Keeping the Lights on: Fixing Pakistan’s Energy Crisis

A stable and thriving Pakistan is the key to preserving harmony and facilitating progress in the broader South Asia region. Afghanistan, which is to the west of Pakistan, has a long border that divides the Pakhtun people between the countries. As a result of this border, Pakistan not only has a significant role in the Afghan economy, but instability in the loosely governed Pakistani frontier region spills across the border into Afghanistan. Because of this relationship, Pakistan has a direct impact on the outcome on the 13 year U.S. led war in Afghanistan. On the other hand, an unstable Pakistan would not only shatter budding trade relations with India, but could also spark conflict between the two nuclear armed rivals.
From frequent attacks by Islamic militants across the country to a slowing economy, it is clear that there are many issues that threaten Pakistan’s stability. However, the most pressing issue that Pakistan faces today is its deteriorating economy. In particular, a crushing energy shortage across the country significantly constrains economic growth. This fiscal year, Pakistan’s Gross Domestic Product (GDP) is forecasted to grow by measly 3.4 percent. At the same time, the country’s population is expected to grow by 1.8 percent adding to the 189 million people living there today. If there aren’t jobs available for the millions of young Pakistanis entering the work force, not only will poverty increase, but there is a strong possibly that some of these youth could vent their frustrations by joining the countless Islamic militant groups active in the country.
To build a more prosperous economy, Pakistan needs to address its energy problems. Without a reliable source of electricity or natural gas, how can Pakistani businesses compete on the global market? Large parts of the country today face blackouts lasting an average of 10 hours each day because of the electricity shortage. The current gap between electricity generation and demand is roughly 2500 MW, a shortage large enough to keep a population of 20 million or the city of Karachi in the dark.
These power shortages are only expected to become worse in the coming summer months. This is because demand for electricity peaks in the sizzling heat, while hydroelectric generation decreases as the water flow in the rivers drops due to seasonal fluctuation. This article will focus on the causes of the country’s energy problems involving the electricity sector and explore possible directions Pakistan can take to improve its energy situation, building its economy in the process.
How Does Pakistan Generate its Electricity?
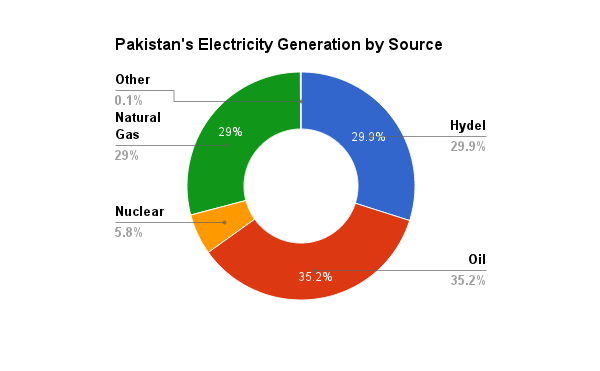
Figure 1 breaks down Pakistan’s electricity generation by source. Thermal power, which includes natural gas, oil, and coal generated electricity, accounts for 70 percent of Pakistan’s total electricity generation, while hydroelectric generation is roughly responsible for the remaining 30 percent.
Electricity generated from furnace oil accounts for slightly over a third of Pakistan electricity. In the early 1990s, the country faced a power shortage of about 2000 MW when there was a peak load on the electricity grid. To resolve the growing crisis, the Pakistani government implemented a new policy in 1994, which was designed to attract foreign investment in the power sector and as a result there was construction of oil based power plants. These power plants were cheaper and faster to construct compared to other electricity generation plants such as hydroelectric dams. At the same time, the relatively low prices (below $17 a barrel) of crude oil meant that these plants generated electricity fairly cheaply. Fast forward to present times, the price of crude oil has risen to hover roughly around $100 a barrel. Unlike nearby Saudi Arabia, Pakistan is naturally not well endowed in crude oil reserves. This means that Pakistan must ship increasing amount of valuable currency abroad to secure the oil it needs to keeps these power plants running.
Along with furnace oil power plants, natural gas is used to generate about another third of electricity; it is provided by domestic reserves, thereby helping Pakistan’s economy and energy security. According to the U.S. Energy Information Administration, Pakistan has proven natural gas reserves of 24 trillion cubic feet (Tcf) in 2012. These reserves will last Pakistan an estimated 17 years based on the country’s annual consumption rate of 1.382 Tcf in 2012. At the same time, consumption rates are estimated to increase four fold to nearly 8 Tcf per year by the year 2020, further reducing the size of the domestic reserves.
The Pakistani government in 2005 under President Pervez Musharraf promoted the conversion of cars to run on compressed natural gas (CNG) instead of gasoline. The rationale was that this conversion would reduce the amount of money spent on purchasing and importing oil abroad. At the same time, CNG is cleaner for the environment than burning gasoline. As a result of this policy, more than 80 percent of Pakistan’s cars today run on CNG.But because of this surging demand for its limited natural gas, there is a critical shortage of it which has adversely impacted the country’s ability to use this fuel source to generate electricity. Essentially Pakistanis are forced to decide whether to use natural gas to fuel their cars, cook their food, or generate electricity.
Power Theft and the Circular Debt Issue
The reliance on oil and natural gas to generate electricity is incredibly inefficient, but these inefficiencies alone are not responsible for the crippling power shortages. The other source of tension involves the accumulation of circular debt in the electricity sector over the past few years. Circular debt is a situation where consumers, electricity producers and the government all owe each other money and are unable to pay. By June 2013 when the new government led by Prime Minister Nawaz Sharif took control, this circular debt had ballooned to $5 billion.
There are several reasons for the accumulation of this debt; the largest problem stems from power theft. Many Pakistani elites and even parts of the government do not pay their electricity bills. The law and order situation also prevent power companies from collecting bills in certain parts of the country. As a result, Pakistani electricity companies currently recover only 76 percent of the money that electricity consumers owe them. In fact, the Pakistani Minister for Water and Power, Mr. Khwaja Muhammad Asif, has acknowledged that the Pakistani government is one of the country’s largest defaulters of electricity bills. As part of recent crackdown, the power ministry cut supplies to the Prime Minister’s home and the Parliament House (among many government offices) because they were delinquent on their electricity bills. While many Pakistanis don’t pay their electricity bills, others steal power by illegally hooking into the power grid. This theft coupled with an inefficient electricity grid and the associated transmission loss means that Pakistan’s electricity generators are left with huge financial losses.
All these losses accumulate to form the circular debt and it places power producers in a position where they are unable to purchase enough fuel from abroad to operate power plants at full capacity. With an installed generation capacity of 22500 MW, Pakistan currently has more than enough installed capacity to meet peak demand levels today. The power producers are in reality only able to generate between 12000MW and 15000MW because of both inefficient energy infrastructure and circular debt. This actual amount of electricity generated is far less than the 17000 MW of demand nationwide during peak hours of electricity usage.
The circular debt also makes it more difficult for power producers to invest in upgrading existing electricity infrastructure. If power producers don’t have the money to operate oil based power plants at full capacity, they certainly do not have enough capital to build newer, more efficient power plants. Even when the lights are on, the inefficient electricity system takes an additional toll on the country’s economy. Pakistanis today pay more than double their Indian neighbors for electricity (16.95 Pakistani Rupees vs. 7.36 Pakistani Rupees per KWh respectively), putting Pakistani firms at a further disadvantage compared to regional competitors.
Fixing Pakistan’s Electricity Problems
One of Prime Minister Nawaz Sharif’s first actions after taking office was to pay off the $5 billion in circular debt that had accumulated by July 2013. Unfortunately, this step alone will not solve the power woes as it does not fix the underlying causes of the country’s power crisis. In fact, the circular debt has accumulate again, and stood at $1.8 billion by January 2014. To sustainably address the power crisis, Pakistanis need to change their attitude towards power theft by forcing the government and those delinquent to clear outstanding bills. At the same time, Pakistan must improve the efficiency of its electricity sector as well as expand and diversify its electricity generating capacity in order to ensure that the country can handle the expected growth in demand over the coming years.
Hydroelectric Generation
Pakistan has tremendous potential to expand its electricity generating capacity by developing its renewable energy resources. At nearly 30 percent, hydroelectricity is already a major source of electricity generation, but according to the Pakistani government, this reflects only 13 percent of the total hydroelectric potential of the country. There are several drawbacks of major hydroelectric projects including that they are capital intensive and require extensive time to build. Furthermore, hydroelectric dams are harmful to the local ecosystem and can displace large populations. The U.S. government is actively investing in helping Pakistan develop its hydroelectric resources; in 2011, USAID funded the renovation of the Tarbela Dam. In the process, this added generation capacity of 128 MW, which is enough electricity for 2 million Pakistanis.
Solar Energy

According to the USAID map of solar potential in Pakistan, the country has tremendous potential in harnessing the sun to generate electricity. Pakistan has an average daily insolation rate of 5.3 kWH/m2, which is similar to the average daily insolation rate in Phoenix (5.38 kWH/m2) or Las Vegas (5.3 kWH/m2), which are some of the best locations in the United States for solar generated electricity. So far, Pakistan has begun construction on a photovoltaic power plant in Punjab that will begin to produce 100 MW by the end of 2014.According to the World Bank some 40,000 villages in Pakistan are not electrified. Tapping into these solar resources could easily electrify many of these off the grid villages, while avoiding an increase in demand on the national electricity grid.
Nuclear Energy
Pakistan has three currently active nuclear power plants: two located in Punjab and one in the southern port city of Karachi. The two Chinese built nuclear power plants in Punjab each have a net generation capacity of 300 MW. The Karachi power plant, which was built with a reactor supplied by Canada in 1972, has a net generation capacity of 125 MW, enough to provide power to 2 million Pakistanis. China has been a key supplier and investor in Pakistani nuclear energy, but there are some concerns regarding the transfer of nuclear technology to Pakistan, where A.Q. Khan’s nuclear network was headquartered. Specifically, China argues that its alliance with Pakistan predates its joining of the Nuclear Suppliers Group (NSG), which has restricted nuclear sales to Pakistan, so this justifies its desire to supply Pakistan with the technology. The Chinese are helping construct four more nuclear power plants, the first of which is expected to be online starting in 2019. While these plants will add 2,200 MW of generation capacity, these nuclear power projects are expensive; the current nuclear power plants under construction are said to cost about $5 billion per plant, an investment that China is helping finance.
Coal Power
There is a large amount of coal located in the Thar Desert in the southeastern part of the country. While the quality of the coal isn’t the best, Pakistan has a lot of it, nearly 175 billion tons, which is enough to meet current electricity demands for more than 300 years. However, Pakistan currently only has one operational coal power plant.
Pakistan is taking steps to develop this resource. In January 2014, Prime Minister Nawaz Sharif and former President Zardari broke ground on a $1.6 billion coal power project in the Thar Desert. This particular project is expected to be operational by 2017.
Pakistan has taken some clear steps such as developing its renewable resources and tapping its coal reserves, which can help expand and diversify where and how it generates its electricity. Further harnessing these resources will help alleviate the electricity shortfall. However, these steps alone will not solve the energy crisis. The more difficult solution involves changing the country’s attitude toward power theft, both by private citizens and the government. Convincing people to pay their electricity bills is difficult when even the government itself doesn’t pay its fair share. At the same time, there is less incentive to pay when citizens don’t even have access to a dependable source of electricity when they need it. As long as this attitude is prevalent among Pakistanis from all walks of life as well as the government, the country cannot sustainably solve its energy woes. Circular debt will continue to accumulate and large sections of the country will face hours of darkness each day.
Tackling the energy problem is the first step to strengthening the economy; over time, a growing economy will attract greater investment in the energy sector. Pakistan’s sensitive geographic location could become a strategic asset as it would serve as a bridge linking the economies of Afghanistan and Central Asia with the broader Indian subcontinent. Not only does the population provide Pakistan with a large domestic market, but it also empowers the country with a young, entrepreneurial workforce. This gives Pakistan tremendous potential, but can only be unleashed if the country figures out a way to keep the lights on and the factories humming.
Population Projection Tables by Country: Pakistan. The World Bank. 2014.
“Global Economic Prospects: Pakistan,” The World Bank, 2014. http://www.worldbank.org/en/publication/global-economic-prospects/regional-outlooks/sar
Ghumman, Khawar, “Increased loadshedding worries Prime Minister,” Dawn, April 24 2014. http://www.dawn.com/news/1102953
“Electricity shortfall reaches 2,500MW,” The Nation, Jan 2 2014. http://www.nation.com.pk/national/02-Jan-2014/electricity-shortfall-reaches-2-500mw
“Pakistan Energy Yearbook,” Hydrocarbon Development Institute of Pakistan, 2012. http://www.kpkep.com/documents/Pakistan%20Energy%20Yearbook%202012.pdf
“Policy Framework and Package of Incentives for Private Sector Power Generation Projects in Pakistan,” Government of Pakistan, 1994. http://www.ppib.gov.pk/Power%20Policy%201994.pdf
Beg, Fatima and Fahd Ali, “The History of Private Power in Pakistan,” Sustainable Development Policy Institute, 2007. http://www.sdpi.org/publications/files/A106-A.pdf
“Crude Oil Purchase Price.” U.S. Energy Information Administration, 2014. http://www.eia.gov/dnav/pet/hist/LeafHandler.ashx?n=PET&s=F004056__3&f=M
Pakistan. U.S. Energy Information Administration. http://www.eia.gov/countries/country-data.cfm?fips=pk
Tirmizi, Farooq, “The Myth of Pakistan’s infinite gas reserves,” The Express Tribune, Mar 14 2011. http://tribune.com.pk/story/132244/the-myth-of-pakistans-infinite-gas-reserves/
“Natural Gas Allocation and Management Policy,” Government of Pakistan: Ministry of Petroleum & Natural Resources, Sept 2005. http://www.ogra.org.pk/images/data/downloads/1389160019.pdf
Boone, Jon, “Pakistan’s government deflates dream of gas-powered cars,” The Guardian, Dec 25 2013. http://www.theguardian.com/world/2013/dec/25/cars-pakistan-compressed-natural-gas-rationing
Bhutta, Zafar, “Circular debt: Power sector liabilities may cross Rs1 trillion by 2014,” The Express Tribune, May 26 2013. http://tribune.com.pk/story/554370/circular-debt-power-sector-liabilities-may-cross-rs1-trillion-by-2014/
Pakistan’s Energy Crisis: Power Politics. The Economist, May 21 2012.http://www.economist.com/blogs/banyan/2012/05/pakistan%E2%80%99s-energy-crisis
Jamal, Nasir. “Amount of unpaid power bills increases to Rs286bn.” Dawn. Apr 16 2014. http://www.dawn.com/news/1100237
“Govt one of the biggest electricity defaulters, says Khawaja Asif.” Dawn, May 2 2014. http://www.dawn.com/news/1103707
“Pakistan cuts prime minister’s electricity for not paying bills” Reuters. Apr 29 2014. http://in.reuters.com/article/2014/04/29/uk-pakistan-electricity-idINKBN0DF1DL20140429
Kazmi, Shabbir. “Pakistan’s Energy Crisis.” The Diplomat, Aug 31 2013. http://thediplomat.com/2013/08/pakistans-energy-crisis/
Abduhu, Salman. “Lack of funds real reason behind loadshedding.” The Nation, May 9 2014. http://www.nation.com.pk/lahore/09-May-2014/lack-of-funds-real-reason-behind-loadshedding
Electricity Shock: “Pakistanis Paying the Highest Tariffs in Region.” The Express Tribune, Jan 31 2014. http://tribune.com.pk/story/665548/electricity-shock-pakistanis-paying-highest-tariffs-in-region/
Chaudhry, Javed. “Circular Debt: ‘All dues will be cleared by July’.” The Express Tribune, June 14 2013. http://tribune.com.pk/story/563095/circular-debt-all-dues-will-be-cleared-by-july/
“Hydropower Resources of Pakistan.” Private Power and Infrastructure Board, Feb 2011. http://www.ppib.gov.pk/HYDRO.pdf
USAID Issues $6.66 m for Tarbela Units. Dawn. Mar 9 2011. http://www.dawn.com/news/612058/usaid-issues-666m-for-tarbela-units
“Tarbela Dam Project.” USAID, Sept 26 2013. http://www.ppib.gov.pk/HYDRO.pdf
“Pakistan Resource Maps.” National Renewable Energy Laboratory, Aug 2006. http://www.nrel.gov/international/ra_pakistan.html
The Feasibility of Renewable Energy in Pakistan, Triple Bottom-Line, 2012. http://www.tbl.com.pk/the-feasibility-of-renewable-energy-in-pakistan/
“Surface Meteorology and Solar Energy,” NASA, 2013. https://eosweb.larc.nasa.gov/sse/RETScreen/
Quad-e-Azam Solar Power. http://www.qasolar.com/
Renewable Energy in Pakistan: Opportunities and Challenges, COMSATS-Science Vision, December 2011. http://www.sciencevision.org.pk/BackIssues/Vol16_Vol17/02_Vol16_and_17_Renewable%20Energy%20in%20Pakistan_IrfanAfzalMirza.pdf
CHASNUPP-1. Nuclear Threat Initiative, 2014. http://www.nti.org/facilities/112/
CHASNUPP-2. Nuclear Threat Initiative, 2014. http://www.nti.org/facilities/113/
KANUPP. Nuclear Threat Initiative, 2014. http://www.nti.org/facilities/111/
Shah, Saeed. “Pakistan in Talks to Acquire 3 Nuclear Plants From China.” The Wall Street Journal, Jan 20 2014. http://online.wsj.com/news/articles/SB10001424052702304757004579332460821261146
Mahr, Krista. “How Pakistan and China Are Strengthening Nuclear Ties.” Time, Dec 2 2013. http://world.time.com/2013/12/02/how-pakistan-and-china-are-strengthening-nuclear-ties/
“Pakistan’s Thar Coal Power Generation Potential.” Private Power and Infrastructure Board, July 2008.http://www.embassyofpakistanusa.org/forms/Thar%20Coal%20Power%20Generation.pdf
“Discovery Of Ignite Coal In Thar Desert.” Geological Survey of Pakistan, 2009. http://www.gsp.gov.pk/index.php?option=com_content&view=article&id=30:thar-coal&catid=1:data
“Nawaz, Zardari launch Thar coal power project.” Dawn, Jan 31 2014. http://www.dawn.com/news/1084003
Ravi Patel is a student at Stanford University where he recently completed a B.S. in Biology and is currently pursuing an M.S. in Biology. He completed an honors thesis on developing greater Indo-Pakistan trade under Sec. William Perry at the Center for International Security and Cooperation (CISAC). Patel is the president of the Stanford U.S.-Russia Forum. He also founded the U.S.-Pakistan Partnership, a collaborative research program linking American and Pakistani university students. In the summer of 2012, Patel was a security scholar at the Federation of American Scientists. He also has extensive biomedical research experience focused on growing bone using mesenchymal stem cells through previous work at UCSF’s surgical research laboratory and Lawrence Berkeley National Laboratory.
Nelson Zhao is a fourth year undergraduate at University of California, Davis pursuing degrees in economics and psychology. Nelson is the Vice-President at the Stanford U.S.-Russia Forum and the Program Director at the U.S.-Pakistan Partnership. At the U.S.-Pakistan Partnership, he aims to develop a platform to convene the brightest students in order to cultivate U.S.-Pakistan’s bilateral relations.
A Scenario for Jihadist Nuclear Revenge
The Greatest Threat
The weapon was ready, a simple fission device similar to the bomb that destroyed Hiroshima. It had been finally assembled in a rented storage space on the outskirts of Las Vegas. Gulbuddin Hekmatyar had spent years quietly contemplating while meticulously planning this diabolical, logistically challenging mission. Among other things, the plot necessitated recruiting and directing a number of operatives, some technically skilled, located in several countries. All were individuals devoted to his cause and committed to the Jihadist goal of detonating a nuclear bomb in an American city. He chose Las Vegas because the city epitomized western decadence.
The bomb’s essential component – 140 pounds of highly enriched uranium (HEU) – had been stolen or secretly purchased, bit-by-bit, mostly from Pakistan, but also from India, North Korea, Russia, Ukraine and Kazakhstan. It took years to collect, hide and safeguard all the necessary HEU in northwest Pakistan. From there, small pieces of the fissile material and some structural bomb components, hidden and well shielded in multiple shipments, were transported to U.S. ports or border crossings, and eventually to Las Vegas and the rented storage space. With all the components covertly acquired or fabricated by dedicated Jihadists in Pakistan and the United States, the relatively simple bomb finally could be assembled. It was comprised of a long, large-bore, artillery-type barrel; a heavy-duty breech; and enough chemical explosive to propel an appropriately shaped, 70-pound HEU piece through the barrel at very high velocity into another appropriately shaped, 70-pound piece of HEU affixed to the end of the barrel. Slamming together these two sub-critical masses would create the critical mass needed for an explosive chain reaction.
It was time. The plan of attack was straightforward and foolproof. Weighing under a ton and less than a dozen feet long, the weapon in its lead-lined crate fit easily inside a small, rented truck. A lone, suicidal operative drove and parked the truck near the Strip, then activated the electronic device triggering the detonator that set off the chemical explosion. The HEU bullet accelerated through the barrel and merged almost instantaneously with the target HEU. Within microseconds, the critical mass exploded, releasing kilotons of energy, a blinding, rapidly expanding ball of light, heat and deadly radiation. A shock wave propagated through the atmosphere, flattening almost every building within a half-mile of the detonation point. Tens of thousands were dead or injured. Las Vegas was in ruins. The threat had become reality.
When President Obama declared in 2009 that “nuclear terrorism is the most immediate and extreme threat to global security,” it was scarcely noticed. Yet when questionable sources announced that the Mayan Calendar predicted the end of the world in 2012, media and public attention was astonishing. The apocalyptic prediction arising from myth took hold, while a warning of potential catastrophe based in reality, put forth by Barack Obama in Prague, passed us by. Supernatural doomsday scenarios readily gain traction in our public discourse, but threats to our civilization from proven nuclear dangers elude us.
