DOE 4.0: Rethinking Program Design for a Clean Energy Future
DOE’s mission and operations have undergone at least three iterations: starting as the Atomic Energy Commission after World War II (1.0), evolving into the Department of Energy during the 1970s Energy Crisis to focus on a wider range of energy research & development (2.0), and then expanding into demonstration and deployment over the last 20 years (3.0). The evolution into DOE 3.0 began with the Energy Policy Act of 2005, which authorized the Loan Programs Office (LPO), and accelerated with the infusion of funding from the American Recovery and Reinvestment Act of 2009. Finally, the Bipartisan Infrastructure Law (BIL) and the Inflation Reduction Act (IRA) crystallized DOE 3.0’s dual mandate to not only drive U.S. leadership in science and technology innovation (as under DOE 1.0 and 2.0), but also directly advance U.S. industrial development and decarbonization through project financing and other support for infrastructure deployment.
While DOE continues to support the full spectrum of research, development, demonstration, and deployment (RDD&D) activities under this dual mandate, the agency is now undergoing another transformation under the Trump administration, as a large number of career staff leave the agency and programs and budgets are overhauled. The Federation of American Scientists (FAS) is launching a new initiative to envision the DOE 4.0 that emerges after these upheavals, with the goals of identifying where DOE 3.0 missed opportunities and how DOE 4.0 can achieve the real-world change needed to address the interlocking crises of energy affordability, U.S. competitiveness, and climate change.
Crucial to these goals is rethinking program design and implementation to ensure that DOE’s tools are fit for purpose. BIL and IRA introduced new types of programs and assistance mechanisms, such as Regional Hubs and “anchor customer” capacity contracts, to try to meet the differing needs of demonstration and deployment activities compared to R&D. Some were a clear success, while others faced implementation challenges. At the same time, the majority of funding from these two bills was still implemented using traditional grants and cooperative agreements, which did not always align with the needs of the commercial-scale projects they sought to support. Based on lessons learned from the Biden administration, this report provides recommendations to DOE to improve the implementation of different types of assistance and identifies opportunities to expand the use of flexible and novel approaches. To that end, this report also advises Congress on how to improve the design of legislation for more effective implementation.
The ideas and insights in this report were informed by conversations with former DOE staff who played a role in implementing many of these programs and experts from the broader clean energy policy community.
Distribution of BIL and IRA Funding
Before diving into program design, it’s helpful to first understand the range of technologies and activities that BIL and IRA programs were meant to address, especially where that funding was concentrated and where there may have been gaps, since programs should be tailored to the purpose.
Authorizations and Appropriations
Congress intentionally provided the lion’s share of BIL and IRA funding to demonstration and deployment activities. The table above shows the distribution of BIL and IRA authorizations and appropriations for DOE. The table excludes DOE’s revolving loan programs – the Tribal Energy Financing Program (TEFP), the Advanced Technology Vehicles Manufacturing Loan Program (ATVM), the Title XVII Innovative Energy Loan Guarantee Program (Title 1703), the Title XVII Energy Infrastructure Reinvestment Financing Program (Title 1706) – which are discussed in the following section.1 The Carbon Dioxide Transportation infrastructure Finance and Innovation program (CIFIA) was included in the table above because that program’s appropriations could be used for both grants and loan credit subsidies.
The technology areas that received the most DOE funding from BIL and IRA (excluding loans) were building decarbonization, grid infrastructure, clean power – combining solar, wind, water, geothermal, and nuclear power, energy storage systems, and technology neutral programs – carbon management, and manufacturing and supply chains, which each received over $10 billion in funding.
Below is a breakdown of the funding distribution for each sector/technology.
Grid Infrastructure received a total of $14.9 billion, second only to building decarbonization. All of the funding went towards demonstration and deployment programs, the majority ($10.5 billion) of which went towards the Grid Resilience and Innovation Partnerships (GRIP) program. The remainder of the funding went towards Grid Resilience State and Tribal formula grants, the Energy Improvement in Rural and Remote Areas, Transmission Facilitation Program, and transmission siting and planning programs. No funding went to R&D or workforce programs. Grid infrastructure was also eligible for the Title 17 and Tribal loans programs.
Power Generation received a total of $13.2 billion, with funding unevenly distributed across technologies and stages of innovation. Nuclear power received the largest share, with over $9.2 billion allocated to the Advanced Reactor Demonstration Program and the Civil Nuclear Credit Program, supporting demonstration of advanced reactors and production incentives to maintain existing nuclear plants, respectively. Geothermal energy received the least funding among power generation technologies, with only $84 million allocated to the Enhanced Geothermal Systems (EGS) Demonstration Program and no other support for R&D or deployment.
Modest amounts were provided for RD&D in solar ($80 million), wind ($100 million), and water power technologies ($146 million). For deployment, hydropower also received production and efficiency incentives to support existing facilities ($754 million); wind energy received funding for Interregional and Offshore Wind Electricity Transmission Planning and Development ($100 million); and solar qualified for the Renew America’s Schools program ($500 million). To complement these technologies, $505 was provided for energy storage demonstration programs to enable reliable deployment of variable renewables.
Power generation was also eligible for the Title 17 and Tribal loan programs.
Manufacturing and Supply Chains received $10.8 billion in funding from BIL and IRA. The majority of that funding, $6.3 billion, went towards battery supply chains, primarily for the Battery Materials Processing Program ($3 billion) and the Battery Manufacturing and Recycling Program ($3 billion). Additional focus areas for funding included EV manufacturing ($2 billion), advanced energy manufacturing and recycling ($750 million), high-assay low-enriched uranium (HALEU) supply chains for nuclear power plants ($700 million), and heat pump manufacturing ($250 million). Energy manufacturing and supply chains are eligible for Title 1703 loans, while EV and battery manufacturing and supply chains are eligible for ATVM loans.
Critical Minerals received a total of $6.9 billion, of which $6 billion was allocated for the Battery Materials Processing Program and the Battery Manufacturing and Recycling Program, which funded demonstration and commercial-scale critical minerals processing and recycling projects. The remainder of the funding went to R&D programs on mining, processing, and recycling technologies; technologies to recover critical minerals from coal-based industry, mining and mine waste, and other industries; and technologies that use less critical minerals or replace them with alternatives. Critical minerals were also eligible for all of DOE’s revolving loan programs, except for CIFIA.
Industrial Decarbonization and Efficiency received a total of $7.5 billion. Six ($6.0) billion of this funding went towards the Industrial Demonstrations Program (IDP), which was sector and solution agnostic and accepted projects for both new facilities and retrofits, making the money extremely flexible. Much smaller funding amounts were allocated to deployment and workforce programs like rebates for energy efficient technologies and systems, decarbonizing energy manufacturing and recycling facilities, and Industrial Training and Assessment Centers. No funding was allocated to R&D programs.
Hydrogen and Clean Fuels received $8 billion for the Regional Clean Hydrogen Hubs program to support near-term demonstration and commercialization of hydrogen production, transportation, and usage. Hydrogen and clean fuels were also eligible for all of the loan programs, except for CIFIA. Investment across the full research-to-deployment (RDD&D) continuum was lacking. Dedicated funding for clean fuels besides hydrogen was also missing.
EVs and Transportation funding from BIL and IRA was largely focused on light-duty personal EVs. By contrast, investments in medium- and heavy-duty vehicles and urban transportation were limited.
EV manufacturing and supply chains received $8.3 billion in funding. The largest single allocations went to the Battery Materials Processing and Battery Manufacturing & Recycling Programs ($6 billion), strengthening domestic battery supply chains for EVs. Domestic Manufacturing Conversion grants ($5 billion), further supported downstream manufacturing of advanced EV technologies. Additional funding supported R&D for battery recycling and second-life applications. EV and battery manufacturing were also eligible for ATVM loans.
A notable new focus for DOE under BIL was the deployment of EV charging infrastructure. Charging infrastructure was eligible for $1.05 billion in DOE funding through the Renew America’s Schools program and the Energy Efficiency and Conservation Block Grant Program. DOE played a key role in the Joint Office of Energy and Transportation’s implementation of the National Electric Vehicle Infrastructure (NEVI) Formula Program, funded by DOT ($5 billion), and other charging programs. This marks a shift from DOE’s previous focus on developing vehicle technologies and fuels to a broader focus on all of the technology and infrastructure needs for widespread EV adoption.
Building Decarbonization and Efficiency received the most non-loan funding from BIL and IRA at $15.2 billion. The largest share of this funding, $12 billion, went towards deployment and affordability programs such as the Home Energy Efficiency Rebate Program, High-Efficiency Electric Home Rebate Program, and the Weatherization Assistance Program – all of which aim to reduce energy costs for low-income households by increasing the energy efficiency of their homes. Additional funding supported workforce training and the improvement of building codes. Little to no funding went to R&D and demonstration programs, signaling the relative maturity of building decarbonization and efficiency technologies compared to other sectors. District heating and cooling facilities are eligible for TEFP loans.
Carbon Management received a total of $11.6 billion. The majority of the funding went towards demonstration and deployment activities, of which $2.1 billion went towards CIFIA to support the deployment of transportation infrastructure, $2.5 billion went towards carbon storage validation and testing, $3.0 billion went towards carbon capture pilots and demonstrations, and $3.5 billion went towards the development of Regional Direct Air Capture (DAC) Hubs. Carbon management was also eligible for loans from the Title 17 programs.
Loans
DOE’s loan programs operate differently from the way authorizations and appropriations work for traditional assistance programs, which is why they are not included in the chart above. These programs receive both a certain amount of loan authority, which set limits on the size of their portfolios, and appropriations for program administration and credit subsidies, which allows the office to provide low-cost financing. The IRA appropriated $13.8 billion total for these four programs and provided an additional $310 billion in loan authority for Title 1703, Title 1706, and TFP. CIFIA was established in the IRA without a cap on its loan authority. The IRA also repealed the cap on ATVM’s loan authority, which remains uncapped.2
During the four years of the Biden administration, the Loan Programs Office (LPO), now renamed the Office of Energy Dominance Financing (EDF), issued a total of 24 loans and 28 conditional commitments, worth over $100 billion in total. Energy storage, battery manufacturing, clean power, and the grid received the greatest number of loans and conditional commitments, while nuclear energy, carbon management, and non-battery or EV manufacturing received the least. No loans were issued for CIFIA, which is why that program is not shown in the following figures.
Program Design & Implementation
Flexible Contracting Mechanisms: Grants vs. Other Transactions
The majority of BIL and IRA funding (excluding loans) was implemented in the form of grants and cooperative agreements governed by 2CFR 200 and 2CFR 910. Even for programs for which the legislation did not specify the exact type of assistance mechanism that DOE should use (i.e., unspecified or “financial assistance”), the agency largely defaulted to those grants and cooperative agreements. One argument for this approach was that program officers and contracting officers are trained and experienced in using these mechanisms, which may have helped programs deploy faster.
However, these grants were originally designed for R&D programs and faced some drawbacks when used for demonstration and deployment programs. 2CFR 200 and 2CFR 910 are almost 200 pages long, requiring extensive compliance that smaller organizations and organizations new to federal applications may not be equipped to navigate. Additionally, some terms and conditions required by those rules (e.g. for intellectual property, real property, and program income) were not compatible with private sector needs for demonstration and commercial-scale projects. Most consequentially, they require a termination for convenience clause, which allows the government to cancel an award without providing a reason. The Trump administration is now using that clause to terminate awards.
Alternatively, DOE could have more frequently used its Other Transaction Authority (OTA) to enter into contracts without 2CFR regulations, allowing the agency to negotiate contracts more like the private sector would, developing terms and conditions as they make sense for the purpose of the specific purpose. This can enable DOE to design and implement more creative arrangements, such as for demand-pull or market-shaping mechanisms. DOE could have also leveraged OTs to make process improvements, rethink the traditional solicitation and evaluation process, and potentially accelerate implementation.3
DOE 3.0 missed a major opportunity to leverage these benefits of OTs. The few exceptions were the Hydrogen Demand Initiative (H2DI), the Advanced Reactor Demonstration Program, and Partnership Intermediary Agreements. Towards the end of the Biden administration, DOE discussed transitioning some of OCED’s awards to OT agreements, but did not get a chance to follow through before the presidential transition.4
DOE 4.0 should pick up where DOE 3.0 and deploy OTs more broadly among demonstration and deployment programs to overcome the challenges of traditional financial assistance regulations and processes. Congress should ensure that future authorizing legislation is designed to enable this flexibility–for example, by not specifying the type of assistance that DOE should use to implement new programs.
Flexible Funding
BIL and IRA authorized and appropriated funding for a wide range of programs, many with very specific goals and eligible uses. That approach allows Congress to provide detailed direction to DOE on legislators’ priorities. However, DOE should also be able to respond dynamically to industries and markets as they develop. For example, when BIL and IRA were being developed, next-generation geothermal technologies were still quite nascent and received very little funding from these bills. Within two years though, the technology rapidly advanced, thanks to the success of the first few demonstration projects, and now shows enormous potential for meeting clean, firm energy demand, but DOE has limited funding available to support the industry.
In future legislation, Congress should consider establishing a few flexible funding programs that would give DOE a greater range of options to support the development of energy technologies and infrastructure as the agency’s experts know best. This could look like a pooled pot of funding with broad authority for DOE to use across technologies and/or activities, such as a single fund for demonstration and deployment activities broadly, or a single fund for grid infrastructure needs. If Congress is wary about this, legislators could start with creating flexible funding programs designed to fit within the scope of a single DOE office, before testing programs that cross multiple offices, which may come with intra-agency coordination challenges.
Program Design: Regional Hubs
The Hydrogen Hubs and Regional Direct Air Capture (DAC) Hubs were a new type of program established by BIL, designed to fund clusters of projects located in different regions rather than individual, unrelated projects. BIL invested $7 billion and $3.5 billion in these programs, respectively, and they made some of the largest awards by dollar amount – on the order of $1 billion per award – out of all of the BIL and IRA programs.
The hub approach aimed to foster an industrial ecosystem, including not only multiple projects aiming to deploy the technology, but also future suppliers, offtakers, labor organizations, academic partners, and state, local, and Tribal governments. Concentrated regional investment and greater coordination would not only accelerate commercialization of hydrogen and DAC technologies but also help distribute the benefits of new clean energy industries across the nation.
Due to the ambitious size and complexity of their goals, the Hydrogen Hubs and DAC Hubs required, and still require, a long timeline to develop. The structure and oversight DOE applied to the hub development process also extended timelines further. When the Trump administration began re-evaluating Biden-era programs and Congress started looking for funds to rescind, these two programs became appealing targets because of the large amount of funding they held and the lack of on-the-ground deployment progress – even though that was to be expected based on the program timeline.5
Project cancellations and funding rescissions are a massive waste of both federal and private sector resources. In the future, before creating any other large-scale programs modeled on the Hydrogen Hubs and DAC Hubs, policymakers should first determine whether there is long-term bipartisan commitment to the program’s goals to avoid the possibility that a change of administration will jeopardize the program. If that commitment isn’t guaranteed, this model may simply be too risky to use; other types of assistance may be easier to implement or more resilient to changes in administration.
An alternate regional hub model that Congress and DOE could consider is the CHIPS and Science Act’s Regional Technology and Innovation Hubs and NSF Engines. These programs had a much lower level of ambition, providing awards – on the order of tens of millions instead of one billion – to seed early-stage innovation, build a research ecosystem, and support workforce development, rather than deploying specific technologies.
Program Design: Demand-Pull
Demand-pull mechanisms have emerged in conversations between FAS and former DOE staff as a very underutilized but promising tool for enabling the scaling and deployment of clean energy technologies and large-scale infrastructure projects. Confidence in long-term offtake is a requirement for private lenders to provide financing at a viable rate for projects. DOE can help provide that certainty through a wide range of tools, including purchase commitments and capacity contracts, contracts-for-difference, and other financial arrangements.
