
[Back]

[Index]

[Next]
 [Back] |
 [Index] |
 [Next] |
SECTION 5 - INTELLIGENCE SUPPORT
5.1 GENERAL Initially, the endurance UAV systems will collect only imagery intelligence (IMINT). They will be employed along with many other sources for analysis of the battlefield situation, and they are designed to augment other theater collection systems (such as the F-14 Tactical Airborne Reconnaissance Podded System (TARPS) and U-2 sensors). UAVs were developed as a cost-effective, low-risk, near-real-time RSTA platform in support of the JTF. Follow on collection packages could include SIGINT applications.
5.2 COLLECTION MANAGEMENT
5.2.1 Collection Platform Endurance UAVs primarily function as intelligence collection platforms and are not equipped with organic exploitation centers as we know them today. In the cycle of collection, exploitation, production, and dissemination, the UAV operates almost exclusively in the collection phase. It will be the responsibility of the JTF/J2 to determine the best means to exploit and disseminate the collected data to the forces he is tasked to support.
5.2.2 UAV Mission Prioritization It is the commandersí EEIs which generate intelligence collection missions (see Figure 5-1). As a collection platform, the missions of UAVs will be prioritized by the JTF/J2. For integrated collection capabilities, UAV operations will be coordinated with other collection platforms in theater such as JSTARS, U-2, or similar platforms. Requests for data will be handled within existing requests for information (RFI) architecture. RFIís will be passed to the JTF/J2 collection manager for coordination, prioritization, and tasking based upon the CINCís prioritized essential elements for information (EEI). The JFACC's allocation of airborne reconnaissance resources is based on the JFC's apportionment guidance. The J2 will work closely with the JTF/J3 for operational planning and the JFACC for sortie tasking to fulfill RFIs.
5.2.3 Priority Reporting For rapid I&W and re-targeting efforts, raw imagery or initial data will be turned around to the appropriate tactical commander as soon as it comes into the GCS, MCE, or designated exploitation site. Rapid turnaround guidance will be issued to the UAV detachment personnel by the JTF/J2. Furthermore, it will be the responsibility of the JFC, in coordination with the JTF/J2 and J3, to modify UAV tasking as required to support the JFC's mission objectives.
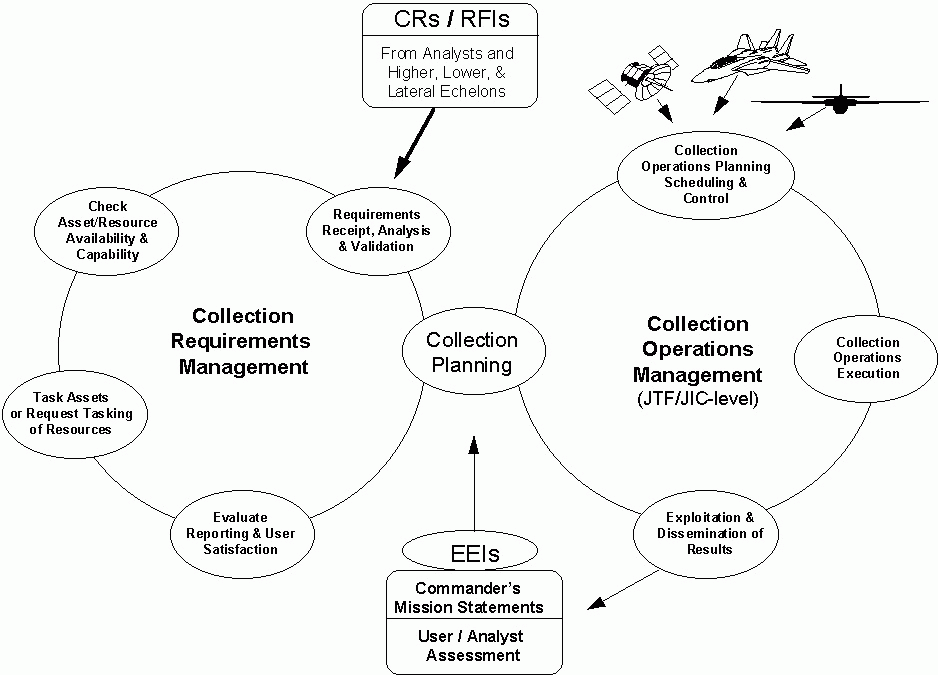
Figure 5-1: The Collection Management Process
5.2.4 UAVs must be able to operate from and link to command and control nodes. When combined with broad area search capabilities in SIGINT, as well as IMINT cueing, UAVs will provide the JTF with NRT targeting and enhanced situation awareness of the battlefield. UAV operations must be integrated into the greater family of reconnaissance and surveillance platforms available to the theater/operational commander. This will provide the breadth of range, altitude, dwell times, and collection footprints required for modern joint operations.
