposal.
In a paper by the Institute for Defense Analyses (IDA) a panel of experts “expressed their belief that high-quality technical expertise and a trusting relationship between laboratory leaders and their sponsor agencies were important to the success of FFRDC laboratories” and felt that “The most effective customers and sponsors set only ‘the what’ (research objectives to be met) and allow the laboratories to determine ‘the how’ (specific research projects and procedures).” Frequent personnel exchange programs between the FFRDC and its sponsor are also suggested.
This and the experience of successful FFRDCs suggests that the proposed FFRDC be closely linked to relevant ongoing efforts in NIST, especially CAISI, with frequent exchanges of information and even personnel. At the same time, the proposed FFRDC should have the freedom to explore very challenging research questions that lie at the heart of its mission.
As an example of the relationship between agencies and associated FFRDCs, the Jet Propulsion Laboratory supports many of NASA’s priorities, addressing long-term goals such as understanding how life emerged on earth, along with more immediate goals such as catalyzing economic growth and contributing to national security. Caltech manages operations of JPL. In general, NASA sets strategic goals, and JPL aligns its long-term quests with these goals. NASA may solicit proposals and JPL may compete to lead or participate in appropriate missions. JPL may also propose missions to NASA. As an example, in 2011 the National Academies recommended that NASA begin a mission to return samples from Mars. NASA decided to launch a new Mars rover mission. NASA then tasked JPL to build and manage operations of Perseverance, to accomplish this mission.
On a less positive note, after concerns about the Department of Energy’s (DOE) management of FFRDCs, DOE shifted from a “transactional model to a systems-based approach” offering greater oversight, but also leading to concerns of loss of flexibility and micromanagement. Concerns have also previously been raised about the level of transparency and assessment of alternatives when agencies renew FFRDC contracts, as well as mission creep of existing FFRDCs
Existing FFRDCs Relevant to AI Work
One of the most important criteria for establishing a new FFRDC is to demonstrate that this will fill a need that cannot be filled by existing entities. Many current FFRDCs are conducting work on AI, but this work does not adequately address the needs of Commerce, especially in light of the requirements of the AI Action Plan. For example, the Software Engineering Institute (SEI) run by CMU has deep expertise in the development of AI systems, along with software development and acquisition. However, their mission is to “execute applied research to drive systemic transition of new capabilities for the DoD.” Its AI work focuses on defense related capabilities, and not on the comprehensive evaluation of frontier models needed by NIST.
NIST does support the National Cybersecurity FFRDC (NCF) operated by MITRE. This unit focuses on security needs, not on general model evaluation (although it will be important to clearly delineate the scopes of a new Commerce FFRDC and the NCF). Other FFRDCs, such as Los Alamos or Lawrence Berkeley have significant AI efforts aimed at using AI to enhance scientific discovery. Industry AI labs address some of the questions central to the proposed FFRDC, but it is important that the government have access to deep technical expertise that is able to act in the public interest.
Establishing a New FFRDC
A precedent on the establishment of FFRDCs comes from the Department of Homeland Security (DHS). Under Section 305 of the Homeland Security Act of 2002, DHS was authorized to establish one or more FFRDCs to provide independent technical analysis and systems engineering for critical homeland security missions. In April 2004, DHS created its first FFRDC, the Homeland Security Institute. Four years later, on April 3, 2008, it issued a notice of intent to establish a successor organization, the Homeland Security Systems Engineering and Development Institute (HSSEDI), and in 2009 selected the MITRE Corporation to operate it. HSSEDI—along with DHS’s other FFRDC, the Homeland Security Operational Analysis Center—is overseen by the Department’s FFRDC Program Management Office. This case illustrates both a procedural pathway (statutory authorization, public notice, operator selection) and the typical timeline for standing up such an entity: roughly 12–18 months from notice of intent to full operation. Similarly, the National Cybersecurity FFRDC had its first notice of intent filed April 22, 2013, with the final contract to operate the FFRDC awarded to MITRE on September 24, 2014, about 17 months later.
Appendix D. Requirements for Establishing an FFRDC
Establishing a new FFRDC requires the sponsoring organization (Commerce in this case) to satisfy the criteria laid out in the Federal Acquisition Regulations (48 CFR 35.017-2) for creating a new FFRDC.
These include:
- Requirement: Existing alternative sources for satisfying agency requirements cannot effectively meet the special research or development needs.
- Meeting the Requirement: The special research or development need for improved understanding, measurement and reliability of AI models is clearly highlighted by the Trump Administration’s AI Action plan, and will only increase with more capable AI systems. As detailed in Appendix C, existing FFRDCs do not focus on problems central to Commerce’s mission, including the promotion of AI exports through model understanding and evaluation, model measurement to promote international standards, and identifying security issues central to export controls. Some work on this is done in industry and universities, but as noted, this is not comprehensive or sufficient to address Commerce’s mandate and the goals of the AI Action Plan.
- Requirement: There is sufficient Government expertise available to adequately and objectively evaluate the work to be performed by the FFRDC.
- Meeting the Requirement: CAISI would serve as a source of expertise within the government that can evaluate the work performed by the FFRDC.
- Requirement: A reasonable continuity in the level of support to the FFRDC is maintained, consistent with the agency’s need for the FFRDC and the terms of the sponsoring agreement.
- Meeting the Requirement: Satisfying this requirement may require ongoing support from Congressional appropriations committees, depending on the level of support needed.
- Requirement: The FFRDC is operated, managed, or administered by an autonomous organization or as an identifiably separate operating unit of a parent organization, and is required to operate in the public interest, free from organizational conflict of interest, and to disclose its affairs (as an FFRDC) to the primary sponsor.
- Meeting the Requirement: The DOC and NIST must identify the appropriate contractor to run the FFRDC. There are many non-profits and universities with relevant expertise, including non-profits devoted to AI measurement.
The establishment of an FFRDC must follow the notification process laid out in 48 CFR 5.205(b). The sponsoring agency must transmit at least three notices over a 90-day period to the GPE (Governmentwide point of entry) and the Federal Register, indicating the agency’s intention to sponsor an FFRDC, and its scope and nature, requesting comments. This plan must be reviewed by the Office of Federal Procurement Policy (OFPP) within the White House Office of Management and Budget (OMB).
A sponsoring agreement (described in 48 CFR 35.017-1) must be generated by Commerce for the new FFRDC. This agreement is required by regulations (48 CFR 35.017-1(e)) to last for no more than five years, but may be renewed. It outlines conditions for awarding contracts and methods of ensuring independence and integrity of the FFRDC. FFRDCs initiate work at the request of federal entities, which would then be approved by appropriate units within DOC. The proposed FFRDC should align its mission closely with Commerce and NIST, obtaining contracts from these sponsoring agencies that will determine its priorities. The FFRDC would hire top tier researchers who can both execute this research and provide bottom-up identification of important new research topics.
The FAIR in Education Act: Federal coordination to support responsible AI deployment
Artificial Intelligence (AI) has the potential to enhance education systems by personalizing student learning, providing real-time feedback, and streamlining administrative tasks to optimize teachers’ time and focus on instruction. AI, like other classroom technologies, can expand access to educational resources and when used properly, support student engagement. However, no long-term studies on the impacts of generative AI on student learning outcomes and the cognitive abilities of early learners exist and issues around algorithm transparency and data security persist. To meet these challenges, we propose a Framework for AI Responsibility (FAIR) in Education Act, a Governor’s Conference, and the establishment of a national center to support AI deployment in K-12.
Challenge and Opportunity
No Guardrails or Guidance
Successful integration of classroom technologies relies on the availability and stability of infrastructure as well as the readiness of the end users. The United States AI Action Plan and Advancing Artificial Intelligence Education for American Youth Executive Order aim to promote streamlined pathways for AI adoption. However, neither provide any practical implementation guidance for the responsible deployment of AI in educational settings nor allocate funds to support the local infrastructure necessary. Current actions also fail to address longstanding concerns regarding data privacy, the establishment of guardrails to mitigate algorithm bias, and efforts to reduce the digital divide which are increasingly more important upon interactions with minors.
AI competency is becoming a necessary skill for the future, much like knowing how to use a search engine effectively to navigate online information. Students who understand how AI works, its limitations, and its potential biases will be better equipped to navigate the technology driven world we live in. Establishing guardrails and guidance is not meant to restrict student access to AI, but aims to ensure students can use these tools safely and responsibly. Proper guardrails, transparency, and guidance allow students to leverage AI as a learning aid while minimizing risks to privacy, fairness, and well being.
In the absence of guardrails and guidance, AI can increase inequities, introduce bias, spread misinformation, and risk data security. These negative impacts are often exacerbated in communities that are marginalized or economically disadvantaged. Simply put, the current posture towards AI puts the cart before the horse. The United States needs a better understanding of the impact of AI on student learning and clear guardrails before introducing it large-scale.
More Data Needed
Reeling from the impacts of the COVID-19 pandemic on student learning, such as learning loss and widening achievement gaps, the most recent National Assessment of Educational Progress asserts a clear decline in K-12 science, reading, and mathematics proficiencies compared to 2019. The results of the study will be used to inform educational reforms, however, educators and policymakers should be cautious in framing AI as the cure-all for America’s educational challenges. The promises of similar tech-driven advances foreshadow a likely failed result if the policy does not adapt accordingly .
Currently, there are no federal guidelines that govern AI usage in the classroom and there are no longitudinal studies on AI’s impact on student learning and cognitive development. Short-term studies have demonstrated that AI can have a positive effect on student learning, however, results are highly variable and context specific. In addition, there are significant risks, such as student overreliance on the technology, especially generative AI chatbots. Early learners are particularly at risk for negative impacts and it is unknown how AI use impacts deeper learning and information retention and synthesis. Studies indicate that technology use among school-aged children can negatively affect attention spans, self-control, cognitive development, and problem-solving skills. Moreover, AI chatbots may pose psychological impacts or “empathy gaps” in children that are not well understood. Only recently has the Federal Trade Commission launched an inquiry into the impact of AI chatbots on children. We need more data on the long-term impacts of AI in the classroom in order to develop coherent policies that support educators and learners.
These shortcomings do not imply that AI cannot have a place in the classroom. Instead it demonstrates that a comprehensive understanding of AI’s impact is necessary before its use is scaled up. Furthermore, algorithm transparency is paramount for minimizing bias, ensuring student psychological safety, and promoting data security. Organizations like TeachAI, acknowledge some of these risks and provide resources for schools and universities developing AI policy, however, there is still much to learn.
Federal Support and Coordination are Paramount
Uncertainty around the future of federal support for education and education research is also a key challenge. The Department of Education (DoEd) is currently responsible for addressing national educational issues by setting federal policy, supporting equal access to education, protecting civil rights, collecting educational data, and analyzing trends. The DoEd also works to hold institutions and States accountable for educational outcomes. The current administration, however, has a stated goal of abolishing the DoEd and sending those powers to States. While States should be empowered to support policy development and implementation, federal coordination and oversight is vital for protecting civil rights and understanding long-term national education trends.
If the DoEd is abolished, it is uncertain what government agency would assume responsibility for the development, monitoring, and evaluation of educational standards at the precipice of the AI age. If States are tasked with this responsibility, it will require sustained financial federal support. Proposed cuts to the National Science Foundation (NSF) STEM Education Directorate and other STEM education federal funders would limit the ability for education researchers to effectively assess the impact of AI on the educational and psychological development of students or develop tools for the effective use of AI.
Implementation Requires Community Involvement
While current federal initiatives are in place promoting the role of AI in education, their ultimate success depends on meaningful training experiences for educators and strong collaboration with State and local stakeholders. Federal frameworks, such as the April 2025 Advancing Artificial Intelligence Education for American Youth Executive Order (E.O. 14277), addresses the critical need to provide America’s youth with opportunities to cultivate AI competency, but it does not express the major value of having States and local districts leading the implementation effort to ensure that AI integration meets community needs, supports student achievement, and strengthens workforce development.
State and local communities could potentially draw on federal resources under this E.O. (if available) and work collaboratively with education-focused professional societies, such as the National Science Teachers Association (NSTA) and the Computer Science Teachers Association (CSTA) to help develop community-created standards, define clear metrics, and continuously evaluate what works within their specific contexts. Initiatives such as NSF’s EducateAI and the National AI Research Resource (NAIRR) offer curriculum models, research infrastructure, and other resources that can complement any locally developed approaches. These federal programs can also support collaborative networks among educators, researchers, and industry partners to share best practices and insights. However, realizing the full potential of these federal programs first requires providing teachers with professional development and training to use AI tools effectively and confidently in the classroom, because even the most advanced resources are only as impactful as the educators who apply and understand them.
Recommendations
Framework for AI Responsibility (FAIR) in Education Act
Congress should propose legislation on the responsible use of AI in education. This comprehensive act, known as the Framework for AI Responsibility in Education Act or the FAIR in Education Act, would support a large-scale study on the impact of AI on education, provide funding for education research, support State leadership in AI in education, require greater algorithm transparency for algorithms influencing minors, and provide infrastructure for ongoing monitoring and assessment of a community-centered implementation of AI technologies in the classroom. This legislation should address both K-12 use and higher education.
First, the FAIR in Education Act should instruct the National Academies of Science, Engineering and Mathematics (NASEM) to conduct a study and report on the impact of AI in K-12 schools, higher education, and informal learning settings such as libraries and museums. This landscape study should address student learning, the impact on cognitive abilities, psychological impacts, the ethical use of AI, and provide recommendations for how the federal, state, and local governments can support AI literacy and teacher education.
Next, the use of AI in the classroom raises several academic integrity and scientific integrity issues, including plagiarism, authorship and credit, accuracy, reliability of AI outputs, reproducibility, and data bias. The FAIR in Education Act should instruct the Committee on STEM Education (CoSTEM), a subcommittee of the National Science and Technology Council under Office of Science and Technology Policy (OSTP), to within 270 days of passage of the act provide guidance to assist educational institutions in thoughtfully updating their own definitions of academic integrity in light of AI and other technologies used in educational settings. This guidance would help institutions uphold ethical standards while enabling the responsible use of AI in learning and assessment.
The Act should also require transparency in how AI algorithms used in education are trained, what data was used, and how the guardrails were tested. Educators should be aware of the design decisions and development processes that engineers made for the algorithms and how those decisions might affect the use of AI as a tool to enhance student learning. Such transparency will enable educators to guide students effectively in using AI as a learning tool, particularly supporting equitable outcomes among disadvantaged communities.
