Introducing Certification of Technical Necessity for Resumption of Nuclear Explosive Testing
The United States currently observes a voluntary moratorium on explosive nuclear weapons testing. At the same time, the National Nuclear Security Administration (NNSA) is required by law to maintain the capability to conduct an underground nuclear explosive test at the Nevada National Security Site, if directed to do so by the U.S. president.
Restarting U.S. nuclear weapons testing could have very negative security implications for the United States unless it was determined to be an absolute technical or security necessity. A restart of U.S. nuclear testing for any reason could open the door for China, Russia, Pakistan, and India to do the same, and make it even harder to condemn North Korea for its testing program. This would have significant security consequences for the United States and global environmental impacts.
The United States conducted over 1,000 nuclear weapons tests before the 1991 testing moratorium took effect. It was able to do so with the world’s most advanced diagnostic and data detection equipment, which enabled the US to conduct advanced computer simulations after the end of testing. Neither Russia or China conducted as many tests, and many fewer of those were able to collect advanced metrics, hampering these countries’ ability to match American simulation capabilities. Enabling Russia and China to resume testing could narrow the technical advantage the United States has held in testing data since the testing moratorium went into effect in 1992.
Aside from the security loss, nuclear testing would also have long-lasting radiological effects at the test site itself, including radiation contamination in the soil and groundwater, and the chance of venting into the atmosphere. Despite these downsides, a future president has the legal authority—for political or other reasons—to order a resumption of nuclear testing. Ensuring any such decision is more democratic and subject to a broader system of political accountability could be achieved by creating a more integrated approval process, based on scientific or security needs. To this end, Congress should pass legislation requiring the NNSA administrator to certify that an explosive nuclear test is technically necessary to rectify an existing problem or doubt in U.S. nuclear surety before a test can be conducted.
Challenges and Opportunities
The United States is party to the 1963 Limited Test Ban Treaty, which prohibits atmospheric tests, and the Threshold Ban Treaty of 1974, limiting underground tests of more than 150 kilotons of explosive yield. In 1992, the United States also established a legal moratorium on nuclear testing through the Hatfield-Exon-Mitchell Amendment, passed during the George H.W. Bush Administration. After extending this moratorium in 1993, the United States, Russia, and China also signed the Comprehensive Nuclear Test Ban Treaty (CTBT) in 1996, which prohibits nuclear explosions. However, none of the Annex 2 (nuclear armed) states have ratified the CTBT, which prevents it from entering into force.
Since halting nuclear explosive tests in 1992, the United States has benefited from a comparative advantage over other nuclear-armed states, given its advanced simulation and computing technologies, coupled with extensive data collected from conducting over 1,000 explosive nuclear tests over nearly five decades. The NNSA’s Stockpile Stewardship Program uses computer simulations to combine new scientific research with data from past nuclear explosive tests to assess the reliability, safety, and security of the U.S. stockpile without returning to nuclear explosive testing. Congress has mandated that the NNSA must provide a yearly report to the Nuclear Weapons Council, which reports to the president on the reliability of the nuclear weapons stockpile. The NNSA also maintains the capability to test nuclear weapons at the Nevada Test Site as directed by President Clinton in Presidential Decision Directive 15 (PDD-15). National Security Memorandum 7 requires the NNSA to have the capability to conduct an underground explosive test with limited diagnostics within 36 months, but the NNSA has asserted in their Stockpile Stewardship and Management plan that domestic and international laws and regulations could slow down this timeline. A 2011 report to Congress from the Department of Energy stated that a small test for political reasons could take only 6–10 months.
For the past 27 years, the NNSA administrator and the three directors of the national laboratories have annually certified—following a lengthy assessment process—that “there is no technical reason to conduct nuclear explosive testing.” Now, some figures, including former President Trump’s National Security Advisor, have called for a resumption of U.S. nuclear testing for political reasons. Specifically, testing advocates suggest—despite a lack of technical justification—that a return to testing is necessary in order to maintain the reliability of the U.S. nuclear stockpile and to intimidate China and other adversaries at the bargaining table.
A 2003 study by Sandia National Laboratories found that conducting an underground nuclear test would cost between $76 million and $84 million in then-year dollars, approximately $132 million to $146 million today. In addition to financial cost, explosive nuclear testing could also be costly to both humans and the environment even if conducted underground. For example, at least 32 underground tests performed at the Nevada Test Site were found to have released considerable quantities of radionuclides into the atmosphere through venting. Underground testing can also lead to contamination of land and groundwater. One of the most significant impacts of nuclear testing in the United States is the disproportionately high rate of thyroid cancer in Nevada and surrounding states due to radioactive contamination of the environment.
In addition to health and environmental concerns, the resumption of nuclear tests in the United States would likely trigger nuclear testing by other states—all of which would have comparatively more to gain and learn from testing. When the CTBT was signed, the United States had already conducted far more nuclear tests than China or Russia with better technology to collect data, including fiber optic cables and supercomputers. A return to nuclear testing would also weaken international norms on nonproliferation and, rather than coerce adversaries into a preferred course of action, likely instigate more aggressive behavior and heightened tensions in response.
Plan of Action
In order to ensure that, if resumed, explosive nuclear testing is done for technical rather than political reasons, Congress should amend existing legislation to implement checks and balances on the president’s ability to order such a resumption. Per section 2530 of title 50 of the United States Code, “No underground test of nuclear weapons may be conducted by the United States after September 30, 1996, unless a foreign state conducts a nuclear test after this date, at which time the prohibition on United States nuclear testing is lifted.” Congress should amend this legislation to stipulate that, prior to any nuclear test being conducted, the NNSA administrator must first certify that the objectives of the test cannot be achieved through simulation and are important enough to warrant an end to the moratorium. A new certification should be required for every individual test, and the amendment should require that the certification be provided in the form of a publicly available, unclassified report to Congress, in addition to a classified report. In the absence of such an amendment, the president should make a Presidential Decision Directive to call for a certification by the NNSA administrator and a public hearing under oath to certify the same results cannot be achieved through scientific simulation in order for a nuclear test to be conducted.
Conclusion
The United States should continue its voluntary moratorium on all types of explosive nuclear weapons tests and implement further checks on the president’s ability to call for a resumption of nuclear testing.
This action-ready policy memo is part of Day One 2025 — our effort to bring forward bold policy ideas, grounded in science and evidence, that can tackle the country’s biggest challenges and bring us closer to the prosperous, equitable and safe future that we all hope for whoever takes office in 2025 and beyond.
Protecting U.S. Critical Infrastructure with Resilience Caches of Reusable Respirators
To help protect U.S. critical infrastructure workers from future pandemics and other biological threats, the next presidential administration should use the federal government’s grantmaking power to ensure ample supplies of high-quality respiratory personal protective equipment (PPE). The administration can take five concrete actions:
- The Office of Pandemic Preparedness and Response Policy (OPPR) can coordinate requirements for federal agencies and recipients of federal emergency/disaster preparedness funding to maintain access to at least one reusable respirator per critical employee.
- The Department of Labor’s Occupational Safety and Health Administration (OSHA) can initiate an occupational safety rule on reusable respirator resilience caches.
- The Department of Health and Human Services’ Administration for Strategic Preparedness and Response (ASPR) can require PPE manufacturers receiving federal funding to demonstrate their robustness to extreme pandemics.
- ASPR’s Strategic National Stockpile can start stockpiling reusable respirators.
- The Federal Emergency Management Agency (FEMA) can leverage its public outreach experience to increase “peacetime” adoption of reusable respirators.
These actions would complete the Biden Administration’s existing portfolio of efforts to reduce the likelihood of dangerous PPE shortages in the future, reaffirming executive commitment to protecting vulnerable workers, building a resilient national supply chain, and encouraging innovation.
Challenge and Opportunity
The next pandemic could strike at any time, and our PPE supply chain is not ready. Experts predict that the chance of a severe natural epidemic could perhaps triple in the next few decades, and advances in synthetic biology are increasing the risk of deliberate biological threats. As the world witnessed in 2020, disposable PPE can quickly become scarce in a crisis. Inadequate stockpiles left millions of workers with insufficient access to respiratory protection and often higher death rates than the general public—especially the critical infrastructure workers who operate the supply chains for our food, healthcare, public safety, and other essential goods and services. In future pandemics, which could have a 4% to 11%+ chance of occurring in the next 20 years based on historical extrapolations, PPE shortages could cause unnecessary infections, deaths, and burnout among critical infrastructure workers.
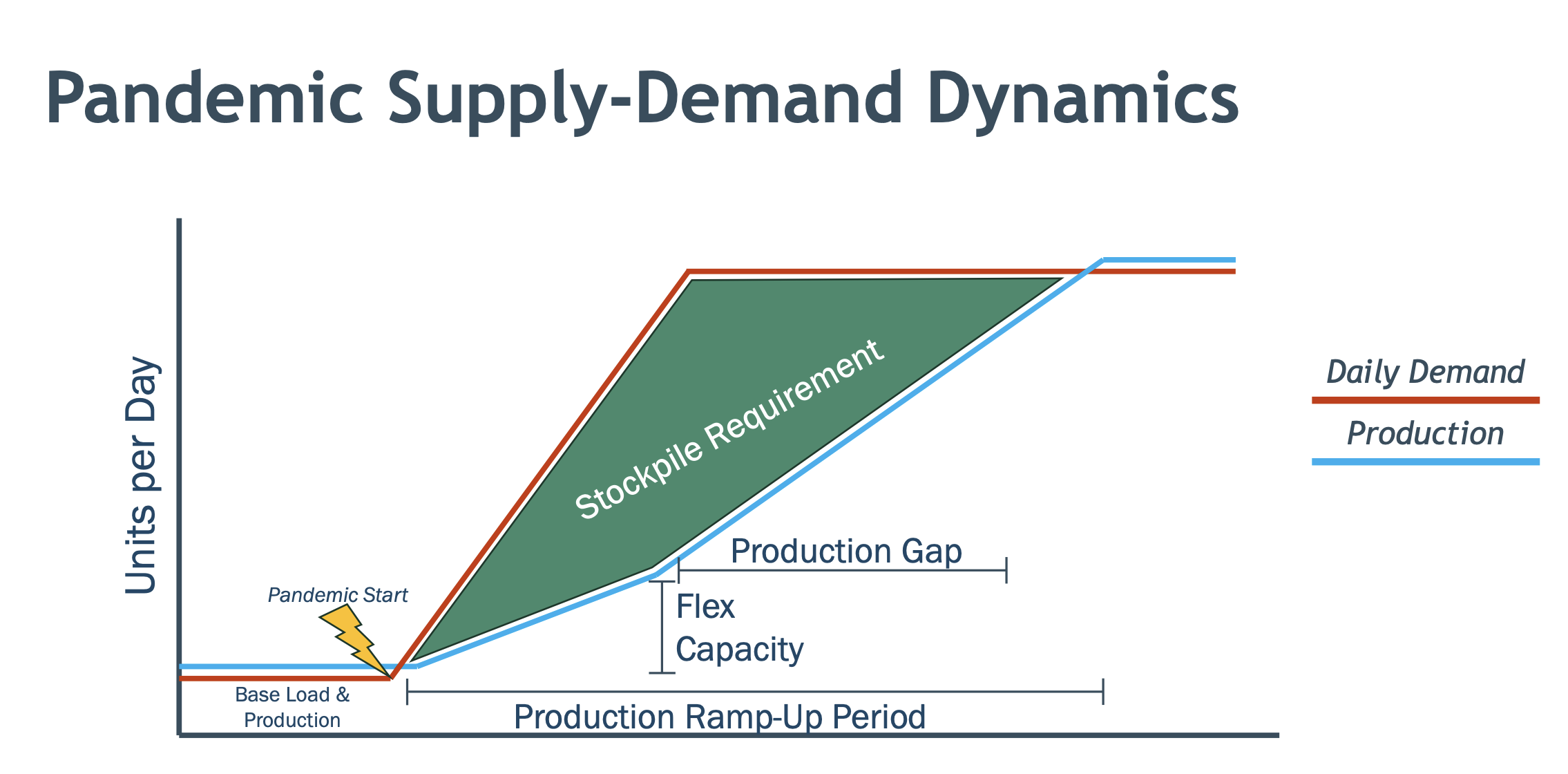
Figure 1. Notional figure from Blueprint Biosecurity’s Next-Gen PPE Blueprint demonstrating the need for stockpiling PPE in advance of future pandemics.
Recognizing the vulnerability of our PPE supply chain to future pandemics, Section 3.3 of the National Biodefense Strategy and Implementation Plan directs the federal government to:
Establish resilient and scalable supply and manufacturing capabilities for PPE in the United States that can: (a) enable a containment response for; and (b) meet U.S. peak projected demand for healthcare and other essential critical infrastructure workers during a nationally or internationally significant biological incident.
At a high level, securing the supply of PPE during crises is already understood as a national priority. However, despite the federal government’s past efforts to invest in domestic PPE manufacturing, production capacity will still take time to ramp up in future scenarios. Our current stockpiles aren’t large enough to bridge that gap. Some illustrative math: there are approximately 50 million essential workers in the United States, but as of 2022 our Strategic National Stockpile only had about 540 million disposable N95 respirators. This is barely enough to last 10 days, assuming each worker only uses one per day. (One per day is even a stretch: extended use and reuse of disposable N95s often leads to air leakage around wearers’ faces.) State- and local-level stockpiles may help, but many states have already started jettisoning their PPE stocks as purchases from 2020 expire and the prudence of paying for storage becomes less visible. PPE shortages may happen again.
Fortunately, there is existing technology that can reduce the likelihood of shortages while also protecting workers better and reducing costs: reusable respirators, like elastomeric half-mask respirators (EHMRs).
A single EHMR typically costs between $20 and $40. While the up-front cost of an EHMR is higher than the ~$1 cost of a disposable N95, a single EHMR can reliably last a worker for thousands of shifts over the entirety of a pandemic. Compared to disposable N95s, EHMRs are also better at protecting workers from infection, and workers prefer them to disposable N95s in risky environments. EHMR facepieces often have a 10-year shelf life, and filter cartridges typically have the same five-year shelf life of a typical disposable N95. A supply of EHMRs also takes up an estimated 1.5% of the warehouse space of the equivalent supply of disposable N95s.
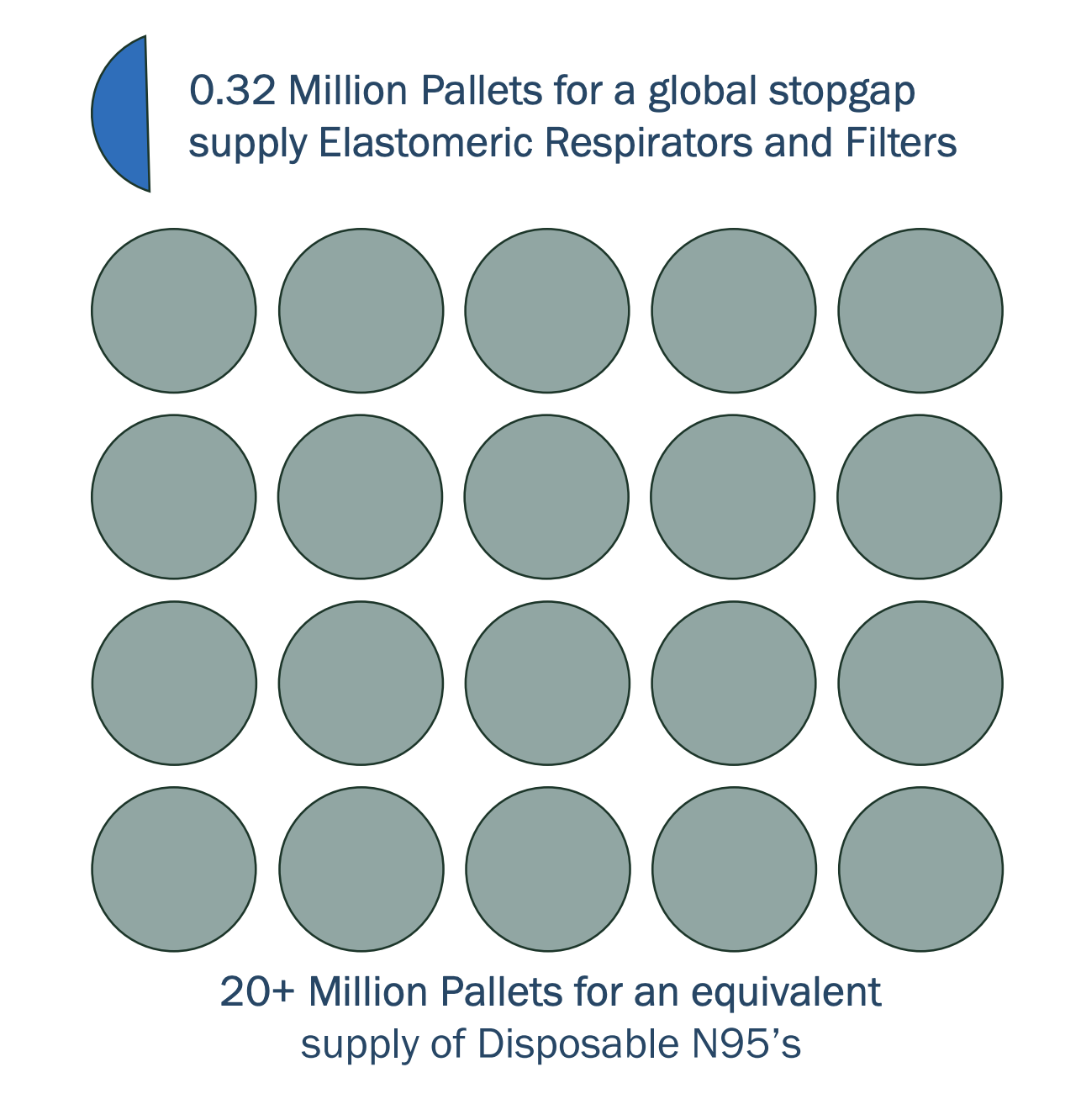
Figure 2. The relative size of equivalent PPE stockpiles. Source: Blueprint Biosecurity’s Next-Gen PPE Blueprint.
Some previous drawbacks of EHMRs were their lack of filtration for exhaled air and the unclear efficacy of disinfecting them between uses. Both of those problems are on their way to being solved. The newest generation of EHMRs on the market (products like the Dentec Comfort-Air Nx and the ElastoMaskPro) provide filtration on both inhalation and exhalation, and initial results from ongoing studies presented by the National Institute for Occupational Safety and Health (NIOSH) have demonstrated that they can be safely disinfected. (Product links are for illustrative purposes, not endorsement.)
Establishing stable demand for the newest generation of EHMRs could drive additional innovation in product design or material use. This innovation could further reduce worker infection rates by eliminating the need for respirator fit testing, improving comfort and communication, and enabling self-disinfection. It could also increase the number of critical infrastructure workers coverable with a fixed stockpile budget by increasing shelf lives and reducing cost per unit. Making reusable respirators more protective, ergonomic, and storable would improve the number of lives they are able to save in future pandemics while lowering costs. For further information on EHMRs, the National Academies has published studies that explore the benefits of reusable respirators.
The next administration, led by the new OPPR can require critical infrastructure operators that receive federal emergency/disaster preparedness funding to maintain resilience caches of at least one reusable respirator per critical infrastructure worker in their workplaces—enough to protect those workers during future pandemics.
These resilience caches would have two key benefits:
- Because many U.S. critical infrastructure operators, from healthcare to electricity providers, receive federal emergency preparedness funds, these requirements would bolster our nation’s mission-critical functions against pandemics or other inhalation hazards like wildfire smoke. At the same time, the requirements would be tied to a source of funding that could be used to meet them.
- By creating large, sustainable private-sector demand for domestic respirators, these requirements would help substantially grow the domestic industrial base for PPE manufacturing, without relying on future warm-basing payments like those that Congress recently rescinded.
By taking action, the next administration has an opportunity to reduce the future burden on taxpayers and the federal government, help keep workers safe, and increase the robustness of domestic critical infrastructure.
Plan of Action
Recommendation 1. Require federal agencies and recipients of federal emergency/disaster preparedness funding to maintain access to at least one reusable respirator per critical employee.
OPPR can coordinate a process to define the minimum target product profile of reusable respirators that employers must procure. To incentivize continual respirator innovation, OPPR’s process can regularly raise the minimum performance standards of PPE in these resilience caches. These standards could be published alongside regular PPE demand forecasts. As products expire every 5 or 10 years, employers would be required to procure the new, higher standard.
OPPR can also convene representatives from each agency that administers emergency/disaster preparedness funding programs to critical infrastructure sectors and can align those agencies on language for:
- Requiring funding recipients to maintain access to resilience caches of enough PPE.
- Explicitly including “maintaining access to PPE resilience caches” as an acceptable and encouraged use of funding.
The Cybersecurity and Infrastructure Security Agency (CISA) within the Department of Homeland Security (DHS) can update its definition of essential workers and set guidelines for which employees would need a reusable respirator.
FEMA’s Office of National Continuity Programs can recommend reusable respirator stocks for critical staff at federal departments and agencies, and the Centers for Medicare and Medicaid Services (CMS) can also set a requirement for healthcare facilities as a condition of participation for receiving Medicare reimbursement.
Recommendation 2. Initiate an occupational safety rule on reusable respirator resilience caches.
To cover any critical infrastructure workplaces that are not affected by the requirements in Recommendation 1, OSHA can also require employers to maintain these resilience caches. This provision could be incorporated into a broader rule on pandemic preparedness, as a former OSHA director has suggested.
OSHA should also develop preemptive guidance on the scenarios in which it would likely relax its other rules. In normal times, employers are usually required to implement a full, costly Respiratory Protection Program (RPP) whenever they hand an employee an EHMR. An RPP typically includes complex, time-consuming steps like medical evaluations that may impede PPE access in crises. OSHA already has experience relaxing RPP rules in pandemics, and preemptive guidance on when those rules might be relaxed in the future would help employers better understand possible regulations around using their resilience caches.
Recommendation 3. Require PPE manufacturers receiving federal funding to demonstrate their robustness to extreme pandemics.
The DHS pandemic response plan notes that workplace absenteeism rates during extreme pandemics are projected to be to 40%.
U.S. PPE manufacturers supported by federal industrial base expansion programs, such as the investments managed by ASPR, should be required to demonstrate that they can remain operational in extreme conditions in order to continue receiving funding.
To demonstrate their pandemic preparedness, these manufacturers should have:
- An on-site stockpile of enough reusable respirators for the maximum number of workers they might hire during a manufacturing surge.
- A comprehensive pandemic response plan that addresses workplace transmission protection.
- Regular exercises and independent evaluations of their pandemic response plans.
Recommendation 4. Start stockpiling reusable respirators in the Strategic National Stockpile.
Inside ASPR, the Strategic National Stockpile should ensure that the majority of its new PPE purchases are for reusable respirators, not disposable N95s. The stockpile can also encourage further innovation by making advance market commitments for next-generation reusable respirators.
Recommendation 5. Leverage FEMA’s public outreach experience to increase “peacetime” adoption of reusable respirators.
To complement work on growing reusable respirator stockpiles and hardening manufacturing, FEMA can also help familiarize the workforce with these products in advance of a crisis. FEMA can use Ready.gov to encourage the general public to adopt reusable respirators in household emergency preparedness kits. It can also develop partnerships with professional groups like the American Industrial Hygiene Association (AIHA) or the Association for Health Care Resource & Materials Management (AHRMM) to introduce workers to reusable respirators and instruct them in their use cases during both business as usual and crises.
Conclusion
Given the high and growing risk of another pandemic, ensuring that we have an ample supply of highly protective respiratory PPE should be a national priority. With new reusable respirators hitting the market, the momentum around pandemic preparedness after the COVID-19 pandemic, and a clear opportunity to reaffirm prior commitments, the time is ripe for the next administration to make sure our workers are safe the next time a pandemic strikes.
This action-ready policy memo is part of Day One 2025 — our effort to bring forward bold policy ideas, grounded in science and evidence, that can tackle the country’s biggest challenges and bring us closer to the prosperous, equitable and safe future that we all hope for whoever takes office in 2025 and beyond.
Yes. Throughout COVID-19, critical infrastructure worker unions have consistently advocated for EHMRs. Examples include the New York State Nurses Association (NYSNA) and the Service Employees International Union (SEIU) 121rn.
Unions have also been at the forefront of broader calls for securing PPE access in future pandemics; the California Nurses Association was the driving force behind California’s most recent PPE stockpiling laws.
Studies have also shown that workers prefer reusable respirators to disposable N95s in risky environments.
