Mixed Messages On Trump’s Missile Defense Review
President Trump personally released the long-overdue Missile Defense Review (MDR) today, and despite the document’s assertion that “Missile Defenses are Stabilizing,” the MDR promotes a posture that is anything but.
Firstly, during his presentation, Acting Defense Secretary Shanahan falsely asserted that the MDR is consistent with the priorities of the 2017 National Security Strategy (NSS). The NSS’ missile defense section notes that “Enhanced missile defense is not intended to undermine strategic stability or disrupt longstanding strategic relationships with Russia or China.” (p.8) During Shanahan’s and President Trump’s speeches, however, they made it clear that the United States will seek to detect and destroy “any type of target,” “anywhere, anytime, anyplace,” either “before or after launch.” Coupled with numerous references to Russia’s and China’s evolving missile arsenals and advancements in hypersonic technology, this kind of rhetoric is wholly inconsistent with the MDR’s description of missile defense being directed solely against “rogue states.” It is also inconsistent with the more measured language of the National Security Strategy.
Secondly, the MDR clearly states that the United States “will not accept any limitation or constraint on the development or deployment of missile defense capabilities needed to protect the homeland against rogue missile threats.” This is precisely what concerns Russia and China, who fear a future in which unconstrained and technologically advanced US missile defenses will eventually be capable of disrupting their strategic retaliatory capability and could be used to support an offensive war-fighting posture.
Thirdly, in a move that will only exacerbate these fears, the MDR commits the Missile Defense Agency to test the SM-3 Block IIA against an ICBM-class target in 2020. The 2018 NDAA had previously mandated that such a test only take place “if technologically feasible;” it now seems that there is sufficient confidence for the test to take place. However, it is notable that the decision to conduct such a test seems to hinge upon technological capacity and not the changes to the security environment, despite the constraints that Iran (which the SM-3 is supposedly designed to counter) has accepted upon its nuclear and ballistic missile programs.
Fourthly, the MDR indicates that the United States will look into developing and fielding a variety of new capabilities for detecting and intercepting missiles either immediately before or after launch, including:
- Developing a defensive layer of space-based sensors (and potentially interceptors) to assist with launch detection and boost-phase intercept.
- Developing a new or modified interceptor for the F-35 that is capable of shooting down missiles in their boost-phase.
- Mounting a laser on a drone in order to destroy missiles in their boost-phase. DoD has apparently already begun developing a “Low-Power Laser Demonstrator” to assist with this mission.
There exists much hype around the concept of boost-phase intercept—shooting down an adversary missile immediately after launch—because of the missile’s relatively slower velocity and lack of deployable countermeasures at that early stage of the flight. However, an attempt at boost-phase intercept would essentially require advance notice of a missile launch in order to position US interceptors within striking distance. The layer of space-based sensors is presumably intended to alleviate this concern; however, as Laura Grego notes, these sensors would be “easily overwhelmed, easily attacked, and enormously expensive.”
Additionally, boost-phase intercept would require US interceptors to be placed in very close proximity to the target––almost certainly revealing itself to an adversary’s radar network. The interceptor itself would also have to be fast enough to chase down an accelerating missile, which is technologically improbable, even years down the line. A 2012 National Academy of Sciences report puts it very plainly: “Boost-phase missile defense—whether kinetic or directed energy, and whether based on land, sea, air, or in space—is not practical or feasible.”
Overall, the Trump Administration’s Missile Defense Review offers up a gamut of expensive, ineffective, and destabilizing solutions to problems that missile defense simply cannot solve. The scope of US missile defense should be limited to dealing with errant threats—such as an accidental or limited missile launch—and should not be intended to support a broader war-fighting posture. To that end, the MDR’s argument that “the United States will not accept any limitation or constraint” on its missile defense capabilities will only serve to raise tensions, further stimulate adversarial efforts to outmaneuver or outpace missile defenses, and undermine strategic stability.
During the upcoming spring hearings, Congress will have an important role to play in determining which capabilities are actually necessary in order to enforce a limited missile defense posture, and which ones are superfluous. And for those superfluous capabilities, there should be very strong pushback.