The public and press largely ignored other sobering news in 2010 when Wikileaks revealed that a 2009 cable from the U.S. Ambassador to Pakistan, Anne W. Patterson, warned that “our major concern is not having an Islamic militant steal an entire weapon, but rather the chance someone working in government of Pakistan facilities could gradually smuggle out enough enriched uranium to eventually make a weapon.”
By raising the specter of nuclear terrorism, the Wikileaks revelation gave concrete urgency to President Obama’s abstract concerns. But few paid attention, in part because few understand nuclear weapons risks and realities.
Passage of time and reluctance to think the unthinkable have generated complacency. No nuclear weapon has been used aggressively since the August 9, 1945, attack on Nagasaki. Despite the existence of vast numbers of nuclear weapons, Americans expect nuclear restraint because they believe Mutually Assured Destruction (MAD) is a reliable deterrent. MAD presumably ensures that a country first using nuclear weapons will be wiped out by a retaliatory blow. But if a non-state entity were to perpetrate a nuclear weapons attack, at whom and where would retaliation be directed? An act of nuclear terrorism would obviate 69 years of stability engendered by MAD, an appropriately chosen topic of satirical banter in the film “Dr. Strangelove,” yet a grim reality.
Obama’s words that nuclear terrorism is an “immediate and extreme threat” are not an exaggeration. Terrorists now have new opportunities to covertly fabricate nuclear weapons on their own, and the threat is compounded by the potential anonymity of the attackers.
The cable allegedly sent by Ambassador Patterson leads to several questions: what is enriched uranium and how available is it? How is it used in a bomb, and who could use it? Where and how could it be delivered? What would be its effect? And perhaps the first and biggest question – why would terrorists aspire to manufacture, deploy, and detonate a nuclear weapon?
The 9/11 attacks marked the beginning of a “Terrorist Era” with a capital T. That triple attack profoundly disturbed, shocked and injured the nation, psychologically as well as physically. It suggested that a goal of certain terrorists is the destruction of the United States and its allies, and nuclear capability would make that goal attainable.
In 1998, Osama bin Laden declared that it was his Islamic duty to acquire weapons of mass destruction. Because Islam deplores killing women and children, religious justification was sought for such weapons. In 2003, three Saudi clerics associated with Al Qaeda provided justification in a fatwa that stated:“One kills in a good manner only when one can.”
Thus the “why” can be revenge for the deaths of Muslim civilians or Osama bin Laden, Jihadist punishment of a decadent, anti-Islamic civilization, or retribution for western support of Israel. Still, the easily stated words “nuclear revenge” are not readily internalized. Unlike “tsunami” or “colon cancer,” the term “nuclear terrorism” does not usually evoke a visceral reaction. Such a response is unlikely until people intellectually and emotionally comprehend the potential threat of rogue nuclear weapons. And comprehension requires some understanding of the bomb itself.
In addition to understanding the weapon, people also must grasp the feasibility and consequences of an act of nuclear terrorism. A credible scenario can provide this. In his book, The Second Nuclear Age, Yale Professor Paul Bracken argues that war games based upon scenarios involving nuclear weapons played a significant role in clarifying and shaping strategic thinking during the height of the Cold War. “Scenarios set the stage for the game’s interactions,” he wrote. “Scenarios…are hypothetical plot outlines of plausible future developments. They are not forecasts or predictions…”
The Pentagon hypothesizes terrorist scenarios, but the public does not. Our opening Las Vegas scenario attempts to focus the reader’s mind on the real potential for nuclear catastrophe.
But first the Bomb.
The Bomb
Tremendous energy can be released when the nucleus or inner core of an atom undergoes a transformation. For uranium, the energy releasing transformation is the splitting apart or fission of the nucleus, producing various combinations of lighter atoms such as barium and krypton as “fission products.”
Uranium can exist in different forms or “isotopes,” but all isotopes of uranium contain 92 positively charged protons in the nucleus with 92 negatively charged electrons dancing around the nucleus. These charged particles determine uranium’s chemical properties. However, the uranium nucleus also can contain varying numbers of uncharged neutrons. Somewhat greater than ninety-nine percent of uranium found in nature – uranium isotope 238 – has 146 neutrons in the nucleus. Thus the isotope’s 92 protons and 146 neutrons account for its atomic weight of 238.
Uranium-235, with only 143 neutrons, is the dangerous isotope –because it tends to easily fission if it absorbs a neutron. The fissioning of U-235 powered the bomb that exploded over Hiroshima. Fortunately this isotope is very rare; less than one percent of all forms of uranium found in the earth consist of U-235. Uranium can create an explosive chain reaction—only if U-235 is in highly concentrated form, which is extremely difficult to obtain as described later. But first we explain the basics of nuclear bomb design.
While modern hydrogen-plutonium bombs use a fission-fusion reaction to create the most powerful explosions (which can also use highly enriched uranium instead of plutonium to start the fission reaction), the easiest first-generation atomic bomb to construct entails only fission of highly enriched uranium (HEU), with a concentration of typically 80 percent or greater in the fissile isotope U-235. The Hiroshima bomb was essentially an artillery gun in which chemical explosives fired one 70-pound piece of HEU into another 70-pound piece of HEU, with an average enrichment of 80 percent U-235. The design was so simple that J. Robert Oppenheimer, scientific director of Los Alamos, decided that the prototype did not need to be tested. (One of the reasons not to do a proof test was due to the very limited HEU available during the Second World War.) Indeed the first test of this gun-type bomb occurred when it exploded with such devastating effect at 1,900 feet above Hiroshima on August 6, 1945, killing nearly 100,000 people. Weapons developers at Los Alamos avoided using the word bomb, instead giving euphemistic names such as gadget to their creations. The Hiroshima weapon was inaptly named “Little Boy.”
During the Manhattan Project, the great challenge was collecting and concentrating fissionable U-235. Because U-238 and U-235 have identical chemical properties, separation can only be achieved by exploiting the slight difference in mass arising from one isotope having three more neutrons than the other. One method of separation for enrichment purposes was developed using electric and magnetic forces in a modified form of the cyclotron called the calutron. A second method involved creating a compound in gaseous form of uranium and fluorine, then passing the gas through successive microscopic filters making use of the principle of diffusion.
After the Second World War, improved centrifuges emerged as a more efficient method for enriching uranium. A Dutch company, which became part of the Urenco consortium that also includes Germany and the United Kingdom, was an early adopter of the improved centrifuge technology. Commercial production of enriched uranium for nuclear power plants became a worldwide activity. A. Q. Khan, a Pakistani metallurgist working at the Dutch facility, stole the centrifuge design drawings and brought the technology to Pakistan by the mid-1970s. Throughout the 1980s to the early 2000s, he then sold enrichment equipment to Iran, North Korea, and Libya, and had a vast network of suppliers in at least a dozen other countries.
Having used these centrifuge designs to enable large-scale production of enriched uranium, today Pakistan is rapidly achieving status as having one of the largest and fastest growing stockpile of nuclear weapons after the United States, Russia and China. While some nuclear-armed countries are reducing their weapons count, Pakistan has a vigorous program of nuclear weapons development. Its stockpile is thought to have 100 to 200 nuclear weapons.
Production of nuclear weapons is of great concern, but production of highly enriched uranium is even more worrisome. Although a nuclear bomb might be stolen from a country’s stockpile, it would have anti-activation safeguards (such as access codes and electronic locks) that a thief would find very difficult to penetrate. However, highly enriched uranium for a terrorist is like flour for a baker. Each material is simply one ingredient from which something much more impressive can be concocted. Pakistan continues to produce weapons-grade U-235 at a more intense rate than any country in the world. It is reliably estimated that they have stockpiled thousands of pounds of enriched U-235 that could lead to the fabrication of dozens of new nuclear weapons.
Eyes continue to focus on Pakistan as a potential source of nuclear bomb material. Yet unsecured highly enriched uranium elsewhere has been a worry for many years. Of particular concern have been the vast amounts of weapons-grade uranium that were left relatively unguarded in Russia, Ukraine, Belarus and Kazakhstan after the break-up of the Soviet Union. These have been potential access points for terrorists. Hundreds of secret bombs could have been fabricated.
Prior to 9/11, we could not imagine rogue, non-state entities having the ability to construct a nuclear weapon. Yet vast numbers of reports, documents, drawings and photographs from the Manhattan Project have been declassified. The Little Boy development work at Los Alamos is available for the world to examine. Following 9/11, government agents visited war museums in the United States to remove publicly displayed, artillery-gun components replicating Little Boy. But the proverbial horse was already out of the barn.
Conceivably, determined terrorists could acquire 140 pounds of weapons-grade uranium-235, the amount used in the Hiroshima bomb. While a person weighing 140 pounds would fully occupy a seat at a dinner table, 140 pounds of uranium, the densest of all naturally occurring elements, is less than the size of a football.With the material in hand, processing and fabrication steps for constructing a weapon rely on well-established and widely known metallurgical and manufacturing techniques. Who then might do this? Where would construction take place? And under whose leadership?
A Return to Our Scenario
The villain of our hypothetical scenario is the leader of a militant group located in the tribal territory of Northwestern Pakistan.Skeptics may doubt that our protagonist, Gulbuddin Hekmatyar, could obtain the equipment and expertise needed for weaponization of highly enriched uranium. While not on Abercrombie and Kent tourist itineraries, the frontier region of Northwest Pakistan is the site of the colorful village of Darra Adam Khel. This unique tribal enclave near the Khyber Pass, just 20 miles South of Peshawar, has been manufacturing copies of small weapons since the late 19th century using basic lathes, drills and other readily available tools. During the Mujahideen struggle with the Soviet Union in the 1980s, the United States was not unhappy to see their production of anti-aircraft weapons. Darra Adam Khel is a major source of weapons in the South Asia region. The potential to fabricate the components for a Little Boy clone clearly exists there.
Osama bin Laden and other Al Qaeda leaders have been eliminated, but other militant jihadists have the capacity and the will to engage in development and use of a nuclear weapon. We chose Gulbuddin for our scenario because he was involved with the 1993 bombing of the World Trade Center, he controls a formidable belligerent organization with the resources to actualize this sequence of events, and he is not part of Al Qaeda or the Taliban. An Afghan student of engineering at Kabul University in the early 1970s, he organized at that time what was probably the first militant Islamic organization in Afghanistan. His student group shot at and threw acid at women in Kabul who were wearing mini-skirts. In a confrontation in 1972 with the rival Maoist political group on campus, Gulbuddin shot and killed their leader. After being imprisoned, he escaped and was given refuge by Islamic fundamentalist elements of the Pakistani government in 1975. Some officials in Pakistan, which had border region disputes with Afghanistan since its founding in 1947, saw in Gulbuddin a potential ally in future conflicts with Afghanistan.
In the early 1980s, when the United States started channeling large amounts of funds and weapons to the Mujahideen for their struggle with the Soviet Union, the Pakistan intelligence agency, the ISI, provided Gulbuddin with a substantial portion of those resources. This enabled the charismatic fanatic to establish a formidable organization known as Hezb-e-Islami.
During the mid-1980s Gulbuddin was instrumental in organizing terrorist training camps in Afghanistan to which “Arab” fighters were invited. Gulbuddin welcomed Osama bin Laden, who first came to Afghanistan to fight the infidel Soviets.
Gulbuddin and his organization did not pursue the Soviets as fully as they might have, since he was waiting to use his fighting potential in a putsch to take over Afghanistan following the departure of the Red Army. He did indeed engage in a civil war for control of Afghanistan that began in 1992. But after achieving the position of Prime Minister of Afghanistan in 1993, Gulbuddin was eventually defeated by the Northern Alliance led by Massoud. With the fall of Gulbuddin, the ISI of Pakistan threw their support in 1994 to the newly organized Taliban.
Few are aware of Gulbuddin’s contacts with the perpetrators of the 1993 bombing of the World Trade Center. Those connections and his meetings with the Blind Sheik were revealed in the trials of the World Trade Center bombers held in New York City. It is too often said that the weakening of Al Qaeda ensures the safety of the U.S. from terrorist attack. However, the 1993 bombing of the World Trade Center involved non-Al Qaeda players and leadership figures from that event are still active. This is just one example of a non-Al Qaeda terrorist group that might become a perpetrator of nuclear terrorism.
Today, Gulbuddin maintains a militant presence in the frontier region and has the organizational ability to engage in ambitious terrorist actions. Gulbuddin is neither a tribal “war lord” nor a narrowly educated religious militant. He is a sophisticated intellectual and political leader who completed two years of engineering education. There is every indication that he is as vicious a proponent of terrorism as was Osama bin Laden.
Nothing suggests that Gulbuddin is, in fact, plotting a nuclear attack on an American city. But he is the key player in our scenario because he has the knowledge, resources and frame of mind for implementing such an attack. If there is one such person and group, there are likely others.
The fissile materials available in Pakistan can be fabricated in the Khyber region to serve as components for a gun-type Hiroshima bomb. The amount of radiation released by the highly enriched uranium can be easily shielded and thus easily elude detection at border crossings or from aerial drones. Since suicidal jihadists probably would assemble it, many of the features that were built into Little Boy 69 years ago to ensure safe delivery and controlled detonation could be ignored.
While this scenario has focused on terrorism originating in the Afghanistan-Pakistan border area, other scenarios might be equally plausible. In May 2011, the Belfer Center for Science and International Affairs at Harvard University issued a report entitled, “The U.S.-Russia Joint Assessment on Nuclear Terrorism.” The study group analyzed possible threats from three terrorist organizations known to have systematically sought to obtain nuclear weapons: Al Qaeda, groups in the Northern Caucasus, and the Japanese cult group, Aum Shinrikyo. Each could be a suitable scenario protagonist. If Iran began producing tens of pounds of HEU, then the possibility of Hezbollah obtaining that material would also merit consideration.
Additional scenarios can be hypothesized with sociopaths who are American citizens. Two figures stand out as prototypes with the organizational and technical capacity needed for implementation. One is Timothy McVeigh, whose homemade bomb destroyed the Alfred P. Murrah Federal Building in Oklahoma City on April 19, 1995. The other is Ted Kaczynski, the mathematics genius known as the Unabomber. He perpetrated seventeen explosive attacks killing three people between 1978 and his arrest in 1996.
The first public alert to the possibility of a small group of individuals in the United States building a nuclear bomb to attack society came in the early 1970s from Theodore B. Taylor, a physicist who invented highly efficient, small sized nuclear weapons at Los Alamos National Laboratory. He recognized and was obsessed by the possibility that fissile material could be stolen from commercial facilities that were enriching uranium. The U.S. government had encouraged corporations to process uranium for use in nuclear reactors. In his book, The Curve of Binding Energy, award-winning writer John McPhee documented the story of this eccentric but highly creative physicist. His account was first published in the New Yorker in 1973. Both Taylor and McPhee seemed convinced that a rogue nuclear weapon would detonate somewhere in the United States prior to the beginning of the 21st Century.
The vulnerabilities of enriched uranium supplies in the United States in the 1970’s were astonishing. We assume that such homeland dangers have been ameliorated. Yet we are aghast at the July 28, 2012, spectacle of an 82-year-old nun and two equally unlikely compatriots penetrating the innermost sanctum of the highly enriched uranium facility at Oak Ridge, Tennessee, and spraying the storage building with graffiti. The words they posted said, “Plowshares Please Isaiah.” If such lax security is exposed in Bear Creek Valley, U.S.A., what might be the case in Pakistan, Russia, North Korea or China?
Implications and Actions
A successful act of nuclear terrorism would, in a blinding flash, change the nature of civilization, as we know it. When the consequences of an action are so enormous, perhaps one should pause to reflect upon it, even if scenarios and anecdotes may not be persuasive. But our lives are frequently influenced by low probability events. We wear seat belts. We buy lottery tickets.
Perhaps we should be more proactive in supporting our government’s actions to ameliorate potential risks. The international community is currently discussing at least three treaties. One is to create uniform legal frameworks for prosecuting terrorists who seek to use nuclear materials, another is to develop uniformly effective security procedures for safeguarding nuclear materials, and the third is the Fissile Material Cut-off Treaty. It is likely that these issues are far more important and could have much greater consequences than some of the actions that might be taken to thwart nuclear weapons development in Iran or North Korea. Nuclear policy priorities need to emphasize non-state weapons proliferation at least at the same level as state-centered weapons proliferation.
In the non-government sector, non-state weapons proliferation also should be as central in public forums, the press, blogs, general discourse and academic discussions as the continuing crises in North Korea and in Iran.
The fact that the Federal Emergency Management Agency (FEMA) and the Department of Homeland Security are engaging in detailed analyses of emergency responses to a Hiroshima-type bomb detonation in central Washington D.C. means that they are taking that possibility seriously. While the Gulbuddin scenario chose Las Vegas as a symbolic target, another team of jihadists might choose to focus on our nation’s capital.
Today, the news media continually reports about the potential for North Korea to attack the United States with nuclear-tipped intercontinental ballistic missiles. But an attack using a crate holding a lead-shielded, twelve-foot long artillery gun, delivered by sea to one of America’s busiest container ports, such as ports in New Jersey, New York, or California, is a more likely mode of attack and would be equally effective and deadly.
“Nuclear Fuel Memos Expose Wary Dance With Pakistan,” New York Times, November 30, 2010.
Nasir Bin Hamad Al-Fahd, “A Treatise on the Legal Status of Using Weapons of Mass Destruction Against Infidels,” 2003, available at http://ahlussunnahpublicaties.files.wordpress.com/2013/04/42288104-nasir-al-fahd-the-ruling-on-using-weapons-of-mass-destruction-against-the-infidels.pdf
Paul Bracken, “The Second Nuclear Age: Strategy, Danger, and the New Power Politics” (Times Books, 2012)
See FAS’s world nuclear forces chart: /issues/nuclear-weapons/status-world-nuclear-forces/ . This estimate shows that Pakistan has 120-199 nuclear weapons, and the UK and France have about 225-300. But the Pakistani nuclear weapons program is estimated to be growing while the UK and France have stopped producing new nuclear weapons.
See the video at http://www.downvids.net/light-engineering-in-darra-adam-khel-pakistan-amazig–472252.htm, accessed on May 14, 2014. This YouTube video shows the light manufacturing equipment in Darra Adam Khel with capacity to manufacture a Hiroshima firing unit.
For example, the profile by Michael Crowley, “Our Man in Kabul?” New Republic, March 9, 2010, http://www.newrepublic.com/article/politics/our-man-kabul
Belfer Center study is available at http://belfercenter.ksg.harvard.edu/publication/21087/usrussia_joint_threat_assessment_of_nuclear_terrorism.html
John McPhee, The Curve of Binding Energy (Farrar, Straus and Giroux, New York, 1973) “He (Ted Taylor) did say he thought it was already too late to prevent the making of a few bombs (by terrorists), here and there, now and then. Society would just have to take that, and go on. None of this was said with the least trace of cynicism or despair.” (p. 196)
Matthew L. Wald and William J. Broad, “Security Questions are Raised by Break-In at a Nuclear Site,” New York Times, August 7, 2012, http://www.nytimes.com/2012/08/08/us/pacifists-who-broke-into-nuclear-weapon-facility-due-in-court.html and see the following website for the image the protestors made: http://cdn.knoxblogs.com/atomiccity/wp-content/uploads/sites/11/2013/07/heumf-blood.jpg
National Capital Region Key Response Planning Factors for the Aftermath of Nuclear Terrorim – November 2011 – FEMA, Homeland Security and Lawrence Livermore National Laboratory, available at /irp/agency/dhs/fema/ncr.pdf
Edward A. Friedman is Professor Emeritus of Technology Management at Stevens Institute of Technology in Hoboken, N.J. He holds a B.S. in Physics from MIT and a Ph.D. in Physics from Columbia University. He was director of a USAID program to develop an indigenous college of engineering in Afghanistan (1970-73) when Gulbuddin Hekmatyar was arrested for murder of a political rival at Kabul University. Dr. Friedman was a founder and senior vice president of the Afghanistan Relief Committee (1979-1995). In 2012 he developed and taught a graduate course on Nuclear Weapons in International Relations as an Adjunct Professor at The John C. Whitehead School of Diplomacy and International Relations at Seton Hall University.
Roger K. Lewis is an Architect and Planner. He has been a long-term columnist for the Washington Post’s “Shaping the City.” He is Planning and Preservation Trustee for the National Children’s Museum and President and Director of the Peace Corps Commemorative Foundation. His book, “Architect? A Candid Guide to the Profession” is known as the best basic introduction to the profession. He is Professor Emeritus of Architecture at the University of Maryland School of Architecture.
A Conversation with Nobel Laureate Dr. Jack Steinberger
On January 27, 2014, I had the privilege and pleasure of meeting with Dr. Jack Steinberger at CERN, the European Organization for Nuclear Research, in Geneva, Switzerland. In a wide-ranging conversation, we discussed nuclear disarmament, nonproliferation, particle physics, great scientific achievements, and solar thermal power plants. Here, I give a summary of the discussion with Dr. Steinberger, a Nobel physics laureate, who serves on the FAS Board of Sponsors and has been an FAS member for decades.
Dr. Steinberger shared the Nobel Prize in 1988 with Leon Lederman and Melvin Schwartz “for the neutrino beam method and the demonstration of the doublet structure of the leptons through the discovery of the muon neutrino.” Dr. Steinberger has worked at CERN since 1968. CERN is celebrating its 60th anniversary this year and is an outstanding exemplar of multinational cooperation in science. Thousands of researchers from around the world have made use of CERN’s particle accelerators and detectors. Notably, in 2012, two teams of scientists at CERN found evidence for the Higgs boson, which helps explain the origin of mass for many subatomic particles. While Dr. Steinberger was not part of these teams, he helped pioneer the use of many innovative particle detection methods such as the bubble chamber in the 1950s. Soon after he arrived at CERN, he led efforts to use methods that recorded much larger samples of events of particle interactions; this was a necessary step along the way to allow discovery of elusive particles such as the Higgs boson.
