

MANAGEMENT AND PLANNING
Management of security and counterintelligence has suffered from chronic problems since the creation of the Department of Energy in 1977. During the past decade, the mismatch between DOE’s security programs and the severity of the threats faced by the Department grew more pronounced. While the number of nations possessing, developing, or seeking weapons of mass destruction continued to rise, America’s reliance on foreign scientists and engineers dramatically increased, and warnings mounted about the espionage goals of other nations, DOE spending on safe-guards and security decreased by roughly one–third.1
The widening gap between the level of security and the severity of the threat resulted in cases where sensitive nuclear weapons information was certainly lost to espionage. In countless other instances, such information was left vulnerable to theft or duplication for long periods, and the extent to which these serious lapses may have damaged American security is incalculable. DOE’s failure to respond to warnings from its own analysts, much less independent sources, underscores the depth of its managerial weakness and inability to implement legitimate policies regarding well–founded threats.
A Sample of Security Issues MANAGEMENT AND PLANNINGPHYSICAL SECURITY
- Decentralized decisionmaking undermines consistency of policies.
- Lack of control for security budget has allowed diversion of funds to other priorities.
- Department leaders with little experience in security and intelligence.
- Lack of accountability.
PERSONNEL SECURITY CLEARANCES
- Training insufficient for some security personnel.
- Nuclear materials stored in aging buildings not designed for containment purposes.
- Recurring problems involving lost or stolen property.
- Poor management results in unnecessary training and purchasing costs.
PROTECTION OF CLASSIFIED INFORMATION
- Extended lags in obtaining clearances, reinvestigating backgrounds, and terminating clear-ance privileges for former employees.
- Some contractors not adequately investigated or subject to drug and substance abuse policies.
- Lack of uniform procedures and accurate data.
- Inadequate pre–employment screening.
- More clearances granted than necessary.
ACCOUNTING FOR NUCLEAR MATERIALS
- Poor labeling and tracking of computer media containing classified information.
- Problems with lax enforcement of password policies.
- Network, email, and Internet connections make transfer of large amounts of data easier.
FOREIGN VISITORS
- Chronic problems in devising and operating an accurate accounting system of tracking stocks and flows of nuclear materials.
- Weak systems for tracking visits and screening backgrounds of visiting scientists.
- Decentralization makes monitoring of discus-sions on sensitive topics difficult.
During the mid–1980s, the predominant concern of DOE officials was improving the physical security of the nuclear weapons laboratories and plants. Following a January 1983 report 2 that outlined vulnerabilities of the weapons labs to terrorism, the Department embarked on a five–year program of construction and purchases that would see its overall safeguards and security budget roughly double and its spending on upgrades nearly triple. Included was money for additional guards, security training, helicopters, fortified guard towers, vehicle barriers, emergency planning, and advanced alarm systems.3
Improving physical security in a wide array of nuclear weapons facilities whose replacement value was an estimated $100 billion 4, proved to be difficult. Reports through the late 1980s and early 1990s continued to highlight deficiencies in the management of physical security.
In the late 1980s, priorities began to shift somewhat. Listening devices were discovered in weapons–related facilities,5 and a 1990 study advised the Department leadership of an intensifying threat from foreign espionage. Less and less able to rely on the former Soviet Union to supply technology and resources, an increasing number of states embarked on campaigns to bridge the economic and technological gap with the United States by developing indigenous capabilities in high technology areas. The study noted that the freer movement of goods, services and information in a less hostile world “intensified the prospects and opportunities for espionage as missing pieces of critically needed information became more easily identified.”6
An intelligence report further highlighted the changing foreign threat to the labs by noting that “new threats are emerging from nontraditional adversaries who target issues key to U.S. national security. DOE facilities and personnel remain priority targets for hostile intelligence collection.”7 Anecdotal evidence corroborates, and intelligence assessments agree, that foreign powers stepped up targeting of DOE during the early 1990s. (See Classified Appendix) While this threat may have been taken seriously at the highest levels of the DOE, it was not uniform throughout the Department.
