
Building Regional Cyber Coalitions: Reimagining CISA’s JCDC to Empower Mission-Focused Cyber Professionals Across the Nation
State, local, tribal, and territorial governments along with Critical Infrastructure Owners (SLTT/CIs) face escalating cyber threats but struggle with limited cybersecurity staff and complex technology management. Relying heavily on private-sector support, they are hindered by the private sector’s lack of deep understanding of SLTT/CI operational environments. This gap leaves SLTT/CIs vulnerable and underprepared for emerging threats all while these practitioners on the private sector side end up underleveraged.
To address this, CISA should expand the Joint Cyber Defense Collaborative (JCDC) to allow broader participation by practitioners in the private sector who serve public sector clients, regardless of the size or current affiliation of their company, provided they can pass a background check, verify their employment, and demonstrate their role in supporting SLTT governments or critical infrastructure sectors.
Challenge and Opportunity
State, local, tribal, and territorial (SLTT) governments face a significant increase in cyber threats, with incidents like remote access trojans and complex malware attacks rising sharply in 2023. These trends indicate not only a rise in the number of attacks but also an increase in their sophistication, requiring SLTTs to contend with a diverse and evolving array of cyber threats.The 2022 Nationwide Cybersecurity Review (NCSR) found that most SLTTs have not yet achieved the cybersecurity maturity needed to effectively defend against these sophisticated attacks, largely due to limited resources and personnel shortages. Smaller municipalities, especially in rural areas, are particularly impacted, with many unable to implement or maintain the range of tools required for comprehensive security. As a result, SLTTs remain vulnerable, and critical public infrastructure risks being compromised. This urgent situation presents an opportunity for CISA to strengthen regional cybersecurity efforts through enhanced public-private collaboration, empowering SLTTs to build resilience and raise baseline cybersecurity standards.