Not in the long run. As a single employee infection can cost $340 per day, it is more cost-effective for most employers to spend around $3 per critical employee per year for reusable respirators. For hospitals in states like California or New York, which mandate one- to three-month PPE stockpiles, switching those stockpiles to reusable respirators would likely be cost-saving, as demonstrated by past case studies. Most of these hospitals are still meeting those requirements with disposable N95s largely because of slow product choice re-evaluation cycles.
Managing these resilience caches would also pose a minimal burden on employers. Most EHMRs can be comfortably stored in most indoor workplaces, taking up around the volume of a large coffee mug for each employee. Small workplaces with fewer than 50 employees could likely fit their entire resilience cache in a cardboard box in a back closet, and large workplaces will likely already have systems for managing emergency products that expire, like AEDs, first-aid kits, and fire extinguishers. As with other consumables like printer ink cartridges, PPE manufacturers can send reminders to employers when the products they purchased are about to expire.
To put this into perspective, fire alarm units should generally be replaced every 10 years for $20 to $30 each, and typically require new batteries once or twice per year. We readily accept the burden and minor cost of fire alarm maintenance, even though all U.S. fire deaths in the last 10 years only accumulate to 3% of COVID-19’s U.S. death toll.
While EHMRs fit most workers, there may be some workers who aren’t able to wear them due to religious norms or assistive devices.
Those workers can instead wear another type of reusable respirator, powered air-purifying respirators (PAPRs). While PAPRs are even more effective at keeping workers safe than EHMRs, they cost significantly more and can be very loud. Employers and government stockpiles can include a small amount of PAPRs for those workers who can’t wear EHMRs, and can encourage eventual cost reductions and user-experience improvements with advance market commitments and incremental increases in procurement standards.
Yes, but they reduce the risk of any lags in PPE access. Every day that workers are exposed to pathogens without adequate PPE, their likelihood of infection goes up. Any unnecessary exposures speed the spread of the pandemic. Also, PPE manufacturing ramp-up could be slowed by employee absences due to infection or caring for infected loved ones.
To accommodate some employers’ reluctance to build physical stockpiles, the administration can enable employers to satisfy the resilience cache requirement in multiple ways, such as:
- On-site resilience caches in their workplaces
- Agreements with distributors to manage resilience cache inventory as a rotating supply bubble
- Agreements with third-party resilience cache managers
- Purchase options with manufacturers that have demonstrated enough capacity to rapidly manufacture resilience cache inventory at the start of a pandemic
Purchase options would function like a “virtual” resilience cache: they would incentivize manufacturers to build extra warm-base surge capacity and test their ability to rapidly ramp up manufacturing pace. However, it would increase the risk that workers will be exposed to infectious disease hazards before their PPE arrives. (Especially in the case of a severe pandemic, where logistics systems could get disrupted.)
Yes. Employers could use respirators from their resilience cache to protect workers from localized incidents like seasonal flu outbreaks, wildfires, or smog days, and put them back into storage when they’re no longer needed.
Yes. Federal emergency/disaster preparedness funding could be tied to other requirements, like:
- Installing the capacity to turn up workplace air ventilation or filtration significantly
- Maintaining and regularly exercising pandemic response protocols
- Investing in passive transmission suppression technology (e.g., germicidal ultraviolet light)
The next time there’s a pandemic, having these requirements in place could help ensure that any post-emergency funding (e.g., Hazard Mitigation Assistance Program grants) will be spent on innovative PPE that aligns with the federal government’s broader PPE supply chain strategies.
If the Strategic National Stockpile receives additional post-emergency funding from Congress, it could also align its purchases with the target product profiles that critical infrastructure operators are already procuring to.
Scaling Proven IT Modernization Strategies Across the Federal Government
Ten years after the creation of the U.S. Digital Service (USDS) and 18F (an organization with the General Services Administration that helps other government agencies build, buy, and share technology products), the federal government still struggles to buy, build, and operate technology in a speedy, modern, scalable way. Cybersecurity remains a continuous challenge – in part due to lack of modernization of legacy technology systems. As data fuels the next transformative modernization phase, the federal government has an opportunity to leverage modern practices to leap forward in scaling IT Modernization.
While there have been success stories, like IRS’s direct file tool and electronic passport renewal, most government technology and delivery practices remain antiquated and the replacement process remains too slow. Many obstacles to modernization have been removed in theory, yet in practice Chief Information Officers (CIOs) still struggle to exercise their authority to achieve meaningful results. Additionally, procurement and hiring processes, as well as insufficient modernization budgets, remain barriers.
The DoD failed to modernize its 25-year-old Defense Travel System (DTS) after spending $374 million, while the IRS relies on hundreds of outdated systems, including a key taxpayer data processing system built in the 1960s, with full replacement not expected until 2030. The GAO identified 10 critical systems across various agencies, ranging from 8 to 51 years old, that provide essential services like emergency management, health care, and defense, costing $337 million annually to operate and maintain, many of which use outdated code and unsupported hardware, posing major security and reliability risks. Despite the establishment of the Technology Modernization Fund (TMF) with a $1.23 billion appropriation, most TMF funds have been expended for a small number of programs, many of which did not solve legacy modernization problems. Meanwhile the urgency of modernizing antiquated legacy systems to prevent service breakdowns continues to increase.
This memo proposes a new effort to rapidly scale proven IT modernization strategies across the federal government. The result will be a federal government with the structure and culture in place to buy, build, and deliver technology that meets the needs of Americans today and into the future.
Challenge and Opportunity
Government administrations typically arrive with a significant policy agenda and a limited management agenda. The management agenda often receives minimal focus until the policy agenda is firmly underway. As a result, the management agenda is rarely well implemented, if it is implemented at all. It should be noted that there are signs of progress in this area, as the Biden-Harris Administration publishing its management agenda in the first year of the Administration, while the the Trump Administration did not publish its management agenda until the second year of the administration. However, even when the management agenda is published earlier, alignment, accountability and senior White House and departmental leadership focus on the management agenda is far weaker than for the policy agenda.
Even when a PMA has been published and alignment is achieved amongst all the stakeholders within the EOP, the PMA is simply not a priority for Departmental/Agency leadership and there is little focus on the PMA among Secretaries/Administrators. Each Department/Agency is responsible for a policy agenda and, unless, IT or other management agenda items are core to the delivery of the policy agenda, such as at the VA, departmental political leadership pays little attention to the PMA or related activities such as IT and procurement.
An administration’s failure to implement a management agenda and improve government operations jeopardizes the success of that administration’s policy agenda, as poor government technology inhibits successful implementation of many policiesThis has been clear during the Biden – Harris administration as departments have struggled to rapidly deliver IT systems to support loan, grant and tax programs, sometimes delaying or slowing the implementation of those programs.
The federal government as a whole spends about 80% of its IT budget on maintenance of outdated systems—a percentage that is increasing, not declining. Successful innovations in federal technology and service delivery have not scaled, leaving pockets of success throughout the government that are constantly at risk of disappearing with changes in staff or leadership.
The Obama administration created USDS and 18F/Technology Transformation Services (TTS) to begin addressing the federal government’s technology problems through improved adoption of modern Digital Services. The Trump administration created the Office of American Innovation (OAI) to further advance government technology management. As adoption of AI accelerates, it becomes even more imperative for the federal government to close the technology gap between where we are and where we need to be to provide the government services that the American people deserve.
The Biden administration has adapted IT modernization efforts to address the pivot to AI innovations by having groups like USDS, 18F/TTS and DoD Software Factories increasingly focus on Data adoption and AI. With the Executive Order on AI and the Consortium Dedicated to AI Safety the Biden-Harris administration is establishing guidelines to adopt and properly govern increasing focus on Data and AI. These are all positive highlights for IT modernization – but there is a need for these efforts to deliver real productivity. Expectations of citizens continue to increase. Services that take months should take weeks, weeks should take days, and days should take hours. This level of improvement can’t be reached across the majority of government services until modernization occurs at scale. While multiple laws designed to enhance CIO authorities and accelerate digital transformation have been passed in recent years, departmental CIOs still do not have the tools to drive change, especially in large, federated departments where CIOs do not have substantial budget authority.
As the evolution of Digital Transformation for the government pivots to data, modernizedAgencies/Department can leap forward, while others are still stuck with antiquated systems and not able to derive value from data yet. For more digitally mature Agencies/Departments, the pivot to data-driven decisions, automation and AI, offer the best chance for a leap in productivity and quality gains. AI will fuel the next opportunity to leap forward by shifting focus from the process of delivering digital services (as they become norms) and more on the data based insights they ingest and create. For the Agencies/Departments “left behind” the value of data driven-decisions, automation and AI – could drive rapid transformation and new tools to deliver legacy system modernization.
The Department of Energy’s “Scaling IT Modernization Playbook” offers key approaches to scale IT modernization by prioritizing mission outcomes, driving data adoption, coordinating at scale across government, and valuing speed and agility because, “we underrate speed as value”. Government operations have become too complacent with slow processes and modernization; we are increasingly outpaced by faster developing innovations. Essentially, Moore’s Law (posited by Gordon Moore that the number of transistors in an integrated circuit doubles every 18 months while cost increases minimally. Moore’s law has been more generally applied to a variety of advanced technologies) is outpacing successful policy implementation.
As a result, the government and the public continue to struggle with dysfunctional legacy systems that make government services difficult to use under normal circumstances and can be crippling in a crisis. The solution to these problems is to boldly and rapidly scale emerging modernization efforts across the federal government enterprise – embracing leaps forward with the opportunistic shift of data and AI fueled transformation.
Some departments have delivered notably successful modern systems, such DHS’ Global Entry site and the State Department’s online passport renewal service. While these solutions are clearly less complex than the IRS’ tax processing system, which the IRS has struggled to modernize, they demonstrate that the government can deliver modern digital services under the right conditions.
Failed policy implementation due to failed technology implementation and modernization will continue until management and leadership practices associated with modern delivery are rapidly adopted at scale across government and efforts and programs are retained between administrations.
Plan of Action
Recommendation 1. Prioritize Policy Delivery through the Office of Management and Budget (OMB) and the General Services Administration (GSA)
First, the Administration should elevate the position of Federal CIO to be a peer to the Deputy Directors at the OMB and move the Federal CIO outside of OMB, while remaining within the Executive Office of the President, to ensure that the Federal CIO and, therefore, IT and Cybersecurity priorities and needs of the departments and agencies have a true seat at the table. The Federal CIO represents positions that are as important as but different from those of the OMB Deputy Directors and the National Security Advisor and, therefore, should be peers to those individuals, just as they are within departments and agencies, where CIOs are required to report to the Secretary or Administrator. Second, Elevate the role of the GSA Administrator to a Cabinet-level position, and formally recognize GSA as the federal government’s “Operations & Implementation” agency. These actions will effectively make the GSA Administrator the federal government’s Chief Operating Officer (COO). Policy, financial oversight, and governance will remain the purview of the OMB. Operations & Implementation will become the responsibility of the GSA, aligning existing GSA authorities of TTS, quality & proven shared services, acquisitions, and asset management with a renewed focus on mission centric government-service delivery. The GSA Administrator will collaborate with the President’s Management Council (PMC), OMB and agency level CIOs to coordinate policy delivery strategy with delivery responsibility, thereby integrating existing modernization and transformation efforts from the GSA Project Management Office (PMO) towards a common mission with prioritization on rapid transformation.
For the government to improve government services, it needs high-level leaders charged with prioritizing operations and implementation—as a COO does for a commercial organization. Elevating the Federal CIO to an OMB Deputy Director and the GSA Administrator to a Cabinet-level position tasked with overseeing “Operations & Implementation” would ensure that management and implementation best practices go hand in hand with policy development, dramatically reducing the delivery failures that put even strong policy agendas at risk.
Recommendation 2. Guide Government Leaders with the Rapid Agency Transformation Playbook
Building on the success of the Digital Services Playbook, and influenced by the DOE’s “Scaling IT Modernization Playbook” the Federal CIO should develop a set of “plays” for rapidly scaling technology and service delivery improvements across an entire agency. The Rapid Agency Transformation Playbook will act both as a guide to advise agency leaders in scaling best practices, as well as a standard against which modernization efforts can be assessed. The government wide “plays” will be based on practices that have proven successful in the private and public sectors, and will address concepts such as fostering innovation, rapid transformation, data adoption, modernizing or sunsetting legacy systems, and continually improving work processes infused with AI. Where the Digital Services Playbook has helped successfully innovate practices in pockets of government, the Rapid Agency Transformation Playbook will help scale those successful practices across government as a whole.
A Rapid Agency Transformation Playbook will provide a living document to guide leadership and management, helping align policy implementation with policy content. The Playbook will also clearly lay out expected practices for Federal employees and contractors who collaborate on policy delivery.
Recommendation 3. Fuel Rapid Transformation by Creating Rapid Transformation Funds
Congress should create Rapid Transformation Funds (RTF) under the control of each Cabinet-level CIO, as well as the most senior-IT leader in smaller departments and independent agencies. These funds would be placed in a Working Capital Fund (WCF) that is controlled by the cabinet level CIO or the most senior IT leader in smaller departments and independent agencies. These funds must be established through legislation. For those departments that do not currently have a working capital fund under the control of the CIO, the legislation should create that fund, rather than depending on each department or agency to make a legislative request for an IT WCF.
This structure will give the CIO of each Department/Agency direct control of the funds. All RTFs must be under the control of the most senior IT leader in each organization and the authority to manage these funds must not be delegatable.The TMF puts the funds under the control of GSA’s Office of the Federal Chief Information Officer (OFCIO) and a board that has to juggle priorities among GSA OCIO and the individual Departments and Agencies. Direct control will streamline decision making and fund disbursement. It will help to create a carrot to align with existing Federal Information Technology Acquisition Reform Act (FITARA) (i.e., stick) authorities. In addition, Congress should evaluate how CIO authorities are measured under FITARA to ensure that CIOs have a true seat at the table.
The legislation will provide the CIO the authority to sweep both expiring and canceling funds into the new WCF. Seed funds in the amount of 10% of department/agency budgets will be provided to each department/agency. CIOs will have the discretion to distribute the funds for modernization projects throughout their department or agency and to determine payback model(s) that best suit their organization, including the option to reduce or waive payback for projects, while the overarching model will be cost reimbursement.
The RTF will enhance the CIO’s ability to drive change within their own organization. While Congress has expanded CIO authorities through legislation three different times in recent years, no legislation has redirected funding to CIOs. Most cabinet level CIOs control a single digit percentage of the Department’s IT budget. For example, the Department of Energy CIO directly controls about 5% of DOE’s IT spending. Direct control of a meaningfully sized pool of money that can be allocated to component IT teams by the cabinet level CIO enables that cabinet level CIOs to drive critical priorities including modernization and security. Without funding, CIO authorities amount to unfunded mandates. The RTF will allow the CIO to enhance their authority by directly funding new initiatives. A reevaluation of the metrics associated with CIO authorities would ensure that CIOs have a true seat at the table.
Recommendation 4. Ensure transformation speed through continuity by establishing a Transformation Advisory Board and department/agency management councils.
First, OMB should establish a Transformation Advisory Board (TAB) within the Executive Office of the President (EOP), composed of senior and well-respected individuals who will be appointed to serve fixed terms not tied to the presidential administration and sponsored by the Federal CIO. The TAB will be chartered to impact management and technology policy across the government and make recommendations to change governance that impedes rapid modernization and transformation of government. Modeled after the Defense Innovation Board, the TAB will focus on entrenching rapid modernization efforts across administrations and on supporting, protecting, and enhancing existing digital-transformation capabilities. Second, each department and agency should be directed to establish a management council composed of leaders of the department/agency’s administrative functions to include at least IT, finance, human resources, and acquisition, under the leadership of the deputy secretary/deputy administrator. In large departments this may require creating a new deputy secretary or undersecretary position to ensure meaningful focus on the priorities, rather than simply holding meaningless council meetings. This council will ensure that collaborative management attention is given to departmental/agency administration and that leadership other than the CIO understand IT challenges and opportunities.
A Transformation Advisory Board will ensure continuity across administrations and changes in agency leadership to prevent the loss of good practices, enabling successful transformative innovations to take root and grow without breaks and gaps in administration changes. The management council will ensure that modernization is a priority of departmental/agency leadership beyond the CIO.
Ann Dunkin contributed to an earlier version of this memo.
This idea was originally published on November 13, 2020; we’ve re-published this updated version on October 22, 2024.
While things have not changed as much as we would like, departments and agencies have made progress in modernizing their technology products and processes. Elevating the GSA Administrator to the cabinet level, adding a Transformation Advisory Board, elevating the Federal CIO, reevaluating how CIO authorities are measured, creating departmental/agency management councils, and providing modernization funds directly to CIOs through working capital funds will provide agencies and departments with the management attention, expertise, support, and resources needed to scale and sustain that progress over time. Additionally, CIOs—who are responsible for technology delivery—are often siloed rather than part of a broad, holistic approach to operations and implementation. Elevating the GSA Administrator and the Federal CIO, as well as establishing the TAB and departmental/agency management councils, will provide coordinated focus on the government’s need to modernize IT.
Elevating the role of the Federal CIO and the GSA Administrator will provide more authority and attention for the President’s Management Agenda, thereby aligning policy content with policy implementation. Providing CIOs with a direct source of modernization funding will allow them to direct funds to the most critical projects throughout their organizations, as well as require adherence to standards and best practices. A new focus on successful policy delivery aided by experienced leaders will drive modernization of government systems that rely on dangerously outdated technology.
We believe that an administration that embraces the proposal outlined here will see scaling innovation as critical. Establishing a government COO and elevating the Federal CIO along with an appointed board that crosses administrations, departmental management councils, better measurement of CIO authorities, and direct funding to CIOs will dramatically increase the likelihood that that improved technology and service delivery remain a priority for future administrations.
The federal government has many pockets of innovation that have proven modern methodologies can and do work in government. These pockets of innovation—including USDS, GSA TTS, 18F, the U.S. Air Force Software Factories, fellowships, the Air Force Works Program (AFWERX), Defense Advanced Research Projects Agency (DARPA), and others—are inspiring. It is time to build on these innovations, coordinate their efforts under a U.S. government COO and empowered Federal CIO, and scale solutions to modernize the government as a whole.
Yes. A cabinet-level chief operating officer with top-level executive authority over policy operations and implementation is needed to carry out policy agendas effectively. It is hard to imagine a high-performing organization without a COO and a focus on operations and implementation at the highest level of leadership.
The legacy of any administration is based on its ability to enact its policy agenda and its ability to respond to national emergencies. Scaling modernization across the government is imperative if policy implementation and emergency response is important to the president.
Investing in Apprenticeships to Fill Labor-Market Talent and Opportunity Gaps
Over the last 20 years, the cost of college has skyrocketed, with tuition costs far outpacing wage growth. At the same time, many employers complain that they’re unable to find high-quality talent, in part due to an excessive focus on the signaling effect conferred by college degrees. Although the last three administrations have made significant strides towards expanding the number of pathways to high-earning jobs through apprenticeship programs, they remain under-utilized and have significant potential for growth. To maximize the potential of apprenticeship programs, the federal government should develop a cohesive approach to supporting “apprenticeships of the future,” such as those in cyber, healthcare, and advanced manufacturing. These apprenticeships provide high pay and upward mobility, support economic growth, and serve vital national interests. To maximize the benefits provided by an expansion of high-quality apprenticeships, the federal government should articulate degree pathways and credit equivalencies for individuals seeking further education, collaborate with industry associations to create standards for skills acquisition, and develop an innovation fund that supports cutting-edge labor market innovations, including those in apprenticeship programs.
Challenge & Opportunity
While recent student debt cancellation received significant attention,, the key underlying driver is the spiraling cost of college: tuition at four-year universities has risen by more than 125% in the last twenty years, far outpacing inflation and leaving students with an average debt load of $28,000 by graduation. To alleviate the strain, policymakers have increasingly recognized the potential of non-degree training, particularly apprenticeships, which mix on-the-job training with targeted academic skills acquisition. Apprenticeships, which typically last between a few months and 2 years, enable an individual in a high school or tertiary education program to work with an employer, earning a wage while developing skills that may lead to a permanent position or enhance future employability. President Obama spent $260 million on apprenticeship training, while the Trump administration spent $1 billion. Thus far, the Biden administration has spent $730 million to expand registered apprenticeships.
Nevertheless, apprenticeships in America remain vastly underutilized compared to some of our peer economies. In Germany, 1.2 million adults are enrolled in apprenticeship programs across 330 occupations. By contrast, the U.S. has roughly half as many apprentices despite enrolling 6.5 times as many college students as Germany. Moreover, apprentices are overwhelmingly concentrated in roles such as electricians, machinists, plumbers, and other industries historically classified as “skilled trades.”
American employers have put a significant premium on college degrees. Research from the Harvard Business School highlights the pervasiveness of degree inflation in many middle-skill, well-paying jobs. The figure below shows the “degree gap percentage,” which is the difference between the percentage of job descriptions requiring a college degree and the percentage of job holders holding a college degree.
Historically, employers’ emphasis on degrees has made wide-scale adoption of apprenticeships outside of skilled trades more challenging. However, attitudes towards apprenticeships continue to change as more employers realize their versatility and applicability to a variety of industries. Over the past few years, companies have started to take action. For instance, JP Morgan Chase has provided $15 million since 2018 to create apprenticeship programs in operations, finance, and technology, while Accenture has led the way in developing apprenticeship networks across the U.S. Apprenticeships have clear momentum and strong applicability to critical, strategic jobs, and federal, state, and local officials should capitalize on the opportunity to create a coherent strategy.
Policy Framework For Strategic Jobs
To identify areas of policy synergy, policymakers should consider the following criteria for jobs that should attract government funding and policy support:
- Essential to economic growth: roles that are frequently employed in high-growth industries, or else required to improve the future general productivity of businesses.
- Necessary to protect American interests: jobs that have broader implications for American national interests, including economic competitiveness, national security, green energy, and public health.
- Middle-skill roles that do not require college degrees: while higher educational attainment is generally desirable, it is not a suitable nor affordable option for all individuals, and many roles can or should support workers who have alternative credentials. Simply put, these jobs should provide pathways into the middle class without excessive education debt burdens.
- High current job shortages: demand for roles far exceeds current labor supply.
Using this framework, there are three areas in which the U.S. has clear, pressing needs:
- Tech job shortages in the United States will cost the American economy over $160 billion in revenue, driven by a shortage of over 1.2 million workers.
- Cyber attacks alone cost the American economy 1% – 4% of GDP , which can be partially addressed by eliminating the existing talent shortage of 350,000 cyber professionals.
- In addition, 50% of the federal tech workforce is over the age of 50 and just 20% is under the age of 40, indicating a large “retirement cliff” in the medium-term horizon.
- Although the U.S. has had a long-standing need for nurses and medical professionals, the COVID pandemic highlighted their importance and exposed systemic workforce shortages. By 2030, the country will be short over 500,000 nurses.
- The country also suffers from a lack of healthcare educators, with nearly 80,000 qualified nursing applicants turned away due to a lack of training capacity.
- While many critical healthcare roles (e.g., RNs and NPs) require at least a bachelor’s degree, apprenticeships are a great way to increase the pipeline of lower-level medical staff (e.g., medical assistants, CNAs, LVNs), who can then be upskilled into the RN role or higher.
- Today, the U.S. has over 600,000 unfilled manufacturing jobs, which may hamper efforts to bring back clean energy and semiconductor manufacturing despite the hundreds of billions invested by the Inflation Reduction Act, CHIPS Act, and Bipartisan Infrastructure Law. Cumulatively, this talent shortage could reduce American GDP by $1 trillion. The gap is most acute in a handful of roles, including assemblers, production supervisor, inspectors, and welders. However, these roles are essential to empowering the advanced manufacturing revolution, and need to be filled in order to maximize American industrial potential.
Policy Recommendations
In order to maximize the potential of apprenticeship programs in key strategic areas, the next administration should focus on coordinating resources, defining standards, and convening key stakeholders, which include employers and higher education providers, including private sector providers who demonstrate strong outcomes. To achieve this, the next administration should focus on the following policies:
Recommendation 1. The Departments of Labor and Education should jointly lead the creation of a national strategy for increasing apprenticeships and blended work-learn programs in essential roles and industries. In conjunction with other government agencies, they will stand up a “Strategic Apprenticeships” Task Force. This task force will consist primarily of governmental agencies, including the Department of Defense, Department of Treasury, and the Fed, that have clear mandates for improving worker outcomes which are tied directly to national strategic priorities. This task force will cooperate with the Advisory Committee on Apprenticeships (a committee convened by the Department of Labor that consists of labor unions, community colleges, and other institutions) to set short, medium, and long-term priorities, propose funding levels, and develop a coherent apprenticeship and training strategy.
