A Scenario for Jihadist Nuclear Revenge
The Greatest Threat
The weapon was ready, a simple fission device similar to the bomb that destroyed Hiroshima. It had been finally assembled in a rented storage space on the outskirts of Las Vegas. Gulbuddin Hekmatyar had spent years quietly contemplating while meticulously planning this diabolical, logistically challenging mission. Among other things, the plot necessitated recruiting and directing a number of operatives, some technically skilled, located in several countries. All were individuals devoted to his cause and committed to the Jihadist goal of detonating a nuclear bomb in an American city. He chose Las Vegas because the city epitomized western decadence.
The bomb’s essential component – 140 pounds of highly enriched uranium (HEU) – had been stolen or secretly purchased, bit-by-bit, mostly from Pakistan, but also from India, North Korea, Russia, Ukraine and Kazakhstan. It took years to collect, hide and safeguard all the necessary HEU in northwest Pakistan. From there, small pieces of the fissile material and some structural bomb components, hidden and well shielded in multiple shipments, were transported to U.S. ports or border crossings, and eventually to Las Vegas and the rented storage space. With all the components covertly acquired or fabricated by dedicated Jihadists in Pakistan and the United States, the relatively simple bomb finally could be assembled. It was comprised of a long, large-bore, artillery-type barrel; a heavy-duty breech; and enough chemical explosive to propel an appropriately shaped, 70-pound HEU piece through the barrel at very high velocity into another appropriately shaped, 70-pound piece of HEU affixed to the end of the barrel. Slamming together these two sub-critical masses would create the critical mass needed for an explosive chain reaction.
It was time. The plan of attack was straightforward and foolproof. Weighing under a ton and less than a dozen feet long, the weapon in its lead-lined crate fit easily inside a small, rented truck. A lone, suicidal operative drove and parked the truck near the Strip, then activated the electronic device triggering the detonator that set off the chemical explosion. The HEU bullet accelerated through the barrel and merged almost instantaneously with the target HEU. Within microseconds, the critical mass exploded, releasing kilotons of energy, a blinding, rapidly expanding ball of light, heat and deadly radiation. A shock wave propagated through the atmosphere, flattening almost every building within a half-mile of the detonation point. Tens of thousands were dead or injured. Las Vegas was in ruins. The threat had become reality.
When President Obama declared in 2009 that “nuclear terrorism is the most immediate and extreme threat to global security,” it was scarcely noticed. Yet when questionable sources announced that the Mayan Calendar predicted the end of the world in 2012, media and public attention was astonishing. The apocalyptic prediction arising from myth took hold, while a warning of potential catastrophe based in reality, put forth by Barack Obama in Prague, passed us by. Supernatural doomsday scenarios readily gain traction in our public discourse, but threats to our civilization from proven nuclear dangers elude us.
The public and press largely ignored other sobering news in 2010 when Wikileaks revealed that a 2009 cable from the U.S. Ambassador to Pakistan, Anne W. Patterson, warned that “our major concern is not having an Islamic militant steal an entire weapon, but rather the chance someone working in government of Pakistan facilities could gradually smuggle out enough enriched uranium to eventually make a weapon.”
By raising the specter of nuclear terrorism, the Wikileaks revelation gave concrete urgency to President Obama’s abstract concerns. But few paid attention, in part because few understand nuclear weapons risks and realities.
Passage of time and reluctance to think the unthinkable have generated complacency. No nuclear weapon has been used aggressively since the August 9, 1945, attack on Nagasaki. Despite the existence of vast numbers of nuclear weapons, Americans expect nuclear restraint because they believe Mutually Assured Destruction (MAD) is a reliable deterrent. MAD presumably ensures that a country first using nuclear weapons will be wiped out by a retaliatory blow. But if a non-state entity were to perpetrate a nuclear weapons attack, at whom and where would retaliation be directed? An act of nuclear terrorism would obviate 69 years of stability engendered by MAD, an appropriately chosen topic of satirical banter in the film “Dr. Strangelove,” yet a grim reality.
Obama’s words that nuclear terrorism is an “immediate and extreme threat” are not an exaggeration. Terrorists now have new opportunities to covertly fabricate nuclear weapons on their own, and the threat is compounded by the potential anonymity of the attackers.
The cable allegedly sent by Ambassador Patterson leads to several questions: what is enriched uranium and how available is it? How is it used in a bomb, and who could use it? Where and how could it be delivered? What would be its effect? And perhaps the first and biggest question – why would terrorists aspire to manufacture, deploy, and detonate a nuclear weapon?
The 9/11 attacks marked the beginning of a “Terrorist Era” with a capital T. That triple attack profoundly disturbed, shocked and injured the nation, psychologically as well as physically. It suggested that a goal of certain terrorists is the destruction of the United States and its allies, and nuclear capability would make that goal attainable.
In 1998, Osama bin Laden declared that it was his Islamic duty to acquire weapons of mass destruction. Because Islam deplores killing women and children, religious justification was sought for such weapons. In 2003, three Saudi clerics associated with Al Qaeda provided justification in a fatwa that stated:“One kills in a good manner only when one can.”
Thus the “why” can be revenge for the deaths of Muslim civilians or Osama bin Laden, Jihadist punishment of a decadent, anti-Islamic civilization, or retribution for western support of Israel. Still, the easily stated words “nuclear revenge” are not readily internalized. Unlike “tsunami” or “colon cancer,” the term “nuclear terrorism” does not usually evoke a visceral reaction. Such a response is unlikely until people intellectually and emotionally comprehend the potential threat of rogue nuclear weapons. And comprehension requires some understanding of the bomb itself.
In addition to understanding the weapon, people also must grasp the feasibility and consequences of an act of nuclear terrorism. A credible scenario can provide this. In his book, The Second Nuclear Age, Yale Professor Paul Bracken argues that war games based upon scenarios involving nuclear weapons played a significant role in clarifying and shaping strategic thinking during the height of the Cold War. “Scenarios set the stage for the game’s interactions,” he wrote. “Scenarios…are hypothetical plot outlines of plausible future developments. They are not forecasts or predictions…”
The Pentagon hypothesizes terrorist scenarios, but the public does not. Our opening Las Vegas scenario attempts to focus the reader’s mind on the real potential for nuclear catastrophe.
But first the Bomb.
The Bomb
Tremendous energy can be released when the nucleus or inner core of an atom undergoes a transformation. For uranium, the energy releasing transformation is the splitting apart or fission of the nucleus, producing various combinations of lighter atoms such as barium and krypton as “fission products.”
Uranium can exist in different forms or “isotopes,” but all isotopes of uranium contain 92 positively charged protons in the nucleus with 92 negatively charged electrons dancing around the nucleus. These charged particles determine uranium’s chemical properties. However, the uranium nucleus also can contain varying numbers of uncharged neutrons. Somewhat greater than ninety-nine percent of uranium found in nature – uranium isotope 238 – has 146 neutrons in the nucleus. Thus the isotope’s 92 protons and 146 neutrons account for its atomic weight of 238.
Uranium-235, with only 143 neutrons, is the dangerous isotope –because it tends to easily fission if it absorbs a neutron. The fissioning of U-235 powered the bomb that exploded over Hiroshima. Fortunately this isotope is very rare; less than one percent of all forms of uranium found in the earth consist of U-235. Uranium can create an explosive chain reaction—only if U-235 is in highly concentrated form, which is extremely difficult to obtain as described later. But first we explain the basics of nuclear bomb design.
While modern hydrogen-plutonium bombs use a fission-fusion reaction to create the most powerful explosions (which can also use highly enriched uranium instead of plutonium to start the fission reaction), the easiest first-generation atomic bomb to construct entails only fission of highly enriched uranium (HEU), with a concentration of typically 80 percent or greater in the fissile isotope U-235. The Hiroshima bomb was essentially an artillery gun in which chemical explosives fired one 70-pound piece of HEU into another 70-pound piece of HEU, with an average enrichment of 80 percent U-235. The design was so simple that J. Robert Oppenheimer, scientific director of Los Alamos, decided that the prototype did not need to be tested. (One of the reasons not to do a proof test was due to the very limited HEU available during the Second World War.) Indeed the first test of this gun-type bomb occurred when it exploded with such devastating effect at 1,900 feet above Hiroshima on August 6, 1945, killing nearly 100,000 people. Weapons developers at Los Alamos avoided using the word bomb, instead giving euphemistic names such as gadget to their creations. The Hiroshima weapon was inaptly named “Little Boy.”
During the Manhattan Project, the great challenge was collecting and concentrating fissionable U-235. Because U-238 and U-235 have identical chemical properties, separation can only be achieved by exploiting the slight difference in mass arising from one isotope having three more neutrons than the other. One method of separation for enrichment purposes was developed using electric and magnetic forces in a modified form of the cyclotron called the calutron. A second method involved creating a compound in gaseous form of uranium and fluorine, then passing the gas through successive microscopic filters making use of the principle of diffusion.
After the Second World War, improved centrifuges emerged as a more efficient method for enriching uranium. A Dutch company, which became part of the Urenco consortium that also includes Germany and the United Kingdom, was an early adopter of the improved centrifuge technology. Commercial production of enriched uranium for nuclear power plants became a worldwide activity. A. Q. Khan, a Pakistani metallurgist working at the Dutch facility, stole the centrifuge design drawings and brought the technology to Pakistan by the mid-1970s. Throughout the 1980s to the early 2000s, he then sold enrichment equipment to Iran, North Korea, and Libya, and had a vast network of suppliers in at least a dozen other countries.