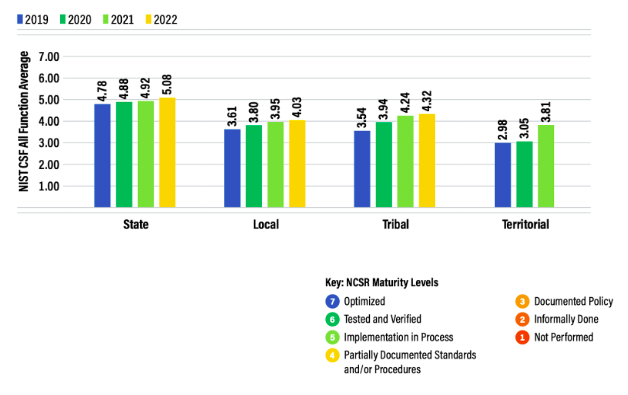
Average cyber maturity scores for the State, Local, Tribal, and Territorial peer groups are at the minimum required level or below. Source: Center for Internet Security
Furthermore, effective cybersecurity requires managing a complex array of tools and technologies. Many SLTT organizations, particularly those in critical infrastructure sectors, need to deploy and manage dozens of cybersecurity tools, including asset management systems, firewalls, intrusion detection systems, endpoint protection platforms, and data encryption tools, to safeguard their operations.
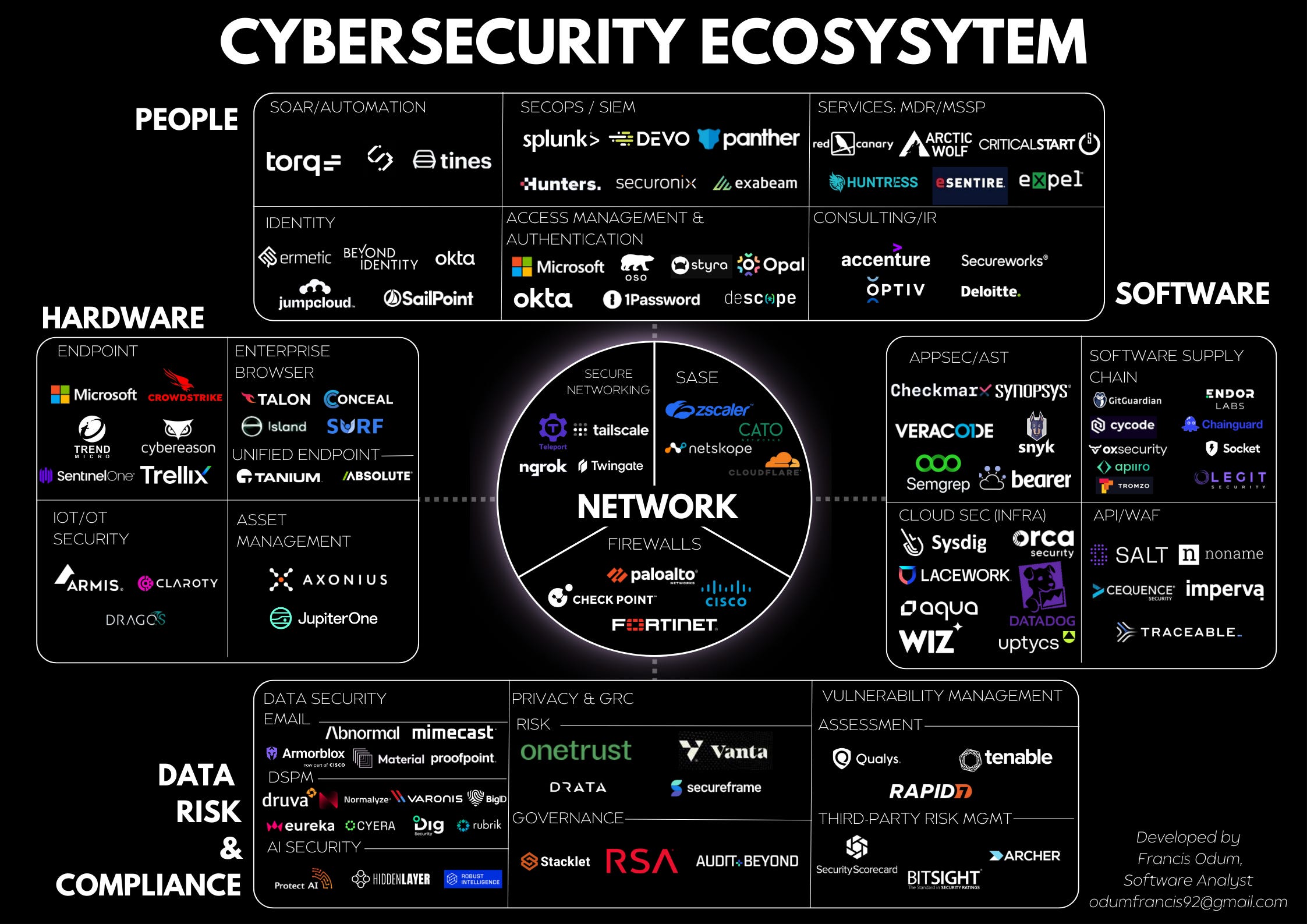
An example of the immense array of different combinations of cybersecurity tools that could comprise a full suite necessary to implement baseline cybersecurity controls. Source: The Software Analyst Newsletter
The ability of SLTTs to implement these tools is severely hampered by two critical issues: insufficient funding and a shortage of skilled cybersecurity professionals to operate such a large volume of tools that require tuning and configuration. Budget constraints mean that many SLTT organizations are forced to make difficult decisions about which tools to prioritize, and the shortage of qualified cybersecurity professionals further limits their ability to operate them. The Deloitte-NASCIO Cybersecurity Study highlights how state Chief Information Security Officers (CISOs) are increasingly turning to the private sector to fill gaps in their workforce, procuring staff-augmentation resources to support security control deployment, management of Security Operations Centers (SOCs), and incident response services.
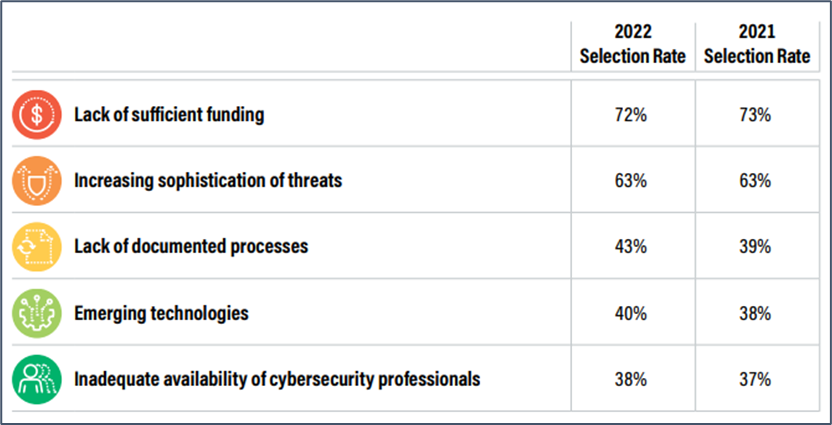
The Top 5 Security Concerns for Nationwide Cybersecurity Review Respondents include lack of sufficient funding and inadequate availability of cybersecurity professionals. Source: Centers for Internet Security.