- The Strategic Apprenticeships Task Force should adopt a “whole of government” approach and when appropriate, include other stakeholders such as the Department of Commerce or the Department of Defense. The task force will then work closely with bodies with deep domain expertise on apprenticeships (e.g., the Advisory Committee on Apprenticeships) to ensure that the proposed standards and structures are appropriately designed and implemented. This will culminate in the development of a strategic plan for apprenticeships that is renewed every five years and outlines key roles, skills, technologies, and training pedagogies that merit greater attention.
- Where necessary, the task force should create standards for apprenticeship programs that qualify for federal funding. The Registered Apprenticeship Program provides a repository of federally or state validated apprenticeships. However, occupations in cybersecurity and software development remain highly under-represented compared to roles in “traditional” industries such as manufacturing. The task force should work with industry certifications and associations, such as the ISC(2) and ISSA, to develop skill acquisition standards that will form the backbone of new apprenticeship programs.
- To ensure that students have multiple pathways to acquire additional educational credentials, the federal government should create a set of competency-based standards that equate on-the-job activities with classroom learning, creating clear pathways for students in apprenticeships who want to later receive an associate’s or bachelor’s degree. While this applies to all apprenticeships (and is a defining feature of the very successful Swiss and German systems), creating federal learning standards will improve the appeal of apprenticeship programs in strategic sectors while giving individuals a path to higher credentials in the future. Great strides were made for the cyber workforce, but more can be done in other sectors as well.
- At the state and local levels, elected officials should work with local chambers of commerce, community colleges, universities, and alternative education providers such as coding bootcamps to translate learning standards into apprenticeship opportunities, course credit, and pathways to an associate’s or bachelor’s degree. Where possible, local officials should also engage with nonprofits and other service organizations to provide wrap-around support structures such as career coaching, financial planning, and mental health resources which have been shown to improve persistence and outcomes.
Recommendation 2. Congress should commit federal funds for apprenticeships in cyber, software engineering, healthcare, and advanced trades (“apprenticeships for the future”), which will be allocated by the Department of Labor as prioritized by the Strategic Apprenticeships Task Force. Given the strategic value and existing job shortages for these roles, the Department of Labor should direct at least 50% of funds to roles that (a) provide strong pathways into middle-class jobs and (b) address pressing economic and strategic shortages in our economy:
- Past presidents’ increased funding for apprenticeship programs demonstrates broad bipartisan appeal for apprenticeships. This can be paired with the increasing bipartisan consensus on China, thereby linking job creation in key industries with national security implications (e.g., cybersecurity). The Jumpstart Our Businesses by Supporting Students Act of 2019 and the Bipartisan Workforce Pell Act both call for Pell Grants to be used for certain short-term learning programs. New legislation can go one step further by adding funding for short-term programs in “strategic roles.”
- Funding policies can take into account other economic and social justice priorities. For instance, the U.S. Department of Labor recently announced $87.5M of funding to expand diversity in registered apprenticeship programs. In addition to expanding the amount of funding targeted at women and individuals of color, the next administration could create funds for former apprentices of color to enter quality 4-year degree programs that continue expanding their earnings potentially (e.g., HBCUs).
- Department of Labor apprenticeship funding should transition away from proposal-style “contests” towards a more consistent and predictable schedule of funding. Currently, the Department of Labor will announce that a pot of money will be made available for competitive proposals and is typically distributed to State Departments of Labor and sometimes to large nonprofits. Going forward, apprenticeship funding, particularly those focused on jobs of the future, should be a consistent budget line item with clear paths towards funding renewal. In addition, the Department of Labor, in conjunction with the Strategic Apprenticeships Task Force, should publish guidelines for roles and skill development as outlined in their strategic plan.
Under the Biden administration, progress has been made on higher education accountability: for example, the Gainful Employment Rule was reinstated, requiring for-profit programs to demonstrate that typical graduates’ debts are less than 8% of their earnings, or 20% of their discretionary income, to maintain access to federal student aid. Moreover, the rule requires more than half of graduates to demonstrate higher earnings than a typical high school graduate.
Nonetheless, more can be done to buttress progress that has been made on higher education, particularly given stronger regulations around ROI. The policies suggested above can roll up into an “Apprenticeships of the Future” initiative jointly managed by the Departments of Labor and Education. By using a coordinated approach to apprenticeships, policymakers can ensure that more attention is paid towards strategically important industries and roles while creating clearer pathways for individuals seeking apprenticeships and for former apprentices looking to gain further skills and training in 4-year degrees and other “alt-ed” training programs. Moreover, the initiative could make diversity and economic advancement for underserved communities a core part of its mission.
This idea was originally published on November 29, 2021; we’ve re-published this updated version on October 21, 2024.
While apprenticeships have been traditionally applied to fields that most people would associate with “vocational” roles such as electricians or construction work, they are also increasingly used in “new economy” roles such as IT and software development. When properly designed, apprenticeships have excellent earning potential. For instance, Kentucky’s FAME program prepares students for advanced manufacturing careers, with graduates enjoying average earnings of nearly $100,000 within five years of program completion.
Employers generally enjoy a strong ROI for apprenticeships. For example, employers who ran registered apprenticeships in industrial manufacturing received $1.47 of benefits for every $1.00 that they invest in apprenticeships, with benefits generally coming in the form of improved productivity and reduced waste. Depending on the upfront investment amount, the duration of the apprenticeship, and the time required to recoup productivity gains and cost efficiencies, the IRR percentage is somewhere between 5% – 25%.
Mobilizing Innovative Financial Mechanisms for Extreme Heat Adaptation Solutions in Developing Nations
Global heat deaths are projected to increase by 370% if direct action is not taken to limit the effects of climate change. The dire implications of rising global temperatures extend across a spectrum of risks, from health crises exacerbated by heat stress, malnutrition, and disease, to economic disparities that disproportionately affect vulnerable communities in the U.S. and in low- and middle-income countries. In light of these challenges, it is imperative to prioritize a coordinated effort at both national and international levels to enhance resilience to extreme heat. This effort must focus on developing and implementing comprehensive strategies to ensure the vulnerable developing countries facing the worst and disproportionate effects of climate change have the proper capacity for adaptation, as wealthier, developed nations mitigate their contributions to climate change.
To address these challenges, the U.S. Agency for International Development (USAID) should mobilize finance through environmental impact bonds focused on scaling extreme heat adaptation solutions. USAID should build upon the success of the SERVIR joint initiative and expand it to include a partnership with NIHHIS to co-develop decision support tools for extreme heat. Additionally, the Bureau for Resilience, Environment, and Food Security (REFS) within the USAID should take the lead in tracking and reporting on climate adaptation funding data. This effort will enhance transparency and ensure that adaptation and mitigation efforts are effectively prioritized. By addressing the urgent need for comprehensive adaptation strategies, we can mitigate the impacts of climate change, increase resilience through adaptation, and protect the most vulnerable communities from the increasing threats posed by extreme heat.
Challenge
Over the past 13 months, temperatures have hit record highs, with much of the world having just experienced their warmest June on record. Berkeley Earth predicts a 95% chance that 2024 will rank as the warmest year in history. Extreme heat drives interconnected impacts across multiple risk areas including: public health; food insecurity; health care system costs; climate migration and the growing transmission of life-threatening diseases.
Thus, as global temperatures continue to rise, resilience to extreme heat becomes a crucial element of climate change adaptation, necessitating a strategic federal response on both domestic and international scales.
Inequitable Economic and Health Impacts
Despite contributing least to global greenhouse gas emissions, low- and middle-income countries experience four times higher economic losses from excess heat relative to wealthier counterparts. The countries likely to suffer the most are those with the most humidity, i.e. tropical nations in the Global South. Two-thirds of global exposure to extreme heat occurs in urban areas in the Global South, where there are fewer resources to mitigate and adapt.
The health impacts associated with increased global extreme heat events are severe, with projections of up to 250,000 additional deaths annually between 2030 and 2050 due to heat stress, alongside malnutrition, malaria, and diarrheal diseases. The direct cost to the health sector could reach $4 billion per year, with 80% of the cost being shouldered by Sub-Saharan Africa. On the whole, low-and middle-income countries (LMICs) in the Global South experience a higher portion of adverse health effects from increasing climate variability despite their minimal contributions to global greenhouse emissions, underscoring a clear global inequity challenge.
This imbalance points to a crucial need for a focus on extreme heat in climate change adaptation efforts and the overall importance of international solidarity in bolstering adaptation capabilities in developing nations. It is more cost-effective to prepare localities for extreme heat now than to deal with the impacts later. However, most communities do not have comprehensive heat resilience strategies or effective early warning systems due to the lack of resources and the necessary data for risk assessment and management — reflected by the fact that only around 16% of global climate financing needs are being met, with far less still flowing to the Global South. Recent analysis from Climate Policy Initiative, an international climate policy research organization, shows that the global adaptation funding gap is widening, as developing countries are projected to require $212 billion per year for climate adaptation through 2030. The needs will only increase without direct policy action.
Opportunity: The Role of USAID in Climate Adaptation and Resilience
As the primary federal agency responsible for helping partner countries adapt to and build resilience against climate change, USAID announced multiple commitments at COP28 to advance climate adaptation efforts in developing nations. In December 2023, following COP28, Special Presidential Envoy for Climate John Kerry and USAID Administrator Power announced that 31 companies and partners have responded to the President’s Emergency Plan for Adaptation and Resilience (PREPARE) Call to Action and committed $2.3 billion in additional adaptation finance. Per the State Department’s December 2023 Progress Report on President Biden’s Climate Finance Pledge, this funding level puts agencies on track to reach President Biden’s pledge of working with Congress to raise adaptation finance to $3 billion per year by 2024 as part of PREPARE.
USAID’s Bureau for Resilience, Environment, and Food Security (REFS) leads the implementation of PREPARE. USAID’s entire adaptation portfolio was designed to contribute to PREPARE and align with the Action Plan released in September 2022 by the Biden Administration. USAID has further committed to better integrating adaptation in its Climate Strategy for 2022 to 2030 and established a target to support 500 million people’s adaptation efforts.
This strategy is complemented by USAID’s efforts to spearhead international action on extreme heat at the federal level, with the launch of its Global Sprint of Action on Extreme Heat in March 2024. This program started with the inaugural Global Heat Summit and ran through June 2024, calling on national and local governments, organizations, companies, universities, and youth leaders to take action to help prepare the world for extreme heat, alongside USAID Missions, IFRC and its 191-member National Societies. The executive branch was also advised to utilize the Guidance on Extreme Heat for Federal Agencies Operating Overseas and United States Government Implementing Partners.
On the whole, the USAID approach to climate change adaptation is aimed at predicting, preparing for, and mitigating the impacts of climate change in partner countries. The two main components of USAID’s approach to adaptation include climate risk management and climate information services. Climate risk management involves a “light-touch, staff-led process” for assessing, addressing, and adaptively managing climate risks in non-emergency development funding. The climate information services translate data, statistical analyses, and quantitative outputs into information and knowledge to support decision-making processes. Some climate information services include early warning systems, which are designed to enable governments’ early and effective action. A primary example of a tool for USAID’s climate information services efforts is the SERVIR program, a joint development initiative in partnership with the National Aeronautics and Space Administration (NASA) to provide satellite meteorology information and science to partner countries.
Additionally, as the flagship finance initiative under PREPARE, the State Department and USAID, in collaboration with the U.S. Development Finance Corporation (DFC), have opened an Adaptation Finance Window under the Climate Finance for Development Accelerator (CFDA), which aims to de-risk the development and scaling of companies and investment vehicles that mobilize private finance for climate adaptation.
Plan of Action
Recommendation 1: Mobilize private capital through results-based financing such as environmental impact bonds
Results-based financing (RBF) has long been a key component of USAID’s development aid strategy, offering innovative ways to mobilize finance by linking payments to specific outcomes. In recent years, Environmental Impact Bonds (EIBs) have emerged as a promising addition to the RBF toolkit and would greatly benefit as a mechanism for USAID to mobilize and scale novel climate adaptation. Thus, in alignment with the PREPARE plan, USAID should launch an EIB pilot focused on extreme heat through the Climate Finance for Development Accelerator (CFDA), a $250 million initiative designed to mobilize $2.5 billion in public and private climate investments by 2030. An EIB piloted through the CFDA can help unlock public and private climate financing that focuses on extreme heat adaptation solutions, which are sorely needed.
With this EIB pilot, the private sector, governments, and philanthropic investors raise the upfront capital and repayment is contingent on the project’s success in meeting predefined goals. By distributing financial risk among stakeholders in the private sector, government, and philanthropy, EIBs encourage investment in pioneering projects that might struggle to attract traditional funding due to their novel or unproven nature. This approach can effectively mobilize the necessary resources to drive climate adaptation solutions.
This approach can effectively mobilize the necessary resources to drive climate adaptation solutions.
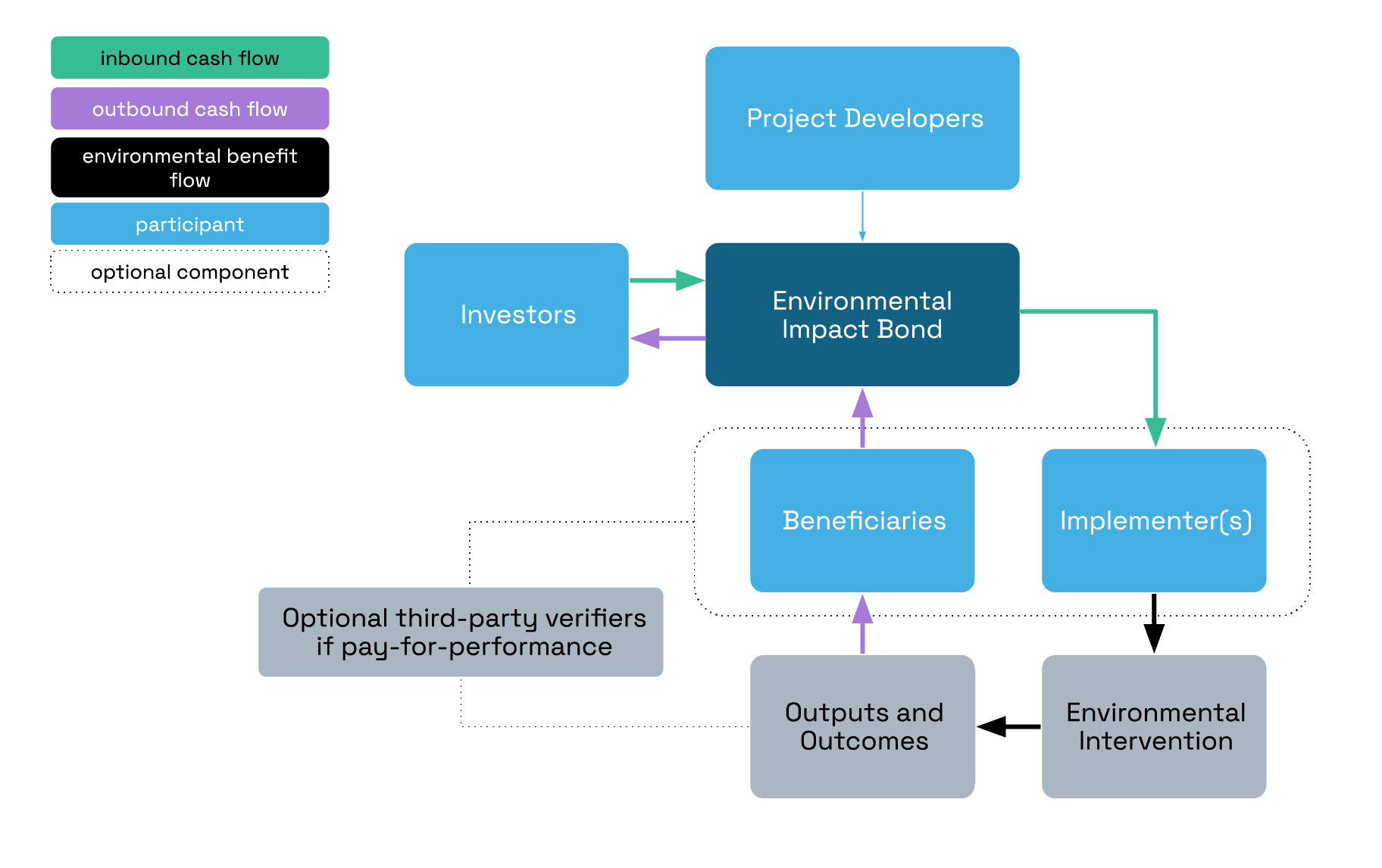
Overview of EIB structure, including cash flow (purple and green arrows) and environmental benefits (black arrows).
Adapted from Environmental Impact Bonds: a common framework and looking ahead
The USAID EIB pilot should focus on scaling projects that facilitate uptake and adoption of affordable and sustainable cooling systems such as solar-reflective roofing and other passive cooling strategies. In Southeast Asia alone, annual heat-related mortality is projected to increase by 295% by 2030. Lack of access to affordable and sustainable cooling mechanisms in the wake of record-shattering heat waves affects public health, food and supply chain, and local economies. An EIB that aims to fund and scale solar-reflective roofing (cool roofs) has the potential to generate high impact for the local population by lowering indoor temperature, reducing energy use for air conditioning, and mitigating the heat island effect in surrounding areas. Indonesia, which is home to 46.5 million people at high risk from a lack of access to cooling, has seen notable success in deploying cool roofs/solar-reflective roofing through the Million Cool Roof Challenge, an initiative of the Clean Cooling Collaborative. The country is now planning to scale production capacity of cool roofs and set up its first testing facility for solar-reflective materials to ensure quality and performance. Given Indonesia’s capacity and readiness, an EIB to scale cool roofs in Indonesia can be a force multiplier to see this cooling mechanism reach millions and spur new manufacturing and installation jobs for the local economy.
To mainstream EIBs and other innovative financial instruments, it is essential to pilot and explore more EIB projects. Cool roofs are an ideal candidate for scaling through an EIB due to their proven effectiveness as a climate adaptation solution, their numerous co-benefits, and the relative ease with which their environmental impacts can be measured (such as indoor temperature reductions, energy savings, and heat island index improvements). Establishing an EIB can be complex and time-consuming, but the potential rewards make the effort worthwhile if executed effectively. Though not exhaustive, the following steps are crucial to setting up an environmental impact bond:
Analyze ecosystem readiness
Before launching an environmental impact bond, it’s crucial to conduct an analysis to better understand what capacities already exist among the private and public sectors in a given country to implement something like an EIB. Additionally working with local civil society organizations is important to ensure climate adaptation projects and solutions are centered around the local community.
Determine the financial arrangement, scope, and risk sharing structure
Determine the financial structure of the bond, including the bond amount, interest rate, and maturity date. Establish a mechanism to manage the funds raised through the bond issuance.
Co-develop standardized, scientifically verified impact metrics and reporting mechanism
Develop a robust system for measuring and reporting the environmental impact projects; With key stakeholders and partner countries, define key performance indicators (KPIs) to track and report progress.
USAID has already begun to incubate and pilot innovative financing mechanisms in the global health space through development impact bonds. The Utkrisht Impact Bond, for example, is the world’s first maternal and newborn health impact bond, which aims to reach up to 600,000 pregnant women and newborns in Rajasthan, India. Expanding the use case of this financing mechanism in the climate adaptation sector can further leverage private capital to address critical environmental challenges, drive scalable solutions, and enhance the resilience of vulnerable communities to climate impacts.
Recommendation 2: USAID should expand the SERVIR joint initiative to include a partnership with NIHHIS and co-develop decision support tools such as an intersectional vulnerability map.
Building on the momentum of Administrator Power’s recent announcement at COP28, USAID should expand the SERVIR joint initiative to include a partnership with NOAA, specifically with NIHHIS, the National Integrated Heat Health Information System. NIHHIS is an integrated information system supporting equitable heat resilience, which is an important area that SERVIR should begin to explore. Expanded partnerships could begin with a pilot to map regional extreme heat vulnerability in select Southeast Asian countries. This kind of tool can aid in informing local decision makers about the risks of extreme heat that have many cascading effects on food systems, health, and infrastructure.
Intersectional vulnerabilities related to extreme heat refer to the compounding impacts of various social, economic, and environmental factors on specific groups or individuals. Understanding these intersecting vulnerabilities is crucial for developing effective strategies to address the disproportionate impacts of extreme heat. Some of these intersections include age, income/socioeconomic status, race/ethnicity, gender, and occupation. USAID should partner with NIHHIS to develop an intersectional vulnerability map that can help improve decision-making related to extreme heat. Exploring the intersectionality of extreme heat vulnerabilities is critical to improving local decision-making and helping tailor interventions and policies to where it is most needed. The intersection between extreme heat and health, for example, is an area that is under-analyzed, and work in this area will contribute to expanding the evidence base.
The pilot can be modeled after the SERVIR-Mekong program, which produced 21 decision support tools throughout the span of the program from 2014-2022. The SERVIR-Mekong program led to the training of more than 1,500 people, the mobilization of $500,000 of investment in climate resilience activities, and the adoption of policies to improve climate resilience in the region. In developing these tools, engaging and co-producing with the local community will be essential.
Recommendation 3: USAID REFS and the State Department Office of Foreign Assistance should work together to develop a mechanism to consistently track and report climate funding flow. This also requires USAID and the State Department to develop clear guidelines on the U.S. approach to adaptation tracking and determination of adaptation components.
Enhancing analytical and data collection capabilities is vital for crafting effective and informed responses to the challenges posed by extreme heat. To this end, USAID REFS, along with the State Department Office of Foreign Assistance, should co-develop a mechanism to consistently track and report climate funding flow. Currently, both USAID and the State Department do not consistently report funding data on direct and indirect climate adaptation foreign assistance. As the Department of State is required to report on its climate finance contributions annually for the Organisation for Economic Co-operation and Development (OECD) and biennially for the United Nations Framework Convention on Climate Change (UNFCCC), the two agencies should report on adaptation funding at similarly set, regular interval and make this information accessible to the executive branch and the general public. A robust tracking mechanism can better inform and aid agency officials in prioritizing adaptation assistance and ensuring the US fulfills its commitments and pledges to support global adaptation to climate change.
The State Department Office of Foreign Assistance (State F) is responsible for establishing standard program structures, definitions, and performance indicators, along with collecting and reporting allocation data on State and USAID programs. Within the framework of these definitions and beyond, there is a lack of clear definitions in terms of which foreign assistance projects may qualify as climate projects versus development projects and which qualify as both. Many adaptation projects are better understood on a continuum of adaptation and development activities. As such, this tracking mechanism should be standardized via a taxonomy of definitions for adaptation solutions.
Therefore, State F should create standardized mechanisms for climate-related foreign assistance programs to differentiate and determine the interlinkages between adaptation and mitigation action from the outset in planning, finance, and implementation — and thereby enhance co-benefits. State F relies on the technical expertise of bureaus, such as REFS, and the technical offices within them, to evaluate whether or not operating units have appropriately attributed funding that supports key issues, including indirect climate adaptation.
Further, announced at COP26, PREPARE is considered the largest U.S. commitment in history to support adaptation to climate change in developing nations. The Biden Administration has committed to using PREPARE to “respond to partner countries’ priorities, strengthen cooperation with other donors, integrate climate risk considerations into multilateral efforts, and strive to mobilize significant private sector capital for adaptation.” Co-led by USAID and the U.S. Department of State (State Department), the implementation of PREPARE also involves the Treasury, NOAA, and the U.S. International Development Finance Corporation (DFC). Other U.S. agencies, such as USDA, DOE, HHS, DOI, Department of Homeland Security, EPA, FEMA, U.S. Forest Service, Millennium Challenge Corporation, NASA, and U.S. Trade and Development Agency, will respond to the adaptation priorities identified by countries in National Adaptation Plans (NAPs) and nationally determined contributions (NDCs), among others.
As USAID’s REFS leads the implementation of the PREPARE and hosts USAID’s Chief Climate Officer, this office should be responsible for ensuring the agency’s efforts to effectively track and consistently report climate funding data. The two REFS Centers that should lead the implementation of these efforts include the Center for Climate-Positive Development, which advises USAID leadership and supports the implementation of USAID’s Climate Strategy, and the Center for Resilience, which supports efforts to help reduce recurrent crises — such as climate change-induced extreme weather events — through the promotion of risk management and resilience in the USAID’s strategies and programming.
In making standardized processes to prioritize and track the flow of adaptation funds, USAID will be able to more effectively determine its progress towards addressing global climate hazards like extreme heat, while enhancing its ability to deliver innovative finance and private capital mechanisms in alignment with PREPARE. Additionally, standardization will enable both the public and private sectors to understand the possible areas of investment and direct their flows for relevant projects.
