USAF Updates Policy on Conscientious Objectors
There may be some US Air Force personnel who are dismayed by the rising number of civilian casualties caused by US air strikes in Syria and Iraq. Others may consider the dropping of a 22,000 pound bomb in Afghanistan yesterday — announced by press release — to be mindless or vulgar.
But of course such critical sentiments, if they exist, would not be sufficient to qualify those who hold them as conscientious objectors (COs). That requires categorical opposition to any and all military action.
“The Air Force does not consider members who believe they can choose the war in which they will participate as COs under the law. The objection must be to all wars rather than to a specific war,” according to an Air Force policy that was updated last week.
On the other hand, a sense of internal conflict is not necessarily inconsistent with conscientious objector status.
Likewise, “A belief in a theocratic or spiritual war between the powers of good and evil does not constitute a [disqualifying] willingness to participate in war within the meaning of this instruction,” the new Air Force policy said. See Procedures for Applying as a Conscientious Objector, Air Force Instruction 36-3204, April 6, 2017.
It could not immediately be learned how many, if any, members of the US Air Force currently have conscientious objector status.
In the absence of a compulsory draft, it is unclear why anyone who is opposed to all wars would enlist in the Air Force in the first place. But the new policy allows for the possibility of conscientious objector beliefs that “crystallized after receipt of an induction notice.”
US Military Advantage in Cyberspace is Challenged
The superiority of the US military in cyberspace, which once could be taken for granted, is gradually eroding, says an Army Field Manual published this week.
In the past decade, “U.S. forces dominated cyberspace and the electromagnetic spectrum (EMS) in Afghanistan and Iraq against enemies and adversaries lacking the technical capabilities to challenge our superiority in cyberspace.”
“However, regional peers have since demonstrated impressive capabilities in a hybrid operational environment that threaten the Army’s dominance in cyberspace and the EMS,” according to the new Field Manual.
“Rapid developments in cyberspace and the EMS will challenge any assumptions of the Army’s advantage in this domain. While it cannot defend against every kind of intrusion, the Army must take steps to identify, prioritize, and defend its most important networks and data.”
The underlying principles of US Army operations in cyberspace were described in the new Field Manual 3-12, Cyberspace and Electronic Warfare Operations, 11 April 2017 (unclassified, 108 pages).
USAF Adopts More Expansive Disclosure Policy
The US Air Force should practice an information policy of “maximum disclosure, minimum delay,” says a newly revised Air Force directive. See Air Force Instruction 35-107, Public Web and Social Communication, 15 March 2017.
“The free flow of information between the government and the public is essential to a democratic society. It is also essential that the government minimize the federal paperwork burden on the public, minimize the cost of its information activities and maximize the usefulness of government information,” the Instruction said.
Information that is classified, inaccurate, or obscene is not to be posted. But Air Force websites should maintain online reading rooms for information “that has been requested via FOIA or could be requested via FOIA [emphasis added].”
Furthermore, “the Air Force views personal Web sites and weblogs positively, and it respects the right of Airmen to use them as a medium of self-expression.”
By itself, the new policy does not mean that the Air Force is now practicing maximum disclosure or that it will necessarily do so in the future. The policy is not self-enforcing.
Still, it represents an official statement of Air Force values, and it therefore provides a point of leverage that can be used by anyone, in the service or among the public, who would seek to uphold those values in practice.
The new version of the Instruction contrasts with the previous version of AFI 35-107 that was released in 2009 and that took a notably less upbeat and more restrictive approach to public disclosure of Air Force information.
Survival and Resistance Under Extreme Conditions
Sometimes eating bugs may be the right thing to do.
“When food is limited and insects are available, they can become a valuable food source.”
That bit of practical wisdom comes from a new US Air Force Handbook on Survival Evasion Resistance Escape (SERE) Operations that was published this week.
However, “Caterpillars with hairs should be avoided. If eaten, the hairs may become lodged in the throat causing irritation or infection.”
More promisingly, “The praying mantis. . . contains 58 percent protein, 12 percent fat, three percent ash, vitamin B complex, and vitamin A. The insect’s outer skeleton is an interesting compound of sugar and amino acids.”
The Air Force Handbook addresses the needs of an Air Force individual who has been captured or otherwise isolated by accident or operational mishap. Whatever his or her mission may have been before, the new mission immediately becomes to “return to friendly control without giving aid or comfort to the enemy, to return early and in good physical and mental condition.”
The 652-page Handbook provides detailed guidance on how, with good fortune, that might be accomplished.
The military SERE program became somewhat notorious in recent years because early post-9/11 CIA interrogation techniques such as water-boarding were derived in part from SERE training. The new Air Force SERE Handbook makes only passing reference to torture and interrogation and does not mention water-boarding.