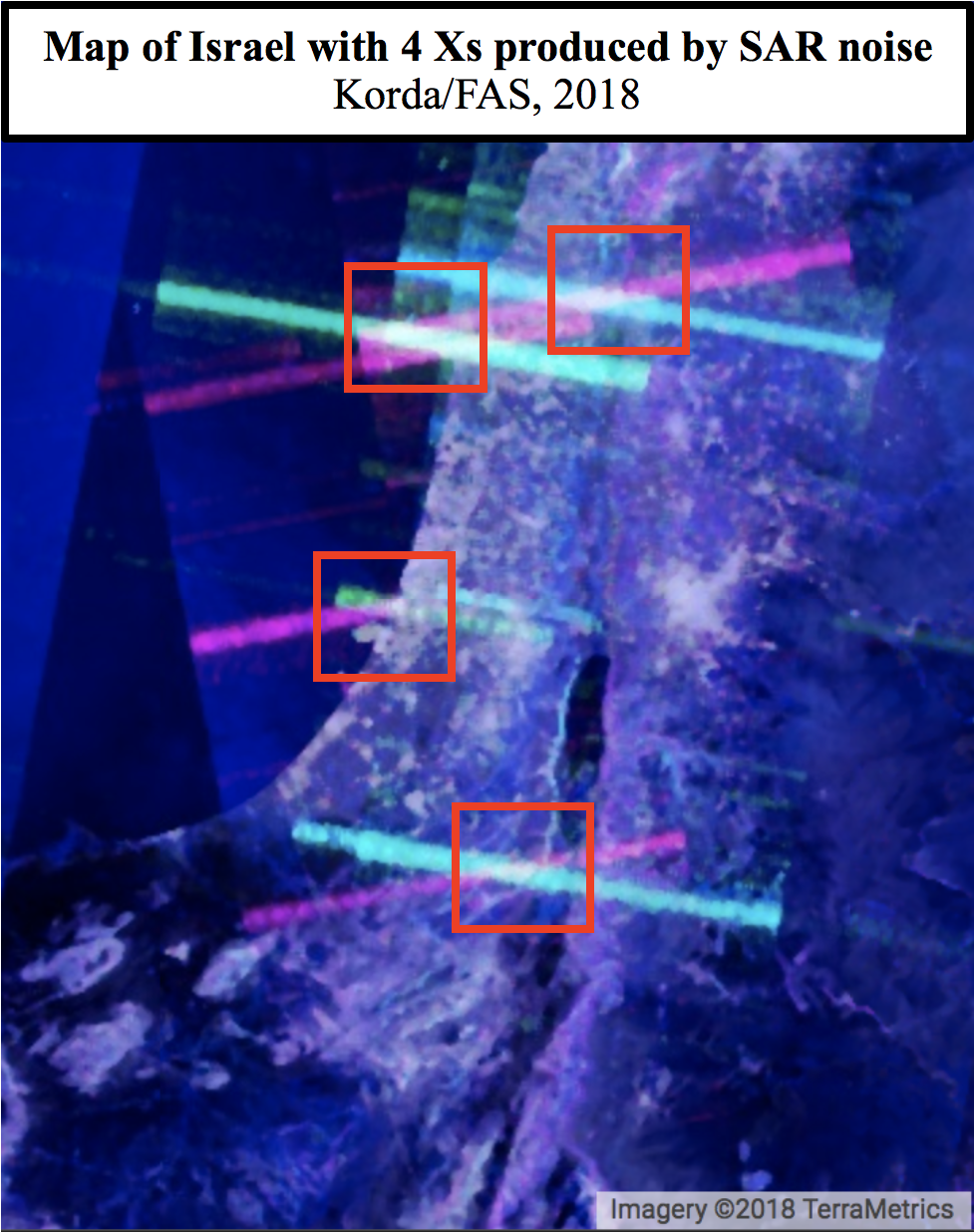
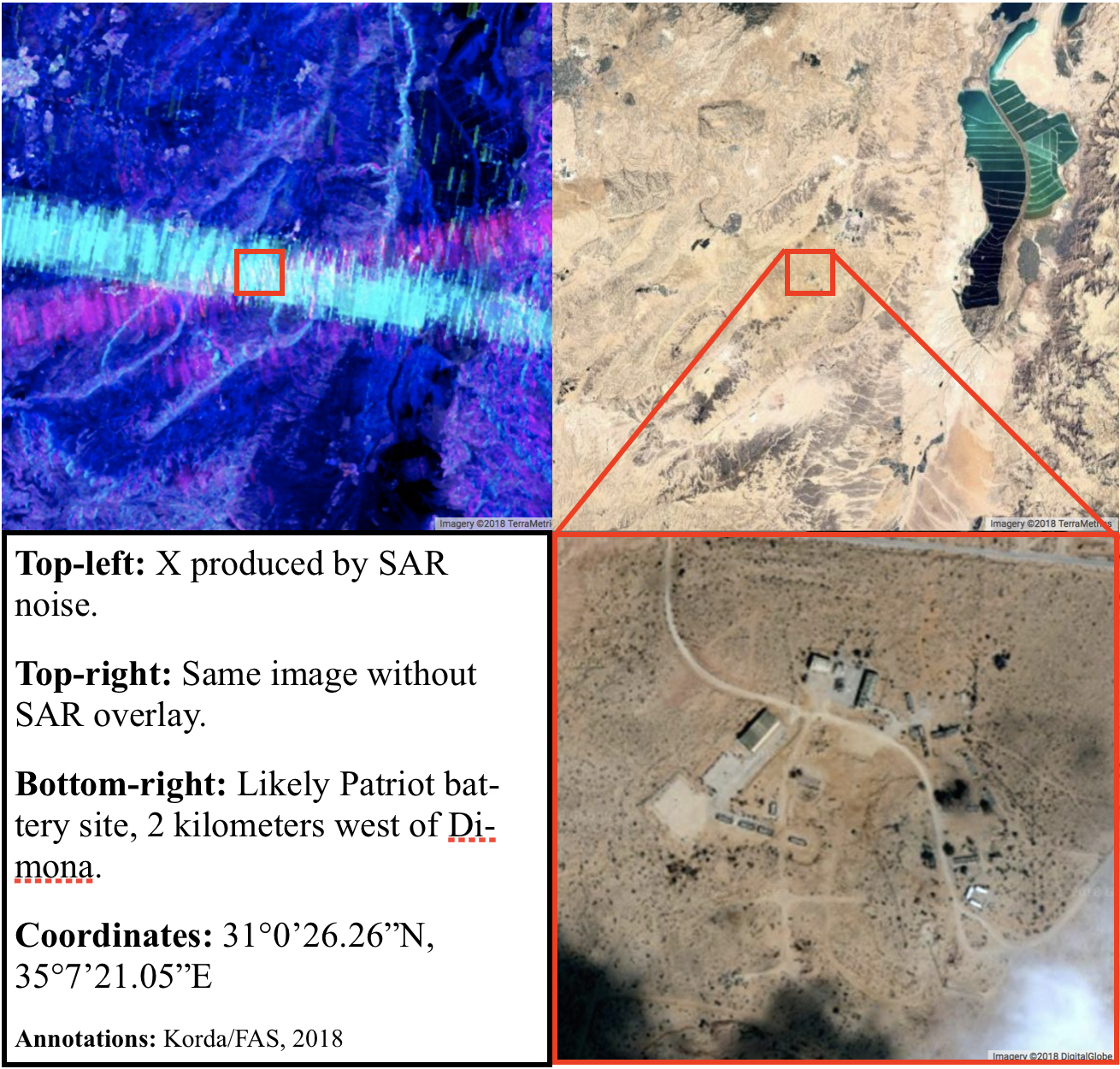
An X reveals a Diamond: locating Israeli Patriot batteries using radar interference
Amid a busy few weeks of nuclear-related news, an Israeli researcher made a very surprising OSINT discovery that flew somewhat under the radar. As explained in a Medium article, Israeli GIS analyst Harel Dan noticed that when he accidentally adjusted the noise levels of the imagery produced from the SENTINEL-1 satellite constellation, a bunch of colored Xs suddenly appeared all over the globe.
SENTINEL-1’s C-band Synthetic Aperture Radar (SAR) operates at a centre frequency of 5.405 GHz, which conveniently sits within the range of the military frequency used for land, airborne, and naval radar systems (5.250-5.850 GHz)—including the AN/MPQ-53/65 phased array radars that form the backbone of a Patriot battery’s command and control system. Therefore, Harel correctly hypothesized that some of the Xs that appeared in the SENTINEL-1 images could be triggered by interference from Patriot radar systems.
Using this logic, he was able to use the Xs to pinpoint the locations of Patriot batteries in several Middle Eastern countries, including Qatar, Bahrain, Jordan, Kuwait, and Saudi Arabia.
Harel’s blog post also noted that several Xs appeared within Israeli territory; however, the corresponding image was redacted (I’ll leave you to guess why), leaving a gap in his survey of Patriot batteries stationed in the Middle East.
This blog post partially fills that gap, while acknowledging that there are some known Patriot sites—both in Israel and elsewhere around the globe—that interestingly don’t produce an X via the SAR imagery.
All of these sites were already known to Israel-watchers and many have appeared in news articles, making Harel’s redaction somewhat unnecessary—especially since the images reveal nothing about operational status or system capabilities.