The Act will direct federal funds to support the requisite infrastructure and security needed to safely use AI. There are examples from previous administrations of funding opportunities and convenings through the Federal Communications Commission (FCC) to support school district cybersecurity and the infrastructure required to support AI and high speed internet use. Additionally, the Act would support streamlined implementation of the Broadband Equity, Access, and Deployment Program to address high speed internet access across the country.
The responsible use of AI requires not only federal engagement, but State engagement as well. The FAIR in Education Act will require Federal, State, and local coordination on AI use in the classroom and facilitate continued monitoring and evaluation. The Act will also increase funding for teacher professional development, with emphasis on development and training for STEM fields. We envision these goals will be accomplished through the funding and development of a “Supporting Pedagogy and AI Readiness in K-12” (SPARK) Center, which will be informed by an inaugural country-wide Governor’s conference.
Governor’s Conference – State-Led Design of the SPARK Center
The creation of the SPARK Center should be conducted in cooperation with state and local officials, as well as parents, educators, and students. The education system in the United States is heavily dependent on state and local government to provide leadership in the implementation of new initiatives or educational practices, and thus it is essential that they are involved in the decision making. To begin incorporating these essential voices, we recommend hosting a“Governor’s Conference” with a primary focus on AI in education, and specifically the community driven design of the SPARK Center. The National Governor’s Association (NGA) Center for Best Practices has a program area focused on K-12 education and previously led a Governor’s convening on a K-12 education agenda in 2023. NGA can utilize these existing networks to drive a new focus on the use of AI in education, and preparation and design of the SPARK Center.
As of September 2025, thirty States have issued guidance on AI in Education. At the conference, Governors can share the successes and challenges of their current AI policies as they relate to education, engage in real-time conversations with teachers, students, and parents, and inspire policy action in States which may not yet have infrastructure in place to support the responsible deployment of AI in their own education systems. Attendees should include all state Governors (or their proxies, such as Secretaries of Education or people in similar positions), representatives from the American Federation of Teachers, the National Education Association, the Association of American Educators, the Superintendents Associations, possible NGOs such as the leadership from CSTA and NSTA, administrators of TeachAI, and relevant NSF funded researchers and academics conducting pedagogical studies on AI impacts on education and childhood development. In addition to representatives from state Governor offices, educators from local school districts must be an essential part of this process to garner buy-in and receive guidance from the final users.
The event organizer should consider the best way to integrate parent and student feedback into the outcomes of the conference, such as dedicating one day of the conference specifically to receive their feedback through Track 1.5 roundtables, or stakeholder prepared presentations. The goal of the conference is to create an opportunity for state governments to learn where there are insurmountable challenges in the deployment of AI in education for States to address independently, and where students could benefit from federal standardization of the U.S. approach. The outcome of the conference should lead to a deployable roadmap and fulsome design of the SPARK Center, including the accumulation of educational training resources for teachers and teachers associations. It could also lead to the percolation of new initiatives for the federal government, such as drafted federal guidelines for AI in K-12 education, a new country-wide grand challenge, or an increase in funding or resources provided to the States. It could also lead to the design of a new research and potential pilot projects conducted by the NGA’s Center for Best Practices. These are solely illustrative examples, and will ultimately be determined by the involved participants.
A community-created approach, paired with federal resources, enables a two-way exchange in which federal guidance informs local practice, while lessons learned from schools will feed back into federal research, policy, and frameworks. This partnership will ensure AI is integrated responsibly, equitably, and effectively across the education system in America.
Supporting Pedagogy and AI Readiness in K-12 (SPARK) Center
For AI to truly benefit classrooms, communities must create, establish, and embrace standards to help guide responsible AI use and effectiveness. These efforts, such as CSTA’s AI Learning Priorities, will be bolstered through the establishment of the SPARK Center per the FAIR in Education Act.
To maximize AI benefits and minimize risks, AI use in the classroom must be guided by community-created standards. Education stakeholders including students, teachers, and families need to be involved with defining how AI is used in the classroom to ensure it aligns with local values, protects student data, and supports student-centered, teacher-facilitated learning. State and local leadership, creating essential policies for these standards, is critical in order to adapt practices to local contexts and to monitor effective classroom use. What works in one district or school may not work elsewhere; standards must be flexible and informed by the community stakeholders because a one-size-fits all approach will not work in every school across America.
Effective AI use requires ongoing monitoring and evaluation. At a local level, schools should track learning outcomes, student experiences, teacher workload, and overall engagement and productivity with the technology. Feedback from students, teachers, and education stakeholders should be a part of every assessment monitoring and evaluation cycle to help improve AI adoption in the classroom. Implementing routine monitoring and evaluation cycles will enable schools to adjust AI practices, identify unintended consequences, and ensure AI is supporting the learning objectives established in the curriculum instead of creating new challenges in the classroom.
This work overall can be burdensome across teachers and school districts. If a community realizes that the deployment of AI in their educational infrastructure is not reaching anticipated goals, or potentially even causing unintended negative consequences across students, there are few places for educators to turn for answers. The SPARK Center will be designed to be a federally managed resource which manages the monitoring and evaluation capacities across the country, and compiles best practices for educators to pull from based on their analyses. Other functions of the center will be determined through a community-driven approach, and informed by a Governor’s Conference convened at the federal level.
Conclusion: Connecting Federal Support to Advance Community-Created Approaches
AI has enormous potential to enhance teaching and learning but only if its adoption is guided by communities, led locally, and continuously monitored. By combining student-centered, teacher-facilitated classroom practices with State and local guidance and federal support, schools can ensure AI empowers both educators and students while safeguarding equity, ethics, and critical thinking. Federal support should strengthen these community centered approaches, providing resources and guidance without replacing local decision making.
The views contained in this memo reflect the personal views of the authors.
Ending Rural Teacher Shortages: What Federal, State and Local Government Can Do
Rural communities face unique barriers to providing every student with a well-rounded, excellent education. Chief among them are staffing shortages: rural communities often struggle to recruit and retain qualified teachers. Recent shifts to the federal policy landscape threaten to worsen this challenge. This memo recommends action steps for federal, state and district policymakers to end rural teacher shortages.
Challenge and Opportunity
When I left my job as an elementary STEM teacher in rural North Carolina, I gave each of my students an envelope, pre-labeled with my family’s address, and told them to write me a letter with their good news. A year later, an envelope arrived from a student who wrote to tell me that he missed science class; he hadn’t had a science teacher all year. My heart sank, remembering his enthusiasm and interest in science, and knowing that a year without science class put him off track for more advanced courses later, courses he would need if he wanted to pursue a STEM major in college.
This is hardly a unique story. The Organisation for Economic Co-operation and Development (OECD) recently made headlines warning of an increasing teacher shortage crisis across the world. In the U.S., teacher shortages are a well-documented problem in certain subject areas and locations. In rural communities like the one where I taught, educator shortages are longstanding and to many, feel intractable.
What do we know about rural teacher shortages?
Rural schools serving low-income students and those serving mostly students of color have the highest rates of teacher turnover nationally–markedly higher than schools serving similar groups of students in urban and suburban areas.
A 2020 study of California school districts found that rural districts posted an additional twelve teacher vacancies for every 100 teachers compared to their urban counterparts. These rural California districts also struggled more to fill vacancies with qualified staff, hiring twice as many emergency certified educators.
And while this pattern may not be consistent across all rural communities, rural schools appear to struggle more with the impact of shortages. In the 2023-2024 school year, a national sample of rural school administrators actually reported lower rates of teacher vacancies than non-rural schools: 69% of rural schools said they were fully staffed compared to 56% of all public schools reporting. But rural schools in this same survey who experienced vacancies were more likely to report that they impacted the day-to-day experience of students and teachers.
Rural schools struggle to recruit educators, with fewer applicants and fewer qualified candidates, and fewer teacher preparation programs nearby from which to recruit teacher candidates. Teacher preferences may work against rural schools’ efforts to recruit from outside the community: national research shows that teachers are more likely to teach within fifteen miles of their hometown, and by virtue of smaller local populations, administrators have a smaller pool of candidates to draw from who fit that profile. Instead, rural schools often find themselves working against the grain of teacher preferences, recruiting from outside of rural communities.
Recruiting from outside the community presents its own share of challenges, and for these and other reasons, rural schools also struggle to retain teachers. New research studying rural teacher mobility between 1987 and 2018 found that rural teacher shortages across the country were driven much more by turnover than by other causes that are often responsible for open positions (such as retirement, or growing student enrollment). Teachers were over twice as likely to move out of rural schools and to urban or suburban schools as they were to move from urban or suburban schools to rural schools.
Non-rural schools may be able to offer some benefits and resources that rural schools cannot, but compensation may not be the main reason educators are leaving rural schools. While thirty-four percent of teachers who left rural schools did cite salary and benefits as their reason for leaving, the most significant reported causes of rural teacher turnover had to do with school culture and working conditions, particularly issues with school leadership.
Plan of Action
In the face of these challenges, rural schools have tremendous assets to draw on in building, hiring and retaining a strong teaching workforce. For local community members in small rural labor economies, teaching can be an attractive job, particularly to community members who don’t want to leave to access economic opportunity. Rural schools that have cultivated positive, close-knit relationships to their school communities can also be attractive to teachers looking for a supportive environment, and many rural schools offer the chance to live in a small, interconnected community with access to nature and affordable cost-of-living.
But rural schools can’t do it alone. In order to leverage these assets and end teacher shortages, local, state and federal leaders play a critical role. What can leaders at each level of government do to end teacher shortages? We recommend action at the district and school, state, and federal levels.
Recommendation 1. District and School-Level Actions to Attract and Retain Teaching Talent
Identify your school community’s strongest assets: what attracts teachers to teaching in your community? Use these as a starting point to inform your recruitment strategy.
Gather data to find the root causes of teacher recruitment and retention issues in your community, and design your teacher recruitment and retention strategy based on these root causes. If your state does not offer a shared teacher exit survey, districts can use their own exit surveys to gather data on teachers’ reasons for leaving, and use that data to narrow in on solutions. Alaska’s Lower Kuskokwim School District, for example, has historically struggled to recruit and retain new teachers, and wanted to know why educators were leaving. As part of a Regional Education Laboratory (or REL)-supported project, the district used exit survey data to identify substandard educator housing (which is provided by the district to educators at a subsidized rate) as a key barrier to working conditions, and has since partnered with a local vocational education program to build additional housing for educators.
A critical step in this process is gathering and monitoring data and pivoting when solutions are not having their intended impact. For example, many rural districts have turned to four-day school weeks in the hope of solving a host of challenges, including teacher shortages, budget shortages and long student commute times. But early evidence suggests that four-day school weeks are not having the intended impact on teacher recruitment and retention, and in fact, may result in additional turnover. Armed with this evidence, districts can adjust course.
Put current students’ and local community members on a path to become educators and school staff. While recruiting from outside the community may still be necessary in the short and medium term, preparing the next generation of local communities for jobs that allow them to stay in the community provides a benefit to both current and future students. Grow-Your-Own programs and high school pipeline programs into teaching jobs are a powerful potential tool. As part of regular reporting, publish data on program outcomes.
Share teachers (and services) across districts. For the hardest to staff roles and roles where student enrollment is too low to support a full-time teacher in a certain subject area, rural districts can work together in cross-district consortia to share access to courses–sometimes virtually, sometimes in person. Some districts also use this shared services model to provide professional learning to educators.
Recommendation 2. State Actions to Support Rural Teacher Recruitment and Retention
Target solutions based on demonstrated staffing shortages. Too often, states fund one-size-fits-all solutions to teacher shortages that direct limited resources too broadly, often to roles that schools don’t actually struggle to fill, or to schools that don’t have any shortage of qualified applicants. Prioritizing the highest-need areas is especially critical when working with limited resources: with a limited amount of money, a state can do more to solve teacher shortages by targeting incentives to the teacher roles where they are most needed. Both Alaska and Colorado, for example,provide incentives to teacher preparation candidates to teach in rural schools.
Fund educator pipeline programs targeted to rural communities with demonstrated shortages. States have made significant recent investments in Registered Apprenticeship, Grow Your Own, post-baccalaureate and high school pipeline programs to recruit and train new teachers. States can prioritize rural districts with demonstrated shortages to pilot and expand these programs. Ensure timely evaluation and publication of outcomes for these programs.
Fund rural schools fairly. Rural districts have lower enrollment, face higher overall costs to deliver student services, can’t reduce costs through economies of scale, and have fewer local resources in the form of local tax dollars and ability to levy local bonds. Rural districts rely more on state and federal funds for this reason, and state education funding formulas are critical to ensure rural schools have enough money to provide critical services. To ensure local schools can fund competitive salaries and support recruitment and retention initiatives, states should evaluate whether or not their current funding formulas are sufficient to meet rural schools’ needs.
States nationwide have taken this on, with Utah recently revising its school funding formula to provide rural schools up to 1.5 times the per-pupil funding rate of non-rural schools. Both Wisconsin and Massachusetts provide schools with supplemental aid specifically for rural schools; Wisconsin’s program has made a demonstrated impact on rural students’ college enrollment and completion.
Some states are committing new state money directly to educator salaries, working to close the gap between rural and non-rural districts. In 2023, Arkansas funded a statewide raise of the state’s minimum teacher salary from $36,000 to $50,000, and provided all K-12 public educators with a raise of at least $2,000. Research from the first year of implementation found that it had substantially increased funding for both rural and urban schools. Rural schools, which had provided average starting pay of $2,400 less than urban districts, cut that gap to $48 in the initiative’s first year.
Give districts the flexibility to share staff and resources. Increasingly, rural school districts are working across districts to share limited staff and resources. Forming local consortia, districts may give students the opportunity to enroll in advanced or specialized coursework across districts. States can ensure that state policy reduces barriers to this approach; Texas, for example, passed state legislation to remove barriers to this approach and support growth through a new Rural Pathway Excellence Partnership Program, which currently serves ten consortia made up of thirty rural districts. Massachusetts’ Rural School Aid Program specifically prioritizes district spending to “increase regional collaboration, consolidation, or other strategies to improve long-term operational efficiency and effectiveness.”
Provide access to virtual courses. When rural districts cannot hire enough teachers or muster enough students to provide specialized or advanced courses, states can also work creatively to provide access to these courses statewide. Montana’s legislature created the Montana Digital Academy, which has provided statewide access to virtual courses since 2009. The classes, taught by certified Montana educators, ensure that students anywhere in the state (which boasts the most one-room schoolhouses of any state), can take Advanced Placement, dual enrollment and specialized courses like Indigenous Languages or Artificial Intelligence.