USAID uses the Standardized Program Structure and Definitions (SPSD) system — established by State F — to provide a common language to describe climate change adaptation and resilience programs and therefore enable the comparison and analysis of budget and performance data within a country, regionally or globally. The SPSD system uses the following categories: (1) democracy, human rights, and governance; (2) economic growth; (3) education and social services; (4) health; (5) humanitarian assistance; (6) peace and security; and (7) program development and oversight. Since 2016, climate change has been in the economic growth category and each climate change pillar has separate Program Areas and Elements. The SPSD consists of definitions for foreign assistance programs, providing a common language to describe programs. By utilizing a common language, information for various types of programs can be aggregated within a country, regionally, or globally, allowing for the comparison and analysis of budget and performance data.
Using the SPSD program areas and key issues, USAID categorizes and tracks the funding for its allocations related to climate adaptation as either directly or indirectly addressing climate adaptation. Funding that directly addresses climate adaptation is allocated to the “Climate Change—Adaptation” under SPSD Program Area EG.11 for activities that enhance resilience and reduce the vulnerability to climate change of people, places, and livelihoods. Under this definition, adaptation programs may have the following elements: improving access to science and analysis for decision-making in climate-sensitive areas or sectors; establishing effective governance systems to address climate-related risks; and identifying and disseminating actions that increase resilience to climate change by decreasing exposure or sensitivity or by increasing adaptive capacity. Funding that indirectly addresses climate adaptation is not allocated to a specific SPSD program area. It is funding that is allocated to another SPSD program area and also attributed to the key issue of “Adaptation Indirect,” which is for adaptation activities. The SPSD program area for these activities is not Climate Change—Adaptation, but components of these activities also have climate adaptation effects.
In addition to the SPSD, the State Department and USAID have also identified “key issues” to help describe how foreign assistance funds are used. Key issues are topics of special interest that are not specific to one operating unit or bureau and are not identified, or only partially identified, within the SPSD. As specified in the State Department’s foreign assistance guidance for key issues, “operating units with programs that enhance climate resilience, and/or reduce vulnerability to climate variability and change of people, places, and/or livelihoods are expected to attribute funding to the Adaptation Indirect key issue.”
Operating units use the SPSD and relevant key issues to categorize funding in their operational plans. State guidance requires that any USAID operating unit receiving foreign assistance funding must complete an operational plan each year. The purpose of the operational plan is to provide a comprehensive picture of how the operating unit will use this funding to achieve foreign assistance goals and to establish how the proposed funding plan and programming supports the operating unit, agency, and U.S. government policy priorities. According to the operational plan guidance, State F does an initial screening of these plans.
MDBs play a critical role in bridging the significant funding gap faced by vulnerable developing countries that bear a disproportionate burden of climate adaptation costs—estimated to reach up to 20 percent of GDP for small island nations exposed to tropical cyclones and rising seas. MDBs offer a range of financing options, including direct adaptation investments, green financing instruments, and support for fiscal adjustments to reallocate spending towards climate resilience. To be most sustainably impactful, adaptation support from MDBs should supplement existing aid with conditionality that matches the institutional capacities of recipient countries.
In January 2021, President Biden issued an Executive Order (EO 14008) calling upon federal agencies and others to help domestic and global communities adapt and build resilience to climate change. Shortly thereafter in September 2022, the White House announced the launch of the PREPARE Action Plan, which specifically lays out America’s contribution to the global effort to build resilience to the impacts of the climate crisis in developing countries. Nineteen U.S. departments and agencies are working together to implement the PREPARE Action Plan: State, USAID, Commerce/NOAA, Millennium Challenge Corporation (MCC), U.S. Trade and Development Agency (USTDA), U.S. Department of Agriculture (USDA), Treasury, DFC, Department of Defense (DOD) & U.S. Army Corps of Engineers (USACE), International Trade Administration (ITA), Peace Corps, Environmental Protection Agency (EPA), Department of Energy (DOE), Federal Emergency Management Agency (FEMA), Department of Transportation (DOT), Health and Human Services (HHS), NASA, Export–Import Bank of the United States (EX/IM), and Department of Interior (DOI).
Congress oversees federal climate financial assistance to lower-income countries, especially through the following actions: (1) authorizing and appropriating for federal programs and multilateral fund contributions, (2) guiding federal agencies on authorized programs and appropriations, and (3) overseeing U.S. interests in the programs. Congressional committees of jurisdiction include the House Committees on Foreign Affairs, Financial Services, Appropriations, and the Senate Committees on Foreign Relations and Appropriations, among others.
Critical Thinking on Critical Minerals
How the U.S. Government Can Support the Development of Domestic Production Capacity for the Battery Supply Chain
Access to critical minerals supply chains will be crucial to the clean energy transition in the United States. Batteries for electric vehicles, in particular, will require the U.S. to consume an order of magnitude more lithium, nickel, cobalt, and graphite than it currently consumes. Currently, these materials are sourced from around the world. Mining of critical minerals is concentrated in just a few countries for each material, but is becoming increasingly geographically diverse as global demand incentivizes new exploration and development. Processing of critical minerals, however, is heavily concentrated in a single country—China—raising the risk of supply chain disruption.
To address this, the U.S. government has signaled its desire to onshore and diversify critical minerals supply chains through key legislation, such as the Bipartisan Infrastructure Law and the Inflation Reduction Act, and trade policies. The development of new mining and processing projects entails significant costs, however, and project financiers require developers to demonstrate certainty that projects will generate profit through securing long-term offtake agreements with buyers. This is made difficult by two factors: critical minerals markets are volatile, and, without subsidies or trade protections, domestically-produced critical minerals have trouble competing against low-priced imports, making it difficult for producers and potential buyers to negotiate a mutually agreeable price (or price floor). As a result, progress in expanding the domestic critical minerals supply may not occur fast enough to catch up to the growing consumption of critical minerals.
To accelerate project financing and development, the Department of Energy (DOE) should help generate demand certainty through backstopping the offtake of processed, battery-grade critical minerals at a minimum price floor. Ideally, this would be accomplished by paying producers the difference between the market price and the price floor, allowing them to sign offtake agreements and sell their products at a competitive market price. Offtake agreements, in turn, allow developers to secure project financing and proceed at full speed with development.
While demand-side support can help address the challenges faced by individual developers, market-wide issues with price volatility and transparency require additional solutions. Currently, the pricing mechanisms available for battery-grade critical minerals are limited to either third-party price assessments with opaque sources or the market exchange traded price of imperfect proxies. Concerns have been raised about the reliability of these existing mechanisms, hindering market participation and complicating discussions on pricing.
As the North American critical minerals industry and market develops, DOE should support the parallel development of more transparent, North American based pricing mechanisms to improve price discovery and reduce uncertainty. In the short- and medium-term, this could be accomplished through government-backed auctions, which could be combined with offtake backstop agreements. Auctions are great mechanisms for price discovery, and data from them can help improve market price assessments. In the long-term, DOE could support the creation of new market exchanges for trading critical minerals in North America. Exchange trading enables greater price transparency and provides opportunities for hedging against price volatility.
Through this two-pronged approach, DOE would simultaneously accelerate the development of the domestic critical minerals supply chain through addressing short-term market needs, while building a more transparent and reliable marketplace for the future.
Introduction
The global transportation system is currently undergoing a transition to electric vehicles (EVs) that will fundamentally transform not only our transportation system, but also domestic manufacturing and supply chains. Demand for lithium ion batteries, the most important and expensive component of EVs, is expected to grow 600% by 2030 compared to 2023, and the U.S. currently imports a majority of its lithium batteries. To ensure a stable and successful transition to EVs, the U.S. needs to reduce its import-dependence and build out its domestic supply chain for critical minerals and battery manufacturing.
Crucial to that will be securing access to battery-grade critical minerals. Lithium, nickel, cobalt, and graphite are the primary critical minerals used in EV batteries. All four were included in the 2023 Department of Energy (DOE) Critical Minerals List. Cobalt and graphite are considered at risk of shortage in the short-term (2020-2025), while all four materials are at risk in the medium-term (2025-2030).
As shown in Figure 1, the domestic supply chain for batteries and critical minerals consists primarily of downstream buyers like automakers and battery assemblers, though there are a growing number of battery cell manufacturers thanks to domestic sourcing requirements in the Inflation Reduction Act (IRA) incentives. The U.S. has major gaps in upstream and midstream activities—mining of critical minerals, refining/processing, and the production of active materials and battery components. These industries are concentrated globally in a small number of countries, presenting supply chain risks. By developing new domestic industries within these gaps, the federal government can help build out new, resilient clean energy supply chains.
This report is organized into three main sections. The first section provides an overview of current global supply chains and the process of converting different raw materials into battery-grade critical minerals. The second section delves into the pricing and offtake challenges that projects face and proposes demand-side support solutions to provide the price and volume certainty necessary to obtain project financing. The final section takes a look at existing pricing mechanisms and proposes two approaches that the government can take to facilitate price discovery and transparency, with an eye towards mitigating market volatility in the long term. Given DOE’s central role in supporting the development of domestic clean energy industries, the policies proposed in this report were designed with DOE in mind as the main implementer.
Adapted from Li-BRIDGE
Segments highlighting in light blue indicated gaps in U.S. supply chains. See original graphic from Li-BRIDGE for more information.
Section 1. Understanding Critical Minerals Supply Chains
Global Critical Minerals Sources
Globally, 65% or more of processed lithium, cobalt, and graphite originates from a single country: China (Figure 2). This concentration is particularly acute for graphite, 91% of which was processed by China in 2023. This market concentration has made downstream buyers in the U.S. overly dependent on sourcing from a single country. The concentration of supply chains in any one country makes them vulnerable to disruptions within that country—whether they be natural disasters, pandemics, geopolitical conflict, or macroeconomic changes. Moreover, lithium, nickel, cobalt, and graphite are all expected to experience shortages over the next decade. In the case of future shortages, concentration in other countries puts U.S. access to critical minerals at risk. Rocky foreign relations and competition between the U.S. and China over the past few years have put further strain on this dependence. In October 2023, China announced new export controls on graphite, though it has not yet restricted supply, in response to the U.S.’s export restrictions on semiconductor chips to China and other “foreign entities of concern” (FEOC).
Expanding domestic processing of critical minerals and manufacturing of battery components can help reduce dependence on Chinese sources and ensure access to critical minerals in future shortages. However, these efforts will hurt Chinese businesses, so the U.S. will also need to anticipate additional protectionist measures from China.
On the other hand, mining of critical minerals—with the exception of graphite and rare earth elements—occurs primarily outside of China. These operations are also concentrated in a small handful of countries, shown in Figure 3. Consequently, geopolitical disruptions affecting any of those primary countries can significantly affect the price and supply of the material globally. For example, Russia is the third largest producer of nickel. In the aftermath of Russia’s invasion of Ukraine at the beginning of 2022, expectations of shortages triggered a historic short squeeze of nickel on the London Metal Exchange (LME), the primary global trading platform, significantly disrupting the global market.
To address global supply chain concentration, new incentives and grant programs were passed in the IRA and the Bipartisan Infrastructure Law. These include the 30D clean vehicle tax credit, the 45X advanced manufacturing production credit, and the Battery Materials Processing Grants Program (see Domestic Price Premium section for further discussion). Thanks to these policies, there are now on the order of a hundred North American projects in mining, processing, and active1 material manufacturing in development. The success of these and future projects will help create new domestic sources of critical minerals and batteries to feed the EV transition in the U.S. However, success is not guaranteed. A number of challenges to investment in the critical minerals supply chain will need to be addressed first.
Battery Materials Supply Chain
Critical minerals are used to make battery electrodes. These electrodes require specific forms of critical minerals for their production processes: typically lithium hydroxide or carbonate, nickel sulfate, cobalt sulfate, and a blend of coated spherical graphite and synthetic graphite.2
Lithium hydroxide/carbonate typically comes from two sources: spodumene, a hard rock ore that is mined primarily in Australia, and lithium brine, which is primarily found in South America (Figure 3). Traditionally, lithium brine must be evaporated in large open-air pools before the lithium can be extracted, but new technologies are emerging for direct lithium extraction that significantly reduces the need for evaporation. Whereas spodumene mining and refining are typically conducted by separate entities, lithium brine operations are typically fully integrated. A third source of lithium that has yet to be put into commercial production is lithium clay. The U.S. is leading the development of projects to extract and refine lithium from clay deposits.
Nickel sulfate can be made from either nickel metal, which was historically the preferred feedstock, or directly from nickel intermediate products, such as mixed hydroxide precipitate and nickel matte, which are the feedstocks that most Chinese producers have switched to in the past few years (Figure 4). Though demand from batteries is driving much of the nickel project development in the U.S., since nickel metal has a much larger market than nickel sulfate, developers are designing their projects with the flexibility to produce either nickel metal or nickel sulfate.
Cobalt is primarily produced in the Democratic Republic of the Congo from cobalt-copper ore. Cobalt can also be found in lesser amounts in nickel and other metallic ores. Cobalt concentrate is extracted from cobalt-bearing ore and then processed into cobalt hydroxide. At this point, the cobalt hydroxide can be further processed into either cobalt sulfate for batteries or cobalt metal and other chemicals for other purposes.
Battery cathodes come in a variety of chemistries: lithium nickel manganese cobalt (NMC) is the most common in lithium-ion batteries thanks to its higher energy density, while lithium iron phosphate is growing in popularity for its affordability and use of more abundantly available materials, but is not as energy dense. Cathode active material (CAM) manufacturers purchase lithium hydroxide/carbonate, nickel sulfate, and cobalt sulfate and then convert them into CAM powders. These powders are then sold to battery cell manufacturers, who coat them onto copper electrodes to produce cathodes.
Graphite can be synthesized from petroleum needle coke, a fossil fuel waste material, or mined from natural deposits. Natural graphite typically comes in the form of flakes and is reshaped into spherical graphite to reduce its particle size and improve its material properties. Spherical graphite is then coated with a protective layer to prevent unwanted chemical reactions when charging and discharging the battery.
The majority of battery anodes on the market are made using just graphite, so there is no intermediate step between processors and battery cell manufacturers. Producers of battery-grade synthetic graphite and coated spherical graphite sell these materials directly to cell manufacturers, who coat them onto electrodes to make anodes. These battery-grade forms of graphite are also referred to as graphite anode powder or, more generally, as anode active materials. Thus, the terms graphite processor and graphite anode manufacturer are interchangeable.
Section 2. Building Out Domestic Production Capacity
Challenges Facing Project Developers
Offtake Agreements
Offtake agreements (a.k.a. supply agreements or contracts) are an agreement between a producer and a buyer to purchase a future product. They are a key requirement for project financing because they provide lenders and investors with the certainty that if a project is built, there will be revenue generated from sales to pay back the loan and justify the valuation of the business. The vast majority of feedstocks and battery-grade materials are sold under offtake agreements, though small amounts are also sold on the spot market in one-off transactions. Offtake agreements are made at every step of the supply chain: between miners and processors (if they’re not vertically integrated), between processors and component manufacturers; and between component manufacturers and cell manufacturers. Due to domestic automakers’ concerns about potential material shortages upstream and the desire to secure IRA incentives, many of them have also been entering into offtake agreements directly with North American miners and processors. Tesla has started constructing their own domestic lithium processing plant.
Historically, these offtake agreements were structured as fixed-price deals. However, when prices on the spot market go too high, sellers often find a way to rip up the contract, and vice versa, when spot prices go too low, buyers often find a way to get out of the contract. As a result, more and more offtake agreements for battery-grade lithium, nickel, and cobalt have become indexed to spot prices, with price floors and/or ceilings set as guardrails and adjustments for premiums and discounts based on other factors (e.g. IRA compliance, risk from a greenfield producer, etc.).
Graphite is the one exception where buyers and suppliers have mostly stuck to fixed-price agreements. There are two main reasons for this: graphite pricing is opaque and products exhibit much more variation, complicating attempts to index the price. As a result, cell manufacturers don’t consider the available price indexes to accurately reflect the value of the specific products they are buying.
Offtake agreements for battery cells are also typically partially indexed on the price of the critical minerals used to manufacture them. In other words, a certain amount of the price per unit of battery cell is fixed in the agreement, while the rest is variable based on the index price of critical minerals at the time of transaction.
Domestic critical minerals projects face two key challenges to securing investment and offtake agreements: market volatility and a lack of price competitiveness. The price difference between materials produced domestically and those produced internationally stems from two underlying causes: the current oversupply from Chinese-owned companies and the domestic price premium.
Market Volatility
Lithium, cobalt, and graphite have relatively low-volume markets with a small customer base compared to traditional commodities. Low-volume products experience low liquidity, meaning it can be difficult to buy or sell quickly, so slight changes in supply and demand can result in sharp price swings, creating a volatile market. Because of the higher risk and smaller market, companies and investors tend to prefer mining and processing of base metals, such as copper, which have much larger markets, resulting in underinvestment in production capacity.
In comparison, nickel is a base metal commodity, primarily used for stainless steel production. However, due to its rapidly growing use in battery production, its price has become increasingly linked to other battery materials, resulting in greater volatility than other base metals. Moreover, the short squeeze in 2022 forced LME to suspend trading and cancel transactions for the first time in three decades. As a result, trust in the price of nickel on LME faltered, many market participants dropped out, and volatility grew due to low trading volumes.
For all four of these materials, prices reached record highs in 2022 and subsequently crashed in 2023 (Figure 4). Nickel, cobalt, and graphite experienced price declines of 30-45%, while lithium prices dropped by an enormous 75%. As discussed above, market volatility discourages investment into critical minerals production capacity. The current low prices have caused some domestic projects to be paused or canceled. For example, Jervois halted operation of its Idaho cobalt mine in March 2023 due to cobalt prices dropping below its operating costs. In January 2024, lithium giant Albemarle announced that it was delaying plans to begin construction on a new South Carolina lithium hydroxide processing plant.
Retrospective analysis suggests that mining companies, battery investors, and automakers had all made overly optimistic demand projections and ramped up their production a bit too fast. These projections assumed that EV demand would keep growing as fast as it did immediately after the pandemic and that China’s lifting of pandemic restrictions would unlock even faster growth in the largest EV market. Instead, China, which makes up over 60% of the EV market, emerged into an economic downturn, and global demand elsewhere didn’t grow quite as fast as projected, as backlogs built up during the pandemic were cleared. (It is important to note that the EV market is still growing at significant rates—global EV sales increased by 35% from 2022 to 2023—just not as fast as companies had wished.) Consequently, supply has temporarily outpaced demand. Midstream and upstream companies stopped receiving new purchase orders while automakers worked through their stock build-up. Prices fell rapidly as a result and are now bottoming out. Some companies are waiting for prices to recover before they restart construction and operation of existing projects or invest in expanding production further.
While companies are responding to short-term market signals, the U.S. government needs to act in anticipation of long-term demand growth outpacing current planned capacity. Price volatility in critical minerals markets will need to be addressed to ensure that companies and financiers continue investing in expanding production capacity. Otherwise, demand projections suggest that the supply chain will experience new shortages later this decade.
Oversupply
The current oversupply of critical minerals has been exacerbated by below market-rate financing and subsidies from the Chinese government. Many of these policies began in 2009, incentivizing a wave of investment not just in China, but also in mineral-rich countries. These subsidies played a large role in the 2010s in building out nascent battery critical minerals supply chains. Now, however, they are causing overproduction from Chinese-owned companies, which threatens to push out competitors from other countries.
Overproduction begins with mining. Chinese companies are the primary financial backers for 80% of both the Democratic Republic of the Congo’s cobalt mines and Indonesia’s nickel mines. Chinese companies have also expanded their reach in lithium, buying half of all the lithium mines offered for sale since 2018, in addition to domestically mining 18% of global lithium. For graphite, 82% of natural graphite was mined directly in China in 2023, and nearly all natural and synthetic graphite is processed in China.
After the price crash in 2023, while other companies pulled back their production volume significantly, Chinese-owned companies pulled back much less and in some cases continued to expand their production, generating an oversupply of lithium, cobalt, nickel, and natural and synthetic graphite. Government policies enabled these decisions by making it financially viable for Chinese companies to sell materials at low prices that would otherwise be unsustainable.
Domestic Price Premium (and Current Policies Addressing It)
Domestically-produced critical minerals and battery electrode active materials come with a higher cost of production over imported materials due to higher wages and stricter environmental regulations in the U.S. The IRA’s new 30D and 45X tax credit and upcoming section 301 tariffs help address this problem by creating financial incentives for using domestically produced materials, allowing them to compete on a more even playing field with imported materials.
The 30D New Clean Vehicle Tax Credit provides up to $7,500 per EV purchased, but it requires eligible EVs to be manufactured from critical minerals and battery components that are FEOC-compliant, meaning they cannot be sourced from companies with relationships to China, North Korea, Russia, and Iran. It also requires that an increasing percentage of critical minerals used to make the EV batteries be extracted or processed in the U.S. or a Free Trade Agreement country. These two requirements apply to lithium, nickel, cobalt, and graphite. For graphite, however, since nearly all processing occurs in China and there is currently no domestic supply, the US Treasury has chosen to exempt it from the 30D tax credit’s FEOC and domestic sourcing requirements until 2027 to give automakers time to develop alternate supply chains.
The 45X Advanced Manufacturing Production Tax Credit subsidizes 10% of the production cost for each unit of critical minerals processed. The Internal Revenue Service’s proposed regulations for this tax credit interprets the legislation for 45X as applying only to the value-added production cost, meaning that the cost of purchasing raw materials and processing chemicals is not included in the covered production costs. This limits the amount of subsidy that will be provided to processors. The strength of 45X, though, is that unlike the 30D tax credit, there is no sunset clause for critical minerals, providing a long term guarantee of support.
In terms of tariffs, the Biden administration announced in May 2024, a new set of section 301 tariffs on Chinese products, including EVs, batteries, battery components, and critical minerals. The critical minerals tariffs include a 25% tariff on cobalt ores and concentrates that will go into effect in 2024 and a 25% tariff on natural flake graphite that will go into effect in 2026. In addition, there are preexisting 25% tariffs in section 301 for natural and synthetic graphite anode powder. These tariffs were previously waived to give automakers time to diversify their supply chains, but the U.S. Trade Representative (USTR) announced in May 2024 that the exemptions would expire for good on June 14th, 2024, citing the lack of progress from automakers as a reason for not extending them.
Current State of Supply Chain Development
For lithium, despite market volatility, offtake demand for existing domestic projects has remained strong thanks to IRA incentives. Based on industry conversations, many of the projects that are developed enough to make offtake agreements have either signed away their full output capacity or are actively in the process of negotiating agreements. Strong demand combined with tax incentives has enabled producers to negotiate offtake agreements that guarantee a price floor at or above their capital and operating costs. Lithium is the only material for which the current planned mining and processing capacity for North America is expected to meet demand from planned U.S. gigafactories.
Graphite project developers report that the 25% tariff coming into force will be sufficient to close the price gap between domestically produced materials and imported materials, enabling them to secure offtake agreements at a sustainable price. Furthermore, the Internal Revenue Service will require 30D tax credit recipients to submit period reports on progress that they are making on sourcing graphite outside of China. If automakers take these reports and the 2027 exemption deadline seriously, there will be even more motivation to work with domestic graphite producers. However, the current planned production capacity for North America still falls significantly short of demand from planned U.S. battery gigafactories. Processing capacity is the bottleneck for production output, so there is room for additional investment in processing capacity.
Pricing has been a challenge for cobalt though. Jervois briefly opened the only primary cobalt mine in the U.S. before shutting down a few months later due to the price crash. Jervois has said that as soon as prices for standard-grade cobalt rise above $20/pound, they will be able to reopen the mine, but that has yet to happen. Moreover, the real bottleneck is in cobalt processing, which has attracted less attention and investment than other critical minerals in the U.S. There are currently no cobalt sulfate refineries in North America; only one or two are in development in the U.S. and a few more in Canada.3
Nickel sulfate is also facing pricing challenges, and, similar to cobalt, there is an insufficient amount of nickel sulfate processing capacity being developed domestically. There is one processing plant being developed in the U.S. that will be able to produce either nickel metal or nickel sulfate and a few more nickel sulfate refineries being developed in Canada.
Policy Solutions to Support the Development of Processing Capacity
The U.S. government should prioritize the expansion of processing capacity for lithium, graphite, cobalt, and nickel. Demand from domestic battery manufacturing is expected to outpace the current planned capacity for all of these materials, and processing capacity is the key bottleneck in the supply chain. Tariffs and tax incentives have resulted in favorable pricing for lithium and graphite project developers, but cobalt and nickel processing has gotten less support and attention.
