 e-Prints
e-Prints e-Prints
e-PrintsJoint Warfare and
Military Dependence on SpaceBy JEFFREY CATON
Major Jeffrey L. Caton, USAF, is assigned to the Space Standardization and Evaluation Division, Cheyenne Mountain Operations Center, U.S. Space Command.Retaining the current international character of space will remain
critical to achieving national security goals.
- National Security Strategy, July 1994
After thirty-five years, space systems remain an integral part of national security. Desert Storm—which some regard as the first space war—represented the first widespread use of military space systems by common soldiers, sailors, marines, and airmen. It was also a harbinger of future military operations in which dependence on space-based force enhancement will continue to grow. This dependence by the Armed Forces on space systems reveals a vulnerability that an enemy with knowledge and expertise could exploit and concentrates on an ignored threat: countries with little or no space capability. The exploitation of space dependency can greatly benefit an unsophisticated foe by dramatically degrading our efficiency in combat.
Dependence
Military space operations were extensive as early as 19631. Both the United States and the Soviet Union used space capabilities to observe strategic weapon systems, and that helped provide for a stable nuclear deterrence strategy. The use of space by the military has not been limited to strategic nuclear applications but has covered the conflict spectrum. A science adviser to President Reagan noted that "even in a very limited war, we would have an absolutely critical dependence on space today."2 Indeed, space systems have played a crucial role in a number of limited operations: El Dorado Canyon (Libya, 1986), Earnest Will (the Persian Gulf, 1988), and Just Cause (Panama, 1989), to name a few.
Probably the best known military use of space occurred during Desert Shield/Desert Storm, when it greatly enhanced coalition effectiveness. Space systems provided support for navigation, weather, missile defense, communications, reconnaissance and surveillance, and target acquisition. As we face increasing global responsibilities with smaller forces, our ability to accomplish military missions will depend ever more on such force-enhancing support from space.
The dependence on a specific space system is linked not only to the availability of alternate means of performing system tasks, but also to the effectiveness and efficiency of those means.3 Since space systems and their alternate means can be affected by outside forces, however, military dependence on space—the so-called space dependency link—is dynamic in a combat environment; that is, subject to constant change in its magnitude.
Vulnerability
The ultimate objective of military space operations is the effective employment of space capabilities in support of land, sea, and air operations to gain and maintain a combat advantage throughout the operational continuum and across the three levels of war.
—Joint Pub 3-14, Space Operations
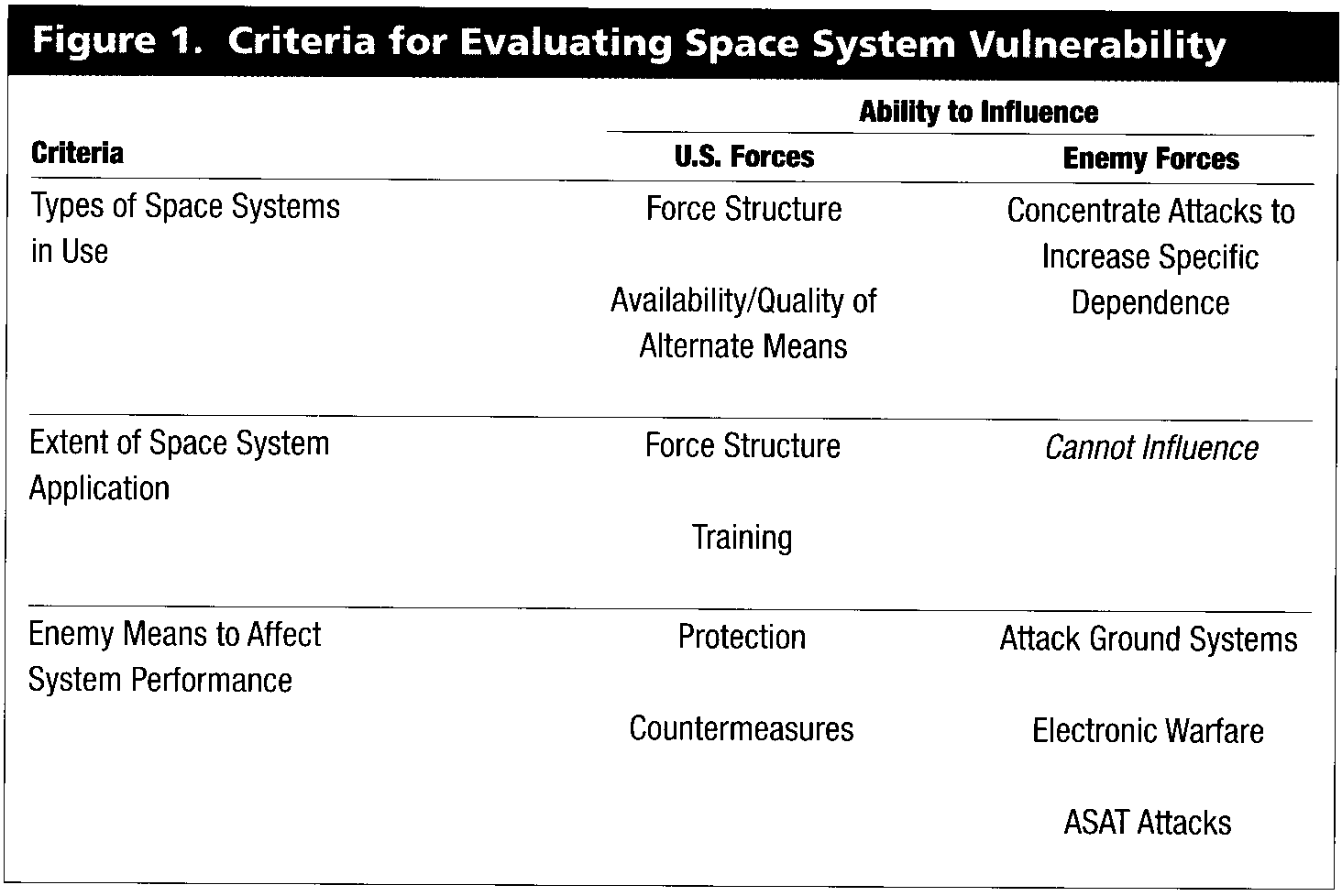