Gather and publish the data to better understand shortage patterns. States should give themselves, districts and the public the ability to understand shortage patterns at a detailed level, including by rurality. States should collect data that allows leaders to understand, at a minimum, how rural schools are experiencing shortages:
- At the school and district level
- Disaggregated by teachers’ certification area and subject taught
- Disaggregated by teachers’ demographics
- Disaggregated by teachers’ years of experience
Gather data on teachers’ reasons for leaving through statewide teacher working conditions surveys and exit surveys for departing teachers. Systematize this data by requiring collection at the state level through a single survey, deliver data back to district and schools, and provide facilitated opportunities to analyze data and act on feedback. Publish disaggregated data by rurality to understand the unique issues facing rural schools. Tennessee’s statewide teacher working conditions survey, for example, provides detailed statewide data on teachers’ and administrators perspectives on working conditions year over year; the survey’s research partner published analysis of results for rural schools.
Recommendation 3. Federal Actions to Support Rural School Funding and Success
Maintain access to federal education funds that rural schools rely on to support teachers. Federal funds are a critical source of funding for rural schools, who rely on them for a host of core functions, including many that directly support teachers: paying salaries, providing supportive professional learning, and funding innovative approaches to recruit new teachers. As the Trump administration has impounded allocated funds, released promised formula funds late, proposed cutting funds for future budget years, and abruptly begun moving funding programs to other agencies that lack the capacity or expertise to run them, rural schools have been left to plan for the worst. This has created an atmosphere of chaos and uncertainty, leaving rural schools struggling to plan ahead for the months and years ahead. (For more on how cuts to these programs impact rural schools, see the table, “Using federal education funds to end rural teacher shortages.”)
Increase access to discretionary grant funding by including rural schools in the Secretary of Education’s Supplemental Priorities. Rural schools often struggle to apply for and effectively compete for discretionary federal grants that could be used to support teacher recruitment and retention. With a Supplemental Priority, the Secretary could ensure rural schools are prioritized in future grant competitions.
Release guidance on how federal funds can be blended and braided to end teacher shortages. The Department of Education has historically provided a wide range of federal funds that can be used in concert to fund teacher recruitment and retention strategies; it is critical to maintain access to these funds. If, in the future, the Department’s role in funding and providing technical assistance to states is restored, the agency could work to ensure that more schools are making strategic investments to meet their goals around the teacher workforce. The Department could provide guidance to states and districts highlighting how schools have successfully brought these funding streams, along with state, local and philanthropic dollars, together to end teacher shortages. For more on current funding sources that states and districts can use to solve teacher shortages, and how cuts to these programs will impact rural schools, see the table, “Using federal education funds to end rural teacher shortages.”
Build a real-time national teacher labor market data system. Currently, very little detailed, timely data exists to understand the national landscape of teacher hiring and persistent vacancies. The Department of Education should spearhead a collaboration between the National Center for Education Statistics (NCES) and the Department of Labor’s Bureau of Labor Statistics (BLS) to provide better national teacher labor market data. States and local communities would be able to use this data to support secondary research to understand where rural communities are having success in lowering teacher vacancies and where others are struggling. Research suggests that the prevalence of rural teacher shortages may vary by state, and the field would benefit from understanding why.
Build the evidence base for teacher recruitment and retention practices, and fund rural-specific research. Much of the research on effective practices for attracting and retaining teachers does not specifically test the effectiveness or implementation challenges of a specific intervention in rural contexts. The federal government has an important role to play in funding action-oriented research to solve these urgent problems. At a minimum, it is critical that Congress continue to invest in programs like the Department’s Education Innovation Research grants (which include a specific priority for rural research).
Using federal education funds to end rural teacher shortages
A range of federal education funds can be used to combat rural teacher shortages, including, but not limited to:
- Title I, Part A
- Title II, Part A
- Rural Education Achievement Program (REAP)
- Teacher Quality Partnership Grants
- Career and Technical Education State Grants
For rural school serving high populations of Native students, the following funds can also be used:
- The Indian Education Professional Development Grant
- The Native Hawaiian Education Program
- The Alaska Native Education Program
- The Native American Career and Technical Education Program
- The Native Hawaiian Career and Technical Education Program
- The Tribally Controlled Postsecondary Career and Technical Institutions Program
Access to the funds listed here have been threatened by the Trump administration, through revoking current awards (such as Teacher Quality Partnership Grants), proposed cuts to future spending, and proposed consolidation of funding streams into block grants to states at drastically lower funding levels (such as REAP and Title II, Part A). At the same time, the administration has begun to transfer administration of many of the programs above to other agencies, which are ill-equipped to quickly stand up complex programs that send billions to states and districts nationwide. In the wake of these disruptions and potential cuts, rural schools will have little support available from the federal government to solve critical teacher shortages, and will likely face worsening challenges in an increasingly strapped budget environment.
Conclusion
The impact of teacher shortages impacts hundreds of thousands of young people like my former student each day–students who may go a whole year without a certified teacher, or graduate high school without ever having access to the advanced classes that unlock their future aspirations. Rural students of color and those living in high-poverty rural areas bear the brunt of this long-standing problem.
States, districts and the federal government each have a critical and distinct role to play in supporting rural schools. And while rural schools are used to being scrappy and doing more with less, without state and federal support, districts will be hard-pressed to close teacher workforce gaps on their own.
A Digital Public Infrastructure Act Should Be America’s Next Public Works Project
The U.S. once led the world in building railroads, highways, and the internet. Today, America lags in building the digital infrastructure foundation that underpins identity, payments, and data. Public Digital systems should be as essential to daily life as roads and bridges, yet America’s digital foundation is fractured and incomplete.
Digital public infrastructure (DPI) refers to a set of core and foundational digital systems like identity, payments, and data exchange that makes it easier for people, businesses, and governments to securely connect, transact, and access services.
DPI consists of interoperable, open, and secure digital systems that enable identity verification, digital payments, and data exchange across sectors. Its foundational pillars are Digital Identity, Digital Payments, and Data Exchange, which together provide the building blocks for inclusive digital governance and service delivery. DPI acts as the digital backbone of an economy, allowing citizens, governments, and businesses to interact seamlessly and securely.
America’s current digital landscape is a patchwork of systems across states, agencies and private companies, and misses an interoperability layer. This means fragmented identity verification, uneven instant payment networks, and siloed data exchange rules and mechanisms. This fragmentation not only frustrates citizens but also costs taxpayers billions, leads to inefficiency and fraud. This memo makes the case that the United States needs sweeping legislation– a Digital Public Infrastructure Act— to ensure that the nation develops a coherent, secure, and interoperable foundation for digital governance.
Challenges and Opportunities
Around the world, governments are investing in digital public infrastructure to deliver trusted, inclusive, and efficient digital services. In contrast, the United States faces a fragmented ecosystem of systems and standards. This section examines each pillar of digital public infrastructure, digital identity, digital payments, and data exchange, highlighting leading international models and what institutional and policy challenges the U.S. must address to achieve a similarly integrated approach.
Fragmented and non-interoperable Digital Identities
Digital Identity. The U.S. has no universal digital identification system. Proving who you are online often relies on a jumble of methods like scanning driver’s licenses, giving your social security number, or one-off logins. Unlike many countries with national e-ID schemes, the U.S. relies on the REAL ID law which sets higher standards for physical driver’s licenses, but it provides no digital ID or consent mechanism for online use. Just under half of U.S. states have rolled out some form of mobile driver’s license (mDL) or digital ID, and each implementation is largely unique.
Federal agencies have tried to streamline login with services like Login.gov, yet many agencies still contract separate solutions (Experian, ID.me, LexisNexis, Okta, etc.), leading to duplication. The Government Accountability Office recently found that two dozen major agencies use a mix of at least five different identity-proofing providers. The result is an identity verification landscape that is inconsistent and costly, both for users and the government.
Fragmented Digital Payment Infrastructure
Digital Payments. The United States still lags in offering universal, real-time payments accessible to all. The payments landscape is highly fragmented, with multiple systems operated by both public and private entities, each governed by distinct rule sets. The Automated Clearing House (ACH) network is the batch-based system that processes routine bank-to-bank transfers such as salaries, bill payments, and account debits or credits. It is co-run by the Federal Reserve (FedACH) and The Clearing House (EPN) under Nacha rules and settles with delay. The Real-Time Payments (RTP) network is an instant 24/7 credit-push system that moves money within seconds through a prefunded joint account at the Federal Reserve Bank of New York. It was launched by The Clearing House in 2017 and is governed by its private bank owners.
In 2023, the Federal Reserve launched FedNow, the first publicly operated real-time payment rail in the United States, offering instant settlement through banks’ Federal Reserve master accounts. Card networks such as Visa, Mastercard, Amex, and Discover continue to operate proprietary systems, while peer-to-peer platforms like Zelle, Venmo, and CashApp run closed-loop schemes that often rely on RTP for back-end settlement. Because these systems differ in ownership, governance, settlement models, and liability frameworks, they remain largely non-interoperable. A payment sent through RTP cannot be received on FedNow, and card or wallet systems do not seamlessly connect to ACH or instant payment rails.
FedNow operates as a real-time gross settlement (RTGS) infrastructure, enabling participating banks and credit unions to send and receive instant payments around the clock. Its design is infrastructure-centric: the Federal Reserve provides the back-end rail, while banks must opt in, build their own consumer interfaces, and set transaction fees and rules. The system does not define standardized public APIs, merchant QR systems, or interoperable consumer applications. These layers are left to the market. Its policy intent centers on efficiency and resilience in interbank payments rather than universal inclusion or open access.
Examples of Complete Public Payment Ecosystems
By contrast, India’s Unified Payments Interface (UPI) and Brazil’s Pix were designed as full digital public infrastructures that combine settlement, switching, and retail layers within a single public framework. Both are centrally governed, with UPI managed by the National Payments Corporation of India under Reserve Bank of India oversight and Pix managed by the Central Bank of Brazil. They enforce mandatory interoperability across all banks, wallets, and payment apps through open API standards. Their architecture integrates digital identity, authentication, and consent layers, allowing individuals and merchants to transact instantly at zero or near-zero cost.
While FedNow provides the plumbing for real-time settlement among banks, UPI and Pix function as complete public payment ecosystems built on open standards, public governance, and inclusion by design. Real-time payment systems in India (UPI), Brazil (Pix), and the United Kingdom (Faster Payments) now process far higher transaction volumes than their U.S. counterparts, reflecting how deeply these infrastructures have become embedded in daily economic activity.

Credit: fxcintel.com
This fragmented payment ecosystem became painfully apparent during COVID-19: some people waited weeks or months for stimulus and unemployment checks, while fraudsters exploited the delays. Only in 2025 did the Treasury Department finally announce it will stop issuing paper checks for most federal payments, to reduce delays, fraud, and theft.
Clearly, the U.S. needs a more cohesive approach to instant, secure payments, from Government-to-Person (G2P) benefits to Person-to-Government (P2G) tax payments and everyday Person-to-Person (P2P) transactions.
Data Exchange. Americans routinely encounter data silos and repetitive paperwork when interacting with different sectors and agencies. Each domain follows its own regulatory and technical standards. Health records are governed by the Health Insurance Portability and Accountability Act of 1996 (HIPAA) and the Trusted Exchange Framework and Common Agreement (TEFCA) established under the 21st Century Cures Act of 2016. Financial data are protected by the Gramm–Leach–Bliley Act of 1999 (GLBA) and will soon fall under the Consumer Financial Protection Bureau’s proposed Personal Financial Data Rights Rule (Section 1033, Dodd–Frank Act). Tax and education data are separately governed by the Internal Revenue Code and the Family Educational Rights and Privacy Act of 1974 (FERPA).
There is no unified, citizen-centric protocol for individuals to consentingly share their data across sectors. For example, verifying income for a mortgage, student loan, or benefits application might require three separate data pulls from the IRS or employer, each with its own process. In healthcare, TEFCA is creating a nationwide data-sharing framework but remains voluntary and limited to medical providers. In finance, Europe’s PSD2 Open Banking Directive (2018) forced banks to open consumer data via APIs, while the United States is only beginning similar steps through the CFPB’s data portability rulemaking. Overall, data-sharing rules remain sector-specific rather than citizen-centric, making it difficult to “connect the dots” across domains.
Data Protection. The United States follows a fragmented, sectoral approach to data protection rather than a single, unified framework. Health information is covered by HIPAA (1996), financial data by GLBA (1999), student records by FERPA (1974), and children’s online data by the Children’s Online Privacy Protection Act (COPPA, 1998).
States have layered on their own privacy laws, most notably the California Consumer Privacy Act (CCPA, 2018) and the California Privacy Rights Act (CPRA, 2020). At the federal level, the Federal Trade Commission (FTC) fills gaps using its authority to regulate “unfair or deceptive practices” under Section 5 of the FTC Act (15 U.S.C. §45). However, there remains no nationwide baseline for consent, portability, or deletion rights that applies uniformly across all sectors.
An illustration from 2021 by the New York Times shows the picture very well.
Credit: Dana Davis
Recent efforts in Congress, including the proposed American Data Privacy and Protection Act (ADPPA, 2022) and the American Privacy Rights Act (APRA, 2024), sought to create a comprehensive federal framework for data privacy and user rights. APRA built on ADPPA’s foundations by refining provisions related to state preemption, enforcement, and individual rights, proposing national standards for access, correction, deletion, and portability, and stronger obligations for large data holders and brokers. It also envisioned expanded enforcement powers for the FTC and state attorneys general, along with a limited private right of action.
Despite initial bipartisan attention, APRA has not secured sustained bipartisan support and remains stalled in Congress. The bill was jointly introduced in 2024 by the Republican Chair of the House Energy and Commerce Committee and the Democratic Chair of the Senate Commerce Committee, reflecting early cross-party interest. However, Democratic support weakened after language addressing civil-rights protections and algorithmic discrimination was removed, prompting several members to withdraw backing (Wired, 2024). As a result, the legislation has not advanced beyond committee referral, leaving the United States reliant on a patchwork of sector-specific and state-based privacy laws.
The outcome is a system where Americans face both fragmented data exchange and fragmented data protection, undermining trust in digital public services and complicating any transition toward a citizen-centric digital infrastructure.