Having used these centrifuge designs to enable large-scale production of enriched uranium, today Pakistan is rapidly achieving status as having one of the largest and fastest growing stockpile of nuclear weapons after the United States, Russia and China. While some nuclear-armed countries are reducing their weapons count, Pakistan has a vigorous program of nuclear weapons development. Its stockpile is thought to have 100 to 200 nuclear weapons.
Production of nuclear weapons is of great concern, but production of highly enriched uranium is even more worrisome. Although a nuclear bomb might be stolen from a country’s stockpile, it would have anti-activation safeguards (such as access codes and electronic locks) that a thief would find very difficult to penetrate. However, highly enriched uranium for a terrorist is like flour for a baker. Each material is simply one ingredient from which something much more impressive can be concocted. Pakistan continues to produce weapons-grade U-235 at a more intense rate than any country in the world. It is reliably estimated that they have stockpiled thousands of pounds of enriched U-235 that could lead to the fabrication of dozens of new nuclear weapons.
Eyes continue to focus on Pakistan as a potential source of nuclear bomb material. Yet unsecured highly enriched uranium elsewhere has been a worry for many years. Of particular concern have been the vast amounts of weapons-grade uranium that were left relatively unguarded in Russia, Ukraine, Belarus and Kazakhstan after the break-up of the Soviet Union. These have been potential access points for terrorists. Hundreds of secret bombs could have been fabricated.
Prior to 9/11, we could not imagine rogue, non-state entities having the ability to construct a nuclear weapon. Yet vast numbers of reports, documents, drawings and photographs from the Manhattan Project have been declassified. The Little Boy development work at Los Alamos is available for the world to examine. Following 9/11, government agents visited war museums in the United States to remove publicly displayed, artillery-gun components replicating Little Boy. But the proverbial horse was already out of the barn.
Conceivably, determined terrorists could acquire 140 pounds of weapons-grade uranium-235, the amount used in the Hiroshima bomb. While a person weighing 140 pounds would fully occupy a seat at a dinner table, 140 pounds of uranium, the densest of all naturally occurring elements, is less than the size of a football.With the material in hand, processing and fabrication steps for constructing a weapon rely on well-established and widely known metallurgical and manufacturing techniques. Who then might do this? Where would construction take place? And under whose leadership?
A Return to Our Scenario
The villain of our hypothetical scenario is the leader of a militant group located in the tribal territory of Northwestern Pakistan.Skeptics may doubt that our protagonist, Gulbuddin Hekmatyar, could obtain the equipment and expertise needed for weaponization of highly enriched uranium. While not on Abercrombie and Kent tourist itineraries, the frontier region of Northwest Pakistan is the site of the colorful village of Darra Adam Khel. This unique tribal enclave near the Khyber Pass, just 20 miles South of Peshawar, has been manufacturing copies of small weapons since the late 19th century using basic lathes, drills and other readily available tools. During the Mujahideen struggle with the Soviet Union in the 1980s, the United States was not unhappy to see their production of anti-aircraft weapons. Darra Adam Khel is a major source of weapons in the South Asia region. The potential to fabricate the components for a Little Boy clone clearly exists there.
Osama bin Laden and other Al Qaeda leaders have been eliminated, but other militant jihadists have the capacity and the will to engage in development and use of a nuclear weapon. We chose Gulbuddin for our scenario because he was involved with the 1993 bombing of the World Trade Center, he controls a formidable belligerent organization with the resources to actualize this sequence of events, and he is not part of Al Qaeda or the Taliban. An Afghan student of engineering at Kabul University in the early 1970s, he organized at that time what was probably the first militant Islamic organization in Afghanistan. His student group shot at and threw acid at women in Kabul who were wearing mini-skirts. In a confrontation in 1972 with the rival Maoist political group on campus, Gulbuddin shot and killed their leader. After being imprisoned, he escaped and was given refuge by Islamic fundamentalist elements of the Pakistani government in 1975. Some officials in Pakistan, which had border region disputes with Afghanistan since its founding in 1947, saw in Gulbuddin a potential ally in future conflicts with Afghanistan.
In the early 1980s, when the United States started channeling large amounts of funds and weapons to the Mujahideen for their struggle with the Soviet Union, the Pakistan intelligence agency, the ISI, provided Gulbuddin with a substantial portion of those resources. This enabled the charismatic fanatic to establish a formidable organization known as Hezb-e-Islami.
During the mid-1980s Gulbuddin was instrumental in organizing terrorist training camps in Afghanistan to which “Arab” fighters were invited. Gulbuddin welcomed Osama bin Laden, who first came to Afghanistan to fight the infidel Soviets.
Gulbuddin and his organization did not pursue the Soviets as fully as they might have, since he was waiting to use his fighting potential in a putsch to take over Afghanistan following the departure of the Red Army. He did indeed engage in a civil war for control of Afghanistan that began in 1992. But after achieving the position of Prime Minister of Afghanistan in 1993, Gulbuddin was eventually defeated by the Northern Alliance led by Massoud. With the fall of Gulbuddin, the ISI of Pakistan threw their support in 1994 to the newly organized Taliban.
Few are aware of Gulbuddin’s contacts with the perpetrators of the 1993 bombing of the World Trade Center. Those connections and his meetings with the Blind Sheik were revealed in the trials of the World Trade Center bombers held in New York City. It is too often said that the weakening of Al Qaeda ensures the safety of the U.S. from terrorist attack. However, the 1993 bombing of the World Trade Center involved non-Al Qaeda players and leadership figures from that event are still active. This is just one example of a non-Al Qaeda terrorist group that might become a perpetrator of nuclear terrorism.
Today, Gulbuddin maintains a militant presence in the frontier region and has the organizational ability to engage in ambitious terrorist actions. Gulbuddin is neither a tribal “war lord” nor a narrowly educated religious militant. He is a sophisticated intellectual and political leader who completed two years of engineering education. There is every indication that he is as vicious a proponent of terrorism as was Osama bin Laden.
Nothing suggests that Gulbuddin is, in fact, plotting a nuclear attack on an American city. But he is the key player in our scenario because he has the knowledge, resources and frame of mind for implementing such an attack. If there is one such person and group, there are likely others.
The fissile materials available in Pakistan can be fabricated in the Khyber region to serve as components for a gun-type Hiroshima bomb. The amount of radiation released by the highly enriched uranium can be easily shielded and thus easily elude detection at border crossings or from aerial drones. Since suicidal jihadists probably would assemble it, many of the features that were built into Little Boy 69 years ago to ensure safe delivery and controlled detonation could be ignored.
While this scenario has focused on terrorism originating in the Afghanistan-Pakistan border area, other scenarios might be equally plausible. In May 2011, the Belfer Center for Science and International Affairs at Harvard University issued a report entitled, “The U.S.-Russia Joint Assessment on Nuclear Terrorism.” The study group analyzed possible threats from three terrorist organizations known to have systematically sought to obtain nuclear weapons: Al Qaeda, groups in the Northern Caucasus, and the Japanese cult group, Aum Shinrikyo. Each could be a suitable scenario protagonist. If Iran began producing tens of pounds of HEU, then the possibility of Hezbollah obtaining that material would also merit consideration.
Additional scenarios can be hypothesized with sociopaths who are American citizens. Two figures stand out as prototypes with the organizational and technical capacity needed for implementation. One is Timothy McVeigh, whose homemade bomb destroyed the Alfred P. Murrah Federal Building in Oklahoma City on April 19, 1995. The other is Ted Kaczynski, the mathematics genius known as the Unabomber. He perpetrated seventeen explosive attacks killing three people between 1978 and his arrest in 1996.
The first public alert to the possibility of a small group of individuals in the United States building a nuclear bomb to attack society came in the early 1970s from Theodore B. Taylor, a physicist who invented highly efficient, small sized nuclear weapons at Los Alamos National Laboratory. He recognized and was obsessed by the possibility that fissile material could be stolen from commercial facilities that were enriching uranium. The U.S. government had encouraged corporations to process uranium for use in nuclear reactors. In his book, The Curve of Binding Energy, award-winning writer John McPhee documented the story of this eccentric but highly creative physicist. His account was first published in the New Yorker in 1973. Both Taylor and McPhee seemed convinced that a rogue nuclear weapon would detonate somewhere in the United States prior to the beginning of the 21st Century.
The vulnerabilities of enriched uranium supplies in the United States in the 1970’s were astonishing. We assume that such homeland dangers have been ameliorated. Yet we are aghast at the July 28, 2012, spectacle of an 82-year-old nun and two equally unlikely compatriots penetrating the innermost sanctum of the highly enriched uranium facility at Oak Ridge, Tennessee, and spraying the storage building with graffiti. The words they posted said, “Plowshares Please Isaiah.” If such lax security is exposed in Bear Creek Valley, U.S.A., what might be the case in Pakistan, Russia, North Korea or China?
Implications and Actions
A successful act of nuclear terrorism would, in a blinding flash, change the nature of civilization, as we know it. When the consequences of an action are so enormous, perhaps one should pause to reflect upon it, even if scenarios and anecdotes may not be persuasive. But our lives are frequently influenced by low probability events. We wear seat belts. We buy lottery tickets.
Perhaps we should be more proactive in supporting our government’s actions to ameliorate potential risks. The international community is currently discussing at least three treaties. One is to create uniform legal frameworks for prosecuting terrorists who seek to use nuclear materials, another is to develop uniformly effective security procedures for safeguarding nuclear materials, and the third is the Fissile Material Cut-off Treaty. It is likely that these issues are far more important and could have much greater consequences than some of the actions that might be taken to thwart nuclear weapons development in Iran or North Korea. Nuclear policy priorities need to emphasize non-state weapons proliferation at least at the same level as state-centered weapons proliferation.