By unlocking private sector investment, demand-pull mechanisms can reduce or eliminate the need for DOE to provide additional financing for project construction. However, public sector funding is still useful for pre-construction stages of project development, such as planning, siting, and permitting, which can be hard to get private sector financing for when other risks to a long-term revenue model have not been addressed yet.
There are three primary use cases for demand-pull mechanisms: building shared infrastructure, demonstrating innovative technologies, and expanding industrial capacity.
Shared infrastructure projects require a large number of customers and can sometimes struggle with securing them: customers are afraid to commit without the developer demonstrating that they’ve secured other customers first. DOE can help address this challenge by serving as an anchor customer for these projects and help attract additional customers. This also makes it easier to finance the project.
A successful example of this from BIL is the Transmission Facilitation Program, which authorized DOE to purchase up to 50% of the planned capacity of large-scale transmission lines for up to 40 years. Once the transmission line is built, DOE can then sell capacity contracts to actual customers who need to use the transmission line and recoup the agency’s investment. This approach could be used for other types of shared infrastructure, such as hydrogen or carbon dioxide transportation, or even large clean, firm power plants (e.g., nuclear) for their generation capacity.
First-of-a-kind projects often struggle to secure offtakers due to the unproven nature of their technology and the lack of a pre-existing market. For example, H2DI was designed to complement the Hydrogen Hubs program by directly supporting demand for select hydrogen producers and also helping establish a transparent strike price for the nascent market that would benefit all hydrogen producers. Other demonstration programs (e.g. IDP) would have also benefited from DOE support for demand and market formation.
Lastly, the development of new industrial capacity for producing energy technologies and their inputs can also face demand challenges because while there may be a pre-existing global market, the domestic market may be small or nonexistent, and existing offtakers may not be willing to reroute their supply chains without market or policy pressure to do so. This was most obvious with the critical minerals and battery supply chain projects that DOE tried to support.
One successful model from the IRA was the HALEU availability program. DOE set up indefinite delivery, indefinite quantity contracts with companies developing HALEU production capacity and set aside $1 billion to procure HALEU from the five fastest movers. The purchase commitment created demand certainty, while the competitive model incentivized faster project development and ensured that the DOE’s funding would only go towards the most viable projects. More programs like this would be transformative for domestic supply chain development.
In designing demand-side support programs for these latter two categories, DOE must tailor the programs to the unique challenges of different technologies or commodities, and whether or not there are additional goals of domestic market formation and/or market stabilization. For example, auctions are a great tool for price discovery, while contracts-for-difference can help projects hedge against price volatility and overcome domestic price premiums.
There are also double-sided market maker programs where DOE serves as an intermediary between producers and buyers, entering into long-term offtake commitments with project developers up front to provide demand certainty, and then reselling the product to buyers on a shorter-term basis when the project comes online This helps make supply chain connections and address mismatches between project developer vs. buyer timelines. For example, for low-carbon cement and concrete, buyers typically procure building materials on a short-term basis as needed for each project, but developers of first-of-a-kind production facilities require long-term offtake commitments in order to secure project financing.
Authorizing language and/or appropriations can be a barrier to DOE using demand-pull mechanisms. To address this issue, Congress should factor the following considerations into the design of legislation:
- Flexible Authorities. Due to the variety of demand-pull mechanisms and the need to tailor them to the unique market challenges of different technologies or commodities, they are best implemented using OT agreements. Statutory language that prescribes the exact type(s) of assistance (e.g., grants) for a program can prevent DOE from using demand-pull. Instead, Congress should provide clear goals for a program to achieve and leave DOE with the flexibility to determine the best type of assistance mechanism.
- Budget Scoring and Timelines. Demand-pull mechanisms often involve multi-year advance commitments of funding, but the exact amount and timing of transactions may be uncertain, since it is conditional upon project performance and overall market conditions (e.g. contracts-for-difference payments are based on the market price at the time of the transaction). This results in budget scoring issues. Legally binding commitments of money can typically only be made if the agency has enough funding to obligate the full amount of the contract when it is signed, even if that funding probably won’t be paid out until much later.6 This results in the need for a significant amount of upfront funding, which can be difficult to obtain from Congress, and long timelines before the outcome of that funding is fully realized, which can make it difficult to manage congressional expectations. These long timelines also mean that no-year funding is ideal for DOE to be able to run demand-pull programs without the funding expiring.7
- Revenue Management. Some demand-pull mechanisms are designed with the potential for revenue generation, so legislation should ideally be designed to include the authorization of a revolving fund to allow revenue to be reused for program costs. Alternatively, DOE may contract with an external entity to manage the program funds, as it did with H2DI, so that the revenue can stay with the partner entity and be reused.
Program Design: Prizes
Unlike most financial assistance, which operates on a cost-reimbursement basis and requires cost-share, prizes reward performance and are awarded after activities are completed and criteria have been met. This means there are no strings attached to the funding and no IP requirements, making these programs easier for applicants to work with.8 Prizes are also of a fixed amount, which incentivizes innovators to find least-cost solutions in order to maximize revenue from the award. On the flip side, innovators are responsible for any cost overruns, and DOE is not required to shoulder that risk.
In the past DOE has used prizes wrongly to try and reach potential applicants that struggle with the application process for traditional assistance. It’s important to keep in mind the best use cases for prize programs. For example, prize programs rely on clear milestones, but are agnostic on the approach, making them great for interdisciplinary innovation. They can be beneficial for incentivizing new innovators to get involved with problem areas that don’t have many pre-existing solvers. They are also well-suited for small dollar amount awards that otherwise may not be worth the administrative overhead, since the overhead costs for prize programs are lower than traditional assistance programs once they have been designed.
Moving forward, DOE should keep in mind best practices for designing equitable prize programs. Prize programs should ideally be designed as stage-gated competitions with incremental prize payments for each phase, rather than one big payment at the end, so that innovators with fewer financial resources can participate. For example, the first stage could be the submission of a whitepaper with a proposed plan for developing and testing the technology, then the second stage could be lab work, and so on. Participants would be whittled down between each stage to hone in on the most competitive projects.
Program Design: Loans
DOE 4.0’s loan programs could be improved by setting clearer expectations on risk, clearer guidance on State Energy Financing Institution (SEFI) projects, and a strategy for using additional tools such as equity.
Risk Tolerance. Discrepancies between statutory language and congressional oversight for DOE’s loan programs have historically made it difficult for the agency to determine the right balance of risk. For example, Title 1703 is designed by legislation to fund innovative, higher-risk, hard infrastructure projects that the private sector is typically reluctant to fund. A high-risk, high-reward program should, by nature, be allowed to have some failed projects and still be considered a success. However, Congress has historically been extremely critical of any defaulted loans, making DOE hesitant to use Title 1703 and ATVM to its full potential.
DOE 3.0 made some attempts to improve communications on its approach to risk management, but the agency could do more to communicate the success of its loan programs. Congressional authorizers should help the agency by building risk into the statute of DOE’s loan programs and budgets and better managing the expectations of oversight members.
State Energy Financing Institution (SEFI) Projects. Another area of reform that DOE 4.0 should tackle is the SEFI-supported projects under Title 17, authorized by BIL, which allows DOE to finance any energy project that also receives “meaningful financial support” from a SEFI, such as state energy offices or green banks. However, ambiguity in the statute behind this new carveout caused confusion among states on how exactly to partner with DOE’s loan program. What is considered meaningful financial support? What qualifies as a SEFI? To clarify these questions from states, either DOE 4.0 should create model SEFI guidance or Congress should amend the statute with clear definitions.
Equity and Other Financing Tools. The Trump administration’s restructuring of the Lithium Americas Thacker Pass loan to include an equity warrant, which gives DOE the right to acquire equity of the company at a set price in the future, has raised questions as to what DOE’s role should be if it were to become an equity owner in a company and what guardrails and visibility is needed in such a scenario.9 Policymakers may also want to consider the risks and benefits of expanding DOE’s loan program authorities to include direct equity investments and other financing tools that agencies like the International Development Finance Corporation (DFC) have access to.10
Program Design: Technical Assistance
DOE 4.0 should expand its technical assistance offerings in three primary ways: technical advising and verification, navigating federal funding, and talent and workforce needs.
Technical Advising and Verification. DOE’s in-house scientific and engineering expertise is a major draw for funding applicants. For example, according to FAS conversations with former agency staff, the project developers behind Vogtle Units 3 and 4, which received a loan guarantee from DOE, would seek advice from LPO engineers when they had engineering questions. Private investors, who may lack the expertise needed for technical due diligence, often use DOE awards as a proxy for assessing project risk. As a result, some project developers will apply for DOE funding to prove their credibility to private financiers and negotiate lower financing rates.
In the face of potential budget cuts, DOE 4.0 could leverage this strength by offering project certifications that would entail the same technical support and verification as a demonstration award or loan, without the funding support. This would provide a similar market signal to private investors, without costing DOE as much – just staff time. And since DOE is not taking on any project risk, the application and negotiation process could also be simplified and streamlined to align better with private-sector timelines.
Navigating Federal Funding. DOE should dedicate increased resources to conducting outreach to underserved communities, small businesses, innovators, and new applicants about funding opportunities and shepherding them through the application process. For example, despite awareness of available funding opportunities, some Native American tribal organizations in Alaska were unable to pursue them due to a lack of bandwidth or expertise to participate in resource-intensive (and often times confusing) application processes, and the awards sizes were too small to make them worth the costs of external private consultants to support. Community Navigator Programs and other forms of technical assistance could help communities overcome these barriers to accessing federal support. PIAs can also help with reaching small businesses and new applicants to apply for programs.
Talent and Workforce Needs. DOE has had success with placing talent at state energy offices and other critical energy organizations like public utility commissions through the Energy Innovator Fellowship to embed expertise in under-resourced offices. DOE should consider expanding this program or establishing new programs to place experts at other institutions, such as grid operators, investor owned utilities, and local governments, to advise and support them in adopting new energy technologies and accelerating infrastructure deployment.
Program Design: Community Benefit Plans
For all of its demonstration and deployment programs, DOE 3.0 introduced a new requirement that awardees create community benefit plans (CBPs) to ensure that communities would share in the benefits of local clean energy projects. CBPs have been both lauded and criticized by community and labor organizations: they praised their intent, but expressed frustration over their limited influence on companies’ plans and that allowable cost limits constrained what could be included in awards. Where CBPs were most effective, they encouraged developers to consider local communities and jobs, though this often required significant internal coordination to use DOE’s funding contracts as leverage. At the same time, CBPs were seen as an additional administrative burden on program implementation, contributing to delays. Under the Trump administration, CBPs will no longer be enforced and are no longer required for future funding opportunities.
DOE 4.0 presents an opportunity to restore and improve CBPs as a mechanism for both distributing the benefits of federally-funded projects and improving project quality. To maximize impact, DOE 4.0 should focus on a smaller set of high-priority outcomes with clear, measurable success metrics. DOE 3.0’s broad mandate, which spanned jobs, justice, climate, and deployment across multiple programs, sometimes diluted effectiveness and created confusion for staff managing both program design and operations. In DOE 4.0, these outcomes should be closely linked to actual project success, whether through facilitating social license to ease permitting, or supporting workforce development to train and retain workers, as developers themselves emphasized when aligning with program goals. Providing actionable guidance, including templates and real-world examples of successful community benefits plans, can further improve project outcomes. The advocacy community can help lay the groundwork for DOE 4.0 by documenting successful case studies and model agreement language. Congress could help embed key priorities in statute, providing clear, practical guidance that reflects DOE’s administrative capacity and enhances the likelihood of successful implementation.
Additionally, it is critical that future CBP mechanisms account for community preferences, including local prohibitions on certain technologies and other expressions of community priorities. By proactively respecting local concerns, DOE can foster trust and strengthen the long-term impact of projects. DOE 4.0 will also need to navigate tensions around labor preferences. While the department cannot explicitly require union labor, questions about labor practices may signal preferences that vary across states, including right-to-work contexts. This underscores the importance of sensitivity to local norms and expectations.
Where resources allow, DOE 4.0 should hire and dedicate staff with expertise in labor engagement and community partnerships to review applications and provide technical assistance, supporting applicants in navigating the CBP process and designing high-quality, community-centered projects. Technical assistance needs to be done carefully though to avoid perceptions of bias and influencing the award selection process.
Lastly, clear and consistent guidance across DOE offices is essential. For example, applicants have reported a lack of clarity about what activities qualify as “allowable costs” in CBPs, and different offices have applied inconsistent standards. Establishing a unified, expansive approach to allowable costs—including activities that indirectly support clean energy workforce development, such as community child care programs—can unlock transformative opportunities for local communities. This standardization should be done for other aspects as well. In general, official guidance needs to find a better middle ground between the overly technical, lengthy documents and vague webinars produced by DOE 3.0, so that ideally applicants can understand requirements without staff intervention.
Conclusion
Good program design is fundamental to effectively engaging with researchers, industry, state and local governments, and communities, in order to realize the full potential of DOE funding. Though much of the real-world impact of BIL and IRA is still yet to come, DOE can already begin learning from the challenges and successes of program design and implementation under the Biden administration. The recommendations in this report are just as applicable to the remaining funding from BIL and IRA that DOE has yet to implement, as they are to future programs. Moving forward, Congress has the opportunity to reconsider the way that programs are designed in future legislation, especially those targeting demonstration and deployment activities, and make sure that DOE has clear direction and the right authorities and flexibility to maximize the impact of federal funding.
Acknowledgements
The authors would like to thank Arjun Krishnaswami for coining the idea of DOE 4.0 and his insightful feedback throughout the development and execution of this project. The authors would also like to thank Kelly Fleming for her leadership of the clean energy team while she was at FAS. Additional gratitude goes to Claire Cody at Clean Tomorrow, Gene Rodrigues, Keith Boyea, Kyle Winslow, Raven Graf and all the other individuals and organizations who helped inform this report through participating in workshops and interviews and reviewing an earlier draft.
Appendix A. Acronyms
Appendix B. BIL and IRA Funding Distribution Methodology
The funding distribution heat map at the beginning of the report includes all of the BIL and IRA programs with funding authorized and/or appropriated directly to DOE, excluding loan programs. The following were not included in this table:
- Loan programs, which are funded differently than traditional programs;
- Tax credits that DOE helped design (e.g., 45X), which are also funded through a different mechanism; and
- Programs implemented by DOE, but funded by other agencies’ appropriations, such as the Methane Emissions Reduction Program funded by the Environmental Protection Agency.
Programs were tagged according to their sector or technology area, their activity area, and type of assistance based on key words in their statutory language. Programs could be tagged with multiple sectors/technologies, activity areas, and/or types of assistance.
To determine the amount of funding for each sector/technology and activity area combination, all of the programs with the corresponding tags were included in the sum. Because of this duplicative counting, the sum of the dollar amounts in the table exceeds the total amount of funding for all of these programs. Sector/technology totals were calculated without this duplication, which is why those amounts are less than what one would obtain by summing all of the activity area amounts for a sector/technology.
Activity area categories:
- “R&D” includes funding for programs covering research, development, and/or pre-commercial pilots.
- “Demonstration” includes funding for demonstration and commercial pilot programs using innovative technologies.
- “Deployment” includes funding for project planning, financing, and offtake; siting and permitting; and the development of standards or codes.
- “Workforce” includes educational outreach, training programs, apprenticeships, and other workforce development programs.
- “Energy Access and Affordability” refers to funding to lower the cost of energy for low-income households and to support the development or improvement of energy infrastructure for rural and remote areas and tribal nations. Some of these programs involve multiple sectors/technologies (see below).
- “National Labs Infrastructure” refers to programs funding construction and facility upgrades at national labs.
Sector/technology categories:
- “Grid infrastructure” refers to programs focused on any part of the transmission network between power generation facilities and consumer households or facilities, plus the planning, operations, and management of grid and the interconnection of new generation or loads to the grid. These were primarily programs implemented by the former Grid Deployment Office or the Office of Electricity.