What Strong Regionalized Communities Would Achieve
This reliance on private-sector expertise presents a unique opportunity for federal policymakers to foster stronger public-private partnerships. However, currently, JCDC membership entry requirements are vague and appear to favor more established companies, limiting participation from many professionals who are actively engaged in this mission.
The JCDC is led by CISA’s Stakeholder Engagement Division (SED) which also serves as the agency’s hub for the shared stakeholder information that unifies CISA’s approach to whole-of-nation operational collaboration. One of the Joint Cyber Defense Collaborative’s (JCDC) main goals is to “organize and support efforts that strengthen the foundational cybersecurity posture of critical infrastructure entities,” ensuring they are better equipped to defend against increasingly sophisticated threats.
Given the escalating cybersecurity challenges, there is a significant opportunity for CISA to enhance localized collaboration between the public and private sectors in the form of improving the quality of service delivery that personnel at managed service providers and software companies can provide. This helps SLTTs/CIs close the workforce gap, allows vendors to create new services focused on SLTT/CIs consultative needs, and boosts a talent market that incentivizes companies to hire more technologists fluent in the “business” needs of SLTTs/CIs.
Incentivizing the Private Sector to Participate
With intense competition for market share in cybersecurity, vendors will need to provide good service and successful outcomes in order to retain and grow their portfolio of business. They will have to compete on their ability to deliver better, more tailored service to SLTTs/CIs and pursue talent that is more fluent in government operations, which incentivizes candidates to build great reputations amongst SLTT/CI customers.
Plan of Action
Recommendation 1. Community Platform
To accelerate the progress of CISA’s mission to improve the cyber baseline for SLTT/CIs, the Joint Cyber Defense Collaborative (JCDC) should expand into a regional framework aligned with CISA’s 10 regional offices to support increasing participation. The new, regionalized JCDC should facilitate membership for all practitioners that support the cyber defense of SLTT/CIs, regardless of whether they are employed by a private or public sector entity. With a more complete community, CISA will be able to direct focused, custom implementation strategies that require deep public-private collaboration.
Participants from relevant sectors should be able to join the regional JCDC after passing background checks, employment verification, and, where necessary, verification that the employer is involved in security control implementation for at least one eligible regional client. This approach allows the program to scale rapidly and ensures fairness across organizations of all sizes. Private sector representatives, such as solutions engineers and technical account managers, will be granted conditional membership to the JCDC, with need-to-know access to its online resources. The program will emphasize the development of collaborative security control implementation strategies centered around the client, where CISA coordinates the implementation functions between public and private sector staff, as well as between cybersecurity vendors and MSPs that serve each SLTT/CI entity.
Recommendation 2. Online Training Platform
Currently, CISA provides a multitude of training offerings both online and in-person, most of which are only accessible by government employees. Expanding CISA’s training offerings to include programs that teach practitioners at MSPs and Software Companies how to become fluent in the operation of government is essential for raising the cybersecurity baseline across various National Cybersecurity Review (NCSR) areas with which SLTTs currently struggle. The training platform should be a flexible, learn-at-your-own-pace virtual learning platform, and CISA is encouraged to develop on existing platforms with existing user bases, such as Salesforce’s Trailhead. Modules should enable students around specific challenges tailored to the SLTT/CI operating environment, such as applying patches to workstations that belong to a Police or Fire Department, where the availability of critical systems is essential, and downtime could mean lives.
The platform should offer a gamified learning experience, where participants can earn badges and certificates as they progress through different learning paths. These badges and certificates will serve as a way for companies and SLTT/CIs to understand which individuals are investing the most time learning and delivering the best service. Each badge will correspond to specific skills or competencies, allowing participants to build a portfolio of recognized achievements. This approach has already proven effective, as seen in the use of Salesforce’s Trailhead by other organizations like the Center for Internet Security (CIS), which offers an introductory course on CIS Controls v8 through the platform.
The benefits of this training platform are multifaceted. First, it provides a structured and scalable way to upskill a large number of cybersecurity professionals across the country with a focus on tailored implementation of cybersecurity controls for SLTT/CIs. Second, the badge system incentivizes ongoing participation, ensuring that cybersecurity professionals can continue to maintain their reputation if they choose to move jobs between companies or between the public and private sectors. Third, the platform fosters a sense of community and collaboration around the client, allowing CISA to understand the specific individuals supporting each SLTT/CI organization, in the case that it needs to mobilize a team with both security knowledge and government operations knowledge around an incident response scenario.