US Army: Hand and Arm Signals
Under ordinary circumstances, the U.S. Army relies on high-speed digital communications. But sometimes that is not an option, and soldiers must revert to more primitive methods.
“When electrical and/or digital means of communication are inadequate, or not available,” a new Army publication explains, messages may be transmitted “through the use of hand-and-arm signals, flags, pyrotechnics, and other visual aids.” Many of those alternate communication methods are described in Visual Signals, U.S. Army Training Circular TC 3-21.60, March 2017.
So, for example, “To signal ‘chemical, biological, radiological and nuclear attack,’ extend the arms and fists. Bend the arms to the shoulders. Repeat. (See figure 1-16.)”
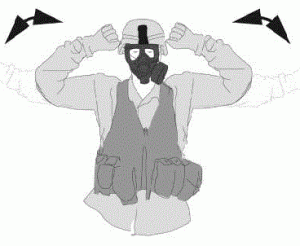
Of course, hand and arm signals have limitations. For one thing, they may be misunderstood.
“Visual signals are generally contextual in nature. For example, the hand-and-arm signal for ‘take cover’ and ‘slow down’ are similar in their perspective movements, however the situation in which each is given is completely different.”
Also, “The range and reliability of visual communications are significantly reduced during periods of poor visibility and when terrain restricts observation.”
Finally, visual or gestural communications “are vulnerable to enemy interception and may be used for deception purposes,” the new Army publication said.
“Competing Observables” Complicate Deception
Deception plays an important role in many military operations. But is hard to deceive an opponent (or anyone else) when evidence of that deception is visible in plain sight.
A new military term — “competing observable” — has been introduced to capture this problem.
In the context of military deception, an ordinary “observable” is defined as “an indicator within an adversary’s conduit [or information pathway] intended to cause action or inaction by the deception target.”
But a “competing observable” is “any observable that contradicts the deception story, casts doubt on, or diminishes the impact of one or more required or supporting observables.”
The term “competing observable” was incorporated in the latest edition of the official DoD Dictionary of Military and Associated Terms this month. The Dictionary, a copy of which appeared in our conduit, provides standard definitions for thousands of words and phrases that constitute the lexicon of U.S. military thought.
Each new update removes some terms, and adds or modifies others in an ongoing adaptation to current military doctrine.
The latest edition, for example, eliminates “berm” (“The nearly horizontal portion of a beach or backshore…”) and “honey pot” (“A trap set to detect, deflect, or in some manner counteract attempts at unauthorized use of information systems…”). These and several other such terms were removed from the Dictionary this month since they are “not used.”
The term “ruse” was slightly modified and is now defined as “an action designed to deceive the adversary, usually involving the deliberate exposure of false information to the adversary’s intelligence collection system.”
Army Intelligence: A Look to the Future
Collection of more intelligence-related information does not necessarily translate into better intelligence.
“Because of limitations associated with human cognition, and because much of the information obtained in war is contradictory or false, more information will not equate to better understanding.”
What makes that sensible observation doubly interesting is that it was written by Lt.Gen. H.R. McMaster, the newly designated National Security Advisor to President Trump.
It appears in the Foreword to the updated U.S. Army Functional Concept for Intelligence, 2020-2040, TRADOC Pamphlet, 525-2-1, February 2017.
The Army document, a somewhat speculative and aspirational look into the future of Army intelligence, presents a stark view of future threats, projected intelligence gaps, and directions forward. Some excerpts:
“International conditions will change more rapidly based on the increased velocity and momentum of human interactions and events. Technologies will become universally available and create a potential to overmatch U.S. capabilities. Weapons of mass destruction (WMD) proliferation among state and nonstate actors will pose an increased threat to U.S. security interests. Advanced cyberspace and counter-space capabilities will spread to state and nonstate actors, allowing them to protect their access and disrupt or deny access to others. Operations will occur among populations in cities and complex terrain.”
“Geospatial databases support the understanding of existing infrastructure and potential entry points but do not fully address the complexities of large urban centers, such as megacities. Country studies establish an overview, but city studies and transnational studies are lacking. While infrastructure and order of battle information remain valid, understanding networked and transnational enemy organizations, social media, and biometric identity information have equal or greater importance in some missions. Commanders must also understand critical infrastructure, assets, and terrain in the cyberspace domain. Nonstate ideological movements or political competition may drive national and subnational change more rapidly than conventional analysis may indicate. Proliferation of technology and WMD between states and nonstate actors disrupts normalcy faster than country studies can update.”