- “Power: Technology Neutral” refers to programs supporting power generation or storage that any zero-emission generation technology was eligible for.
- “Power: Solar Energy”, “Power: Wind Energy”, “Power Hydro and Marine Energy”, “Power: Geothermal Energy”, “Power: Nuclear Energy”, and “Power: Energy Storage Systems” refers to programs focused on the underlying technologies and the demonstration and deployment of power generation and storage facilities using these technologies. Demonstration and deployment programs for the manufacturing of these energy technologies and input materials and components (e.g. battery manufacturing or HALEU fuel) were not included in these categories, but rather under the “Manufacturing and Supply Chains” category.
- “EV Charging Infrastructure” refers to programs supporting charging infrastructure for EVs of any weight class.
- “Critical Minerals” refers to programs supporting the mining, processing, recycling, and recovery from non-traditional sources of materials on either DOE’s Critical Materials List or the U.S. Geological Service’s Critical Minerals list.
- “Manufacturing and Supply Chains” refers to programs supporting the manufacturing of energy technologies and their input components and materials, as well as advanced manufacturing technologies in general. This category can overlap with both “Critical Minerals” (e.g. the Battery Materials Processing Program) and “Industrial Decarbonization/Efficiency” (e.g. the Advanced Energy Manufacturing & Recycling Grants Program)
- “Industrial Decarbonization & Efficiency” refers to programs supporting the reduction or elimination of carbon emissions from manufacturing industries.
- “Building Decarbonization & Efficiency” refers to programs supporting the reduction or elimination of carbon emissions from building heating, cooling, and electricity consumption. The manufacturing of building technologies was not included in this category, but rather the “Manufacturing and Supply Chains” category.
- “Hydrogen and Clean Fuels” had only one program, the Regional Clean Hydrogen Hubs.
- “Carbon Management” refers to programs supporting the capture (point source and direct air), transportation, utilization, and storage of carbon dioxide.
- “Cross-cutting” refers to programs that are not specific to any one sector or technology.
One Year into the Trump Administration: DOE’s FY26 Budget Cuts and the Path Forward
This piece is the last in a series analyzing the current state of play at DOE, one year into the second Trump administration. The first piece covers staff loss and reorganization; the second piece looks at the status of BIL and IRA funding and the impact of award cancellations.
Overview of DOE Funding for FY26
On January 15th, Congress passed the FY26 E&W Appropriations as part of a second minibus along with the Commerce, Justice, Science and the Interior and Environment Appropriations (bill text and joint explanatory statement). Assuming the President signs this package into law, it will dictate DOE’s funding through the rest of FY26, which ends in September, and potentially into FY27 if any continuing resolutions are passed in the next appropriations cycle.
Though the administration originally requested drastic cuts to all of DOE’s offices involved in clean energy RDD&D, the FY26 E&W Bill takes a much more restrained approach to budget cuts and reprograms some BIL funds to bolster EERE, NE, FE, and SC budgets. Notably, Congress increased appropriations levels for SC, NE, and SCEP, despite DOE’s request to zero out the budget for SCEP. Overall, compared to FY25, the FY26 Appropriations enact a 1.4% cut to the agency’s budget – a modest amount compared to DOE’s original request for a steep 7.0% cut.
The passage of the FY26 E&W Appropriations is a major accomplishment for Congress, especially given the short timeline over which the conferenced bill came together and the rejection of the deep cuts advocated for by this administration. Nevertheless, even minor cuts threaten to decelerate progress on energy innovation, manufacturing, and infrastructure necessary for the United States to meet energy demand growth, reliability, affordability, and security challenges – precisely when we need it the most. As we begin the FY27 appropriations process this year, it’s all the more important that Congress not only maintain stable funding levels for DOE, but also begin to rebuild momentum for energy innovation and technological progress.
Reallocation of Unobligated BIL Funds
Section 311 of the FY26 E&W bill repurposes $5.16 billion in unobligated funding from BIL for the following programs:
- $1.28 billion from the Civil Nuclear Credit Program;
- $1.5 billion from the Carbon Dioxide Transportation Infrastructure Finance and Innovation program (CIFIA);
- $1.04 billion from the Regional Direct Air Capture (DAC) Hubs;
- $950 million from the Carbon Capture Large-Scale Pilot Projects and the Carbon Capture Demonstration Projects; and
- $394 million from BIL programs funded through EERE’s account, including those implemented by MESC and SCEP.
The Civil Nuclear Credit Program is a new addition that was not present in either the House or the Senate’s original versions of the E&W bill. The other programs targeted for reallocation and the corresponding amounts were all proposed in either the House and/or the Senate’s original versions of the E&W bill. Notably, funding for the Hydrogen Hubs was spared after conferencing, despite previous inclusion in both chambers’ E&W bills.
The reprogrammed funds are to be used as follows:
- $3.1 billion for NE to be used for the Advanced Reactor Demonstration Program;
- $375 million for the Grid Deployment Office “to enhance the domestic supply chain for the manufacture of distribution and power transformers, components, and materials, and electric grid components, including financial assistance, technical assistance, and competitive awards for procurement and acquisition”;
- $1.15 billion for EERE activities;
- $100 million for NE activities;
- $140 million for FE activities;
- $150 million for SC activities; and
- $150 million for Title 17.
These moves reflect Congress’ emphasis on advanced nuclear demonstration projects, growing concern over grid supply chain bottlenecks, and continued commitment to funding EERE activities, as well as skepticism about the goals and execution of carbon management demonstration programs.
Zooming in: EERE Suboffices
DOE’s FY26 budget request proposed a major contraction of the EERE portfolio, explicitly requesting zero funding for four sub-accounts Hydrogen and Fuel Cell Technologies, Solar Energy Technologies, Wind Energy Technologies, and Renewable Energy Grid Integration. For the first three, the Department argued that these technologies had reached sufficient market maturity to rely primarily on private capital—which is definitely not the case for hydrogen and fuel cell technologies, and inconsistent with DOE’s continued funding for more mature technologies such as nuclear, coal, and gas. For Renewable Energy Grid Integration, DOE argued that the work would be absorbed into other programs. DOE also sought to near-eliminate the budget for the Building Technologies Office (BTO) and the Vehicle Technologies Office (VTO) by requesting only $20 million and $25 million, respectively, signaling a broader retreat from technologies that would support electrification, energy efficiency, and affordability.
Congress largely rejected wholesale eliminations in the FY26 bill they passed. Compared to FY24 and FY25 enacted levels, the deepest cuts for FY26 were for Solar Energy Technologies (31%) and Wind Energy Technologies (27%). Hydrogen and Fuel Cell Technologies was also targeted for deep cuts in the original House and Senate appropriations bills, but ended up with only a 6% budget cut after conferencing and passage, putting the office in a better position than many of the other EERE suboffices that lost more than 10% of their annual budget. The only two offices that received budget increases were Geothermal Technologies (27%) and Water Power Technologies (10%), reflecting Congress’ prioritization of clean firm energy technologies.
EERE suboffice funding amounts are dictated in the Joint Explanatory Statement, a report that accompanies annual appropriations bills and provides detailed guidance on how funds are to be allocated within the topline account numbers set by the appropriations bill. Historically, agencies have always adhered to report language; even under full-year continuing resolutions, agencies would still follow the funding guidance set in the prior fiscal year’s report language.
The second Trump administration broke this precedent: DOE’s FY25 spend plan – released more than three-quarters of the way through the fiscal year – shifted more than $1 billion away from core clean energy programs under EERE, disregarding Congressional direction in the FY24 appropriations report.1 DOE moved funding away from Vehicle, Hydrogen and Fuel Cell, Solar, Wind, and Building Technologies, towards Renewable Energy Grid Integration and Water Power, Geothermal, Industrial, and Advanced Materials and Manufacturing Technologies. These actions have raised concerns about whether the administration will attempt to do the same in FY26.
Zooming in: National Labs
The Joint Explanatory Statement does not provide guidance on how DOE allocates funding to national labs, though there tends to be a trickle down effect depending on which offices labs are reliant on funding from. DOE proposed drastic cuts to the FY26 budgets of many national labs, particularly those that get a significant amount of funding from EERE. Under the proposed budget cuts, the national labs would reportedly plan to lay off 3,000 or more scientists and other staff.
The National Renewable Energy Laboratory (NREL) – recently renamed the National Lab of the Rockies, or NLR for short – faces the largest proposed budget cut of 72% because it’s affiliated with EERE and gets the majority of its funding from that office. Such deep cuts would require NLR to lay off up to a third of its staff and shut down many of its facilities and ongoing activities.
With the passage of FY26 appropriations, hopefully, DOE will reconsider funding for national labs and adjust budgets upwards to reflect the much milder cuts that Congress passed.
Long-Term Impacts
Sustained budget cuts to DOE pose significant long-term risks to the nation’s scientific enterprise and ability to compete globally. Because DOE is the federal government’s primary engine for energy research and advanced technology commercialization, reductions in funding have both immediate operational consequences, as well as lasting structural ones.
Budget cuts translate directly into workforce attrition across DOE program offices, national laboratories, and partner institutions. When staffing levels fall, the federal government’s capacity to execute world-leading scientific research diminishes. Essential functions like managing user facilities, overseeing complex R&D portfolios, and ensuring the continuity of long-term research programs are all jeopardized, slowing the pace of innovation and limiting the nation’s ability to respond to emerging scientific and energy challenges.
Loss of program funding and workforce capacity raises a broader strategic concern: the U.S. may no longer retain the scientific and engineering talent necessary to develop next-generation energy technologies. DOE plays a critical role in cultivating and sustaining technical talent pipelines through early-career research programs, national lab fellowships, university partnerships, and long-term R&D initiatives that span decades. When the continuity of these programs is disrupted, students, postdocs, and mid-career researchers may exit the field entirely or shift their expertise abroad, diminishing the domestic talent base. These losses cannot be quickly reversed as rebuilding a skilled scientific workforce takes sustained investment, stability, and opportunity signals that cuts fundamentally undermine.
Attrition is not limited to DOE itself. The broader U.S. science and innovation workforce – spanning clean energy startups, universities, private-sector R&D, and communities that host national laboratories – absorbs the shock of federal retreat. Reduced research funding forces universities to shrink labs, scale back graduate cohorts, and limit collaborations with DOE facilities. National laboratory communities, often in rural or specialized high-tech regions, face economic consequences when jobs disappear or major facilities reduce their operating capacity. The ripple effects of lost researchers, technical staff, and support personnel weaken the entire innovation ecosystem that underpins clean energy deployment.
Quantifying these long-term losses is essential. Each scientist or engineer who leaves the field takes with them years of specialized training, intellectual and institutional capital, and future contributions to technological advancement. The economic value of these foregone innovations – from delayed commercialization timelines to missed breakthrough discoveries – can be substantial. A shrinking innovation pipeline also slows private-sector investment domestically and increases dependence on imported technologies at a moment when global competition in clean energy, advanced computing, and critical minerals is accelerating.
In the long run, sustained budget cuts compromise the United States’ ability to remain a global leader in science and innovation. They jeopardize advancements in energy innovation, undermine national competitiveness, and reduce the nation’s capacity to deliver affordable, secure, and clean energy solutions. Protecting DOE’s workforce and research infrastructure is therefore not only a matter of annual appropriations, but also a long-term investment in America’s economic strength and technological leadership.
Conclusion: The Path Forward
As we begin the second year of the second Trump administration, DOE sits upon the precipice of transformation. Over the past year, the rapid pace and unprecedented scale of changes to the agency’s staff, organizational structure, programs and awards, and budget have generated waves of uncertainty and volatility that has rippled out across the energy sector, destabilizing commercial projects worth billions of dollars, as well as DOE’s relationship with the private sector, state and local governments, its own career staff.
After all these changes, whether DOE transforms for better or worse will depend on the decisions this administration makes over the next three years. Realizing this administration’s priorities of energy dominance and abundance will require DOE to rebuild its technical and organizational capacity to design and implement programs, oversee loans and awards, and engage in public-private and intergovernmental partnerships.
This should start with carefully managing the agency’s reorganization and providing clearer, more detailed explanations to the public on the mandate and internal structure of new offices and where existing programs and activity areas have been moved, and guidance to employees about how the reorganization will impact their roles and the programs on which they work. DOE leadership should then evaluate the functions and capacities missing under the new organizational structure and rehire for those roles, ideally with the reinstatement of remote work flexibility.
As the agency rebuilds internal capacity, it should reorient efforts away from reacting to the previous administration and towards actions that will build the infrastructure necessary to modernize and expand the energy system, ensure reliability and affordability in the face of demand growth, secure energy supply chains, and maintain U.S. leadership in energy innovation. The wave of funding opportunity announcements for BIL critical minerals programs over the past few months was a good start, but that is not DOE’s only mandate. DOE must also restart activities across other technologies and sectors. Luckily, the agency still has $30 billion plus in funding from BIL and IRA that has yet to be awarded. In implementing the remaining funding, DOE can learn from the many lessons learned reports on the previous administration’s experience and adopt internal reforms. The agency should also make sure to adhere closely to the statutory intent behind this funding.
Lastly, stable year-to-year funding is essential for progress. As Congress begins the FY27 appropriations process this month, congress members should also turn their eyes towards rebuilding DOE’s programs and strengthening U.S. energy innovation and reindustrialization. Higher DOE funding levels will be necessary to put the United States back on a growth trajectory with respect to global energy leadership and competitiveness.
Acknowledgements
The authors would like to thank Megan Husted and Arjun Krishnaswami for their pivotal roles in shaping the vision for this project, planning and executing the convenings that informed this report, and providing insightful feedback throughout the entire process. The authors would also like to thank Kelly Fleming for her leadership of the project team while she was at FAS. Additional gratitude goes to Colin Cunliff, Keith Boyea, Kyle Winslow, and all the other individuals and organizations who helped inform this report through participating in workshops and interviews and reviewing an earlier draft.
One Year into the Trump Administration: DOE Awards Cancelled and Programs Stalled
This piece is the second in a series of analyzing the current state of play at DOE, one year into the second Trump administration. The previous piece on staff loss and reorganization can be read here.
Introduction
$25.8 billion in BIL appropriations, over a third of the total amount, have yet to be awarded, plus up to $4.3 billion in IRA funding left after OBBBA rescissions. Yet, for the entire first year of the Trump administration, DOE has focused primarily on undoing the work of the prior administration. Politically motivated award cancellations and the delayed distribution of obligated funds have broken the hard-earned trust of the private sector, state and local governments, and community organizations. DOE also carried out a significant internal reorganization that eliminated many of the commercialization and deployment focused offices and moved their programs into other offices, leaving their futures unclear.
The implementation of remaining BIL and IRA funding has been stalled across the board (except for critical minerals-related programs), and the administration has attempted to push the limits of legislative interpretation by redirecting funds for carbon capture and rural and remote energy improvements towards bringing inactive coal power plants back into service and/or extending the life of coal plants near retirement.
Overview of BIL and IRA Funding Status
BIL and IRA appropriated $71 billion and $35 billion, respectively, in funding for DOE clean energy programs. Once appropriated, DOE funding moves through three phases before being received by awardees:
- First, funding is awarded when DOE selects and announces the recipients for a program. Only 57% of BIL funding and 52% of IRA funding was awarded by the end of the previous administration.
- Then, funding is obligated when DOE legally commits the amount to the recipient through a contractual agreement. Obligations may be made in phases over time, especially if the award is of a large amount. Thirty-three percent (33%) of BIL funding has been obligated as of December 17th, 2025.
- Finally, funding is outlayed when the money is paid to the recipient(s) and officially transferred out of the federal government’s account. This can occur in installments over the course of the period of performance or through a single up-front payment. Four point eight percent (4.8%) of BIL funding has been outlayed as of December 17th, 2025.