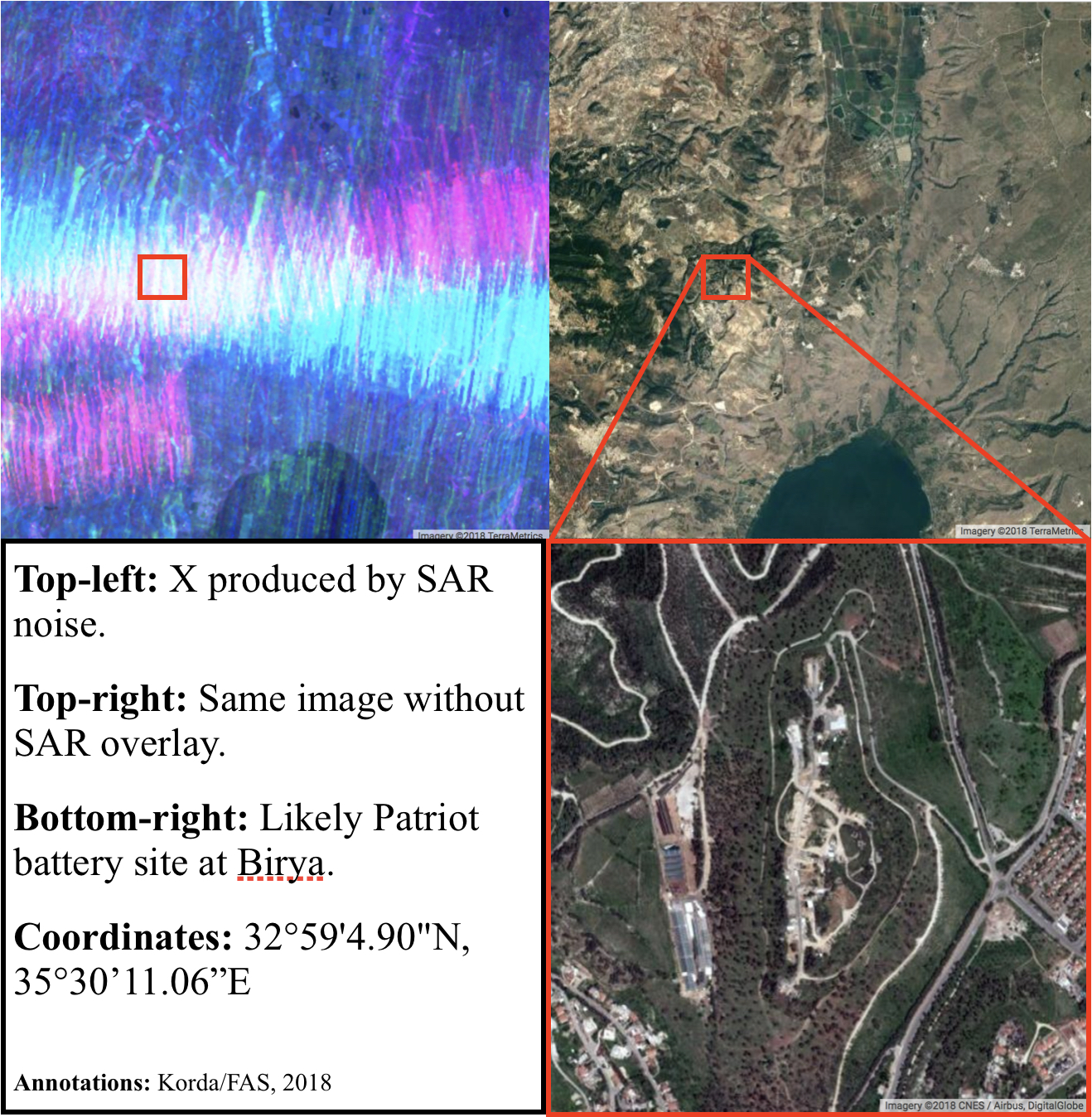
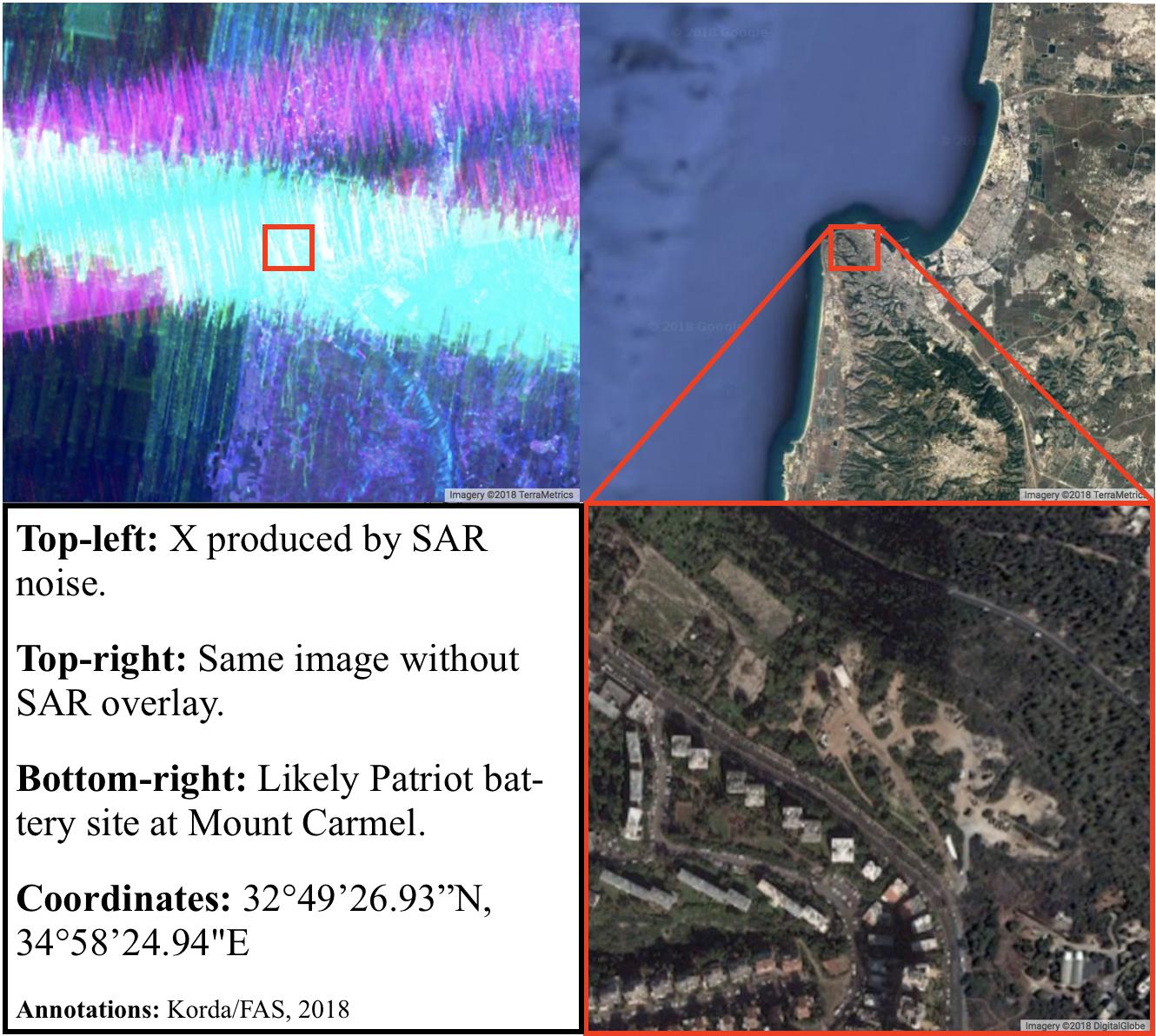
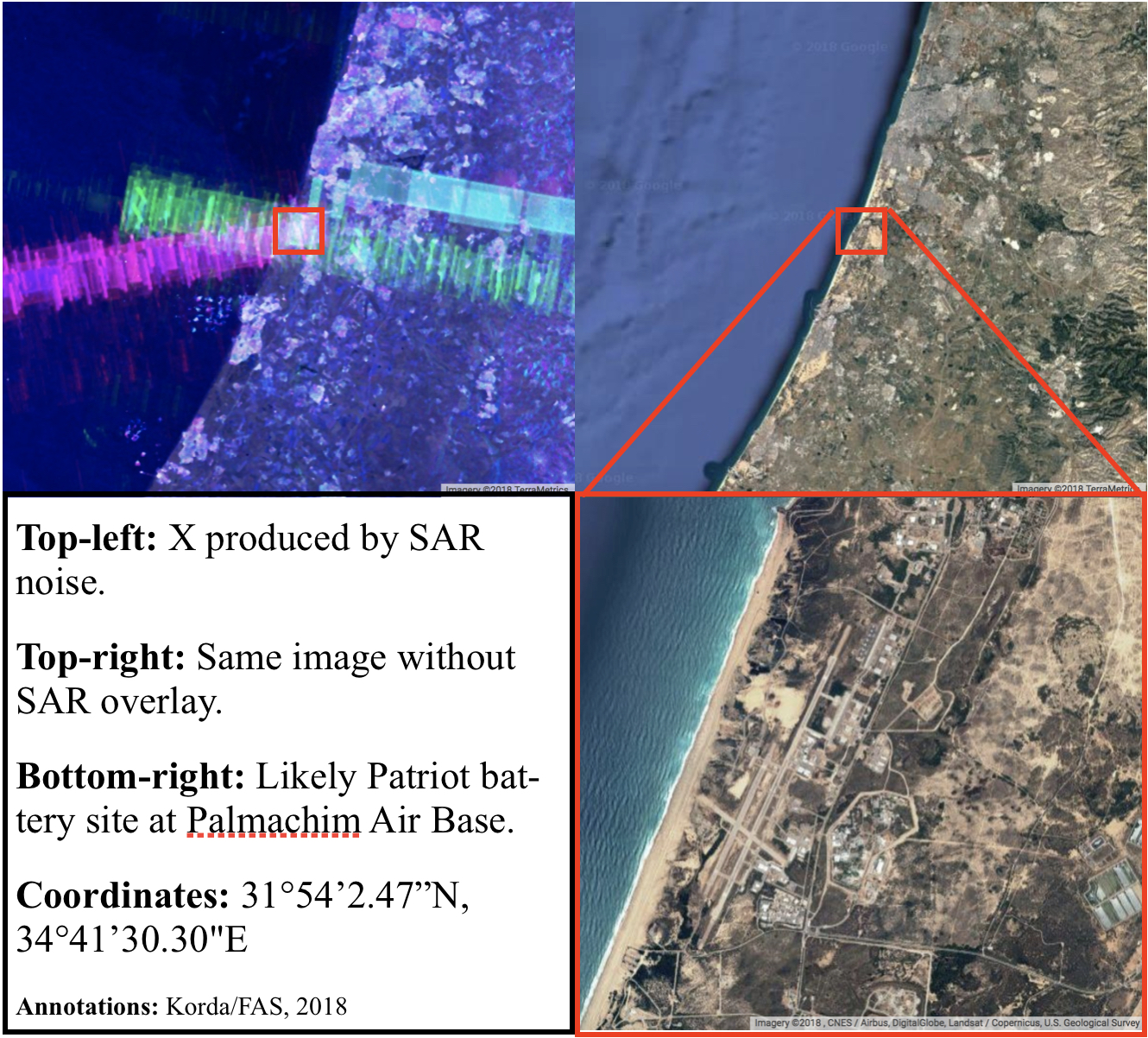
Looking at the map of Israel through the SENTINEL-1 SAR images, four Xs are clearly visible: one in the Upper Galilee, one in Haifa, one near Tel Aviv, and one in the Negev. All of these Xs correspond to likely Patriot battery sites, which are known in Israel as “Yahalom” (יהלום, meaning “Diamond”) batteries. Let’s go from north to south.
The northernmost site is home to the 138th Battalion’s Yahalom battery at Birya, which made news in July 2018 for successfully intercepting a Syrian Su-24 jet which had reportedly infiltrated two kilometers into Israeli airspace before being shot down. Earlier that month, the Birya battery also successfully intercepted a Syrian UAV which had flown 10 kilometers into Israeli airspace.