DOE should provide demand-side support for processed, battery-grade critical minerals to accelerate the development of processing capacity and address cobalt and nickel pricing needs. The Office of Manufacturing and Energy Supply Chains (MESC) within DOE would be the ideal entity to administer such a program, given its mandate to address vulnerabilities in U.S. energy supply chains. In the immediate term, funding could come from MESC’s Battery Materials Processing Grants program, which has roughly $1.9B in remaining, uncommitted funds. Below we propose a few demand-support mechanisms that MESC could consider.
Long term, the Bipartisan Policy Center proposes that Congress establish and appropriate funding for a new government corporation that would take on the responsibility of administering demand-support mechanisms as necessary to mitigate volume and price uncertainty and ensure that domestic processing capacity grows to sufficiently meet critical minerals needs.
Offtake Backstops
Offtake backstops would commit MESC to guaranteeing the purchase of a specific amount of materials at a minimum negotiated price if producers are unable to find buyers at that price. This essentially creates a price floor for specific producers while also providing a volume guarantee. Offtake backstops help derisk project development and enable developers to access project financing. Backstop agreements should be made for at least the first five years of a plant’s operations, similar to a regular offtake agreement. Ideally, MESC should prioritize funding for critical minerals with the largest expected shortages based on current planned capacity—i.e., nickel, cobalt, and graphite.
There are two primary ways that DOE could implement offtake backstops:
First. The simplest approach would be for DOE to pay processors the difference between the spot price index (adjusted for premiums and discounts) and the pre-negotiated price floor for each unit of material, similar to how a pay-for-difference or one-sided contract-for-difference would work.4 This would enable processors to sign offtake agreements with no price floor, accelerating negotiations and thus the pace of project development. Processors could also choose to keep some of their output capacity uncommitted so that they can sell their products on the spot market without worrying about prices collapsing in the future.
A more limited form of this could look like DOE subsidizing the price floor for specific offtake agreements between a processor and a buyer. This type of intervention requires a bit more preliminary work from processors, since they would have to identify and bring a buyer to the table before applying for support.
Second. Purchasing the actual materials would be a more complex route for DOE to take, since the agency would have to be ready to receive delivery of the materials. The agency could do this by either setting up a system of warehouses suitable for storing battery-grade critical minerals or using “virtual warehousing,” as proposed by the Bipartisan Policy Center. An actual warehousing system could be set up by contracting with existing U.S. warehouses, such as those in LME and CME’s networks, to expand or upgrade their facilities to store critical minerals. These warehouses could also be made available for companies’ to store their private stockpiles, increasing the utility of the warehousing system and justifying the cost of setting it up. Virtual warehousing would entail DOE paying producers to store materials on-site at their processing plants.
The physical reserve provides an additional opportunity for DOE to address market volatility by choosing when it sells materials from the reserve. For example, DOE could pause sales of a material when there is an oversupply on the market and prices dip or ramp up sales when there is a shortage and prices spike. However, this can only be used to address short-term fluctuations in supply and demand (e.g. a few months to a few years at most), since these chemicals have limited shelf lives.
A third way to implement offtake backstops that would also support price discovery and transparency is discussed in Section 3.
Section 3. Creating Stable and Transparent Markets
Concerns about Pricing Mechanisms
Market volatility in critical minerals markets has raised concerns about just how reliable the current pricing mechanisms for these markets are. There are two main ways that prices in a market are determined: third-party price assessments and market exchanges. A third approach that has attracted renewed attention this year is auctions. Below, we walk through these three approaches and propose potential solutions for addressing challenges in price discovery and transparency.
Index Pricing
Price reporting agencies like Fastmarkets and Benchmark Mineral Intelligence offer subscription services to help market participants assess the price of commodities in a region. These agencies develop rosters of companies for each commodity, who regularly contribute information on transaction prices. That intel is then used to generate price indexes. Fastmarkets and Benchmark’s indexes are primarily based on prices provided by large, high-volume sellers and buyers. Smaller buyers may pay higher than index prices.
It can be hard to establish reliable price indexes in immature markets if there is an insufficient volume of transactions or if the majority of transactions are made by a small set of companies. For example, lithium processing is concentrated among a small number of companies in China and spot transactions are a minority share of the market. New entrants and smaller producers have raised concern that these companies have significant control over Asian spot prices reported by Fastmarkets and Benchmark, which are used to set offtake agreement prices, and that the price indexes are not sufficiently transparent.
Exchange Trading
Market exchanges are a key feature of mature markets that helps reduce market volatility. Market exchanges allow for a wider range of participants, improving market liquidity, and enables price discovery and transparency. Companies up and down the supply chain can use physically-delivered futures and options contracts to hedge against price volatility and gain visibility into expectations for the market’s general direction to help inform decision-making. This can help derisk the effect of market volatility on investments in new production capacity.
Of the materials we’ve discussed, nickel and cobalt metal are the only two that are physically traded on a market exchange, specifically LME. Metals make good exchange commodities due to their fungibility. Other forms of nickel and cobalt are typically priced as a percentage of the payable price for nickel and cobalt metal. LME’s nickel price is used as the global benchmark for many nickel products, while the in-warehouse price of cobalt metal in Rotterdam, Europe’s largest seaport, is used as the global benchmark for many cobalt products. These pricing relationships enable companies to use nickel and cobalt metal as proxies for hedging related materials.
After nickel trading volumes plummeted on LME in the wake of the short squeeze, doubts were raised about LME’s ability to accurately benchmark its price, sparking interest in alternative exchanges. In April 2024, UK-based Global Commodities Holdings Ltd (GCHL) launched a new trading platform for nickel metal that is only available to producers, consumers, and merchants directly involved in the physical market, excluding speculative traders. The trading platform will deliver globally “from Baltimore to Yokohama.” GCHL is using the prices on the platform to publish its own price index and is also working with Intercontinental Exchange to create cash-settled derivatives contracts. This new platform could potentially expand to other metals and critical minerals.
In addition to LME’s troubles though, changes in the battery supply chain have led to a growing divergence between the nickel and cobalt metal traded on exchanges and the actual chemicals used to make batteries. Chinese processors who produce most of the global supply of nickel sulfate have mostly switched from nickel metal to cheaper nickel intermediate products as their primary feedstock. Consequently, market participants say that the LME exchange price for nickel metal, which is mostly driven by stainless steel, no longer reflects market conditions for the battery sector, raising the need for new tradeable contracts and pricing mechanisms. For the cobalt industry, 75% of demand comes from batteries, which use cobalt sulfate. Cobalt metal makes up only 18% of the market, of which only 10-15% is traded on the spot market. As a result, cobalt chemicals producers have transitioned away from using the metal reference price towards fixed-prices or cobalt sulfate payables.
These trends motivate the development of new exchange contracts for physically trading nickel and cobalt chemicals that can enable price discovery separate from the metals markets. There is also a need to develop exchange contracts for materials like lithium and graphite with immature markets that exhibit significant volatility.
However, exchange trading of these materials is complicated by their nature as specialty chemicals: they have limited shelf lives and more complex storage requirements, unlike metal commodities. Lithium and graphite products also exhibit significant variations that affect how buyers can use them. For example, depending on the types and level of impurities in lithium hydroxide/carbonate, manufacturers of cathode active materials may need to conduct different chemical processes to remove them. Offtakers may also require that products meet additional specifications based on the characteristics they need for their CAM and battery chemistries.
For these reasons, major exchanges like LME, the Chicago Mercantile Exchange (CME), and the Singapore Exchange (SGX) have instead chosen to launch cash-settled contracts for lithium hydroxide/carbonate and cobalt hydroxide that allow for financial trading, but require buyers and sellers to arrange physical delivery separately from the exchange. Large firms have begun to participate increasingly in these derivatives markets to hedge against market volatility, but the lack of physical settlement limits their utility to producers who still need to physically deliver their products in order to make a profit. Nevertheless, CME’s contracts for lithium and cobalt have seen significant growth in transaction volume. LME, CME, and SGX all use Fastmarkets’ price indexes as the basis for their cash-settled contracts.
As regional industries mature and products become more standardized, these exchanges may begin to add physically settled contracts for battery-grade critical minerals. For example, the Guangzhou Futures Exchange (GFEX) in China, where the vast majority of lithium refining currently occurs, began offering physically settled contracts for lithium carbonate in August 2023. Though the exchange exhibited significant volatility in its first few months, raising concerns, the first round of physical deliveries in January 2024 occurred successfully, and trading volumes have been substantial this year. Access to GFEX is currently limited to Chinese entities and their affiliates, but another trading platform could come to do the same for North America over the next few decades as lithium production volume grows and a spot market emerges. Abaxx Exchange, a Singapore-based startup, has also launched a physically settled futures contract for nickel sulfate with delivery points in Singapore and Rotterdam. A North American delivery point could be added as the North American supply chain matures.
No market exchange for graphite currently exists, since products in the industry vary even greater than other materials. Even the currently available price indexes are not seen as sufficiently robust for offtake pricing.
Auctions
In the absence of a globally accessible market exchange for lithium and concerns about the transparency of index pricing, Albemarle, the top producer of lithium worldwide, has turned to auctions of spodumene concentrate and lithium carbonate as a means to improve market transparency and an “approach to price discovery that can lead to fair product valuation.” Albemarle’s first auction in March of spodumene concentrate in China closed at a price of $1200/ton, which was in line with spot prices reported by Asian Metal, but about 10% greater than prices provided by other price reporting agencies like Fastmarkets. Plans are in place to continue conducting regular auctions at the rate of about one per week in China and other locations like Australia. Lithium hydroxide will be auctioned as well. Auction data will be provided to Fastmarkets and other price reporting agencies to be formulated into publicly available price indexes.
Auctions are not a new concept: in 2021 and 2022, Pilbara Minerals regularly conducted auctions of spodumene on its own platform Battery Metals Exchange, helping to improve market sentiment. Now, though, the company says that most of its material is now committed to offtakers, so auctions have mostly stopped, though it did hold an auction for spodumene concentrate in March. If other lithium producers join Albemarle in conducting auctions, the data could help improve the accuracy and transparency of price indexes. Auctions could also be used to inform the pricing of other battery-grade critical minerals.
Policy Solutions to Support Price Discovery and Transparency Across the Market
Right now, the only pricing mechanisms available to domestic project developers are spot price indexes for battery-grade critical minerals in Asia or global benchmarks for proxies like nickel and cobalt metal. Long-term, the development of new pricing mechanisms for North America will be crucial to price discovery and transparency in this new market. There are two ways that DOE could help facilitate this: one that could be implemented immediately for some materials and one that will require domestic production volume to scale up first.
First. Government-Backed Auctions: Auctions require project developers to keep a portion of their expected output uncommitted to any offtakers. However, there is a risk that future auctions won’t generate a price sufficient to offset capital and operating expenses, so processors are unlikely to do this on their own, especially for their first domestic project. MESC could address this by providing a backstop guarantee for the portion of a producer’s output that they commit to regularly auctioning for a set timespan. If, in the future, auctions are unable to generate a price above a pre-negotiated price floor, then DOE would pay sellers the difference between the highest auction price and the price floor for each unit sold. Such an agreement could be made using DOE’s Other Transaction Authority. DOE could separately contract with a platform such as MetalsHub to conduct the auction.
Government-backed auctions would enable the discovery of a true North American price for different battery-grade critical minerals and the raw materials used to make them, generating a useful comparison point with Asian spot prices. Such a scheme would also help address developers’ price and demand needs for project financing. These backstop-auction agreements could be complementary to the other types of backstop agreements proposed earlier and potentially more appealing than physically offtaking materials since the government would not have to receive delivery of the materials and there would be a built-in mechanism to sell the materials to an appropriate buyer. If successful, companies could continue to conduct auctions independently after the agreements expire.
Second. New Benchmark Contracts: Employ America has proposed that the Loan Programs Office (LPO) could use Section 1703 to guarantee lending to a market exchange to develop new, physically settled benchmark contracts for battery-grade critical minerals. The development of new contracts should include producers in the entire North American region. Canada also has a significant number of mines and processing plants in development. Including those projects would increase the number of participants, market volume, and liquidity of new benchmark contracts.
In order for auctions or new benchmark contracts to operate successfully, three prerequisites must be met:
- There must be a sufficient volume of materials available for sale (i.e. production output that is not committed to an offtaker).
- There must be sufficient product standardization in the industry such that materials produced by different companies can be used interchangeably by a significant number of buyers.
- There must be a sufficient volume of demand from buyers, brokers, and traders.
Market exchanges typically conduct research into stakeholders to understand whether or not the market is mature enough to meet these requirements before they launch a new contract. Interest from buyers and sellers must indicate that there would be sufficient trading volume for the exchange to make a profit greater than the cost of setting up the new contract. A loan from LPO under Section 1703 can help offset some of those upfront costs and potentially make it worthwhile for an exchange to launch a new contract in a less mature market than they typically would.
Government-backed auctions, on the other hand, solve the first prerequisite by offering guarantees to producers for keeping a portion of their production output uncommitted. Product standardization can also be less stringent, since each producer can hold separate auctions, with varying material specifications, unlike market exchanges where there must be a single set of product standards.
Given current market conditions, no battery-grade critical minerals can meet the above prerequisites for new benchmark contracts, primarily due to a lack of available volume, though there are also issues with product standardization for certain materials. However, nickel, cobalt, lithium, and graphite could be good candidates for government-backed auctions. DOE should start engaging with project developers that have yet to fully commit their output to offtakers and gauge their interest in backstop-auction agreements.
Nickel and Cobalt
As discussed prior, there are only a handful of nickel and cobalt sulfate refineries currently being developed in North America, making it difficult to establish a benchmark contract for North America. None of the project developers have yet signed offtake agreements covering their full production capacity, so backstop-auction agreements could be appealing to project developers and their investors. Given that more than half of the projects in development are located in Canada, MESC and DOE’s Office of International Affairs should collaborate with the Canadian government in designing and implementing government-backed auctions.
Lithium
Domestic companies have expressed interest in establishing North American-based spot markets and price indexes for lithium hydroxide and carbonate, but say that it will take quite a few years before production volume is large enough to warrant that. Product variation has also been a concern from lithium processors when the idea of a market exchange or public auction has been raised. Lessons could be learned from the GFEX battery-grade lithium carbonate contracts. GFEX set standards on the purity, moisture, loss on ignition, and maximum content of different impurities. Some Chinese companies were able to meet these standards, while others were not, preventing them from participating in the futures market or requiring them to trade their materials as lower-purity industrial-grade lithium carbonate, which sells for a discounted price. Other companies producing lithium of much higher quality than the GFEX standards, opted to continue selling on the spot market because they could charge a premium on the standard price. Despite some companies choosing not to participate, trading volumes on GFEX have been substantial, and the exchange was able to weather through initial concerns of a short squeeze, suggesting that challenges with product variation can be overcome through standardization.
Analysts have proposed that spodumene could be a better candidate for exchange trading, since it is fungible and does not have the limited shelf-life or storage requirements of lithium salts. 60% of global lithium comes from spodumene, and the U.S. has some of the largest spodumene deposits in the world, so spodumene would be a good proxy for lithium salts in North America. However, the two domestic developers of spodumene mines are planning to construct processing plants to convert the spodumene into battery-grade lithium on-site. Similarly, the two Canadian mines that currently produce spodumene are also planning to build their own processing plants. These vertical integration plans mean that there is unlikely to be large amounts of spodumene available for sale on a market exchange in the near future.
DOE could, however, work with miners and processors to sign backstop-auction agreements for smaller amounts of lithium hydroxide/carbonate and spodumene that they have yet to commit to offtakers. This may be especially appealing to companies that have announced delays to project development due to current low market prices and help derisk bringing timelines forward. Interest in these future auctions could also help gauge the potential for developing new benchmark contracts for lithium hydroxide/carbonate further down the line.
Graphite
Natural and synthetic graphite anode material products currently exhibit a great range of variation and insufficient product standardization, so a market exchange would not be viable at the moment. As the domestic graphite industry develops, DOE should work with graphite anode material producers and battery manufacturers to understand the types and degree of variations that exist across products and discuss avenues towards product standardization. Government-backed auctions could be a smaller-scale way to test the viability of product standards developed from that process, perhaps using several tiers or categories to group products. Natural and synthetic graphite would have to be treated separately, of course.
Conclusion
The current global critical minerals supply chain partially reflects the results of over a decade of focused, industrial policies implemented by the Chinese government. If the U.S. wants to lead the clean energy transition, critical minerals will also need to become a cornerstone of U.S. industrial policy. Developing a robust North American critical minerals industry would bolster U.S. energy security and independence and ensure a smooth energy transition.
Promising progress has already been made in lithium, with planned processing capacity expected to meet demand from future battery manufacturing. However, market and pricing challenges remain for battery-grade nickel, cobalt, and graphite, which will fall far short of future demand without additional intervention. This report proposes that DOE take a two-pronged approach to supporting the critical minerals industry through offtake backstops, which address project developers’ current pricing dilemmas, and the development of more reliable and transparent pricing mechanisms such as government-backed auctions, which will set up markets for the future.
While the solutions proposed in this report focus on DOE as the primary implementer, Congress also has a role to play in authorizing and appropriating new funding necessary to execute a cohesive industrial strategy on critical minerals . The policies proposed in this report can also be applied to other critical minerals crucial for the energy transition and our national security. Similar analysis of other critical minerals markets and end uses should be conducted to understand how these solutions can be tailored to those industry needs.
GenAI in Education Research Accelerator (GenAiRA)
The United States faces a critical challenge in addressing the persistent learning opportunity gaps in math and reading, particularly among disadvantaged student subgroups. According to the 2022 National Assessment of Educational Progress (NAEP) data, only 37% of fourth-grade students performed at or above the proficient level in math, and 33% in reading. The rapid advancement of generative AI (GenAI) technologies presents an unprecedented opportunity to bridge these gaps by providing personalized learning experiences and targeted support. However, the current mismatch between the speed of GenAI innovation and the lengthy traditional research pathways hinders the thorough evaluation of these technologies before widespread adoption, potentially leading to unintended negative consequences.
Failure to adapt our research and regulatory processes to keep pace with the development of GenAI technologies could expose students to ineffective or harmful educational tools, exacerbate existing inequities, and hinder our ability to prepare all students for success in an increasingly complex and technology-driven world. The education sector must act with urgency to establish the necessary infrastructure, expertise, and collaborative partnerships to ensure that GenAI-powered tools are rigorously evaluated, continuously improved, and equitably implemented to benefit all students.
To address this challenge, we propose three key recommendations for congressional action:
- Establish the GenAI in Education Research Accelerator Program (GenAiRA) within the Institute of Education Sciences (IES) to support and expedite efficacy research on GenAI-powered educational tools.
- Adapt IES research and evaluation processes to create a framework for the rapid assessment of GenAI-enabled educational technology, including alternative research designs and evidence standards.
- Support the establishment of a GenAI Education Research and Innovation Consortium, bringing together schools, researchers, and education technology (EdTech) developers to participate in rapid cycle studies and continuous improvement of GenAI tools.
By implementing these recommendations, Congress can foster a more responsive and evidence-based ecosystem for GenAI-powered educational tools, ensuring that they are equitable, effective, and safe for all students. This comprehensive approach will help unlock the transformative potential of GenAI to address persistent learning opportunity gaps and improve outcomes for all learners, while maintaining scientific rigor and prioritizing student well-being.
During the preparation of this work, the authors used the tool Claude 3 Opus (by Anthropic) to help clarify and synthesize, and add accessible language around concepts and ideas generated by members of the team. The authors reviewed and edited the content as needed and take full responsibility for the content of this publication.
Challenge and Opportunity
Widening Learning Opportunity Gap
NAEP data reveals that many U.S. students, especially those from disadvantaged subgroups, are not achieving proficiency in math and reading. In 2022, only 37% of fourth-graders performed at or above the NAEP proficient level in math, and 33% in reading—the lowest levels in over a decade. Disparities are more profound when disaggregated by race, ethnicity, and socioeconomic status; for example, only 17% of Black students and 21% of Hispanic students reached reading proficiency, compared to 42% of white students.
Rapid AI Evolution
GenAI is a transformative technology that enables rapid development and personalization of educational content and tools, addressing unmet needs in education such as lack of resources, 1:1 teaching time, and teacher quality. However, that rapid pace also raises concerns about premature adoption of unvetted tools, which could negatively impact students’ educational achievement. Unvetted GenAI tools may introduce misconceptions, provide incorrect guidance, or be misaligned with curriculum standards, leading to gaps in students’ understanding of foundational concepts. If used for an extended period, particularly with vulnerable learners, these tools could have a long-term impact on learning foundations that may be difficult to remedy.
On the other hand, carefully designed, trained, and vetted GenAI models that have undergone rapid cycle studies and design iterations based on data have the potential to effectively address students’ misconceptions, build solid learning foundations, and provide personalized, adaptive support to learners. These tools could accelerate progress and close learning opportunity gaps at an unprecedented scale.
Slow Vetting Processes
The rapid pace of AI development poses significant challenges for traditional research and evaluation processes in education. Efficacy research, particularly studies sponsored by the IES or other Department of Education entities, is a lengthy, resource-intensive, and often onerous process that can take years to complete. Randomized controlled trials and longitudinal studies struggle to keep up with the speed of AI innovation: by the time a study is completed, the AI-powered tool may have already undergone multiple iterations or been replaced.
It can be difficult to recruit and sustain school and teacher participation in efficacy research due to the significant time and effort required from educators. Moreover, obtaining certifications and approvals for research can be complex and time-consuming, as researchers must navigate institutional review boards, data privacy regulations, and ethical guidelines, which can delay the start of a study by months or even years.
Many EdTech developers find themselves in a catch-22 situation, where their products are already being adopted by schools and educators, yet they are simultaneously expected to participate in lengthy and expensive research studies to prove efficacy. The time and resources required to engage in such research can be a significant burden for EdTech companies, especially start-ups and small businesses, which may prefer to focus on iterating and improving their products based on real-world feedback. As a result, many EdTech developers may be reluctant to participate in traditional efficacy research, further exacerbating the disconnect between the rapid pace of AI innovation and the slow process of evaluating the effectiveness of these tools in educational settings.
Gaps in Existing Efforts and Programs
While federal initiatives like SEERNet and ExpandAI have made strides in supporting AI and education research and development, they may not be fully equipped to address the specific challenges and opportunities presented by GenAI for several reasons:
- GenAI has the ability to generate novel content and interact with users in unpredictable and personalized ways.
- GenAI-powered educational technologies involve unique considerations in terms of data training, prompt engineering, and output evaluation, especially when considering the developmental stages of PreK-12 students.
- GenAI raises specific ethical concerns, such as the potential for biased or inappropriate content generation, ensuring the accuracy and quality of generated responses, and protecting student privacy and agency.
- GenAI is evolving at an unprecedented pace.
Traditional approaches to efficacy research and evaluation may not be well-suited to evaluating the potential benefits and outcomes associated with GenAI-powered tools in the short term, particularly when assessing whether a program shows enough promise to warrant wider deployment with students.
A New Approach
To address these challenges and bridge the gap between GenAI innovation and efficacy research, we need a new approach to streamline the research process, reduce the burden on educators and schools, and provide timely and actionable insights into the effectiveness of GenAI-powered tools. This may involve alternative study designs, such as rapid cycle evaluations or single-case research, and developing new incentive structures and support systems to encourage and facilitate the participation of teachers, schools, and product developers in research studies.
GenAiRA aims to tackle these challenges by providing resources, guidance, and infrastructure to support more agile and responsive efficacy research in the education sciences. By fostering collaboration among researchers, developers, and educators, and promoting innovative approaches to evaluation, this program can help ensure that the development and adoption of AI-powered tools in education are guided by rigorous, timely, and actionable evidence—while simultaneously mitigating risks to students.
Learning from Other Sectors
Valuable lessons can be drawn from other fields that have faced similar balancing acts between innovation, research, and safety. Two notable examples are the U.S. Food and Drug Administration’s (FDA) expedited review pathways for drug development and the National Institutes of Health’s (NIH) Clinical and Translational Science Awards (CTSA) program for accelerating medical research.
Example 1: The FDA Model
The FDA’s expedited review programs, such as Fast Track, Breakthrough Therapy, Accelerated Approval, and Priority Review, are designed to speed up the development and approval of drugs that address unmet medical needs or provide significant improvements over existing treatments. These pathways recognize that, in certain cases, the benefits of bringing a potentially life-saving drug to market quickly may outweigh the risks associated with a more limited evidence base at the time of approval.
Key features include:
- Early and frequent communication between the FDA and drug developers to provide guidance and feedback throughout the development process.
- Flexibility in clinical trial design and evidence requirements, such as allowing the use of surrogate endpoints or single-arm studies in certain cases.
- Rolling review of application materials, allowing drug developers to submit portions of their application as they become available rather than waiting for the entire package to be complete.