Under the current administration, at least $11 billion, or 32%, of unobligated IRA funding was rescinded through the One Big Beautiful Bill Act (OBBBA), including the IRA credit subsidy appropriations for DOE’s loan programs, while $5.16 billion in BIL funding was transferred for other purposes by the Fiscal Year 2026 (FY26) Energy and Water Development (E&W) bill. Mass rescissions and reallocations of funding on this scale have been unheard of in the past.
A further $6.8 billion in BIL awards and $2.5 billion in IRA awards have been cancelled by the Department of Energy, primarily because they do not align with the new administration’s priorities. For BIL, the cancellations will impact 17% of awarded funding, 14% of obligated funding, and 3% of outlayed funding. For IRA, the cancellations will impact 7% of awarded funding. While DOE has in the past made one-off cancellations of individual awards for various reasons, mass cancellations on this scale are unprecedented and uniquely destructive to the relationship between DOE and the private sector, not to mention state and local governments and community organizations.
Award Cancellations
The first round of DOE award cancellations were announced in May 2025. The 24 cancelled awards, worth $3.7 billion, all came from OCED programs funded by BIL and IRA. The Industrial Demonstration Program (IDP) was the most severely impacted: 18 awards worth $3 billion, half of the total for the program, were cancelled. The other primary targets from this round of cancellations were the Carbon Capture Demonstrations Program and the Carbon Capture Large-Scale Pilots Program.
In early October 2025, DOE announced the cancellation of another 321 awards, worth over $8 billion. Of those awards, five from the IDP were duplicates from the May announcement. Once again, OCED’s programs were the most heavily impacted, with GDO a close second. The largest awards cancelled were the two west coast Hydrogen Hubs, each worth at least $1 billion and three of the Grid Resilience and Innovation Program (GRIP) awards located in California, Minnesota, and Oregon. Unlike the first round, other DOE awards not funded by BIL or IRA, roughly half of the list, were also cancelled. These awards primarily came from EERE and FE.
Only about 1.5% of the funding for these BIL and IRA awards was outlayed before they were cancelled. Non-BIL and IRA awards fared slightly better, with 38% of funding outlayed before they were cancelled. As a result of these cancellations, awardees may decide to abandon their projects entirely, which would end up wasting the hundreds of millions of dollars of federal funding that has already been spent.
The most direct impact of these cancellations is that communities that were promised jobs and other benefits will no longer get them. DOE is breaking its commitment to companies, workers, and other stakeholders, taking away the economic opportunity that new investments provided.
Moreover, federal funding would not be the only funding wasted: many of the canceled awards came with matching private-sector investments, totaling over $5.7 billion. In order for those private-sector investments to be put to use, project developers would need to seek additional funding to close the gap left by cancelled DOE awards. Even in the best case scenario, that process requires additional time and effort, resulting in delays and higher overall project costs.
The vast majority of these private-sector investments were intended to fund grid resilience and modernization projects. In the face of demand growth and grid reliability challenges, particularly from data centers, it seems counterintuitive to pull funding from these projects rather than doubling down on investments to improve and expand our grid infrastructure. These cancellations also run counter to the administration’s stated priority of “unleashing American energy” and will make it harder to provide the electricity needed to power the AI applications and innovations touted by this administration.
An additional list of projects has been circulating since the beginning of October, said to contain an additional $16 billion worth of projects being considered by DOE for cancellation. In late October 2025, Politico’s E&E News reported that DOE confirmed the cancellation of five of the projects on that list, totaling $718 million in funding, because they were not “economically viable.” All of the projects were funded by the Office of Manufacturing and Energy Supply Chains (MESC), which had been largely spared by the previous rounds of cancellations. Four of the cancelled awards were from the Battery Materials Processing and Battery Manufacturing Grant Programs, while the other award came from the Advanced Energy Manufacturing and Recycling Program. Since then, at least one of the projects, a lithium iron phosphate plant in Missouri, has folded, partially as a result of the DOE award cancellation.
In response to the cancellations, most companies are challenging the decision and seeking as much compensation as they can through the courts. The Supreme Court has ruled that challenges to the termination of specific awards must be filed through the U.S. Court of Federal Claims, which is understaffed and struggling with significant backlogs and delays. However, while large companies may be able to wait six months or up to one year for compensation, many small businesses and startups will go under if they cannot get recourse in time and run out of funding to keep paying their employees. Furthermore, the Federal Claims Court does not have the authority to reinstate terminated grants or contracts, which is what companies actually want.
A coalition of energy and environmental organizations filed a lawsuit over seven of the cancelled grants and won, arguing that DOE’s termination decisions were politically motivated and thus illegal, targeting awards primarily because they were located in blue states and/or funded clean energy technologies that the administration opposes. Those seven award cancellations have now been blocked by the judge’s decision, but the hundreds of other cancellations will continue unless additional lawsuits are brought forth.
All of this has resulted in a growing belief across the private sector (and also local governments and community organizations) that federal grants and contracts are no longer guaranteed to survive a change in administration. This destroys the trust built by 50 years of DOE upholding its contracts and commitments to the private sector. The Biden administration expanded this partnership with the private sector further, conducting significant outreach to improve interest from top tier companies in BIL and IRA programs. Now, all of that hard-won trust has been undone.
Members of Congress from both sides of the aisle have been watching these cancellations with concern. Section 301 of the FY26 E&W Bill introduces a new requirement that DOE must notify both the House and Senate Appropriations Committees at least three full business days before the agency issues a letter to terminate a grant, contract, other transaction agreement, or lab call award in excess of $1 million. The same requirement applies to any letter to terminate nonoperational funding for a national lab if the total amount is greater than $25 million.
Loan Cancellations, Delays, and New Terms
In addition to reevaluating and cancelling awards, DOE leadership also reevaluated the loans and conditional commitments made under the Biden administration, slowing down the evaluation process. So far, DOE has publicly terminated a $4.9 billion conditional commitment for the Grain Belt Express transmission. DOE was also reported to have plans to cancel six more conditional commitments and one active loan, totaling $8.5 billion. Former LPO staff have shared that these terminations were mutually agreed upon between the borrowers and DOE due to project economics. Some of this administration’s policies (e.g. the permitting ban on wind energy projects) may have indirectly contributed to worsening project economics.
Under the current administration, DOE has moved some projects that align with the White House’s priorities from conditional commitment to close – namely, AEP’s transmission upgrades and Wabash Valley Resources’ Coal-Powered Fertilizer Facility – and fast tracked a loan to restart the Three Mile Island Crane nuclear unit directly to close. However, for other projects less aligned with this administration’s priorities, DOE appears to be delaying the process to move conditional commitments forward and close out the loans. Former agency staff from the office claim that this is a way to softly cancel loans by putting timelines in limbo and waiting out the borrower, since conditional commitments have a maximum window of two years to either move to close or be rejected.
Changes to the term sheet when closing a loan is another way to force applicants out of the pipeline. Applicants typically receive an initial term sheet with the conditional commitment and then a final term sheet when closing the loan; applicants may not be able to accept or accommodate drastic changes between the two.
Notably, this administration restructured Lithium Americas’ Thacker Pass loan after it was closed, but before funds were disbursed. LPO has the right to restructure loan terms and get new conditions or concessions to protect taxpayer resources if there are concerns, but this is rarely done. LPO negotiated the right to 5% equity in Lithium Americas and 5% equity in the Thacker Pass joint venture in the form of a warrant. The agency statement points to LPO’s loan to Tesla in 2010 as precedent for using warrants. This move raises the question of whether LPO will be negotiating additional equity stakes in future loan agreements, given this administration’s many other equity deals.
Remaining BIL & IRA Funding and Awards
Loans are not the only thing DOE has slow-walked: recipients of active BIL and IRA awards have complained that DOE also delayed the distribution of obligated funds and was not paying invoices in a timely manner. This issue was especially acute in the beginning of 2025, when many grants and contracts were frozen and recipients were told to stop all work while new DOE leadership reviewed their funding. While some projects were allowed to move forward, some remained in limbo even towards the end of 2025, causing significant uncertainty and financial stress to awardees.
As for the remaining unobligated BIL and IRA funds, DOE has not issued any new funding opportunity announcements (FOAs), except for critical minerals-related programs, which have been favored by this administration, and a repurposing of BIL funding to support coal power plants:
- FE issued two FOAs for piloting byproduct critical minerals and materials recovery and mine technology proving grounds. MESC issued an FOA for a rare earth elements demonstration facility and a notice of intent to issue an FOA for round three of the Battery Materials Processing and Battery Manufacturing and Recycling Grant Program.
- FE issued an $525 million FOA “to expand and reinvigorate America’s coal industry.” Up to $175 million of funding would come from BIL funding for energy improvements in rural and remote areas. The remaining $350 million would come from BIL funding for the Carbon Capture Demonstration Projects Program and the Carbon Capture Large-Scale Pilot Projects, which both have unobligated balances as a result of prior award cancellations. Critics have questioned the legality of repurposing the carbon capture program funds in this way, since the FOA allows federal funding to be used for near-term reliability upgrades “without requiring immediate Carbon Capture Utilization and Storage (CCUS) installation,” even though the Congress specifically directed this funding to be used “to demonstrate the construction and operation of six facilities to capture carbon dioxide from coal electric generation facilities, coal electric generation facilities, natural gas electric generation facilities, and industrial facilities” and specifically two of each kind.1
Acknowledgements
The authors would like to thank Megan Husted and Arjun Krishnaswami for their pivotal roles in shaping the vision for this project, planning and executing the convenings that informed this report, and providing insightful feedback throughout the entire process. The authors would also like to thank Kelly Fleming for her leadership of the project team while she was at FAS. Additional gratitude goes to Colin Cunliff, Keith Boyea, Kyle Winslow, and all the other individuals and organizations who helped inform this report through participating in workshops and interviews and reviewing an earlier draft.
Appendix: Methodology for BIL and IRA Funding Analysis
Data on total BIL and IRA appropriations and award amounts was obtained from the archived Invest.gov website created by the Biden administration’s White House. Loan amounts were not included, since loan authority is separate from appropriations. The archived Invest.gov website has not been updated since the end of the Biden administration. As of December 17th, 2025, the Trump administration has not made any new awards yet with BIL or IRA funding, so the data should be accurate up to that date.
Data on obligations and outlays came from the Department of Treasury’s USA Spending database. The total amount of obligations and outlays of BIL funding for DOE was determined by filtering for the Disaster Emergency Fund Codes for Infrastructure Spending associated with BIL and DOE as the Awarding Agency. All assistance awards and contracts that resulted from these filters were included in the total amounts.
The obligations and outlays for cancelled BIL and IRA awards in October were determined by searching the database for each unique award ID found in the list obtained by Latitude Media. The total amount of obligations and outlays for cancelled BIL and IRA awards in May was determined by searching the database for the awardees in the list reported by The New York Times and matching the award amounts, award location, and/or award description. All available data up until December 17th, 2025 was included. USA Spending tracks the amount of obligations and outlays for each award that came from BIL; this data was used to determine whether or not a cancelled award was funded by BIL. Whether or not a cancelled award was funded by the IRA was determined based on whether or not the award description explicitly mentions IRA and/or searching official DOE announcements and other public documents for the specific award using the recipient name and award description available on USA Spending. Any remaining awards were assumed to be funded by neither BIL nor IRA.
In this report, the total amount of unobligated funding rescinded by OBBBA is a minimum estimate. The minimum rescission amount for every loan program listed in Section 50402 of the OBBBA was determined by subtracting the total funding obligated from the loan program account between FY23 and FY25 (found on USA Spending) from the total appropriations for the program from the IRA (found in the bill text). The minimum rescission amount for every other program listed in Section 50402 of the OBBBA was determined by subtracting the total funding awarded for the program from the total appropriations for the program (both obtained from Invest.gov).
What’s New for Nukes in the New NDAA?
At the time of publication, the NDAA had passed both chambers of Congress but had not yet been signed by the president. The Act, S. 1071, was signed into law on December 18.
Congress’ new annual defense spending package, passed on December 17, authorizes $8 billion more than the Trump administration requested, for a total of $901 billion. The FY2026 National Defense Authorization Act (NDAA) paints a picture of a Congress that is working to both protect and accelerate nuclear modernization programs while simultaneously lacking trust in the Pentagon and the Department of Energy to execute them. Below is an overview of provisions of note in the new NDAA related to nuclear weapons.
Sentinel / Intercontinental Ballistic Missiles
Every year since fiscal year (FY) 2017, Congress has inserted language into the NDAA prohibiting the Air Force from deploying fewer than 400 ICBMs (an arbitrary requirement put in place by pro-ICBM members of Congress fearful of any reductions in the force). The FY26 NDAA does not break this streak; in fact, it entrenches the requirement deeper into US policy. Rather than repeating the minimum ICBM requirement as a simple provision as previous NDAAs have done, Section 1632 of the new legislation inserts the requirement into Title 10 of the United States Code (the US Code is the official codification by subject matter of the general and permanent federal laws of the United States. Title 10 of the Code is the subset of laws related to the Armed Forces). This change means that Congress will no longer have to agree to and insert the requirement into the NDAA year after year. Instead, the requirement becomes the permanent standard and will require an affirmative change in a future NDAA to undo. Beyond requiring the Air Force to deploy at least 400 ICBMs, the new defense spending act additionally amends Title 10 of US Code to prohibit the Air Force from maintaining fewer than the current number of 450 ICBM launch facilities (essentially meaning that the Air Force cannot decommission any of the 50 extra launch facilities in the US inventory).
This change is indicative of a desire by Congress to bolster its protection of the ICBM program in response to increased scrutiny prompted by the ever-growing budgetary and programmatic failures of the Sentinel ICBM program. Interestingly, a provision in the Senate version of the defense authorization bill that would have established an initial operational capability (IOC) date for the Sentinel program of September 30, 2033, did not make it into the final text, suggesting a lack of confidence in the Air Force’s ability to achieve the milestone. With an original IOC of September 2030, the September 2033 date would have aligned with the Pentagon’s 2024 announcement that the Sentinel program was delayed by at least three years. The omission may thus indicate Congress’ anticipation of potential further delays to Sentinel’s schedule beyond the Air Force’s most recent estimate.
Nuclear Armed Sea-Launched Cruise Missile (SLCM-N)
In addition to protecting the most politically vulnerable nuclear weapons programs, the FY26 NDAA also aims to speed up US nuclear modernization and development, in some cases even beyond the requests of the administration. Despite the fact that the Pentagon’s FY26 budget request requested no discretionary funding for the nuclear-armed, sea-launched cruise missile (SLCM-N), the NDAA authorized $210 million for the program — on top of the $2 billion to the Department of Defense and $400 million to the National Nuclear Security Administration (NNSA) included in the July 2025 reconciliation package to “accelerate the development, procurement, and integration” of the SLCM-N missile and warhead, respectively.
Most notably, the new defense authorization act speeds up the SLCM-N’s deployment timeline by two years. Section 1633 of the act repeats the IOC date of September 30, 2034, established by the FY24 NDAA, but also requires DOD to deliver a certain number of SLCM-N — a number to be determined by the Nuclear Weapons Council — by September 30, 2032, to achieve “limited operational deployment” prior to IOC.
Future nuclear development
In addition to speeding up the deployment timeline for SLCM-N, the FY26 NDAA initiates and accelerates the development of new nuclear weapons by creating a new NNSA program in addition to the stockpile stewardship and stockpile responsiveness programs: the rapid capabilities program. The new program — established by section 3113 of the NDAA via insertion into Title 50 of the US Code (War and National Defense) — is tasked with developing new and/or modified nuclear weapons on an accelerated, five-year timeline (compared to the traditional 10-15 year timeline for new weapons programs) to meet military and deterrence requirements.