The High Cost of Fragmentation
This patchwork system isn’t just inconvenient; it also bleeds billions of dollars. When agencies can’t reliably identify people, deliver payments quickly, or cross-check data, waste and fraud increase. Here are just a few examples:
Improper Payments. In FY2023 the federal government reported an estimated $236 billion in improper payments. That astronomical sum (almost a quarter-trillion dollars) stemmed from issues like payments to deceased or ineligible individuals and clerical errors. In fact, over 74% of the improper payments were overpayments The largest drivers included Medicare/Medicaid billing mistakes and identity-verification failures in pandemic relief programs. For example, the Pandemic Unemployment Assistance program alone saw an increase of $44 billion in erroneous payments, as identity thieves and imposter claims slipped through weak verification checks. While not all improper payments can be eliminated, a significant portion, GAO notes, can be eliminated. The biggest share of improper payments results from documentation and eligibility verification weaknesses, not intentional fraud. All errors could be reduced with better digital identity and data sharing systems.
Identity Theft and Fraud. American consumers are suffering a wave of identity-related fraud. In 2023, the Federal Trade Commission received over 1 million reports of identity theft such as credit cards opened in another person’s name or fraudsters hijacking unemployment benefits. Identity theft now accounts for about 17% of all consumer fraud reports. The surge during the pandemic (when government aid became a target) showed how criminals exploit weak ID verification. State unemployment systems, for instance, paid out a significant sum to fraudsters who used stolen identities. Strengthening the digital ID infrastructure in U.S. could curb these losses by catching imposters before payments go out.
Administrative Overhead. Fragmentation forces each agency and company to reinvent the wheel, at great expense. Consider identity proofing: federal agencies spent over $240 million from 2020–2023 on contracts for login and ID verification solutions, much of it to third-party vendors, despite overlapping functionality. States and private institutions likewise pour resources into redundant systems for onboarding and verifying users. Processing paper documents and manual checks adds further costs and an indirect cost of time and frustration for citizens. A GAO report noted that agencies have widely varying systems and that a coordinated digital identity approach could improve security and save money. In short, the lack of shared public digital infrastructure means higher costs and slower service across the board.
Plan of Action
What would a Digital Public Infrastructure Act do?
It’s clear that the status quo isn’t working. The U.S. needs a Digital Public Infrastructure (DPI) Act, a comprehensive federal law that would build the rails and rules for secure, efficient digital interactions nationwide. Just as past Congresses invested in highways and the internet itself, Congress today should invest in core digital systems to serve as public goods. A DPI Act could establish three pillars in particular:
Federated, Privacy-preserving Digital Identity
A secure digital ID that Americans can use (voluntarily) to prove who they are online, without creating a centralized “Big Brother” database. This would be a federated system, meaning you could choose from multiple trusted identity providers. For example, you could share your identification with your state DMV, the U.S. Postal Service, or a certified private entity, all adhering to common standards. The federated system must follow the latest NIST digital identity guidelines for security and privacy (e.g. NIST SP 800-63) to ensure high Identity Assurance Levels.
Crucially, it should be privacy-preserving by design: using techniques like encrypted credentials and pairwise pseudonymous identifiers so that each service you log into only sees a unique code, not your entire identity profile. A federated approach would leverage existing ID infrastructures (state IDs, passports, social security records) without replacing them. Instead, it links and elevates them to a digital plane.
Under a DPI Act, an American citizen might verify their identity once through a trusted provider and then use that digital credential to access any federal or state service, open a bank account, or consent to a background check, with one login. This approach can dramatically reduce fraud (no more 5 different logins for 5 agencies) while protecting civil liberties by avoiding any single centralized ID database. The Act could establish a national trust framework (operating under agreed standards and audits) so that a digital ID issued in, say, Colorado is trusted by a bank in New York or a federal portal, just as state driver’s licenses are mutually recognized today. Done right, a digital ID saves time and protects privacy: imagine applying for benefits or a loan online by simply confirming a verified ID attribute (e.g. “I am Alice, over 18 and a U.S. citizen”) rather than scanning and emailing your driver’s license to unknown clerks.
Universal, Real-time Payments (G2P, P2G, P2P)
The DPI Act should ensure that instant payment capability becomes as ubiquitous as email. This likely means leveraging FedNow, the Federal Reserve’s new instant payment rail, and expanding its use. For Government-to-Person (G2P) payments, Congress could mandate that federal disbursements (tax refunds, Social Security, veterans’ benefits, emergency relief, etc.) use a real-time option by default, with an ACH or card fallback only if a recipient opts out.
No citizen should wait days or weeks for funds that could be sent in seconds. The same goes for Person-to-Government (P2G) payments: taxes, fees, and fines should be payable instantly online, with immediate confirmation. This reduces float and uncertainty for both citizens and agencies. Finally, Person-to-Person (P2P): while the government doesn’t run private payment apps, a robust public instant payments infrastructure can connect banks of all sizes, enabling truly universal P2P transfers. This way, someone at Bank A can instantly pay someone at Credit Union B without needing both to join the same private app.
FedNow, as a public utility, is an important player, but the Act could incentivize or require banks to join so no institution is left behind. The result would be a seamless national payments system where money moves as fast as email, enabling things like on-demand wage payments, rapid disaster aid, and easier commerce.
Cross-sector, Consent-based Data Exchange
The third pillar is perhaps the most forward-looking: creating standard protocols for data sharing that put individuals in control. Imagine a secure digital pipeline that lets you, the citizen, pull or push your personal data from one place to another with a click – for instance, authorizing the IRS to share your income info directly with a state college financial aid office, or allowing your bank to verify your identity by querying a DMV record (with your consent) instead of asking you to upload photos or scans.
A DPI Act can establish an open-data exchange framework inspired by efforts like open banking and TEFCA, but broader. This framework would include technical standards (APIs, encryption, logging of data requests) and legal rules (what consents are needed, liability for misuse, etc.) to enable “tell us once” convenience for the public.
Importantly, it must be consent-based: your data doesn’t move unless you approve and authorize it.It can let you carry digital attestations i.e. driver’s license, vaccination, veteran status, etc. on an e-wallet and share just the necessary bits with whoever needs to know. Some building blocks already exist: the federal Office of the National Coordinator for Health IT (ONC) is working on health data interoperability through TEFCA (so hospitals can query each other’s records), and the Consumer Financial Protection Bureau has begun rulemaking to give bank customers the right to share their financial data with third-party apps.
A DPI Act could unify these efforts under one umbrella, extend them to other domains, and fill in the gaps (for instance, enabling portable eligibility, if you qualify for one program, easily prove it for another). It could establish a governance entity or standards board to oversee the trust frameworks needed. Crucially, this must be accompanied by strong privacy and security measures like audit trails, encryption, and an emphasis that individuals can see and control who accesses their data. An example of this is how the EU wallet provides a dashboard for users to review and revoke data sharing.
The Digital Public Infrastructure Act would not necessarily build each piece from scratch but set national standards and provide funding to knit them together. It could, for example, direct NIST and a multi-agency task force to implement a federated ID by a certain date (building on Login.gov’s lessons), require the Treasury and Federal Reserve to ensure every American has a route to instant payments across platforms (leveraging FedNow), and authorize pilot programs for cross-sector data exchange in key areas like social services.
Precedent for such an approach already exists in bipartisan efforts:
Navigating Roadblocks: Federalism, Privacy, and Tech Contractors
Enacting a U.S. Digital Public Infrastructure Act will face several real challenges. It’s important to acknowledge these roadblocks and consider strategies to overcome them:
Federalism and Decentralized Authority
Unlike many countries where a central government can launch a national ID or payments platform by decree, the U.S. must coordinate federal, state, and local authorities. Identity in the U.S. is traditionally a state domain (driver’s licenses, birth certificates), while federal agencies also issue identifiers (Social Security numbers, passports). A DPI solution must respect these layers. States may fear a federal takeover of their DMV role, and agencies might guard their IT turf. Solution: design the system as a federation of trust. The Act could explicitly empower states by providing grants for states to upgrade to digital driver’s licenses (the Improving Digital Identity Act proposed in 2022 did exactly this, offering grants for state DMV mobile IDs). It could also create a governance council with state CIOs and federal officials to jointly set standards.
Civil Liberties and Privacy Concerns
Any mention of a “digital ID” in America raises eyebrows about Big Brother. Civil liberties advocates will rightly question how to prevent government overreach or mass surveillance. The Act should incorporate privacy by design provisions e.g., require minimal data collection, mandate independent audits for security, and give users legal rights over their data. One promising approach is using decentralized identity technologies, where your personal data (like credentials) stay mostly on your device under your control, and only verification proofs are shared. Also, the law can explicitly forbid certain uses, for instance, prohibit law enforcement from fishing through the digital ID system without a warrant, or forbid using the digital ID for profiling citizens. Including groups like the ACLU and EFF in the drafting process could help address concerns early. It’s worth noting that privacy and security can actually be enhanced by a good digital ID: today, Americans hand over copious personal details to random companies for ID checks (e.g. scan of your driver’s license to rent an apartment, which might sit in a landlord’s email forever). A federated ID could reduce exposure by only transmitting a yes/no verification or a single attribute, rather than a photocopy of your entire ID. Conveying that narrative, that this can protect people from identity theft and data breaches, will be key to overcoming knee-jerk opposition. Still, robust safeguards and perhaps a pilot phase to prove the concept will be needed to convince skeptics that a U.S. digital identity won’t become a surveillance tool.
Incumbent Resistance (Big tech and Contractors)
There are vested interests in the current disjointed system. Large federal IT contractors and identity verification vendors profit from selling agencies one-off solutions; big tech companies dominate payments and data silos in the status quo. A unified public infrastructure could be seen as competition or a threat to some business models. For example, if a free government-backed digital ID becomes widely accepted, companies like credit bureaus (which sell ID verification services) or ID.me might lose market share. If open-data sharing is mandated, banks that monetize data might push back. The solution is to engage industry so they can find new opportunities within the ecosystem. Many banks, for instance, actually support digital ID because it would cut fraud costs for them. The banking industry has been calling for better ID verification to fight account takeover and synthetic identities. In fact, a coalition of financial institutions endorsed the earlier Improving Digital Identity legislation.
Fintechs will favor Digital Public Infrastructure (DPI) because it transforms customer acquisition from a slow, expensive manual process into an instant, low-cost digital utility. By plugging into standardized government layers for identity (e-KYC) and data sharing (Account Aggregators), fintechs can instantly verify and underwrite users who lack traditional credit histories. This allows them to scale rapidly and profitably serve millions of previously “unbanked” customers by making lending decisions based on real-time data rather than rigid credit scores.. The Act can create a public-private task force (as earlier bills proposed) to hash out implementation. For government contractors, the reality is that building DPI will still require significant IT work, just more standardized. Contractors who adapt can win contracts to build the new infrastructure.
Political Will and Public Perception
DPI can be a bipartisan win if framed correctly.
For conservatives and fiscal hawks: emphasize the anti-fraud, waste-cutting angle. Stopping improper payments (recall that $236B figure!) and preventing identity theft aligns with the goal of efficient government. The Act essentially plugs leaky buckets, something everyone can get behind.
For liberals and tech-progressives: emphasize equity and empowerment. How digital infrastructure can help the unbanked access financial services, ensure eligible people aren’t left out of benefits, and give individuals control of their own data (a pro-consumer, anti-monopoly stance). Indeed, digital public goods are often framed as a way to ensure big tech doesn’t exclusively control our digital lives.
The key will be avoiding hot button mis-framings: this is not a surveillance program, not a national social credit system, etc. It’s an upgrade to basic government digital infrastructure. One strategy is to start with pilot programs and voluntary adoption to build trust. For example, the Act could fund a pilot in a few states to link a state’s digital driver’s license with federal Login.gov accounts, showing a working federated ID in action. Or pilot using FedNow for a chunk of tax refunds in one region. Early successes will create momentum and help refine the approach. Champions in the Congress will need to communicate that this is infrastructure in the truest sense: just as U.S. needed electrification and interstate highways, it now needs the digital equivalent to keep America competitive and secure.
Conclusion
A Digital Public Infrastructure Act represents more than a technical upgrade; it is an investment in America’s institutional capacity. The challenges the U.S. faces today like identity theft, improper payments, slow benefit delivery, and fragmented data governance are the predictable consequences of an outdated public digital foundation that has never been treated as national infrastructure. Just as the interstate highway system knit together the physical economy, and just as the early internet created the backbone for the digital economy, the United States now needs a unified, secure, and interoperable set of digital rails to support the next era of public service delivery and economic growth.
Unlike centralized systems elsewhere in the world, the American version of DPI would be federated, privacy-preserving, and deeply respectful of federalism. States would remain primary issuers of identity credentials. Private innovators would continue to build consumer-facing services. Federal agencies would govern standards rather than run monolithic platforms. This hybrid model plays to America’s institutional strengths such as distributed authority, competitive innovation, and strong civil liberties protections.
Congress must enact a Digital Public Infrastructure Act, a recognition that the government’s most fundamental responsibility in the digital era is to provide a solid, trustworthy foundation upon which people, businesses, and communities can build. America has done this before when it built the railroads, electrified the nation, and invested in the early internet. The next great public works project must be digital.
Increasing the Value of Federal Investigator-Initiated Research through Agency Impact Goals
American investment in science is incredibly productive. Yet, it is losing trust with the public, being seen as misaligned with American priorities and very expensive. To increase the real and perceived benefit of research funding, funding agencies should develop challenge goals for their extramural research programs focused on the impact portion of their mission. For example, the NIH could adopt one goal per institute or center “to enhance health, lengthen life, and reduce illness and disability”; NSF could adopt one goal per directorate “to advance the national health, prosperity and welfare; [or] to secure the national defense”. Asking research agencies to consider person-level or economic impacts in advance helps the American people see the value of federal research funding, and encourages funders to approach the problem holistically, from basic to applied research. For almost every problem there are different scientific questions that will yield benefit over multiple time scales and insight from multiple disciplines.
This plan has three elements:
- Focus some agency funding on measurable mission impacts
- Fund multiple timescales as part of a single plan
- Institutionalize the impact funding process across science funders
For example, if NIH wanted to reduce the burden of Major Depression, it could invest in a shorter time frame to learn how to better deliver evidence-based care to everyone who needs it. At the same time, it can invest in midrange work to develop and test new models and medications, and in the decades-long work required to understand how the exosome influences mood disorders. A simple way to implement this approach would be to build on the processes developed by the Government Performance Results Act (GPRA), which already requires goal setting and reporting, though proposals could be worked into any strategic planning process through a variety of administrative mechanisms.