A former FBI senior official noted in discussions with the PFIAB investigative panel that DOE lab scientists during these years appeared naive about the level of sophistication of the nontraditional threat posed by Chinese intelligence collection. The trend in openness to for-eign visitors and visits does not indicate any sense of heightened wariness. A 1997 GAO report concluded that from mid–1988 to the mid–1990s, the number of foreign visitors to key weapons labs increased from 3,800 to 5,900 annually and sensitive country visitors increased from 500 to more than 1,600. 8 Meanwhile, the DOE budget for counterintelligence was in near–constant decline.
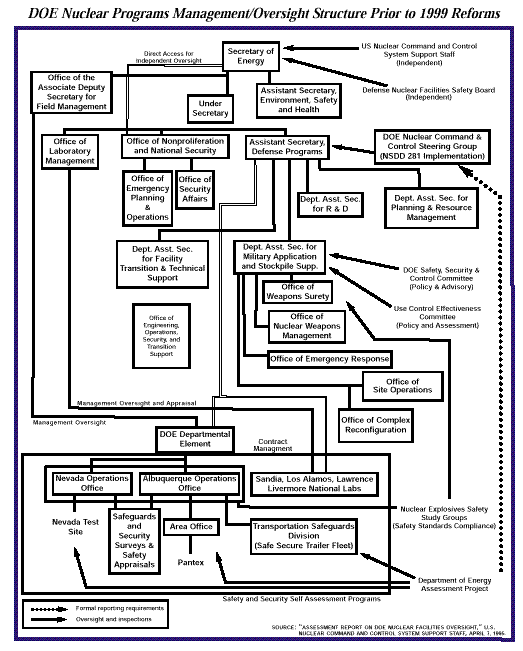
As noted in the previous chapter, federal officials in charge of oversight of nuclear weapons laboratories have historically allowed decisionmaking on basic aspects of security to be decentralized and diffuse. With their budget spread piecemeal throughout a number of offices, security and counterintelligence officials often found themselves with a weak voice in internal bureaucratic battles and an inability to muster the authority to accomplish its goals. Indeed, an excerpt from a history of the early years of the Atomic Energy Commission, reads much like recent studies:

More than 30 years later, decentralization still posed a problem for security managers. An internal DOE report in 1990 found that the Department lacked a comprehensive approach to management of threats and dissemination of information about them.10 A DOE annual report in 1992 found that security “has suffered from a lack of management focus and inconsistent pro-cedural execution throughout the DOE complex. The result is that personnel are seldom held responsible for their disregard, either intentional or unintentional, of security requirements." 11
The counterintelligence effort at DOE in the late 1980s and mid–1990s was in its infancy and grossly underfunded. Although the Department could have filled its gap in some areas, such as counterintelligence information, through cooperation with the broader intelligence community, PFIAB research and interviews indicate that DOE headquarters’ relationship with the FBI—the United States’ primary domestic CI organization—was strained at best.
DOE requested an FBI agent detailee in 1988 to assist in developing a CI program, but the agent found that DOE failed to provide management support or access to senior DOE decisionmakers. A formal relationship with the FBI was apparently not established until 1992: a Memorandum of Understanding between the FBI and DOE on respective responsibilities concerning the coordination and conduct of CI activities in the United States. However, in 1994 two FBI detailees assigned to DOE complained about their limited access and were pulled back to FBI because of a “lack of control of the CI program by DOE headquarters which resulted in futile attempts to better manage the issue of foreign visitors at the laboratories.”12
We asked a number of DOE officials to whom they report, to whom they were responsible. Invariably, their answer was: “It depends."
The haphazard assortment of agencies and missions folded into DOE has become so confusing as to become a running joke within the institution. In the course of the panel’s research and interviews, rare were the senior officials who expressed any sort of confidence in their understanding of the extent of the agency’s operations, facilities, or procedures. Time and again, PFIAB panel members posed the elementary questions to senior DOE officials. To whom do you report? To whom are you accountable? The answer, invariably, was: “It depends.”