The Yahalom battery in the northwest is based on one of the ridges of Mount Carmel, near Haifa’s Stella Maris Monastery. It is located only 50 meters from a residential neighborhood, which has understandably triggered some resentment from nearby residents who have complained that too much ammunition is stored there and that the air sirens are too loud.
The X in the west indicates the location of a Yahalom site at Palmachim air base, south of Tel Aviv, where Israel conducts its missile and satellite launches. In March 2016, the Israeli Air Force launched interceptors as part of a pre-planned missile defense drill, and while the government refused to divulge the location of the battery, an Israeli TV channel reported that the drill was conducted using Patriot missiles fired from Palmachim air base.
Finally, the X in the southeast sits right on top of the Negev Nuclear Research Centre, more commonly known as Dimona. This is the primary facility relating to Israel’s nuclear weapons program and is responsible for plutonium and tritium production. The site is known to be heavily fortified; during the Six Day War, an Israeli fighter jet that had accidentally flown into Dimona’s airspace was shot down by Israeli air defenses and the pilot was killed.
The proximity of the Negev air defense battery to an Israeli nuclear facility is not unique. In fact, the 2002 SIPRI Yearbook suggests that several of the Yahalom batteries identified through SENTINEL-1 SAR imagery are either co-located with or located close to facilities related to Israel’s nuclear weapons program. The Palmachim site is near the Soreq Centre, which is responsible for nuclear weapons research and design, and the Mount Carmel site is near the Yodefat Rafael facility in Haifa—which is associated with the production of Jericho missiles and the assembly of nuclear weapons—and near the base for Israel’s Dolphin-class submarines, which are rumored to be nuclear-capable.