In addition to his significant path-breaking contributions to physics, he has worked on issues of nuclear disarmament which are discussed in the book A Nuclear-Weapon-Free World: Desirable? Feasible?, (was edited by him, Bhalchandra Udgaonkar, and Joseph Rotblat). The book had recently reached its 20th anniversary when I talked to Dr. Steinberger. I had bought a copy soon after it was published in 1993, when I was a graduate student in physics and was considering a possible career in nuclear arms control. That book contains chapters by many of the major thinkers on nuclear issues including Richard Garwin, Carl Kaysen, Robert McNamara, Marvin Miller, Jack Ruina, Theodore Taylor, and several others. Some of these thinkers were or are affiliated with FAS.
While I do not intend to review the book here, let me highlight two ideas out of several insightful ones. First, the chapter by Joseph Rotblat, the long-serving head of the Pugwash Conferences, on “Societal Verification,” outlined a program for citizen reporting about attempted violations of a nuclear disarmament treaty. He believed that it was “the right and duty” for citizens to play this role. Asserting that technological verification alone is not sufficient to provide confidence that nuclear arms production is not happening, he urged that the active involvement of citizens become a central pillar of any future disarmament treaty. (Please see the article on Citizen Sensor in this issue of the PIR that explores a method of how to apply societal verification.)
The second concept that is worth highlighting is minimal deterrence. Nuclear deterrence, whether minimal or otherwise, has held back the cause of nuclear disarmament, as argued in a chapter by Dr. Steinberger, Essam Galal, and Mikhail Milstein. They point out, “Proponents of the policy of nuclear deterrence habitually proclaim its inherent stability… But the recent political changes in the Soviet Union [the authors were writing in 1993] have brought the problem of long-term stability in the control of nuclear arsenals sharply into focus. … This development demonstrates a fundamental flaw in present nuclear thinking: the premise that the world will forever be controllable by a small, static, group of powers. The world has not been, is not, and will not be static.”
Having laid bare this instability, they explain that proponents of a nuclear-weapon-free world also foresee that minimal deterrence will “encourage proliferation” because nations without nuclear weapons would argue that if minimal deterrence appears to strengthen security for the nuclear-armed nations, then why shouldn’t the non-nuclear weapon states have these weapons. After examining various levels for minimum nuclear deterrence, the authors conclude that any level poses a catastrophic risk because it would not “eliminate the nuclear threat.”
While Dr. Steinberger demurred that he has not actively researched nuclear arms control issues for almost 20 years, he is following the current nuclear political debates. He expressed concern that President Barack Obama “has said that he would lead toward nuclear disarmament but he hasn’t.” Dr. Steinberger emphasized that clinging to nuclear deterrence is “a roadblock” to disarmament and that “New START is too slow.”
On Iran, he said that if he were an Iranian nuclear scientist, he would want Iran to develop nuclear bombs given the threats that Iran faces. He underscored that if the United States stopped threatening Iran and pushed for global nuclear disarmament, real progress can be made in halting Iran’s drive for the latent capability to make nuclear weapons. He also believes that European governments need to decide to “get rid of U.S. nuclear weapons based in Europe.”

Another major interest of his is renewable energy that can provide reliable, around the clock electrical power. In particular, he has repeatedly spoken out in favor of solar thermal power. A few solar thermal plants have recently begun to show that they can generate electricity reliability even during the night or when clouds block the sun. Thus, they would provide “baseload” electricity. For example, the Gemasolar Thermosolar Plant in Fuentes de Andalucia, Spain, has an electrical power of 19.9 MW and uses a “battery” to generate power. The battery is a molten salt energy storage system that consists of a mixture of 60 percent potassium nitrate and 40 percent sodium nitrate. This mixture can retain 99 percent of the thermal energy for up to 24 hours. More than 2,000 specially designed mirrors, or “heliostats,” arrayed 360 degrees around a central tower, reflect sunlight onto the top part of the tower where the molten salt is heated up. The heated salt is then directed to a heat exchanger that turns liquid water into steam, which then spins a turbine coupled to an electrical generator.
Dr. Steinberger urges much faster accelerated development and deployment of these types of solar thermal plants because he is concerned that within the next 60 years the world will run out of relatively easy access to fossil fuels. He is not opposed to nuclear energy, but believes that the world will need greater use of true renewable energy sources.
Turning to the future of the Federation of American Scientists, Dr. Steinberger supports FAS because he values “getting scientists working together,” but he realizes that this is “hard to do” because it is difficult “to make progress in understanding issues” that involve complex politics. Many scientists can be turned off by messy politics and prefer to stick within their comfort zones of scientific research. Nonetheless, Dr. Steinberger urges FAS to get scientists to perform the research and analysis necessary to advance progress toward nuclear disarmament and to solve other challenging problems such as providing reliable renewable energy to the world.
Prospects for a Middle East Regional Safeguards Organization
Recent efforts to convene a conference on a Middle East zone free of weapons of mass destruction (WMDs) have stalled, reflecting the political difficulties in working towards that goal in the region. Pursuing a regional safeguards organization for nuclear energy programs in the Middle East could be an easier diplomatic and strategic alternative, given the growing energy demands by some of the countries in the region. In addition, if established, the institutions and fora for nuclear discussions could facilitate the eventual establishment of a Middle East zone free of WMDs. For example, the Brazilian-Argentine Agency for Accounting and Control of Nuclear Materials (ABACC) performed a crucial function in helping Argentina and Brazil verify one another’s non-nuclear weapon status and enact policies to officially renounce any interest in nuclear weapons. Given the resurgent interest in the pursuit of nuclear energy in the Middle East coupled with concerns of a nuclear-armed Iran, the phased establishment of a regional organization similar to ABACC could (1) prevent further nuclear proliferation in the region and (2) pave the way for the establishment of a Middle East zone free of WMDs.
ABACC is a relatively unknown non-proliferation success story within the foreign policy and international security expert community. Currently, this community is concerned about the prospects of a nuclear-armed Iran, especially since fears abound that should Iran’s suspected nuclear weapons program become fully realized, it is quite possible that a nuclear cascade in the Middle East would ensue. Important lessons learned from the creation and subsequent implementation of ABACC – notably (1) the importance of sustained dialogue, (2) confidence and trust building, and (3) political leadership/political will – could be useful to assist in the creation of a regional safeguards organization for nuclear energy programs in the Middle East.
ABACC was established under an agreement reached between Argentina and Brazil to ensure the exclusively peaceful uses of nuclear energy in 1991. It is the world’s only bi-national safeguards agency responsible for verifying that the nuclear materials existing in both countries are being used exclusively for peaceful purposes. It is vested with the power to designate inspectors, carry out and evaluate inspections, and take legal action. It is made up of an equal number of representatives from Argentina and Brazil. Today, nuclear physicists from both countries continue to conduct mutual inspections at nuclear facilities on a cross-national basis through ABACC. These inspectors render their services to ABACC only during the periods encompassed by the missions for which they are appointed. Brazilian inspectors verify the Argentine facilities, and Argentine inspectors verify the Brazilian facilities. The inspections include verification of inventories of nuclear materials, unannounced and short-notice inspections, and inspections carried out along with the International Atomic Energy Agency (IAEA). It is important to stress that their work is undertaken with the full support of both governments.
Skeptics may argue that ABACC might not be the best model to use as a comparison for the Middle East region for three important reasons. First, tensions are high and deep-rooted feelings of suspicion and mistrust are currently rampant in the region. Second, existing indigenous nuclear capabilities are very limited in the region. Third, within the states across the region, sustained dialogue is overshadowed by veiled threats, confidence and trust building measures are simply not an option, and due to the inherent distrust, the political will is certainly not there. However, the lessons learned from the creation and subsequent sustained success of ABACC provide a starting point for assessing a regional safeguards organization for nuclear energy programs in the Middle East.
Options for a Regional Safeguards Organization in the Middle East
No two regions in the world can be deemed geographically or culturally alike. Equally, no two regions can be expected to have identical characteristics politically, militarily, or economically. Therefore, if a mutual inspections and safeguards verification system works well in one region, there is no guarantee that it will work just as well in another region. The Middle East has more dissimilarities than similarities with the Southern Cone. In the Southern Cone, there is a shared culture, shared religion, shared history, shared interests, and in all but one country, a shared language. In the Middle East, however, there are extensive ethnic divides including: Persians, Jews, Kurds, Druze, Turkic, Azeri, Baloch, Arabs, and others. The region has seen armed conflicts amongst various groups and there are long standing divisions between Shiites and Sunnis and tensions among other religious lines. Arguably, one of the only things the people of the Middle East share with one another is the geographical location. Cultures, languages, religions, and interests in the region are as widespread and disparate as the peoples’ political beliefs.
Yet, issues such as the verification procedures and the structure of various regional nuclear non-proliferation agreements exhibit similarities. The scope of these provisions, however, is usually a reflection upon the expectations and intentions of the parties involved. In the case of ABACC, there was shared and mutual interest from both Argentina and Brazil to create a mutual inspections and safeguards verification system, which developed over time. Even though the nuclear rapprochement of both countries can be traced back to the late 1960s/early 1970s, the idea of both countries participating in bilateral inspections was unfathomable back then. It took years of sustained dialogue, trust building, creation of democracies, and, perhaps most importantly, having political leaders that shared the political will to turn these desires into actual policy. Furthermore, the willingness to promote a collaborative nuclear partnership did not come from both countries at the same time. In fact, it was Argentina that proposed a partnership; Argentina’s earliest official statement on nuclear cooperation was prepared in 1978 by the Foreign Ministry’s policy planning staff, which led to the May 1980 joint nuclear accord. Five years after the 1980 joint nuclear accord was signed – by which time, both countries had become democracies (Argentina in 1983; Brazil in 1985) – both the Argentine and Brazilian governments agreed to create the Joint Working Group on Nuclear Affairs (JWG) to discuss nuclear issues, which, by 1988, had been institutionalized as the Permanent Committee on Nuclear Affairs (PCNA).1 The PCNA not only furthered nuclear negotiations, but also facilitated the presidential and technical nuclear installation visits – important confidence and trust building steps that led to the creation of ABACC.
It is not clear to what extent the countries in the Middle East could develop a shared and mutual interest to create a regional safeguards organization in the way that Argentina and Brazil did. The last minute cancellation of the December 2012 conference on a Middle East zone free of WMDs would indicate that neither the timing nor the political will exists at the present moment (no official reason was given for the cancellation). However, the region’s resurgent interest in the pursuit of nuclear energy in the Middle East could motivate such an arrangement. In December 2006, the six nations of the Gulf Cooperation Council (GCC) – Bahrain, Kuwait, Oman, Qatar, Saudi Arabia, and the UAE – announced their intention to explore a joint nuclear development program.2 In November 2012, the GCC announced that its member states would set up a center to monitor nuclear radiation and to act as a platform to use nuclear energy for peaceful purposes and avoid radiation hazards.3 If realized, it could form a regional organization similar to ABACC with the following three phase process: (1) the establishment of the GCC’s joint nuclear development program including the formation of an institution similar to ABACC with an inspection mandate, (2) extending the institutional arrangement in the region, and (3) bringing in the outliers: Iran and Israel.
The first phase would include the establishment of the GCC’s joint nuclear development program, which would manage the peaceful uses of nuclear energy. It is not clear (a) how long it would take for such an ambition to be realized, or (b) how feasible this might be given that none of the council’s member states has a significant nuclear infrastructure. All member states lack power and research reactors, and none of the member states has all the necessary components of the nuclear fuel cycle. In addition, most of the GCC members lack trained personnel, a nuclear regulatory structure, and a record of transparency and non-proliferation credentials.4 While the program was announced in December 2009, it remains in the early planning stages as the GCC member states commissioned a study to assess the feasibility of developing a joint nuclear energy program. IAEA officials are involved with the feasibility study and it has been reported that the GCC members would like the agency to have continued involvement in and regulation over the project.5
Since the commissioning of the feasibility study, some of the GCC members have made efforts to set up a nuclear infrastructure with technical help from the United States and other countries. For example, the UAE, Saudi Arabia, and Bahrain signed memorandums of understanding (MOU) on nuclear energy cooperation with the United States in 2008.6 Kuwait signed an MOU with the United States on nuclear safeguards and other non-proliferation topics in June 2010.7 These efforts may help the GCC countries establish a nuclear infrastructure so that the joint nuclear development program can be realized.
The next phase in the process would be to extend this program to energy-hungry countries in the region, including Jordan, Egypt, Lebanon, Syria, Turkey, and Yemen. One option might be to build joint power stations with the assistance of third parties between bordering GCC states and the energy-hungry states, like Oman and Yemen, Saudi Arabia and Jordan. In the case of ABACC, Argentina and Brazil independently pursued an autonomous nuclear fuel cycle. Their first nuclear accord – the May 1980 agreement – helped to establish a common nuclear policy, which was defined as “cooperation in the use of nuclear energy” and the “development and application of the peaceful uses of nuclear energy.” This accord called for bilateral technical collaboration and joint ventures for the production of reactor components and fuel elements, with the aim of minimizing dependence on western supplier countries.8 It was not, however, an arms control agreement, but a call for technical-scientific collaboration in nuclear research. Even though the agreement did not offer an inspection regime, it offered verbal assurances and some limited technical cooperation between their respective atomic energy authorities. It was through this agreement that both sides took the first tentative steps towards a preliminary mutual inspection and verification regime since it was the first of many joint nuclear cooperation agreements. As a result of the agreement, Argentina leased uranium concentrate to Brazil and sold zircalloy tubing for nuclear fuel elements. In exchange, Brazil supplied Argentina with a portion of the pressure vessel for its Atucha II nuclear power generator. Even though the agreement did not put an end to the nuclear technology race, it was the first major step towards a comprehensive nuclear regime based on proliferation restraint and mutual safeguards. The GCC countries extending their shared nuclear program resources to the energy-hungry countries in the region would therefore mark an important second phase.
The final phase would be to bring in the outliers in the region, notably Iran and Israel. This would undoubtedly be the hardest phase to conquer politically. It is no secret how the two governments publically perceive one another. However, contrary to the other Middle Eastern states, Israel and Iran are united by being the region’s only non-Arab governments although each has Arabs living in their countries. Yet, neither country share the same culture, language, history, identity, religion, or politics, so bringing them both into the regional safeguards organization for nuclear energy programs will be incredibly difficult. None of the three key lessons learned from the creation of ABACC can be applied to Iran and Israel. First, the concept of dialogue between these two states is shrouded in belligerent threats. Second, confidence and trust building measures are notably absent. Third, the political will of both countries is to continue to engage in war-mongering. Interestingly though, both countries are keen to participate in the eventual establishment of a Middle East zone free of WMDs, yet the inherent political differences across the countries in the region are creating a stumbling block. While the previous two phases are no easy feat- given the inherent lack of a significant nuclear infrastructure- if these technical barriers are overcome through the GCC’s vast amount of amalgamated financial resources, Iran and Israel may be able to set aside their political differences to participate in this regional organization.
Verification, Safeguards, and Enforcement
Having laid the groundwork for the three-phased approach in creating a regional safeguards organization for nuclear energy programs in the Middle East, it is important to address verification, safeguards, and enforcement issues. The overall set of verification provisions should enable the inspectors from the regional organization to have suitable access to carry out their job effectively during all types of inspections (i.e., ad hoc, routine, and challenge). During the first high-level technical visit of the Brazilian delegation to the Argentine unsafeguarded Pilcaniyeu pilot uranium enrichment facility in July 1987, the Brazilian delegation asked the Argentines many sensitive questions. To their surprise, the Argentines answered all their questions, showed them the entire facility, and provided information on top-secret sites. This was a very important step in confidence and trust building and accounts for ABACC’s continuing success. It is therefore important that members of a regional safeguards organization in the Middle East be fully transparent and provide regular and detailed information on the operations in their facilities.
Regarding the actual inspections themselves, in the case of ABACC, inspections are carried out by both the IAEA and ABACC (even though there is no obligation for both agencies to work together in any given inspection). The facilities and the material under safeguards are the same for both agencies. All inspections are previously coordinated by the agencies. Each one of the agencies has the right to trigger inspections (short notice and announced inspections) on its own while informing the other agency. The agencies share equipment such as cameras and counters. Even though the inspections are carried out jointly, the conclusions of the inspections are independent. Therefore, it would be expected that the regional safeguards organization in the Middle East would work in conjunction with the IAEA, similar to ABACC.
Finally, in relation to enforcement issues, the Middle East regional organization would need to have the authority and the capacity to effectively sanction the violators. In this regard, it is difficult to draw from the ABACC experience since both countries have been open and transparent with one another with no reported violations from either side. In fact, in the creation of ABACC, non-compliance was not discussed given that the two nations were embarking on confidence and trust building measures; if the issue of non-compliance were to be raised, it may have conveyed feelings of mistrust. Therefore, given the lack of trust that already exists across the countries in the Middle East, it would be pertinent to avoid discussing issues of non-compliance at an early stage and instead address them (if necessary), once effective confidence and trust building measures are in place. However, if there are issues of non-compliance that the regional organization is unable to overcome, the IAEA Board of Governors could discuss the issue with the Director General. If non-compliance persists, the issue can then be reported to the United Nations Security Council.
Benefits and Limitations for a Regional Safeguards Organization in the Middle East
There would be many benefits to consider should the creation of a regional safeguards organization for nuclear energy programs in the Middle East be realized. Equally, however, there are important limitations to consider.
Benefits
The first benefit would be the development of confidence and trust building, which would be an incremental step in easing suspicions and diffusing tensions in the region. In the case of ABACC, each of the ten nuclear cooperation agreements signed by Argentina and Brazil facilitated closer nuclear cooperation and instilled greater confidence between the two nations. Earlier declarations stressed the decision to increase reciprocal technical visits and consultations; today Argentina and Brazil continue to share information on nuclear technological developments, radiological security and protection. They also called for strengthening the coordination of policy positions before international fora to defend common interests and protect the region from the risk of nuclear weapons. The high-level reciprocal presidential and technical visits to unsafeguarded and sensitive nuclear facilities and the subsequent nuclear accords played a decisive role in assuring each other and the international community that their nuclear programs were of a peaceful nature. All the presidential visits were followed by visits of specialized technical personnel, which represented another step towards nuclear transparency and subsequent trust building.
The GCC countries could adopt nuclear cooperation agreements similar to Argentina and Brazil using the same common elements. The GCC, through INFCIRC/225 (which strengthens the security of nuclear materials through physical protection measures), could promote robust nuclear physical security measures at sites in the region as a step towards confidence and trust building.
A second benefit to consider includes the Middle Eastern countries’ greater involvement in the nuclear non-proliferation regime. In the case of Argentina and Brazil, both nations were initially hostile to the international nuclear non-proliferation regime; notably after the creation of ABACC, they both became fully integrated within the non-proliferation regime by signing various non-proliferation agreements. Soon after ABACC was created, Argentina, Brazil, and ABACC signed the Quadripartite Agreement with the IAEA to establish coordination between it and ABACC on full-scope safeguards (which means safeguards on all declared nuclear facilities and materials). Their bilateral cooperation and subsequent agreement with the IAEA made it possible for Argentina and Brazil to reconsider their opposition to existing nuclear non-proliferation treaties. By the end of the decade, both countries had ratified the Tlatelolco Treaty (the South American and Caribbean Nuclear Weapon Free Zone), the Nuclear Non-Proliferation Treaty and then became members of the Nuclear Suppliers Group. Even though Argentina always took the lead in signing these agreements first, Brazil eventually signed, indicating a willingness to continue their nuclear partnership.
Not all the countries in the Middle East are parties to various nuclear non-proliferation agreements, which is a similar situation that Argentina and Brazil found themselves in, prior to the creation of ABACC. Middle Eastern countries are all NPT signatories (with the exception of Israel), and they all have signed a full-scope safeguards agreement with the IAEA, except for Qatar. However, only a handful has either a modified Small Quantities Protocol (SQP) or an Additional Protocol (AP) in force.9 Based on the ABACC experience, it could be argued that once a regional safeguards organization has been created in the Middle East, all parties might become further integrated into the nuclear non-proliferation regime and potentially agree to a Middle East zone free of WMDs. However, neither Argentina nor Brazil has signed the AP, which calls into question their position within the nuclear non-proliferation regime (even though ABACC inspections cover what the AP stipulates, just without the IAEA). This begs the question whether the Middle Eastern states would sign an AP if such an organization were created. One way to alleviate this concern might be to ensure that the GCC members sign an AP before its joint nuclear program is developed, which might be difficult to achieve. Third party countries helping the GCC states with their nuclear infrastructure may be able to entice/influence the GCC states to sign an AP before construction of power plants begins. Then, insofar as Phase 2 is concerned, the energy-hungry countries can only receive help if they too have signed an AP.
The final benefit to the creation of a regional safeguards organization in the Middle East would include further cooperation in other areas, notably economic, technical, and energy provision. The next phase would be for the GCC to help the energy-hungry countries acquire energy through the joint nuclear energy program discussed above. In the case of ABACC, the nuclear agreements signed between Argentina and Brazil promoted the peaceful uses of nuclear energy and encouraged joint nuclear research and development plans.
Limitations
Given the inherent political problems and internal barriers within the Middle Eastern countries, it is difficult to assess the feasibility of a “neighbors watching neighbors” organization being created and even sustained in the region. One of the most obvious internal barriers is the existence of conflict, distrust, deep-rooted enmity, and overt hostility in the region. Argentina and Brazil’s relationship was previously marked by a strong rivalry since they were the two major industrial, economic, and military powers in the Southern Cone. Their individual attempt to acquire the nuclear fuel cycle was viewed as yet another competition between the two longstanding rivals. However, unlike states in the Middle East, their relationship was a competitive rivalry, and not an enmity. There was no real cause for armed conflict between the two states; instead, they were both striving for technological and indigenous superiority. However, in the Middle East there are severe regional conflicts, with some countries not recognizing the existence of other countries, and some countries threatening to destroy other countries. This climate does not make the idea of a regional safeguards organization where trust is key to its success conceivable. It would, in fact, strongly suggest otherwise.