- Shortened review timelines, with the FDA committing to reviewing and making a decision on an application within a specified timeframe (e.g., six months for Priority Review).
These features can accelerate the development and approval process while still ensuring that drugs meet standards for safety and effectiveness. They also acknowledge that the evidence base for a drug may evolve over time, with post-approval studies and monitoring playing a crucial role in confirming the drug’s benefits and identifying any rare or long-term side effects.
Example 2: The CTSA Program
The NIH’s CTSA program established a national network of academic medical centers, research institutions, and community partners to accelerate the translation of research findings into clinical practice and improve patient outcomes.
Key features include:
- Collaborative research infrastructure, consisting of a network of institutions and partners that work together to conduct translational research, share resources and expertise, and disseminate best practices.
- Streamlined research processes with standardized protocols, templates, and tools to facilitate the rapid design, approval, and implementation of research studies across the network.
- Training and development of researchers and clinicians to build a workforce equipped to conduct innovative and rigorous translational research.
- Community engagement in the research process to ensure that studies are responsive to real-world needs and priorities.
By learning from the successes and principles of the FDA’s expedited review pathways and the NIH’s CTSA program, the education sector can develop its own innovative approach to accelerating the responsible development, evaluation, and deployment of GenAI-powered tools, as outlined in the following plan of action.
Plan of Action
To address the challenges and opportunities presented by GenAI in education, we propose the following three key recommendations for congressional action and the evolution of existing programs.
Recommendation 1. Establish the GenAI in Education Research Accelerator Program (GenAiRA).
Congress should establish the GenAiRA, housed in the IES, to support and expedite efficacy research on products and tools utilizing AI-powered educational tools and programs. This program will:
- Provide funding and resources to researchers and educators to conduct rigorous, timely, and cost-effective efficacy studies on promising AI-based solutions that address achievement gaps.
- Create guidelines and offer webinars and technical assistance to researchers, educators, and developers to build expertise in the responsible design, implementation, and evaluation of GenAI-powered tools in education.
- Foster collaboration and knowledge-sharing among researchers, educators, and GenAI developers to facilitate the rapid translation of research findings into practice and continuously improve GenAI-powered tools.
- Develop and disseminate best practices, guidelines, and ethical frameworks for responsible development and deployment of GenAI-enabled educational technology tools in educational settings, focusing on addressing bias, accuracy, privacy, and student agency issues.
Recommendation 2. Under the auspices of GenAiRA, adapt IES research and evaluation processes to create a framework to evaluate GenAI-enabled educational technology.
In consultation with experts in educational research and AI, IES will develop a framework that:
- Identifies existing research designs and creates alternative research designs (e.g., quasi-experimental studies, rapid short evaluations) suitable for generating credible evidence of effectiveness while being more responsive to the rapid pace of AI innovation.
- Establish evidence-quality guidelines for rapid evaluation, including minimum sample sizes, study duration, effect size, and targeted population.
- Funds replication studies and expansion studies to determine impact in different contexts or with different populations (e.g., students with IEPs and English learners).
- Provides guidance to districts on how to interpret and apply evidence from different types of studies to inform decision-making around adopting and using AI technologies in education.
Recommendation 3. Establish a GenAI Education Research and Innovation Consortium.
Congress should provide funding and incentives for IES to establish a GenAI Education Research and Innovation Consortium that brings together a network of “innovation schools,” research institutions, and EdTech developers committed to participating in rapid cycle studies and continuous improvement of GenAI tools in education. This approach will ensure that AI tools are developed and implemented in a way that is responsive to the needs and values of educators, students, and communities.
To support this consortium, Congress should:
- Allocate funds for the IES to provide grants and resources to schools, research institutions, and EdTech developers that meet established criteria for participation in the consortium, such as demonstrated commitment to innovation, research capacity, and ethical standards.
- Direct IES to work with programs like SEERNet and ExpandAI to identify and match potential consortium members, provide guidance and oversight to ensure that research studies meet rigorous standards for quality and ethics, and disseminate findings and best practices to the broader education community.
- Encourage the development of standardized protocols and templates for data sharing, privacy protection, and informed consent within the consortium, to reduce the time and effort required for each individual study and streamline administrative processes.
- Incentivize participation in the consortium by offering resources and support for schools, researchers, and developers, such as access to funding opportunities, technical assistance, and professional development resources.
- Require the establishment of a central repository of research findings and best practices generated through rapid cycle evaluations conducted within the consortium, to facilitate the broader dissemination and adoption of effective GenAI-powered tools.
Conclusion
Persistent learning opportunity gaps in math and reading, particularly among disadvantaged students, are a systemic challenge requiring innovative solutions. GenAI-powered educational tools offer potential for personalizing learning, identifying misconceptions, and providing tailored support. However, the mismatch between the pace of GenAI innovation and lengthy traditional research pathways impedes thorough vetting of these technologies to ensure they are equitable, effective, and safe before widespread adoption.
GenAiRA and development of alternative research frameworks provide a comprehensive approach to bridge the divide between GenAI’s rapid progress and the need for thorough evaluation in education. Leveraging existing partnerships, research infrastructure, and data sources can expedite the research process while maintaining scientific rigor and prioritizing student well-being.
The plan of action creates a roadmap for responsibly harnessing GenAI’s potential in education. Identifying appropriate congressional mechanisms for establishing the accelerator program, such as creating a new bill or incorporating language into upcoming legislation, can ensure this critical initiative receives necessary funding and oversight.
This comprehensive strategy charts a path toward equitable, personalized learning facilitated by GenAI while upholding the highest standards of evidence. Aligning GenAI innovation with rigorous research and prioritizing the needs of underserved student populations can unlock the transformative potential of these technologies to address persistent achievement gaps and improve outcomes for all learners.
This idea is part of our AI Legislation Policy Sprint. To see all of the policy ideas spanning innovation, education, healthcare, and trust, safety, and privacy, head to our sprint landing page.
Implementing AI and GenAI-powered educational tools without sufficient evidence of their effectiveness or safety could lead to the widespread use of ineffective interventions. If these tools fail to improve student outcomes or even hinder learning progress, they can have long-lasting negative consequences for students’ academic attainment and self-perception as learners.
When students are exposed to ineffective educational tools, they may struggle to grasp key concepts, leading to gaps in their knowledge and skills. Over time, these gaps can compound, leaving students ill-prepared for future learning challenges and limiting their academic and career opportunities. Moreover, repeated experiences of frustration and failure with educational technologies can erode students’ confidence, motivation, and engagement with learning.
This erosion of learner identity can be particularly damaging for students from disadvantaged backgrounds, who may already face additional barriers to academic success. If AI-powered tools fail to provide effective support and personalization, these students may fall even further behind their peers, exacerbating existing educational inequities.
A Safe Harbor for AI Researchers: Promoting Safety and Trustworthiness Through Good-Faith Research
Artificial intelligence (AI) companies disincentivize safety research by implicitly threatening to ban independent researchers that demonstrate safety flaws in their systems. While Congress encourages companies to provide bug bounties and protections for security research, this is not yet the case for AI safety research. Without independent research, we do not know if the AI systems that are being deployed today are safe or if they pose widespread risks that have yet to be discovered, including risks to U.S. national security. While companies conduct adversarial testing in advance of deploying generative AI models, they fail to adequately test their models after they are deployed as part of an evolving product or service. Therefore, Congress should promote the safety and trustworthiness of AI systems by establishing bug bounties for AI safety via the Chief Digital and Artificial Intelligence Office and creating a safe harbor for research on generative AI platforms as part of the Platform Accountability and Transparency Act.
Challenge and Opportunity
In July 2023, the world’s top AI companies signed voluntary commitments at the White House, pledging to “incent third-party discovery and reporting of issues and vulnerabilities.” Almost a year later, few of the signatories have lived up to this commitment. While some companies do reward researchers for finding security flaws in their AI systems, few companies strongly encourage research on safety or provide concrete protections for good-faith research practices. Instead, leading generative AI companies’ Terms of Service legally prohibit safety and trustworthiness research, in effect threatening anyone who conducts such research with bans from their platforms or even legal action.
In March 2024, over 350 leading AI researchers and advocates signed an open letter calling for “a safe harbor for independent AI evaluation.” The researchers noted that generative AI companies offer no legal protections for independent safety researchers, even though this research is critical to identifying safety issues in AI models and systems. The letter stated: “whereas security research on traditional software has established voluntary protections from companies (‘safe harbors’), clear norms from vulnerability disclosure policies, and legal protections from the DOJ, trustworthiness and safety research on AI systems has few such protections.”
In the months since the letter was released, companies have continued to be opaque about key aspects of their most powerful AI systems, such as the data used to build their models. If a researcher wants to test whether AI systems like ChatGPT, Claude, or Gemini can be jailbroken such that they pose a threat to U.S. national security, they are not allowed to do so as companies proscribe such research. Developers of generative AI models tout the safety of their systems based on internal red-teaming, but there is no way for the federal government or independent researchers to validate these results, as companies do not release reproducible evaluations.
Generative AI companies also impose barriers on their platforms that limit good-faith research. Unlike much of the web, the content on generative AI platforms is not publicly available, meaning that users need accounts to access AI-generated content and these accounts can be restricted by the company that owns the platform. In addition, companies like Google, Amazon, Microsoft, and OpenAI block certain requests that users might make of their AI models and limit the functionality of their models to prevent researchers from unearthing issues related to safety or trustworthiness.
Similar issues plague social media, as companies take steps to prevent researchers and journalists from conducting investigations on their platforms. Social media researchers face liability under the Computer Fraud and Abuse Act and Section 1201 of the Digital Millennium Copyright Act among other laws, which has had a chilling effect on such research and worsened the spread of misinformation online. The stakes are even higher for AI, which has the potential not only to turbocharge misinformation but also to provide U.S. adversaries like China and Russia with material strategic advantages. While legislation like the Platform Accountability and Transparency Act would enable research on recommendation algorithms, proposals that grant researchers access to platform data do not consider generative AI platforms to be in scope.
Congress can safeguard U.S. national security by promoting independent AI safety research. Conducting pre-deployment risk assessments is insufficient in a world where tens of millions of Americans are using generative AI—we need real-time assessments of the risks posed by AI systems after they are deployed as well. Big Tech should not be taken at its word when it says that its AI systems cannot be used by malicious actors to generate malware or spy on Americans. The best way to ensure the safety of generative AI systems is to empower the thousands of cutting-edge researchers at U.S. universities who are eager to stress test these systems. Especially for general-purpose technologies, small corporate safety teams are not sufficient to evaluate the full range of potential risks, whereas the independent research community can do so thoroughly.
Figure 1. What access protections do AI companies provide for independent safety research? Source: Longpre et al., “A Safe Harbor for AI Evaluation and Red Teaming.”
Plan of Action
Congress should enable independent AI safety and trustworthiness researchers by adopting two new policies. First, Congress should incentivize AI safety research by creating algorithmic bug bounties for this kind of work. AI companies often do not incentivize research that could reveal safety flaws in their systems, even though the government will be a major client for these systems. Even small incentives can go a long way, as there are thousands of AI researchers capable of demonstrating such flaws. This would also entail establishing mechanisms through which safety flaws or vulnerabilities in AI models can be disclosed, or a kind of help-line for AI systems.
Second, Congress should require AI platform companies, such as Google, Amazon, Microsoft, and OpenAI to share data with researchers regarding their AI systems. As with social media platforms, generative AI platforms mediate the behavior of millions of people through the algorithms they produce and the decisions they enable. Companies that operate application programming interfaces used by tens of thousands of enterprises should share basic information about their platforms with researchers to facilitate external oversight of these consequential technologies.
Taken together, vulnerability disclosure incentivized through algorithmic bug bounties and protections for researchers enabled by safe harbors would substantially improve the safety and trustworthiness of generative AI systems. Congress should prioritize mitigating the risks of generative AI systems and protecting the researchers who expose them.
Recommendation 1. Establish algorithmic bug bounties for AI safety.
As part of the FY2024 National Defense Authorization Act (NDAA), Congress established “Artificial Intelligence Bug Bounty Programs” requiring that within 180 days “the Chief Digital and Artificial Intelligence Officer of the Department of Defense shall develop a bug bounty program for foundational artificial intelligence models being integrated into the missions and operations of the Department of Defense.” However, these bug bounties extend only to security vulnerabilities. In the FY2025 NDAA, this bug bounty program should be expanded to include AI safety. See below for draft legislative language to this effect.
Recommendation 2. Create legal protections for AI researchers.
Section 9 of the proposed Platform Accountability and Transparency Act (PATA) would establish a “safe harbor for research on social media platforms.” This likely excludes major generative AI platforms such as Google Cloud, Amazon Web Services, Microsoft Azure, and OpenAI’s API, meaning that researchers have no legal protections when conducting safety research on generative AI models via these platforms. PATA and other legislative proposals related to AI should incorporate a safe harbor for research on generative AI platforms.
Conclusion
The need for independent AI evaluation has garnered significant support from academics, journalists, and civil society. Safe harbor for AI safety and trustworthiness researchers is a minimum fundamental protection against the risks posed by generative AI systems, including related to national security. Congress has an important opportunity to act before it’s too late.
This idea is part of our AI Legislation Policy Sprint. To see all of the policy ideas spanning innovation, education, healthcare, and trust, safety, and privacy, head to our sprint landing page.
The authors of this memorandum as well as the academic paper underlying it submitted a comment to the Copyright Office in support of an exemption to DMCA for AI safety and trustworthiness research. The Computer Crime and Intellectual Property Section of the U.S. Department of Justice’s Criminal Division and Senator Mark Warner have also endorsed such an exemption. However, a DMCA exemption regarding research on AI bias, trustworthiness, and safety alone would not be sufficient to assuage the concerns of AI researchers, as they may still face liability under other statutes such as the Computer Fraud and Abuse Act.
Much of this research is currently conducted by research labs with direct connections to the AI companies they are assessing. Researchers who are less well connected, of which there are thousands, may be unwilling to take the legal or personal risk of violating companies’ Terms of Service. See our academic paper on this topic for further details on this and other questions.
See draft legislative language below, building on Sec. 1542 of the FY2024 NDAA:
SEC. X. EXPANSION OF ARTIFICIAL INTELLIGENCE BUG BOUNTY PROGRAMS.
(a) Update to Program for Foundational Artificial Intelligence Products Being Integrated Within Department of Defense.—
(1) Development required.—Not later than 180 days after the date of the enactment of this Act and subject to the availability of appropriations, the Chief Digital and Artificial Intelligence Officer of the Department of Defense shall expand its bug bounty program for foundational artificial intelligence models being integrated into the missions and operations of the Department of Defense to include unsafe model behaviors in addition to security vulnerabilities.
(2) Collaboration.—In expanding the program under paragraph (1), the Chief Digital and Artificial Intelligence Officer may collaborate with the heads of other Federal departments and agencies with expertise in cybersecurity and artificial intelligence.
(3) Implementation authorized.—The Chief Digital and Artificial Intelligence Officer may carry out the program In subsection (a).
(4) Contracts.—The Secretary of Defense shall ensure, as may be appropriate, that whenever the Secretary enters into any contract, such contract allows for participation in the bug bounty program under paragraph (1).
(5) Rule of construction.—Nothing in this subsection shall be construed to require—
(A) the use of any foundational artificial intelligence model; or
(B) the implementation of the program developed under paragraph (1) for the purpose of the integration of a foundational artificial intelligence model into the missions or operations of the Department of Defense.
Update COPPA 2.0 to Strengthen Children’s Online Voice Privacy in the AI Era
Emerging technologies like artificial intelligence (AI) are changing the way humans interact with machines. As AI technology has made huge progress over the last decade, the processing of modalities such as text, voice, image, and video data has been replaced with data-driven large AI models. These models were primarily aimed for machines to comprehend various data and perform tasks without human intervention. Now, with the emergence of generative AI like ChatGPT, these models are capable of generating data such as text, voice, image, or video. Policymakers across the globe are struggling to draft to govern ethical use of data as well as regulate the creation of safe, secure, and trustworthy AI models.
Data privacy is a major concern with the advent of AI technology. Actions by the US Congress such as the proposed American Privacy Rights Act aim to enforce strict data privacy rights. With emerging AI applications for children, the privacy of children and the safekeeping of their personal information is also a legislative challenge.
Congress must act to protect children’s voice privacy before it’s too late. Companies that store children’s voice recordings and use them for profit-driven applications (or advertising) without parental consent pose serious privacy threats to children and families. The proposed revisions to the Children’s Online Privacy Protection Act (COPPA) aim to restrict companies’ capacity to profit from children’s data and transfer the responsibility of compliance from parents to companies. However, several measures in the proposed legislation need more clarity and additional guidelines.
Challenge and Opportunity
Human voice1 is one of the most popular modalities for AI technology. Advancements in voice AI technology such as voice AI assistants (Siri, Google, Bixby, Alexa, etc.) in smartphones have made many day-to-day activities easier; however, there are also emerging threats from voice AI and a lack of regulations governing voice data and voice AI applications. One example is AI voice impersonation scams. Using the latest voice AI technology,2 a high-quality personalized voice recording can be generated with as little as 15 seconds of the speaker’s recorded voice. A technology rat race among Big Tech has begun, as companies are trying to achieve this using voice recordings that are less than a few seconds. Scammers have increasingly been using this technology for their benefit. OpenAI, the creator of ChatGPT, recently developed a product called Voice Engine—but refrained from commercializing it by acknowledging that this technology poses “serious risks,” especially in an election year.
A voice recording contains very personal information about a speaker, and that gives the ability to identify a target speaker from recordings of multiple speakers. Emerging research in voice AI technology has potential implications for medical and health-related applications from voice recordings, plus identification of age, height, and much more. When using cloud-based applications, privacy concerns also arise during voice data transfer and from data storage leaks, due to noncompliance with data collection and storage. Therefore, the threats from misuse of voice data and voice AI technology are enormous.
Social media services, educational technology, online games, and smart toys are just a few services for children that have started adopting voice technology (e.g., Alexa for Kids). Any service operator (or company) collecting and using children’s personal information, including their voice, is bound by the Children’s Online Privacy Protection Act (COPPA). The Federal Trade Commission (FTC) is the enforcing federal agency for COPPA. However, several companies have recently violated COPPA by collecting personal information from children without parental consent and used it for advertising and maximizing their platform profits. “Amazon’s history of misleading parents, keeping children’s recordings indefinitely, and flouting parents’ deletion requests violated COPPA and sacrificed privacy for profits,” said Samuel Levine of the FTC’s Bureau of Consumer Protection. The FTC alleges that Amazon maintained records of children’s data, disregarding parents’ deletion requests, and trained its Voice AI algorithms on that data.
Children’s spoken characteristics are different from those of adults; thus, developing voice AI technology for children is more challenging. Most commercial voice-AI-enabled services work smoothly for adults, but their accuracy in understanding children’s voices is often limited. Another challenge is the relatively sparse availability of children’s voice data to train AI models. Therefore, Big Tech is looking to leverage ways to acquire as much children’s voice data as possible to train AI voice models. This challenge is prevalent not only in industry but also in academic research on the subject due to very limited data availability and varying spoken skills. However, misuse of acquired data, especially without consent, is not a solution, and operators must be penalized for such actions.
Considering the recent violations of COPPA by operators, and with a goal to strengthen the compliance of safeguarding and avoid misuse of personal information such as voice, Congress is updating COPPA with new legislation. The COPPA updates propose to extend and update the definition of “operator,” “personal information” including voice prints, “consent,” “website/service/application” including devices connected to the internet, and guidelines for “collection, use, disclosure, and deletion of personal information.” These updates are especially critical when the personal information of users (or consumers) can serve as valuable data for operators for profit-driven applications and misuse without any federal regulation. The FTC acknowledges that the current version of COPPA is insufficient; therefore, these updates would also enable the FTC to act on operators and take strict action.
Plan of Action
The Children and Teens’ Online Privacy Protection Act (COPPA 2.0) has been proposed in both the Senate and House to update COPPA for the modern internet age, with a renewed focus on limiting misuse of children’s personal data (including voice recordings). This proposed legislation has gained momentum and bipartisan support. However, the text in this legislation could still be updated to ensure consumer privacy and support future innovation.
Recommendation 1. Clarify the exclusion clause for audio files.
An exclusion clause has been added in this legislation particularly for audio files containing a child’s voice, declaring that the collected audio file is not considered personal information if it meets certain criteria. This was added to adopt a more expansive audio file exception, particularly to allow operators to provide some features to their users (or consumers).
While just having the text “only uses the voice within the audio file solely as a replacement for written words”3 might be overly restrictive for voice-based applications, the text “to perform a task” might open the use of audio files for any task that could be beneficial to operators. The task should only be related to performing a request or providing a service to the user, and that needs to be clarified in the text. Potential misuse of this text could be (1) to train AI models for tasks that might help operators provide a service to the user—especially for personalization, or (2) to extract and store “audio features”4 (most voice AI models are trained using audio features instead of the raw audio itself). Operators might argue that extracting audio features is necessary as part of the algorithm that assists in providing a service to the user. Therefore, the phrasing “to perform a task” in this exclusion might be open-ended and should be modified as suggested:
Current text: “(iii) only uses the voice within the audio file solely as a replacement for written words, to perform a task, or engage with a website, online service, online application, or mobile application, such as to perform a search or fulfill a verbal instruction or request; and”
Suggestion text: “(iii) only uses the voice within the audio file solely as a replacement for written words, to only perform a task to engage with a website, online service, online application, or mobile application, such as to perform a search or fulfill a verbal instruction or request; and”
On a similar note, legislators should consider adding the term “audio features.” Audio features are enough to train voice AI models and develop any voice-related application, even if the original audio file is deleted. Therefore, the deletion argument in the exclusion clause should be modified as suggested:
Current text: “(iv) only maintains the audio file long enough to complete the stated purpose and then immediately deletes the audio file and does not make any other use of the audio file prior to deletion.”
Suggestion text: “(iv) only maintains the audio file long enough to complete the stated purpose and then immediately deletes the audio file and any extracted audio-based features and does not make any other use of the audio file (or extracted audio-features) prior to deletion.”
Adding more clarity to the exclusion will help avoid misuse of children’s voices for any task that companies might still find beneficial and also ensure that operators delete all forms of the audio which could be used to train AI models.
Recommendation 2. Add guidelines on the deidentification of audio files to enhance innovation.
A deidentified audio file is one that cannot be used to identify the speaker whose voice is recorded in that file. The legislative text of COPPA 2.0 does not mention or have any guidelines on how to deidentify an audio file. These guidelines would not only protect the privacy of users but also allow operators to use deidentified audio files to add features and improve their products. The guidelines could include steps to be followed by operators as well as additional commitment from operators.
The steps include:
- Each audio file collected by an application should be stored with an anonymous identifier.
- Each audio file collected from the same user account (a child) or a device (e.g., smartphone, tablets/iPad, laptop/computer) should be treated as an individual file and stored with anonymous identifiers. This will avoid linking multiple audio files from the same user or device.
- If any audio file contains any personally identifiable information, that audio file must be deleted instantly, and the user (parent of the child) must be informed. There is no guarantee that an audio recording will not contain any personally identifiable information, and therefore this step is critical.
The commitments include:
- An operator should commit not to reidentify the speaker from any given audio file (both anonymized and non-anonymous) (this task is often called “speaker identification”).
- An operator should seek consent (or approval) from the parent of the user (child) to allow the use of the deidentified audio files for product development, and only then use it or else immediately delete the audio file following the completion of the task for which it was collected.
Following these guidelines might be expensive for operators; however, it is crucial to take as many precautions as possible. Current deidentification steps of audio files followed by operators are not sufficient, and there have been numerous instances in which anonymized data had been reidentified, according to a statement released by a group of State Attorneys General. These proposed guidelines could allow operators to deidentify audio files and use those files for product development. This will allow the innovation of voice AI technology for children to flourish.
Recommendation 3. Add AI-generated avatars in the definition of personal information.
With the emerging applications of generative AI and growing virtual reality use for education (in classrooms) and for leisure (in online games), “AI-based avatar generation from a child’s image, audio, or video” should be added to the legislative definition of “personal information.” Virtual reality is a growing space, and digital representations of the human user (an avatar) are increasingly used to allow the user to see and interact with virtual reality environments and other users.
Conclusion
As new applications of AI emerge, operators must ensure compliance in the collection and use of consumers’ personal information and safety in the design of their products using that data, especially when dealing with vulnerable populations like children. Since the original passage of COPPA in 1998, how consumers use online services for day-to-day activities, including educational technology and amusement for children, has changed dramatically. This ever-changing scope and reach of online services require strong legislative action to bring online privacy standards into the 21st century. Without a doubt, COPPA 2.0 will lead this regulatory drive not only to protect children’s personal information collected by online services and operators from misuse but also to ensure that the burden of compliance rests on the operators rather than on parents. These recommendations will help strengthen the protections of COPPA 2.0 even further while leaving open avenues for innovation in voice AI technology for children.