Challenge and Opportunity
In 1945, Vannevar Bush called science the ‘endless frontier’, and argued funding scientific research is fundamental to the obligations of American government. He wrote “without scientific progress no amount of achievement in other directions can insure our health, prosperity, and security as a nation in the modern world”. The legacy of this report is that health, prosperity, and security feature prominently in the missions of most federal research agencies (see Table 1). However, in this century we have begun to drift from his focus on the impacts of science. We have the strange situation where our enterprise is both incredibly productive, and losing trust with the public, viewed as out of touch or misaligned with American priorities. This memo proposes a simple solution to address this issue for federal funding agencies like NIH and NSF that largely focus on extramural investigator-initiated research. These are research programs where the funding agency signals interest in specific topics and teams of scientists submit their research plans addressing those topics. The agency then funds a subset of those plans with input from external scientific reviewers.
This funding approach is incredibly productive. For example, NIH funds most of the pipeline for the emerging bioeconomy, which accounts for 5.1% of our GDP. From 2010 to 2016, every one of the 210 new entities approved by the FDA had some NIH funding. And yet, there appears to be a disconnect between our funding strategy and the public interest focus of the Endless Frontier operationalized through our federal science agency missions for investigator initiated research.
A fundamental driver of this disconnect might be a slight misalignment of the incentives of academic scientists, who are rewarded for novelty and scientific impact, with the broader public interest. Our federal agencies are highly attuned to scientific leaders, and place equal or even greater weight on innovation (novelty plus scientific impact) than real world impact. For example, NSF review criteria place equal weight on intellectual merit (‘advance knowledge’) and broader impacts (‘benefit society and contribute to the achievement of specific, desired societal outcomes’). NIH’s impact score of new applications is an ‘assessment of the likelihood for the project to exert a sustained, powerful influence on the research field(s) involved’ [emphasis mine], which is only part of the agency’s mission. The practical implications of this sustained focus away from the impact portion of agencies missions become apparent in figure 1, showing tremendous spending in health research unrelated to a key public interest measure like lifespan, especially when compared to other nations’ health research spending.
Perhaps the realization that the federal research investment is not strongly linked to their mission impact is one reason why American science has been slowly losing public trust over time. Among the people of 68 nations ranking the integrity of scientists, Americans ranked scientists 7th highest, whereas we ranked scientists 16th highest in our estimation of them acting in the public interest. And this is despite the fact that the American investment in science is many times higher than the 15 nations who rated scientists more highly on public interest. A more accurate description of our 21st century federal science enterprise might be the ‘timeless frontier’, where our science agencies pursue cycles of funding year in and year out, with their functional goal being scientific changes and their primary measure of success being projects funded. Advancing the economy, health, national defense, etc., are almost incidental benefits to our process measures.
We can do better. In 2024, the National Academy of Medicine called out the lack of high level coordination in research funding. In 2025, the administration has been making drastic cuts and dramatic changes to goals and processes of federal research funding, and the ultimate outcome of these changes is unclear. In the face of this change, Drs. Victor Dzau and Keith Yamamoto, staunch champions of our federal science programs, are calling for “a coherent strategy […] to sustain and coordinate the unrivaled strengths of government-funded research and ensure that its benefits reach all Americans”.
We can build on the incredible success of the federal science enterprise – inarguably the most productive science enterprise in all history. The primary source of American scientific strength is scale. American funding agencies are usually the largest funders in their space. I will highlight some challenges of the current approach and suggest improvements to yield even more impactful approaches more closely aligned with the public interest.
The primary federal funding strategy is broad diversification, where our agencies fund every high scoring application in a topic space (see FAQs). Further, federal science agencies pay little attention to when they expect to see a fundamental impact arising from their research portfolio. For example, a centrally directed program like the Human Genome Project can lead to breakthrough treatments decades later, but in the meantime, other research that generates improvements on faster timescales could have been coordinated, such as developing conventional drug treatments, or research to optimize quality and delivery of existing treatment.
And yet, the breadth and complexity of broad diversification makes it easy to cherry pick successes. This is a strategic issue, and is bigger than the project selection issues highlighted in the earlier discussion about review criteria. When research funding agencies make their pitch for federal dollars they highlight a handful of successes over tens of thousands of projects funded over many years. They ignore failures, the time when investments were made, and time to benefit. With the goals and metrics we have in place, it is simply too hard to summarize progress in any other way.
Overly diversified science funding supports both good Congressional testimony and bad strategy. If your problem happens to fall into a unicorn space of success, there is a lot to celebrate. But most problems do not, and we experience inconsistent returns. We need to define the success of research funding more precisely, in advance, and in ways that more obviously align with the public interest.
Plan of Action
If we tweak our funding strategy to focus on societal impacts, we can move to a more impactful science enterprise, and help regain public support for science funding. We can focus federal research funding on effective answers to difficult problems demanding both urgency and short term improvements, and fundamental discoveries that may take decades to realize. My solution and implementation actions for agencies, and potentially Congress, are described below.
Recommendation 1. Focus some agency funding on measurable mission impacts.
We should empower our science agencies to step away from broad diversification as the predominant funding strategy, and pursue measurable mission impacts with specific time horizons. It can be a challenge for funders to step away from process measures (e.g. projects or consortia funded) and focus on actual changes in mission impact.
Ideally, these specific impacts would be broken into measurable goals that would be selected through a participatory process that includes scientific experts, people with lived experience of the issue, and potential partner agencies. I recommend each agency division (e.g. an NSF Directorate) allocate a percentage of their budget to these mission impact strategies. Further, to avoid strategic errors that can arise from overwhelming power of federal funding to shape the direction of scientific fields, these high level funding plans should be as impact focused as possible, and avoid steering funding to one scientific theory or discipline over another.
Recommendation 2. Fund multiple timescales as part of a single plan.
Research funders need to balance their investment portfolios not only across problem areas, but over time. Complex challenges will often require funding different aspects of the solution on different timelines in parallel as part of a larger plan. Balancing time as well as spending allows for a more robust portfolio of funding that draws from a broader array of scientific disciplines and institutions.
Note, this approach means starting lines of research that may not lead to ultimate impact for decades. This approach might seem strange given our relatively short budget cycles, but is very common in science, where projects like the Human Genome initiative, the Brain Initiative, or the National Nanotechnology Initiative, have all exceeded a single budget cycle and will take years to realize their full impact. These kinds of efforts require milestones to ensure they stay on track over time.
Recommendation 3. Institutionalize the impact funding process across science funders.
Our research enterprise has become oriented around investigator-initiated, project-based awards. Alternative funding strategies, such as the DARPA model, are viewed as anomalies that must require completely different governance and procedures. These differences in goals are unnecessary. A consistent focus on impacts and strategy in funding across agencies will help the scientific community become more aware of the time to benefit of research, help underscore the value of research investment to the American public, and help research agencies collaborate among themselves and with their partner agencies (e.g. NIH collaborates more closely with CMS, FDA, etc.).
In short, institutionalizing this process can lead to greater accountability and recognition for our science enterprise. This structure allows our funders to report to the public progress on specific goals on predetermined and preannounced timelines, rather than having to comb through tens of thousands of independent funding decisions and competing strategies to find case studies to highlight. In this way, expected and unexpected scientific results, and even operational challenges, can be discussed within an impact framework that clearly ties to the agency mission and public interest.
Example of Planning using an Impact Focus
Here is an example of a mission impact goal Reducing the Burden of Major Depressive Disorder that could be put forth by the National Institute of Mental Health (NIMH), and the process to develop it.
Commence Inclusive Planning: NIMH brings together experts from academia, clinical care, industry, people impacted by depression, and FDA and CMS to develop measures, timelines and funding strategies.
Develop Specific Impact Measures: These should reflect the agency’s impact portion of their mission. For example, NIH’s mission impact of “enhance health, lengthen life, and reduce illness and disability” requires measuring impact on human beings. Example measurement targets could include:
- Reduced incidence of Major Depressive Disorder
- Increased productivity (e.g. days worked) of people living with Major Depressive Disorder
- Reduced suicide rates
Fund Multiple Time Scales: Designate time scales in parallel as part of a comprehensive strategy. These different plans would involve different disciplines, funding mechanisms, and private sector and government partners. Examples of plans working at different timescales to support the same goal and measures could include:
- 10 year plan: Increase utilization of evidence based care
- 15 year plan: Develop and implement new treatments
- 30 year plan: Determine how the exposome causes and prevents depression, and how can be changed
- It is likely that NIMH has already obligated funds to projects that support one of these plans, though they may need additional work to ensure that those projects can directly tie to the specific plan measures.
Implementation Strategies for Impact Goals
Each federal funding agency could allocate a percentage of their budget to these and other impact goals. The exact amount would depend on the current funding approach of each agency. As this proposal calls for more direct focus on agency mission, and not a change in mission, it is likely that a significant percentage of the agency’s current budget already supports an impact goal on one or more of its time scales.
For an agency heavily weighted towards project based funding of small investigator teams, like NIH, I would recommend starting with a goal of 20% of their budgets set towards impact spending and consider increases over time. Other agencies with different funding models may want to start in a different place. Further, I would recommend different goals and targeted funds for each major administrative unit, such as an institute or directorate.
All federal funders already engage in some form of strategic and budget planning, and most also have formal structures for engaging stakeholders into those planning decisions. Therefore, each agency already has sufficient authorities and structures to implement this proposal. However, it is likely that these impact goals will require collaboration across agencies, and that could be difficult for agencies to efficiently conduct by themselves.
Additional support to make this change could come from Congressional Report language as part of the budget process, through interagency leadership from the White House Office of Science and Technology, or through the Office of Management and Budget. For example, the Government Performance Results Act (GPRA) already requires agency goal setting, reporting and supports cross agency priority goals. That planning process could easily be adapted to this more specific impact focus for research funding agencies, and reporting on those goals could be incorporated into routine reporting of agency activities.
Conclusion
We are living through a massive disruption in federal research funding, and as of the fall of 2025, it is not clear what future federal research funding will look like. We have an opportunity to focus the incredibly productive federal research enterprise around the central reasons why Americans invest in it. We can meet Bush’s challenge of the Endless Frontier simply by clearly defining the benefits the American people want to see, and explicitly setting plans, timing and money to make that happen.
We can call our shots and focus our science funding around impacts, not spending. And we can set our goals with enough emotional resonance and depth to capture both the interests of the average American, and the needs of scientists from different disciplines and types of institutions. We already have the legal authorities in place to adopt these techniques, we just need the will.
Inadvertently, the huge scale of federal funding could lead to a monopsonistic effect. In other words, NIH’s buying power is so large, if NIH does not fund a specific type of research, people may stop studying it. This risk is highest within a narrow scientific field if there is a bias in grant selection. A well publicized example being NIH’s strong funding preference to one theory of Alzheimer’s Disease to the diminishment of competing theories, which in turn influenced careers and publication patterns to contribute to that bias.
Privacy-Preserving Research Models Essential for Large Scale Education R&D Infrastructure
The current education research-to-policy pipeline is too slow to keep pace with the urgent needs of districts and states. Researchers face steep barriers to accessing high-quality, multimodal data, while existing R&D infrastructures remain siloed and under-resourced. Without scalable, trusted, systems that enable timely and secure data use, the U.S. risks falling behind in generating actionable and evidence-based insights to guide policy and practice. In this memo, we discuss how privacy-preserving research models can be used to strengthen education R&D capacity.
Challenge and Opportunity
Learning is a lifelong and multidimensional process, yet data about learning has historically been difficult to obtain. The shift to digital learning platforms (DLPs), accelerated by COVID-19, has created a wealth of data, but accessing it remains complex and slow – especially for researchers with fewer institutional resources.
Additionally, complex privacy laws, such as the Children’s Online Privacy Protection Act (COPPA) and Family Educational Rights and Privacy Act (FERPA), alongside state-specific regulations and institutional risk aversion, create substantial barriers. These laws were not designed to accommodate privacy scenarios within the current environment of pervasive data collection and rapidly advancing AI.
As such, trusted mechanisms for safe data access that remove barriers to critical R&D, bolster global competitiveness, and leverage innovation to cultivate a skilled STEM workforce, are more important than ever. Without trusted mechanisms to ensure privacy while enabling secure data access, essential R&D stalls, educational innovation stalls, and U.S. global competitiveness suffers.
Flipping the traditional research model
The landscape of educational research and development (R&D) is rapidly evolving as digital learning platforms (DLPs) capture increasingly rich streams of data about how students learn. These multimodal data streams provide unprecedented opportunities to accelerate insights into how learning happens, for whom, and in what contexts – as well as how these processes, in turn, affect learning outcomes, engagement, and persistence. Yet, despite this potential, access to platform-generated learning data remains highly constrained – particularly for early-career researchers with minimal institutional resources and organizations outside elite academic settings.
Current challenges to accessing DLP data include privacy risks (e.g., data leaks), opaque legal environments, institutional risk aversion, and the lack of trusted third-party intermediaries to balance privacy with data utility. As a result, promising research is delayed and the research-to-policy pipeline is exacerbated – leaving decision-makers without timely evidence to address urgent needs such as learning recovery, responsible AI integration, or workforce readiness.
Privacy-preserving models offer transformative opportunities to address these barriers. Across sectors, the field is converging on trusted research environments that include secure enclaves that keep data in situ and move analysis to the data. SafeInsights, the U.S. Census’ Federal Statistical Research Data Center (FSRDC), and North Carolina Education Research Data Center (NCERDC) are examples of such systems complemented by privacy-preserving methods.
Privacy-preserving research models, such as SafeInsights, flip the traditional research model: instead of giving data to researchers, it brings researchers’ questions and analyses, encoded as software, to the data. At no point in the research process does the researcher have direct access to raw data, thereby minimizing concerns for data leaks.
Researchers instead use sample or synthetic data to craft their analyses. Once the researchers’ analysis code is submitted to the owner of the data, it is reviewed by experts for approval. This model minimizes risk, reduces delays in the research-to-policy pipeline, and unlocks data that would otherwise remain inaccessible.
Think of it as a secure research zone: a trusted third-party intermediary where researchers can run analyses using specific tools and applications, but cannot access data directly, ensuring strict security.