A further limitation to consider might be the existence of more nuclear fuel cycles in the region. Currently, there are fears that should Iran’s suspected nuclear weapons program become fully realized, it is quite possible that a nuclear cascade in the Middle East would ensue. However, should the phased approach outlined be conceived, the GCC members states would not need an entire nuclear fuel cycle, thereby alleviating the fear of a greater number of nuclear fuel cycles in the region. Finally, the prospects of sensitive technology transfer from countries within the regional organization (e.g., Iran to Syria, Lebanon, Iraq) would also need to be considered.
Conclusion
The political and technical realities of the Middle East suggest that the likelihood of creating such a regional safeguards model is far from being accomplished, at least in the immediate future. That is not to say that this issue should not be addressed. Nonetheless, discussing a regional safeguards organization in the Middle East is to be encouraged because if it is created, it could very well lead to the overall goal of creating a further WMD-free zone in the world. ABACC is an underrated success story, but importantly, it took Argentina and Brazil a few decades before ABACC could be realized. Furthermore, once both countries became democracies, the transition to a nuclear rapprochement became a lot smoother. The Middle Eastern countries should consider starting the conversation about a joint nuclear technical program to be used exclusively for peaceful purposes given that the current approach of trying to convene a conference on a Middle East zone free WMDs has failed for four decades. Furthermore, there has yet to be a new initiative offered to this persistent problem, and, as such, creativity is required, whatever the obstacles it might face.
Dr. Sara Z. Kutchesfahani is a Senior Research Associate at the Center for International Trade & Security at the University of Georgia (CITS/UGA), where she works on nuclear security culture projects. In addition, she teaches a graduate class on “Nuclear History and Security Policy” at UGA’s School of Public and International Affairs. She came to the Center from the Nuclear Engineering and Nonproliferation Division at Los Alamos National Laboratory (LANL), where she was the only political science research associate among a pool of 440 at the laboratory. At LANL, her work focused on nuclear non-proliferation policy-related research projects, with an emphasis on international safeguards. From LANL, she also taught a graduate distance-learning education course, titled “Nuclear Safeguards & Security Policy,” at the New Mexico Institute of Mining and Technology, a premier science and engineering research university.
She has worked on nuclear non-proliferation policy issues for most of the past decade holding research positions at the International Institute for Strategic Studies (London), the European Union Institute for Security Studies (Paris), and the RAND Corporation (Washington). She holds a Ph.D. in Political Science from University College London. She is the author of the recently published book: Politics and the Bomb: The Role of Experts in the Creation of Cooperative Nuclear Non-Proliferation Agreements (Routledge/Taylor & Francis, 2013).
50 Years Later “Dr. Strangelove” Remains a Must-See Film and Humorous Reminder of Our Civilization’s Fragility
Fifty years ago on January 30th, “Dr. Strangelove: Or How I Learned to Stop Worrying And Love the Bomb,” a seminal political-military satire and dark comedic film premiered. Based on Peter George’s novel Red Alert, the film gave us some of the most outrageously humorous and simultaneously satirical dialog in the history of the silver screen. For example, Peter Sellers as the President of the United States, “Gentleman, you cannot fight in here. This is the War Room.” Director/producer Stanley Kubrick produced a masterpiece that not only entertained viewers but turned out to be incredibly predictive about U.S.-Soviet Cold War nuclear policies, strategies, and outcomes.
The U.S. Air Force refused to cooperate with Kubrick and his production company because they felt that the premise of an accidental nuclear war being launched by a U.S. general wasn’t credible. In fact, on December 9, 1950, General Douglas MacArthur requested authorization to use atomic bombs against 26 targets in China after the People’s Liberation Army entered the Korean War. The Soviet Union had tested their first A-bomb the year before, so it is certainly possible that MacArthur’s use of such weapons could have triggered a nuclear conflict. In terms of nuclear accidents or “broken arrows” as the U.S. military refers to such events, there have been dozens of incidents including a January 17, 1966 Air Force crash involving nuclear warheads that contaminated thousands of acres in Palomares, Spain (although thankfully fail-safe switches on the damaged atomic bombs prevented any nuclear explosions). A computer generated false alert (one of countless false warnings over the years), on November 9, 1979 almost triggered nuclear Armageddon when President Jimmy Carter’s National Security Adviser Zbigniew Brzezinski was informed at 3 a.m. that 2,200 Soviet missiles were within minutes of impacting on the U.S. mainland. It turned out to be a training exercise loaded inadvertently into SAC’s early warning computer system.
Actor George C. Scott played a Strategic Air Command (SAC) general named Buck Turgidson not unlike real life Chief of Naval Operations Admiral Thomas Moorer. In 1969, Moorer proposed salvaging the war by targeting North Vietnam with two nuclear bombs – a proposal allegedly lobbied for by President Nixon’s Secretary of State Dr. Henry Kissinger. After it is discovered that Sterling Hayden’s character, General Jack D. Ripper has on his own authority (a credible possibility until coded locks were installed on most U.S. nuclear weapons later in the 1960s and on submarine-launched nuclear missiles in the late 1990s)1 ordered an all-out nuclear attack on Russia by his squadrons of B-52 bombers (an aircraft the United States still relies on after sixty years of deployment), General Turgidson pleads with Peter Sellers’ character President Merkin Muffley to consider, “…if on the other hand, we were to immediately launch an all-out and coordinated (nuclear) attack on all their airfields and missile bases, we’d stand a damn good chance of catching them with their pants down…I’m not saying we wouldn’t get our hair mussed, but I do say no more than 10-20 million (Americans) killed, tops, depending on the breaks.” Ironically nuclear war advocates Colin Gray and Keith Payne literally quoted Turgidson’s casualty figures verbatim when in 1980 they advised then presidential candidate Ronald Reagan that America could fight and win such a war against the Soviet Union.2
But Peter Sellers, who incredibly played three roles in the film, excelled as the title character Dr. Strangelove, an amalgam of NASA’s Werner von Braun, who built Nazi V-2 rockets by turning his back when SS soldiers worked thousands of Jewish conscripts to death and was part of Operation Paperclip, a group of German scientists amnestied by the United States (and the Soviet Union handpicked its own Nazi brainpower) after the war to help build Cold War weapons, Edward Teller, who worked on the hydrogen bomb, helped found Lawrence Livermore National Laboratory, was an Atoms for Peace enthusiast and advocated for the Strategic Defense Initiative (SDI- the “Star Wars” missile shield), and Herman Kahn, who worked at RAND, then founded the Hudson Institute, and wrote the seminal “thinking about the unthinkable” book On Thermonuclear War, published in 1960.
Deep in the bowels of the War Room, Dr. Strangelove responded to the Russian ambassador’s fearful notification that even if only one of the U.S. nuclear bombs struck Russia, the result would be the triggering of a doomsday machine. Sellers’ character admonished the ambassador, “But the whole point of a doomsday machine is lost if you keep it a secret. Why didn’t you tell the world, aye?” Coincidentally again, truth followed fiction according to David Hoffman’s Pulitzer Prize-winning 2009 work The Dead Hand, as in November 1984, the Soviets did indeed construct a partially automated retaliatory nuclear strike system called Perimetr and tested it. Stranger still, Colonel Valery Yarynich of the Soviet Union’s Strategic Rocket Forces pointed out to his superiors that it was irrational and inconsistent with deterrence theory for them to go out of their way to hide Perimetr’s existence from U.S. leaders. This occurred during the height of the Cold War when the United States possessed 11,000 strategic nuclear warheads to the Soviet’s 9,900. In total, including tactical and intermediate-range bombs, the United States led 20,924 to 19,774 warheads.
When General Turgidson expressed skepticism that the Russians had the brains to build such a doomsday machine, Dr. Strangelove strongly disagreed, noting that such a system was entirely feasible. “The technology required is even within the means of the smallest nuclear power. It requires only the will to do so….It is remarkably simple to [build]. When you merely wish to bury bombs, there’s no limit to the size. After that they are connected to a gigantic complex of computers.” This echoed the real life February 1955 radio broadcast of German Nobel Laureate Otto Hahn, who first split the uranium atom in the late 1930s. Hahn warned that the detonation of as few as ten cobalt bombs, each the size of a naval vessel, would cause all mankind to perish. In the early 1980s, astronomer Carl Sagan and other scientists3 examined and subsequently built-on analyses of the last few decades via the TTAPS study. They concluded that as few as 100-200 nuclear warheads exploding within the span of a few hours could credibly trigger a nuclear winter, plunging temperatures dramatically in the northern hemisphere as tremendous nuclear firestorms block the sun’s rays, leading to wholesale starvation, exposure, and the radiation-borne deaths of billions of people worldwide.4
Dr. Strangelove was originally scheduled for its first screening on Friday, November 22, 1963. The assassination of President Kennedy earlier that day caused the producers to delay the film’s release date by several weeks. Time was needed to not only heal the nation’s gaping wound but to edit the film to remove some objectionable material relating to the murder of the president. Coincidental references by the hydrogen bomb-riding Slim Pickens character Major T.J. “King” Kong that the survival kits carried by each bomber crewman could help provide them a pretty good time in Dallas was redubbed to “Vegas.” A concluding sequence of a free-for-all pie fight in the War Room was edited out for stylistic reasons and also removed George C. Scott’s objectionable dialogue that, “Our commander-in-chief has been struck down in the prime of his life.” Not so coincidentally, perhaps, JFK’s murder and Nikita Khrushchev’s Politburo ouster in 1964 (the year of the film’s actual release), ended a post-Cuban Missile Crisis-Almost Armageddon (October 1962) apotheosis by both leaders to prevent another nuclear crisis. They cooperated in an earnest effort to prevent another visit to the brink of extinction by working to end the Cold War and reverse the nuclear arms race in favor of peaceful coexistence. The results of their labors cannot be underestimated—the Hot Line Agreement and the Limited Test Ban Treaty.
Today in 2014, “Dr. Strangelove,” along with other antiwar films like “Fail Safe,” “The Sum of All Fears,” “On the Beach,” “War Games,” and “Olympus Has Fallen,” remind us that all of humanity must acknowledge that nuclear war is not a blast from the past or an obsolete fear from a remote period in history. It is a real life current and future threat to our global civilization – indeed to our species’ continued existence on this planet.
But has anyone studied the actual possibilities of a nuclear Armageddon? Aside from Dr. Strangelove’s analysis discussing a study on nuclear war made by “the Bland Corporation” (which is obviously a reference to the real-life Rand Corporation), the answer is a definitive “yes.” According to Ike Jeane’s 1996 book Forecast and Solution: Grappling with the Nuclear, the risks of large-scale nuclear war average about 1-2 percent per year, down from a high of 2-3 percent annually during the Cold War (1945-1991). But Dr. Martin Hellman of Stanford and other analysts believe that as more decades pass since the only recorded use of nuclear weapons in combat (Hiroshima and Nagasaki in August 1945), the probability may increase to ten percent over the duration of this century.5
While President Barack Obama has called for the elimination of nuclear weapons, so too have past American leaders as diverse politically as Jimmy Carter, Ronald Reagan, and Ralph Nader. Meanwhile thousands of nuclear warheads – 90-plus percent in the hands of America and Russia – still exist in global arsenals. Both countries continue to spend tens of billions of dollars annually to update, improve, and modernize their nuclear forces. For example, U.S. submarine-launched ballistic missiles (SLBMs) have increased dramatically in accuracy from a 12 percent chance of destroying a hardened Russian missile silo to 90-98 percent effectiveness; thus giving these weapons a highly effective “kill” probability and putting pressure on Russia to launch its silo-based ballistic missiles on warning of attack. While U.S. missile “defenses” may soon include “Rods from God,” 20-30 foot long, two-foot wide tungsten cylinders fired from U.S. Air Force space-based assets, the Russians have also upgraded their aging Cold War arsenal by building dozens of new Topol-M ICBMs and Bulava SLBMs.
Substantial progress in reducing this Armageddon threat cannot be accomplished until decades-long objections by overly conservative members of Congress, the Russian Duma and both nations’ military leadership are lifted. Such multilateral, verifiable (new technologies make this relatively easy to achieve), measures include a global comprehensive nuclear test ban (laboratory sub-critical nuclear tests not excluded), and the standing down from heightened alert levels of not only Russian and American strategic and tactical nuclear weapons but those of China, France, Britain, Israel, Pakistan and India. This would transition all sides’ dangerous nuclear weapons from the physical capability of being fired in 15 minutes or less to 72 hours or longer—don’t we at least deserve three days to think about it before we destroy the world? We also need an accelerated global zero nuclear reduction agreement as well as an essential, little-mentioned but critically important move that the mainstream corporate media has rarely granted its stamp of legitimacy. This would be a unanimous United Nations demand as voiced by leaders in America and Russia, for the phase-out of all nuclear power plants, research as well as production facilities (with the exception of a handful of super-guarded medical radioisotope manufacturing and storage facilities) in the next 10-15 years.
Eliminating not just existing stocks of nuclear weapons, but also all of the 400 global nuclear power facilities is the trump card in the deck of human long-term survival. There are numerous issues including: proliferation, nuclear accidents, the long-term sequestration of tremendous amounts of deadly nuclear wastes, the economic non-competitiveness of nuclear energy, and the realization that nuclear plants are not a viable, safe or reasonable solution to global warming especially in the long term (since plutonium-239 has a half-life of an amazing duration of more than 20,000 years)! Dr. Strangelove’s circular slide rule-assisted calculation requiring humanity to survive the war by remaining in deep underground mineshaft spaces for merely a century was ergo a definite miscalculation—sorry Herr Merkwurdichliebe. 6
Five decades later, the hauntingly humorous end title lyrics and music of “Dr. Strangelove,” accompanied by actual images of awesome Cold War-era nuclear tests, serves as a read-between-the-lines warning to the human race: “We’ll meet again, don’t know where, don’t know when, but I know we’ll meet again some sunny day.” Nuclear weapons and nuclear power – indistinguishable in terms of the deadly threat to our species – must be eliminated now before it is too late. A penultimate but overwhelmingly appropriate edit of George C. Scott’s last line in the film is especially relevant here. “We must not allow a nuclear Armageddon!”
Additional Sources
Walter J. Boyne, Beyond the Wild Blue: A History of the U.S. Air Force, 1947- 1997, New York: St. Martin’s Press, 1997, p. 394.
Columbia Pictures Corporation-Sony Pictures, 40th Anniversary Edition: Dr. Strangelove. Documentary- “Inside Dr. Strangelove,” 2004.
Bruce Cumings, The Origins of the Korean War, Volume 2. Princeton University Press, 1990, pp. 749-751.
The Defense Monitor (Center for Defense Information), Vol. 15, No. 7, “Accidental Nuclear War: A Rising Risk?” by Michelle Flournoy, 1986.
The Defense Monitor (Center for Defense Information), Vol. 36, No. 3, “Primed and Ready- Special Report: Nuclear Issues,” by Bruce G. Blair, May/June 2009.
Peter Janney, Mary’s Mosaic: The CIA Conspiracy to Murder John F. Kennedy, Mary Pinchot Meyer, and Their Vision for World Peace. New York: Skyhorse Publishing, 2012, pp. 242-247; 261-263.
Premiere (Magazine), “The 100 Greatest Movie Characters of All-Time,” April 2004, p. 58.
Carl Sagan, “The Case Against SDI,” Discover, September 1985, pp. 66-75.
H. Eric Semler, et al., The Language of Nuclear War: An Intelligent Citizen’s Dictionary. New York: Harper & Row Publishers, 1987, p. 44.
Oliver Stone and Peter Kuznick, The Untold History of the United States. New York: Gallery Books-Simon & Schuster, 2012, pp. 272, 362, 540-42.
John Tierman, editor, Empty Promise: The Growing Case Against Star Wars. Boston:
Beacon Press, 1986, pp. 2-3.
Louis Weber, editor, Movie Trivia Mania. Beekman House-Crown Publishers, Inc., 1984 p. 21.
Jeffrey W. Mason is a nuclear weapons, arms control, outer space, and First Contact scholar, published author and scriptwriter for acclaimed PBS-TV documentaries who possesses two MA degrees—one in international security. He has worked for the Center for Defense Information (11 years) where he helped produce award-winning PBS-TV documentaries on child soldiers, the Hiroshima bombing, and “The Nuclear Threat at Home.” He worked for the Defense Threat Reduction Agency, the State Department, Professionals’ Coalition for Nuclear Arms Control, Congressional Research Service, Amnesty International, Clean Water Action, and the International Studies Association.
Hedging and Strategic Stability
The concept of strategic stability emerged during the Cold War, but today it is still unclear what the term exactly means and how its different interpretations influence strategic decisions. After the late 1950s, the Cold War superpowers based many of their arguments and decisions on their own understanding of strategic stability1 and it still seems to be a driving factor in the arms control negotiations of today. However, in absence of a common understanding of strategic stability, using this argument to explain certain decisions or threat perceptions linked to the different aspects of nuclear policy tend to create more confusion than clarity.
In the 2010 Nuclear Posture Review (NPR) report,2 the Obama administration used the term strategic stability as a central concept of U.S. nuclear policy vis-à-vis Russia and China. Altogether it appeared 29 times in the report, in reference to issues mostly related to nuclear weapons capabilities. In the U.S.-Russian bilateral relationship, strategic stability was associated with continued dialogue between the two states to further reduce U.S.-Russian nuclear arsenals, to limit the role of nuclear weapons in national security strategies, and to enhance transparency and confidence-building measures. At the same time, the United States pledged to sustain a safe, secure, and effective nuclear arsenal by modernizing its nuclear forces, retaining the triad, and “hedging against potential technical problems or vulnerabilities.”
On the other hand, Russia seems to use the term strategic stability in a broader context, claiming that the question of ballistic missile defense, conventional prompt global strike, and the militarization of outer space all affect strategic stability between Moscow and Washington. U.S. modernization efforts in these areas are seen as attempts to undermine the survivability of the Russian nuclear arsenal and steps to gain strategic advantage over Russia. Therefore, Moscow has been repeatedly arguing that any future arms control agreement should address all factors which affect strategic stability.3
Although these are the issues which Russia explicitly mentions in reference to strategic stability, there is another “hidden” issue which might also have a counterproductive impact on long term stability because of its potential to undermine strategic parity (which seems to be the basis of Russian interpretation of strategic stability).4 This issue is the non-deployed nuclear arsenal of the United States or the so-called “hedge.”
During the Cold War, both superpowers tried to deploy the majority of their nuclear weapons inventories. Reserve nuclear forces were small as a result of the continuous development and production of new nuclear weapons, which guaranteed the rapid exchange of the entire stockpile in a few years. The United States started to create a permanent reserve or hedge force in the early 1990s. The role of the hedge was twofold: first, to guarantee an up-build capability in case of a reemerging confrontation with Russia, and second, a technical insurance to secure against the potential failure of a warhead type or a delivery system. Despite the dissolution of the Soviet Union, during the first years of the 1990s, the United States was skeptical about the democratic transition of the previous Eastern Block and the commitment of the Russian Federation to arms control measures in general. Therefore, the Clinton administration’s 1994 NPR officially codified – for the first time – the concept of a hedge force against the uncertainties and the potential risks of the security environment.5 This concept gradually lost importance as the number of deployed strategic and non-strategic nuclear weapons kept shrinking on both sides and relations improved between Washington and Moscow. By the end of the 1990s, the main rationale for upholding the hedge force shifted towards the necessity of maintaining a back-up against technical failures. Although the nuclear arsenal was aging, a moratorium was declared on nuclear weapons testing, and several production facilities were closed. Therefore, it seemed imperative to retain fully functional nuclear warheads in reserve as an insurance policy.6
While the Clinton administration’s NPR was not too explicit about what the hedge really was, both the Bush and the Obama administrations made the specific role of the hedge clearer. Although technical considerations remained important, the Bush administration’s 2001 NPR refocused U.S. hedging policy on safeguarding against geopolitical surprises. The administration tried to abandon Cold War “threat-based” force planning and implemented a “capabilities-based” force structure which was no longer focused on Russia as an imminent threat but broadened planning against a wider range of adversaries and contingencies: to assure allies, deter aggressors, dissuade competitors and defeat enemies.7 This shift in planning meant that the force structure was designed for a post-Cold War environment with a more cooperative Russia. Therefore, the primary goal of the hedge was to provide guarantees in case this environment changed and U.S.-Russian relations significantly deteriorated.
Regardless of the main focus of the acting administration, the hedge has always served two different roles which belong to two separate institutions: the military considers the hedge a responsive force against the uncertainties of the international geopolitical environment, while the National Nuclear Security Administration (NNSA) views the hedge as a repository to safeguard the aging U.S. nuclear arsenal. These two institutions advise the administration on the required size of the hedge. Since the end of the Cold War, both the United States and Russia considerably reduced their deployed nuclear warheads, but Washington retained many of these weapons in the hedge. By now there are more non-deployed nuclear weapons than deployed nuclear weapons in its military stockpile.
According to the Federation of American Scientists,8 the United States has a military stockpile of 4,650 nuclear weapons, of which roughly 1,900 strategic nuclear weapons are deployed (this includes bomber weapons on bomber bases as deployed) and another approximately 200 non-strategic nuclear weapons are deployed in Europe. Altogether this leaves around 2,500 non-deployed nuclear weapons in reserve – approximately 2,200 strategic and 300 non-strategic.9 This hedge force10 provides the United States with a capability to increase its deployed nuclear arsenal to more than 4000 nuclear weapons within three years.11 In the long run, this capability might feed into Russian paranoia over anything that can potentially undermine strategic parity and it could become a serious roadblock on the way toward further reductions in deployed strategic as well as non-strategic nuclear arsenals.