Two studies conducted by the Ford administration in 1976 concluded that the United States was growing dependent on satellites for various functions, with little provision for satellite survival during wartime.4 While the studies concentrated on satellite vulnerabilities, it is important to look at vulnerabilities in joint surface forces (including air forces) that result from dependence on space. The extent of our space dependency link is based on three criteria: the types of space systems vital to ongoing operations, the extent of their use among our forces, and an enemy's ability to affect system performance (see figure 1).
Both the United States and its adversaries can influence the first criterion—the importance of a given space system to ongoing operations. We may affect it in our selection of force structure which, in turn, dictates the availability and quality of alternate means of performing system tasks. Since these alternate means may include assets from other countries, dependence on space systems extends to coalition operations. At least eight U.S. and coalition civilian satellites were called upon during Desert Storm to augment U.S. systems.5 It can be expected that such systems would be "fair game" for enemy antisatellite (ASAT) efforts during wartime.6
An enemy can influence these criteria by conducting operations that increase dependence on a satellites given space system This may include physically destroying alternate means of task performance or simply concentrating their efforts to increase U.S. use of satellites.
The second criterion—scope of application—is influenced only by the United States. Once again, our force structure is the key player since it dictates the amount of surface-based equipment that is acquired and the level at which it is used. Space systems are well ingrained in our forces, as illustrated by three applications from Desert Storm: communications, navigation, and intelligence. Over a thousand single-channel, manportable satellite radio units were issued at small unit level. All told, satellites provided 85-90 percent of intratheater and intertheater communications. Also thousands of global positioning system (GPS) receivers were used by coalition ships, planes, and ground troops to navigate on unfamiliar and featureless terrain. Finally, each service supported an ongoing initiative called Tactical Exploitation of National Capabilities (TENCAP), which allowed joint force tactical units to receive and sort intelligence data directly from space.7
The third criterion—enemy ability to affect system performance—can be influenced by both ourselves and adversaries. The United States can affect the enemy's ability to attack friendly space systems by using countermeasures for satellites.8 These protective measures fall under the "space control" mission area. The objective is defending friendly space assets and denying an enemy use of his own. Currently, the popular view of space control emphasizes its role in the larger category of "information warfare." As such, space control strategies are geared more toward the protection and denial of satellite data than physical attacks on space system assets.9
An enemy might weigh the vulnerability of a space system to determine if the U.S. space dependency link could be impacted. How can an enemy take advantage of such vulnerabilities?