This idea is part of our AI Legislation Policy Sprint. To see all of the policy ideas spanning innovation, education, healthcare, and trust, safety, and privacy, head to our sprint landing page.
A National Training Program for AI-Ready Students
In crafting future legislation on artificial intelligence (AI), Congress should introduce a Digital Frontier and AI Readiness Act of 2025 to create educator training sites in emerging technology to ensure our students can graduate AI-ready. Computing, data, and AI basics will be critical for every student, yet our education system does not have the capacity to impart them. A national mobilization for the education workforce would ensure U.S. leadership in the global AI talent race, address mounting challenges in teacher shortages and retention, and fill critical workforce preparedness gaps not addressed by the CHIPS and Science Act. The legislation would include three components: (1) a prestigious national fellowship program for classroom educators with extended summer pay; (2) an evidence-based national network of training sites for peer-based learning; and (3) a modernization competition for teacher college programs to sustain long-term improvement in our education workforce.
Investing in effective educators has a significant impact: one high-quality teacher can significantly boost lifetime incomes, degree attainment, and other life satisfaction measures for many classrooms of students. These programs would be facilitated through the National Science Foundation (NSF), including through simplified application procedures, expanded eligibility, and evaluation approaches.
Challenge and Opportunity
If AI is positioned to dramatically transform our economy, from the production line to the c-suite, then everyone must be prepared to leverage its power. AI alone may add between an estimated $2.6 trillion to $4.4 trillion annually to the global economy and may automate between 60% to 70% of task-time within existing jobs, rather than full replacement. Earlier studies estimated that emerging technologies will increase the technology intensity of existing careers across all sectors. A report by the Burning Glass Institute found that 22% of all current open jobs in the U.S. economy include at least one “data science skill,” with the highest share of data-skill job postings in utilities, manufacturing, and agriculture. Not every worker will build the next AI algorithm or become a data scientist, but nearly every American will need to leverage data and AI to maintain a competitive edge in their sector or risk losing entire industries to other countries who do the same. This unprecedented economic growth will only be captured by the countries whose workers are prepared in data and AI basics.
U.S. educators are mostly unsupported to teach students about AI and other emerging technologies. An analysis of math educators nationally found that teachers are least confident to teach about data and statistics, as well as technology integration, compared to other content categories. Computer science was the least popular credential for K-12 educators to pursue as recently as the 2018–2019 school year. These challenges translate to student opportunities and outcomes. As of 2023, only 5.8% of our high school students are enrolled in foundational computer science courses. Introductory basics in data or AI are typically not covered even if they exist in some state standards. Nationally, students’ foundational data literacy has declined between one and three grade levels steadily over the past decade, varying disproportionately by race and geography, with losses only accelerated by the pandemic.
Moreover, our teacher workforce capacity is declining. Teacher entry, preparation, and retention rates remain at historical lows across the country and have not meaningfully recovered since the pandemic. Over the past decade, the number of individuals completing a teacher preparation program has fallen 25%, with only modest recovery since the pandemic, shortages of at least 55,000 unfilled positions this year, and long-term forecasts reaching at least 100,000 shortages annually. Factors including low pay, low prestige, and difficult environments create a perception challenge for the profession: less than 1 in 5 Americans would encourage a young person to become a teacher. These challenges compound over time, as more graduate schools of education close or cut their programming. In 2022, Harvard discontinued its Undergraduate Teacher Program completely, citing low interest and enrollment numbers, one among many.
What if the concurrent challenges of digital upskilling and teacher shortages could help solve one another? The teaching profession is facing a perception problem just as AI has made education more important than ever before. In the global information age, U.S. worker skills and talent are our greatest weapons. The expectations of teachers and teaching must change. Major U.S. economic peers, including Canada, Germany, China, India, New Zealand, and the United Kingdom, have all announced similar national efforts to make robust investments in teacher upskilling in high-value technology areas. In our new AI era, U.S. policymakers now have the opportunity to develop the infrastructure, 21st-century training, and prestigious social recognition to properly value education as an economic and national security priority. A recent report from Goldman Sachs identified “a narrow window of opportunity – what we call the inter-AI years,” in which policymaker “decisions made today will determine what is possible in the future. A generative world order will emerge.” Inaction today risks the United States falling quickly behind tomorrow.
Teacher preparation program enrollment by program and year, 2010–2018 via CAP, 2019
Plan of Action
A Digital Frontier Teaching Corps (DFT Corps) would mobilize a new generation of teachers who are fluent in, adaptive to, and resilient to fast-changing technology, equipped to help our students become the same. The DFT Corps would re-norm the job of teaching to become a full-year profession, making the summer months an essential part of the job of adaptive 21st-century teaching with regular training intensives. Currently, educators only work and are paid for nine months of the year.
Upon acceptance by application, selected teachers would enter a three-year fellowship program to participate in training intensives facilitated at local institutes of higher education, nonprofits, educational service agencies, or industry partners. Scholarships facilitated through the National Science Foundation would extend educator pay and hours from nine months to a full annualized salary. DFT Corps members would also be eligible for substantial federal loan forgiveness in return for their additional time investment.
After three rotations, members would become eligible to serve as DFT Corps site leaders, responsible for program design at new or existing training sites. These opportunities would lend greater compensation, prestige, and retention through leadership opportunities, concurrently addressing systemic talent challenges in education at their root and creating an adaptive mechanism for faster upskilling. Additional program components, including licensure incentives and teacher college innovation grants, would further sustain long-term impacts. By year three of the program, 50,000 educators would be on the path to preparing our students for the future of work, 500 inaugural Corps members would become state or local site leaders to expand the mobilization, and the perception of teaching would further shift from childcare to a critical and respected national service.
To accomplish this vision, Congress should authorize the National Science Foundation to create:
1. A national Digital Frontier Teaching Corps, a three-year “talent surge” fellowship opportunity covering summertime pay for high-potential educators to conduct intensive study in AI, data science, and computing foundations. The DFT Corps would be a prestigious and materially meaningful program to both impart digital technical skills and transform the social perception of the teaching profession. The DFT Corps would include:
- Educator scholarships for full summertime pay
- A low-barrier digital application process for individuals to apply for funding directly from the NSF or an intermediary third-party organization
- Automatic enrollment in local site-based training sites, including college-level coursework (computer science, data science, artificial intelligence, quantum computing) and peer-based pedagogical training
- Tax-based verification for program completion status
- Federal loan forgiveness upon successful program completion
- Federal recognition awards of schools employing DFT Corps educators
- Eligibility to apply for DFT Corps training site leadership upon successful program completion
2. DFT Corps training sites, a national network of university-based, locally led professional development sites in collaboration with local education agencies, based on the evidence-based model of the National Writing Project. Competitive five-year grants would support the creation of Corps sites, one per state, with the opportunity for renewal. DFT Corps training sites would:
- Provide college-level coursework (computer science, data science, artificial intelligence, quantum computing) and peer-based pedagogy training to 100 educators per summer
- Be co-designed with local faculty, researchers, or industry experts, along with prior DFT Corps members
- Be evaluated on an annual basis, with criteria determined by the NSF, with all evaluation results published publicly and submitted to the NSF
- Expand with matching funds from state, industry, or philanthropic support as resources allow
3. Teacher College Innovation Grants, a competitive NSF grant program for modernizing teacher preparation programs and teacher licensure models. Teacher College Innovation Grants would provide research funding and capacity to evaluate DFT Corps training sites and ensure lessons learned are quickly integrated back into teacher preparation programs. Competitive priorities would be made for:
- Proposals that develop and/or scale new methods-style courses for teaching digital technology (i.e., computational thinking, data literacy, AI literacy) to students across traditional school subjects
- Proposals that develop new models for teacher preparation, leveraging online learning or other digital training systems that result in lower program costs
- Proposals that focus on building or modernizing teacher preparation capacity in majority-rural or majority-Indigenous communities
The DFT Corps program is intended to be catalytic. Should the program find success in early scaling, state and local funding could support further adoption of the model over time, so that teaching transforms to an annualized profession across subject areas and grade-levels.
Conclusion
In the new era of AI, education is a national security issue. Advancing our population’s ability to effectively deploy AI and other emerging technology will uniquely determine U.S. leadership and economic competitiveness in the coming years and decades. Education investments made by states within the next few years will all but determine local long-term economic trajectories.
In the 1950s and 1960s, education and competitiveness were one and the same. One year after the Soviets launched Sputnik, Congress took action and passed the National Defense Education Act, a $1 billion spending package to advance teaching and learning in science, mathematics, and foreign languages. At one time, we respected teachers as critical to the national mission, leading the charge to prepare our next generation to lead, and we took swift action to support their mission. We must take the same bold action now.
This idea is part of our AI Legislation Policy Sprint. To see all of the policy ideas spanning innovation, education, healthcare, and trust, safety, and privacy, head to our sprint landing page.
The scale of this national challenge requires meaningful appropriations to raise teacher pay, ensure high-quality training opportunities with sufficient expertise, and sustain a long-term strategy to address deeply-rooted sector challenges. A short-term, one-shot approach will simply waste money and generate minimal impact.
Moreover, the program’s creation necessitates a significant simplification of National Science Foundation application processes to reduce grant application length, burden, and paperwork. It also creates a targeted exception for the NSF to support broader nonresearch activities that are otherwise sector-critical for national scientific and educational endeavors. If enacted, this legislation could help reduce overhead for program administration and redirect more resources to supporting quality state and local implementation vs. program compliance.
Once scaled to all 50 states, the recurring annual costs of the proposed legislation would be $250 million:
- $150 million for DFT Corps member scholarships (5,000 teachers per year)
- $50 million for DFT Corps training sites (one site per state at $1 million each)
- $50 million for Teacher College Innovation Grants (one site per state at $1 million each)
In the first five years, the cost would slowly increase to the total amount, starting at a base $25 million for five states ($15 million for 500 scholarships, $5 million for training sites, $5 million for Innovation grants).
Creating an AI-ready workforce is a critical national priority to maintain U.S. economic competitiveness, mitigate risk of AI primacy, and ensure our citizenry can successfully navigate a complex technology landscape they will graduate into. McKinsey projects that successful integration of AI across more than 63 business use cases would add between $13.6 trillion and $22.1 trillion to the global economy. A recent National Institutes of Health analysis suggests that, for any country to successfully specialize in AI, there must be general preexisting technological capabilities and a strong scientific knowledge base. AI-readiness must be a population-wide goal. Given that 60% of Americans do not complete a bachelor’s degree, AI readiness must begin early in K-12 education and in community colleges.
Estimated return on investment: $250 million represents less than 1.5% of the Every Student Succeeds Act’s last annual appropriation level in 2020, the nation’s primary national education funding mechanism. If this legislation increases the share of economic growth forecasted by effectively harnessing AI by only five percent, we would conservatively add $171 billion to the U.S. economy each year.
The majority of educator training programs are too short, only given during the busy school year, and do not have the opportunity to improve over multiple years within a given school. Early iterations of the National Writing Project, on which this program is based, determined that “although schools may see results from C3WP in a single school year, a longer-term investment may produce a greater impact.” Even if sustained during a school year, researchers have found that “absent a surrounding context that is highly supportive of teacher learning and change, 1 year of PD cannot sufficiently alter instructional practices enough to impact student outcomes.” While earlier evaluation studies saw no impact on student achievement, the National Writing Project is now one of the most lauded and effective educator training models trialed in the United States, made possible by a long-term and consistent investment in professional learning.
A three-year program will allow educators to advance from novice (year 1) to intermediate (year 2) to mentor or facilitator (year 3).By year 4, graduating educators would be prepared to serve as site leaders, dramatically increasing the available talent pool for sustaining and growing DFT Corps sites nationally. Additional time will also enable a local site to improve its own programming and align tightly with multi-year school and district planning.
The DFT Corps is an accelerated investment in the creation of locally led professional development sites, uniquely designed with (1) direct support for current classroom educators to participate; (2) a replicated network model for summer-based, in-service training; and (3) innovation grants to research aligned training improvements and best practices. No current federal program does all three at once for current classroom educators.
Existing teacher training grant programs, such as the Teacher Quality Partnerships or Supporting Effective Educator Development carry strong evidence requirements or incompatible competitive preferences. Given AI is new and little research exists on effective teaching practices, these requirements serve to significantly limit proposals on emerging topics. Grants also vary widely by institution.
Existing educator scholarship programs, such as the Robert Noyce Teacher Scholarship Program, focus mostly on recruitment of new teachers, and only provide small support for existing teachers pursuing or having previously obtained a master’s degree. 40% of U.S. teachers do not have a master’s degree. A targeted national focus on AI readiness would also require several higher-education institutions across states to organically propose training programs to the Noyce program at the same time, with the same model.
AI technology development is moving faster than the education sector can respond. In order to accelerate site creation, reduce application burden, and modernize grant distribution, the DFT Corps program would direct the NSF to:
- Allow nonresearch activities to be funded under the program, including educator salary support
- Remove and centralize all program evaluation requirements away from individual grantees, reallocating evaluation activities to external researchers across sites
- Centrally manage disbursement of DFT salary supplements, potentially via tax credits
- Modernize required data management plan requirements for present-day technology
- Limit total grant application length to 10 pages or less. In other fields, NSF grant applications take investigators over 171 hours to prepare, despite little relation between time invested and actual funding outcomes in some cases. Another study found that 42% of investigators time is spent on administrative and reporting tasks to support the execution of an NSF grant.
Yes, with appropriations. Under new 2023 guidance, the Robert Noyce Teacher Scholarship Program has expanded salary supplement options and enabled two-summer support. An executive action version of this proposal would expand the Robert Noyce Teacher Scholarship program via (1) increasing support for Track 3 with lower degree requirements (i.e. Bachelors instead of Masters); (2) stipulating a competitive priority for AI readiness and emerging technology education (defined as: computer science, computational thinking, data science, artificial intelligence literacy across the curriculum); and (3) direct the White House Office of Science & Technology Policy to launch a multi-agency, public-facing communications and recruitment effort for the DFT Corps program, in collaboration with the 50 largest teacher colleges and other participating Noyce program institutions.
The proposed DFT Corps mirrors a long-running evidence-based model, the National Writing Project (NWP), which has trained over 95,000 teachers in high-quality writing instruction across 2,000 school districts since 1974. Three independent evaluation studies over multiple years across 20 states found “positive and statistically significant effects on student achievement” across all measured components of writing. The evidence base supporting NWP is “unusually robust” for education research, employing randomized-controlled trials and meeting ESSA Tier 1 evidence criteria. A recent replication study in 2023 focusing on rural schools found positive results on “on all attributes measured,” a similar priority for the proposed DFT Corps program.
Similar to the Robert Noyce Scholarship program, the DFT Corps program would waive tuition costs and provide scholarship funds in exchange for a multi-year teaching commitment. Each year’s participation in the program would extend an educator’s teaching commitment by two additional years. A 2013 evaluation of the Noyce program found this model worked, with longer retention rates compared to new teachers graduating from the same institutions.
Recodes a nine-month profession to annual pay, and annual expectations: A primary change advanced by the DFT Corps is converting the typical teacher job from a nine-month term to an annual salary, similar to lawyers, doctors, and other high-prestige professions. In a recent RAND report on why teachers wanted to leave the profession, salary was the #2 reason, hours worked outside the school day the #3, and total hours worked was the #4. Teachers are promised a flexible and part-year job on paper, when the reality is very different. Nine-month pay challenges are so extreme that several U.S. banks host articles on “surviving the summer paycheck gap.” Many teachers take second (non-academic) jobs. And the popular #NoSummersOff hashtag gained a significant following amongst educators pre-pandemic. Concurrently, the rate of technology and curriculum changes demand more professional learning time than is typically given by schools and districts. Summer professional learning is often optional and highly variable across states. Our expectations are far too low for one of our most critical knowledge jobs. DFT Corps members would be paid during the summer for intensive study to update curriculum, plan content, and incorporate new education research on how students learn. Full-time summer work would remove pressure for administrators to “squeeze in” short, one-day professional development sessions during the school year, which study after study has demonstrated are a waste of time and money. Many current classroom educators to the former U.S. Secretary of Education continue to question these existing PD approaches.
Creates a leadership ladder: Leadership opportunities for classroom educators are few and far between. Teaching is often described as a “flat” profession, and nearly half of educators leaving the field point to a perceived lack of leadership or decision-making opportunities as contributing factors. Concurrently, new teachers who have the opportunity to collaborate with teacher-leaders within their own school generate stronger academic gains for their students. The DFT Corps would create state-wide leadership opportunities at Corps summer sites that do not disrupt school-year teaching, allowing educators to remain in the classroom during the other nine months of the year but still access visible leadership and mentor roles during the summer.
Leverages peer-based learning: Beyond the opportunity to positively impact students and student learning, 63% of educators report that strong relationships with other teachers are a top reason for staying in the classroom. The DFT Corps would leverage peer-based professional development over multiple years, reallocating the summer months to joint study and creating stronger educator networks statewide. One of the DFT Corp’s precedent peer-based models, the National Writing Project, “has a legacy as being the best professional development model for K-12 teachers” precisely due to a targeted focus on peer exchange. In post-training interviews, researchers found that educators “immediately changed several of their teaching practices and felt a renewed sense of enthusiasm towards the teaching of writing after participating in the NWP… a renewed sense of authority that quickly transferred to agency, these teachers possessed the self-efficacy to share what they knew and had learned with other teachers, administrators, district leaders, fellow graduate students, and most importantly, the students who would enter their classrooms in the fall.”
Builds needed prestige for the profession: The DFT Corps program forwards a reinvigorated national prioritization of the education field. In the information economy, educators are one of our most critical professions, and a greater determinant of gross domestic product than any individual semiconductor or algorithm. Under a DFT Corps communications rollout, teaching would be separated from any prior stereotypes of “caretakers,” positioned instead as essential to the economic, technology, and security fabric that advance societal progress. Research consistently suggests that low prestige of the profession pushes high-achievers away from teaching, is closely correlated with both falling preparation and retention, and may even directly affect student achievement. In China, where educators have long enjoyed high prestige for their profession, researchers found that an expansion of the country’s Free Teacher Education program helped to increase application competitiveness, extend retention rates, and enhance self-identity for program participants in a pre-publication evaluation study. In a 2018 “Global Teacher Status Index,” China was the only country to score 100 while the United States scored under 40 points. The United States is falling behind in our education culture, and we have little time to make up for lost ground.
The long-term vision for this proposal also extends beyond the NSF AI Education Act and suggests a new mechanism for federal education support in the Every Student Succeeds Act.
National Security AI Entrepreneur Visa: Creating a New Pathway for Elite Dual-Use Technology Founders to Build in America
NVIDIA, Anthropic, OpenAI, HuggingFace, and scores of other American startups helping cement America’s leadership in the race for artificial intelligence (AI) dominance all have one thing in common: they have at least one immigrant co-founder. In fact, in 2023, the National Foundation for American Policy released a policy analysis on the role of immigrants in the top American AI companies. According to their research, 65% of the companies appearing on the Forbes AI 50 list were founded or co-founded by at least one immigrant. Immigrant entrepreneurs are critical to America’s economic success, and as the private sector takes an increasing role in developing critical dual-use technologies like AI, they will be critical to America’s defense.
According to a Brookings Foundation report, “China sees talent as central to its technological advancement; President Xi Jinping has repeatedly called talent ‘the first resource’ in China’s push for ‘independent innovation.’” It’s easy to understand why the CCP sees talent as critical in its efforts to dominate key dual-use technologies relevant to national and economic security – in today’s knowledge economy, those who can innovate faster win. A company like SpaceX, which almost single-handedly reinvigorated America’s spacefaring economy, would likely not exist without Elon Musk. The lists of companies and dual-use technologies critical to American national and economic security that are unlikely to have been created successfully without the right personalities behind them are innumerable. America needs these entrepreneurs more than ever as competition with China for global leadership in key fields like AI heats up.
Given increased competition for talent – from allies like the United Kingdom to competitors and adversaries like China – in critical technology areas like AI, Congress must act to support high-skilled entrepreneurs by creating a National Security Startup Visa specifically targeted at founders of AI firms whose technology is inherently dual-use and critical for America’s economic leadership and national security. To maximize the potential economic benefits of such a visa for all Americans, it can be narrowly tailored, focusing only on entrepreneurs who (1) have raised significant capital from accredited American investors and venture capitalists (VCs), (2) are willing to physically reside and start their business in an Opportunity Zone, and (3) will hire at least five Americans within the first year of operation. Immigration may be a complex issue, but there is no doubt that immigrant founders are the not-so-secret ingredient that have helped to fuel America’s rise as a tech superpower. Developing a narrowly scoped visa targeted at a critical technology segment means that America can ensure its continued dominance in AI, a technology that the CEO of Google has said may be as profound as fire or electricity.
Challenge and Opportunity
While the United States has long been the preferred destination for immigrant entrepreneurs, America has never had more competition for global talent. Countries like Canada, Germany, and Estonia have created visas to attract entrepreneurs, and they appear to be working. After the introduction of a Canadian startup visa in 2013, the program increased the likelihood of previously U.S.-based immigrants creating a startup in Canada by 69%. These are immigrants who were already in America to study or work, and it should have been an obvious choice for them to stay and build their company in the United States. This means that the United States is losing out to hundreds of new companies and likely thousands of high-paying jobs that would come along with them. The fact that Canada, thanks to a streamlined immigration process for founders, was able to attract so many who were already in the United States should serve as a serious warning as to how the competition for talent is heating up.
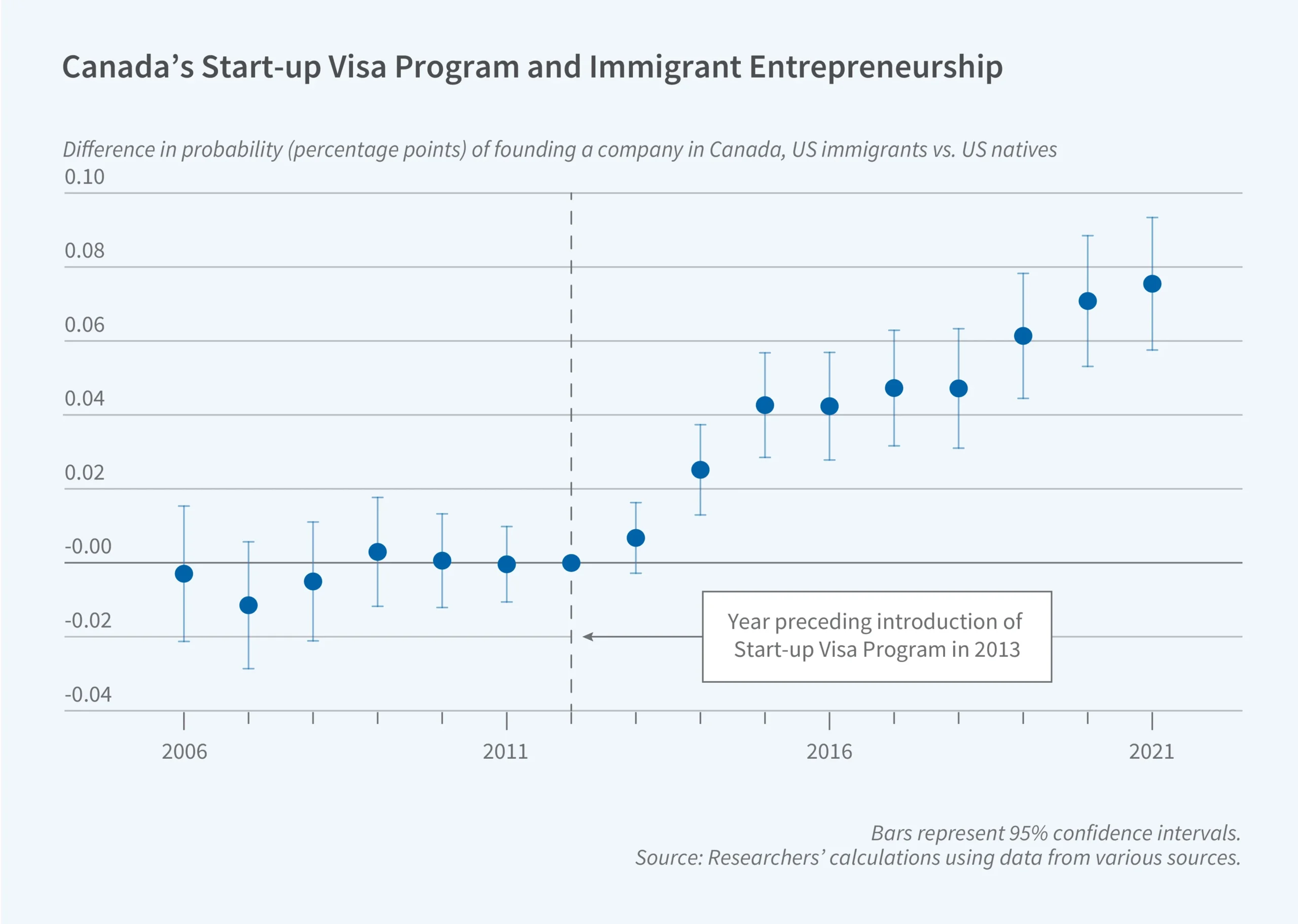
Canada demonstrates how a start-up visa enhances immigrant entrepreneurship via National Bureau of Economic Research
Historically, the United States—and Silicon Valley in particular—was the undisputed leader for venture capital fundraising and the place to start a potential unicorn (a company valued at over $1 billion). However, America’s dominance has shrunk, and VC dollars along with unicorns are increasingly found across the world in tech hotspots from China to India to the United Kingdom, showing it is increasingly easy for entrepreneurs to build a successful startup elsewhere. This is critical, because when America was the only place to build a leading company, entrepreneurs had little choice but to wade through the labyrinth that is the American immigration system. Now, top talent have many choices, and the United States must compete to become not just the premier destination to build a company and raise capital but one that is accessible to startup founders who can’t afford high-priced immigration lawyers or to wait for years until their visa is granted.