The Obama administration has already indicated in the 2010 NPR that it is considering reductions in the nuclear hedge. According to the document, the “non-deployed stockpile currently includes more warheads than required” and the “implementation of the Stockpile Stewardship Program and the nuclear infrastructure investments” could set the ground for “major reductions” in the hedge. However, in parallel to these significant reductions, the United States “will retain the ability to ‘upload’ some nuclear warheads as a technical hedge against any future problems with U.S. delivery systems or warheads, or as a result of a fundamental deterioration of the security environment.” In line with the 2010 NPR, the 2013 Presidential Employment Guidance also envisions reductions in the deployed strategic nuclear arsenal and reaffirms the intention to reduce the hedge as well. The Pentagon report on the guidance12 discusses an “alternative approach to hedging” which would allow the United States to provide the necessary back-up capabilities “with fewer nuclear weapons.” This alternative approach puts the main emphasis on the technical role of the hedge, claiming that “a non-deployed hedge that is sized and ready to address these technical risks will also provide the United States the capability to upload additional weapons in response to geopolitical developments.” According to Hans Kristensen, Director of the Nuclear Information Project at the Federation of American Scientists, this might imply that the hedge will no longer contain two categories of warheads – as there will be enough reserve warheads to protect against technical failures and potential geopolitical challenges.13 However, at this point it is still unclear if (and when) this new approach will lead to actual force reductions in the non-deployed nuclear arsenal.
In the meantime, the United States could achieve several benefits by reducing the hedge. First, reducing the number of warheads (which require constant maintenance and periodic life extension) could save a few hundred million dollars in the federal budget. Second, it could send a positive signal to Russia about U.S. long-term intentions. In his 2013 Berlin address, President Obama indicated that his administration would seek “negotiated cuts with Russia” to reduce the number of deployed strategic nuclear weapons below the ceilings of the New START Treaty.14 In terms of deployed strategic nuclear weapons, Moscow has already met the limits of the Treaty and seems to be reluctant to negotiate any further cuts until the 2018 New START implementation deadline or until the United States also meets the Treaty limits15 (which – in light of the current trends – is probably not going to happen earlier than 2018). In addition, the deeper the two sides reduce their deployed strategic nuclear arsenals, the harder Russia tries to press the United States to include all other issues which affect strategic stability (especially ballistic missile defense). The United States has tried to alleviate Russian concerns over missile defense by offering some cooperative and transparency measures but Moscow insists that a legally binding treaty is necessary, which would put serious limits on the deployment of the system (a condition that is unacceptable to the United States Congress at the moment). Therefore, the future of further reductions seems to be blocked by disagreements over missile defense. But the proposed reduction of the hedge could signal U.S. willingness to reduce its strategic advantage against Russia.
Despite the potential benefits, U.S. government documents16 have been setting up a number of preconditions for reducing the size of the hedge. Beyond “geopolitical stability,” the two most important preconditions are the establishment of a responsive infrastructure by constructing new warhead production facilities and the successful completion of the warhead modernization programs. The Department of Energy’s FY 2014 Stockpile Stewardship and Management Plan (SSMP) proposes a so-called 3+2 warhead plan that would create three interoperable warheads for ballistic missiles and two for long-range bombers.17 The transition to interoperable warheads could, according to the plan, permit a reduction of the number of warheads in the hedge. In light of the current budget constraints, it is still unclear if the program will start as planned and even if completed according to schedule, the gradual reduction of the technical hedge would not begin until the mid-2030s. Similar challenges will arise if the administration wishes to link the reduction of the hedge to the construction of new warhead production facilities – some of which have already been delayed due to budget considerations, and the exact dates and technical details of their future completion are still unclear.
The preconditions would mean that significant reductions in the hedge18 are unlikely to materialize for at least another 15 years. Meanwhile, the deployed arsenal faces two scenarios in the coming decades: the number of warheads and delivery platforms could keep shrinking or arms control negotiations might fail to produce further reductions as a result of strategic inequalities (partly caused by the huge U.S. non-deployed arsenal). Under the first scenario, keeping the hedge in its current size would be illogical because a smaller deployed arsenal would require fewer replacement warheads19 in case of technical failures, and because fewer delivery platforms would require fewer up-load warheads in case of geopolitical surprises. Maintaining the current non-deployed arsenal would not make any more sense under the second scenario either. If future arms control negotiations get stuck based on arguments over strategic parity, maintaining a large hedge force will be part of the problem, not a solution. Therefore, insisting on the “modernization precondition” and keeping the current hedge for another 15 years would not bring any benefits for the United States.
On the other hand, President Obama could use his executive power to start gradual reductions in the hedge. Although opponents in Congress have been trying to limit his flexibility in future nuclear reductions (which could happen in a non-treaty framework), current legislative language does not explicitly limit cuts in the non-deployed nuclear arsenal. After the successful vote on the New START Treaty, the Senate adopted a resolution on the treaty ratification which declares that “further arms reduction agreements obligating the United States to reduce or limit the Armed Forces or armaments of the United States in any militarily significant manner may be made only pursuant to the treaty-making power of the President.”20 However, if gradual cuts in the hedge would not be part of any “further arms reduction agreement” but instead implemented unilaterally, it would not be subject to a new legally binding treaty (and the necessary Senate approval which comes with it). Similarly, the FY2014 National Defense Authorization Act (NDAA), which was adopted in December 2013, does not use explicit language against unilateral reductions in the hedge.21 The NDAA only talks about preconditions to further nuclear arms reductions with Russia below the New START Treaty levels and it does not propose any limitations on cutting the non-deployed arsenal. In fact, the NDAA encourages taking into account “the full range of nuclear weapons capabilities,” especially the non-strategic arsenals – and this is exactly where reducing the United States hedge force could send a positive message and prove beneficial.
The 2013 Presidential Employment Guidance appears to move towards an alternative approach to hedging. This new strategy implies less reliance on non-deployed nuclear weapons which is a promising first step towards their reduction. However, the FY 2014 Stockpile Stewardship and Management Plan links this reduction to the successful completion of the ongoing nuclear modernization programs, anticipating that the number of warheads in the hedge force will not change significantly in the near future. Its fate will mainly depend on congressional budget fights.
This might send a bad signal to Russia, where U.S. missile defense developments and its alleged impact on strategic stability are already a primary source of concern to the Kremlin. As a result of aging technologies and necessary retirements, Russian nuclear forces have been constantly decreasing, and despite all modernization efforts,[ref]Russian has an ongoing modernization program, in the framework of which it has already begun to build a new heavy ICBM and a multiple-warhead Bulava SLBM.[/ref] it is expected that by the early 2020s the ICBM arsenal will shrink to 220 missiles.22 Russia already deploys 40 percent less strategic delivery systems than the United States and tries to keep the balance of deployed weapons by higher warhead loadings. This does not give Russia the ability to significantly increase the deployed number of warheads – not just because of the lower number of delivery vehicles but also because of the lack of reserve warheads comparable in number to the United States hedge force. In this regard there is an important asymmetry between Russia and the United States – while Washington keeps a hedge for technical and geopolitical challenges, Moscow maintains an active production infrastructure, which – if necessary – enables the production of hundreds of new weapons every year. It definitely has its implications for the long term (10-15 years) status of strategic parity, but certainly less impact on short term prospects.
In the meantime, the United States loads only 4-5 warheads on its SLBMs (instead of their maximum capacity of 8 warheads) and keeps downloading all of its ICBMs to a single warhead configuration.23 Taken into account the upload potential of the delivery vehicles and the number of warheads in the hedge force, in case of a dramatic deterioration of the international security environment the United States could increase its strategic nuclear arsenal to above 4000 deployed warheads in about three years.
Whether one uses a narrow or a broader interpretation of strategic stability, these tendencies definitely work against the mere logic of strategic parity and might have a negative effect on the chances of further bilateral reductions as well. Cutting the hedge unilaterally would definitely upset Congress and it could endanger other foreign policy priorities of the United States (such as the CTBT ratification or negotiations with Iran), but it would still be worth the effort as it could also indicate good faith and contribute to the establishment of a more favorable geopolitical environment. It could signal President Obama’s serious commitment to further disarmament, send a positive message to Russian military planners and ease some of their paranoia about U.S. force structure trends.
Anna Péczeli is a Fulbright Scholar and Nuclear Research Fellow at the Federation of American Scientists. Additionally, Péczeli is an adjunct fellow at the Hungarian Institute of International Affairs, where she works on nuclear arms control. Péczeli earned a master’s degree in international relations from Corvinus University of Budapest, and is currently working on her doctoral dissertation, which focuses on the Obama administration’s nuclear strategy.
President’s Message: Legitimizing Iran’s Nuclear Program

Be careful of self-fulfilling prophecies about the intentions for Iran’s nuclear program. Often, Western analysts view this program through the lens of realist political science theory such that Iranian leaders seek nuclear weapons to counteract threats made to overthrow their regime or to exert dominance in the Middle East. To lend support to the former argument, Iranian leaders can point to certain political leaders in the United States, Israel, Saudi Arabia, or other governments that desire, if not actively pursue, the downfall of the Islamic Republic of Iran. To back up the latter rationale for nuclear weapons, Iran has a strong case to make to become the dominant regional political power: it has the largest population of any of its neighbors, has a well-educated and relatively technically advanced country, and can shut off the vital flow of oil and gas from the Strait of Hormuz. If Iran did block the Strait, its leaders could view nuclear weapons as a means to protect Iran against attack from powers seeking to reopen the Strait. (Probably the best deterrent from shutting the Strait is that Iran would harm itself economically as well as others. But if Iran was subject to crippling sanctions on its oil and gas exports, it might feel compelled to shut down the Strait knowing that it is already suffering economically.) These counteracting external threats and exerting political power arguments provide support for the realist model of Iran’s desire for nuclear bombs.
But viewed through another lens, one can forecast continual hedging by Iran to have a latent nuclear weapons capability, but still keeping barriers to proliferation in place such as inspections by the International Atomic Energy Agency (IAEA). In particular, Iranian leaders have arguably gained considerable political leverage over neighbors by just having a latent capability and have maintained some legitimacy for their nuclear program by remaining part of the IAEA’s safeguards system.
If Iran crosses the threshold to make its own nuclear weapons, it could stimulate neighbors to build or acquire their own nuclear weapons. For example, Saudi leaders have dropped several hints recently that they will not stand idly by as Iran develops nuclear weapons. The speculation is that Saudi Arabia could call on Pakistan to transfer some nuclear weapons or even help Saudi Arabia develop the infrastructure to eventually make its own fissile material for such weapons. Pakistan is the alleged potential supplier state because of stories that Saudi Arabia had helped finance Pakistan’s nuclear weapons program and thus, Islamabad owes Riyadh for this assistance. Moreover, Pakistan remains outside the Non-Proliferation Treaty and therefore would not have the treaty constraint as a brake on nuclear weapons transfer. Furthermore, one could imagine a possible nuclear cascade involving the United Arab Emirates, Jordan, and Egypt, all states that are developing or considering developing nuclear power programs. This proliferation chain reaction would likely then undermine Iran’s security and make the Middle East further prone to potential nuclear weapons use.
I would propose for the West to act optimistically and trust but verify Iran’s claim that its nuclear program is purely for peaceful purposes. The interim deal that was recently reached between Iran and the P5+1 (the United States, Russia, France, China, United Kingdom, and the European Union) is encouraging in that it places a temporary halt on some Iranian activities such as construction of the 40 MW reactor at Arak, the further enrichment of uranium to 20 percent uranium-235 (which is about 70 percent of the work needed to reach the weapons-grade level of 90 percent uranium-235), and continued expansion of the enrichment facilities. Iran also has become more open to the IAEA’s inspections. But these are measures that can be readily reversed if the next deal cannot be negotiated within the next several months. Iran is taking these actions in order to get relief from some economic sanctions.
Without getting into the complexities of the U.S. and Iranian domestic politics as well as international political considerations, I want to outline in the remaining part of this president’s message a research agenda for engineers and scientists. I offer FAS as a platform for these technical experts to publish their analyses and communicate their findings. Specifically, FAS will create a network of experts to assess the Iranian nuclear issues, publish their work on FAS.org, and convene roundtables and briefings for executive and legislative branch officials.
Let’s look at the rich research agenda, which is intended to provide Iran with access to a suite of peaceful nuclear activities while still putting limits on the latent weapons capacity of the peaceful program. By doing so, we can engender trust with Iranians, but this will hinge on adequate means to detect breakout into a nuclear weapons program.
First, consider the scale of Iran’s uranium enrichment program. It is still relatively small, only about a tenth of the capacity needed to make enough low enriched uranium for even the one commercial nuclear plant at Bushehr. Russia has a contract with Iran for ten years of fuel supply to Bushehr. If both sides can extend that agreement over the 40 or more years of the life of the plant, then Iran would not have the rationale for a large enrichment capacity based on that one nuclear plant. However, Iran has plans for a major expansion of nuclear power. Would it be cost effective for Iran to enrich its own uranium for these power plants? The short answer is no, but because of Iranian concerns about being shut out of the international enrichment market and because of Iranian pride in having achieved even a modestly sized enrichment capacity, Iranian leaders will not give up enrichment. I would suggest that a research task for technical experts is to work with Iran to develop effective multi-layer assurances for nuclear fuel. Another task is to assess what capacity of enrichment is appropriate for the existing and under construction research and isotope production reactors or for smaller power reactors. These reactors require far less enrichment capacity than a large nuclear power plant. A first order estimate is that Iran already has the right amount of enrichment capacity to fuel the current and planned for research reactors. But nuclear engineers and physicists can and should perform more detailed calculations.
One reactor under construction has posed a vexing challenge; this is the 40 MW reactor being built at Arak. The concern is that Iran has planned to use heavy water as the moderator and natural uranium as the fuel for this reactor. (Heavy water is composed of deuterium, a heavy form of hydrogen with a proton and neutron in its nucleus, rather than the more abundant “normal” hydrogen, with a proton in its nucleus, which composes the hydrogen atoms in “light” or ordinary water.) A heavy water reactor can produce more plutonium per unit of power than a light water reactor because there are more neutrons available during reactor operations to be absorbed by uranium-238 to produce plutonium-239, a fissile material. The research task is to develop reactor core designs that either use light water or use heavy water with enriched uranium. The light water reactor would have to use enriched uranium in order to operate. A heavy water reactor could also make use of enriched uranium in order to reduce the available neutrons. Another consideration for nuclear engineers who are researching how to reduce the proliferation potential of this reactor is to determine how to lower the power rating, while still providing enough power for Iran to carry out necessary isotope production services and scientific research with the reactor. The 40 MW thermal power rating implies that if operated at near full power for a year, this reactor can make one to two bombs’ worth of plutonium annually. Another research problem is to design the reactor so that it is very difficult to use in an operational mode to produce weapons-grade plutonium. Safeguards and monitoring are essential mechanisms to forestall such production but might not be adequate. Here again, research into proliferation-resistant reactor designs would shed light on this problem.
Regarding isotope production, further research and development would be useful to figure out if non-reactor alternative technologies such as particle accelerators can produce the needed isotopes at a reasonable cost. Derek Updegraff and Pierce Corden of the American Association of the Advanced of Science have been investigating alternative production methods. Science progresses faster when additional researchers investigate similar issues. Thus, this research task could bear considerable fruit if teams can develop cost effective non-reactor means to produce medical and other industrial isotopes in bulk (or whatever quantity is required). If such development is successful, Iran and other countries could retire isotope production reactors that could pose latent proliferation concerns.
Finally, I will underscore perhaps the biggest research challenge: how to ensure that the Iranian nuclear program is adequately safeguarded and monitored. One of the next important steps for Iran is to apply a more rigorous safeguards system called the Additional Protocol and for a period of time, perhaps from five to ten years, apply inspection measures that go beyond the requirements of the Additional Protocol in order to instill confidence in the peaceful nature of Iran’s nuclear program. Dozens of states have ratified the Additional Protocol, which requires the IAEA to assess whether there are any undeclared nuclear material and facilities in the country being inspected. The Additional Protocol was formed in response to the finding in 1991 in Iraq that Saddam Hussein’s nuclear technicians were getting close to producing fissile material for nuclear weapons, despite the fact that Iraq was subject to regular IAEA inspections of its declared nuclear material and facilities. The undeclared facilities were often physically near declared facilities. There are concerns that given the large land area of Iran, clandestine nuclear facilities might go unnoticed by the IAEA or other means of detection and thus pose a significant risk for proliferation. The research task is to find out if there are effective means to find such clandestine facilities and to provide enough warning before Iran would be able to make enough fissile material and form it into bombs.
A key consideration of any part of this research agenda is how to cooperate with Iranian counterparts. For this plan to be acceptable and achievable, Iranian engineers, scientists, and leaders must own these concepts and believe that the plan supports their objectives to have a legitimate nuclear program that can generate electricity, produce isotopes for medical and industrial purposes, and provide other peaceful benefits including scientific research. Thus, we will need to leverage earlier and ongoing outreach to Iran by organizations such as the Pugwash Conferences on Science and World Affairs, the U.S. National Academy of Sciences, the American Association for the Advance of Science, and the Richard M. Lounsbery Foundation. Future workshops with Iranian counterparts are essential and companion studies by these counterparts would further advance the cause of legitimizing the Iranian nuclear program.
Several scientists and other technically trained experts in the United States have already been assessing aspects of this agenda as I indicated above with the mention of Updegraff and Corden’s research. Also, without meaning to slight anyone I may not know of or forget to mention, I would call out David Albright and his team at the Institute for Science and International Security, Richard Garwin of IBM, Frank von Hippel and colleagues at Princeton University, and Scott Kemp of MIT. This group is doing insightful work, but I believe that getting more engineers and scientists involved would bring more diverse ideas and more technical expertise to bear on this challenge to international security.
Engineers and scientists have a fundamental role to play in explaining the technical options to policy makers. For FAS, in particular, such work will help revitalize the organization as a true federation of scientists and engineers dedicated to devoting their talents to a more secure and safer world. FAS invites you to contact us if you have skills and knowledge you want to contribute to this proposal to help ensure Iran’s nuclear program remains peaceful.
Charles D. Ferguson, Ph.D.
President, Federation of American Scientists
A Citizen Approach to Nonproliferation
Have you ever watched a football match where thousands of attendees witness an event that the officials missed? Sometimes there is wisdom in the crowd, especially a crowd who understand the rules of the game. Officials, no matter how dedicated and hardworking they may be, cannot be everywhere or look everywhere at every moment. Indeed, sometimes just one set of eyes can call attention to what should have been obvious or would have been missed.
Consider the individual with administrative responsibilities working for an import/export company who has been told that the company works on the acquisition of farming equipment. Invoices and shipment information cross their desk for large diameter carbon fiber tubes or those made from maraging steel or high-speed electronics, potential items for a gas centrifuge uranium enrichment facility or nuclear weapons detonation fire sets. Maybe they are laborers in the company’s receiving facility and are responsible for uncrating and repackaging these purchases. They are witnesses to illegal activities and, if they remain uninformed, these individuals would simply go about their everyday tasks.
Shouldn’t we consider a way to reach the citizens of the world to make the world a safer place? Shouldn’t we explore how the power of the web and crowdsourcing might have a profound impact in the area of nonproliferation? Part of the power of the web is how inexpensive it is to explore concepts and allow users to vote with their participation and support.
This article describes the concept of Citizen Sensor1, which aims at leveraging citizens around the world to further strengthen the nonproliferation and international safeguard regime. Start by imagining a world with new and inexpensive methods of vigilance against the spread of nuclear weapons by producing as many knowledgeable citizens as possible – using the observations of crowds and attentive individuals through the power of the web.
The detection of undeclared nuclear facilities and nuclear weapons programs is unequivocally the greatest challenge facing the International Atomic Energy Agency. The common theme for all nuclear nonproliferation challenges is the exposure of people to information, but they are often unaware of the actual application or nature of their work or of the items and activities they see. Or, even if they are aware, they are not sure where to turn to or how to safely inform others. By using the web as both an education tool and a reporting platform, Citizen Sensor aims to alert them to this type of threat, instruct them on how they can help with early detection through education and vigilance and share their knowledge to try to deter those who seek to create a nuclear weapon or other weapons of mass destruction. From the proposed website: “The problem of nuclear proliferation is much like a puzzle – one piece of the puzzle may not show you much, but a collection of pieces will. By combining even seemingly innocuous pieces of information we can help deter nuclear threats and provide nuclear security for the world at large.”
Elements of the Internet-based Citizen Sensor Culture
A variety of potential elements could influence the creation of the Citizen Sensor. These include:
- Proliferation indicator training – What are the most important signs that might indicate proliferation is happening and how do you watch for them? Citizen Sensor would educate the web-based community as a formidable mechanism for early detection of the construction of clandestine nuclear facilities and discovery of weaponization activities. The website would allow education through words and pictures.
- “Neighborhood Watch” as a sharing platform – Post your evidence/suspicions anonymously or signed for discussion and analysis by the crowd.
- “Amber” or “911” type alert for urgent real-time events – If nuclear or radiological material or sensitive information goes missing, mobilize people to help law enforcement find them.
- “Suggestion” box – What are your ideas on how to improve a Citizen Sensor website?
- Testimonials – What supporting activities can be shared with the general public in order to encourage this work?
The concept of Citizen Sensor reaches beyond its website; it would leverage information and capabilities on other websites (such as the IAEA, Google Earth, and Wikipedia) and it will develop an international culture of informed training, watchfulness, and reflection regarding proliferation, coupled with statistical and social science analysis of the information exchanges and discussions that transpire.
Citizen Sensor would include tools for education, information discovery, and anonymous reporting, and could serve as a test bed for other researchers to experiment with specific data processing and social science techniques. These include incentives for the public to participate and methods to screen for incorrect information.