Exploitation
[Satellites] would be so valuable to the overall order of battle that any opponent would have to take them into account in his overall battle plan and try to exploit any possible weakness.10
Attacking our space systems could provide an enemy with excellent leverage by degrading our combat efficiency and effectiveness. An enemy who is not dependent on space systems (civil or military) can target ours with no fear of retaliation in kind. In such a case no space deterrence exists for the United States.
Enemies with no space capabilities can lease them. America may conduct diplomatic space control by encouraging states not to provide space support to foes. This occurred during Operation Desert Shield when France, working in collaboration with the coalition, agreed not to sell SPOT multispectral imagery data to Iraq.11 But cutting off access to space data may make the targeting of U.S. space assets more attractive to an enemy. This may apply even to systems that have open access, such as GPS. Simply put, if the enemy cannot use space or must use it at a disadvantage, he can only gain by knocking space systems out.
The equipment and tactics required for attacks on ground systems by conventional, special operations, and terrorist forces are readily available. The equipment for certain ground-based, air-based, and sea-based electromagnetic jamming also is obtainable from many countries, especially the former Soviet Union (FSU). Methods of attack against the space segment include direct ascent and coorbital weapon systems and directed energy beams that can disrupt or destroy satellites.12 FSU has demonstrated several types of ASAT systems, and this technology may be" come available to aggressor nations.
Feasibility of Attack
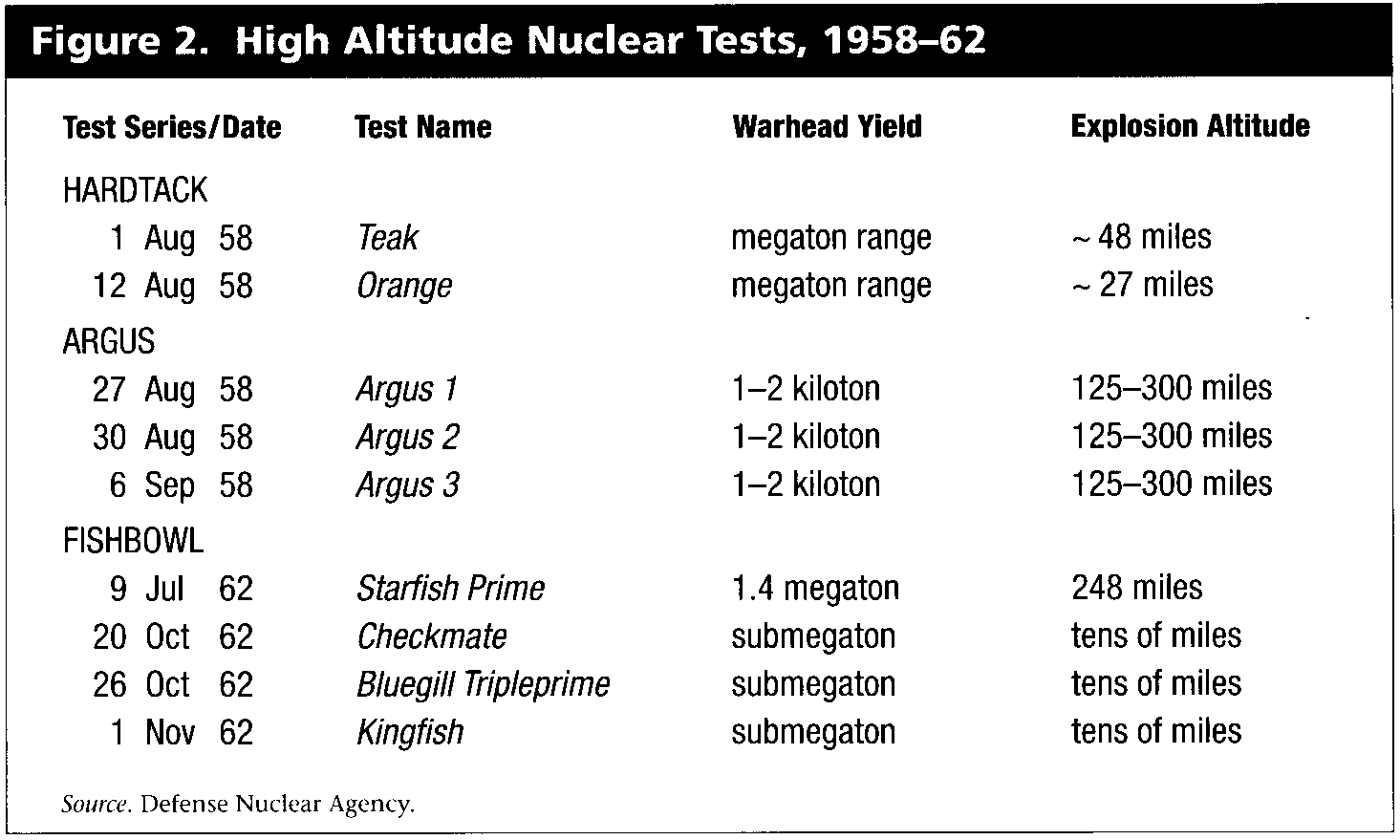
One method of electromagnetic disruption is the high-altitude detonation of nuclear devices. Three series of high-altitude nuclear tests conducted by the United States between 1958 and 1962 (see test summary in figure 2) demonstrated electromagnetic phenomena that affected space operations: widespread ionization, electromagnetic pulse (EMP), and artificial auroras.13 Of particular interest was the "argue effect," named for the shell formed around the earth by beta particles after a nuclear detonation. Trapped radiation from the test explosion with the largest yield, Starfish Prime which had a 1.4 megaton warhead, inadvertently damaged at least three satellites.