Rather than extracting and sharing sensitive data with researchers, privacy-preserving research models bring researchers’ analytic tools to secure data enclaves – preserving privacy while enabling rigorous, scalable, inquiry of DLP data. Through secure enclaves, transparent governance, and standardized compliance frameworks, a durable large-scale infrastructure for research can be created.
Benefits of privacy-preserving research models
- Accelerate time to insight for policy and decision-makers who need rapid, evidence-based guidance. Standardized governance reduces delays arising from fragmented compliance and legal processes. For federal, state, and local level policy and decision-makers, this means actionable insights can be delivered in months rather than years, potentially informing legislative decisions and programs with greater speed.
- Safely join data across platforms, enabling richer analyses of student learning. Shared infrastructure maximizes critical research infrastructure return on investments and spreads costs across funders. Secure, trusted, interoperable research environments protect privacy while enabling cumulative evidence. This aligns with federal agency priorities to modernize research infrastructure and ensure taxpayer investments translate into impact.
- Democratize access and participation in complex research by lowering barriers for early-career researchers with minimal institutional resources and organizations outside elite academic settings. Lowering barriers to entry broadens the reach of federal R&D investments and supports state leaders and research organizations seeking to participate in research.
By securing cross-sector investment for embedding scalable privacy-preserving models into R&D ecosystems and infrastructures, we can expand access to high-value data while supporting long-term research scalability, security, and trust.
Such models can fill a critical gap in the R&D ecosystem by establishing a secure and sustainable research infrastructure that extends well beyond its initial NSF funding and is ideally suited to broker access between DLP developers, school districts, and researchers.
Plan of Action
Promote R&D Infrastructure Development and Sustainability
Privacy-preserving research models have the potential to offer researchers safer, faster, reliable, high-value, de-identified data analyses – while simultaneously saving DLPs and school districts time and resources on compliance reviews and privacy audits. It also creates opportunities for funders to support a sustainable research infrastructure that multiplies the impact of each dollar invested.
To move from promise to practice, interested stakeholders, including research institutions, school districts, and funders, should consider the following actions:
Recommendation 1. Lay the Foundation for Sustainable Large-Scale R&D Infrastructure
- Conduct policy landscape scans, including review of state student privacy laws, to identify commonalities, constraints, and pathways for district participation.
- Interview stakeholders, including district data leads, state education agencies, and platform providers, to understand pain points and demand for trusted intermediaries.
- Review existing research infrastructures and operational frameworks, including research data hub governance, fee structures, data-sharing agreements, IRB support services, and services, adapting effective practices to the privacy-preserving context.
Recommendation 2. Embed Infrastructure Costs into Research Contracts and Budgets
- Require researchers to include service fees for privacy-preserving infrastructure directly in grant applications, with templates to simplify proposal preparation.
- Embed privacy-preserving infrastructure costs in contracting and budgeting to support scalability, drive down the marginal cost of data access across the field, and make rigorous educational research more accessible and sustainable beyond single grants.
Recommendation 3. Catalyze Scaling through Foundation and Philanthropic Support
- Engage major education funders (e.g., Gates Foundation, Carnegie, Hewlett, Chan Zuckerberg Initiative) to support large scale R&D infrastructure efforts by underwriting core operations and reducing costs for under-resourced research organizations and districts.
- Draw on models such as the North Carolina Education Research Data Center (NCERDC), ICPSR (University of Michigan), and Harvard Dataverse, to sustain operations via grant-embedded fees, service contracts, and institutional memberships.
Recommendation 4. Develop Large Scale R&D Infrastructure across Sectors
- Extend privacy-preserving models across sectors, such as education, health, workforce, housing, and finance, to capture increasingly rich streams of data about how people live, learn, work, and access services.
- Enable secure, interoperable, cross-sector research on questions such as how early education experiences impacts long-term workforce outcomes or how neighborhood-level educational access connects to public health disparities.
- Align with federal agency efforts, such as the Federal Data Strategy, to support the linking of data ecosystems across sectors.
Conclusion
Privacy-preserving research models offer standardized, secure, and privacy-conscious ways to analyze data – helping researchers at the local, state, and federal levels understand long-term educational trends, policy impacts, and demographic disparities with unprecedented clarity.
By accelerating time-to-insight, investing in critical R&D infrastructure, and expanding participation in complex research, privacy-preserving research models offer possibilities for delivering on urgent policy priorities – building towards a modern, responsive, trustworthy education R&D ecosystem.
Privacy-preserving research models could offer the possibility to connect researchers with DLP data representing different learning contexts. DLP data is often rich and versatile, possibly enabling the exploration of multiple research topics, including:
- Learning Behaviors: Analyze patterns of engagement, tool usage (e.g., text-to-speech, digital pencil), or response time.
- Personalized Learning: Investigate how adaptive experiences influence outcomes.
- Achievement Gaps: Study differences across subgroups (e.g., students with disabilities, English Language Learners).
- Intervention Effectiveness: Test how interventions or instructional strategies impact student performance.
- Learning Trajectories: Examine longitudinal progress and identify barriers to success.
Privacy-preserving research models could facilitate connections among various types of educational data from DLP developers, each representing different aspects of K16+ teaching and learning, including administrative records, learning management systems, and curricular resource usage data.
Examples of DLP data categories include digital curricula, university data systems, and student information systems for K-12 institutions.
Across sectors, the field is converging on privacy-preserving research models that utilize secure enclaves to keep data in situ and move analysis to the data. Such examples include:
- Federal statistical system: the FSRDC network provides secure facilities (now including some remote access) where qualified researchers run analyses on restricted microdata under rigorous review.
- Cross-agency administrative data: the Coleridge Initiative’s Administrative Data Research Facility (ADRF) is a FedRAMP-certified, cloud based platform that supports inter-state and inter-agency linkages under shared governance.
- State education data enclaves: NCERDC at Duke University and the Texas Education Research Center (ERC) support secure access to longitudinal education/workforce data with well-defined agreements and masking rules.
- Health: OpenSAFELY operationalizes a strict “code-to-data” model—researchers develop code on dummies, submit jobs to run against in-place EHR data, and only aggregate outputs leave the enclave. NIH’s N3C and All of Us Researcher Workbench similarly provide secure, cloud based research environments where individual-level data never leave the enclave.
These approaches are complemented by privacy-preserving release methods (e.g., differential privacy), used by the U.S. Census Bureau and supported by open-source toolkits like OpenDP/SmartNoise.
At the center of privacy-preserving research models is privacy-by-design that enables secure research with protected information – while alleviating technical, logistical, and collaborative challenges for researchers.
Technical
Privacy-preserving research models can offer technical components that support large-scale digital learning research such as:
- Analysis options, which enable large-scale analysis of single platform data
- Intervention options, which enable researchers —under appropriate agreements—to introduce different kinds of interactive activities (including surveys, assessments, and learning activities) within a partner platform’s student experience
- Enclave fusion, which in some designs can enable researchers to leverage multi-platform data
Logistical
- Shared data sharing agreement templates
- Streamlined IRB and data-sharing processes
- Consent management across different populations
- Regulatory compliance with the changing data protection landscape
Community and Collaboration
- Help easily surface researchers and the research that they are conducting
- Bridge connections among platforms, researchers, and educational institutions to support meaningful research to inform practice
- Connect researchers at different levels of their careers and different domains to support mentorship and collaboration
If assessment results are the scoreboard that reveals what students are learning, user data is the game film that reveals how students learn: time on task, requesting support, revising, using resources.
Using SafeInsights’ privacy-preserving tools, researchers can securely analyze real-time digital learning platform data to better understand how students engage with digital learning. Consider two students with the same score:
Student A works steadily, using hints to revise answers. This pattern suggests a need for additional content support, scaffolding, and practice.
Student B races through with rapid guessing and skipped items. This pattern suggests a need to adjust prompts, pacing, and support.
By distinguishing between these pathways, researchers, educators, and policymakers can target digital learning platform interventions more precisely—whether that means redesigning practice problems, adjusting instructional supports, or tailoring engagement strategies.
Bottom line: SafeInsights securely transforms raw data into actionable evidence, helping policymakers and practitioners invest in solutions that boost learning outcomes and improvement at scale.
Tax Filing as Easy as Mobile Banking: Creating Product-Driven Government
Americans trade stocks instantly, but spend 13 hours on tax forms. They send cash by text, but wait weeks for IRS responses. The nation’s revenue collector ranks dead last in citizen satisfaction. The problem isn’t just paperwork — it’s how the government builds.
The fix: build for users, not compliance. Ship daily, not yearly. Cultivate talent, don’t rent it. Apple doesn’t outsource the creation of its products; the IRS shouldn’t outsource taxpayer experience. Why?
The goal: make taxes as easy as mobile banking.
The IRS, backed by a Congress and an administration that truly wants real improvements and efficiencies, must invest in building its tax products in house. Start with establishing a Chief Digital Officer (CDO) at the IRS directly reporting to the Commissioner. This CDO must have the authority to oversee digital and business transformation across the organization. This requires hiring hundreds of senior engineers, product managers, and designers—all deeply embedded with IRS accountants, lawyers, and customer service agents to rebuild taxpayer services. This represents true government efficiency: redirecting contractor spending to fund internal teams that build what American taxpayers should own rather than rent.
This is about more than broken technology. This is a roadmap for building modern, user-centric government organizations. The IRS touches every American, making it the perfect lab for proving the government can work.
Transform the IRS first, then apply these principles across every agency where citizens expect digital experiences that actually work.
Challenge & Opportunity
It’s April 15th. For the first time, you’re not fretting.
You finished filing your taxes on a free app. It took 15 minutes. Your income? Already there. Your credits? Pre-calculated and ready to claim. Your refund? Hitting your bank account tomorrow.
For millions around the world, swift, painless tax filing isn’t a dream. It’s the norm. It should be for Americans, too.
But in the U.S., the IRS experience is still slow, opaque, process-heavy, and frustrating. Tax filing is one of the few universal interactions Americans have with their government—and it’s not one that earns much trust.
It doesn’t have to be this way. We were on the path to delivering that with IRS Direct File and needed to recommit. To deliver wildly easier taxes for Americans, we can, and must, build an IRS that meets high modern expectations: fast, transparent, digital-first, and relentlessly taxpayer-focused.
The Diagnosis
Each year, the IRS collects more than 96% of the revenue that funds the federal government—$5.1 trillion supporting everything from Social Security, defense, infrastructure, veterans’ services, and investing in America’s future.
The quote from Justice Oliver Wendell Holmes, carved into the limestone face of the IRS headquarters in D.C., captures the spirit well:
“Taxes are what we pay for civilized society.”
It is not only essential to the functioning of government—it is also a major way most Americans interact with it. And that experience? Frustrating, costly, and confusing. According to a recent Pew survey, Americans rate the IRS less favorably than any other federal agency. The average taxpayer spends 13 hours and $270 out of pocket just to file their return.
The core problem: The IRS needs to be user-focused.
Despite the stakes, the IRS operates far behind what Americans expect. We live in a world where people can tap to pay, split bills by text, or trade stocks in slick apps. But that world does not include the IRS.
A staggering 63% of the 10.4 billion hours Americans spend dealing with the federal government are consumed by IRS paperwork. But much of the source of that pain isn’t the IRS, but Congress with the crushing complexity of decades long tax code changes, sedimented on top of each other. This year was no different. The “One Big Beautiful Bill” runs 331 pages, with large swaths devoted to new, intricate tax changes.
Dealing with the IRS still often involves paper forms, long phone waits, chasing down documents, and confusing processes.
If you’ve dealt with the IRS for anything beyond filing, it feels impossible to get a task finished. Will someone pick up the phone? Can I get an answer to my questions and resolve my situation? Would I expect the same answer if I talked to someone else? Last year the IRS answered just 49% of the 100 million calls it received, including automated answering.
This underperformance is beyond outdated technology—it’s structural and institutional. The IRS’s core systems are brittle and fragmented. Ancient procurement rules and funding constraints have made sustained modernization nearly impossible. Siloed organizations sit within siloes. In place of long-term investment, the agency leans heavily on short-term contractor fixes, band-aids applied to legacy wounds.
This complexity has stymied scaled change.
The root cause: The IRS has never treated world-class technology and product development as mission-critical capabilities core to its identity, to be hired, owned, and continually improved by internal teams focused on user outcomes.
A modern service agency builds end-to-end experiences for users—from pre-populating data through to filing and refunds. Empowered teams building these features have a holistic viewpoint and control over their service to ensure taxpayers are able to repeatedly and reliably complete their task.
Today’s reality is different: federal agencies like the IRS treat technical and product expertise as afterthoughts—all nice-to-haves that serve bureaucratic processes rather than core capabilities essential to their mission. Strategy and execution get outsourced by default. This creates a growing divide between “business” and “IT” teams, each lacking a deep understanding of the other’s work, despite both being critical to delivering services that actually function for taxpayers.
This outsourcing has hollowed out the agency’s internal technical capacity. Rather than building technical competency in-house, and paying that talent a salary approaching private companies, the IRS grows more dependent on vendors. It no longer knows what it needs technically, what questions to ask or which paths to pursue. Instead they must trust the vendors–companies financially incentivised towards ballooning scopes, lock-in, and complexity.
The result: a siloed experience that mirrors a siloed organization, one that is risk-averse, paper-heavy IRS, too slow to meet modern expectations.
The agency approaches service delivery as a compliance and bureaucratic process to digitize, rather than a product to design. “Never ship your org-chart” is a common refrain you’ll hear at tech companies, to explain how products tend to take on the communication style of their builders. Yet IRS product faultlines visibly follow its org structure and thus fail to deliver a holistic experience.
There were bright spots. Direct File showed what’s possible when empowered teams build for users. A dead simple idea: let Americans file taxes directly on the IRS site was a reality. It worked. It was well regarded. In surveys, users beamed about Direct File: 9 out of 10 gave it an “excellent” or “above average” rating, 74% said they preferred it over what they used before, and 86% said it increased their trust in the IRS.
The government actually delivered for its citizens, and they felt it.
But it didn’t last. The project was abruptly dismantled due to political ideology, not taxpayer experience or feedback.
Many of the people with the technical skills and vision to modernize the IRS have left, often without a choice. The agency will likely slide further backward—into deeper dependence on systems built by the lowest bidder or those currying political favor, with poorer service and diminished public trust in return.
We’ve seen this up close.
Both of us worked at The White House’s technology arm; the U.S. Digital Service. One of us helped lead Direct File into existence and built the Consumer Financial Protection Bureau’s digital team. The other previously led Google’s first large language model products and prototyped AI tools at the IRS to streamline internal knowledge work.