In the non-government sector, non-state weapons proliferation also should be as central in public forums, the press, blogs, general discourse and academic discussions as the continuing crises in North Korea and in Iran.
The fact that the Federal Emergency Management Agency (FEMA) and the Department of Homeland Security are engaging in detailed analyses of emergency responses to a Hiroshima-type bomb detonation in central Washington D.C. means that they are taking that possibility seriously. While the Gulbuddin scenario chose Las Vegas as a symbolic target, another team of jihadists might choose to focus on our nation’s capital.
Today, the news media continually reports about the potential for North Korea to attack the United States with nuclear-tipped intercontinental ballistic missiles. But an attack using a crate holding a lead-shielded, twelve-foot long artillery gun, delivered by sea to one of America’s busiest container ports, such as ports in New Jersey, New York, or California, is a more likely mode of attack and would be equally effective and deadly.
“Nuclear Fuel Memos Expose Wary Dance With Pakistan,” New York Times, November 30, 2010.
Nasir Bin Hamad Al-Fahd, “A Treatise on the Legal Status of Using Weapons of Mass Destruction Against Infidels,” 2003, available at http://ahlussunnahpublicaties.files.wordpress.com/2013/04/42288104-nasir-al-fahd-the-ruling-on-using-weapons-of-mass-destruction-against-the-infidels.pdf
Paul Bracken, “The Second Nuclear Age: Strategy, Danger, and the New Power Politics” (Times Books, 2012)
See FAS’s world nuclear forces chart: /issues/nuclear-weapons/status-world-nuclear-forces/ . This estimate shows that Pakistan has 120-199 nuclear weapons, and the UK and France have about 225-300. But the Pakistani nuclear weapons program is estimated to be growing while the UK and France have stopped producing new nuclear weapons.
See the video at http://www.downvids.net/light-engineering-in-darra-adam-khel-pakistan-amazig–472252.htm, accessed on May 14, 2014. This YouTube video shows the light manufacturing equipment in Darra Adam Khel with capacity to manufacture a Hiroshima firing unit.
For example, the profile by Michael Crowley, “Our Man in Kabul?” New Republic, March 9, 2010, http://www.newrepublic.com/article/politics/our-man-kabul
Belfer Center study is available at http://belfercenter.ksg.harvard.edu/publication/21087/usrussia_joint_threat_assessment_of_nuclear_terrorism.html
John McPhee, The Curve of Binding Energy (Farrar, Straus and Giroux, New York, 1973) “He (Ted Taylor) did say he thought it was already too late to prevent the making of a few bombs (by terrorists), here and there, now and then. Society would just have to take that, and go on. None of this was said with the least trace of cynicism or despair.” (p. 196)
Matthew L. Wald and William J. Broad, “Security Questions are Raised by Break-In at a Nuclear Site,” New York Times, August 7, 2012, http://www.nytimes.com/2012/08/08/us/pacifists-who-broke-into-nuclear-weapon-facility-due-in-court.html and see the following website for the image the protestors made: http://cdn.knoxblogs.com/atomiccity/wp-content/uploads/sites/11/2013/07/heumf-blood.jpg
National Capital Region Key Response Planning Factors for the Aftermath of Nuclear Terrorim – November 2011 – FEMA, Homeland Security and Lawrence Livermore National Laboratory, available at /irp/agency/dhs/fema/ncr.pdf
Edward A. Friedman is Professor Emeritus of Technology Management at Stevens Institute of Technology in Hoboken, N.J. He holds a B.S. in Physics from MIT and a Ph.D. in Physics from Columbia University. He was director of a USAID program to develop an indigenous college of engineering in Afghanistan (1970-73) when Gulbuddin Hekmatyar was arrested for murder of a political rival at Kabul University. Dr. Friedman was a founder and senior vice president of the Afghanistan Relief Committee (1979-1995). In 2012 he developed and taught a graduate course on Nuclear Weapons in International Relations as an Adjunct Professor at The John C. Whitehead School of Diplomacy and International Relations at Seton Hall University.
Roger K. Lewis is an Architect and Planner. He has been a long-term columnist for the Washington Post’s “Shaping the City.” He is Planning and Preservation Trustee for the National Children’s Museum and President and Director of the Peace Corps Commemorative Foundation. His book, “Architect? A Candid Guide to the Profession” is known as the best basic introduction to the profession. He is Professor Emeritus of Architecture at the University of Maryland School of Architecture.
A Credible Radioactive Threat to the Sochi Olympics?
With the Sochi Olympics set to start on February 6th there has been an escalating concern about security threats to the Games. There are hunts for female suicide bombers (“black widows”), video threats from militant groups, etc., all of which have triggered a massive Russian security response, including statements by President Putin insuring the safety of the Games.
Many of the security concerns are raised by the proximity of Sochi to Chechnya and relate to the threats expressed by Chechen leader Doku Umarov who exhorted Islamic militants to disrupt the Olympics.
In the past weeks the region has seen Islamic militants claims that they carried out two recent suicide bombings in Volgorad which tragically killed 34 people and injured scores of others. Volgograd is about 425 miles from Sochi and although the media stresses the proximity it is a considerable distance.
Radioactive Theft in Mexico: What a Thief Doesn’t Know Can Kill Him
While the theft of a truck carrying radioactive cobalt made international headlines, this was unfortunately not the first time thieves or scavengers have exposed themselves or others to lethal radiation. Probably the most infamous case was on September 13, 1987 in Goiania, Brazil. Scavengers broke into an abandoned medical clinic and stole a disused teletherapy machine. These machines are used to treat cancer by irradiating tumors with gamma radiation typically emitted by either cobalt-60 or cesium-137. In the Goiania case, the gamma-emitting radioisotope was cesium-137 in the chemical form of cesium chloride, which is a salt-like substance. When the scavengers broke open the protective seal of the radioactive source, they saw a blue glowing powder: cesium chloride. This material did not require a “dirty bomb” to disperse it. Because of the easily dispersible salt-like nature of the substance, it spread throughout blocks of the city and contaminated about 250 people. Four people died form radiation sickness by ingesting just milligrams of the substance.
The effects could have been worse, but an extensive cleanup effort, costing tens of millions of dollars, captured about 1200 Curies of the estimated 1350 Curies of radioactivity in the disused teletherapy source. To put this Curie content in perspective, a source with 100 or more Curies of gamma-emitting radioactive material would be considered a source of security concern. The International Atomic Energy Agency has published an authoritative account of the Goiania event.
For an in-depth assessment of the radioisotopes of security concern and the commercial radioactive source industry, see the January 2003 report “Commercial Radioactive Sources: Surveying the Security Risks,” by myself, Tahseen Kazi, and Judith Perrera. In that report, we underscore that even suicidal terrorists would have to live long enough to withstand the lethal radiation of a highly radioactive substance to use it as a radiological weapon. Of course, if the terrorists or thieves have training in safely handling radioactive materials, then they would not kill themselves in the process of accessing the material and making it into a weapon.
Based on the news accounts of the recent theft in Mexico, the thieves broke open the box carrying the radioactive cobalt sources and exposed themselves to lethal radiation. They were thus unlikely to have been skilled at handling radioactive materials or even apparently knowledgeable about the cargo they had stolen.
We were lucky this time. The cobalt-60 was reportedly from an old teletherapy machine. While the Curie content has not been reported, I would estimate that it could range from a few hundred Curies to a few thousand depending on the age of the cobalt source. Cobalt-60 has a half-life of 5.27 years, so after that amount of time has elapsed, only half the original amount of radioactivity is left. After two half-lives or about 10.5 years have elapsed, one-fourth of the radioactivity remains; three half-lives, one-eighth and so on. A fresh cobalt-60 source for a teletherapy machine could contain upwards of ten thousand Curies.
While the thieves who exposed themselves will likely die within the next few days from radiation sickness, they fortunately did not expose innocent people. Because cobalt is a solid metal, it is hard to disperse, even with explosives. But if the radioactive material had been cesium-137 in chloride form, this event in Mexico could have been a ghastly replay of the 1987 event in Goiania.
In 2008, the Committee on Radiation Source Use and Replacement of the U.S. National Research Council drew attention to the dangers of cesium chloride. In the report, published by the National Academies Press, the committee ranked cesium chloride as their number one security concern and recommended that the U.S. government take steps to replace the use of this material. Technologies that don’t use radioactive cesium such as X-ray irradiators, for example, are one potentially promising pathways to reduce the use of cesium chloride. The 2008 report discusses incentives to encourage greater development and use of alternative and replacement technologies.
Last year, I wrote a report on “Ensuring the Security of Radioactive Sources: National and Global Responsibilities,” for the 2012 Nuclear Security Summit in Seoul, South Korea. Among the recommendations, I discuss the need for more effective means of tracking shipments, training of response forces, developing replacement technologies for phasing out dispersible sources, and increasing government cooperation in sharing intelligence information about threats to radioactive materials of security concern.
Unfortunately, hijacking of trucks is common in Mexico, but the police were able to track down the truck and the sources were recovered. Without better controls on highly radioactive sources, the next time something like this happens it could be a lot worse.