While America’s largest geopolitical competitor may suffer from extreme difficulties in attracting foreign entrepreneurs to its shores, China has a massive population advantage. This can be seen directly in the STEM space and AI in particular. According to a CSIS report, “By 2025, Chinese universities are projected to produce more than 77,000 STEM PhD graduates per year, more than double the 2010 level of about 34,000 STEM PhD graduates. In comparison, the United States is projected to graduate only approximately 40,000 STEM PhD students in 2025, a figure that includes over 16,000 international students.”
China has already outpaced the United States in the number of AI-related research articles published, and its domestic tech champions are global leaders in AI-enabled technology like facial recognition. Given the strong domestic showing in AI from Chinese researchers and entrepreneurs, with local AI startups raising billions of dollars in 2023 despite a slowdown in VC funding in China, China presents a strategic threat to America’s leadership in the AI space. America is on the cusp of losing its leadership in AI to China, but this policy creates clear opportunities to expeditiously regain lost ground by bringing in AI entrepreneurs who have already raised venture funding and are able to immediately hire American workers.
However daunting the challenge China presents, America has long had a superpower: attracting the best and brightest to our shores to build innovative global businesses. And while many leading American AI startups have an immigrant co-founder, for every entrepreneur coming to the United States today, many more are turned away or dissuaded from applying. Take Erdal Arikan, a Turkish MIT and CalTech graduate who had difficulty staying in America to continue his research and returned to Turkey. According to Graham Allison and Eric Schmidt, “It turned out that Arikan’s insight was the breakthrough needed to leap from 4G telecommunications networks to much faster 5G mobile internet services. Four years later, China’s national telecommunications champion, Huawei, was using Arikan’s discovery to invent some of the first 5G technologies. Today, Huawei holds over two-thirds of the patents related to Arikan’s solution… Had the United States been able to retain Arikan—simply by allowing him to stay in the country instead of making his visa contingent on immediately finding a sponsor for his work—this history might well have been different.”
By creating a narrowly tailored AI National Security Entrepreneur Visa, the United States has a unique opportunity to recruit founders in a field deemed “critical and emerging” by the White House and help the nation maintain both its economic and national security competitiveness. And while many are concerned about the potential economic dislocation from AI, one way to mitigate such a risk is by helping entrepreneurship flourish in the United States, especially in underserved communities like those found in Opportunity Zones across every state. With hundreds or thousands of new businesses creating high-paid jobs in rural and underserved communities, Americans outside existing tech hubs of New York City and San Francisco could finally see real economic benefits of the tech boom.
The economic potential for such a visa is tremendous. According to a 2024 report from the Center for Growth and Opportunity at Utah State University, a startup visa could have a significant impact: “Data collected at the state level suggests that when the population’s share of immigrant college graduates increases by 1 percent, patents per capita increase by 9 to 18 percent” with the report going on to say that (depending on the number of entrepreneurs brought in) “Census and industrial data predict an increase of 500,000 to 1.6 million new jobs from young start-up visa companies in the United States after 10 years of operation.”
The time for an AI startup visa is now. It will help create American jobs and revitalize local economies, cement American global leadership, and ensure that we beat China in the AI race.
Plan of Action
Create a 10-year pilot AI Entrepreneur Visa program for a select group of countries to demonstrate the potential efficacy of the visa.
The AI National Security Entrepreneur Visa will be narrowly tailored to founders from friendly nations, who have already raised significant capital for their companies from accredited American investors and are willing to physically reside in an Opportunity Zone. This will minimize risks of visa overstays and espionage while maximizing the potential economic benefits by bringing companies that have capital ready to deploy to the United States.
Visa Characteristics
- Initially available for nationals of Israel, the European Union, Japan, South Korea, Australia, New Zealand, United Kingdom, Canada, Ukraine, Armenia, Colombia, India, and Nigeria based on these country’s close ties to the U.S. and/or high rates of entrepreneurship.
- A two-year visa with an opportunity for a single three-year extension, plus a pathway to citizenship after the third year of residence in the United States.
- Also applies to immediate family members only (children and spouse).
- Allows for physical residency within any designated Opportunity Zone for the visa holder and, if applicable, their spouse and children.
- Rapid issuance by default with a maximum timeline for issuing a visa of 30 days from the date of a completed application being submitted.
- Allows for multiple foreign cofounders of a company to submit an application for a visa.
Initial Visa Application Requirements
- Must demonstrate that the company has raised at least $500,000 from an accredited American venture investor or firm.
- Have a startup focused on developing an AI or AI-enabled solution.
- To be considered eligible, each applicant must own at least 20% of the startup.
- Applicants must have demonstrated AI-related technology skills including software engineering, AI research, applied AI research, or tech product management OR have a bachelor’s or graduate degree in software engineering, physics, or mathematics from an accredited college or university.
Visa Extension Requirements
- The applicant must demonstrate that the visa holder’s company has created a minimum of five jobs employing American citizens within the first year of operation.
- The applicant must demonstrate that the company has grown revenues by at least 10% month over month on average during the period in which the visa was held OR have raised at least an additional $1.5 million from accredited American investors.
- The applicant must own 10% or more of the company at time of application for the visa extension.
Recommended Timeline
- Congress should mandate that the U.S. Citizenship and Immigration Services (USCIS) begin accepting applications for the pilot program within 180 days of the bill’s passage.
- Congress may consider adding a sunset provision 10 years after the program formally begins accepting applications in order to assess the program’s efficacy and determine whether it should be continued as is, scaled up, scaled down, or deprecated.
Miscellaneous Recommendations
- Consider creating a volunteer board of current and former American investors and entrepreneurs who can provide training and recommendations to the Department of Homeland Security/USCIS while guidelines and rules are being created for the new program.
- Example: An immigration officer may have difficulty understanding how prestigious an accelerator program such as Y Combinator or StartX is, leading them to downgrade an applicant who actually has a high likelihood of building a competitive startup.
- Require an independent economic impact assessment to be conducted every three years to understand the current and projected future impact of the program over time.
- Make the program fee-based, so that applicant fees pay for USCIS’s operating costs and no additional costs are passed on to taxpayers.
- Consider creating a cap of under $10,000 for total federal fees to make it accessible to early-stage startups.
- Ensure that it is possible for existing visa holders (student, work) to easily switch to the AI Entrepreneur Visa assuming they meet the relevant criteria.
- Consider allowing governors to opt in to the program, so that only states that would like to participate in the program do so.
Conclusion
America is in a race for global talent, especially when it comes to AI. The data shows that the majority of leading AI companies in America were created with at least one immigrant founder—but our immigration system makes it incredibly difficult for experts to come and build their companies in America, a serious strategic disadvantage compared to China, which produces dramatically more STEM graduates. By creating an AI National Security Entrepreneur Visa targeting high-skill founders who have already raised funds, Congress can quickly close the gap with China, bringing the best and brightest from around the world to America to build their companies. Not only will this help create jobs across the United States, it will make America the undisputed superpower in AI, allowing us to set standards and control the development of a technology whose impact may surpass those of all other innovations in recent decades.
This idea is part of our AI Legislation Policy Sprint. To see all of the policy ideas spanning innovation, education, healthcare, and trust, safety, and privacy, head to our sprint landing page.
Yes. Take it from the founder of Yahoo and naturalized American citizen, Jerry Yang, who said “If I had to worry about a visa, maybe Yahoo wouldn’t have gotten started,” and that “There are more places around the world where entrepreneurship has taken off… so founders have more choices. And to the extent that our immigration policies are not so welcoming, people don’t want to come.”
Created under President Trump’s Tax Cuts and Jobs Act, Opportunity Zones are designated areas across all 50 states deemed economically distressed by the Internal Revenue Service. Many previous technology booms have created outsized benefits to existing wealthy tech hubs like San Francisco and New York City thanks to positive agglomeration and network effects. By pushing entrepreneurs to found their business in a Opportunity Zone, which by its nature is an economically distressed area, the visa will help bring new jobs and opportunities to areas that previously had a difficult time attracting tech entrepreneurs and high-growth startups.
The Economic Innovation Group has written extensively about the concept of a “heartland visa,” which would allow counties to decide on specific new immigration pathways based on their distinct needs. The AI Entrepreneur Visa could be structured similarly, with states or localities opting in to the program and deciding the number and type of AI entrepreneurs they would like to bring to their communities.
Yes. Some options to further narrow the visa:
- Decrease the number of countries eligible for the pilot visa program.
- Create a cap for the number of potential founders per year (recommended minimum of 10,000 to create a sample size large enough for an economic impact assessment).
- Create a mandatory sunset for the program, requiring it to be renewed after five or 10 years.
- Increase equity ownership requirements or implement a maximum number of applicants per company.
- Allow individual states or counties to opt in to the program rather than it being available for the entire nation’s Opportunity Zones at the start.
Yes. Some options to further expand the visa:
- Increase the number of countries eligible to apply for the visa.
- Expand the technologies/industries eligible for the visa.
- Decrease or eliminate the threshold for the amount of funds raised to be eligible.
- Decrease or eliminate equity ownership requirements.
- The company’s primary physical place of business must be shown to be within an Opportunity Zone.
Improving Health Equity Through AI
Clinical decision support (CDS) artificial intelligence (AI) refers to systems and tools that utilize AI to assist healthcare professionals in making more informed clinical decisions. These systems can alert clinicians to potential drug interactions, suggest preventive measures, and recommend diagnostic tests based on patient data. Inequities in CDS AI pose a significant challenge to healthcare systems and individuals, potentially exacerbating health disparities and perpetuating an already inequitable healthcare system. However, efforts to establish equitable AI in healthcare are gaining momentum, with support from various governmental agencies and organizations. These efforts include substantial investments, regulatory initiatives, and proposed revisions to existing laws to ensure fairness, transparency, and inclusivity in AI development and deployment.
Policymakers have a critical opportunity to enact change through legislation, implementing standards in AI governance, auditing, and regulation. We need regulatory frameworks, investment in AI accessibility, incentives for data collection and collaboration, and regulations for auditing and governance of AI systems used in CDS systems/tools. By addressing these challenges and implementing proactive measures, policymakers can harness AI’s potential to enhance healthcare delivery and reduce disparities, ultimately promoting equitable access to quality care for everyone.
Challenge and Opportunity
AI has the potential to revolutionize healthcare, but its misuse and unequal access can lead to unintended dire consequences. For instance, algorithms may inadvertently favor certain demographic groups, allocating resources disproportionately and deepening disparities. Efforts to establish equitable AI in healthcare have seen significant momentum and support from various governmental agencies and organizations, specifically regarding medical devices. The White House recently announced substantial investments, including $140 million for the National Science Foundation (NSF) to establish institutes dedicated to assessing existing generative AI (GenAI) systems. While not specific to healthcare, President Biden’s blueprint for an “AI Bill of Rights” outlines principles to guide AI design, use, and deployment, aiming to protect individuals from its potential harms. The Food and Drug Administration (FDA) has also taken steps by releasing a beta version of its regulatory framework for medical device AI used in healthcare. The Department of Health and Human Services (DHHS) has proposed revisions to Section 1557 of the Patient Protection and Affordable Care Act, which would explicitly prohibit discrimination in the use of clinical algorithms to support decision-making in covered entities.
How Inequities in CDS AI Hurt Healthcare Delivery
Exacerbate and Perpetuate Health Disparities
The inequitable use of AI has the potential to exacerbate health disparities. Studies have revealed how population health management algorithms, which proxy healthcare needs with costs, allocate more care to white patients than to Black patients, even when health needs are accounted for. This disparity arises because the proxy target, correlated with access to and use of healthcare services, tends to identify frequent users of healthcare services, who are disproportionately less likely to be Black patients due to existing inequities in healthcare access. Inequitable AI perpetuates data bias when trained on skewed or incomplete datasets, inheriting and reinforcing the biases through algorithmic decisions, thereby deepening existing disparities and hindering efforts to achieve fairness and equity in healthcare delivery.
Increased Costs
Algorithms trained on biased datasets may exacerbate disparities by misdiagnosing or overlooking conditions prevalent in marginalized communities, leading to unnecessary tests, treatments, and hospitalizations and driving up costs. Health disparities, estimated to contribute $320 billion in excess healthcare spending, are compounded by the uneven adoption of AI in healthcare. The unequal access to AI-driven services widens gaps in healthcare spending, with affluent communities and resource-rich health systems often pioneering AI technologies, leaving underserved areas behind. Consequently, delayed diagnoses and suboptimal treatments escalate healthcare spending due to preventable complications and advanced disease stages.
Decreased Trust
The unequal distribution of AI-driven healthcare services breeds skepticism within marginalized communities. For instance, in one study, an algorithm demonstrated statistical fairness in predicting healthcare costs for Black and white patients, but disparities emerged in service allocation, with more white patients receiving referrals despite similar sickness levels. This disparity undermines trust in AI-driven decision-making processes, ultimately adding to mistrust in healthcare systems and providers.
How Bias Infiltrates CDS AI
Lack of Data Diversity and Inclusion
The datasets used to train AI models often mirror societal and healthcare inequities, propagating biases present in the data. For instance, if a model is trained on data from a healthcare system where certain demographic groups receive inferior care, it will internalize and perpetuate those biases. Compounding the issue, limited access to healthcare data leads AI researchers to rely on a handful of public databases, contributing to dataset homogeneity and lacking diversity. Additionally, while many clinical factors have evidence-based definitions and data collection standards, attributes that often account for variance in healthcare outcomes are less defined and more sparsely collected. As such, efforts to define and collect these attributes and promote diversity in training datasets are crucial to ensure the effectiveness and fairness of AI-driven healthcare interventions.
Lack of Transparency and Accountability
While AI systems are designed to streamline processes and enhance decision-making across healthcare, they also run the risk of inadvertently inheriting discrimination from their human creators and the environments from which they draw data. Many AI decision support technologies also struggle with a lack of transparency, making it challenging to fully comprehend and appropriately use their insights in a complex, clinical setting. By gaining clear visibility into how AI systems reach conclusions and establishing accountability measures for their decisions, the potential for harm can be mitigated and fairness promoted in their application. Transparency allows for the identification and remedy of any inherited biases, while accountability incentivizes careful consideration of how these systems may negatively or disproportionately impact certain groups. Both are necessary to build public trust that AI is developed and used responsibly.
Algorithmic Biases
The potential for algorithmic bias to permeate healthcare AI is significant and multifaceted. Algorithms and heuristics used in AI models can inadvertently encode biases that further disadvantage marginalized groups. For instance, an algorithm that assigns greater importance to variables like income or education levels may systematically disadvantage individuals from socioeconomically disadvantaged backgrounds.
Data scientists can adjust algorithms to reduce AI bias by tuning hyperparameters that optimize decision thresholds. These thresholds for flagging high-risk patients may need adjustment for specific groups to balance accuracy. Regular monitoring ensures thresholds address emerging biases over time. In addition, fairness-aware algorithms can apply statistical parity, where protected attributes like race or gender do not predict outcomes.
Unequal Access
Unequal access to AI technology exacerbates existing disparities and subjects the entire healthcare system to heightened bias. Even if an AI model itself is developed without inherent bias, the unequal distribution of access to its insights and recommendations can perpetuate inequities. When only healthcare organizations that can afford advanced AI for CDS leverage these tools, their patients enjoy the advantages of improved care that remain inaccessible to disadvantaged groups. Federal policy initiatives must prioritize equitable access to AI by implementing targeted investments, incentives, and partnerships for underserved populations. By ensuring that all healthcare entities, regardless of financial resources, have access to AI technologies, policymakers can help mitigate biases and promote fairness in healthcare delivery.
Misuse
The potential for bias in healthcare through the misuse of AI extends beyond the composition of training datasets to encompass the broader context of AI application and utilization. Ensuring the generalizability of AI predictions across diverse healthcare settings is as imperative as equity in the development of algorithms. It necessitates a comprehensive understanding of how AI applications will be deployed and whether the predictions derived from training data will effectively translate to various healthcare contexts. Failure to consider these factors may lead to improper use or abuse of AI insights.
Opportunity
Urgent policy action is essential to address bias, promote diversity, increase transparency, and enforce accountability in CDS AI systems. By implementing responsible oversight and governance, policymakers can harness the potential of AI to enhance healthcare delivery and reduce costs, while also ensuring fairness and inclusion. Regulations mandating the auditing of AI systems for bias and requiring explainability, auditing, and validation processes can hold organizations accountable for the ethical development and deployment of healthcare technologies. Furthermore, policymakers can establish guidelines and allocate funding to maximize the benefits of AI technology while safeguarding vulnerable groups. With lives at stake, eliminating bias and ensuring equitable access must be a top priority, and policymakers must seize this opportunity to enact meaningful change. The time for action is now.
Plan of Action
The federal government should establish and implement standards in AI governance and auditing for algorithms directly influencing diagnosis, treatment, and access to care of patients. These efforts should address and measure issues such as bias, transparency, accountability, and fairness. They should be flexible enough to accommodate advancements in AI technology while ensuring that ethical considerations remain paramount.
Regulate Auditing and Governance of AI
The federal government should implement a detailed auditing framework for AI in healthcare, beginning with stringent pre-deployment evaluations that require rigorous testing and validation against established industry benchmarks. These evaluations should thoroughly examine data privacy protocols to ensure patient information is securely handled and protected. Algorithmic transparency must be prioritized, requiring developers to provide clear documentation of AI decision-making processes to facilitate understanding and accountability. Bias mitigation strategies should be scrutinized to ensure AI systems do not perpetuate or exacerbate existing healthcare disparities. Performance reliability should be continuously monitored through real-time data analysis and periodic reviews, ensuring AI systems maintain accuracy and effectiveness over time. Regular audits should be mandated to verify ongoing compliance, with a focus on adapting to evolving standards and incorporating feedback from healthcare professionals and patients. AI algorithms evolve due to shifts in the underlying data, model degradation, and changes to application protocols. Therefore, routine auditing should occur at a minimum of annually.
With nearly 40% of Americans receiving benefits under a Medicare or Medicaid program, and the tremendous growth and focus on value-based care, the Centers for Medicare & Medicaid Services (CMS) is positioned to provide the catalyst to measure and govern equitable AI. Since many health systems and payers leverage models across multiple other populations, this could positively affect the majority of patient care. Both the companies making critical decisions and those developing the technology should be obliged to assess the impact of decision processes and submit select impact-assessment documentation to CMS.
For healthcare facilities participating in CMS programs, this mandate should be included as a Condition of Participation. Through this same auditing process, the federal government can capture insight into the performance and responsibility of AI systems. These insights should be made available to healthcare organizations throughout the country to increase transparency and quality between AI partners and decision-makers. This will help the Department of Health and Human Services (HHS) meet the “Promote Trustworthy AI Use and Development” pillar of its AI strategy (Figure 1).
Congress must enforce these systems of accountability for advanced algorithms. Such work could be done by amending and passing the 2023 Algorithmic Accountability Act. This proposal mandates that companies evaluate the effects of automating critical decision-making processes, including those already automated. However, it fails to make these results visible to the organizations that leveraging these tools. An extension should be added to make results available to governing bodies and member organizations, such as the American Hospital Association (AHA).
Invest in AI Accessibility and Improvement
AI that integrates the social and clinical risk factors that influence preventive care could be beneficial in managing health outcomes and resource allocation, specifically for facilities providing care to mostly rural areas and patients. While organizations serving large proportions of marginalized patients may have access to nascent AI tools, it is very likely they are inadequate given they weren’t trained with data adequately representing this population. Therefore, the federal government should allocate funding to support AI access for healthcare organizations serving higher percentages of vulnerable populations. Initial support should stem from subsidies to AI service providers that support safety net and rural health providers.
The Health Resources and Services Administration should deploy strategic innovation funding to federally qualified health centers and rural health providers to contribute to and consume equitable AI. This could include funding for academic institutions, research organizations, and private-sector partnerships focused on developing AI algorithms that are fair, transparent, and unbiased specific for these populations.
Large language models (LLM) and GenAI solutions are being rapidly adopted in CDS tooling, providing clinicians with an instant second opinion in diagnostic and treatment scenarios. While these tools are powerful, they are not infallible and pose a risk without the ability to evolve. Therefore, research regarding AI self-correction should be a focus of future policy. Self-correction is the ability for an LLM or GenAI to identify and rectify errors without external or human intervention. Mastering the ability for these complex engines to recognize possible life-threatening errors would be crucial in their adoption and application. Healthcare agencies, such as the Agency for Healthcare Research and Quality (AHRQ) and the Office of the National Coordinator for Health Information Technology, should fund and oversee research for AI self-correction specifically leveraging clinical and administrative claims data. This should be an extension of either of the following efforts:
- 45 CFR Parts 170, 171 as it “promotes the responsible development and use of artificial intelligence through transparency and improves patient care through policies…which are central to the Department of Health and Human Services’ efforts to enhance and protect the health and well-being of all Americans”
- AHRQ’s funding opportunity from May 2024 (NOT-HS-24-014), Examining the Impact of AI on Healthcare Safety (R18)
Much like the Breakthrough Device Program, AI that can prove it decreases health disparities and/or increases accessibility can be fast-tracked through the audit process and highlighted as “best-in-class.”
Incentivize Data Collection and Collaboration
The newly released “Driving U.S. Innovation in Artificial Intelligence” roadmap considers healthcare a high-impact area for AI and makes specific recommendations for future “legislation that supports further deployment of AI in health care and implements appropriate guardrails and safety measures to protect patients,… and promoting the usage of accurate and representative data.” While auditing and enabling accessibility in healthcare AI, the government must ensure that the path to build equity into AI solutions does not remain an obstacle. This entails improved data collection and data sharing to ensure that AI algorithms are trained on diverse and representative datasets. As the roadmap declares, there must be “support the NIH in the development and improvement of AI technologies…with an emphasis on making health care and biomedical data available for machine learning and data science research while carefully addressing the privacy issues raised by the use of AI in this area.”
These data exist across the healthcare ecosystem, and therefore decentralized collaboration can enable a more diverse corpus of data to be available to train AI. This may involve incentivizing healthcare organizations to share anonymized patient data for research purposes while ensuring patient privacy and data security. This incentive could come in the form of increased reimbursement from CMS for particular services or conditions that involve collaborating parties.
To ensure that diverse perspectives are considered during the design and implementation of AI systems, any regulation handed down from the federal government should not only encourage but evaluate the diversity and inclusivity in AI development teams. This can help mitigate biases and ensure that AI algorithms are more representative of the diverse patient populations they serve. This should be evaluated by accrediting parties such as The Joint Commission (a CMS-approved accrediting organization) and their Healthcare Equity Certification.
Conclusion
Achieving health equity through AI in CDS requires concerted efforts from policymakers, healthcare organizations, researchers, and technology developers. AI’s immense potential to transform healthcare delivery and improving outcomes can only be realized if accompanied by measures to address biases, ensure transparency, and promote inclusivity. As we navigate the evolving landscape of healthcare technology, we must remain vigilant in our commitment to fairness and equity so that AI can serve as a tool for empowerment rather than perpetuating disparities. Through collective action and awareness, we can build a healthcare system that truly leaves no one behind.
This idea is part of our AI Legislation Policy Sprint. To see all of the policy ideas spanning innovation, education, healthcare, and trust, safety, and privacy, head to our sprint landing page.