DOE’s relationship with the broader intelligence community was not well–defined until the mid–1990s. Coordination between DOE CI elements and the broader intelligence community, according to a 1992 intelligence report, was hampered from the 1980s through the early 1990s by DOE managers’ inadequate understanding of the intelligence community.13 The Department did not become a core member of the National Counterintelligence Policy Board (established in 1994 under PDD-24) until 1997.
Even when the CI budget was expanded in the late–1990s, the expenditures fell short of the projected increases. In Fiscal Year 1997, for example, DOE’s CI budget was $3.7 million but the actual expenditures on CI were only two–thirds of that level, $2.3 million. Shortly before the 1997 GAO and FBI reports on DOE’s counterintelligence posture were issued, DOE began instituting changes to beef up its counterintelligence and foreign intelligence analytic capabilities.14
When DOE did devote its considerable resources to security, it too often faltered in implementation. A report to the Secretary in January 1994 noted “growing confusion within the Department with respect to Headquarters’ guidance for safeguards and security. At this time, there is no single office at Headquarters responsible for the safeguards and security program. Most recently, a number of program offices have substantially expanded their safeguards and security staff to office–size organizations. These multiple safeguards and security offices have resulted in duplication of guidance, unnecessary requests for information and clarification, and inefficient program execution. Unchecked, this counterproductive tendency threatens the success of the overall safeguards and security effort.”15
A 1996 DOE Inspector General report found that security personnel at the weapons programs had purchased and stockpiled far more firepower—ranging from handguns and rifles to submachine guns and grenade launchers—than could ever be used in an actual emergency. The Oak Ridge facilities had more than three weapons per armed security officer—on and off duty. Los Alamos National Laboratory had more than four.16
Foreign agents could probably not shoot their way into U.S. weapons laboratories. But they could apply for an access pass to walk in and strike up a conversation.
Around the same time, GAO security audits of the research laboratories at these sites found lax procedures for issuing access passes to secure areas, inadequate prescreening of the more than 1,500 visitors from sensitive countries that visited the weapons laboratories annually, and poor tracking of the content of discussions with foreign visitors. The implication: foreign agents could probably not shoot their way past the concertina wires and bolted doors to seize secrets from U.S. weapons laboratories, but they would not need to do so. They could probably apply for an access pass, walk in the front door, and strike up a conversation.
PHYSICAL SECURITY
The physical security of the Department of Energy’s weapons–related programs is roughly divided into two essential functions: tracking and control over the property and equipment within the weapons-related laboratories, and keeping unwarranted intruders out, often referred to as the realm of “guns, guards, and gates."
The general approach to security, of course, was defined by the emphasis on secrecy associated with nuclear weapons program during World War II. Los Alamos National Laboratory was created as a “closed city”—a community with a high degree of self-sufficiency, clearly defined and protected boundaries, and a minimum of ingress from and egress to the outer world. Although the community is no longer “closed,” the weapons laboratories at Los Alamos, like those at the other national laboratories, still retain formidable physical protections and barriers. In examining the history of the laboratories, the panel found only a few instances where an outsider could successfully penetrate the grounds of an operation by destruction of a physical safeguard or direct violent assault.
In visits to several of the weapons laboratories, the members of the Special Investigative Panel were impressed by the great amount of attention and investment devoted to perimeter control, weaponry, and security of building entrances and exits. Indeed, one cannot help but be struck by the forbidding and formidable garrison–type atmosphere that is prevalent at many of the facilities: barbed wire, chain–link fences, electronic sensors, and surveillance cameras. Further, the panel recognizes that the labs themselves have developed and produced some of the most sophisticated technical security devices in the world. Nonetheless, DOE reports and external reviews since at least 1984 have continued to raise concerns about aging security systems.17
Clearances to secure DOE areas have been granted simply for convenience, such as to reduce the length of an employee’s walk from the car to the office each morning.