“Current information collection techniques are not robust enough to understand the rapidly changing urban environment. The speed of human interaction is greatest in a large urban environment. Operations in urban environments are not traditional adversary centric problems — the environment itself offers significant challenges to a conventional force and provides ample concealment to the enemy. Social networking, flows, infrastructure layering, radical variations by neighborhood, multiple authority structures, and others, complicate information collection against populations, infrastructure, and physical environment signatures. Government, religious, economic, and ideological actors use social and traditional public media to influence the population. Understanding the environment requires collecting and exploiting relevant signatures, many of which are either as of yet undiscovered, or lack sufficient technical exploitation to be useful.”
“Population and structural and signal density in urban environments produce physical and virtual clutter that reduces the effectiveness of intelligence collection, and complicates target acquisition. Market saturation of cell phones and other web-enabled devices produce a signal dense environment which complicates target acquisition and SIGINT collection…. Increasing proliferation of personal mobile communications is making connectedness more robust at the personal level adding to the difficulty of identifying relationships. The density of information and communications technologies may slow our ability to identify actionable intelligence.”
Meanwhile, the document says, the Army should anticipate “budget and force reductions.”
“Fiscal constraints demand near-term solutions that preserve the balance of readiness, force structure, and modernization necessary to meet the demands of the national defense strategy now, while setting the stage to begin evolving the force in the mid-term (2020-2030) and bringing innovative solutions to fruition to meet the challenges of the far-term (2030-2040).”
Domestically, “Legal constraints govern intelligence support to operations conducted within the homeland, specifically Defense Support to Civil Authorities (DSCA) and homeland defense. The U.S. is a litigious environment within which the Army operates; intelligence leaders must understand the role legal limitations and authorities play in shaping intelligence support.”
Geospatial Engineering in the US Army
The discipline of geospatial engineering and its role in U.S. military operations are described in a newly updated U.S. Army publication.
“Geospatial engineering is an art and a science that pertains to the generation, management, analysis, and dissemination of geospatial information that is accurately referenced to a precise location on the earth and is used in offense, defense, stability, or defense support of civil authorities tasks.”
“Geospatial engineers aid in the analysis of physical and cultural mapping and other activities that significantly contribute to anticipating, estimating, and warning of possible future events. Providing geospatial information that is timely, accurate, and relevant is a critical enabler throughout the operations process for developing shared situational awareness, improving the understanding of capabilities and limitations for friendly forces and the adversary, and highlighting other conditions of the operational environment that are required for mission command.”
“Today, geospatial engineering leverages finer temporal, spatial, and spectral resolutions from additional sensors and platforms that allow increased volumes and more complex data. New methods and technologies provide additional utility and capability and the ability to work effectively and efficiently within a broad pool of partners and allies.”
See Geospatial Engineering, Army Techniques Publication (ATP) 3-34.80, February 22, 2017.
U.S. Faces Evolving Threat Networks, DoD Says
Transnational threat networks pose increasingly complex challenges to U.S. interests, according to a new doctrinal publication from the Joint Chiefs of Staff.
“Networked threats are highly adaptable adversaries with the ability to select a variety of tactics, techniques, and technologies and blend them in unconventional ways to meet their strategic aims,” the document said. See Countering Threat Networks, Joint Publication 3-25, December 21, 2016.
The new DoD publication is focused on networks that are engaged, often clandestinely, in violent or criminal activity, and that may challenge U.S. forces or undermine national or regional stability.
However, the description of threat networks lends itself to — and, in light of current events, almost invites — a broader reading applicable to political disruption of other types.
“These threat networks jeopardize the stability and sovereignty of nation-states, including the US. They tend to operate among civilian populations and in the seams of society and may have components that are recognized locally as legitimate parts of society,” the document said.
“Collecting information and intelligence on these networks, their nodes, links, and affiliations is challenging, and analysis of their strengths, weaknesses, and centers of gravity (COGs) differs greatly from traditional nation-state adversaries.”
“Understanding a threat network’s motivation and objectives is required to effectively counter its efforts. The issues that drive a network and its ideology should be clearly understood. For example, they may be driven by grievances, utopian ideals, power, revenge over perceived past wrongs, greed, or a combination of these.”
“Many threat networks rely on family and tribal bonds when recruiting for the network’s inner core. These members have been vetted for years and are almost impossible to turn.”
“Threat networks… can be composed of criminal, insurgent or terrorist organizations, each of which may have different motivations for operating outside of societal norms. [But] they can also be government entities, legitimate legal organizations, or anyone who opposes the achievement of friendly objectives.”
“Transnational criminal organizations are self-perpetuating associations of individuals that operate to obtain power, influence, monetary and/or commercial gains, wholly or in part by illegal means.”
“Transnational criminal networks are not only expanding operations, but they are also diversifying activities, creating a convergence of threats that has become more complex, volatile, and destabilizing. These networks also threaten US interests by forging alliances with corrupt elements of national governments and using the power and influence of those elements to further their criminal activities. In some cases, national governments exploit these relationships to further their interests to the detriment of the US,” the DoD document said.