Numerous provisions in the new NDAA reflect a lack of trust by Congress in DOD and DOE’s ability to execute and deliver nuclear modernization programs. The creation of stricter and more detailed reporting requirements and action items for making progress on various nuclear weapons related programs constitute an increased effort by Congress to micromanage nuclear modernization programs.
One example of nuclear micromanagement in the act are Sections 150-151 regarding the B–21 bomber. Section 150 mandates the Air Force to submit to Congress:
- An annual report on the new B–21 nuclear bomber including:
- An estimate for the program’s average procurement unit cost, acquisition unit cost, and life-cycle costs,
- “A matrix that identifies, in six-month increments, plans for and progress in achieving key milestones and events, and specific performance metric goals and actuals for the development, production, and sustainment of the B–21 bomber aircraft program” (with detailed requirements for how the matrix should be subdivided and what information it must include),
- A cost matrix (also in six-month increments and including specified subdivisions),
- A semiannual update on the aforementioned matrices.
In addition, the provision requires the US Comptroller General to “review the sufficiency” of the Air Force’s report and submit an assessment to Congress. The following section of the NDAA additionally requires the Air Force to submit to Congress — within 180 days of the act’s enactment — “a comprehensive roadmap detailing the planned force structure, basing, modernization, and transition strategy for the bomber aircraft fleet of the Air Force through fiscal year 2040” (once again, including detailed requirements for what information the roadmap must include).
In a similar fashion, Sections 1641 and 1652 lay out strict reporting and planning requirements for sustaining the Minuteman III ICBM force and developing the Golden Dome ballistic missile defense program, respectively.
Such efforts by Congress to increase its management of US nuclear weapons programs could be in response to repeated and ongoing delays, cost overruns, and setbacks, or could simply reflect Congress’ desire to seize more control over the nuclear enterprise to get what it wants (or, likely, a bit of both). To be clear, Congressional scrutiny into nuclear programs is welcome amidst a trend of over-budget and behind-schedule procurement of unnecessary weapon systems by the Pentagon. Congress can and should play an important role in ensuring that the Departments of Defense and Energy are not handed blank checks for nuclear modernization.
That said, with this legislation, Congress authorized nearly $30 billion in spending for select nuclear weapons programs in FY26 alone. The tables below, developed by the Center for Arms Control and Non-Proliferation, show a breakdown of Congress’ authorizations for these programs:
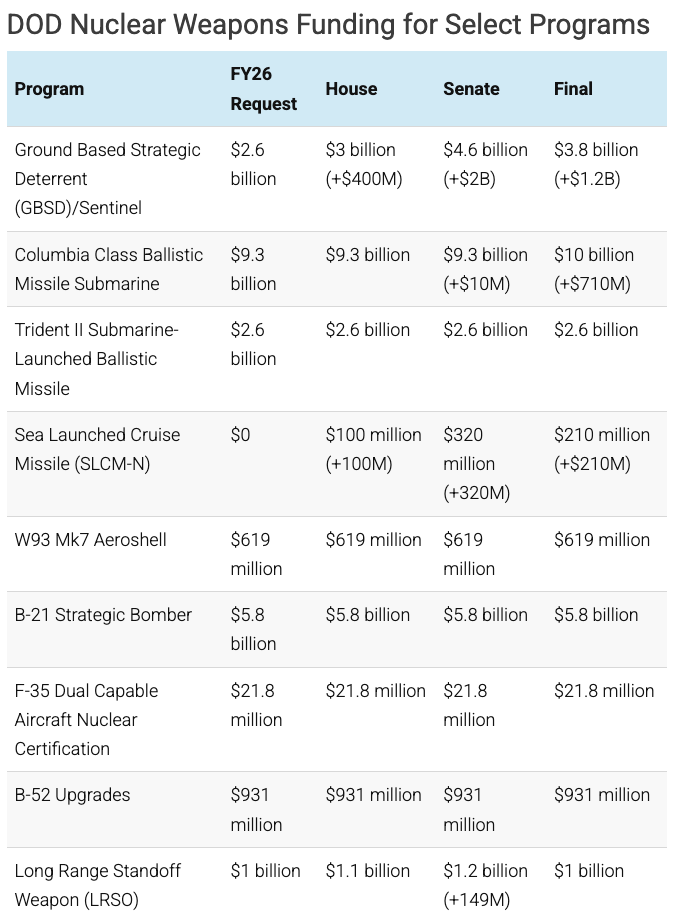
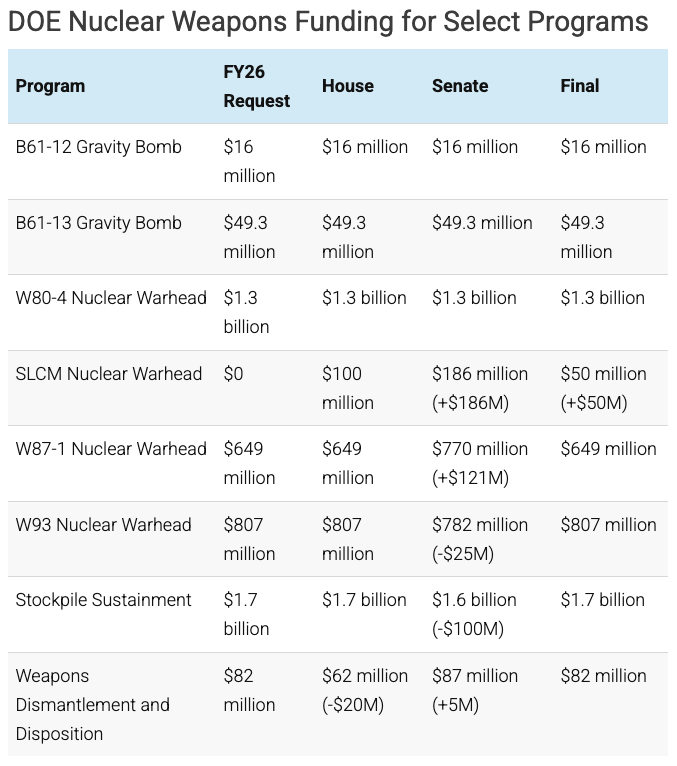
This article was researched and written with generous contributions from the Carnegie Corporation of New York, the New-Land Foundation, Ploughshares, the Prospect Hill Foundation, and individual donors.
Demystifying the New President’s Management Agenda
By design, the Office of Management and Budget’s (OMB) work follows a predictable, seasonal rhythm: budget guidance to agencies in the spring, strategic management reviews in the late summer, passback in the fall, shutdown saber-rattling in late September, release of the president’s budget request in the winter, and so on. A giant novelty clock in the building counts down the days until the end of the fiscal year, each year, whether Congress has done its work to appropriate money for the next one or not. Presidents, Congresses, crises, political movements – all of these come and go, but OMB’s work largely continues to cycle.
This week, OMB completed one such ritual: it released the President’s Management Agenda (PMA). The PMA–closely watched by federal employee groups, contractors, public administration academics, and the handful of general-public bureaucracy-enjoyers–is the vehicle with which each president outlines policy priorities on how the government manages itself. Each 21st-century president has had one, after George W. Bush’s Administration issued the very first one in August of 2001–and President Trump is the first to have issued two discrete ones.
Not familiar with this ritual? You’re not alone. Though not statutorily required, a PMA is meant to be a blueprint for improving how the federal government delivers policy, whether hiring, buying, designing services, listening to Americans, measuring performance, or delivering financial assistance. A PMA is also load-bearing, one of the few levers capable of coordinating action across the enormous machinery of government, aligning budgets, capacity, and accountability behind long-term modernization rather than the short-term crisis response that often drives management changes.
In a year when management issues like human capital, IT modernization, and improper payments have received greater attention from the public, examining this PMA tells us a lot about where the Administration’s policy is going to be focused through its last three years. As we did for a major policy release on hiring earlier this year, the Federation of American Scientists and the Niskanen Center are teaming up to break down and contextualize this year’s PMA.
The Structure of the PMA
As OMB noted in an accompanying memo to this PMA release, the core of the PMA has for many years, been a set of cross-cutting “priority goals” that OMB is required to establish under the Government Performance and Results Act Modernization Act (GPRAMA) of 2010, which codified much of what the Bush and Obama Administrations had done to focus on performance-based goal setting and reporting. Over the years, the PMA has grown to be the organizing principle for these priority goals, explaining how they relate to one another and are part of a broader coherent whole.
This current iteration of the PMA (reproduced below) is organized – like the Biden Administration’s was – as something of a nesting doll. It has three broad priorities, each with a few goals, and a series of objectives within each of those goals:
Unlike previous iterations of the PMA, it appears this new one won’t be accompanied by the type of long narratives and explanations typical of the Bush, Trump I, and Biden PMAs. It also differs somewhat from the Obama Administration’s approach, which focused on a series of detailed “Cross-Agency Priority (CAP) Goals that largely cohered into a formal PMA after the fact as GPRAMA was passed during the term and codified the modern process mid-stream.
Regardless of how they start, however, previous administrations have largely committed to providing ongoing reporting on their progress towards achieving each objective or goal throughout the remainder of the term. It is not yet clear whether the second Trump Administration intends to do this–Congress should inquire about their GPRAMA obligations–but in general this practice has been valuable both to keep agencies accountable for making progress and so that interested third parties can get a window into how the government is changing over time.
In the meantime, this week’s release gives us enough insight into the contours of this term’s PMA to assess how it compares with previous efforts and with what we’ve learned from observing and managing past PMAs.
What’s Promising: A Renewed Focus on Some Hard Problems
Normally, the PMA contains two types of initiatives. The first are evergreen topics —such as the perennial need to hire federal employees more quickly and efficiently—which have appeared in every PMA to date. The second category consists of more idiosyncratic or extremely timely “hard problems” that either haven’t received attention or where past reform has stalled. In the Biden PMA, for instance, this included integrating lessons from the pandemic’s disruption of work life. In the first Trump Administration, it included an ambitious overhaul of personnel vetting transformation on the heels of the massive OPM security clearance data breach in 2015.
Occasionally, these hard problems “graduate” out of the PMA once sustained focus produces results. The PMA’s emphasis on personnel vetting, for example, has largely given way to a multi-year, bipartisan Trusted Workforce 2.0 strategy that has and is making progress despite its challenges.
This year’s PMA includes several such issues, offering the second Trump Administration an opportunity to spotlight underappreciated but consequential aspects of federal management, including:
- Offloading unnecessary leases and buildings: Federal facilities and real estate have never truly been managed as a portfolio with all the transparency, tradeoffs, accountability and management that entails. Before the pandemic, many agencies had significant excess office space and struggled to offload unneeded square footage, even as the average age of federal facilities climbed north of 50 years old and many buildings are no longer suitable for modern work. Rationalizing and right-sizing this portfolio is a worthy and important initiative but it will be difficult: Congress has historically underfunded agencies that are aiming to reconfigure or move, and individual members of Congress frequently oppose specific office closures among their constituents. Any effort to responsibly modernize these real estate holdings will take a lot of patience and willingness to take on sacred cows, but has the potential to earn significant savings and efficiencies.
- Holding contractors and grantees accountable for performance: Most indirect federal spending flows through intermediaries and, too often, the outcomes agencies define for their work are unclear, don’t meet intent, cost more than they should, or aren’t set up for other stakeholders to learn from. Many agencies are captured technologically, intellectually, and psychologically by vendors, leading to a type of learned helplessness where their inability to technically manage contracts leads to an inability to hold them accountable for their performance. Fighting these entrenched forces and inertia is not easy, however, and will require arming agencies with the federal experts, tools and training necessary to change their approach to vendor and grantee management but also give them top-cover to push back on powerful, politically-connected awardees that fail to deliver again and again without consequence.
- Eliminating data silos: While data protections necessarily inhibit privacy and security violations, too much federal data sits in silos built by habit, culture, or old technology. Driving responsible interoperability could have a meaningful impact on service delivery, including for two of the thorniest issues in public service delivery: identity regulation and eligibility verification. However, prior actions and whistleblower complaints about misuse of personal citizen data put an imperative on the Administration demonstrating its commitment to data security under this PMA initiative. It presents an opportunity to right the ship and build the type of trust that will be required from Congress and the public to make good on the transformative power of better data management.
- Removing poor performers: The federal government has long struggled to swiftly remove poor-performing employees. The system we have today was never intended to be permanent or perfect—it was meant to provide incremental improvements toward processing removals quickly but fairly. Nearly every former deputy secretary, in administrations of both parties, has wished they could establish a simple, actionable, repeatable framework for performance management that includes reasonable safeguards. This Administration has an opportunity to chart that path. But proceeding without those safeguards—particularly protections against arbitrary or partisan dismissals—risks undermining good-faith reforms that are crucial for cross-partisan credibility and for helping managers manage well.
- Building the most agile and efficient procurement system: The Revolutionary FAR overhaul underway at OMB and the General Services Administration (GSA) is a concrete opportunity to modernize federal buying at its foundations by paring back the FAR to just its “statutory” requirements and allowing agencies to buy more flexibly. But the regulation update is at best only half the battle: the administration will need to dedicate time, people, and championship to making them stick in training, norms, culture, and leadership. It also needs to resist the temptation to add back its own non-statutory clauses, an impulse that led to the FAR’s bloated and unwieldy state in the first place.
Ideally, success in these areas means they will eventually fade into the background of standard management practice. Agency leaders may not earn themselves splashy press coverage or public adulation by improving procurement or tackling data silos. No agency head wants to spend time grappling with underutilized buildings. Genuine progress here, however, would allow future leaders to remain focused on mission delivery.
What’s Returning: Places to Learn from the Past
This brings us to the evergreen PMA topics. To GPRA veterans, some of the things in here are expected and represent the evolution of years of work by Republicans, Democrats, and nonpartisan civil servants to make the government run better. Many of these reflect years–or even decades–of work to address some of the core challenges of managing a large organization in any sector (how to hire the right people, how to buy effectively, how to build and secure systems, etc.)
But there’s a deeper reason these issues recur, beyond aspirations for bipartisan comity. Adding an item to the management agenda is only a starting point. Meaningful progress requires far more than a talking point, executive order, or regulatory tweak. Leadership attention and cover, technical capacity to actually understand, teach, and monitor reform, oversight partnerships that orient their activities to the new model, administrative data that’s accurate, real-time, and actionable, and central funds to resource pilots too edgy to get agency support or toolkits that no one agency wants to own.
In this PMA, some of these evergreen topics include ones this Administration can learn from its predecessors and accelerate towards success, including:
- Tackling improper payments, fraud, waste, and abuse: The Trump Administration inherits a solid foundation in this area from its predecessor, which invested serious effort into tackling the surge in improper payments in the COVID-19 era. That work included investing in upfront controls, fraud prevention, and collaboration between agencies and their oversight communities. The Government Accountability Office, Agency Inspectors General, and others have also long offered suggestions about how to continue to reduce the government’s improper payments rate. Groups like the Payment Integrity Alliance are developing new technology-powered tools to support this work from outside government. These are evidence-based solutions that are likely to work, as opposed to arbitrary, highly-partisan, and ultimately untrue declarations of fraud that marked the early days of this Administration, in addition to counterproductive efforts to cut or constrain the oversight community. As OMB looks towards 2026, it should take into account these models.
- Streamlining the federal workforce and eliminating duplicative programs: While this year’s efforts are the first in a couple decades to seek to dramatically reduce the size of the federal workforce, they are not without precedence in American history. Following both World Wars (and especially through the late 1940s), the federal government had to demobilize hundreds of thousands or millions of civilian employees in a way that both treated them with dignity and economized on taxpayer dollars. More recently, in the 1990s, the Clinton Administration also conducted large-scale downsizing, with decidedly mixed results because the cuts came before changes to agency to-do lists that never materialized. It will be important for this Administration to learn lessons from the past to avoid some of the long-term damage wrought by the Clinton years, for which agencies are still paying.