Management of the secure environments at the laboratories has posed more serious problems. As noted earlier, DOE may be spending too much money in some areas, buying more weapons than could conceivably be used in an emergency situation. In other cases, it may be spending too little. Budget cuts in the early and mid-1990s led to 40 to 50 percent declines in officer strength and over-reliance on local law enforcement. Resources became so low that normal protective force operations required “the use of overtime scheduling to accomplish routine site protection.”18 GAO has found an assortment of problems at Los Alamos over the past decade: security personnel failed basic tests in such tasks as firing weapons, using a baton, or handcuffing a suspect, and inaccurate and incomplete records were kept on security training.19 Other DOE facilities have had substantial problems in management of physical property.
DOE had begun to consolidate its growing stockpile of sensitive nuclear material by 1992, but a 1997 DOE report to the Secretary found that significant quantities of the material “remain in aging buildings and structures, ranging in age from 12 to 50 years, that were never intended for use as storage facilities for extended periods.”23
SCREENING AND MONITORING OF PERSONNEL
Insider threats to security have been a chronic problem at the nation’s weapons laboratories. From the earliest years, the importance of the labs’ missions and their decentralized structure have had an uneasy coexistence with the need for thorough background investigations of researchers and personnel needing access to sensitive areas and information.
In 1947, the incoming director of security for the AEC was greeted with a backlog of more than 13,000 background investigations and a process where clearances had been dispersed to field offices that operated with few formal guidelines.24
Forty years later, GAO found that the backlog of personnel security investigations had increased more than nine-fold, to more than 120,000. Moreover, many clearances recorded as valid in the Department’s records should have been terminated years before.25
Even after DOE discovered listening devices in some of its weapons laboratories, security audits found that thousands of “Q" clearances were being given to inappropriate personnel.26
The research of the PFIAB panel found that problems with personnel security clearances, while mitigated in some aspects, have persisted to an alarming degree. From the mid–1980s through the mid–1990s, the DOE Inspector General repeatedly warned Department officials that personnel were receiving clearances that were much higher than warranted and that outdated clearances were not being withdrawn on a timely basis. The issue became more urgent with the discovery of a clandestine surveillance device at a nuclear facility.27
But problems persisted. DOE Inspector General reports in 1990 and 1991 found that one of the weapons laboratories had granted “Q” clearances (which provide access to U.S. government nuclear weapons data) to more than 2,000 employees who did not need access to classified information.28 A 1992 report to the Secretary of Energy noted that “DOE grants clearances requested by its three major defense program sponsored labs based on lab policies to clear all employees regardless of whether actual access to classified interests is required for job performance.”29
Three years later, a review of personnel security informed the Secretary there were “individuals who held security clearances for convenience only and limited security clearances to those individuals requiring direct access to classified matter or [special nuclear materials] to perform official duties.”30
More recent evidence is no more reassuring. A counterintelligence investigation at a nuclear facility discovered that the subject of an inquiry had been granted a “Q" clearance simply to avoid the delay caused by the normal processing of a visit.31 That same year, an illegal telephone wiretap was discovered at the same lab. The employee who installed it confessed, but was not prosecuted by the government.32
PROTECTION OF CLASSIFIED AND SENSITIVE INFORMATION
Two vulnerabilities regarding classified and sensitive information at DOE have recurred repeatedly throughout the past 20 years: inappropriate release of classified information, either directly through inadvertence or indirectly through improper declassification; and the increasing mobility of classified and sensitive information through electronic media, such as computers.
As computers have progressed from the large mainframes of the 1950s and 1960s to desktop models in the 1980s and decentralized networks in the 1990s, it has become progressively easier for individuals to retrieve and transport large amounts of data from one location to another. This has presented an obvious problem for secure environments. GAO found in 1991 that DOE inspections revealed more than 220 security weaknesses in computer systems across 16 facilities. Examples included a lack of management plans, inadequate access controls, and failures to test for compliance with security procedures.33
As a 1996 DOE report to the President said, “adversaries no longer have to scale a fence, defeat sensors, or bypass armed guards to steal nuclear or leading–edge ‘know-how’ or to shut down our critical infrastructure. They merely have to defeat the less ominous obstacles of cyber–defense.”34
Computer systems at some DOE facilities were so easy to access that even Department analysts likened them to “automatic teller machines, [allowing] unauthorized withdrawals at our nation’s expense."