Civilian Control of the Military, and More from CRS
The nomination of Gen. James Mattis to be Secretary of Defense will require a legislative waiver of the prohibition against appointing persons who have been on active duty in the military within the past seven years to the position of Secretary.
A new report from the Congressional Research Service takes a look at the underlying issue of civilian control of the military, and related concerns.
“Historically, the restriction relating to the prior military service of the Secretary of Defense appears to be a product of congressional concern about preserving the principle of civilian control of the military, a fundamental tenet underpinning the design and operation of the American republic since its inception in 1776, if not before,” the report says.
The report reviews the origins and background of this principle and then ventures an analysis of its application today.
“The public discussion surrounding the proposed nomination of General Mattis seems to be less about preserving the principle of civilian control of the military (although that is certainly being debated), and more about civilian-military relations more generally.”
“Very few observers, if any, appear concerned that General Mattis, if appointed to the position of Secretary of Defense, will compromise the longstanding American tradition of ensuring that the military remains subordinate to the authority of civilian leaders. Instead, the possible appointment of General Mattis has served as a catalyst for a more wide-ranging discussion [of] the ways in which the U.S. military, civil society, and civilian leaders relate to each other,” CRS said. See Statutory Restrictions on the Position of Secretary of Defense: Issues for Congress, January 5, 2017.
Other new and updated reports from the Congressional Research Service include the following.
Alien Registration Requirements: Obama Administration Removes Certain Regulations, but Underlying Statutory Authority Remains, CRS Legal Sidebar, January 5, 2017
Latin America and the Caribbean: Key Issues for the 114th Congress, updated January 4, 2017
The Budget Reconciliation Process: Stages of Consideration, updated January 4, 2017
Budget Reconciliation Measures Enacted Into Law: 1980-2010, updated January 4, 2017
Systemically Important or “Too Big to Fail” Financial Institutions, updated January 4, 2017
Temporary Assistance for Needy Families (TANF): Size of the Population Eligible for and Receiving Cash Assistance, January 3, 2017
Congressional Careers: Service Tenure and Patterns of Member Service, 1789-2017, updated January 3, 2017
Inspectors General in and Beyond the Presidential Transition Period, CRS Insight, January 3, 2017
Discipline and Punishment at the Department of Defense
The Pentagon has prepared a newly updated compilation of infractions that might be committed and prohibitions that might be violated by Department of Defense employees, together with the recommended punishments.
“Mishandling or failing to safeguard information or documentation that is classified,” for example, can entail punishment ranging from written reprimand to removal. See Disciplinary and Adverse Actions, Administrative Instruction 8, December 16, 2016.
The document’s Table of Offenses and Penalties does not include overclassification, faulty compliance with the Freedom of Information Act, or some other readily imaginable forms of misconduct.
But proscribed (and punishable) activities do include retaliation against whistleblowers (conduct unbecoming a federal employee), discourtesy (abusive language or gestures), and lack of candor or truthfulness.
Joint Chiefs Urge “Due Diligence” in Targeting the Enemy
The proper selection and validation of enemy targets in war is a critical function for military planners and intelligence analysts. Errors can result in horrific civilian casualties and may also be strategically counterproductive.
“In extreme cases, failure to exercise due diligence in target development can result in outcomes that have negative strategic repercussions for the United States and its allies,” a newly disclosed Pentagon manual on targeting acknowledges (in bold type).
Procedures for correctly identifying and approving targets are described in the manual. See Target Development Standards, Chairman of the Joint Chiefs of Staff Instruction 3370.01B, 230 pages, 6 May 2016 (Unclassified, For Official Use Only).
A target is “an entity or object that performs a function for the adversary considered for possible engagement or other action,” the manual explains.
“Targets fall into one of five target types: facility, individual, virtual, equipment, or organization.”
“Examples include POL [petroleum, oil or lubricant] or PWR [electric power] sites (facilities), the chief accountant of a terrorist group (individual), a Web site (virtual), mobile radar (equipment), or a motorized infantry brigade (organization).”
“A terrorist network is the adversary, not a target. A front company (an entity) that ships lethal aid (a function) for the terrorist network (the adversary) would be a target.”
“Collateral effects are unintentional or incidental adverse consequences of target engagement. Such effects are not unlawful so long as it is not excessive in light of the overall military advantage anticipated from the engagement.”
“While all targets are entities, not all entities in the battlespace are valid targets. To be validated as a target, the function of the entity must be tied to commander’s objectives (operationally relevant) and meet Law of War (LOW) requirements,” the manual notes.
The manual applies to the Department of Defense and the military services. It does not govern lethal operations by the Central Intelligence Agency.