- Hiring exceptional talent for key presidential priorities based on skills and merit: All presidents have priorities and many of those involve some kind of hiring surge: following 9/11, the Bush Administration had to rapidly create and staff up the Department of Homeland Security for new mission sets–for example, like airport security. More recently, the Biden Administration conducted several surges around topics like the Bipartisan Infrastructure Law and artificial intelligence. To make this work, previous efforts have succeeded by setting up dedicated teams that focused on specific, measurable goals and bought-in mission area leadership to champion the effort. As OMB and OPM consider their efforts this time, they should explore common data standards to ID bottlenecks, interagency approaches to share resources and talent, and investing in all the accoutrement to new and updated career paths and roles – and doing their best to embed these practices in the system, not just as part of a special effort.
They might also consider reactivating networks and programs that were successful in previous eras, like Tech to Gov, which worked across sectors to hire technologists into government. On merit and skills based hiring, implementation appears to be under way with a variety of initiatives that have promising goals, but will require significant investment of resources and leadership attention to complete, as we’ve written about.
- Buy as one entity: smarter, faster, cheaper: Successive administrations, dating back several decades, have tried to strike the right balance between decentralized and centralized procurement. The Clinton team, for example, called for greater decentralization to agencies because it “allows strangers-often thousands of miles away-to make purchasing decisions.” More recently, however, administrations have gone in the other direction, including a discrete goal to drive category management in the first Trump PMA, though agencies often still complain about being forced to use government-wide vehicles that don’t meet their exact custom needs.
To avoid the pendulum swinging back and forth between centralization and decentralization, efforts to implement this PMA should learn from efforts to achieve savings by transparent use of procurement data that were pioneered in the Biden Administration like the Procurement Co-pilot, Hi-Def initiative, and the strategic acquisition data framework. Rather than mandates from above, these initiatives help drive savings and get “spend under management” by solving information asymmetries and transparently helping agencies understand “what’s in it for them” when they use best-in-class contracts.
- Consolidate and standardize systems, while eliminating duplicative ones: The federal government has long operated on a system of both shared, government-wide, and also bespoke agency systems. The Bush, Obama, and first Trump administrations had OMB focusing on consolidating duplicative systems across government through shared services. This model, while promising in many cases, is difficult to pull off in practice – of those initiatives, the Bush Administration’s payroll consolidation is far and away the most successful, while efforts to adopt standard payment system (e.g., e- and g-invoicing) and innovative payroll solution have languished, as did GSA’s NewPay program.
This PMA should take to heart the lessons of its predecessors: agencies must be resourced up front to execute their part of any migration to shared systems, and OMB must ruthlessly prioritize and rigorously validate any requests for deviations from the standard product. In most cases, it will be far easier—and considerably cheaper—to adjust policy to fit a modern, standard solution than to customize that solution to accommodate every agency’s unique requirements.
Leaders should also address the internal politics of these transitions directly. Champions of bespoke systems often have deep attachment to their legacy tools, and their resistance can be stronger and more personal than expected.
- Defend against and persistently combat cyber enemies: Reactive and proactive cybersecurity has been a central federal government focus as long as government systems have been connected to the internet. Of all the discussed areas, continuity is perhaps most crucial to cybersecurity, with the need for sustained attention to legacy system replacement, identity management, continuous monitoring, secure architectures, and the significant talent demands that come with all of those. This Administration should heed the lessons of its predecessors, which lost valuable time to bureaucratic reshuffling and inconsistent “carrot vs. stick” approaches in its engagement with the private sector.
It’s never going to be possible to truly “solve” these issues that are core parts of ongoing management in any large enterprise. However, because progress is incremental, this PMA can accelerate its own impact by learning from what has and hasn’t worked in the past.
What’s Missing: Outcomes for Americans
There is, however, one “evergreen” PMA topic that we’re surprised to see missing from this iteration: Customer Experience (CX).
The previous two PMAs featured big customer experience pushes to modernize and centralize how the government designs, delivers, and updates benefits based on customer needs. These delivered favorable results for veterans’ benefits, disaster survivors, new families, travelers and more, and fostered innovative approaches to benefits delivery like the cross-agency “life experience” program that reconceptualizes the way the government engages with people who need its support. In recent years, the bipartisan success of these initiatives has led to four straight years of improvements in the industry-standard American Consumer Satisfaction Index, with the government closing out last fiscal year at an impressive 19-year high.
While this PMA does mention “digital-first services” that are “built for real people, not bureaucracy,” that principle sits inside a technology-and-efficiency frame rather than a clear commitment to outcomes for the public. What’s missing is an explicit stance that service delivery, burden reduction, and trust-building are core measures of government performance and are not encompassed by a positive government IT experience or a more fetching website design. Plenty of core users of government services–seniors, for example–do not interface with the government in a “digital-first” way, further complicating this as a focus for customer experience.
Hopefully this absence will still allow for the bipartisan CX agenda to continue in other spaces, such as the new National Design Studio. It’s not enough to declare that the government will deliver high-quality services to the people who rely on them. Agencies need the ability to collaborate and know that the White House will back them when they need to request incremental funding to conduct user research or A/B test a new form before rolling out.
A real test of any PMA isn’t how well it modernizes, it’s whether people notice government working better on their behalf. In that way, CX is what we might call the “love language of democracy” and it’s important that OMB is attentive to building that.
What’s Concerning: The Culture War is Coming for Management
The Biden Administration received criticism for attaching progressive goals from environmental standards to equity to labor onto every possible management tool (procurement, grantmaking) until the weight of implementation is slow, diffuse, or nearly impossible. Its PMA embodied that instinct: broad, values-aligned expansive goals that had great intentions but struggled to operationalize.
The new PMA both reacts against and mirrors that instinct: it pairs standard management reforms with culture-war directives that seek single-minded discipline, accountability, and ideological alignment.
At times, it reads like two agendas stitched together: one technocratic, aimed at federal administrators, and one ideological, aimed at unofficial commissars and social media. Alongside modernization goals you might find in any PMA sit directives to:
- Eradicate woke and weaponized programs across government, which is a sweeping slogan with unclear scope at odds with the usual evidence- and performance-based mandates embedded in GPRAMA and past PMAs.
- End discrimination by government, which is a superficially unobjectionable shibboleth, but incorrectly implies that the government has been discriminating in how it carries out its management functions, despite the fact that its equity programs largely only follow the rules Congress has set out in offering employment preference to veterans or procurement preference to certain categories of small businesses.
- Defund DEI, gender ideology, K-12 indoctrination, child mutilation, and open borders, which are culture war buzzwords with no obvious relation to government performance or management issues.
And scope creeps further into territory historically outside PMA (or OMB) control, such as a set of general goals with choose-your-own-adventure interpretation and murky implementation paths, written at a strange distance from the government the Administration oversees:
- Find and annihilate government censorship of speech, which is perhaps the first time annihilate has ended up in an OMB memo and implies that there are “hidden” examples of censorship while the administration pursues overt censorship in other areas.
- Reverse malicious schemes to hide information from Americans, which gestures at a conspiratorial approach to government management that seems at odds with the Administration’s claim that it’s fully in control of the executive branch. It’s difficult to simultaneously claim that there are truths hidden from the public while also deprecating transparency, as in Federal data sets.
- Abolish abusive intelligence activity targeting unwitting Americans, which is certainly a laudable goal for any civil libertarian in a democracy but doesn’t necessarily have any resonance with normally much-duller management functions like HR and finance, which have struggled to accomplish even their overt functions in recent years, nevermind anything more nefarious.
As we’ve written before, hijacking these normally low-temperature operational processes to fight the culture war not only raises the partisan pressure on normally bipartisan issues, but it also “needlessly politicizes our institutions, snarls our civil servants in red tape, and usually fails to achieve even those unrelated objectives.”
Nowhere is this danger greater than in implementation of the PMA’s objective to “[p]ut political appointees in control of grant process to deliver results,” which supposes that political control and, by implication, alignment with the President’s partisan priorities is a main factor in how Congressionally-authorized grants are executed. The President certainly gets to set some overall parameters for grantmaking across the federal government, and politically-appointed agency heads are ultimately accountable for the money they spend.
But this priority implicates a much more arbitrary and politically-motivated process for determining how public funds are spent that strikes at the heart of what makes government action legitimate: the fair application of rules that are defined ahead of time and apply equally to all. Like a similar requirement in the Merit Hiring Plan, this also creates an obvious bottleneck in agency processes as recommendations stack up for political review, reducing efficiency and elongating the path to “results.”
Perhaps including these initiatives–which largely fall outside of the normal OMB management purview–was the price OMB had to pay to get the rest of the PMA through the hyper-partisan (even in normal order) communications processes of the White House. If that’s the case, agencies should be able to largely proceed with the rest of the agenda unbothered by also having to separately organize around these initiatives. But if not, it will be critical to ensure that directing agencies into partisan goose chases does not pull time and attention away from the harder—and ultimately more rewarding—work of genuine management reform.
Declaration is not Implementation
Publicly releasing the PMA is the easy part. The real work goes into changing government. As the Bush Administration’s first PMA noted: “Government likes to begin things—to declare grand new programs and causes. But good beginnings are not the measure of success. What matters in the end is completion. Performance. Results. Not just making promises, but making good on promises.”
Many of the objectives outlined in the PMA are sound ideas with long track records across different administrations. We largely agree with many of them and they echo our policy priorities and those of partner organizations. But their appearances on multiple PMAs underscores how hard these problems are to solve. Category management,real property portfolio rationalization, and cybersecurity, were problems for many years because of the inherent difficulty of tackling them.. This is doubly true for the ideas that are fresh from the front lines of the culture war, which lack both a track record of successes and failures to learn from and the bipartisan support that more established issues—like improper payments or IT modernization—typically receive in Congress.
To actually impact the entire government – one of the largest and most complex enterprises in human history – it’s not enough to just declare that it’s the policy of the Administration that X or Y happens, or even convene regular gatherings of deputies. We’ve seen that approach fail repeatedly: agencies cannot and will not implement a PMA just because OMB issues it.
Real success requires disciplined implementation. That means selecting strategies that genuinely move the needle; setting aggressive but achievable measures and timelines; incentivizing leaders to invest time, attention, and talent in relentless follow-through; maintaining up-to-date metrics and feedback loops to know what’s working and what isn’t; and sustaining clarity of focus all the way to the finish.Without that, it becomes all too easy for OMB and agencies to skate by on superficial changes that check boxes but result in no real systems change–a PMA of performance art, where everyone claps but nothing changes. Amid all the swirl of any White House, this work of sticking the landing is the hardest part.
That’s because the PMA – like any strategy – itself isn’t really valuable on its own. It can, however, cut through the noise, clarify what the priorities are, and provide a framework for holding agencies and leaders accountable as they do their work. Any PMA will rise and fall based on how well it manages to do this. The way this term’s PMA is structured at the outset makes this task supremely difficult because it’s pulling in several directions all at once: it’s trying to simultaneously pass as a deeply partisan political document, a check-list for agencies of recent EOs, and a sober management policy agenda.
The real danger is that this lack of clarity and flurry of culture war buzzwords means nothing changes. That the same broken systems of human capital, procurement, IT modernization, security clearances, and user feedback, that have contributed to what OMB refers to as “accumulating perils” persist for yet another presidential term because OMB’s own management approach mistook a policy memo for progress and failed to chart a path forward. “Declare success and move on” is how these hard problems survive for decades.
This failure mode is easy to imagine: as humbling as it is to admit when you sit at OMB, reform requires changing the habits of work in agencies, sub-agencies, offices, and teams for whom policy memos about HR and procurement are the last thing on their mind (or even in their inbox). This is the hardest work of governance – rewiring workflows, seeding change in budgets, resetting culture – and demands management be treated as a core, can’t-fail function rather than a sideshow of dashboards and Powerpoint.
As they should be, agency implementers are more focused on the day-to-day administration of their programs: achieving their particular program objectives, responding to requests from Congress, serving the public, tracking their own budgets, and managing their own chaotic work lives. If the PMA can’t provide them with clarity, a limited number of clearly articulated goals, and a simple on/off ramp for change, it will be hard to change the direction of travel – not because of some deep state conspiracy, but because they don’t know what to focus on or how they’re going to be measured. What gets implemented, and what people experience, is what counts; everything else is decoration.
What We’re Watching
As with all broad, whole-of-government strategies like this, it will only be obvious in retrospect whether this administration is successful at achieving those goals. However, there are some things to watch out for that will clue close-watchers in about how things are going:
- First, will OMB continue the type of detailed, quarterly status reports that were the hallmarks of previous PMAs and allowed the public to see how things were progressing?
- Second, are there key metrics that OMB and its partner agencies will commit to tracking, reacting to, and publishing to measure their success?
- Third, are agencies resourced to actually accomplish many of these ambitious goals and what do they prioritize (and indeed, since agencies are not mentioned in the PMA itself, what ownership do agencies feel over it)?
Finally, and more abstractly, we’re also going to be looking out for how OMB and others engage with the rest of the PMA-interested community, including career federal employees, good government groups, congressional staffers, think tanks, academics, and others who have trod this same path. The permanent institutions of the federal government don’t serve any one president exclusively; instead, they represent a deep and important investment that the American people have made in themselves as a bedrock of our democracy. While reasonable disagreements about how to do so will certainly always exist, this community can, should, and will embrace a government asking for help. OMB would do well to welcome them in.
Trump’s Cuts Could Exacerbate The Energy Emergency
Originally published at Forbes.
Demand for power is climbing to unprecedented levels. U.S. Energy Information Administration data reveals that July set a new record for electricity peak demand, driven by nationwide heat waves and increasing reliance on power-intensive artificial intelligence tools. And, given the state of the electrical grid in several jurisdictions, the U.S. The Department of Energy declared an emergency order on July 28 to secure the mid-Atlantic power grid. The situation could worsen as summer continues, although it has already been a long time in coming.
On day one of his second administration, President Donald Trump declared a national energy emergency. The declaration formalized the idea that economic prosperity, national security, and foreign policy are under threat due to an insufficient energy supply. While this claim may be intended to encourage leniency towards the fossil fuel industry, there are many issues with our energy infrastructure that do need urgent attention. The American Society of Civil Engineers gave the nation’s aging electrical infrastructure a D+, a failing grade, in the organization’s latest annual Infrastructure Report Card. The aging grid is in dire need of infrastructure upgrades so that it is able to serve the increasing power demand as we see more frequent extreme temperatures and weather events due to climate change, alongside the expansion of data center power use and the electrification of buildings and transportation.
Currently, energy generation takes years to connect to the grid due to slow permitting processes and a patchwork of utility regulations and forecasters predict electricity use will increase 50% by 2050 in the U.S.
However, instead of creating a pathway to speed up the connection of new energy sources to the grid, Trump followed this emergency declaration with a budget request for fiscal year 2026 that kneecaps energy innovation. Followed closely after that was the passage of the One Big Beautiful Bill Act, which, in combination with severe budget and personnel cuts in government-funded science and technology research and development, will likely result not in energy stability or even dominance, but a true national emergency: a long-lasting rise in energy prices. It may also lead to a decline in the U.S.’s leadership in technology innovation and talent.
Investing In Innovation Could Help Address The Energy Crisis
Today’s ubiquitous GPS, computer chips, solar photovoltaic cells, and lithium-ion batteries didn’t arrive from the ether fully-formed and ready for consumers to use. Many of these innovations are thanks to the equivalent of $7.4 billion (in today’s dollars) taxpayers invested shortly after WWII ended to create the Office of Scientific Research and Development. Funds from OSRD eventually led to discoveries in the 1940s and 50s that resulted in the establishment of the National Science Foundation National Aeronautics and Space Administration, Atomic Energy Commission (later becoming the Department of Energy), and other science agencies.
Federal funding for research and investment in these agencies has resulted in trillions of dollars of economic benefit, resulting in the U.S. being a leading developer of technologies that have transformed our world.
Funding cuts to the DOE pose a threat to our energy system and leadership in energy systems like next-generation grid technology, AI, and clean energy development and manufacturing.