Global Threat Reduction Initiative Efforts to Prevent Radiological Terrorism
Saturday, August 17, 2013 at 2:35 am
Suburban location—Anywhere, United States
Three men enter a darkened building of a mid-size university closed for summer break. The university has unarmed security guards that make periodic checks of the campus building exteriors, and the local law enforcement agency is a county police department that interacts with the university on an “occasional” basis. The men enter a third floor laboratory housing a Cesium 137 irradiator. The irradiator is used by faculty and students to expose tissue samples to high levels of radiation during their research. Using simple tools, they partially dismantle the device and remove the radioactive source capsule containing 3,000 curies of Cesium 137. The three perpetrators move the material in a crudely constructed lead bucket providing light shielding and minimal protection to them, and place the material in a self-storage locker ten miles away. The theft goes unnoticed until Monday morning when it is reported to the county police. The county police are not immediately concerned or recognize the significance of the theft or the amount of radioactive material taken.
Monday, August 19, 2013 at 10:45 am
Urban location—Anywhere, United States
Over the past two days, the three perpetrators have taken the radioactive material and assembled it with explosives stolen from a construction site into a Radiological Dispersal Device (RDD), commonly called a “dirty bomb.” The device has been transported to a medium-sized city, one hundred miles from the university. All three men are suffering from radiation sickness but are able to detonate the device in the city’s business and financial district. Seven people, in addition to the three terrorists, are killed in the explosion. The resulting contamination from the dispersal of the Cesium 137 produces general panic due to health concerns, along with potentially devastating financial consequences.
The above scenario is fictional but will serve as an introduction to the discussion of what could have been done to deter or interdict the attack. Could the university and local police have had strategies to better secure the radioactive materials that were stolen? Could the local police have been notified in a timelier manner through a closer working relationship with university radiation safety professionals? Could police have searched for the material after it had been stolen, while in transit, during assembly at self-storage facility, or while en route to the final target?
The attacks of September 11, 2001, heightened the nation’s concerns regarding all forms of terrorism in the U.S., including the potential use of radioactive materials in a terrorist act. The possibility of such an attack has been of particular concern because of the widespread use and availability of radioactive materials in the United States industry, hospitals, and academic institutions. Loss or theft of such materials, in risk-significant quantities, could lead to their diversion for malicious use in a Radiological Dispersal Device. This past April’s bombing at the Boston Marathon again raised such concerns. In the wake of the Boston attack, Richard Daddario, Deputy Commissioner for counterterrorism at the New York City Police Department, testified that the psychological and economic fallout from a radiological “dirty bomb” event could demand a much longer recovery than a conventional strike. 1
An RDD is a device or mechanism that is intended to spread radioactive material from the detonation of conventional explosives or other means. An RDD detonation would likely result in few deaths (mainly from the explosion), but substantial social and economic impacts could result from public panic, decontamination costs, and denial of access to area for extended periods of time.
The economic consequences of an RDD attack could be enormous. As a point of reference, according to an estimate by Bloomberg Businessweek, it cost $333 million to shut down Boston for a day to facilitate the manhunt for Dzokhar Tsarnaev. Imagine the costs of closing a large portion of any major city for substantially longer periods. An attack at a port could also have major economic consequences. A 2007 study published in Risk Analysis estimated that the economic consequences from a shutdown of the harbors due to the contamination from a plausible dirty bomb scenario could result in losses in the tens of billions of dollars, including the decontamination costs and the indirect economic impacts due to the port shutdown.2
Global Threat Reduction Initiative
In order to prevent a radiological attack, the United States government sponsors a broad range of programs designed to prevent, detect and respond to the loss or theft of nuclear and radiological material. The Global Threat Reduction Initiative (GTRI) is a Department of Energy (DOE) program designed to reduce the amount of vulnerable nuclear and radiological material located at civilian sites worldwide and improve protection of these materials. Because the bulk of its work is pursued overseas, the program is best known for its international activities, in particular removing vulnerable nuclear material from, for example Kazakhstan, and securing high risk radioactive materials, for example in Russia. However, a lesser known and equally complex element of GTRI is its domestic component carried out in the United States. The domestic component involves the interaction and cooperation between federal government officials, scientists and policy makers with state and local police, emergency officials, and operators of private and public institutions, such as hospitals.
This article is intended to describe the domestic component of the GTRI; how it is implemented, why it is needed and how state and local officials take advantage of the program. The goal of this article is to present the joint views of a local police official together with those of a scientist and former policy maker and to explore the technical and policy issues associated with domestic threat reduction programs.
The Context
Radiological materials are located throughout the United States (see Figure 1) with the majority of high activity sources located in large urban population centers. A successfully deployed RDD using radioactive sources commonly found in public facilities such as hospitals could potentially result in radioactive contamination that could require relocation of inhabitants, prohibit the use of facilities, and have debilitating economic impacts. 3
Most radioactive sources in the U.S. are regulated by the Nuclear Regulatory Commission and state authorities. GTRI works with civilian sites to enhance security for their radiological materials; however, it does not regulate them. Participation with GTRI is voluntary on the part of sites although GTRI has an aggressive outreach program to encourage sites to participate. In addition, the Department of Homeland Security’s Domestic Nuclear Detection Office provides assistance to state and local officials in establishing an overall architecture for detecting nuclear and radioactive material that are not under regulatory control, e.g. which have already been lost or stolen. This detection assistance supports the GTRI’s efforts by providing equipment and training to establish a general baseline for state and local first responder nuclear and radiological detection capabilities, but is not focused on specific sites.
Some have expressed concern that funding for radiological threat reduction is better spent overseas, in particular in countries that do not have a strong regulatory infrastructure, as the U.S. does. Indeed, GTRI’s overseas accomplishments are much more frequently in the news. In the U.S., the protection of sources is primarily the responsibility of the owner/operator, following the requirements of the regulator. So, why should the federal government spend funds to protect radiological sources when they should already be adequately protected? Through the current and evolving program, GTRI and partner agencies and institutions have created a strong partnership for a well-rounded domestic security program. The domestic portion of GTRI has evolved to one that seeks to fill the gaps that may exist in the very complicated relationship between local, state, and federal agencies in preventing and responding to radiological security incidents. The focus of the program is shifting toward sustainability of completed security upgrades and improved response capabilities and communication networks.
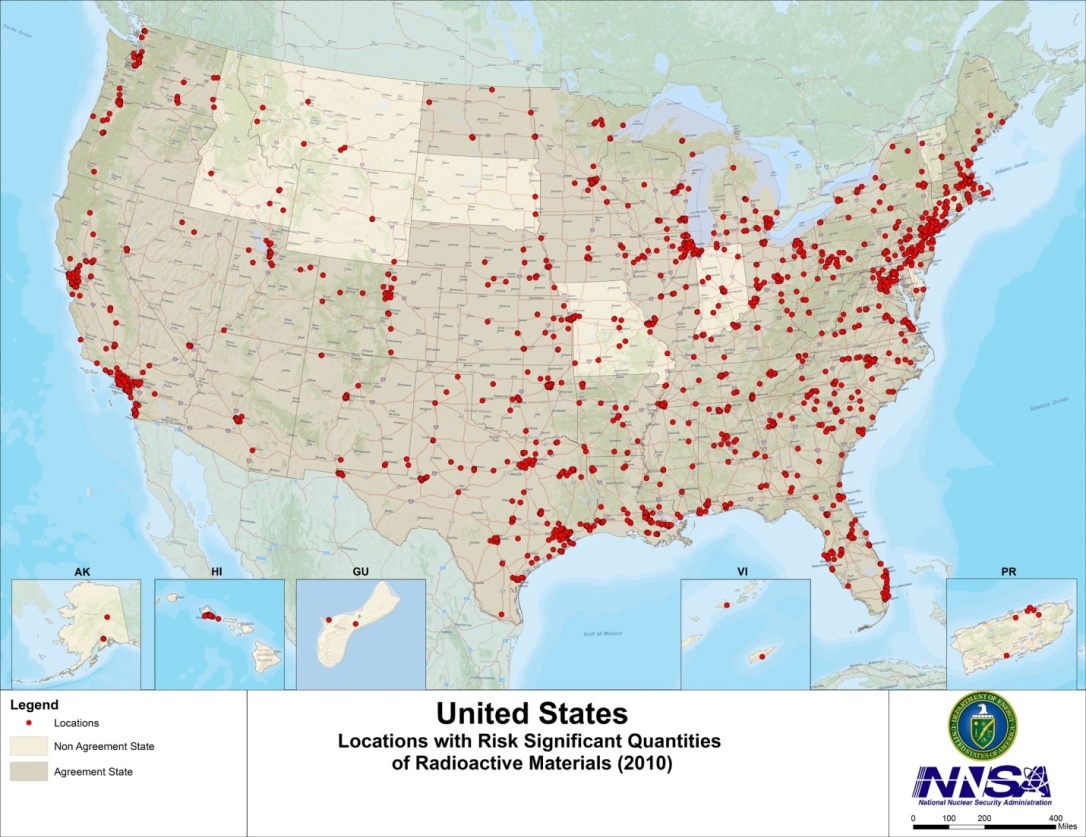
Locations in the U.S. with risk-significant quantities of radiological sources. 4
Domestic Security Enhancement Program
Since GTRI’s domestic security enhancement program began in 2008, it has worked with host sites to enhance security at more than five hundred buildings which host over four million curies of radioactive materials. GTRI physical security enhancements are applied on a voluntary basis to assist sites in the prevention and detection of any unauthorized access to radiological sources located in their facility. The physical protection principle of detection, specifically early detection, means that detection of a theft is early enough in the act that it can be stopped at the site or nearby. Ideally, early detection should allow time for response forces to prevent an adversary from acquiring the radioactive material. GTRI’s detection upgrades build upon sites’ existing security measures but may include enhancing the following physical protection system components:
- Biometric access control devices
- Door alarms
- Motion sensors
- Cameras
- Duress buttons
- Radiation sensors
- Electronic tamper indicating seals
- Remote monitoring systems
The Insider Threat
A remote monitoring system (RMS) is a critical security measure for detecting an insider threat because the insider (by definition) will have access to the device containing the radioactive material, or to the material itself depending on the type of facility. The insider will also have authorization to use some or all of the site’s access control and detection devices without sending an alarm of unauthorized access. In addition to detecting an insider, the RMS also improves the response by a site’s local law enforcement or other responding agencies by providing them with critical assessment information immediately.