In our work at the IRS, we witnessed how far the agency must go. Inside the IRS Commissioner’s office, with leaders across the agency, we built a collaborative digital strategic plan. This memo details those proposals since left by the wayside after seven different IRS commissioners rotated in the seat, just this year.
The IRS needs more than modernization. It will need a systemic rebuild from:
- compliance, to user-centered design and product thinking
- vendor dependence to empowered internal product teams
- once-a-year panic to real-time, year-round services
- fragile mainframes to composable platforms and APIs
- waterfall contracting to iterative, continuous delivery
We’re sharing these recommendations for a future Day One—when there’s a refocus on rebuilding the government. When that day comes, the blueprint will be here: drawn from inside experience, built on hard lessons, and focused on what it will take to deliver a digital IRS that truly works for the American people.
What we need is the mandate to build a tax system that makes Americans think: “That was it? That was easy.”
Plan of Action
The IRS must rebuild taxpayer services around citizen needs rather than compliance and bureaucratic processes. This requires in-housing the talent to strategically build it. We propose establishing a Chief Digital Officer directly reporting to the Commissioner, with the authority to oversee digital and business transformation across the organization, hire hundreds of senior engineers, product managers, and designers. The goal, a team empowered to deliver a tax-filling product experience that meets modern expectations.
The Products
Build for Users, Not Internal Compliance
We’ve become accustomed to a user-focused fit-and-finish in the app era. Let’s deliver that same level for taxpayers.
It all starts around building a digital platform that empowers taxpayers, businesses, and preparers with the information, tools and services to handle taxes accurately and confidently. A fully-featured online account becomes the one-stop, self-service hub for all tasks. Taxpayers access their complete tax profile, updated in real-time, with current data across income sources, financial institutions, and full tax history. The system proactively recommends tax breaks, credits, and withholding adjustments they’re eligible for.
Critically, this can’t be built in a vacuum. It requires rapid iteration with users as part of a constant feedback loop. This digital platform runs on robust APIs that power internal tools, IRS public sites, and third-party software. Building this way ensures alignment across IRS teams, eliminates duplicate efforts, and lifts the entire tax software ecosystem.
This is what we need to build for Americans:
Online tax filing: From annual panic to year-round readiness
Reboot Direct File. Stop forcing everything into tax season. Let taxpayers update information year-round—add a child, change addresses, adjust withholdings, upload documents. When April arrives, their return is already 90% complete.
This is a natural evolution of Direct File and the existing non-editable online account dashboard into a living, breathing system taxpayers optimize throughout the year. And not just for individuals—this should be extended to businesses—reducing this burden for as many filer types as possible.
Pre-populated returns: Stop making people provide what the IRS already knows
The IRS already has W-2s, 1099s, and financial data. Use it. Pre-populate returns to cut filing time from hours to minutes. Deliver secure APIs so any tax software can access IRS data (with taxpayer permission), and use machine learning to flag issues including fraud before submission. This increases accuracy, reduces errors, and spurs competition by making it easy to switch between tax-filing programs.
Income verification as a service: Turn tax data into financial opportunity
The IRS sits on verified income data that could help Americans access government services, credit, mortgages, and benefits like student aid. Instead of weeks-long transcript requests, offer instant verification through secure APIs. This creates a government-backed source alongside credit bureaus, increases financial access, and reduces paperwork across all government services.
Tax calculator as a platform: One source of truth
Every tax software company recreates the same calculations, each slightly different. Across the organization, the IRS itself uses multiple third-party tax calculators in audits. This should be a core, integral service the IRS offers—build a definitive tax calculator as an API, the single source of truth that internal audits and checks use, and external software can access or run on their own. Make it transparent, auditable, and open source. Put up cash “bounties” to encourage the public to find bugs and errors and invite taxation-critics to review the code. Use generative AI to aid IRS accountants, lawyers and engineers translate tax law changes into code–speeding the roll out of Congressional tax changes.
When everyone calculates taxes the same way the IRS does, errors vanish. When everyone can see how the IRS does it, trust grows.
Modern MeF: From submission pipe to intelligent platform
Today’s Modernized e-File (MeF) is barely modern—it’s a dumb pipe that accepts tax returns and hopes for the best. Transform it into intelligent infrastructure that validates in real-time, catches errors immediately (not weeks later in confusing notices), and stops fraud before refunds are deposited. Build it like a real API, not XML dumps. Enable multi-part submissions so taxpayers can fix mistakes without starting over. This isn’t just a technical upgrade—it’s the foundation that makes every other improvement possible.
The Process
Ship Daily, Not Yearly
Taxpayer-first product development
The IRS is the single largest interaction point between Americans and their government. Every improvement saves millions of hours and builds trust. This requires abandoning bureaucratic processes for product thinking.
Build with taxpayers from day one through constant user testing and feedback loops. Organize around taxpayer journeys—”I need to update my withholdings” or “I’m checking my refund”—not org charts.
Measure what matters: time-to-file, satisfaction scores, error rates, not only compliance metrics. Internal Objectives and Key Results planning makes priorities clear and syncs the organization towards focused goals. Publish Service Level Objectives on external products to ensure we target creating systems that others can confidently rely and build on.
Give full-stack product teams the authority to make integrated technical, design, policy and legal decisions together. Staff these teams with internal technologists embedded alongside accountants and lawyers in functional organizations, building IRS competency while reducing contractor dependence. Today’s IRS is highly siloed across functions with authority so fragmented it’s unclear who “owns” what. Yet go to any top tech organization and you’ll see what we’re pushing for: aligned and cross-functional teams whose job is delivering with clear ownership. Inherently we’re pushing for more than a new team, we’re factoring out unclear ownership in general away from IT and Business Divisions.
When teams own outcomes, we can better ensure taxpayer experience transforms from painful to painless.
API-first architecture
The IRS is fundamentally a data organization, yet information flows through siloed systems that can’t talk to each other. Amazon solved this with a simple mandate: all teams must expose their data and communicate through APIs. (This mindset set in motion the seeds of Amazon Web Services, the company’s most profitable division).
The IRS needs the same revolution.
Every team exposes data and functionality through standardized REST APIs—no direct database access, no per-department clones of the data, no exceptions. Design every API to be externalizable (with strong access controls) from day one, unlocking government APIs to become platforms for innovation. When systems communicate through versioned APIs instead of tangled dependencies, teams can ship improvements daily without compromising everything else. This isn’t just technical architecture—it’s how modern organizations move fast without breaking things.
The People
Cultivate it, Don’t Outsource It; Build a Delivery Culture
A digital IRS that delivers for Americans cannot be built by the lowest bidder. Its core capability isn’t digitized forms–it’s people who can understand taxpayers’ needs, imagine solutions, design thoughtfully, ship them fast, listen to users, and keep improving based on feedback.
Silicon Valley understands this instinctively on two fronts. The fight for great engineers is the fight to build teams that can deliver great products. And two, no leading tech company outsources its own R&D. Delivering well-functioning and beloved products requires tight ownership of the product iteration loop.
Businesses long learned to never outsource a core competency. OpenAI would never outsource the training of its models, Apple its industrial design, Google its search algorithm, or Facebook its social graph. The same should be true for the IRS.
Yet, despite accepting 93% of its tax returns digitally, it still does not consider itself to be a digital-first agency. Building great teams is inseparable from building great taxpayer experiences. For decades, the agency has outsourced its technical mission and vision.
What we witnessed at the IRS was often vendor theater. Consultants transformed routine meetings into sales presentations that should have been dedicated to improving the products. Solutions specialists added layers of proprietary middleware, despite readily available enterprise-grade open source solutions running on commodity servers could easily meet the objectives. All of this unfolded within an organizational culture where securing contracts took precedence over delivering meaningful outcomes. Contracts that, of course, cost multiples more than the price of a competent internal team.
Commodities like cloud infrastructure or off-the-shelf software that serve broad, generic needs should absolutely be acquired externally. But the IRS’s critical, taxpayer-facing products—the systems at the heart of filing, payments, and taxpayer accounts—must be built and owned internally. There is only one agency that collects taxes for the United States of America.
When everything is handed to vendors, the IRS sends more than money out the door; it loses institutional memory, technical craft, quality systems, and the ability to move quickly. A modern IRS cannot be built on rented skills.
Talent: Build a Permanent Product Core
This transformation starts with the people: build and keep an in-house corps of top-tier technologists—engineers, product managers, designers, user experience researchers—working in small, empowered, cross-functional teams hand in hand with fellow IRS accountants, auditors, customer service representatives and lawyers. Not a handful of digital specialists scattered in a bureaucracy as it was, but several hundred people whose full-time job is delivering and evolving the IRS’s core taxpayer experiences and services.
- Create a dedicated Digital Profession inside the IRS, led by a Chief Digital Officer with the authority to hire, fire, and shape teams and technology stacks.
- Break the straitjacket of outdated civil service rules by creating specialist pay bands to compete for top talent like the CFPB has done.
- Empower cross-functional teams to ship without endless escalation. Start small, test early, iterate quickly, and make product decisions by those close to the work.
Funding: Invest in Teams, Not Projects
Current funding locks the IRS into one-off projects that end when the money runs out, leaving no path for iteration. A product-centered IRS needs enduring funding for enduring teams. Long-lived services, not short-lived milestones. This should be no surprise for a tax organization. There are two certainties in life; death and taxes. We should properly set ourselves up to manage the latter.
- Fund continuous development rather than one-and-done “delivery.”
- Tie funding to taxpayer outcomes like faster filing, fewer errors, higher satisfaction, instead of compliance checklists.
- Secure multi-year budgets for core product teams so they can improve services year-round, not scramble for appropriations each cycle.
This shift will reduce long-term capital costs and ensure that every dollar invested keeps improving the taxpayer experience.
Quality & Standards: Build Once, Build Right
Owning our products means owning their quality. That requires clear, enforceable service standards, like performance, usability, scalability, and accessibility, that every IRS product must meet.
- Establish service performance benchmarks and hold teams accountable to them. These should be highly taxpayer centric; time to file, support response time, ease of use.
- Create communities of practice inside the organization to share patterns, tooling, and lessons learned across the agency.
- Apply spend controls that tie contract renewals to measurable outcomes and prevent redundant vendor builds.
Culture Eats Strategy: Time to Invest in a Delivery Culture
“Culture eats strategy for breakfast,” as Peter Drucker famously said. Yet government agencies too often treat culture-building as off-limits or irrelevant. This is backwards. Creating a shared, collaborative culture centered on delivery isn’t just important; it’s the foundation that makes everything else possible. The hardest and most critical step is investing in people. Give employees space to collaborate meaningfully, contribute their expertise, and take ownership of outcomes. Leadership must empower teams with real authority, establish clear performance standards, and hold everyone accountable for meeting—or exceeding—those benchmarks. Without this cultural shift, even the best strategy becomes just another plan gathering dust.
When every product meets the same high standard, trust in the IRS will grow—because taxpayers will feel it in every interaction.
A template for all agencies
The IRS touches more Americans than any other federal agency–making it the perfect proof point that the government can deliver digital products that work seamlessly. The principles–build for users, not compliance, shipping daily, not yearly, and keeping the talent in house is not unique to the IRS.
We believe these goals and strategies apply to nearly every agency and level of government. Imagine Social Security retirement planning tools that lead to easy withholding adjustments, a Medicare/Medicaid that is easy to enroll in, or a FEMA with easy to file disaster relief disbursement.
Transform the IRS this towards this path, and then use these lessons to reset and lift up expectations between Americans and their government. One so easy citizens say: “That was it? That was easy.”
Analytical Literacy First: A Prerequisite for AI, Data, and Digital Fluency
As digital technologies reshape every aspect of society, students must be equipped and proficient in not only specialized literacies (such as digital literacy, data literacy, and AI literacy), but with a foundational skill set that allows them to think critically, reason logically, and solve problems effectively. Analytical literacy is the scaffolding upon which more specialized literacies are built. Students in the 21st century need strong critical thinking skills like reasoning, questioning, and problem-solving, before they can meaningfully engage with more advanced domains like digital, data, or AI literacy. Without these skills, students may struggle to engage critically with the technologies shaping their lives. We urge education leaders at the federal, state, and institutional levels to prioritize development of analytical literacy by incentivizing integration across disciplines, aligning standards, and investing in research and professional development.
Introduction
As society becomes increasingly shaped by digital technologies, data-driven decision-making, and artificial intelligence, the ability to think analytically is no longer optional, it’s essential. While digital, data, and AI literacies focus on domain-specific skills, analytical literacy enables students to engage with these domains critically and ethically. Analytical literacy encompasses critical thinking, logical reasoning, and problem-solving, and equips students to interpret complex information, evaluate claims, and make informed decisions. These skills are foundational not only for academic success but for civic engagement and workforce readiness in the 21st century.
Despite its importance, analytical literacy remains unevenly emphasized in K–12 education. These disparities are often driven by systemic inequities in school funding, infrastructure, and access to qualified educators. According to NCES’s Education Across America report, rural schools and those in under-resourced communities frequently lack the professional development opportunities, instructional materials, and technology needed to support analytical skill-building. In contrast, urban and well-funded districts are more likely to offer inquiry-based curricula, interdisciplinary projects, and formative assessment tools that foster deep thinking. Additionally, while some schools integrate analytical thinking through inquiry-based learning, project-based instruction, or interdisciplinary STEM curricula, there is no consistent national framework guiding its development at this time. Instructional strategies vary widely by state or district, and standardized assessments often prioritize procedural fluency over deeper cognitive engagement like analytical reasoning.
Recent research underscores the urgency of this issue. A 2024 literature review from the Center for Assessment highlights analytical thinking as a core competency for future success, noting its role in supporting other 21st-century skills such as creativity, collaboration, and digital fluency. Similarly, a systematic review published in the International Journal of STEM Education emphasizes the need for early engagement with analytical and statistical thinking to prepare students for a data-rich society.
There is growing consensus among educators, researchers, and policy advocates that analytical literacy deserves a more central role in K–12 education. Organizations such as NWEA and Code.org have called for stronger integration of analytical and data literacy skills into curriculum and professional development efforts. However, without coordinated policy action, these efforts remain fragmented.
This memo builds on that emerging momentum. It argues that analytical literacy should be treated as a skill that underpins students’ ability to engage meaningfully with digital, data, and AI literacies. By elevating analytical literacy through standards, instruction, and investment, we can ensure that all students are prepared to participate, innovate, and thrive in a complex and rapidly changing world.