DOE is the largest funder of basic physical science research in the government. The DOE’s Office of Science’s annual budget is $8.2 billion for projects related to critical minerals, quantum computing, enhanced geothermal energy, and artificial intelligence. All are topics that the Trump administration has identified as crucial to U.S. economic competitiveness and “dominance.” Applied technology offices within the DOE – the ones that transform scientific research into commercial applications, like the Manufacturing and Energy Supply Chain Office, Office of Clean Energy Demonstrations, and the Energy Efficiency and Renewable Energy office— have funded projects across industries and sectors. These include the private sector, national labs, and universities, all of whose work has resulted in historically low costs for battery storage, solar photovoltaics, grid components, and critical infrastructure.
These investments have fed into a resurgence of our domestic manufacturing industry across the Rust Belt (Midwest) and the Sunbelt (southern states like Georgia, South Carolina, and Texas). The DOE historically has a positive return on taxpayer investment across its research and development offices. From its start in 1976 through 2015, DOE invested $12 billion in research, development, and deployment in EERE and found that its return yielded $388 billion in economic benefits, or an ROI of over 27% by conservative estimates.
The Building Technologies Office within DOE, which is known for developing energy-saving technologies that save consumers money on their utility bills, has estimated that for every $1 invested in its R&D, it has yielded between $20 and $261 in economic benefits. The benefits of these investments are in the form of job creation, consumer cost savings, and new technologies like horizontal drilling – yes, the technology used for fracking developed through the DOE’s R&D program on natural fracturing.
Given that context, it may be counterintuitive that the same officials touting U.S. leadership in innovation and discovery are proposing the largest financial cuts to DOE in history. The president’s budget request is proposing a 26% cut to non-defense DOE programs. The table below summarizes the cuts, with a heavy focus on programs that have resulted in the development and economic success of new energy technologies, especially clean energy technology.
Slashing research and development programs across the DOE, all while Congress rolls back clean energy tax incentives and programs, is not going to solve the nation’s energy emergency. It makes our current challenges even worse.
The problems that the aging U.S. power grid faces are already compounded by historically high (and growing) consumer demand – a result of increasingly extreme temperatures and weather events, the explosion of data centers’ energy demand, and the electrification of even more transportation and buildings. Budget cuts and the insistence on using energy derived from fossil fuels may only exacerbate the problems the U.S. is already facing. In fact, defunding scientific research will most likely allow international competitors to slingshot ahead of the U.S. in new technology development and adoption.
If Americans become increasingly reliant on foreign intellectual property and technology, while the domestic grid continues to decay, the national energy emergency is likely to grow even more dire in the years to come.
What’s Progress and What’s Not in the Trump Administration’s AI Action Plan
Artificial intelligence is already shaping how Americans work, learn, and receive vital services—and its influence is only accelerating. To steer this technology toward the public good, the United States needs a coherent, government-wide AI agenda that encourages innovation and trustworthiness, grounded in the best scientific evidence.
In February 2025, the Trump Administration sought public comment on its development of an AI Action Plan. The Federation of American Scientists saw this as an opportunity to contribute expert, nonpartisan guidance, combining insights from our policy team with ideas from the broader science and technology community, developed as part of our Day One Project. In our comments to the White House Office of Science and Technology Policy we recommended incorporating responsible policies to unleash AI innovation, accelerate AI adoption, ensure secure and trustworthy AI, and strengthen our existing world-class government institutions.
Last week, the Trump Administration released their AI Action Plan. The document contains many promising aspects related to AI research and development, interpretability and control, managing national security risks, and new models for accelerating scientific research. However, there are also concerning provisions, such as those inhibiting state regulations and removing mentions of diversity, equity, and inclusion and climate change from the NIST AI Risk Management Framework. These omissions weaken the United States’ ability to lead on some of the most pressing societal challenges associated with AI technologies.
Despite the AI Action Plan’s ambitious proposals, it will remain aspirational without funding, proper staffing, and clear timelines. The deep cuts to budgets and personnel across the government present an incongruous picture of the Administration’s priorities and policy agenda for emerging technologies, and places pressure on Congress to ensure this plan is properly supported.
Promising Advances & Opportunities
AI Interpretability
As an organization, we’ve developed and shared concrete ideas for advancing AI interpretability—the science of understanding how AI works under the hood. The Administration’s elevation of AI interpretability in the plan is a promising step. Improving interpretability is not only critical for technical progress but also essential to fostering public trust and confidence in AI systems.
We have provided a roadmap for the government to deliver on the promise of interpretable AI in both our AI Action Plan comments and a more detailed memo. In these documents we’ve advocated for advancing AI explainability through open-access resources, standardized benchmarks, common tasks, user-centered research, and a robust repository of techniques to ensure consistent, meaningful, and widely applicable progress across the field. We’ve also argued for the federal government to prioritize interpretable AI in procurement—especially for high-stakes applications—and to establish research and development agreements with AI companies and interpretability research organizations to red team critical systems and conduct targeted interpretability research.
AI Research and Development
Beyond interpretability, the AI Action Plan lays out an ambitious and far-reaching agenda for AI research and development, including robustness and control, advancing the science of AI, and building an AI evaluation ecosystem. We recognize that the Administration has incorporated forward-looking proposals that echo those from our Day One Project—such as building world-class scientific datasets and using AI to accelerate materials discovery. These policy proposals showcase our perspective that the federal government has a critical role to play in supporting groundbreaking scientific and technical research.
A Toolbox for AI Procurement
The Administration’s focus on strengthening the federal workforce’s capacity to use and manage AI is an essential step toward responsible deployment, cross-agency coordination, and reliability in government AI use. The proposed GSA-led AI procurement toolbox closely mirrors our recommendation for a resource to guide agencies through the AI acquisition process. Proper implementation of this policy could further support government efficiency and agility to respond to the needs of constituents.
Managing National Security Risks
The Administration also clearly recognizes the emerging national security risks posed by AI. While the exact nature of many of these risks remains uncertain, the plan contains prudent recommendations on key areas like biosecurity and cybersecurity, and highlights the important role that the Center for AI Standards and Innovation can play in responding to these risks. FAS has previously published policy ideas on how to prepare for emerging AI threats and create a system for reporting AI incidents, as well as outlining how CAISI can play a greater role in advancing AI reliability and security. These proposals can help the government implement the recommendations advanced in the Action Plan.
Focused Research Organizations
The Administration’s support of Focused Research Organizations (FROs) is a promising step. FROs are organizations that address well-defined challenges that require scale and coordination but that are not immediately profitable, and are an exciting model for accelerating scientific progress. FAS first published on FROs in 2020, and has since released a range of proposals from experts that are well-suited to the FRO model. Since 2020, various FROs have gained over $100 million in philanthropic funding, but we believe that this is the first time that the U.S. government has explicitly embraced the FRO model.
Where the AI Action Plan Falls Short
Restricting State-Level Guardrails
The Administration’s AI Action Plan proposes to restrict federal AI funding to states when state AI rules “hinder the effectiveness” of that funding. While avoiding unnecessary red tape is sensible, this unclear standard could offer the administration a wide latitude to block state rules at its discretion. FAS has recently opposed preemption of state-level AI regulation by Congress in the absence of federal action. Without national standards for AI, state rules provide an opportunity to develop best practices for responsible AI adoption.
Failing to Address Bias in AI Systems
We are also concerned by the recommended revision to the NIST AI Risk Management Framework (RMF) that would eliminate references to diversity, equity, and inclusion. AI bias is a proven, measurable phenomenon, as documented by a broad scientific consensus from leading researchers and practitioners across sectors. Failing to address such biases leaves the public vulnerable to the harms of discriminatory or unfair systems that can affect people in areas like healthcare, housing, hiring, and access to public services. This includes deeply consequential biases, such as those affecting rural communities. A lack of action to address AI bias will only inhibit beneficial adoption and further erode trust in the accuracy of algorithmic systems.
The AI Action Plan contains a direction for the federal government to only procure AI models from developers who “ensure that their systems are objective and free from top-down ideological bias,” which is implemented via an associated executive order. Building modern AI systems involves a huge range of choices, including which data to use for training, how to “fine tune” the model for particular use-cases, and the “system prompt” which guides model behavior. Each of these stages can affect model outputs in ways that are not well understood and can be difficult to control. There is no standard definition for what constitutes a model that is “free from top-down ideological bias”, and this vague standard could easily be misused or improperly implemented at the agency level with unintended consequences for the public. We encourage the administration to instead focus on increasing transparency and explainability of systems as a mechanism to prevent unintended bias in outputs.
Ignoring the Environmental Costs and Opportunities
The Administration’s direction to remove mention of climate change from the RMF overlooks the very real climate and environment impacts associated with the growing resource demands of large-scale AI systems. Measuring and managing environmental impacts is an important component of AI infrastructure buildout, and removing this policy lever will also restrict AI adoption. This is also a missed opportunity to push forward the ways that AI can help tackle climate change and other environmental issues. In our recent AI and Energy Policy Sprint, we developed policy memos which highlighted the benefits AI could bring to our energy system and environment, while also highlighting ways of responding to AI’s environmental and health impacts.
The Importance of Public Trust
The current lack of public trust in AI risks inhibiting innovation and adoption of AI systems, meaning new methods will not be discovered and new benefits won’t be felt. A failure to uphold high standards in the technology we deploy will also place our nation at a strategic disadvantage compared to our competitors. Recognizing this issue, both the first and second Trump administrations have emphasized public trust as a key theme in their AI policy documents. Many of the research directions outlined in the administration’s AI Action Plan promise to steer AI technology in a more trustworthy direction and deliver widespread benefits to the public. However, several measures simultaneously threaten to undermine important guardrails, while cuts to important government programs also work against the goals the administration has set for itself.
The Federation of American Scientists will continue to collaborate with the scientific community to place rigorous evidence-based policy at the heart of delivering AI that works for all Americans.
Federation of American Scientists Statement on the Preemption of State AI Regulation in the One Big Beautiful Bill Act
As the Senate prepares to vote on a provision in the One Big Beautiful Bill Act, which would condition Broadband Equity, Access, and Deployment (BEAD) Program funding on states ceasing enforcement of their AI laws (SEC.0012 Support for Artificial Intelligence Under the Broadband Equity, Access, and Deployment Program), the Federation of American Scientists urges Congress to oppose this measure. This approach threatens to compromise public trust and responsible innovation at a moment of rapid technological change.
The Trump Administration has repeatedly emphasized that public trust is essential to fostering American innovation and global leadership in AI. That trust depends on clear, reasonable guardrails, especially as AI systems are increasingly deployed in high-stakes areas like education, health, employment, and public services. Moreover, the advancement of frontier AI systems is staggering. The capabilities, risks, and use cases of general-purpose models are predicted to evolve dramatically over the next decade. In such a landscape, we require governance structures that are adaptive, multi-layered, and capable of responding in real-time.
While a well-crafted federal framework may ultimately be the right path forward, preempting all state regulation in the absence of federal action would leave a dangerous vacuum, further undermining public confidence in these technologies. According to Pew Research, American concerns about AI are growing, and a majority of US adults and AI experts worry that governments will not go far enough to regulate AI.
State governments have long served as laboratories of democracy, testing policies, implementation strategies, and ways to adapt to local needs. Tying essential broadband infrastructure funding to the repeal of sensible, forward-looking laws would cut off states’ ability to meet the demands of AI evolution in the absence of federal guidance.
We urge lawmakers to protect both innovation and accountability by rejecting this provision. Conditioning BEAD Funding on halting AI regulation sends the wrong message. AI progress does not need to come at the cost of responsible oversight.
Position on President Trump’s Executive Order “Empowering Commonsense Wildfire Prevention and Response”
President Trump’s Executive Order (EO) “Empowering Commonsense Wildfire Prevention and Response” is the latest of several significant federal policy efforts aimed at tackling the wildfire crisis. Other recent efforts include the passage of the Fix Our Forest Act in the House and introduction of a bipartisan negotiated companion in the Senate; an Executive Order on expanding timber production; and the recently signed Aerial Firefighting Advancement Act of 2025.
The Federation of American Scientists (FAS) focuses on embedding science, data, and technology into government to support communities in preparing for, responding to, and recovering from wildfires. We are encouraged that the Administration and Congress are recognizing the severity of the wildfire crisis and elevating it as a national priority. Yet the devil is in the details when it comes to making real-world progress.
“Wildfires are burning faster and hotter than ever before, destroying communities and ecosystems and producing vast amounts of harmful smoke and debris,” said Dr. Hannah Safford, Associate Director of Climate and Environment at FAS. “As wildfires increasingly impact cities like Los Angeles and states beyond the western U.S., smart federal leadership on this issue is needed.”
FAS applauds several elements of President Trump’s EO. For instance, the EO correctly recognizes that wildfire technology and prescribed fire are powerful tools for reducing risk and strengthening wildfire resilience. FAS is also glad to see the Administration promote interagency coordination; emphasize the importance of state, local, and Tribal leadership; and recognize the intersection of wildfire resilience and other sectors, such as the grid and our bioeconomy.
“However,” said Jessica Blackband, Senior Manager of Climate and Environment at FAS, “the Executive Order also contains elements that do not seem feasible against a backdrop of enacted and proposed cuts to federal wildfire staff, programs, and funding.”
For example, President Trump’s FY2026 budget proposes significant cuts to federal agencies, including the National Oceanic and Atmospheric Administration (NOAA) and the U.S. Geological Survey (USGS) that provide critical data, forecasting tools, and other technical capabilities needed for wildfire preparedness and response (Section 3 of the EO). Workforce shortages in the U.S. Forest Service and partner agencies are raising alarm about readiness for extreme wildfires as well as capacity to carry out risk-reduction projects, including prescribed fires (Sec. 4(a)), safely and successfully. And erosion of federal technical expertise will likely make it difficult for agencies to revise wildfire-related rules (Secs. 4 and 5) in ways that are evidence-based and appropriately balance other health, economic, and environmental priorities.
FAS also has concerns about timelines and processes established in the EO. For example, section 2 gives agencies just 90 days to “consolidate their wildland fire programs to achieve the most efficient and effective use” of resources. This timeline coincides with wildfire season, when agencies are already stretched thin. Moreover, proposals and consensus recommendations for improving wildfire governance are available, including the final report of the Wildland Fire Mitigation and Management Commission. It is unclear how the EO will build on this substantial work.
Finally, FAS believes that the EO overemphasizes deregulation as a strategy for tackling the wildfire crisis. While there may be regulatory barriers or bureaucratic processes that could be streamlined or improved in the interest of wildfire resilience, other opportunities for progress are more potent. FAS recommends that future directives and policies provide greater support for science that improves our understanding of how wildfires impact people and places; technical assistance to support states and localities in wildfire planning; investments to reduce wildfire risk; development of metrics that make it easier to assess and track wildfire resilience; and approaches for ensuring transparent, responsible spending on wildfire.
“Tackling the wildfire crisis will require an integrated national approach that is grounded in evidence, carefully executed, and appropriately resourced,” said James Campbell, Wildfire Policy Specialist at FAS. “The Administration should work closely with Congress and the wildfire community in implementing this EO and any complementary policies.”
FAS stands ready to help advance constructive plans and proposals that further wildfire resilience. Our team is working to build a more fire-resilient nation through policy development and analysis, fellowships, and issue education. We look forward to continuing to engage with the Administration, Congress, and state, local, and nongovernmental leaders to this end.
Don’t Let American Allies Go Nuclear
President Trump is moving quickly to push U.S. allies to invest even more in their own defense. NATO allies have already committed to spend 3% of their GDP on defense, yet the U.S. is now calling for them to spend at least 5%. It is likely that U.S. allies in East Asia will soon face similar calls to do more. Greater investments in conventional capabilities make a lot of sense. However, there are some U.S. policy experts, officials and academics calling for more U.S. allies to go nuclear to reduce U.S. defense requirements. These calls are dangerously misguided and ignore the threat any proliferation – including by U.S. allies – poses to American security interests. They must be rejected wholesale by the Trump Administration.