For most U.S. sites, timely notification to local law enforcement is critical to prevent potential theft attempts. The RMS integrates what GTRI calls critical alarms (e.g., device tampering to gain access to the radioactive source(s), increased radiation levels indicating that the source has been removed from its shielding, communications loss between the site and monitoring station, or loss of power) with real time live video images. For increased protection, the RMS is housed in a tamper-indicating housing with battery back-up to ensure its continued operation. To address information security concerns, the RMS also encrypts the video and alarm data. The RMS can send alarm and video data simultaneously to onsite and offsite security and local law enforcement monitoring stations to prevent single-point failures in a site’s security and response planning.

Enhancing Delay Measures
Along with early detection capabilities, GTRI also provides sites with delay enhancements that impede an adversary’s progress to access nuclear and radiological materials. By increasing the delay time and adding valuable minutes in an adversary’s attack time lines, responders have more time to interrupt the adversary before they can remove and steal these materials. GTRI’s delay systems may include:
- Device tie downs
- Security cages
- Security grating
- Hardened doors/rooms
- Ballistic glass
- In-Device Delay Kits
A particularly important delay enhancement is the In-Device Delay kit for irradiators. The National Research Council, a private nonprofit institute, performed a risk and consequence analysis, which showed Cesium Chloride irradiators pose relatively higher security risks compared to other radiological materials.5 To help mitigate this risk, GTRI and DHS developed In-Device Delay (IDD) kits for Cesium irradiators that can be installed on the device. The installation of the IDD kits on selected irradiators significantly increases the time and/or difficulty involved if an intruder tries to remove a source—while not impacting the functionality of the irradiator—and consequently is an important element of security enhancements.
Response Capabilities
One of the most important elements of any security system is a timely, well-equipped, well-trained response team of appropriate size to interrupt and neutralize the adversary before they gain access to the radioactive source or immediately after they gain access. First responders from state and local law enforcement do not work with nuclear material or radiological sources on a daily basis and may lack knowledge of the risks posed by these materials. GTRI has therefore made a focused effort to provide security personnel and local law enforcement with the tools and training to help prepare them to respond to an event involving nuclear or radiological material.
In 2008 GTRI began to sponsor table top exercises for GTRI partners at select nuclear and radiological sites in the United States. These exercises are conducted at predominately private institutions, hospitals and universities and bring together key decision-makers from the actual agencies that would respond to a terrorist WMD incident. At the exercise, host level players include on-site security forces, radiation safety personnel, facility managers and public affairs personnel. At the city and state levels, players can include police, fire, hazmat, EMS, Office of Emergency Management, regulatory agencies and National Guard Civil Support Teams. At the federal level players can include the FBI, DOE/NNSA nuclear response assets the Federal Emergency Management Agency, the Nuclear Regulatory Commission, the Department of Homeland Security and the Environmental Protection Agency.
The overall exercise objectives are to promote cross-sector communication, cooperation, and team-building among public and private sector first responders and to exercise FBI lead responsibility for criminal investigation. In addition, the exercise allows players to examine newly developed tactics, techniques, and procedures resulting from GTRI voluntary security enhancements. The exercises promote attack prevention through intelligence sharing and a coordinated approach to neutralize the threat, along with site specific integrated response planning with federal, state, local, and private sector partners.
Since the first GTRI exercise in December 2008, there have been 29 Silent Thunder table top exercises at state and private universities, hospitals, research and test reactors, the U.S. Department of Agriculture and National Institutes of Health. To date, 329 FBI agents and 3760 players and observers have participated in these GTRI table-top exercises.
Additionally, at the Y-12 National Security Complex in Oak Ridge, Tennessee, GTRI offers participants a three-day alarm response training course. This training includes hands-on exercises and classroom training and teaches site personnel and local law enforcement how to protect themselves and their communities when responding to alarms indicating possible theft of radiological materials.
Removing Disused Sources Before They Can Become a Threat
The final element of GTRI’s domestic radiological security effort involves the removal of sources that are unused and may ultimately be lost or stolen due to lack of attention. In addition to security enhancements, GTRI’s Off-Site Source Recovery Program (OSRP) removes thousands of excess or disused sources in the United States annually. The initial scope of the project included a narrow group of sources (those that fell into the regulatory category of Greater than Class C (GTCC) low-level radioactive waste), but since the terrorist attacks of September 11, 2001, OSRP’s scope has expanded to include the recovery of other sources. 6 Over the years, OSRP has recovered more than 30,000 sources from more than 1,000 sites located in all 50 U.S. states, Washington D.C., and Puerto Rico.7 By removing sources from facilities that no longer had a use for them, GTRI has removed the risk of these materials to be potentially used in a RDD, thus resulting in permanent threat reduction.

From “Global” Threat Reduction to “Local” Threat Reduction
At its core, the GTRI domestic program is a partnership between federal officials, state and local officials and facility operators. One example of this is in Philadelphia, where over a dozen sites are protected in the Philadelphia Metropolitan Area by the GTRI Program, ranging from hospitals and universities, drug manufacturers and government research labs, to one of the American Red Cross’s largest blood distribution centers. Law enforcement agencies (the Philadelphia Police Department being the largest), have benefited tremendously from GTRI’s tabletop exercises, training at the Y12 National Security Complex, and personal radiation detectors provided by the GTRI Program.
The Philadelphia region had an existing Preventive Radiological Nuclear Detection (PRND) program supported by the Domestic Nuclear Detection Office (DNDO) of DHS that the NNSA was able to use as a vehicle to integrate their source security into the overall effort to prevent radiological and nuclear terrorism. This created a very effective two tiered “inside-out” and “outside-in” prevention strategy. The existing deployment of nuclear detection assets protected special events and provided a 24/7 “steady state” coverage from threats from outside the region. The regional law enforcement agencies, assisted by DNDO, were able to field a range of detection equipment on a daily basis, including aircraft, mobile and marine systems. The addition of the GTRI program allowed for the protection of radiological sources of concern within and near relevant facilities while bolstering the defense against an “insider threat” due to the closer relationships created by participation. This “inside-out” approach took Philadelphia’s protection and response effort to the next level by adding source security as a priority. The previous outwardly focus PRND program was equipment and personnel driven while the GTRI Program stresses relationship building between the partner sites and their local law enforcement agencies.
The scenario depicted at the beginning of this article would have multiple chances at prevention/interdiction in the Philadelphia model. The GTRI alarm systems and response programs would have protected the material and facilitated an immediate response and the existing detection assets could be deployed to recover any stolen material. Together, the two programs form an effective deterrent.
The University of Pennsylvania has been the largest beneficiary of the GTRI Program in the area, and has served as a model site for others in the nation for implementing the security and emergency response upgrades. All partners, facility and law enforcement, have enjoyed a much closer relationship that extends to joint training and exercises as well as facility operators providing subject matter expert support to the overall PRND effort.
Due in part to the GTRI program, in October 2013, all the protected facilities alarm notifications are received in the regional “Fusion Center”, the Delaware Valley Intelligence Center (DVIC), creating another layer of defense and allowing for a regional protection and response capability.
Conclusion
As mentioned at the outset of this paper, some in the policy community believe U.S. radiological protection dollars are better spent overseas, where regulatory controls are not as effective as those in the United States. It is true that despite years of effort, many other countries do not have strong regulatory infrastructures for managing access to radiological and nuclear material and funding overseas is well spent. However, as illustrated above, this view does not fully take into account the multifaceted needs of radiological security, which requires the integration of the facility operators, state, local and federal capabilities. Moreover, while sources overseas are generally less well regulated and protected than U.S. sources, radiological sources in the U.S. should receive special attention because they pose the greatest risk: diversion closest to a target of the attack minimizes the likelihood of detection through the global detection capabilities overseas and at U.S. borders. In this view, it makes little sense for the federal government to help provide for a security measure overseas, but not domestically, where the risk may be higher.
A recent Government Accountability Office (GAO) report is instructive in regard to the limitations of regulatory controls. GAO was asked by Congress to determine the extent to which NRC’s regulations ensure the security of radiological sources at U.S. medical facilities and the status of NNSA’s efforts to improve the security of sources at these facilities. GAO reviewed relevant laws, regulations, and guidance; interviewed federal agency and state officials; and visited 26 hospitals and medical facilities in Washington, D.C. and 7 states. The review concluded that existing regulatory requirements do not consistently ensure the security of high-risk radiological sources at the 26 selected hospitals and medical facilities visited. According to the review, one reason for this is that the requirements are broadly written and do not prescribe specific measures that hospitals and medical facilities must take to secure medical equipment containing sealed sources, such as the use of cameras or alarms. Rather, the requirements provide a general framework for what constitutes adequate security practices, which is implemented in various ways at different hospitals. Some of the medical equipment in the facilities visited was more vulnerable to potential tampering or theft than that of other facilities because some hospitals developed better security controls than others. 8
Protecting America from a radiological attack requires a strong alliance between facility operators, state, federal and local officials. In the U.S., the NRC sets the regulatory framework that includes security requirements, licensing, inspection, and enforcement. But the regulatory framework is insufficient for all threats; rather it provides a common baseline level of security. GTRI works with sites to build upon these security standards set by NRC and state regulations. GTRI’s voluntary security enhancements provide sites with security best practices which further enhance security above regulatory requirements. Because the GTRI upgrades are voluntary and may have cost implications for the facility operators as well as state and local authorities, it is essential that all partners are aware of the threats and risks involved in working with certain radioactive material as well as programs to mitigate these risks.