To understand why analytical literacy must be prioritized, we examine the current landscape of specialized literacies and the foundational skills they require.
Challenges and Opportunities
In today’s interconnected world, digital literacy, data literacy, and AI literacy are no longer optional, they are essential skill sets for civic participation, economic mobility, and ethical decision-making. These literacies enable students to navigate online environments, interpret complex datasets, and engage thoughtfully with emerging technologies.
- Digital literacy encompasses the ability to use technology effectively and critically, including evaluating online information, understanding digital safety, and engaging ethically in digital environments.
- Data Literacy involves the capacity to understand, interpret, evaluate, and communicate data. This includes recognizing data sources, identifying patterns, and drawing informed conclusions.
- AI Literacy entails understanding the basic concepts of artificial intelligence, its applications, ethical implications, and how to interact with AI systems responsibly.
Together, these literacies form a cognitive toolkit that empowers students to be not just consumers of information and technology, but thoughtful participants in civic and digital life.
While these literacies address specific domains, they all fundamentally rely on what should be called Analytical Literacy. Analytical literacy, at its core, involves the ability to:
- Ask insightful questions. Identifying the core issues and seeking relevant information.
- Evaluate information critically. Assessing the credibility, bias, and relevance of sources.
- Identify patterns and relationships. Recognizing connections and trends in complex information.
- Reason logically. Constructing sound arguments and drawing valid inferences.
- Solve problems effectively. Applying analytical skills to find solutions and make informed decisions.
Yet, without structured development of these foundational skills, students risk becoming passive consumers of technology rather than active, informed participants. This presents an urgent opportunity: by centering Analytical Literacy in standards and assessment, instruction, and professional learning, we can create enduring pathways for students to participate, innovate, and thrive in an increasingly data-driven world.
Examples of implementation must include:
- In Standards and Assessment. States should revise academic standards to include grade-level expectations for analytical reasoning across disciplines. For example, middle school science standards might require students to construct evidence-based arguments using data, while high school civics assessments could include open-ended questions that ask students to evaluate competing claims in news media.
- In Instruction. Teachers should embed analytical skill development into daily practice through inquiry-based learning, Socratic seminars, or interdisciplinary projects. A math teacher could guide students in analyzing real-world datasets to identify trends and make predictions, while an English teacher might use argument mapping to help students deconstruct persuasive texts.
- In Professional Learning. Districts should offer workshops that train educators to use formative assessment strategies that surface student reasoning such as think-alouds, peer critiques, or performance tasks. Coaching cycles should focus on how to scaffold questioning techniques that push students beyond recall toward deeper analysis.
By embedding these practices systemically, we move from episodic exposure to analytical thinking toward a coherent, equitable framework that prepares all students for the demands of the digital age.
Addressing these gaps requires coordinated action across multiple levels of the education system. The following plan outlines targeted strategies for federal, state, and institutional leaders.
Plan of Action
To strengthen analytical literacy in K–12 education, we recommend targeted efforts from three federal offices, supported by state agencies, educational organizations, and teacher preparation programs.
Recommendation 1. Federal Offices
Federal agencies have the capacity to set national priorities, fund innovation, and coordinate cross-sector efforts. Their leadership is essential to catalyzing systemic change. For example:
White House Office of Science and Technology Policy (OSTP)
OSTP now chairs the newly established White House Task Force on Artificial Intelligence Education, per the April 2025 Executive Order on Advancing AI Education. This task force is charged with coordinating federal efforts to promote AI literacy and proficiency across the K–12 continuum. We recommend that OSTP:
- Expand the scope of the Task Force to explicitly include analytical literacy as a foundational competency for AI readiness.
- Ensure that public-private partnerships and instructional resources developed under the order emphasize reasoned decision-making as a core component, not just technical fluency.
- Use the Presidential Artificial Intelligence Challenge as a platform to showcase interdisciplinary student work that demonstrates analytical thinking applied to real-world AI problems.
This alignment would ensure that analytical literacy is not treated as an adjacent concern, but as a central pillar of the federal AI education strategy.
Institute of Education Sciences (IES)
IES should coordinate closely with the Task Force to support the Executive Order’s goals through a National Analytical Literacy Research Agenda. This agenda could:
- Fund studies that explore how analytical thinking supports AI literacy across grade levels.
- Evaluate the effectiveness of instructional models that integrate analytical reasoning into AI and computer science curricula.
- Develop scalable tools and assessments that measure students’ analytical readiness for AI-related learning pathways.
IES could also serve as a technical advisor to the Task Force, ensuring that its initiatives are grounded in evidence-based practice.
Office of Elementary and Secondary Education (OESE)
In light of the Executive Order’s directive for educator training and curriculum innovation, OESE should:
Prioritize analytical literacy integration in discretionary grant programs that support AI education.
Develop guidance for states on embedding analytical competencies into AI-related standards and instructional frameworks.
Collaborate with the Task Force to ensure that professional development efforts include training on how to teach analytical thinking—not just how to use AI tools.
National Science Foundation (NSF)
The National Science Foundation plays a pivotal role in advancing STEM education through research, innovation, and capacity-building. To support the goals of the Executive Order and strengthen analytical literacy as a foundation for AI readiness, we recommend that NSF:
- Establish a dedicated grant program focused on developing and scaling instructional models that integrate analytical literacy into STEM and AI education. This could include interdisciplinary curricula, project-based learning frameworks, and performance-based assessments that emphasize reasoning, problem-solving, and data interpretation.
- Fund research-practice partnerships that explore how analytical thinking develops across grade levels and how it supports students’ engagement with AI concepts. These partnerships could include school districts, universities, and professional organizations working collaboratively to design and evaluate scalable models.
- Support educator capacity-building initiatives, such as fellowships or professional learning networks, that equip teachers to foster analytical literacy in STEM classrooms. This aligns with NSF’s recent Dear Colleague Letters on expanding K–12 resources for AI education.
- Invest in technology-enhanced learning tools that provide real-time feedback on student reasoning and support formative assessment of analytical skills. These tools could be piloted in diverse school settings to ensure equity and scalability.
By positioning analytical literacy as a research and innovation priority, NSF can help ensure that K–12 students are not only technically proficient but cognitively prepared to engage with emerging technologies in thoughtful, ethical, and creative ways.
Note: Given the evolving organizational landscape within the U.S. Department of Education—including the elimination of offices like Educational Technology—it is critical to identify stable federal anchors. The agencies named above have longstanding mandates tied to research, policy innovation, and K–12 support, making them well-positioned to advance this work.
Recommendation 2. State Education Policymakers
While federal agencies can provide vision and resources, states hold the levers of implementation. Their role is critical in translating policy into classroom practice.
While federal agencies can provide strategic direction and funding, the implementation of analytical literacy must be led by states. Each state has the authority—and responsibility—to shape standards, assessments, and professional development systems that reflect local priorities and student needs. To advance analytical literacy meaningfully, we recommend the following actions:
Elevate Analytical Literacy in Academic Standards
States should conduct curriculum audits to identify where analytical skills are currently embedded—and where gaps exist. This process should inform the revision of academic standards across disciplines, ensuring that analytical literacy is treated as a foundational competency, not an ancillary skill. California’s ELA/ELD Framework, for example, emphasizes inquiry, argumentation, and evidence-based reasoning across subjects—not just in English language arts. Similarly, the History–Social Science Framework promotes critical thinking and source evaluation as core civic skills.
States can build on these models by:
- Developing cross-disciplinary analytical literacy frameworks that guide integration from elementary through high school.
- Embedding analytical competencies into STEM, humanities, and career technical education standards.
- Aligning revisions with the goals of the Executive Order, which calls for foundational skill-building to support digital and AI literacy.
Invest in Professional Development and Instructional Capacity
States should fund and scale professional learning ecosystems that equip educators to teach analytical thinking explicitly. This includes:
- Training on inquiry-based learning, Socratic dialogue, and formative assessment strategies that surface student reasoning.
- Development of microcredential pathways for educators to demonstrate expertise in fostering analytical literacy across content areas.
- Support for instructional coaches and teacher leaders to model analytical practices and mentor peers.
California’s professional learning modules aligned to the Common Core State Standards and ELA/ELD frameworks offer a useful starting point for designing scalable, standards-aligned training.
Redesign Student Assessments to Capture Deeper Thinking
States should move beyond traditional standardized tests and invest in assessment systems that measure analytical reasoning authentically. States can catalyze this innovation by issuing targeted Requests for Proposals (RFPs) that invite districts, assessment developers, and research-practice partnerships to design and pilot new models of assessment aligned to analytical literacy. These RFPs should prioritize:
- Performance tasks that require students to analyze real-world problems and propose solutions.
- Portfolio assessments that document students’ growth in reasoning and problem-solving over time.
- Open-ended questions that ask students to evaluate claims, synthesize evidence, and construct logical arguments.
- Scalable models that can inform statewide systems over time.
By using the RFP process strategically, states can surface promising practices, support local innovation, and build a portfolio of assessment approaches that reflect the complexity of students’ analytical capabilities.
Recommendation 3. Professional Education Organizations
Beyond government, professional education organizations shape the field through resources, advocacy, and collaboration. They are key partners in scaling analytical literacy.
Professional education organizations play a vital role in shaping the landscape of K–12 education. These groups—ranging from subject-specific associations like the National Council of Teachers of English (NCTE) and the National Science Teaching Association (NSTA), to broader coalitions like ASCD and the National Education Association (NEA)—serve as hubs for professional learning, policy advocacy, resource development, and field-wide collaboration. They influence classroom practice, inform state and federal policy, and support educators through research-based guidance and community-building.
Because these organizations operate at the intersection of practice, policy, and research, they are uniquely positioned to champion analytical literacy as a foundational skill across disciplines. To advance this work, we recommend the following actions:
- Develop Flexible, Discipline-Specific Resources. Create adaptable instructional materials—such as lesson plans, assessment templates, and classroom protocols—that help educators integrate analytical thinking into diverse subject areas. For example, NCTE could develop resources that support argument mapping in English classrooms, while NSTA might offer tools for teaching evidence-based reasoning in science labs.
- Advocate for Analytical Literacy as a National Priority. Publish position papers, host public events, and build strategic partnerships that elevate analytical literacy as essential to digital and civic readiness. Organizations can align their advocacy with the federal directive for AI education, emphasizing the role of analytical thinking in preparing students for ethical and informed engagement with emerging technologies.
- Foster Cross-Sector Collaboration. Convene working groups, research-practice partnerships, and educator networks to share best practices and scale effective models. For example, AERA could facilitate studies on how analytical literacy develops across grade levels, while CoSN might explore how digital tools can support real-time feedback on student reasoning.
By leveraging their convening power, subject-matter expertise, and national reach, professional education organizations can accelerate the adoption of analytical literacy and ensure it is embedded meaningfully into the fabric of K–12 education.
Recommendation 4. Teacher Preparation Programs
To sustain long-term change, we must begin with those entering the profession. Teacher preparation programs are the foundation for instructional capacity and must evolve to meet this moment.
Teacher preparation programs (TPPs) are the gateway to the teaching profession. Housed in colleges, universities, and alternative certification pathways, these programs are responsible for equipping future educators with the knowledge, skills, and dispositions needed to support student learning. Their influence is profound: research consistently shows that well-prepared teachers are the most important in-school factor for student success.
Yet many TPPs face persistent challenges. Too often, graduates report feeling underprepared for the realities of diverse, data-rich classrooms. Coursework may emphasize theory over practice, and clinical experiences vary widely in quality. Critically, few programs offer explicit training in how to foster analytical literacy—despite its centrality to digital, data, and AI readiness. In response to national calls for foundational skill-building and educator capacity, TPPs must evolve to meet this moment.
While federal funding for teacher preparation has become more limited, states are stepping in through innovative models like teacher residencies, registered apprenticeships, and microcredentialing pathways. These initiatives are often supported by modified use of Title II funds, state general funds, and workforce development grants. To accelerate this momentum, federal programs like Teacher Quality Partnership (TQP) grants and Supporting Effective Educator Development (SEED) grants could be adapted to prioritize analytical literacy, while states can issue targeted RFPs to redesign coursework, practicum experiences, and capstone projects that center reasoning, problem-solving, and ethical decision-making. To ensure that new teachers are ready to cultivate analytical thinking in their students, we recommend the following actions:
- Integrate Analytical Pedagogy into Coursework and Practicum. Embed instructional strategies that center analytical literacy into pre-service coursework. This includes training in inquiry-based learning, argumentation, and data interpretation. Practicum experiences should reinforce these strategies through guided observation and practice in real classrooms.
- Ensure Faculty Model Analytical Thinking. Faculty must demonstrate analytical reasoning in their own teaching—whether through modeling how to deconstruct complex texts, facilitating structured debates, or using data to inform instructional decisions. This modeling helps pre-service teachers internalize analytical habits of mind.
- Strengthen Field Placements for Analytical Instruction. Partner with districts to place candidates in classrooms where analytical literacy is actively taught. Provide structured mentorship from veteran teachers who use questioning techniques, performance tasks, and formative assessments to surface student reasoning.
- Develop Capstone Projects Focused on Analytical Literacy. Require candidates to complete a culminating project that demonstrates their ability to design, implement, and assess instruction that builds students’ analytical skills. These projects could be aligned with state standards and local district priorities.
- Align Program Outcomes with Emerging Policy Priorities. Ensure that program goals reflect the competencies outlined in federal initiatives like the AI Education Executive Order. This includes preparing teachers to support foundational literacies that enable students to engage critically with digital and AI technologies.
Together, these actions form a coherent strategy for embedding analytical literacy across the K–12 continuum. But success depends on bold leadership and sustained commitment. By reimagining teacher preparation through the lens of analytical literacy, we can ensure that every new educator enters the classroom equipped to foster deep thinking, ethical reasoning, and problem-solving—skills that students need to thrive in a complex and rapidly changing world.
Conclusion
Analytical literacy is not a nice-to-have, it is a prerequisite for the specialized proficiencies students need in today’s complex world. By embedding critical thinking, logical reasoning, and problem-solving across the K–12 continuum, we empower students to meet challenges with curiosity and discernment. We urge policymakers, educators, and institutions to act boldly by demanding analytical literacy be established as a cornerstone of 21st-century education. and co-create a future where every student has the analytical tools essential for meaningful participation, innovative thinking, and long-term success in the digital age and beyond.