Training modules on all elements of the nuclear fuel cycle, single/dual use items, and aspects of weaponization would be developed, along with search tools to allow users to discover any linkages/matches from their “found” information to be translated into written and/or visual knowledge.

A successful Citizen Sensor website would catalyze a watchful and credible culture of citizen sensors – a worldwide community that produces potential actionable threats and concerns that those with authority and power would consider and act upon. It could be a significant deterrent to proliferators, as it targets the very human resources they count on.
As smart phones continue to grow in computational and sensor capability, new applications continue to arise. GammaPix™ works with the camera of iPhones2 and Android-based3 smart phones to detect radioactivity. The app allows you to measure radioactivity levels wherever you are and determine if your local environment is safe. The app can be used for the detection of radioactivity in everyday life such as exposure on airplanes, from medical patients, or from contaminated products. GammaPix™ can also be used to detect hazards resulting from unusual events like nuclear accidents (such as Fukushima), a terrorist attack by a dirty bomb, or quietly placed and potentially dangerous radioactive sources. As this technology becomes more widespread, a way to gather, process, and post the information is needed. Educating the public on its limitations is just as important as its capabilities, and Citizen Sensor website could potentially accomplish both aspects.
If Citizen Sensor had already been operational, perhaps it could have helped during the 2013 theft in Mexico of a cobalt-60 radioactive source. The thieves apparently had not been aware of what they had stolen, but what if they had been interested in making a radiological dispersal device? Just as an Amber Alert aims to help officials find a missing child or a 911 call is used for emergencies in the United States, perhaps a Citizen Sensor alert could help find missing radioactive materials.
Through the Comprehensive Test Ban Treaty Organization, the world is building a surveillance network to detect nuclear tests. According to an article in the Washington Post, “the nearly-completed International Monitoring System is proving adept at tasks its inventors never imagined. The system’s scores of listening stations continuously eavesdrop on Earth itself, offering clues about man-made and natural disasters as well as a window into some of nature’s most mysterious processes.”4 What might thousands of people, educated observers, and radioactivity-detecting smart phones find?
Requirements
Citizen Sensor must be as open as possible, without any government affiliation, by hosting through a non-governmental organization. It must be unencumbered by government policy and/or regulations. It must be responsive to current events and actively maintain updated information. Knowledgeable developers of websites and training modules for nuclear fuel cycle facilities, proliferation indicators, and sustained funding are all key factors for any chance of success.
The effort must be international and multi-lingual with capabilities that evolve over time as experience and suggestions drive its future. Contributions can be either public posts or private messages and can be either anonymous or signed. It is certain there will be false positives, and issues and concerns that do not point to proliferation activity. Both the culture and software must be structured to minimize false positives and protect it and contributors from the ramifications of false positives. It will also act as a nexus for discovery tools at other websites offering maps, images, knowledge, and analysis tools.
The challenge that is faced is the support (financial and skills) to make this concept a reality. This includes recruiting scientific talent to populate educational modules, website creation and operators and methods to promote the Citizen Sensor and its potential to educate citizens about the nature of nuclear materials and proliferation.
Editor’s Note
If interested, please send feedback and ideas to citizensensor@inl.gov.
Mark Schanfein joined Idaho National Laboratory (INL) in September 2008, as their Senior Nonproliferation Advisor, after a 20-year career at Los Alamos National Laboratory where, in his last role, he served as Program Manager for Nonproliferation and Security Technology. He served as a technical expert on the ground in the DPRK during the disablement activities resulting from the 6-Party Talks. Mark has eight years of experience working at the International Atomic Energy Agency in Vienna, Austria, in the Department of Safeguards where he served four years as a safeguards inspector and as Inspection Group Leader in Operations C, and four years as the Unit Head for Unattended Monitoring Systems (UMS) in Technical Support. In this position he was responsible for the installation of all IAEA unattended systems in nuclear fuel cycle facilities worldwide.
With over 30 years of experience in international and domestic safeguards, his current focus is on conducting R&D to develop the foundation for effective international safeguards on pyroprocessing facilities and solutions to other novel safeguards challenges.
Steven Piet has worked 31 years at Idaho National Laboratory. He earned the Bachelors, Masters, and Doctor of Science degrees in nuclear engineering from the Massachusetts Institute of Technology (MIT). He has 57 peer-reviewed journal articles and is author or co-author of 3 book chapters – in the fields of nuclear fuel cycles, fusion safety and technology, environmental science and decision making, and stakeholder assessment and decision making. For the nuclear fuel cycle program, he framed questions, searched for broadly acceptable and flexible solutions, promoted consensus on criteria, evaluated trade-offs, and identified R&D needs and possibilities to improve concepts; and was responsible for development of the world-leading multi-institution fuel cycle system dynamic model VISION. For the Generation IV advanced nuclear power program, his lab-university team diagnosed public/stakeholder issues and heuristics.
He has also been a Toastmaster for almost 9 years and has attained the educational achievement level of “Distinguished Toastmaster,” which less than 1% of Toastmasters achieve. As Club President, his club achieved President’s Distinguished Status. He was recognized as Area Governor of the year (2011-2012) and Division Governor of the year (2012-2013) and now serves as District Lt Governor of Marketing.
U.S. Spent Nuclear Fuel: The Up To $80/kgU Solution
A congressional impasse on what to do with U.S. reactors’ spent nuclear fuel could last to 2017 or beyond unless a compromise can be found between the House and Senate. The House has voted to support finishing review of the site license application for the Yucca Mountain repository, but the Senate has not. Facing opposition from the state of Utah, Private Fuel Storage, LLC, has let a license for storage for twenty years of 40,000 metric tons (tonne) of spent nuclear fuel (i.e. from 40,000 tonne of uranium originally loaded into reactors) lapse. The Nuclear Waste Policy Act of 1982 allowed for the federal government to build a monitored retrievable storage facility (MRS) for up to 10,000 tonne, but there has been insufficient support for this in Congress.
Resolving the Impasse
A recent review 1 considered two suggestions for keeping the current impasse from dragging on for years. One was to approve funds to complete the Yucca Mountain site license review, but give Nevada control over transportation to the site. If the application were approved, this could reduce the time needed to come to an agreement with Nevada on terms for opening the repository by several years. However, prospects for such a compromise in the current Congress are dim.
Another suggestion was to revisit the payment amounts specified in the “benefits agreements” in the Nuclear Waste Policy Act of 1982 (NWPA). These amounts are $20 million/yr while a repository is open to receive spent fuel and $10 million/yr while an MRS is open. These amounts will likely be less than 60 percent of their purchasing power on the originally scheduled Yucca Mountain opening date of 1998. The purchasing power of the annual benefits payments would likely decline by about another factor of two over the time envisioned to fill the facility to its licensed capacity. Even without taking account of other considerations discussed below, this situation creates a prima facie case for revisiting the benefits payments.
The estimated cost of spent nuclear fuel disposal exceeds $600 per kg of waste. (This is a cost per uranium originally loaded into commercial reactors; estimate is based on the amount spent on Yucca Mountain so far and the Nuclear Waste Fund balance that the Department of Energy previously estimated as adequate.) The annual benefit payments now allowed for by the NPWA amount to a fraction of a percent of the total project cost. A private property owner would likely balk at such a small return on a valuable asset, so it is hardly surprising that the Nevada Congressional delegation is united in opposition to execution of the terms of the current Yucca Mountain license application.
The suggested benefits payment in the title of this article is “up to $80/kg.” This maximum amount would be annually adjusted for inflation starting every year after 2013 in order to maintain its purchasing power. The $80/kg figure comes from an interchange during a July 31, 2013, appearance of Secretary of Energy Ernest Moniz before the House’s Energy and Commerce Subcommittee on Environment and the Economy.[ref]Oversight of DOE’s Strategy for the Management and Disposal of Used Nuclear Fuel and High-level Radioactive Waste, U.S. House of Representatives Energy and Commerce Subcommittee on Environment and the Economy, July 31, 2013, http://energycommerce.house.gov/hearing/%E2%80%9Coversight-doe%E2%80%99s-strategy-management-and-disposal-used-nuclear-fuel-and-high-level[/ref] Noting a cost estimate of $5.6 billion to conduct a search for a new repository site, the subcommittee chair twice asked why this sum should not instead be given to Nevada. Divided by the 70,000 tonne capacity specified in the Yucca Mountain site license application (90 percent of which is for commercial spent fuel), this would amount to $80/kg. While these questions may have well been a rhetorical device highlighting an additional expenditure (thought unnecessary), there is merit in giving this question serious consideration.
Why Sooner Rather Than Later?
There are several problems with looking to open Yucca Mountain within the existing NWPA and its current benefits agreements. The license application only allows for 63,000 tonne of commercial spent fuel. More than that has already accumulated. Any attempt to expand the licensed capacity would face the challenge of revision of the NWPA through normal congressional procedures, rather than the straight up or down vote required if the Nuclear Regulatory Commission approves the current license application. Also, opening Yucca Mountain in the context of the current NWPA is likely to face determined opposition from Nevada on all legally available fronts and lead to extensive delays. A particular Achilles’ heel of the license application is a provision to install billions of dollars’ worth of protective titanium-palladium alloy protective shields upon site closure. This is under the assumption that humans nearby will continuously use wells near the site for a million years; but never in that time will the value of the installed metal lead to intrusion to recover it. Even if the Nuclear Regulatory Commission considers the possibility of intrusion to be outside its purview, there is no guarantee of successful legal challenge against this or any other provisions of license for construction and operation.
Recent decisions to close the Crystal River (FL), Kewaunee (WI), Vermont Yankee (VT), and San Onofre (CA) reactors highlight the growing amounts of spent nuclear fuel stranded at sites with no operating reactors. Without a place to move stranded spent fuel for many years until Yucca Mountain is (maybe) ready to receive shipments, each stranded fuel site costs millions of dollars per year to secure. Additionally, until there is a U.S. state available to willingly host spent commercial reactor fuel, there is virtually no possibility of the United States being able to negotiate agreements that preclude another country enriching uranium or reprocessing in pursuit of economic efficiency and nonproliferation objectives in exchange for permanent U.S. acceptance of spent nuclear fuel. While an opportunity to export spent fuel is only one consideration in determining whether a country of potential future concern acquires weapons-relevant nuclear capabilities, the potential consequences of these capabilities eventually falling into the wrong hands can be enormous. Failure to promptly resolve the spent fuel management problem in the United States thus ties the country’s hands in an arena with national and international security implications.
Promoting Flexibility
It is important to avoid an overly narrow focus concentrating only on repository siting. Thus, what is specifically suggested here is for the federal government to allow one or more states to charge up to $80 ($US2012)/kg to take spent fuel into a facility licensed to manage it for at least 100 years. This could be any combination of underground and above ground facilities in one or more states. The time frame of 100 years is chosen for two reasons. First, the dominant radiation hazard and heat load from casked spent fuel is from cesium-137 and strontium-90, which both have half-lives of about 30 years. Once these have decayed for about 100 years, it is easier either to dispose of the spent fuel underground or (less likely in the United States but still pursued in other countries) reprocess it to recover plutonium to fuel nuclear reactors.
Secondly, the most recent Waste Confidence Decision revealed a consensus among Nuclear Regulatory Commissioners that nuclear waste can be safely stored above ground in dry casks for at least 100 years. To actually license such a facility for so long requires that it have capability for repackaging material in dry casks and moving casks to new storage areas as needed; this should be readily manageable. Also, while there could be problems with licensing Yucca Mountain to contain radioactive materials for a million years, there seems to be little question that it could safely contain spent nuclear fuel for at least 100 years. As long as the federal government retains title to the spent fuel, licensing 100 years of storage at one or more locations should leave ample time to observe the results of other countries’ efforts and adequately research alternatives (for example, deep boreholes that would make recovery of weapons usable fissile materials much more difficult over the long term).
The phrase “up to” $80/kg is chosen deliberately in case more than one state is willing to host a spent nuclear fuel management facility. This would allow a competitive environment where states would in fact only be able to charge what the market will bear, thus potentially reducing outlays from federally controlled funds.
Two things should be kept in mind concerning a substantial increase in benefit payments beyond that called for in the NWPA. First, considering the cost of expected delays, legal costs, expense of managing stranded spent fuel, and ability of utilities to plan for what is going to happen upon retirement of aging nuclear reactors, it is not unlikely that charges of up to $80/kg will turn out to be “cheap at the price” compared to the alternative. Second, payments to host states can be put to good use for other needed purposes, while much of the money otherwise spent in a contentious siting process will be spent on what could be avoidable costs.
It is not clear whether $80/kg will be sufficient to encourage Nevada to cooperate with licensing Yucca Mountain, or to encourage other states to host spent fuel management facilities. What Nevada authorities and representatives would need to ponder is whether they might eventually get stuck with Yucca Mountain and only the comparatively paltry and inflation-eroded benefits payments called for in the NWPA. Preparation of legislation to amend the NWPA to update benefits payments might at least start a conversation about what level of compensation to prospective host states would be suitable. In light of the four imperatives enumerated above, there is much to recommend for making the attempt.
Clifford E. Singer is Professor of Nuclear, Plasma, and Radiological Engineering and of Political Science at the University of Illinois, and is currently co-director of the College of Engineering Initiative on Energy Sustainability Engineering. Singer received a B.S. in Mathematics from the University of Illinois, a Ph.D. in biochemistry at the University of California, Berkeley and was a National Science Foundation Postdoctoral Fellow at MIT. He subsequently did research in plasma physics, advanced space propulsion, and the computational simulation of thermonuclear plasma performance at the University of London, Princeton University, and the University of Illinois. He was an Alexander von Humboldt Fellow at the Max Planck Institutes for Strömungsforschung and Plasmaphysik at Göttingen and Garching in Germany. As a local elected official he was briefly the final Chair of the Champaign County Solid Waste Disposal association, and he has supervised thesis research on the Illinois/Kentucky Low Level Radioactive Waste Compact. He is currently supervising research on global energy economics with emphasis on spent nuclear fuel management, sources of energy for transportation, and greenhouse gas emissions. Prior to completing a sabbatical leave at the American Association for the Advancement of Science Center for Technology and Security Policy in Washington, DC, he was the Director of the University of Illinois at Urbana-Champaign Program in Arms Control, Disarmament, and International Security (ACDIS).
Global Threat Reduction Initiative Efforts to Prevent Radiological Terrorism
Saturday, August 17, 2013 at 2:35 am
Suburban location—Anywhere, United States
Three men enter a darkened building of a mid-size university closed for summer break. The university has unarmed security guards that make periodic checks of the campus building exteriors, and the local law enforcement agency is a county police department that interacts with the university on an “occasional” basis. The men enter a third floor laboratory housing a Cesium 137 irradiator. The irradiator is used by faculty and students to expose tissue samples to high levels of radiation during their research. Using simple tools, they partially dismantle the device and remove the radioactive source capsule containing 3,000 curies of Cesium 137. The three perpetrators move the material in a crudely constructed lead bucket providing light shielding and minimal protection to them, and place the material in a self-storage locker ten miles away. The theft goes unnoticed until Monday morning when it is reported to the county police. The county police are not immediately concerned or recognize the significance of the theft or the amount of radioactive material taken.
Monday, August 19, 2013 at 10:45 am
Urban location—Anywhere, United States
Over the past two days, the three perpetrators have taken the radioactive material and assembled it with explosives stolen from a construction site into a Radiological Dispersal Device (RDD), commonly called a “dirty bomb.” The device has been transported to a medium-sized city, one hundred miles from the university. All three men are suffering from radiation sickness but are able to detonate the device in the city’s business and financial district. Seven people, in addition to the three terrorists, are killed in the explosion. The resulting contamination from the dispersal of the Cesium 137 produces general panic due to health concerns, along with potentially devastating financial consequences.
The above scenario is fictional but will serve as an introduction to the discussion of what could have been done to deter or interdict the attack. Could the university and local police have had strategies to better secure the radioactive materials that were stolen? Could the local police have been notified in a timelier manner through a closer working relationship with university radiation safety professionals? Could police have searched for the material after it had been stolen, while in transit, during assembly at self-storage facility, or while en route to the final target?
The attacks of September 11, 2001, heightened the nation’s concerns regarding all forms of terrorism in the U.S., including the potential use of radioactive materials in a terrorist act. The possibility of such an attack has been of particular concern because of the widespread use and availability of radioactive materials in the United States industry, hospitals, and academic institutions. Loss or theft of such materials, in risk-significant quantities, could lead to their diversion for malicious use in a Radiological Dispersal Device. This past April’s bombing at the Boston Marathon again raised such concerns. In the wake of the Boston attack, Richard Daddario, Deputy Commissioner for counterterrorism at the New York City Police Department, testified that the psychological and economic fallout from a radiological “dirty bomb” event could demand a much longer recovery than a conventional strike. 1
An RDD is a device or mechanism that is intended to spread radioactive material from the detonation of conventional explosives or other means. An RDD detonation would likely result in few deaths (mainly from the explosion), but substantial social and economic impacts could result from public panic, decontamination costs, and denial of access to area for extended periods of time.
The economic consequences of an RDD attack could be enormous. As a point of reference, according to an estimate by Bloomberg Businessweek, it cost $333 million to shut down Boston for a day to facilitate the manhunt for Dzokhar Tsarnaev. Imagine the costs of closing a large portion of any major city for substantially longer periods. An attack at a port could also have major economic consequences. A 2007 study published in Risk Analysis estimated that the economic consequences from a shutdown of the harbors due to the contamination from a plausible dirty bomb scenario could result in losses in the tens of billions of dollars, including the decontamination costs and the indirect economic impacts due to the port shutdown.2
Global Threat Reduction Initiative
In order to prevent a radiological attack, the United States government sponsors a broad range of programs designed to prevent, detect and respond to the loss or theft of nuclear and radiological material. The Global Threat Reduction Initiative (GTRI) is a Department of Energy (DOE) program designed to reduce the amount of vulnerable nuclear and radiological material located at civilian sites worldwide and improve protection of these materials. Because the bulk of its work is pursued overseas, the program is best known for its international activities, in particular removing vulnerable nuclear material from, for example Kazakhstan, and securing high risk radioactive materials, for example in Russia. However, a lesser known and equally complex element of GTRI is its domestic component carried out in the United States. The domestic component involves the interaction and cooperation between federal government officials, scientists and policy makers with state and local police, emergency officials, and operators of private and public institutions, such as hospitals.
This article is intended to describe the domestic component of the GTRI; how it is implemented, why it is needed and how state and local officials take advantage of the program. The goal of this article is to present the joint views of a local police official together with those of a scientist and former policy maker and to explore the technical and policy issues associated with domestic threat reduction programs.
The Context
Radiological materials are located throughout the United States (see Figure 1) with the majority of high activity sources located in large urban population centers. A successfully deployed RDD using radioactive sources commonly found in public facilities such as hospitals could potentially result in radioactive contamination that could require relocation of inhabitants, prohibit the use of facilities, and have debilitating economic impacts. 3
Most radioactive sources in the U.S. are regulated by the Nuclear Regulatory Commission and state authorities. GTRI works with civilian sites to enhance security for their radiological materials; however, it does not regulate them. Participation with GTRI is voluntary on the part of sites although GTRI has an aggressive outreach program to encourage sites to participate. In addition, the Department of Homeland Security’s Domestic Nuclear Detection Office provides assistance to state and local officials in establishing an overall architecture for detecting nuclear and radioactive material that are not under regulatory control, e.g. which have already been lost or stolen. This detection assistance supports the GTRI’s efforts by providing equipment and training to establish a general baseline for state and local first responder nuclear and radiological detection capabilities, but is not focused on specific sites.
Some have expressed concern that funding for radiological threat reduction is better spent overseas, in particular in countries that do not have a strong regulatory infrastructure, as the U.S. does. Indeed, GTRI’s overseas accomplishments are much more frequently in the news. In the U.S., the protection of sources is primarily the responsibility of the owner/operator, following the requirements of the regulator. So, why should the federal government spend funds to protect radiological sources when they should already be adequately protected? Through the current and evolving program, GTRI and partner agencies and institutions have created a strong partnership for a well-rounded domestic security program. The domestic portion of GTRI has evolved to one that seeks to fill the gaps that may exist in the very complicated relationship between local, state, and federal agencies in preventing and responding to radiological security incidents. The focus of the program is shifting toward sustainability of completed security upgrades and improved response capabilities and communication networks.
Locations in the U.S. with risk-significant quantities of radiological sources. 4
Domestic Security Enhancement Program
Since GTRI’s domestic security enhancement program began in 2008, it has worked with host sites to enhance security at more than five hundred buildings which host over four million curies of radioactive materials. GTRI physical security enhancements are applied on a voluntary basis to assist sites in the prevention and detection of any unauthorized access to radiological sources located in their facility. The physical protection principle of detection, specifically early detection, means that detection of a theft is early enough in the act that it can be stopped at the site or nearby. Ideally, early detection should allow time for response forces to prevent an adversary from acquiring the radioactive material. GTRI’s detection upgrades build upon sites’ existing security measures but may include enhancing the following physical protection system components:
- Biometric access control devices
- Door alarms
- Motion sensors
- Cameras
- Duress buttons
- Radiation sensors
- Electronic tamper indicating seals
- Remote monitoring systems
The Insider Threat
A remote monitoring system (RMS) is a critical security measure for detecting an insider threat because the insider (by definition) will have access to the device containing the radioactive material, or to the material itself depending on the type of facility. The insider will also have authorization to use some or all of the site’s access control and detection devices without sending an alarm of unauthorized access. In addition to detecting an insider, the RMS also improves the response by a site’s local law enforcement or other responding agencies by providing them with critical assessment information immediately.