Warren Stern is Senior Advisor in Brookhaven National Laboratory’s Nonproliferation and National Security Department. In 2010, he was appointed by President Obama to lead the Domestic Nuclear Detection Office at DHS and before that, Head of the IAEA’s Incident and Emergency Centre. He has also held a number of leadership positions at the U.S .Department of State, Arms Control and Disarmament Agency and CIA.
Lieutenant Edward Baldini is a twenty four year veteran of the Philadelphia Police Department and has been assigned to the Counter Terrorism Operations Unit since its inception in spring 2002. He has assisted in development of Counter Terrorism Training at the local, state and national level. He has been very active with Preventive Radiological/Nuclear Detection (PRND) mission and has assisted the Domestic Nuclear Detection Office (DNDO) and the National Nuclear Security Administration (NNSA) in several initiatives. He holds a Bachelor’s Degree from Philadelphia University and a Master’s Degree from the Naval Postgraduate School in Monterey, California. He is also a graduate of Northwestern University Center for Public Safety’s School of Police Staff and Command.
Report Examines MANPADS Threat and International Efforts to Address It
On November 28, 2002, terrorists fired two Soviet-designed SA-7 man-portable air defense systems (MANPADS) at an Israeli plane destined for Tel Aviv as it departed from Moi International Airport in Mombasa, Kenya. The missiles missed their target but the incident was a wake-up call for governments around the world. Shortly after the attack, the United States created an inter-agency task force to counter the threat posed by MANPADS, with other countries following suit. These countries launched several initiatives aimed at securing and destroying surplus, obsolete and poorly secured stockpiles of missiles; strengthening controls on international transfers of MANPADS; and improving information sharing on the international trade in these weapons. But are these efforts enough?
In the report, “The MANPADS Threat and International Efforts To Address It”, Matt Schroeder, Director of the Arms Sales Monitoring Project, assesses the terrorist threat from MANPADS, evaluates efforts by the international community to curb this threat, and proposes additional measures that governments can take to further reduce the illicit proliferation and use of MANPADS.
The Federation of American Scientists would like to thank the following individuals and institutions for their invaluable contributions to this report: James Bevan, Jeremy Binnie, Peter Courtney-Green, Gene Crofts, Alan Flint, Andy Gleeson, Jose Manuel Heredia Gonzalez, Paul Holtom, J. Christian Kessler, Stephanie Koorey, Jonah Leff, Cheryl Levy, Maxim Pyadushkin, Steve Priestley, Saferworld, Small Arms Survey and officials from the Organization of American States, the Organization for Security and Co-operation in Europe, the United Nations Regional Centre for Peace, Disarmament and Development in Latin America and the Caribbean and the Wassenaar Arrangement , along with officials from numerous governments. Without their talent and support, this study would not have been possible.
Radiological Ray Gun: More Buck Rogers Fantasy than Risk to Real People
The June 18th arrest of two men for allegedly plotting to build a bizarre yet potentially deadly radiological device once again highlights the potential nexus of non-state actors with so-called weapons of mass destruction (WMD). However, much like this year’s troika of ricin-laced letters addressed to government facilities (including one to the CIA) and public officials (all three incidents targeted President Obama at his White House address), this most recent plot reveals the historical rarity and non-lethality of non-state actors and their behaviors with radiological weapons and agents. While the potential for catastrophe posed by terrorist use of chemical, biological, radiological, and nuclear (CBRN) weapons deserves ongoing and serious attention, recent events remind us how public apprehension is sometimes founded more in fear than reality; indeed, reactions based on fear are capable of far more disruption than the physical reality of the event itself. The role of science-based organizations such as the Federation of American Scientists is to educate the public about the real risks. [box border=”full”]The methodologies and data sets used in this article, augmented by several others of each, will be discussed in a two day professional education summer course, “Terrorism Analysis: Quantitative and Qualitative Research Methodologies and Tools” held at George Mason University in Fairfax, VA on July 25-26, 2013. This non-credit course introduces participants to state-of-the art analytical techniques, research methods, and cutting-edge databases used by the industry for the study of terrorism. Course participants gain a detailed understanding of single and multi-methodological techniques, learning how to develop analytical tools applicable to the needs of those responsible for preventing, preparing, responding to, or predicting terrorism. Highlights include how to use these research techniques to identify previous and emerging trends in terrorist activities and to cogently assess the potential role of WMD in terrorism. Register now for the “early bird” discount – 25 percent less than the listed fee. For more information and to register, please visit the course page.[/box]
Of the CBRN threats, the nuclear threat is undoubtedly truly catastrophic because a nuclear weapon can cause massive destruction, but obtaining a nuclear weapon or the fissile material to make such a weapon is very hard to do. In comparison, radiological sources are far more common, but most of them would cause little or no harm to human health if dispersed by a radiological weapon because there is not enough radioactive material contained in the vast majority of each of these sources. And even those radiological sources containing highly radioactive materials would pose great difficulties for terrorists to use because they would hazard exposing themselves to lethal ionizing radiation. These latter issues, and others outlined below, are very relevant to the recent radiological plot.
According to Tuesday’s radiological- related FBI affidavit, Glenford Scott Crawford, an industrial mechanic who reportedly self-identified as a member of the Ku Klux Klan, plotted to build “a mobile, remotely operated, radiation emitting device capable of killing human targets silently and from a distance with lethal doses of radiation.” Crawford, along with Eric J. Freight, an electronics specialist, allegedly succeeded in constructing a “remote initiation device,” but according to the FBI’s affidavit had not yet “weaponized” the device before their arrest. Monitored by the FBI since April 2012, the duo never obtained a radiological source for their device.
While the affidavit lacks a definitive answer on whether or not Crawford and Freight sought to craft a device that would emit x-rays or were trying to obtain a radioactive source to emit radiation, it appears likely that the former is the case. Significant differences exist between an x-ray emitting device and a radioactive source that emits gamma radiation. The first distinction is that an x-ray device needs electrical power to work but a radioactive source is always “on” and emitting radiation due to the natural process of radioactive decay. The other salient distinction is that if Crawford and Freight had sufficient electrical power they could—in principle—have a device capable of emitting potent radiation from a relatively far off distance— such as several meters. That is, the output of the x-ray device would depend on the electrical power available. In contrast, a radioactive source would not be able to boost its potency with the use of electrical power because the potency depends on the properties of the radioisotope and the natural process of decay.
Active in two small towns near Albany, New York, over the past year, Crawford and Freight unwittingly dealt with at least one FBI planted “confidential human source” who posed as a potential financer of the project and buyer of the finished device. Tuesday’s arrests came as the suspects, “planned to conduct a test-run of the triggering system.”
Contrary to public perceptions of radiological weapons, or “dirty bombs,” as weapons of mass destruction, experts correctly note that radiological attacks could not produce mass destruction or mass casualties. This is because when dispersed the radioactive material would be spread out over a wide area and thus would be far less potent than material concentrated in the original source. Moreover, trying to use the original source as a lethal means of exposing large numbers of people from a distance would be hard to do because the potency of the ionizing radiation would decrease the farther the source is from the targeted population. Specifically, it would decrease as one divided by the distance squared. For example, an unshielded source that is lethal at one-meter distance would have a potency of one one-hundredth when the source is ten meters away and would not likely pose a lethal threat.
Thus, the reality is that radiological devices are “weapons of mass disruption” – likely to directly generate few, if any, immediate casualties via ionizing radiation, yet capable of precipitating mass panic and large-scale economic disruption.
Similarly, belying public apprehension of radiological terrorism, there is the extreme rarity of such events; indeed, terrorist use of harmful radioisotopes, according to open-source data, numbers no more than three incidents—none of which generated casualties. If other non-state actors are included, those not considered terrorists, but include, for example, lone actors seeking revenge, recorded radiological incidents are more numerous, but still strikingly rare. A finding from a 2009 study—conducted by a University of Maryland (UMD) research team that included this author, combined with research into radiological events occurring subsequent to the studies completion—reveals only 19 recorded radiological incidents by non-state actors. (Maintaining harmony with the UMD study, the criteria for inclusion excluded hoaxes and “clear cases of smuggling or transfer activity with no apparent links to end-users.”)