Recommendation 3. A “Smart Rolodex”
A Customer Relationship Management (CRM) system should be integrated within CISA’s Office of Stakeholder Engagement to manage the community of cyber defenders more effectively and streamline incident response efforts. The CRM will maintain a singular database of regionalized JCDC members, their current company, their expertise, and their roles within critical infrastructure sectors. This system will act as a “smart Rolodex,” enabling CISA to quickly identify and coordinate with the most suitable experts during incidents, ensuring a swift and effective response. The recent recommendations by a CISA panel underscore the importance of this approach, emphasizing that a well-organized and accessible database is crucial for deploying the right resources in real-time and enhancing the overall effectiveness of the JCDC.
Recommendation 4. Establishment of Merit-Based Recognition Programs
Finally, to foster a sense of mission and camaraderie among JCDC participants, recognition programs should be introduced to increase morale and highlight above-and-beyond contributions to national cybersecurity efforts. Digital badges, emblematic patches, “CISA Swag” or challenge coins will be awarded as symbols of achievement within the JCDC, boosting morale and practitioner commitment to the greater mission. These programs will also enhance the appeal of cybersecurity careers, elevating those involved with the JCDC, and encouraging increased participation and retention within the JCDC initiative.
Cost Analysis
Estimated Costs and Justification
The proposed regional JCDC program requires procuring ~100,000 licenses for a digital communication platform (Based on Slack) across all of its regions and 500 licenses for a popular Customer Relationship Management (CRM) platform(Based on Salesforce) for its Office of Stakeholder Engagement to be able to access records. The estimated annual costs are as follows:
Digital Communication Platform Licenses:
- Standard Plan: $8,700,000 per year (100,000 users at $7.25 per month).
CRM Platform Licenses:
- Professional Tier: $450,000 per year (500 users at $75 per month).
Total Estimated Cost:
- Lower Tier Option (Standard Communication + Professional CRM): $9,150,000 per year.
Buffer for Operational Costs: To ensure the program’s success, a buffer of approximately 15% should be added to cover additional operational expenses, unforeseen costs, and any necessary uplifts or expansions in features or seats. This does not take into consideration volume discounts that CISA would normally expect when purchasing through a reseller such as Carahsoft or CDW.
Cost Justification: Although the initial investment is significant, the potential savings from avoiding cyber incidents should far outweigh these costs. Considering that the average cost of a data breach in the U.S. is approximately $9.48 million, preventing even a few such incidents through this program could easily justify the expenditure.
Conclusion
The cybersecurity challenges faced by State, Local, Tribal, and Territorial (SLTT) governments and critical infrastructure sectors are becoming increasingly complex and urgent. As cyber threats continue to evolve, it is clear that the existing defenses are insufficient to protect our nation’s most vital services. The proposed expansion of the Joint Cyber Defense Collaborative (JCDC) to allow broader participation by practitioners in the private sector who serve public sector clients, regardless of the size or current affiliation of their company presents a crucial opportunity to enhance collaboration, particularly among SLTTs, and to bolster the overall cybersecurity baseline.These efforts align closely with CISA’s strategic goals of enhancing public-private partnerships, improving the cybersecurity baseline, and fostering a skilled cybersecurity workforce. By taking decisive action now, we can create a more resilient and secure nation, ensuring that our critical infrastructure remains protected against the ever-growing array of cyber threats.
This action-ready policy memo is part of Day One 2025 — our effort to bring forward bold policy ideas, grounded in science and evidence, that can tackle the country’s biggest challenges and bring us closer to the prosperous, equitable and safe future that we all hope for whoever takes office in 2025 and beyond.
PLEASE NOTE (February 2025): Since publication several government websites have been taken offline. We apologize for any broken links to once accessible public data.
OPM’s new HR 2.0 initiative is entering hostile terrain. Those who have followed federal HR modernization for years desperately want this effort to succeed.
This rule gives agencies significantly more authority over certain career policy roles. Whether that authority improves accountability or creates new risks depends almost entirely on how agencies interrupt and apply it.
Our environmental system was built for 1970s-era pollution control, but today it needs stable, integrated, multi-level governance that can make tradeoffs, share and use evidence, and deliver infrastructure while demonstrating that improved trust and participation are essential to future progress.
Durable and legitimate climate action requires a government capable of clearly weighting, explaining, and managing cost tradeoffs to the widest away of audiences, which in turn requires strong technocratic competency.