For most U.S. sites, timely notification to local law enforcement is critical to prevent potential theft attempts. The RMS integrates what GTRI calls critical alarms (e.g., device tampering to gain access to the radioactive source(s), increased radiation levels indicating that the source has been removed from its shielding, communications loss between the site and monitoring station, or loss of power) with real time live video images. For increased protection, the RMS is housed in a tamper-indicating housing with battery back-up to ensure its continued operation. To address information security concerns, the RMS also encrypts the video and alarm data. The RMS can send alarm and video data simultaneously to onsite and offsite security and local law enforcement monitoring stations to prevent single-point failures in a site’s security and response planning.

Enhancing Delay Measures
Along with early detection capabilities, GTRI also provides sites with delay enhancements that impede an adversary’s progress to access nuclear and radiological materials. By increasing the delay time and adding valuable minutes in an adversary’s attack time lines, responders have more time to interrupt the adversary before they can remove and steal these materials. GTRI’s delay systems may include:
- Device tie downs
- Security cages
- Security grating
- Hardened doors/rooms
- Ballistic glass
- In-Device Delay Kits
A particularly important delay enhancement is the In-Device Delay kit for irradiators. The National Research Council, a private nonprofit institute, performed a risk and consequence analysis, which showed Cesium Chloride irradiators pose relatively higher security risks compared to other radiological materials.5 To help mitigate this risk, GTRI and DHS developed In-Device Delay (IDD) kits for Cesium irradiators that can be installed on the device. The installation of the IDD kits on selected irradiators significantly increases the time and/or difficulty involved if an intruder tries to remove a source—while not impacting the functionality of the irradiator—and consequently is an important element of security enhancements.
Response Capabilities
One of the most important elements of any security system is a timely, well-equipped, well-trained response team of appropriate size to interrupt and neutralize the adversary before they gain access to the radioactive source or immediately after they gain access. First responders from state and local law enforcement do not work with nuclear material or radiological sources on a daily basis and may lack knowledge of the risks posed by these materials. GTRI has therefore made a focused effort to provide security personnel and local law enforcement with the tools and training to help prepare them to respond to an event involving nuclear or radiological material.
In 2008 GTRI began to sponsor table top exercises for GTRI partners at select nuclear and radiological sites in the United States. These exercises are conducted at predominately private institutions, hospitals and universities and bring together key decision-makers from the actual agencies that would respond to a terrorist WMD incident. At the exercise, host level players include on-site security forces, radiation safety personnel, facility managers and public affairs personnel. At the city and state levels, players can include police, fire, hazmat, EMS, Office of Emergency Management, regulatory agencies and National Guard Civil Support Teams. At the federal level players can include the FBI, DOE/NNSA nuclear response assets the Federal Emergency Management Agency, the Nuclear Regulatory Commission, the Department of Homeland Security and the Environmental Protection Agency.
The overall exercise objectives are to promote cross-sector communication, cooperation, and team-building among public and private sector first responders and to exercise FBI lead responsibility for criminal investigation. In addition, the exercise allows players to examine newly developed tactics, techniques, and procedures resulting from GTRI voluntary security enhancements. The exercises promote attack prevention through intelligence sharing and a coordinated approach to neutralize the threat, along with site specific integrated response planning with federal, state, local, and private sector partners.
Since the first GTRI exercise in December 2008, there have been 29 Silent Thunder table top exercises at state and private universities, hospitals, research and test reactors, the U.S. Department of Agriculture and National Institutes of Health. To date, 329 FBI agents and 3760 players and observers have participated in these GTRI table-top exercises.
Additionally, at the Y-12 National Security Complex in Oak Ridge, Tennessee, GTRI offers participants a three-day alarm response training course. This training includes hands-on exercises and classroom training and teaches site personnel and local law enforcement how to protect themselves and their communities when responding to alarms indicating possible theft of radiological materials.
Removing Disused Sources Before They Can Become a Threat
The final element of GTRI’s domestic radiological security effort involves the removal of sources that are unused and may ultimately be lost or stolen due to lack of attention. In addition to security enhancements, GTRI’s Off-Site Source Recovery Program (OSRP) removes thousands of excess or disused sources in the United States annually. The initial scope of the project included a narrow group of sources (those that fell into the regulatory category of Greater than Class C (GTCC) low-level radioactive waste), but since the terrorist attacks of September 11, 2001, OSRP’s scope has expanded to include the recovery of other sources. 6 Over the years, OSRP has recovered more than 30,000 sources from more than 1,000 sites located in all 50 U.S. states, Washington D.C., and Puerto Rico.7 By removing sources from facilities that no longer had a use for them, GTRI has removed the risk of these materials to be potentially used in a RDD, thus resulting in permanent threat reduction.

From “Global” Threat Reduction to “Local” Threat Reduction
At its core, the GTRI domestic program is a partnership between federal officials, state and local officials and facility operators. One example of this is in Philadelphia, where over a dozen sites are protected in the Philadelphia Metropolitan Area by the GTRI Program, ranging from hospitals and universities, drug manufacturers and government research labs, to one of the American Red Cross’s largest blood distribution centers. Law enforcement agencies (the Philadelphia Police Department being the largest), have benefited tremendously from GTRI’s tabletop exercises, training at the Y12 National Security Complex, and personal radiation detectors provided by the GTRI Program.
The Philadelphia region had an existing Preventive Radiological Nuclear Detection (PRND) program supported by the Domestic Nuclear Detection Office (DNDO) of DHS that the NNSA was able to use as a vehicle to integrate their source security into the overall effort to prevent radiological and nuclear terrorism. This created a very effective two tiered “inside-out” and “outside-in” prevention strategy. The existing deployment of nuclear detection assets protected special events and provided a 24/7 “steady state” coverage from threats from outside the region. The regional law enforcement agencies, assisted by DNDO, were able to field a range of detection equipment on a daily basis, including aircraft, mobile and marine systems. The addition of the GTRI program allowed for the protection of radiological sources of concern within and near relevant facilities while bolstering the defense against an “insider threat” due to the closer relationships created by participation. This “inside-out” approach took Philadelphia’s protection and response effort to the next level by adding source security as a priority. The previous outwardly focus PRND program was equipment and personnel driven while the GTRI Program stresses relationship building between the partner sites and their local law enforcement agencies.
The scenario depicted at the beginning of this article would have multiple chances at prevention/interdiction in the Philadelphia model. The GTRI alarm systems and response programs would have protected the material and facilitated an immediate response and the existing detection assets could be deployed to recover any stolen material. Together, the two programs form an effective deterrent.
The University of Pennsylvania has been the largest beneficiary of the GTRI Program in the area, and has served as a model site for others in the nation for implementing the security and emergency response upgrades. All partners, facility and law enforcement, have enjoyed a much closer relationship that extends to joint training and exercises as well as facility operators providing subject matter expert support to the overall PRND effort.
Due in part to the GTRI program, in October 2013, all the protected facilities alarm notifications are received in the regional “Fusion Center”, the Delaware Valley Intelligence Center (DVIC), creating another layer of defense and allowing for a regional protection and response capability.
Conclusion
As mentioned at the outset of this paper, some in the policy community believe U.S. radiological protection dollars are better spent overseas, where regulatory controls are not as effective as those in the United States. It is true that despite years of effort, many other countries do not have strong regulatory infrastructures for managing access to radiological and nuclear material and funding overseas is well spent. However, as illustrated above, this view does not fully take into account the multifaceted needs of radiological security, which requires the integration of the facility operators, state, local and federal capabilities. Moreover, while sources overseas are generally less well regulated and protected than U.S. sources, radiological sources in the U.S. should receive special attention because they pose the greatest risk: diversion closest to a target of the attack minimizes the likelihood of detection through the global detection capabilities overseas and at U.S. borders. In this view, it makes little sense for the federal government to help provide for a security measure overseas, but not domestically, where the risk may be higher.
A recent Government Accountability Office (GAO) report is instructive in regard to the limitations of regulatory controls. GAO was asked by Congress to determine the extent to which NRC’s regulations ensure the security of radiological sources at U.S. medical facilities and the status of NNSA’s efforts to improve the security of sources at these facilities. GAO reviewed relevant laws, regulations, and guidance; interviewed federal agency and state officials; and visited 26 hospitals and medical facilities in Washington, D.C. and 7 states. The review concluded that existing regulatory requirements do not consistently ensure the security of high-risk radiological sources at the 26 selected hospitals and medical facilities visited. According to the review, one reason for this is that the requirements are broadly written and do not prescribe specific measures that hospitals and medical facilities must take to secure medical equipment containing sealed sources, such as the use of cameras or alarms. Rather, the requirements provide a general framework for what constitutes adequate security practices, which is implemented in various ways at different hospitals. Some of the medical equipment in the facilities visited was more vulnerable to potential tampering or theft than that of other facilities because some hospitals developed better security controls than others. 8
Protecting America from a radiological attack requires a strong alliance between facility operators, state, federal and local officials. In the U.S., the NRC sets the regulatory framework that includes security requirements, licensing, inspection, and enforcement. But the regulatory framework is insufficient for all threats; rather it provides a common baseline level of security. GTRI works with sites to build upon these security standards set by NRC and state regulations. GTRI’s voluntary security enhancements provide sites with security best practices which further enhance security above regulatory requirements. Because the GTRI upgrades are voluntary and may have cost implications for the facility operators as well as state and local authorities, it is essential that all partners are aware of the threats and risks involved in working with certain radioactive material as well as programs to mitigate these risks.
Warren Stern is Senior Advisor in Brookhaven National Laboratory’s Nonproliferation and National Security Department. In 2010, he was appointed by President Obama to lead the Domestic Nuclear Detection Office at DHS and before that, Head of the IAEA’s Incident and Emergency Centre. He has also held a number of leadership positions at the U.S .Department of State, Arms Control and Disarmament Agency and CIA.
Lieutenant Edward Baldini is a twenty four year veteran of the Philadelphia Police Department and has been assigned to the Counter Terrorism Operations Unit since its inception in spring 2002. He has assisted in development of Counter Terrorism Training at the local, state and national level. He has been very active with Preventive Radiological/Nuclear Detection (PRND) mission and has assisted the Domestic Nuclear Detection Office (DNDO) and the National Nuclear Security Administration (NNSA) in several initiatives. He holds a Bachelor’s Degree from Philadelphia University and a Master’s Degree from the Naval Postgraduate School in Monterey, California. He is also a graduate of Northwestern University Center for Public Safety’s School of Police Staff and Command.
Uranium Mining and the U.S. Nuclear Weapons Program
Formed over 6 billion years ago, uranium, a dense, silvery-white metal, was created “during the fiery lifetimes and explosive deaths in stars in the heavens around us,” stated Nobel Laureate Arno Penzias.1 With a radioactive half-life of about 4.5 billion years, uranium-238 is the most dominant of several unstable uranium isotopes in nature and has enabled scientists to understand how our planet was created and formed. For at least the last 2 billion years, uranium shifted from deep in the earth to the rocky shell-like mantle, and then was driven by volcanic processes further up to oceans and to the continental crusts. The Colorado Plateau at the foothills of the Rocky Mountains, where some of the nation’s largest uranium deposits exist, began to be formed some 300 million years ago, followed later by melting glaciers, and erosion which left behind exposed layers of sand, silt and mud. One of these was a canary-yellow sediment that would figure prominently in the nuclear age.
From 1942 to 1971, the United States nuclear weapons program purchased about 250,000 metric tons of uranium concentrated from more than 100 million tons of ore.2 Although more than half came from other nations, the uranium industry heavily depended on Indian miners in the Colorado Plateau. Until recently,3 their importance remained overlooked by historians of the atomic age. There is little doubt their efforts were essential for the United States to amass one of the most destructive nuclear arsenals in the world. By the 1970s an estimated 3,000 to 5,000 of the 12,000 miners employed in the United States were Navajos. 4 5
From the late 1940s to the mid-1960s, they dug up nearly 4 million tons of uranium ore – nearly a quarter of the total national underground production in the United States.6 In doing so they were sent into harm’s way without their knowledge, becoming the most severely exposed group of workers to ionizing radiation in the U.S. nuclear weapons complex.
For minimum wage or less, they blasted open seams of ore, built wooden beam supports in the mine shafts, and dug out ore pieces with picks and wheel barrows. The shafts were as deep as 1,500 feet with little or no ventilation. The bitter tasting dust was all pervasive, coating their teeth and causing chronic coughing. They ate in the mines and drank water that dripped from the walls. The water contained high quantities of radon – a radioactive gas emanating from the ore. Radon decays into heavy, more radiotoxic isotopes called “radon daughters,” which include isotopes of polonium, bismuth, and lead. Radon daughters’ alpha particle emissions are considered to be about 20 times more carcinogenic than x-rays.7 As they lodge in the respiratory system, especially the deep lung, radon daughters emit energetic ionizing radiation that can damage cells of sensitive internal tissues.
The miners were never warned of the hazards of radioactivity in the mines in which they inhaled, ingested and brought home along with their contaminated clothing. Withholding information about the hazards of the workplace was deeply embedded in the bureaucratic culture of the nuclear weapons program. In 1994, a previously secret document (written in the late 1940s) was made public by the Department of Energy which crystallized the long-held rationale for keeping nuclear workers in the dark.
“We can see the possibility of a shattering effect on the morale of the employees if they become aware that there was substantial reason to question the standards of safety under which they are working. In the hands of labor unions the results of this study would add substance to demands for extra-hazardous pay . . . knowledge of the results of this study might increase the number of claims of occupational injury due to radiation.”8
Kee Begay worked in the mines for 29 years and was dying of lung cancer. “The mines were poor and not fit for human beings,” he testified at a citizen’s hearing in 1980. Begay also lost a son to cancer. “He was one of many children that used to play on the uranium piles during those years. We had a lot of uranium piles near our homes –just about fifty or a hundred feet away or so. Can you imagine? Kids go out and play on those piles.”9
For many years the Navajos and other tribes living in the Colorado Plateau used uranium ore in sand paintings and for body adornment. By 1896 samples of this ore were passed along to mineralogists at the Smithsonian Institute in Washington, D.C. Initially confounded by its properties, the Smithsonian experts concluded this was an extremely rare mineral containing uranium and vanadium.
That same year, French physicist Antoine Henri Becquerel discovered that uranium crystals emitted “luminous rays” on photographic plates. Two years later, Becquerel’s colleagues Marie and Pierre Curie painstakingly extracted tiny amounts of two new elements that they named polonium and radium from several tons of uranium ore in an abandoned shed in Paris. Emitting millions of times more of these mysterious rays than uranium, Marie Curie coined the term “radioactivity” to describe their energetic properties.
News of the discovery in Colorado came quickly to the Curies, who were seeking richer ores than those from eastern Germany. In 1897, aware of growing scientific interest in their native country, chemists Henry Poulot and Charles Volleque (who lived in Colorado), purchased 10 tons of this mysterious ore and sent samples to the Paris School of Mines in France,10 where they were also analyzed by Marie Curie.11 A year later it was named Carnotite after Aldophe Carnot, the Inspector General of French mines.
By 1910, a 20 by 60 mile oval strip of carnotite with countless visible swaths of canary-yellow became one of the world’s first major radioactive metal discoveries – helping to usher in the nuclear age. By 1912, nearly all of the uranium ore went to European firms. Its vanadium content (used to harden steel), came into heavy demand during World War I for use in armaments as it would during World War II.
The Colorado Plateau became one of the world’s most important sources of radium, which at a price of $160,000 a gram in 1913 became the most precious substance in the world. About three tons of uranium contained one gram of radium. Half went for use in medicine and the rest was used for luminous paint on dials and other instruments.
By the mid-1920s, the U.S. uranium boom ended when far richer deposits were found in the Shinkolobwe mine in the Belgian Congo. While uranium mining continued in Colorado, the Union Minière du Haut Katanga (UMHK) of Belgium dominated the world uranium market. In the shadow of the highly lucrative radium boom, a revolutionary and fiercely competitive scientific exploration of its radioactive properties would reveal the enormous energy contained in the atoms of uranium. 12
Spurred on by the scientific discoveries and growing consensus among scientists and engineers that atomic weapons fueled by uranium could be made in a relatively short period of time by Germany, the United States launched an unprecedented crash program in December 1941 under the auspices of the Manhattan Engineering District (MED) of the U.S. Army Corps of Engineers. After surveying the known uranium sources, the MED concluded that the Shinkolobwe Mine in the Belgian Congo, the Eldorado Mine in Canada, and the Colorado Plateau were the three most important locations of uranium mining in the world. After being warned by a British scientist in 1939, Edgar Sengier, the head of Union Miniere’s that owned the Congo mine, managed to secretly ship 1,250 tons to the United States in late 1940, where it was stored in a warehouse in Staten Island, New York.
Described as a “freak occurrence of nature” by a top official of the early U.S. nuclear weapons program,13 the Congo mine yielded the highest concentrations of uranium (30-70%)14 of any mine in the world since.15 By comparison, the Congo ore contained as much as much as 7,000 times the concentration uranium than mined in the United States. Between 1942 and the late 1950s, the U.S. nuclear weapons program plant processed approximately roughly 20,000 tons of uranium oxide from the Shinkolobwe mine.16 17 18
Under the MED, the government assumed total control over the production, milling, refining, and use of uranium. This was done out of an office in New York City. Because of its higher purity and immediate availability, uranium from the Belgian Congo proved to be the most significant supply.
By the end of the war, the Colorado Plateau provided 2,698,000 pounds of uranium oxide, (about 14 percent of the project’s uranium needs)19 with the rest coming from the Belgium Congo and Canada. However, the Plateau’s ore reserve was considered very important because it was considered the world’s third largest reserve and primary domestic source of uranium. Grand Junction, Colorado became the center of this secret operation.
On August 1, 1946, Congress passed the Atomic Energy Act, which created a new civilian-controlled Atomic Energy Commission (AEC). This new agency consisted of a civilian panel, and a panel of senators and congressmen who formed the Joint Committee on Atomic Energy (JCAE). As it was during the war, all nuclear facilities and uranium remained under federal control with the government as the only producer of fissionable materials. Even though mining and milling were left to the private sector, the government remained the sole customer with total control over the industry.
Given the potentially tenuous dependence on foreign supplies, the AEC realized that the enormous uranium demand to fuel plutonium production reactors being constructed at the Hanford site in Washington and the uranium enrichment plants in Tennessee and Kentucky could not be met without a major increase in domestic mining. By 1948, the AEC stimulated a uranium mining boom that led to the discovery of other important ore findings on the Navajo reservation and elsewhere. Mining companies promptly entered into agreements that included requirements to hire and train tribal members. In addition to the Colorado Plateau, uranium mining extended to the Black Hills of South Dakota, Northwest Nebraska, Spokane, Washington, the Wind River Indian Reservation and other sites in central Wyoming, the Powder River Basin in Wyoming and Montana, and the Texas Gulf coast.
In the Colorado Plateau alone, uranium mining increased by nearly 150 times from 1948 (54,000 tons of ore) to 1960 (8 million tons). The U.S. Atomic Energy Commission’s uranium purchases exceeded $2.4 billion (2013 dollars) in 1960 alone, making it the third most valuable metal mined in the United States.20
The AEC also encouraged private companies to establish mills and buying stations to process the ore. After milling, about 99 percent of the ore is left behind as waste containing significant amounts of long-lived radiotoxic elements such as radium 226 (which has a half-life equal to 1,625 years). At the end of 1961, there were 25 active uranium mills with a daily capacity of 20,800 metric tons of uranium oxide. Nearly half of the total ore mined was milled in the Grants, New Mexico area.21
More than 230 million tons of uranium mill tailings in the United States have accumulated, dwarfing the volume of all radioactive waste from the production of nuclear weapons and nuclear power generation. Only after widespread contamination containing long-lived radiotoxic elements such as radium 226 drew public alarm were regulations established for the remediation of uranium mill tailings in 1980.
The hazards of uranium mining were known for centuries. As early as 1556, dust in the Ore Mountain mines (Erzgebirge, bordering Germany and what is now the Czech Republic), was reported as having “corrosive qualities, it eats away the lungs and implants consumption in the body…”22 By 1879, researchers found that 75 percent of the miners in the Ore Mountains had died from lung cancer. By 1932, the Ore Mountain miners were receiving compensation for their cancers from the German government.
Uranium mining was convincingly linked to lung cancer by dozens of epidemiological and animal studies by the late 1930s.23 In 1942, Wilhelm C. Hueper, the founding director of the environmental cancer section of the National Cancer Institute, brought the European studies to light in the United States—concluding that radon gas was responsible for half of the deaths of European miners after 10 to 20 years of exposure.24 By this time, uranium had become a key element for the making of the first atomic weapons. Dr. Hueper was blocked from further publications and discussion in this area by his superiors- who informed him that it was “not in the public interest.”25
In defiance to the AEC, Dr. Heuper prepared a paper discussing the hazards of uranium mining for the Colorado Medical Society in 1952. Shields Warren, Director of the AECs Division of Biology and Medicine, ordered the head of the National Cancer Institute (NCI) to direct Dr. Heuper to remove all references to uranium mining hazards. Declaring he had not joined the NCI to be called “a scientific liar,” Dr. Heuper withdrew from the conference and sent a copy of his paper to the President of the Society. The Surgeon General soon forbade him from any further epidemiological research on occupational cancer, and he was further prevented from traveling on official business west of the Mississippi River.26
A year before Dr. Heuper’s confrontation with the AEC, researchers from the U.S. Public Health Service (PHS) and the Atomic Energy Commission (AEC), in the confines of Cold War secrecy, conclusively showed that radiation doses to the miners’ lungs were from radon decay products.27 Around that same time, PHS researchers reported in a classified progress report that radon levels were “310 times the accepted allowable concentration.”28
Radiation doses were calculated to be “twice to nearly ten times the allowable amount of radiation… In the worst cases, they were exceeding allowable weekly doses in less than one day, and were reaching total annual doses in just a week.” 29 The report concluded, “It is not surprising the exposure to radiation doses of this magnitude should produce malignancies.”30
At private meetings with the AEC, mining companies bitterly resisted ventilating the mines, claiming that it would close smaller operations and raise the price of uranium. “While it has a big effect on the price of ore,” an AEC Health scientist argued at a meeting of agency’s Advisory Committee on Biology and Medicine in 1956. “By the time you get it into a reactor or into a bomb that differential is insignificant.”31
By 1957, PHS official Henry Doyle told a hostile audience that radon concentrations in some domestic mines were 67 times higher than in the German mines, where a lung cancer epidemic had been long identified. He also pointed out that the average radiation lung dose to miners in the Colorado Plateau was 21 times higher than allowed in AEC nuclear weapons plants.32 By 1962, the Public Health Service revealed that radon exposure in the mines was statistically linked to lung cancer among miners in the United States.33
Lung disease associated with radon exposure was “totally avoidable” declared Merrill Eisenbud, a former Chief AEC health scientist in 1979. “The Atomic Energy Commission …is uniquely responsible for the death of many men who developed lung cancer as a result of the failure of the mine operators, who must also bear the blame, because they too had the information, and the Government should not have had to club them into ventilating their mines.” Lung cancer risk for Navajo miners was subsequently reported in 2000 to be nearly 30 times higher than for non-miners.34 The percentage of cancer cases linked to radon exposure was comparable to what Wilhelm Heuper first reported in 1942.