5.3 COLLECTION MANAGEMENT TASKING
5.3.1 Routine Tasking Tasking of imagery collection is accomplished through the established JTF Collection Management Process via the Air Tasking Order (ATO). Tasking comes in two formats; the ATO and execution cell ad hocs. The ATO, developed by the Combat Plans Division of the Air Operations Center (AOC), details the products required. It takes into account the limited exploitation capability of the GCS and the expanded production capability of the major intelligence production centers. It also accommodates the unique capabilities of both UAV systems. The ATO specifies types of products needed to fill user requests and when those products are required. It also directs the number and frequency of visits and reconnaissance, surveillance, and stare options based on the UAV system capability. Requested target types are also detailed and are important to mission planning and exploitation process. These types include point and area targets, as well as, lines of communications. The ATO may direct sensor use that can most appropriately capture the desired intelligence.
5.3.2 Ad Hoc Tasking Ad hoc tasking is developed by the execution cell in the Combat Operations Division of the AOC. Execution cell direction is supplemental to the ATO and it is used to modify UAV tasking to support changing mission objectives. This tasking may include time-sensitive changes to the ATO regarding UAV tasking or may require an entirely new UAV mission. It contains the same type of information included in the ATO. Due to the flexibility of UAV systems and their long mission duration, the air vehicles can be airborne in excess of an entire ATO cycle. The ground control station will likely receive some ad hoc tasking while the UAV is in flight. UAV liaison officers will normally be assigned at the JFACC level to provide information to requesters and to evaluate and filter ad hoc requests. These actions will, of course, be accomplished with JTF coordination and approval.
5.4 RECONNAISSANCE, SURVEILLANCE, & TARGET ACQUISITION (RSTA) Related to the UAV intelligence collection function is RSTA support for joint operations. RSTA provides information on enemy forces and installations. RSTA operations may require both continuous surveillance and as-required reconnaissance to provide timely I&W of a threat or impending attack. RSTA assets can also assist in monitoring or verifying compliance in international agreements. RSTA provides commanders with current data on enemy terrain, organization, infrastructure, and forces necessary for planning theater campaigns and major operations to include contingencies. It can also provide for adaptive, real-time planning for current operations, including monitoring enemy centers of gravity, conventional attack capabilities, enemy offensive and defensive positions, deception postures, and battle damage assessment (BDA).
5.4.1 Collections and RSTA functions will have an impact on the targeting cycle of JTF operations. The Predator UAV will have immediate and substantial applications for target development and BDA phases of the targeting cycle. To meet the challenge of mobile targets and rapidly changing enemy orders of battle, the Predatorís long dwell capability, as well as its near real-time down link and its naturally small radar signature, will greatly enhance the JTF's targeting efforts.
5.4.2 After collection of the target is accomplished, data recovery, rudimentary imagery exploitation, and dissemination will flow from the ground control station. If the ops tempo and EEI requirements dictate, the JTF/J-2 will determine if and at what level of effort forward deployed exploitation is required. The idea is to place the value added that exploitation provides in direct contact, whether physically or electronically, with the AOC/JFACC combat operations division who can best use the information to either retask the platform and collect more information, or use the intelligence to nominate a high value target. Voice reports will be made to the appropriate tactical and component commanders, staff elements, and the JTF/JIC. Selected images and video will be transmitted over the dedicated communications suite with continuous video being transmitted over commercial wideband satellite, if required. Video tapes will be passed to the JTF/JIC for analysis, reproduction, and further dissemination as directed by the JTF commander.
5.5 COLLECTION MANAGEMENT AUTOMATION Collection management for the Predator, DarkStar, and Global Hawk and other airborne reconnaissance systems includes an ability to electronically receive large numbers of tasks from a central Collection Management Authority (CMA), to share collection tasks with other RSTA assets, and to provide feedback to the CMA and using community. An automated collection management tool for the JFC, JFACC/AOC, and other Components is being developed under a separate program. The Joint Collection Management Tool (JCMT) has been designated by the Intelligence Systems Board (ISB) as the migration collection management tool to be used by all JFC collection managers. JCMT will be installed at all component collection management offices and may facilitate dynamic retasking of the UAV flight path and sensors.