The overall ASAT system concept was proven by the 10th Aerospace Defense Squadron at Johnston Island in 1964-1975.14 Successful operation of this unit required years of research and testing. The many challenges for an enemy to develop and operate such a system can be divided into three areas: tracking and targeting, delivery, and warhead.
Tracking and targeting a satellite is often considered an expensive process that requires an immense infrastructure and highly qualified technical personnel. However, the Kettering group, an informal network that monitors space activities, has proven that it can be done using common and inexpensive electronics with minimal training. For example, in 1978 a 12-year-old student at Kettering Boys School, with the aid of his physics teacher (a Kettering group member), predicted within a 24 hour range when the Cosmos 954 satellite would reenter the atmosphere. The group also was credited with discovering the then-secret Soviet launch facility at Plesetsk in 1966 as well as tracking Soviet spy satellites that were observing the 1967 Arab-Israeli War.15 In both cases the tracking was done without modern calculators and personal computers. Today, an enemy can purchase commercial software packages to calculate orbital mechanics and can access the computer Internet to obtain the orbital parameters of satellites. Using this information, tracking and targeting a nuclear ASAT within its effective radius (usually measured in milesl6) is certainly feasible.
Once a target is selected, a delivery vehicle must place the warhead in a given effect radius. Not including countries with established missile programs (namely, the United States, countries of the former Soviet Union, France, China, and Great Britain), there are at least 22 states with active ballistic missile programs.17 Ballistic missiles can be developed to optimize the apogee for ASAT effectiveness. Technological hurdles to the development of missile systems may be overcome with the help of FSU workers for hire: NPO Energomash, Russia's leading developer of liquid-fueled rocket engines, lost much of its experienced staff in September 1993.15
Hiring expertise could also help develop space hardware for the final guidance and control of warheads. But generating a satellite bus was another task accomplished by a group of amateur radio enthusiasts who designed, constructed, and operated six satellites. Built mostly in their garages, the first orbiting satellite carrying amateur radio equipment (OSCAR 1) was launched in December 1961. The design and performance of the OSCAR series have improved over time, yet the majority of the work is still done by amateurs using their own resources.
The final challenge to operating a nuclear ASAT is acquiring a warhead. Though difficult, developing or procuring nuclear weapons is feasible enough that our national security strategy lists their proliferation as a major concern. A recent Air Force study estimated that in 1993 as many as 10 countries were capable of producing nuclear weapons.
This could increase to 25 by 2003.19 A separate probe by a government proliferation study team estimated that eight third world countries would be added to the list by 2000.20
Effects
Spending billions in space makes little sense if the assets are unusable in wartime.21
An attack on our space assets could impact every element of national power—political, diplomatic, economic, and military. During conflict, a priority of any commander is to prepare the battlespace22 for combat operations—that is, to "stack the deck" to his advantage. An enemy has much to gain by exploiting the dependency link between our terrestrial forces and force-enhancing space systems. An assault on U.S. military space systems is a force multiplier for an enemy.