DOE’s cyber–defenses were, in fact, found to be “less ominous obstacles." In 1994, an internal DOE review found that despite security improvement “users of unclassified computers continue to compromise classified information due to ongoing inadequacies in user awareness training, adherence to procedures, enforcement of security policies, and DOE and [lab] line management oversight."35 Also in 1994, a report to the Energy Secretary cited five areas of concern: “failure to properly accredit systems processing classified information, lack of controls to provide access authorities and proper password management; no configuration management; improper labeling of magnetic media; and failure to perform management reviews."36
Apparently, the warnings were to no avail. A year later, the annual report to the Secretary noted: “Overall, findings and surveys, much like last year, continue to reflect deficiencies in self–inspections and procedural requirements or inappropriate or inadequate site guidance … In the area of classified matter protection and control, like last year, marking, accountability, protection, and storage deficiencies are most numerous."37
Some reports made extra efforts to puncture through the fog of bureaucratic language. A 1995 report to the President said: “By placing sensitive information on information systems, we increase the likelihood that inimicable interests, external and internal, will treat those systems as virtual automatic teller machines, making unauthorized withdrawals at our nation’s expenses." Indeed, a report found security breaches at one of the major weapons facility in which documents with unclassified but sensitive information “were found to be stored on systems that were readily accessible to anyone with Internet access."38 In other instances, personnel were found to be sending classified information to outsiders via an unclassified email system.39
Ahead of its Time In 1986, the DOE Office of Safeguards and Quality Assessment issued an inspection report on a weapons lab that warned of shortcomings in computer security and noted that the “ability of [a] user to deliberately declassify a classified file without detection and move classified information from the secure partition to the open partition can be made available to any authorized user either on or off site."40 The warning turned out to be on the mark. In April of this year, Energy Secretary Bill Richardson issued a statement: “While I cannot comment on the specifics, I can confirm that classified nuclear weapons computer codes at Los Alamos were transferred to an unclassified computer system. This kind of egregious security breach is absolutely unacceptable ... ."
Even though the hard evidence points to only sporadic penetrations of the labs by foreign intelligence services (see classified appendix), volumes of sensitive and classified information may have been lost over the years—via discarded or purloined documents; uninformed and often improperly vetted employees, and a maze of uncontrolled computer links. In one recent case discovered by PFIAB, lab officials initially refused to rectify a security vulnerability because “no probability is assigned to [a loss of sensitive information], just the allegation that it is possible.”41
As recent as last year’s annual DOE report to the President, security analysts were finding “numerous incidents of classified information being placed on unclassified systems, includ-ing several since the development of a corrective action plan in July 1998.”42
TRACKING OF NUCLEAR MATERIALS: HOW MUCH MUF?
MUF stands for “materials unaccounted for,” the official term used until the late 1970s for discrepancies in the amount of nuclear materials that can be physically located in inventory versus the amount noted in Department records. MUF (now termed with the more politic phrase “inventory differences”) has been a recurring concern—and debate—in the nuclear research field since the beginning. The question at the center of the debate: if large quantities of nuclear material are impossible to measure with absolute precision, what constitutes a significant loss?