Google Earth’s images of Israel have been intentionally blurred since 1997, due to a US law known as the Kyl-Bingaman Amendment which prohibits US satellite imagery companies from selling pictures that are “no more detailed or precise than satellite imagery of Israel that is available from commercial sources.” As a result, it is not easy to locate the exact position of the Yahalom batteries; for example, given the number of facilities and the quality of the imagery, the site at Palmachim is particularly challenging to spot.
However, this law is actually being revisited this year and could soon be overturned, which would be a massive boon for Israel-watchers. Until that happens though, Israel will remain blurry and difficult to analyze, making creative OSINT techniques like Harel’s all the more useful.
—–
Sentinel-1 data from 2014 onwards is free to access via Google Earth Engine here, and Harel’s dataset is available here.
BMD Flight Test Schedule Must Be Unclassified
Earlier this year, the Department of Defense classified the schedule of flight tests of ballistic missile defense systems, even though such information had previously been unclassified and publicly disclosed.
Rejecting that move, Congress has now told the Pentagon’s Missile Defense Agency that the flight test schedule must be unclassified.
A new provision in the FY2019 national defense authorization act (sect. 1681) would “require that MDA make the quarter and fiscal year for execution of planned flight tests unclassified.”
“Together with the release of each integrated master test plan of the Missile Defense Agency, and at the same time as each budget of the President is submitted to Congress…, the Director of the Missile Defense Agency shall make publicly available a version of each such plan that identifies the fiscal year and the fiscal quarter in which events under the plan will occur,” the provision states.
This legislative action will effectively override the classification judgment of the executive branch. That is something that Congress rarely does and that the executive branch regards as an infringement on its authority.
Missile Defense Flight Test Secrecy May Be Reversed
Some members of the House Armed Services Committee want the Pentagon’s Missile Defense Agency to return to its previous practice of publicly disclosing information about planned flight tests of ballistic missile defense (BMD) systems and components.
Earlier this year, the Department of Defense said that information about BMD flight tests, objectives and schedules was now classified, even though such information had routinely been made public in the past. (DOD Classifies Missile Defense Flight Test Plans, Secrecy News, March 5, 2018).
But in their initial markup of the FY2019 National Defense Authorization Act, members of the House Armed Services Strategic Forces Subcommittee said that the new secrecy was unacceptable, at least with respect to the test schedule.
They directed that “Together with the release of each integrated master test plan of the Missile Defense Agency, the Director of the Missile Defense Agency shall make publicly available a version of each such plan that identifies the fiscal year and the fiscal quarter in which events under the plan will occur.”
The pending provision would “require that MDA make the quarter and fiscal year for execution of planned flight tests unclassified.” (h/t Kingston Reif)
Aside from the merits of the House language, it represents a noteworthy legislative intervention in national security classification policy.
Under other circumstances, the executive branch might consider it an intolerable infringement on its authority for Congress to require information to be unclassified over and against an agency’s own judgment or preference.
But in the context of the context of the ambitious and contentious defense authorization act — which among other things would establish a new U.S. Space Command under U.S. Strategic Command — this particular dispute over classification authority recedes into comparative insignificance.
Somewhat relatedly, the Joint Chiefs of Staff have updated DoD doctrine on space operations, with an expanded discussion of natural and man-made threats.
“Our adversaries’ progress in space technology not only threatens the space environment and our space assets but could potentially deny us an advantage if we lose space superiority.”
The doctrine describes general approaches to defending against threats to space-based assets, including defensive operations, reconstitution, and enhanced resilience through distribution, proliferation and deception. See Joint Publication (JP) 3-14, Space Operations, 10 April 2018.
An Airborne Defense Against North Korean ICBMs?
Could an airborne network of drone-based interceptors effectively defend against the launch of North Korean ballistic missiles? A recent assessment by physicists Richard L. Garwin and Theodore A. Postol concludes that it could.
“All of the technologies needed to implement the proposed system are proven and no new technologies are needed to realize the system,” they wrote.
Their concept envisions the deployment of a number of Predator B drones loitering outside of North Korean airspace each bearing two boost-phase intercept missiles.
“The baseline system could technically be deployed in 2020, and would be designed to handle up to 5 simultaneous ICBM launches.”
“The potential value of this system could be to quickly create an incentive for North Korea to take diplomatic negotiations seriously and to destroy North Korean ICBMs if they are launched at the continental United States.”
See Airborne Patrol to Destroy DPRK ICBMs in Powered Flight by R.L. Garwin and T.A. Postol, November 26, 2017.
The asserted role of such a system in promoting diplomatic negotiations rests on certain assumptions about how it would be perceived and evaluated by North Korea that are not addressed by the authors here.