If prepared, the Armed Forces could probably operate in remote theaters without the aid of space systems. However, based on the increasing strength of space dependency links, they would have problems operating under the immediate and unexpected loss of critical space support, which would give at least temporary advantage to an enemy. That edge could increase by synchronizing attacks on space systems with assaults on terrestrial forces. While this may not enable an enemy to triumph militarily, it may cause loss of life and materiel sufficient to bring our withdrawal.
Bang for the Buck
The most effective and least defendable method of attack against space systems is the high-altitude detonation of a nuclear device.23 Depending on the yield of the warhead, a nuclear ASAT could attack multiple satellite systems with one detonation. Such an attack would have temporary and permanent effects on U.S. forces. Depending on the design and operating radio frequency of the target, temporary effects could last minutes, hours, or days. These effects can be used to great advantage. If an enemy plans an offensive with the high-altitude nuclear environment in mind (for example, EMP, atmospheric ionization), it can opt to outfit troops with low-tech equipment and procedures that would be unaffected by such an attack. Devices such as signal flags, compasses, and presurveyed attack routes could be turned into enemy force enhancers that exploit GPS navigation and satellite communication links that are suddenly severed. An enemy could thus strengthen the synergistic synchronization effects of his terrestrial attack.A nuclear ASAT can destroy or damage satellites in its kill radius. As a consequence of the inadvertent satellite damage caused by the Starfish Prime nuclear test, it was obvious that nuclear ASATs would have limited usefulness because of unavoidable collateral damage they would inflict on other U.S. satellites.24 While such damage may concern us, it is of great benefit to a country which is not space dependent. Without penalties—indeed with benefits—for collateral damage, an enemy can pursue indiscriminate area targeting that allows less sophisticated targeting and delivery systems for its ASAT.
The permanent damage to satellites may introduce secondary damage mechanisms that would benefit an enemy. Even though space is vast, many of the useful orbits to support given areas on earth are heavily populated by satellites. This "bunching" could allow secondary satellite kills through debris fratricide. This could have a cascading effect as new collisions create more debris.25 The bottom line is that an enemy need not possess space forces to be a space threat.
The use of any nuclear device is likely to have significant political implications. While it may be acceptable to direct such a device at inanimate objects, the indiscriminate nature of ASAT may not be acceptable to neutral countries whose space systems and related economic links may be impacted. But faced with an enemy who has a low regard for world opinion (a Saddam Hussein or Mu'ammar Qadhafi), these factors
may have little effect on enemy strategy. Given that reality, how can we best prepare against such a threat?
Countermeasures
In considering countermeasures against threats to space systems, the objective is to assess all elements of a system for vulnerabilities and provide survivability measures. Proliferation and reconstitution measures can then be added to ensure continuous capability on all levels of conflict.
As microelectronics become more sophisticated, they are more vulnerable to radiation. The radiation level needed to produce instantaneous failure in circuits today is two orders of magnitude less than in the 1970s. Worse, domestic vendors who produce radiation-tolerant semiconductors fell from twenty in 1990 to four in 1995. DOD investment in radiation-hardening technology also dropped, from $50 million in 1989 to $20 million in 1995.26
Equipment hardening and autonomy can reduce electromagnetic and radiation interference from ASAT attacks. However, hardening countermeasures would offer little protection from blast and debris damage. Also, the ability to maneuver may be of little use since there would be only a few minutes for ground operators to observe the ASAT launch, assess intent, determine its target, and command the target satellite to avoid the impact area. But such maneuver capability may be useful for an untargeted satellite to avoid a fratricide threat resulting from a successfully targeted satellite.
The use of on-orbit spares (proliferation) confronts the enemy with more potential targets. However, since some of these spares may have to be in orbits similar to the target satellites to be effective, they may also be vulnerable to fratricide.
Reconstitution through space launch offers promise as a countermeasure. As one analyst observed, "reconstituting essential space assets after hostilities begin may be the only method of ensuring that critical systems survive.27 While reconstitution would not be effective in preventing an enemy's initial operations, it would allow for satellites to be reintroduced into the battlespace, possibly in support of U.S. counteroffensive operations.
Finally, one of the best countermeasures, training, is not directly related to space systems. Future joint and coalition training should insert unexpected interruptions of space systems support. Our forces should identify and practice alternate means of conducting operations which normally include space dependency links.