As in many questions, the answer depends on whom you ask. Officials of nuclear research facilities have argued that the scale and complexity of the processing and handling of nuclear material inevitably result in losses that are detectable but inconsequential. Outside observers have tended to be less sanguine about what constitutes a significant loss from a security standpoint. In 1976, the General Accounting Office reported that the Nuclear Regulatory Commission and the Energy Research and Development Administration (DOE’s predecessor) could not account for 8,000 pounds of highly enriched uranium and plutonium. Officials of the two agencies responded that part of the accounting discrepancy could be ascribed to the statistical margin of error in their measuring equipment, the rest was probably dregs created during processing and left in machinery parts, wiping cloths, and scrap items.43
Critics of the agencies have pointed out that thieves could easily use the variance in statistical measures to cover their tracks, stealing an increment during each measuring period that falls just within the margin of error. They have also pointed out that if Department records are not accurate, it is impossible for anyone to estimate the stock of nuclear material at any given point, much less the difference between two levels as it proceeds from one stage of the nuclear cycle to the next. In December 1994, the Department released updated figures for the cumulative amount of MUF or inventory difference for the 50-year period beginning in 1944. The cumulative figure: 6,174 pounds. Of that amount, a cumulative total of about 10 pounds was ascribed to “accidental losses" and “approved write-offs."44
GAO has continued to highlight the issue since DOE has become the steward of the nation’s nuclear weapons laboratories. GAO published a report in 1991 criticizing the insufficiency of the Department’s measuring systems and handling procedures 45 ; in 1994, criticizing its methods of tracking exported nuclear material;46 and in 1995, for installing a new system that was allegedly faulty.47
Even if accurate systems of measurement and accounting had been in place, it is not clear whether DOE officials would have been qualified to manage them effectively. A 1995 report to the President warned that “severe budget reductions, diminished technical resources, increased responsibilities, and reduced mission training ... have undermined protection of special nuclear material and restricted data."48
Last year, a report by an external review panel found “a lack of nuclear physical security expertise at all levels in the oversight process; ad hoc structuring of safeguards and security functions throughout the Department, and placement of oversight functions in positions which constrain their effectiveness."49
The dispute over the accuracy of nuclear measurements, of course, is beyond the technical capabilities of this panel to resolve. But the panel members do believe that its persistence and the low priority given to the issue relative to other DOE scientific goals is indicative of the institutional attitude that DOE has had toward security: nonscientists have a poor understanding of all things nuclear, so their judgments about acceptable levels of risk are suspect prima facie.
FOREIGN VISITORS AND ASSIGNMENTS PROGRAM
True to the tradition of international partnership molded by the experiences of the Manhattan Project, the weapons labs have remained a reservoir of the best international scientific talent. Recent examples abound: a supercomputing team from Oak Ridge National Lab, made up of three PRC citizens and a Hungarian, recently won the Gordon Bell Prize; a Bulgarian and a Canadian, both world-class scientists, are helping Lawrence Livermore National Lab solve problems in fluid dynamics; a Spanish scientist, also at Livermore, is collaborating with colleagues on laser propagation.
But for more than a decade, the increasing prominence of foreign visitors in the weapons labs has increased concern about security risks. The PFIAB panel found that as early as 1985, the DCI raised concerns about the foreign visitors’ program with the Energy Secretary. A year later, researchers conducting internal DOE review could find only scant data on the number and composition of foreign nationals at the weapons labs. Although intelligence officials drafted suggestions for DOE’s foreign visitor control program, PFIAB found little evidence of reform efforts until the tenure of Secretary Watkins.
A 1988 GAO report cited DOE for failing “to obtain timely and adequate information on for-eign visitors before allowing them access to the laboratories." The GAO found three cases where DOE allowed visitors with questionable backgrounds—possible foreign agents—access to the labs. In addition, the GAO found that about 10 percent of 637 visitors from sensitive countries were associated with foreign organizations suspected of conducting nuclear weapons activities but DOE did not request background data on them prior to their visit. DOE also had not conducted its own review of the visit and assignment program at the weapons labs despite the DOE requirement to conduct audits or reviews at a minimum of every five years. Moreover, GAO reported that few post–visit or host reports required by DOE Order 12402 were submitted within 30 days of the visitors’ departure and some were never completed.50
The following year, DOE revised its foreign visitor policy and commissioned an external study on the extent and significance of the foreign visitor problem. DOE’s effort to track and vet visitors, however, still lagged well behind the expansion of the visitor program, allowing foreigners with suspicious backgrounds to gain access to weapons facilities. A study pub-lished in June 1990 indicated DOE had a “crippling lack of essential data, most notably no centralized, retrievable listing of foreign national visitors to government facilities." 51
By September, 1992, DOE had instituted Visitor Assignment Management System (VAMS) databases, used to track visitors and assignees requesting to visit DOE. The system, however, failed to provide links between the labs that could be used for CI analysis and cross-checking of prospective visitors. Moreover, labs frequently did not even use the database and failed to enter visitor information. Instead, each lab developed its own computer program independently.