While the Navajos were contributing to the increase of ore production during the 1950s, production of fissionable materials was reaching its height. By the mid-1960s, the U.S. nuclear arsenal contained more than 30,000 warheads.35 This is when President Johnson ended production of highly enriched uranium for weapons and sharply curtailed plutonium production – signaling an end to AEC uranium purchases that would stop by 1971. The once booming uranium market was now stagnant, with some of the oldest and largest companies on the Colorado Plateau pulling out. Between 1961 and 1966, domestic uranium ore production dropped by 50 percent.36
In early March of 1967, the Washington Post ran a series of front-page stories by John Reistrup exposing decades of failure by the U.S. government to prevent what had become a growing epidemic of lung cancers among uranium miners. Keying off Reistrup’s stories, the Post’s editorial board castigated the Johnson Administration and Congress for presiding over “death mines.”37
Moved by the stories, Labor Secretary Willard Wirtz took unilateral action in May of 1967, proposing the first federal standard to limit radiation exposures in U.S. uranium mines. It would reduce the average radon concentrations measured in the mines that year by more than three times. True-to-form, it provoked immediate opposition by the industry and the JCAE, which held 12 days of hearings in an effort to block the Labor Department. Wirtz was undeterred, arguing “ventilation is a cost item. It doesn’t belong on the same balance sheet with cancer.”38 By the late summer the standard was endorsed by the Johnson Administration, but delayed its implementation until 1971.
By this time, the Department of Defense declared that its uranium stockpile goals were met and stopped purchasing uranium. Moreover, Congress authorized a cutback on acquisitions. The AEC would no longer guarantee prices for crude ore and cancelled its exploration campaigns. As a result, the demand for uranium slowed and insecurity crept over the mining industry. The United States would never again experience the enormous uranium boom brought on during the first 30 years of the nuclear arms race.
Even though there was a significant body of evidence spanning decades of deliberate negligence by the U.S. government, federal courts denied claims by the miners and others exposed to radioactive fallout from Nevada nuclear weapons testing, on the grounds of sovereign immunity stating, “all the actions of various governmental agencies complained of by plaintiffs were the result of conscious policy decisions made at high government levels based on considerations of political and national security feasibility factors.”39
It took more than 20 years and a considerable amount of effort by the miners, their families, before the Radiation Exposure Compensation Act was passed in October 1990. The Act offered a formal apology for sending people into harm’s way and provided a one-time compensation to each victim in the amount of $100,000.
Ten years later, Congress passed even more sweeping legislation, known as the Energy Employee Occupational Illness Compensation Program Act. It not only provided compensation for the many thousands of nuclear weapons workers, but also expanded the benefits for uranium miners – increasing the lump sum to $150,000 per person and providing health care. Financial compensation came too little and too late. It would never be enough for an illness and death that could have been prevented.
The legacy of U.S. uranium mining lingers on. More than three billion metric tons of mining and milling wastes were generated in the United States.40 Today, Navajos still live near about one third of all abandoned uranium mines in the United States (~1,200 out of 4,000).41 Only after a concerted effort by Navajo activists to spur congressional investigations in 1993 and 2006, has the U.S. government recently promised to complete remediation of abandoned mines, nearly a century after the first uranium leases were issued on Navajo land.42
Robert Alvarez is a Senior Scholar at IPS, where he is currently focused on nuclear disarmament, environmental, and energy policies. Between 1993 and 1999, Mr. Alvarez served as a Senior Policy Advisor to the Secretary and Deputy Assistant Secretary for National Security and the Environment. While at DOE, he coordinated the effort to enact nuclear worker compensation legislation. In 1994 and 1995, Bob led teams in North Korea to establish control of nuclear weapons materials. He coordinated nuclear material strategic planning for the department and established the department’s first asset management program. Bob was awarded two Secretarial Gold Medals, the highest awards given by the department.
Geopolitical and Cyber Risks to Oil and Gas
Whether an oil and gas company is working in the United States or is spread throughout the world, it will face geopolitical and cyber risks which could affect global energy security.
Geopolitical Risk
There are numerous geopolitical risks for any oil and gas company. Even if a company just works in the United States, it needs to know what is happening in countries all over the world, especially those countries that are large oil and gas producers. Because oil markets are so tightly connected globally, major political events in oil exporting states could seriously affect the price and even availability of oil. An attack on an oil platform in Nigeria, a terrorist event in Iraq, the closing down of port facilities in Libya and many other examples come to mind. Consider the potential effects of a major attack on the Ab Qaiq facility in Saudi Arabia. If this facility is damaged or destroyed on a large scale by rockets or bombs, the world oil market could be out 6-7 million barrels of oil a day- out of the 90-92 millions of barrels a day the world needs. World spare oil production capacity is about 2.3 million barrels a day. It could take some time to get this online. The spare production can be ramped up, but not immediately. Given that the grand majority of excess capacity in the world is located in Saudi Arabia and that this excess capacity could be significantly cut back with damage to Ab Qaiq, the situation is even riskier.
Another major risk nearby is transits through the Straits of Hormuz. About 16-17 million barrels a day goes out of the Straits. Any attempts to close the Straits (even unsuccessful ones) could have significant effects on the prices of various grades of oil. Even with the seemingly warming in relations between the U.S. and Iran, it is still possible that things could take a turn for the worse in the Gulf region. If the present negotiations with Iran break down, tensions could rise to even higher levels than before negotiations began. This could bring discussions of the military option more public. If there is a major conflict involving Gulf countries, the United States and its allies, then all bets are off on where oil prices may go. There could be many scenarios: from oil prices increasing $100 over the pre-conflict base price to well over $200 over the pre-conflict base price.
In many other parts of the world, geopolitical risks going “kinetic” can affect oil markets. Syria is a potential whirlpool of trouble for the entire Middle East. Egypt and Libya are far from stable. Algeria could be heading into some rough times. The Sudan’s will remain problematic and potentially quite violent for some time to come. The East China Sea and South China Sea disputes are not resolved. The Central Sahara could be a source and locale for troubles for some time to come.
Terrorist events can happen anywhere. Google Earth allows terrorists and others to get very close looks at major oil and gas facilities, transport choke points and more. Also, there are not that many tankers plying the vast seas and oceans of the world. Some of the most important routes are between the Gulf region and East Asia and Europe. Others travel from West Africa to Europe, and less so to the United States than before its shale oil revolution. The Mediterranean has many important tanker shipping routes. The Red Sea is a crucial route for both ships going north and south. Over 50 percent of oil trade happens on maritime routes. Many of these tankers cross through vital chokepoints like the Strait of Malacca, the Strait of Hormuz, The Bab al Mandab, The Suez Canal, The Turkish Straits, The Danish Straits, The Panama Canal, and various harbor and river routes where risks may be higher r at sea. Even whilst at sea, ships are at risk as shown by pirate attacks and hijackings off of East Africa, West Africa and previously off of Indonesia. There are about 1,996 crude oil tankers. However, only 623 of these are of the Ultra Large Crude Carrier (ULCC) or Very Large Crude Carrier (VLCC) variety that are the most important for transporting crude oil economically over long distances from the Gulf region to places like China (the biggest importer of oil), the United States, Japan, South Korea, and Europe. VLCCs can carry about 2 million barrels of oil while ULCCs can carry up to 2.3 or, rarely, 2.5 million barrels of oil. Normally these massive ships carry crude oil, but sometimes carry many different types of crude oil. Smaller petroleum tankers may carry both crude and refined products depending on their trade routes and the state of the markets at any times. There are about 493 Suez Max tankers, which can hold about 1 million barrels of oil and refined products and about 408 Afrimax vessels, which hold about 500,000 to 800,000 barrels of crude or refined products. Additionally, there are 417 Panamax vessels, which can carry 300,000 to 500,000 barrels of oil or refined products.
This may seem like a lot of ships to some. However, especially in tight markets, the pressure is immense to keep these ships at sea and to keep them on time. Moreover, there are lots of logistical complexities in trying to keep the crude moving at the right times and to the right places. If anything disturbs this complex economic and logistical ballet of behemoths, then the economic effects could be considerable. If the oil does not arrive on time then refinery production and deliveries of refined products to markets could be disturbed. Most countries have crude and product reserves to handle short term disruptions that may result from tanker losses. If the tanker losses are large or other disruptions occur in the supply chains of crude via ships, then those reserves could be worn down. It takes well over a year to build one of these tankers.
If the market for tankers is soft and some available tankers are moored in port, (such as when close to 500 hundred ships and dozens of tankers were moored off Singapore a few years ago), then the chances are better of getting the shipping logistics back to normal faster. However, problems could still arise in getting ships needed in Houston or Ras Tanura from Singapore. The travel times of these massive ships add considerable costs and disruptions.
When disruptions occur, some crude cargos can change direction and can be sold and resold, depending on the sorts of contracts that are in effect, along the way. Sometimes the disruptions are from political events, such as revolutions, insurrections, civil instability, and natural events like hurricanes and tsunamis. For example, when the tsunami hit Japan on March 11, 2011, many cargos were delayed or reconfigured. However, these sorts of events are different from terrorists blowing up a series of ships, as the psychology is different.
There is a certain amount of flexibility built into crude tanker transport markets, but a larger question is what would happen if many of them were taken out in various parts of the world. Would such a “black swan event” cause great disruptions? This is most likely. The follow on question would be how the tanker and other connected markets would react to this to help resolve the logistical attacks and how this might affect tanker insurance and lease rates.
Given that the crude and other products feed into other supply chains and markets, there could be cascades of disruptions in many parts of the world from a significant attack on even one large VLCC. Attacks on more ships would become increasingly more complex and costly in their effects.
If even one ship is sunk with a missile, the effects on oil markets and the world economy could far outweigh the mere few hundred millions of dollars in value the tanker and its cargo may represent. Ports, pipelines, refineries, tankers and other parts of the oil, transport and other infrastructures could be affected.
The destruction of an oil facility in a sensitive area that may be worth a few billion dollars could have a negative economic impact globally in the hundreds of billions, if not more. Attacks on the Houston Ship Channel, the Louisiana Offshore Oil Port, Ras Tanura in Saudi Arabia, the Jubail Complex in Saudi Arabia, Kharg or Lavan Island in Saudi Arabia could have considerable impacts economically and even militarily.
The impacts of attacks on these facilities would be stronger when oil and tanker markets are tight, and when the world or salient regional economies are growing quickly. An attack on a major tanker route out of Saudi Arabia heading to China or Japan will have a lot less effect on tanker and oil markets when there are excess tankers at anchor, and when there is excess capacity in oil production to make up in a relatively short time than when both tanker and oil markets are tight and there is little excess capacity. The less elastic the markets, the more effect any attacks will have. If a terrorist group wanted to have the most impact on the world economy it would likely attack in times of high growth in various important economies and when there is little excess oil capacity and no spare tankers. Often these three markets are tied together. When the global economy is growing quickly oil markets are under stress. When oil markets are under stress then tanker markets are stressed.
Looking to the future, some countries could be facing political turmoil such as Russia, Saudi Arabia, Iran, and Venezuela. This turmoil is not deterministic, but it is also not completely out of the bounds of probability. Depending on the type of turmoil, damage, and loss of production and export capacity, these events could have significant effects on world oil markets.
If such turmoil is going to happen, it is better for the world oil markets and the world economy that these happen during times of greater excess production and export capacity than the losses in oil production and export capacity from the turmoil. The worst of all possible combinations would be the loss of production and export capacity during very tight market times in a country where most of the excess capacity is found, which is in Saudi Arabia. If the world economy is growing quickly all around, then the effects of such turmoil will be far greater than if the world economy is in a slow growth period.
There are also regional aspects; during the 2011 Libyan Revolution, Europe’s economy was starting to dig itself out of a deep recession that had affected most European countries. Most of Libya’s oil that was cut off for a while was supposed to go to European countries, especially Italy, Spain, and France. Libyan oil production was about 1.7 million barrels a day until the civil war/ revolution began in February 2011. About 1.5 million barrels a day was exported. After the beginning of the conflict, production dropped to about 200,000 barrels a day, and did not recover until the post-civil war “recovery” that began about 8 months later. In the period between the start of the civil war/ revolution and the start of the ramp up, oil production dropped to 100,000 barrels a day and then on down to about zero barrels a day. Very little was exported during the times of the conflict. The fact that many European economies were growing slowly, or in some cases not growing at all, helped alleviate the potential effects of the cutting off of oil shipped from Libya. About 85 percent of Libya’s oil exports before the conflict went to Europe. The countries that relied considerably on Libyan were Italy, Austria, Ireland, Switzerland, Spain, Austria, and France. However, most of these were in slow-growth phases due to the ongoing recession and growing financial crises in their countries. The tanker markets were also soft and there was significant excess capacity of oil production in Saudi Arabia. The Saudis tried to backfill some orders for Libyan crude, but some of these did not work out well due to the heavier, sourer nature of the available Saudi crude compared to the usually light, sweet crude out of Libya. Switzerland is different from the other European countries as its “consumption” of Libyan oil was mostly for trading the oil in hedge funds and the big commodity firms in Geneva. The rest of these countries needed it for their overall economic needs.
Libyan crude production increased to about 1.4-1.5 million barrels a day until further problems occurred in mid-2013 with strikes at the ports and some energy facilities. Production is now down to 200,000 barrels per day. The effects on prices has been a lot less this time than during the civil war due to new, more flexible trading arrangements and better planning for such contingencies out of Libya, but also because the European economy and tanker markets remain weak.
Many Americans may think that they are relatively immune from geopolitical turmoil in oil disruptions because of the shale oil and gas revolution in the United States and Canada. However, there is potential for the increase in trade of oil with Canada which will result in greater access to oil and gas. But, this will not buffer the United States from the vagaries of oil prices caused by geopolitical events. This is mainly due to oil being a globally traded commodity.
Unlike the oil industry, the natural gas industry is not fully globally integrated, but it looks to be heading that way. As more countries invest in both conventional and unconventional reserves production, the development of LNG (Liquefied Natural Gas) export and import facilities, and expansions of major international pipeline networks, the world natural gas market will have some great changes. Some of these may include the convergence of prices of natural gas globally. Recent prices of natural gas (FOB – Freight on Board, where the buyer pays for transport costs) in China were about $15 per MMBTU (Million British Thermal Units), a common measurement of natural gas amounts. In Japan they were in the $16-17 ranger per MMTBTU. In many parts of Western Europe LNG (FOB) prices were about $9-11 per MMBTU. Natural gas in the United States recently has sold for about $3 per MMBTU. Qatar could sell at cost for much lower, as it sells to the United States for about $3 MMBTU similar LNG that it sells to China and Japan for much higher prices. With the convergence of prices, the lower cost countries will likely be the survivors. Others may have to drop out if they have to export the LNG at a loss, unless the country subsidizes these exports, which would be problematic under the World Trade Organization (WTO) agreements.
Those countries that develop their LNG export facilities the fastest will capture more of the most important markets (such as Japan, South Korea, and especially the potentially gigantic market in China), than those countries that doddle along in their decisions to export or not. The future of global gas markets is more of a very competitive and very expensive 4D chess game played by very powerful people, rather than just some engineering or economics exercise as some look at it.
As the now regional and segmented natural gas markets develop into global integrated markets, they will become more efficient and regional prices will start to converge toward a global price, much like oil. As the global natural gas markets develop, there will be more spot markets developed and less need for long term contracts in many instances. For decades, oil and gas prices were linked. As a global natural gas market develops, and especially with the further spread of the shale gas revolution, fewer and fewer natural gas contracts will be linked to oil prices. However, this integration of the natural gas industry globally also brings the risk of terrorist or political driven turmoil at or near LNG ports, LNG ships, and even in the market trading centers in places far removed from the United States. The more globally integrated the natural gas markets are, the more likely reverberations to prices will occur globally, rather than just locally. It is sort of like dropping a large rock in a pond with many barriers compared to dropping a large rock in a pond without many barriers in it. The waves will have more extensive effects without the barriers.
At the moment, the United States has a special domestic market that is fairly immune from outside events, as one would expect that they would happen in Canada, the United States’ major natural gas trading partner. This will change over time as U.S. natural gas markets get more connected with the world. The United States have some buffers during difficult gas shocks globally due to massive shale gas reserves. However, it could take a long time for these reserves to surge into the domestic markets to make up for the price increases.
Large profits can be made in exporting natural gas to places like China, Japan, South Korea, and Western Europe where gas prices are much higher. Over time those price differentials will decline because more LNG and piped gas will be flowing to the more profitable markets, hence putting pressure on prices. Global gas prices will tend to converge, but not entirely given different extraction, production, liquefaction and gasification prices.
With greater integration there are also new risks to consider. Some of these include potential attacks on major LNG facilities as natural gas becomes a more vital part of the world economy and some countries. There are also increased risks that as the global markets get more integrated in natural gas, events distant from the United States could affect prices in the United States much like what happens now with oil markets.
There are great profits to be made from exporting the potentially massive amounts of natural gas (mostly shale gas), from the United States into these newly developing world markets. (The greatest profits can be made in the first years of the development of these markets prior to the lowering of prices in Asia, Europe and higher priced areas as the markets get integrated.)
However, nothing is ever certain and some planning and emergency regulations may be required to help potential shocks from entering U.S. markets. Complete immunity is not possible when a market is globalized, but with proper consideration risks might be mitigated. A very large natural gas strategic reserve system might be best built and filled when the natural gas is cheap for times when it may be less accessible (likely for the short run given how quickly shale gas pads and production can be set up).
Cyber Risks
According to Europol there have been many cyber-raids in 2012 on logistics and computer networks connected to container ships by criminal gangs to obtain the illegal drugs they had hidden in the holds of the ship. The gang truck drivers were able to find the containers, get the security codes, and were able to get the drugs off the ship without being caught. This could be the start of far more serious cyber-attacks on shipping and maritime logistical networks. The oil and gas industry is information intensive and it is hard to get around that. Computer systems, the internet, and other cyber-based devices and operations are key elements to the operations of the industry. For example, Saudi Aramco and many other oil companies in the Middle East region have been cyber-attacked in recent years.
In addition, cyber-attacks have both financial and real effects, including distortions in the prices of oil and gas. Hacking into the derivatives and futures markets could wreak serious havoc on the industry. Real effects could include attacks on SCADA (Supervisory Control and Data Acquisition) systems that control oil and gas pipelines. SCADA is also used in refinery operations. If a container ship can be hacked, how far off is it when an LNG or oil tanker is taken over or hacked? Tanker traffic is often controlled and monitored via computer systems and the internet. Clever cyber warriors and others are likely trying to crack these systems (or potentially have even cracked them at times), but the industry would rather not discuss such events. It may be entirely possible to use something like STUXNET on affected SCADA systems to send the wrong signals to those trying to monitor the complex logistics of the shipping. A ship may be seen on the company’s monitor being one place, whereas it might be somewhere else. That is anyone’s guess, but I suggest that is not impossible. The new pirates attacking tankers may be cyber-pirates sending in malicious code, not just the barefoot Somalis and others tossing hook anchors on to the stern of the tanker and climbing up.
Cyber risk can also have considerable effects on the overall supply chains for the oil and gas industry. To get an oil rig, a refinery, a series of pipelines up and running takes a massive administrative supply chain effort that could involve sometimes hundreds if not thousands of subcontractors and suppliers that have to get things done in a specific order and on time. Anyone who has built a house or even had a kitchen remodeled knows how important it is to get the carpenters, electricians, masons, and roofers to be on schedule and in the right order. Now consider the complexity of getting all the right people, equipment and information on schedule and in the right order in the build out of a complex oil rig in 10,000 feet of water 150 miles at sea with millions of dollars (and maybe lives) at risk due to any scheduling mistakes.
A cyber-attack on major refineries and pipeline systems could bring costs that may seem unthinkable at the moment. However, this could just be a matter of time if the industry does not constantly update its protective systems and understanding of the risks. The industry remains constantly vigilant as hackers and cyber-warriors like the SEA (Syrian Electronic Army) are always looking for opportunities to attack. Constant vigilance will not be enough if one of these attackers gets “lucky” and gets through. The sophistication of cyber warriors and hackers is not static, nor should the sophistication of the oil and gas industry to counter these threats be static.
Note: All opinions expressed are those of the author alone. Sources supplied upon request.
Paul Sullivan is the Adjunct Senior Fellow for Future Global Resources Threats at the Federation of American Scientists and a Professor of Economics at the Eisenhower School at the National Defense University. He is also an Adjunct Professor of Security Studies at Georgetown University and a columnist for newspapers in Turkey and Mongolia.
Dr. Sullivan is an expert on resource security issues, with a special focus on the nexus of energy, water, food and land. He is also an expert on issues related to the economics, politics, and militaries in the Middle East and North Africa.