5.6 SENSOR DATA LINKS The program objective of UAV sensor data links are full interoperability and compatibility with all vehicle ground control segments and all theater and national exploitation ground systems. Direct down links from UAV sensors to current (CARS, JSIPS, ETRAC, etc) and future Multi-source Intelligence Ground Systems (MIGS) is ACCís goal. The Global Hawk and DarkStar sensor links will be developed to satisfy these requirements while the Predator will migrate to meet requirements. Sensor data links will have the capability of untethered worldwide operations through the use of satellite communications between the aircraft and receiving ground system. It is envisioned that data rates of 50 Mb/s and greater are achievable via commercial satellites (INTELSAT, PANAMSAT, etc). The CDL will be utilized for sensor data links when UAV aircraft are within LOS of the receiving ground system. The Global Hawk and DarkStar will be developed to satisfy this requirement while the Predator will migrate towards CDL architectures.
5.7 EXPLOITATION The Air Force concept for exploiting UAV data is to take the data from the UAV or mission control element and perform exploitation in the UAV Exploitation Segment (UES) of the Air Force Common Imagery Ground/Surface System (CIGSS)/JASA compliant ground stations. For the Air Force, those ground stations are CARS and JSIPS, ultimately migrating to MIGS. The new upgrades to CARS and JSIPS will incorporate COTS based technology and system specific interfaces to allow tailored exploitation to be performed from each platform. As stated before, the UAV GCS and MCE are organic to UAV operations and have only a rudimentary exploitation capability. Exploitation within the UAV GCS and MCE is limited to spot reporting. First phase exploitation reporting, (i.e., Reconnaissance Exploitation Report (RECCEXREP), and Initial Photo Interpretation Report (IPIR)), would be accomplished at either CARS, JSIPS, or other theater designated exploitation facility, to include a Joint Intelligence Center (JIC). The unit tasked to perform UAV exploitation will disseminate the reports and imagery products through the secondary dissemination systems for the theater of operations. Second phase reporting and beyond would be accomplished by the Theater JIC or other national agency tasked with that responsibility. Exploitation of Global Hawk and Dark Star intelligence data will closely follow existing U-2 concepts since the mode of employment for those platforms will be very similar to the U-2. The critical aspect of exploitation is managing the volume of data that is collected and the man-Machine interface used to efficiently exploit the data in lockstep with the ops tempo.
5.7.1 PREDATOR EXPLOITATION. It is the supported theaterís responsibility to ensure Predator derived data is adequately exploited. As stated in para 5.4.2., the GCS is equipped with only rudimentary imagery exploitation capability. Once initial flight ops and collection tasking begins, the organic GCS equipment and manpower will be quickly task saturated. ACC is developing a plan under the MIGS migration concept for an exploitation cell organized under the existing Numbered Air Forces ground stations. This cell can forward deploy or collocate with the GCS based on the JFCís tasking. For specific details of the ACC UAV exploitation plan refer to the ACC Imagery Exploitation Plan for Endurance Unmanned Aerial Vehicles.
5.7.1.1 Predator Exploitation Cell Deployed. When deployed forward, the cellís foot print would be sized to accomplish SPOT reporting, RECCE EXREPS, and first phase readout if necessary. Unless otherwise tasked, all other detailed readouts (second and third phase) would be accomplished in the theaterís Joint Intelligence Center or potentially existing CARS and JSIPS ground stations. When forward deployed, the exploitation cell would receive the video feed from the GCS where a shift supervisor and up to seven imagery analysts would exploit, report, and disseminate the imagery. Functionally, there would exist one voice narrator, one database operator, and up to five exploiters per shift with two shifts scheduled per day. Once an image was grabbed, exploited and reported, dissemination would be directly to the JFC/JFACC Combat Ops Center or sent to an imagery server depending on EEI reporting criteria.
5.7.2 GLOBAL HAWK/DARK STAR EXPLOITATION. Imagery collected and transmitted by the two UAV systems (Tier II+ and Tier III- vehicles and ground stations) will be processed, formatted, and distributed for exploitation by current and planned (CIGSS compliant) exploitation facilities. Existing exploitation ground stations will receive the processed data and perform first phase exploitation reporting and dissemination.