DOD Classifies Missile Defense Flight Test Plans
The Department of Defense has decided to classify previously public information regarding future flight tests of ballistic missile defense systems and components.
Information about pending missile defense flight tests, their objectives, and their timing had previously been included in each year’s budget request documents. But that is no longer the case, and such information was withheld from the FY 2019 Missile Defense Agency RDT&E budget book that was published last month.
“Due to the need to safeguard critical defense information, the DOD will not provide timing or test details in advance beyond the required safety notifications for any planned flight tests,” Lt. Gen. Sam Greaves told Jason Sherman of InsideDefense, who noticed the newly restrictive disclosure practice. See “DOD now treating missile defense flight test plans — once public — as classified” by Jason Sherman, Inside the Pentagon, March 1 (subscription req’d).
Classification of flight test information makes it harder for outside observers and overseers — not just foreign intelligence services — to monitor the progress of US ballistic missile defense programs. The Missile Defense Agency’s specific justification for classifying previously unclassified categories of flight test information has not been publicly explained.
JASON on BMD Midcourse Discrimination (2010)
A comprehensive defense against intercontinental ballistic missiles remains difficult — and perhaps impossible — for several reasons, including the difficulty of achieving “midcourse discrimination” to identify weaponized payloads in a cloud of debris or decoys.
A newly released summary of a classified 2010 report on the subject prepared by the JASON scientific advisory panel explains the issue.
“In the context of missile defense, to discriminate is to distinguish among lethal RVs [reentry vehicles] in mid-course flight that should be targeted by defensive kill vehicles, and non-lethal accompanying objects, whether deliberate countermeasures such as decoys or objects that usually accompany a missile launch, such as booster stage and rocket fuel tanks. Even in the absence of countermeasures, discrimination is still necessary to distinguish RVs from these launch-associated objects.”
“Discrimination of countermeasures is a stringent challenge, because given a reasonable amount of time, money, initiative, and expertise, the offense can (in principle) field countermeasures that the defense cannot handle at any reasonable marginal cost.”
See MDA Discrimination (executive summary), JASON report JSR-10-620, August 3, 2010, released under the Freedom of Information Act on October 3, 2016.
The JASON authors found that the Pentagon’s Missile Defense Agency (MDA) was not well-equipped to address this fundamental problem.
“MDA today has a good record of intercepting RVs, but under conditions that often do not challenge the discrimination capabilities of the missile defense system.”
Even the scope of the discrimination problem is not entirely clear, the JASONs said at the time. “Much remains to be learned about the practical feasibility and effectiveness of countermeasure threats.”
MDA itself “is not agile and flexible, and it may have trouble responding to opponents’ timelines for developing and fielding decoys and other countermeasures,” the JASONs said.
The JASON report recommended that MDA incorporate critical reviews of its programs by independent experts, establish a countermeasures test program through an independent agency, and work more closely with intelligence agencies on analyzing foreign missile threats and countermeasures. It was not immediately clear if the recommendations had been acted upon.
Intelligence for Air and Missile Defense
A new U.S. Army manual addresses the challenges of intelligence support for air and missile defense programs.
“A large number of adversary countries possess or are trying to acquire TBMs [tactical ballistic missiles] and Advanced Air Breathing Threats (ABTs) (i.e. Fixed-Wing (FW) aircraft, Rotary-Wing (RW) aircraft, Unmanned aircraft systems (UAS), Anti-Radiation Missiles (ARMs), and Cruise Missiles (CMs)), for prestige and/or military purposes,” the Army manual stated.
“These aerial and TBM threats have the potential to give the adversary a military advantage against the United States (US) and multinational forces. The threat the adversary presents is a complex, multi-dimensional, intelligence problem.”
To meet this emerging threat, the Army prescribes an Air and Missile Defense (AMD) Intelligence Preparation of the Battlefield (IPB) process, as outlined in the manual. See Air and Missile Defense Intelligence Preparation of the Battlefield, ATP 3-01.16, March 31, 2016.
“AMD IPB identifies facts and assumptions about the battlefield environment and the air and missile defense threat. AMD IPB determines enemy air and missile defense courses of action (COAs), their associated branches and sequels, and describes the operating environment for air and missile defense operations. This supports commander and staff planning and the development of friendly COAs.”
“Applied properly, AMD IPB provides for the timely and effective neutralization and/or destruction of the aerial and TBM threat, while minimizing the requirement for friendly AMD assets. ”
Air and missile defense systems may be vulnerable to attack through cyberspace, the Army manual noted, so consideration should be given to “what mitigations can be put into effect to limit or negate the effects of an attempted cyber-attack on the AMD system.”