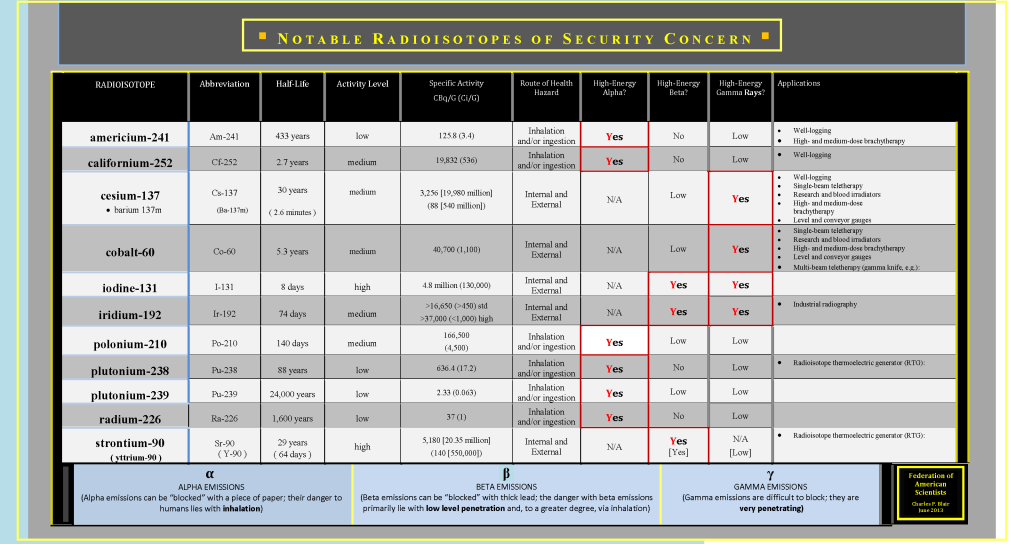
Taking a brief pause, here are some basic nuclear physics useful when putting this event in the proper context. The entire universe consists of less than 120 elements; 92 are naturally occurring. Each element contains a unique number of protons. While their number of protons remains the same, some elements possess different numbers of neutrons. These are called isotopes. With neutrons in greater quantity than those found in lead and bismuth, are isotopes prone to natural decay. Such unstable isotopes are referred to as radioisotopes, which undergo decay in one of three ways: alpha, beta, or gamma decay. Depending on the rate of decay and the other factors, less than a dozen radioisotopes pose serious health risks.
Easily blocked from entering the human body, alpha emitting radioisotopes pose a health risk via inhalation or ingestion. Beta particles possess greater penetrating power, yet these can be blocked by thin layers of lead or other dense materials. It is gamma particles that pose the greatest health risk via exposure. The device Crawford and Freight sought—“a radiation emitting device that could be placed in the back of a van to covertly emit ionizing radiation strong enough to bring about radiation sickness or death against Crawford’s enemies,” required a radiological source emitting high-energy gamma rays.
States long ago foresaw radiological weapons as ineffective for battlefield use—easily obviated by many conventional and unconventional weapons. As early as 1943, notes Robert S. Norris in his 2002 book Racing for the Bomb, the “impending invasion of Europe precipitated fears and concerns about possible German use of radioactive materials on Allied forces.” U.S. scientists investigated the threat. They concluded, Norris writes, “that there would be many difficulties in devising munitions that would effectively deliver radioactive materials…” Still, Norris explained to this author on June 20, 2013, “Even in the early 1940s the fear of radioactivity was enough to move Allied planners to equip some D-Day soldiers with dosimeters.” Thankfully, Nazi Germany did not develop radiological weaponry and although serious consideration was given to their potential development (including the United States), no open-source data exists of any state having done so with the exception of one incident. The November 2006 death of Alexander Litvinenko, occurring three weeks after the former Russian Federal Security Service (FSB) officer drank tea containing polonium-210 (Po-210) in a London restaurant, was likely the work of Russian state operatives.
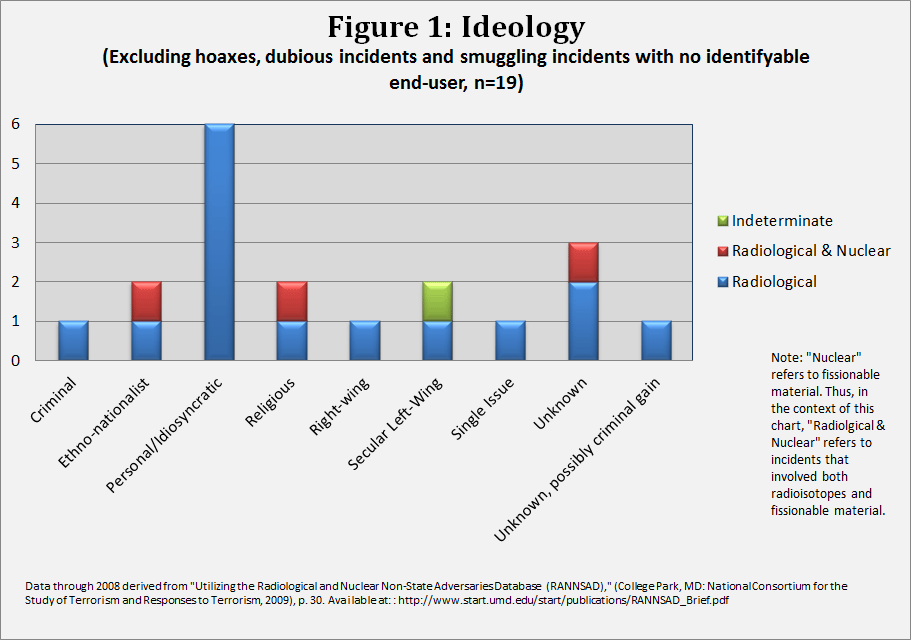
Non-state actors, in contrast, sometimes perceive harmful radioisotopes as an effective means towards achieving their goals. With regard to four possible perpetrator types, of the 19 recorded incidents, lone-actors account for ten. Four incidents are attributed to formal organizations and two to unaffiliated cells. Unknown perpetrator types account for three incidents.
Figure 1 demonstrates the variety of general ideologies adhered to by the perpetrators. Note that the most active of all individuals and groups with “Religious” and “Personal / Idiosyncratic” ideologies were Sunni Islamists and U.S. right-wing extremist respectively.
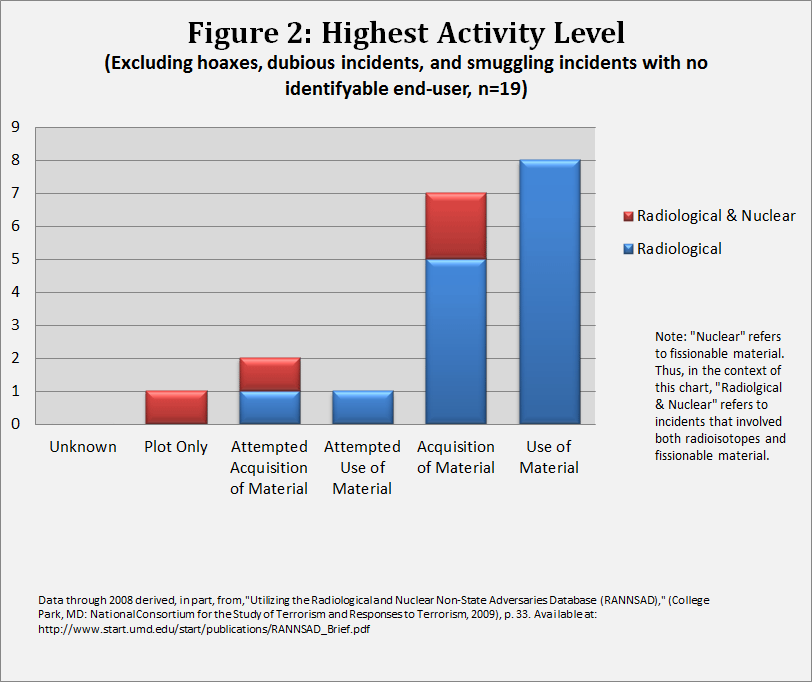
Figure 2 reveals how far along groups and individuals got on the spectrum of radiological activity. As noted in the UMD study, perpetrators successful in acquisition of radioisotopes more likely than not used the materials, although “success” came in only five of the incidents (assuming operational objectives that included generating casualties). The data set used to compile the previously mentioned UMD study—the Radiological and Nuclear Non-State Adversaries Database (RANNSAD)—when enlarged by this author’s subsequent research, reveals the following: four incidents that each resulted in one injury. A fifth incident, involving the use of iridium-192 (Ir-192) by a “nuclear medical researcher” in Guangzhou, China, sickened 75 individuals. When correctly excluding the death of Alexander Litvinenko, noted earlier as likely due to state actions, radiological incidents writ large have yet to yield a single fatality.
Some radioisotopes pose an extreme risk. One case of inadvertent dispersal—the 1988 Goiânia, Brazil, incident—killed four and negatively affected thousands. For well over a decade experts have warned of the likelihood of terrorist use of radioisotopes (almost half the expert respondents in a seminal 2005 survey “judged the risk of such an attack [occurring in the next ten years – i.e. by 2015] as 50 percent or greater”). Explaining non-use is akin to proving a negative—impossible. The latest incident, as farcical as elements of it may seem, should serve as a reminder that, despite a paucity of incidents and no fatalities, non-state actors continue to plot and actualize the nefarious use of radioisotopes.
Regulating Japanese Nuclear Power in the Wake of the Fukushima Daiichi Accident
The 2011 accident at the Fukushima Daiichi nuclear power plant was preventable. The Great East Japan earthquake and the tsunami that followed it were unprecedented events in recent history, but they were not altogether unforeseeable. Stronger regulation across the nuclear power industry could have prevented many of the worst outcomes at Fukushima Daiichi and will be needed to prevent future accidents.
In an FAS issue brief, Dr. Charles Ferguson and Mr. Mark Jansson review some of the major problems leading up to the accident and provides an overview of proposed regulatory reforms, including an overhaul of the nuclear regulatory bureaucracy and specific safety requirements which are being considered for implementation in all nuclear power plants.
Confronting Emerging Security Challenges: A Call for Ontological Coherence
By Michael Edward Walsh
The concept of emerging security challenges is not new. Mankind has always had to adapt to novel scientific and technological innovations that have changed the nature of war and violence within society. The sudden focus on emerging security challenges is then not driven by their mere emergence but rather by the context in which they are emerging. For this reason, it is critical that security experts not delink the external world from the conversation.