One of the most enduring successes of U.S. national security policy has been its effort to limit the number of states with nuclear weapons. Predictions that dozens of countries might possess nuclear weapons did not materialize because of concerted U.S. actions. The risks include the reality that U.S. allies can and often do experience internal instability or even regime collapse, that any state with nuclear weapons creates a risk that those materials or knowhow can be stolen or diverted, that any state with nuclear weapon in a crisis might actually use those weapons, and lastly the reality that states with their nuclear weapons are less susceptible open to U.S. influence. There may be reasons why a state may want to go nuclear from their own perspective but there are few if any lasting benefits to American security that comes from proliferation to friends and allies.
Nine countries currently have nuclear weapons, but perhaps 40 additional states are technically advanced enough to build nuclear weapons if they chose to do so. Many of these states are U.S. allies or partners, including in Europe as well as Japan, South Korea, and even the island of Taiwan. That these states never went nuclear (although some tried) is due to a combination of factors, including the credibility of U.S. defense commitments to their security, the pressure America brought to bear when these states indicated a potential interest in building independent nuclear arsenals, and the recognition that if the world was serious about getting rid of all nuclear weapons then their spread was a step in the wrong direction.
The re-election of Donald Trump has understandably spooked many U.S. allies, renewing doubts that America will come to their aid. The growth of China’s military and economic power relative to the United States is adding to these concerns. More allies are asking now, just as they did during the Cold War if America would really risk Boston to protect Berlin, or Seattle to protect Seoul. As this question festers and as America’s relative power over China and other states ebbs, the lure to encourage U.S. friends to develop nuclear weapons of their own to deter or defeat an attack will grow. After all, the theory goes, why should the United States worry if its friends go nuclear?
In the real world, however, the spread of nuclear weapons anywhere complicates and undermines U.S. security. One reason is states are not always stable. In the 1970s, the U.S. supported its Treaty partner Iran acquiring nuclear reactors and advanced technology but in 1979, that regime was overthrown by the Islamic Revolution. Pakistan went nuclear when the U.S. needed its help fighting the Soviets in Afghanistan, and has faced wave after wave of instability and crisis. And South Korea is a more recent challenge. For the last few decades, South Korea was considered a stable and vibrant democracy – even hosting a Summit for Democracy last year. Under President Yoon, South Korea has voiced increasing interest in an independent nuclear arsenal. And just last year, a former Trump official, Elbridge Colby, expected to serve in a senior policy role at the Pentagon publicly encouraged South Korea to build their own nuclear weapons to deter North Korea and enable the U.S. to focus more on China. The situation in South Korea, with an impeached President and no clear sense of who controls the country’s military, would be a lot more dangerous if Seoul had nuclear weapons.
This is not just an issue for newer nuclear weapons states. Prior to the Soviet Union’s collapse in 1991, a coup created confusion for days over exactly who had the ability to control Soviet nuclear weapons. Following the USSR’s demise, nuclear weapons and materials remained at risk of theft and diversion for years and required massive U.S. efforts and investments to prevent their loss. And even the United States is not immune from these risks. The 2021 insurrection raised nuclear risk to the point that the Speaker of the House had to publicly ask the Chairman of the Joint Chiefs about the risk that President Trump might use nuclear weapons in a gambit to remain in power, and Chairman Milley took extraordinary steps to insert himself into the nuclear chain of command to preempt that risk. Any nuclear arsenal anywhere is a potential danger if political circumstances change.
And states with nuclear weapons create a nuclear risk if nuclear technology, materials and knowhow are stolen or diverted. Five of today’s nuclear weapon states – America, Russia, China, France, and Pakistan – have either knowingly or unwittingly helped other states go nuclear. Even if theft or transfer were not an issue, when new states have gone nuclear in the past, others have followed. America’s nuclear success led the Soviet Union to build them as well. This in turn led the UK and France to follow suit. These four nuclear weapon programs fueled China’s desire to join the club. Beijing having the bomb drove India to do the same, which then led Pakistan to follow suit.
And any nuclear state might decide one day to use those weapons. Every nuclear leader must get every nuclear decision right, every time or boom. The history of U.S. and Soviet nuclear deterrence is marked as much by nuclear misunderstandings and potential accidents as by stable deterrence. India and Pakistan have the same problem. It is reasonable to assume new nuclear states with nuclear weapons would encounter many of the same risks.
And finally, from a very direct Americentric point of view, each state that acquires their own nuclear weapons lessens the ability of the United States to influence, control or dictate security outcomes in that state and region. While not the message U.S. diplomats use openly when trying to work diplomatically to stop proliferation, the issue of influence is as relevant to U.S. allies as adversaries. To the extent that the U.S. security is enhanced by being able to heavily influence how states around the world act, then enabling the spread of nuclear weapons undermines that ability.
It is and will continue to be tempting for the next Administration to find rapid and easy solutions to long-standing security challenges. Empowering U.S. allies to do more so Washington can do and spend less, or focus more effectively on fewer challenges is an understandable policy outcome. But enabling, or looking the other way at the spread of nuclear weapons is not in America’s interests anymore today than it was in the 20th century.
Energy Dominance (Already) Starts at the DOE
Earlier this week, the Senate confirmed Chris Wright as the Secretary of Energy, ushering in a new era of the Department of Energy (DOE). In his opening statement before Congress, Wright laid out his vision for the DOE under his leadership—to unleash American energy and restore “energy dominance”, lead the world in innovation by accelerating the work of the National Labs, and remove barriers to building energy projects domestically. Prior to Wright’s nomination, there have already been a range of proposals circulating for how, exactly, to do this.
Of these, a Trump FERC commissioner calls for the reorganization – a complete overhaul – of the DOE as-is. This proposed reorganization would eliminate DOE’s Office of Infrastructure, remove all applied energy programs, strip commercial technology and deployment funding, and rename the agency to be the Department of Energy Security and Advanced Science (DESAS).
This proposal would eliminate crucial DOE offices that are accomplishing vital work across the country, and would give the DOE an unrecognizable facelift. Like other facelifts, the effort would be very costly – paid for by the American taxpayer, unnecessary, and a waste of public resources. Further, reorganizing DOE will waste the precious time and money of the Federal government, and mean that DOE’s incoming Secretary, Chris Wright, will be less effective in accomplishing the goals the President campaigned on – energy reliability, energy affordability, and winning the competition with China. The good news for the Trump Administration is that DOE’s existing organization structure is already well-suited and well-organized to pursue its “energy dominance” agenda.
The Cost of Reorganizing
Since its inception in 1977, the Department of Energy has evolved several times in scope and focus to meet the changing needs of the nation. Each time, there was an intent and purpose behind the reorganization of the agency. For example, during the Clinton Administration, Congress restructured the nuclear weapons program into the semi-autonomous National Nuclear Security Administration (NNSA) to bolster management and oversight.
More recently, in 2022, another reorganization was driven by the need to administer major new Congressionally-authorized programs and taxpayer funds effectively. With the enactment of the Bipartisan Infrastructure Law (BIL) and the Inflation Reduction Act (IRA), DOE combined existing programs, like the Loan Programs Office, with newly-authorized offices, like the Office of Clean Energy Demonstrations (OCED). This structure allows DOE to hone a new Congressionally-mandated skill set – demonstration and deployment – while not diluting its traditional competency in managing fundamental research and development.
Even when they make sense, reorganizations have their risks, especially in a complex agency like the DOE. Large-scale changes to agencies inherently disrupt operations, threaten a loss of institutional knowledge, impair employee productivity, and create their own legal and bureaucratic complexities. These inherent risks are exacerbated even further with rushed or unwarranted reorganizations.
The financial costs of reorganizing a large Federal agency alone can be staggering. Lost productivity alone is estimated in the millions, as employees and leadership divert time and focus from mission-critical projects to logistical changes, including union negotiations. These efforts often drag on longer than anticipated, especially when determining how to split responsibilities and reassign personnel. Studies have shown that large-scale reorganizations within government agencies often fail to deliver promised efficiencies, instead introducing unforeseen costs and delays.
These disruptions would be compounded by the impacts an unnecessary reorganization would have on billions of dollars in existing DOE projects already driving economic growth, particularly in rural and often Republican-led districts, which depend on the DOE’s stability to maintain these investments. Given the high stakes, policymakers have consistently recognized the importance of a stable DOE framework to achieve the nation’s energy goals. The bipartisan passage of the 2020 Energy Act in the Senate reflects a shared understanding that DOE needs a well-equipped demonstration and deployment team to advance energy security and achieve American energy dominance.
DOE’s Existing Structure is Already Optimized to Pursue the Energy Dominance Agenda
In President Trump’s second campaign for office, he ran on a platform of setting up the U.S. to compete with China, to improve energy affordability and reliability for Americans, and to address the strain of rising electricity demand on the grid by using artificial intelligence (AI). DOE’s existing organization structure is already optimized to pursue President Trump’s ‘energy dominance’ agenda, most of which being implemented in Republican-represented districts.
Competition with China
As mentioned above, in response to the 2021 Bipartisan Infrastructure Law (BIL), DOE created several new offices, including the Manufacturing and Energy Supply Chains Office (MESC) and the Office of Clean Energy Demonstrations (OCED). Both of these offices are positioning the U.S. to compete with China by focusing on strengthening domestic manufacturing, supply chains, and workforce development for critical energy technologies right here at home.
MESC is spearheading efforts to establish a secure battery manufacturing supply chain within the U.S. In September 2024, the Office announced plans to deliver over $3 billion in investments to more than 25 battery projects across 14 states. The portfolio of selected projects, once fully contracted, are projected to support over 8,000 construction jobs and over 4,000 operating jobs domestically. These projects encompass essential critical mineral processing, battery production, and recycling efforts. By investing in domestic battery infrastructure, the program reduces reliance on foreign sources, particularly China, and enhances the U.S.’s ability to compete and lead on a global scale.
In passing BIL, Congress understood that to compete with China, R&D alone is not sufficient. The United States needs to be building large-scale demonstrations of the newest energy technologies domestically. OCED is ensuring that these technologies, and their supply chains, reach commercial scale in the U.S. to directly benefit American industry and energy consumers. OCED catalyzes private capital by sharing the financial risk of early-stage technologies which speeds up domestic innovation and counters China’s heavy state-backed funding model. In 2024 alone, OCED awarded 91 projects, in 42 U.S. states, to over 160 prize winners. By supporting first-of-a-kind or next-generation projects, OCED de-risks emerging technologies for private sector adoption, enabling quicker commercialization and global competitiveness. With additional or existing funding, OCED could create next-generation geothermal and/or advanced nuclear programs that could help unlock the hundreds of gigawatts of potential domestic energy from each technology area.
Energy Affordability and Reliability
Another BIL-authorized DOE office, the Grid Deployment Office (GDO), is playing a crucial role in improving energy affordability and reliability for Americans through targeted investments to modernize the nation’s power grid. GDO manages billions of dollars in funding under the BIL to improve grid resilience against wildfires, extreme weather, cyberattacks, and other disruptions. Programs like the Grid Resilience and Innovation Partnerships (GRIP) Program aim to enhance the reliability of the grid by supporting state-of-the-art grid infrastructure upgrades and developing new solutions to prevent outages and speed up restoration times in high-risk areas. The U.S. is in dire need of new transmission to keep costs low and maintain reliability for consumers. GDO is addressing the financial, regulatory, and technical barriers that are standing in the way of building vital transmission infrastructure.
The Office of State and Community Energy Programs (SCEP), also part of the Office of Infrastructure, supports energy projects that help upgrade local government and residential infrastructure and lower household energy costs. Investments from BIL and IRA funding have already been distributed to states and communities, and SCEP is working to ensure that this taxpayer money is used as effectively as possible. For example, SCEP administers the Weatherization Assistance Program (WAP), which helps Americans in all 50 states improve energy efficiency by funding upgrades like insulation, window replacements, and modern heating systems. This program typically saves households $283 or more per year on energy costs.
Addressing Load Growth by Using AI
The DOE’s newest office, the Office of Critical and Emerging Tech (CET), leads the Department’s work on emerging areas important to national security like biotechnology, quantum, microelectronics, and artificial intelligence (AI). In April, CET partnered with several of DOE’s National Labs to produce an AI for Energy report. This report outlines DOE’s ongoing activities and the near-term potential to “safely and ethically implement AI to enable a secure, resilient power grid and drive energy innovation across the economy, while providing a skilled AI-ready energy workforce.”
In addition to co-authoring this publication, CET partners with national labs to deploy AI-powered predictive analytics and simulation tools for addressing long-term load growth.
By deploying AI to enhance forecasting, manage grid performance, and integrate innovative energy technologies, CET ensures that the U.S. can handle our increasing energy demands while advancing grid reliability and resiliency.
The Path Forward
DOE is already very well set up to pursue an energy dominance agenda for America. There’s simply no need to waste time conducting a large-scale agency reorganization.
In a January 2024 Letter from the CEO, Chris Wright discusses his “straightforward business philosophy” for leading a high-functioning company. As a leader, he strives to “Hire great people and treat them like adults…” which makes Liberty Energy, his company, “successful in attracting and retaining exceptional people who together truly shine.” Secretary Wright knows how to run a successful business. He knows the “secret sauce” lies in employee satisfaction and retention.
To apply this approach in his new role, Wright should resist tinkering with DOE’s structure, and instead, give employees a vision, and get off to the races of achieving the American energy dominance agenda without wasting time, the public’s money, and morale. Instead of redirecting resources to reorganizations, the DOE’s ample resources and existing program infrastructure should be harnessed to pursue initiatives that bolster the nation’s energy resilience and cut costs. Effective governance demands thoughtful consideration and long-term strategic alignment rather than hasty or superficial reorganizations.
Trump Jr: “Declassify Everything!!!”
On November 8 Donald J. Trump Jr., the President’s oldest son, tweeted: “DECLASSIFY EVERYTHING!!!” adding “We can’t let the bad actors get away with it.”
This was not an actual policy proposal and it was not seriously intended for classification officials or even for Trump’s own father, who as President is the one ultimately responsible for classification policy.
Rather, it was directed at Trump Jr.’s 6.4 million Twitter followers, telling them that classification is a corrupt process that protects “bad actors” and that must therefore be discredited and dismantled. It’s a juvenile notion but not, given the size and malleability of Trump’s audience, an inconsequential one.
To the extent that national security classification is in fact required, for example, to protect advanced military technologies, the conduct of diplomacy or the collection of intelligence, it is important to establish and maintain the legitimacy of classification policy. For the same reason, abuse of classification authority can itself be a threat to national security.
The current executive order on classification policy (sect. 1.7a(1)) directs that “in no case shall information be classified . . . in order to conceal violations of law.”
But this is merely a limitation on the classifier’s mental state — which is unverifiable — and not on classification itself. It is entirely permissible for classified information to conceal violations of law, according to a judicial interpretation of the executive order, as long as the information is not classified with that specific purpose (“in order to”) in mind. This is a standard that has never been enforced and that is probably unenforceable.
So one step that the incoming Biden Administration could take to enhance the integrity and accountability of classification policy would be to direct that classification may not conceal violations of US law at all, whether or not that is the intent of classifying. (It is probably necessary to specify “US” law since classified intelligence collection may often involve the violation of foreign laws.)
Donald Trump is the first president since George H.W. Bush who made no formal changes to the executive order on classification policy.
Instead, Trump often defied or disregarded existing classification and declassification policies, withholding previously public information (e.g. the number of nuclear warheads dismantled each year) and disclosing normally classified information (e.g. an actual application for counterintelligence surveillance) when it advanced his political interests to do so.
But it seems that arbitrary secrecy combined with selective declassification is not the way to stop “bad actors.”