Reviews of security determined that, despite an increase of more than 50 percent in foreign visits to the labs from the mid–1980s to the mid–1990s, DOE controls on foreign visitors actually weakened in two critical areas: screening for visitors that may pose security risks, and monitoring the content of discussions that might touch on classified information.
In 1994, DOE headquarters delegated greater authority to approve nonsensitive country visitors to the laboratories, approving a partial exception for Los Alamos and Sandia National Laboratories to forego background checks to help “reduce costs and processing backlogs." This resulted in almost automatic approval of some foreign visitors and fewer background checks. The FBI and GAO subsequently found that “questionable visitors, including suspected foreign intelligence agents, had access to the laboratories without DOE and/or laboratory officials’ advance knowledge of the visitors’ backgrounds."52
Changes in records checks over the past decade also made it easier for individuals from sensitive countries to gain access to the laboratories. In 1988, for example, all visitors from Communist countries required records checks regardless of the purpose of the visit. By 1996, records checks were only required for visitors from sensitive countries who visited secure areas or discussed sensitive subjects.
An internal DOE task force in 1996 determined that the Department’s definitions of sensitive topics were not specific enough to be useful. It directed the DOE office of intelligence to develop a new methodology for defining sensitive topics, but did not set a due date. The 1996 group also called for a Deputy Secretary–level review of foreign visits and assignments to be completed by June 1997. 53 The PFIAB panel found no evidence to suggest that these tasks were accomplished.
In 1997, GAO found that DOE lacked clear criteria for identifying visits that involve sensitive subjects, U.S. scientists may have discussed sensitive subjects with foreign nationals without DOE’s knowledge or approval; and the Department’s counterintelligence program had failed to produce comprehensive threat assessments that would identify likely facilities, technologies, and programs targeted by foreign intelligence.a href="#54">54 The study found that records checks were still not being conducted regularly on foreign visitors from sensitive countries. 55 Last year, 7,600 foreign scientists paid visits to the weapons labs.56 Of that total, about 34 percent were from countries that are designated “sensitive” by the Department of Energy—meaning they represent a hostile intelligence threat. The GAO reported last year that foreign nationals had been allowed after-hours and unescorted access to buildings.57


2. Classified DOE Report.
3. Classified DOE Report.
4. Classified DOE Report.
5. Classified DOE Report.
6. DOE, Office of Counterintelligence, “The Foreign Intelligence Threat to Department of Energy Personnel, Facilities and Research, Summary Report,” August 1990.
7. Classified U.S. Government report.
8. GAO/RCED-97-229, “Department of Energy: DOE Needs to Improve Controls Over Foreign Visitors to Weapons Laboratories,” September 25, 1997.