The military use of space is a double-edged sword with strengths as well as vulnerabilities. Faced with growing responsibilities and decreasing forces, our ability to accomplish missions will depend more and more on force-enhancing support from space. Launch The resulting vulnerability may be affected by both the United States and a potential enemy. Developing counter-measures to threats against our space systems may enable us to avoid a needless loss of lives and equipment on the battlefield of the future.
NOTES
1
Paul B. Stares, The Militarization of Space, U.S. Policy, 1945-1984 (Ithaca, N.Y.: Cornell University Press, 1984), p.240.2
Quoted in Paul B. Stares, Space and National Security (Washington: The Brookings Institution, 1987), p.46.3
Stares, Space and National Security, p. 47.4
Stares, The Militarization of Space, pp. 169-70.5
Peter Anson and Dennis Cummings, "The First Space War: The Contribution of Satellites to the Gulf War," RUSI Journal, vol. 136, no. 4 (Winter 1991), p. 49.6
Stares, The Militarization of Space, p. 248. Also see George E Jelen, "Space System Vulnerabilities and Countermeasures," in National Interests and the Military Use of Space, William J. Durch, editor (Cambridge, Mass.: Ballinger Publishing Co., 1984), p.90.7
David A. Fulghum, "Talon Lance Gives Aircrews Timely Intelligence from Space," Aviation Week and Space Technology, vol. 139, no. 8 (August 23,1993), p.70.8
Robert B. Giffen, "Space System Survivability: Strategic Alternatives for the 1990s," in International Security Dimensions Of Space, Uri Ra'anan and Robert L. Pfaltzgraff, Jr., editors (Medford, Mass.: Archon Books, 1984), pp. 87-92, discusses satellite countermeasures.9
Robyn A. Chumley, "Supporting the Warfighter," Airman, vol. 38, no. 11 (November 1994), p.35.10
Gregory H. Canavan and Simon P. Worden, "Military Space in the Next Century" lecture to Air University Spacecast 2020 Team, Air War College, Maxwell Air Force Base, Ala., 1993, p.10.11
Patricia Gilmartin, "Gulf War Rekindles U.S. Debate on Protecting Space Systems Data," Aviation Week and Space Technology, vol. 134, no. 17 (April 29.1991). D.55.12
Jelen, "Space System Vulnerabilities," pp.91-95.13
Samuel Glastone and Philip J. Dolan, editors, The Effects of Nuclear Weapons, third edition (Washington: Government Printing Office, 1977), pp. 45-48, 71-77, 461, 487, 518-23; F.R. Gladeck et al., Operation Hardtack I-1958, DNA report 6038F (Washington: Defense Nuclear Agency, December 1, 1982), pp. 257-73; C.B. Jones et al., Operation Argus 1958, DNA report 6039F (Washington: Defense Nuclear Agency, April 30, 1982), pp. 58-72.14
Curtis Peebles, Battle for Space (New York: Beaufort Books, 1983), pp. 85-94.15
Doug Stewart, "Satellite Sleuths," Air and Space, vol. 5, no.2 June/July 1990), pp.27-34.i6 Peebles, Battle for Space, pp. 88-91. The reported satellite killing radius for the 10th Aerospace Defense Squadron was five miles. During two CEL tests the ASAT simulated warhead passed within 0.89 and 2.019 nautical miles, both highly successful.
|7 Thomas A. Torgerson, Global Power Through Tactical Flexibility: Rapid Deployable Space Units, Airpower Research Institute Research Report no. AU-ARI-93-6 (Maxwell Air Force Base, Ala.: Air University Press, 1994).
18
Jeffrey M. Lenorovitz and Boris Rybak, "Engineers Flee Low-Paying CIS Jobs," Aviation Week and Space Technology, vol. 139, no. 13 (September 27, 1993), p. 53.19
Headquarters, U.S. Air Force (AF/XOXI), briefing entitled "Countering Weapons of Mass Destruction Proliferation" (1993), p. 5.20
Torgerson, Global Power, p. 16.21
Giffen, "Space System Survivability," p. 100.22
Battlespace is replacing battlefield in military lexicons and is taken to be the logical extension of battlefield into all dimensions and media of operation.23
Stares, Space and National Security, p. 77.24
Stares, The Militarization of Space, p. 108.25
Canavan, "Military Space," p. 12.26
R.C. Webb et al., "The Commercial and Military Satellite Survivability Crisis," Defense Electronics, vol. 27, no. 8 (August 1995), pp. 21-25.27
Giffen, "Space System Survivability," p. 92.