Towards Enhanced Safeguards for Iran’s Nuclear Program
Iran’s controversial nuclear program has been front and center on the international stage for more than eight years. Despite negotiations, sanctions, and political tug-of-war, the United States and its allies have yet to tame Iran’s atomic phoenix. At the center of this nuclear standoff is Iran’s controversial uranium enrichment program and efforts to obtain full nuclear fuel-cycle capabilities. To alleviate concerns about the intended nature of these activities, the United Nations Security Council (UNSC) has demanded -through six resolutions – that Iran suspend enrichment activities as well as construction of a heavy-water research reactor. Yet, Iran has opted to pay no heed to these resolutions and despite numerous proposals from different sides, the stalemate persists.
Dr. Charles D. Ferguson and Dr. Ali Vaez, authored a FAS report (PDF) analyzing the outstanding issues regarding Iran’s nuclear program, and provide recommendations to the major stakeholders in this debate including Iran, the United States, Russia and the International Atomic Energy Agency (IAEA).
Additionally, the report proposes a multipronged approach to resolving this deadlock, including enhanced safeguards and positive-sum diplomacy with incentives for Iran and other aspiring nuclear states.
Anatomizing Non-State Threats to Pakistan’s Nuclear Infrastructure
The discovery and subsequent killing of Osama bin Laden in Abbottabad, Pakistan raises troubling questions. The success of the U.S.’s airborne raid on bin Laden’s compound-undetected by Pakistan’s radar- lends credence to the belief that terrorists might be capable of successfully seizing Pakistan’s nuclear weapons.
Mr. Charles P. Blair has authored a new FAS report (PDF) that addresses the security gap and identifies specific terrorists within Pakistan who are motivated and potentially capable of taking Pakistani nuclear assets. Blair explains in the report details why, amid Pakistan’s burgeoning civil war, the Pakistani Neo-Taliban is the most worrisome terrorist group motivated and possibly capable of acquiring nuclear weapons.
Norway’s Anders Brevik: Weapons of Mass Destruction and the Politics of Cultural Despair
ABOUT THIS REPORT (click to show)
At some point, most security analysts face the dilemma of balancing expediency with analytical thoroughness. Such is the case with Norway’s Anders Breivik. As his victims await burial, Breivik’s treatise—the 1500 page, 2083:
A European Declaration of Independence (click here for PDF link)—became available only a few days ago. While some researchers, mindful of the value of analytical completeness, patiently plod through this massive manifesto, analysts at the Federation of American Scientists (FAS) conclude that the nature of Breivik’s attacks, compounded with the extraordinary content of his treatise, raise questions of such immediate concern that the formulation and release of initial analyses are prudent. We present such an effort here as both a highly formatted blog post and as a preliminary report. The former allows for a quick delivery of our preliminary investigation amid a platform for open discussion of a threat that remains, we believe, largely inchoate. The latter conforms to our professional dedication to robust research and application of various relevant analytical methodologies.
While Breivik’s unprecedented attacks alone warrant profound study, his treatise seeks to portend far greater acts of terror and destruction than those visited upon Norway on July 22nd. However, to date, no substantive effort addresses the document’s detailed exposition of the fabrication, delivery and general merits of chemical, biological, radiological and nuclear weapons (CBRN). The paucity of concern and immediacy revolving around Breivik’s assertions of forthcoming CBRN attacks likely result from two interrelated issues. First, Breivik is incarcerated and will likely remain so for the rest of his life; Breivik himself is no longer a threat. Second, some question his technical acumen with regard to CBRN; even if he were free, according to one putative CBRN expert, “Breivik’s WMD idea is not realistic.”[1] We
largely agree with such conclusions. However, any proper risk assessment must conduct a so-called “assumptions check.” Such an exercise has two primary elements: 1) explicitly identifying conclusions that rely, in part or in whole, on assumptions and 2) identifying and evaluating the consequences should such assumptions prove false.[2] Application of an assumptions check to the Breivik case, we believe, precipitates the need for serious and immediate analyses of the treatise’s content for two primary reasons.
First, Breivik has made claims, through his writing as well as to Oslo District Court Judge Kim Heger, that he is in league with extremist cells and that some of these co-conspirators “are already in the process of attempting to acquire chemical, biological, radiological, or nuclear materials.”[3] While it is likely that Breivik acted alone, we are not comfortable assuming that this is the case. Moreover, given the operational sophistication of his attacks, and, among other salient components in the case writ large, the overall operational security that he maintained for years, it is axiomatic that Breivik’s threats should be considered in great detail. Indeed, as renowned terrorism expert Gary Ackerman has warned, “History is replete with cautionary tales warning against basing threat assessments on static analyses of an opponent’s motivations and capabilities.”[4] In short, it is possible that subsequent attacks—some perhaps even utilizing CBRN—may be forthcoming, and it is therefore prudent for the intelligence communities to carefully consider Breivik’s writings.
Second, our initial analyses of Brevik’s comprehension of the relevant issues surrounding the fabrication and employment of CBRN concludes that he was motivated and capable of credibly pursuing low-end CBRN attacks—specifically those likely to result in mass effect as opposed to mass destruction . As our report details, this is specifically the case with some biological and radiological agents. Should Breivik be part of a cell of violent extremists, it is possible that his confederates share an equal, if not greater, understanding of the technologies underlying certain CBRN. Moreover, they may have access to the necessary agents and technologies necessary to actualize Breivik’s more ambitious stratagems for the employment of CBRN.
We are presently inclined to conclude that Breivik acted alone. Consequently, his warnings of forthcoming CBRN events are likely invalid. However, given the nature of his attacks and the content of his treatise we urge the security community to seriously consider the possibility that cells of violent extremists are linked to Breivik; the pursuit of a CBRN capability—as well as the possibility of radiological and/or biological use—are a possibility.
Blog posts and reports from the FAS Terrorism Analysis Project are produced to increase the understanding of policymakers, the public, and the press about threats to national and international security from terrorist
groups and other violent non-state actors. The reports are written by individual authors—who may be FAS staff or acknowledged experts from outside
the institution. These reports do not represent an FAS institutional position on policy issues. All statements of fact and expressions of opinion contained in this and other FAS-published reports are the sole responsibility of the author or authors.
See “Alleged Norway Shooter Considered WMD Attack, Jihadi Alliance,” ABC News,
July 24, 2011. Available at: http://abcnews.go.com/Blotter/anders-breivik-alleged-norway-shooter-considered-wmd-attack/story?id=14148151
Whether we are conscious of it or not, most of us frequently conduct an
assumptions check. For example, imagine that as you are about to lie down in
bed for a night of sleep you suddenly realize that you cannot be sure if you
locked your car doors. You might temporarily assume you did; however,
you mind quickly assesses the consequences of a faulty assumption.
Whether or not you get up, get dressed, and trudge out to your car is largely
the result of the risk assessment you make should the car be unlocked.
Andrew Berwick [pseudonym for Anders Behring Breivik], 2083 A European
Declaration of Independence, July 2011, 1022.
United States Senate Committee on Homeland Security
and Governmental Affairs Hearing on “Nuclear Terrorism: Assessing the Threat to
the Homeland.” Testimony of Gary A. Ackerman, April 2, 2008, 3.
Available at: http://hsgac.senate.gov/public/_files/040208Ackerman3.pdf
Norway’s Anders Brevik: Weapons of Mass Destruction and the Politics of Cultural Despair
CHARLES P. BLAIR, KELSEY GREGG, AND JONATHAN GARBOSE[ref]The authors thank Rebecca A. Remy for her valuable research assistance.[/ref]
July 27, 2011
Ten years after the events of 9/11, it is often forgotten that high fatality terrorist incidents remain a rarity. Indeed, prior to 9/11 the single deadliest terrorist attack was the 1978 Iranian theatre firebombing perpetrated by Mujahedin-e Khalq (MEK: People’s Majahedin of Iran) with 470 fatalities. Since 1970, only 118 incidents of terrorism have killed more than 100 people—0.12 percent of the 98,000 terrorist events encompassing that four decade span. As the death toll of the July 22 attacks in Norway approaches 100, it is useful to appreciate this fact. In addition to recognizing their uncommonly deadly outcomes, two other features related to the attack are salient. First, significant elements of Anders Breivik’s treatise—the 1500 page 2083: A European Declaration of Independence [ref]Andrew Berwick, pseudonym for Anders Behring Breivik, 2083 A European Declaration of Independence, July 2011, hereafter referred to as The Declaration.[/ref] (click here for PDF link)—address the acquisition, weaponization, and use of chemical, biological, radiological, and nuclear (CBRN) agents or devices against Breivik’s perceived enemies. Second, his ideological platform, said by Breivik to represent his role as “Justiciar Knight Commander for Knights Templar Europe and one of several leaders of the National and pan-European Patriotic Resistance Movement,” is largely informed by European racist ideology that first emerged in the nineteenth century and continues to this day. This report principally evaluates the CBRN elements of Breivik’s treatise. A subsequent report (schedule for release in late 2011) will orient Breivik’s ideological underpinnings within the broader historical milieu of European racist thinking. First, however, it is useful to place Breivik’s attack in perspective.
The Twenty Percent Solution: Breaking the Iranian Stalemate
President Obama’s deadline to address concerns about Tehran’s nuclear program passed at the end of 2009, so the White House is moving to harsher sanctions. But the U.S. is having trouble rallying the needed international support because Iranian intentions remain ambiguous.