9. Hewlett, Richard G. and Francis Duncan, “Atomic Shield: A History of the U.S. Atomic Energy Commission,” May 1969.
10. Classified DOE report.
11. DOE, “Office of Safeguards and Security, Report to the Secretary: Status of Safeguards and Security,” February 1993
12. Classified FBI document.
13. Classified U.S. Government report.
14. Classified DOE report.
15. DOE, “Office of Safeguards and Security, Status of Safeguards and Security, Fiscal Year 1993,” January 1994 (U)
16. DOE/IG-385, “Special Audit Report on the Department of Energy’s Arms and Military-Type Equipment,” February 1, 1996
17. Classified DOE report.
18. DOE, “Annual Report to the President on the Status of Safeguards and Security at Domestic Nuclear Weapons Facilities,” September 1996
19. GAO/RCED-91-12, “Nuclear Safety: Potential Security Weaknesses at Los Alamos and Other DOE Facilities,” October 1990 (U) and GAO/RCED-92-39, “Nuclear Security: Safeguards and Security Weaknesses at DOE’s Weapons Facilities,” December 13, 1991
20. GAO/RCED-90-122, “Nuclear Security: DOE Oversight of Livermore’s Property Management System is Inadequate,” April 18, 1990
21. GAO/”Key Factors Underlying Security Problems at DOE Facilities,” (Statement of Victor S. Rezendes, Director, Energy, Resources and Science Issues, Resources, Community, and Economic Development Division, GAO, in testimony before the Subcommittee on Oversight and Investigations, Committee on Commerce, House of Representatives), April 20, 1999
22. GAO/”Key Factors Underlying Security Problems at DOE Facilities,” (Statement of Victor S. Rezendes, Director, Energy, Resources and Science Issues, Resources, Community, and Economic Development Division, GAO, in testimony before the Subcommittee on Oversight and Investigations, Committee on Commerce, House of Representatives), April 20, 1999
23. Classified DOE report.
24. Hewlett, Richard G. and Francis Duncan, “Atomic Shield, A History of the United States Atomic Energy Commission,” May 1969
25. GAO/RCED-89-34, “Nuclear Security: DOE Actions to Improve the Personnel Clearance Program,” November 9, 1988
26. DOE/IG/WR-O-90-02, “Nevada Operations Office Oversight of Management and Operating Contractor Security Clearances," March 1990;
27. Classified DOE report.
28. DOE/IG/WR-B-91-08, “Review of Contractor’s Personnel Security Clearances at DOE Field Office, Albuquerque," September 1991.
29. DOE, “Office of Safeguards and Security, Report to the Secretary: Status of Safeguards and Security," February 1993
30. DOE, “Office of Safeguards and Security, Status of Safeguards and Security, Fiscal Year 1995," January 1996
31. Classified U.S. Government report.
32. Classified DOE report.
33. GAO/RCED-92-39, “Nuclear Security: Safeguards and Security Weaknesses at DOE Weapons Facilities," December 13, 1991.
34. Classified DOE report.
35. Classified DOE report.
36. DOE, “Office of Safeguards and Security, Status of Safeguards and Security, Fiscal Year 1993," January 1994 (U)
37. DOE, “Office of Safeguards and Security, Status of Safeguards and Security, Fiscal Year 1994," January 1995 (U)
38. Classified DOE report.
39. Classified DOE report.
40. Classified DOE report.
41. Classified DOE report.
42. Classified DOE report.
43. New York Times, “Abstract," August 5, 1977
44. DOE, “Plutonium: The First 50 Years. United States Plutonium Production, Acquisition, and Utilization from 1944 Through 1994
45. GAO/RCED-92-39, “Nuclear Security: Safeguards and Security Weaknesses at DOE’s Weapons Facilities," December 13, 1991
46. GAO/RCED/AIMD-95-5, “Nuclear Nonproliferation: U.S. International Nuclear Materials Tracking Capabilities are Limited," December 27, 1994
47. GAO/AIMD-95-165, “Department of Energy: Poor Management of Nuclear Materials Tracking Capabilities Are Limited," August 3, 1995
48. DOE, “Office of Safeguards and Security, Status of Safeguards and Security, Fiscal Year 1995," January 1996
49. U.S. Nuclear Command and Control System Support Staff, “Assessment Report: Department of Energy Nuclear Weapons-Related Security Oversight Process," March 1998
50. GAO/RCED-89-31, “Major Weaknesses in Foreign Visitor Controls at Weapons Laboratories," October 11, 1988
51. Classified U.S. Goverment report.
52. GAO/RCED-97-229, “Department of Energy: DOE Needs to Improve Controls Over Foreign Visitors to Weapons Laboratories," September 25, 1997
53. Classified DOE report.
54. GAO/RCED-97-229, “Department of Energy: DOE Needs to Improve Controls Over Foreign Visitors to Weapons Laboratories," September 25, 1997
55. GAO/RCED-97-229, “Department of Energy: DOE Needs to Improve Controls Over Foreign Visitors to Weapons Laboratories," September 25, 1997
56. DOE, “Response to the Cox Committee Report: The Benefits of Department of Energy International Scientific and Technical Exchange Programs," April 1999.
57. GAO/RCED-99-19, “Department of Energy: Problems in DOE’s Foreign Visitors Program Persist," October 6, 1998.