In a democratic society, the citizens both choose their governors and are the governed. This dual role of the public has produced a tension between the need for secrecy and the need to keep government accountable. Broad access to information is critical for government officials to shape well-reasoned policies and for the public to monitor those it has elected to act on its behalf. However, expansion of the Government's national security bureaucracy since the end of World War II and the closed environment in which it has operated have outpaced attempts by the Congress and the public to oversee that bureaucracy's activities.
As Chapter II made clear, core secrets do exist that need the highest level of protection. There is widespread agreement, even by those who most vigorously support broad declassification, that there are many types of government information that will always require zealous protection--for example, sources whose exposure would jeopardize human life; signals intelligence or imagery, the loss of which would profoundly hinder the capability to collect data; information that would assist chemical, biological, or nuclear proliferators; and details about special military capabilities. However, these types of information are only a portion of the universe of information that now is classified. This chapter focuses on the rest of the classified world, including policy, analysis, factual, and historical data, and how to ensure its public availability when it no longer needs protection.
Ensuring public access to information that does not require protection is a key to striking the balance between secrecy and the openness that is central to the proper functioning of this country's political institutions. There has been a gradual but encouraging shift in recent years on the part of many agencies that use classified information toward declassifying and releasing more of that information to the public. Some agencies realize that better relations with the public can grow from easier access to agency records that no longer need protection. Openness can also demonstrate to the world, especially newly-emerging democracies that are beginning to open their own countries' archives, the strength of our free institutions.
Other benefits flow from moving information that no longer needs protection out of the classification system. Broad access to information promotes better decisions. It permits public understanding of the activities of government and promotes more informed debate and accountability. It increases the Government's ability to respond to criticism and justify its actions to the public. It makes possible the free exchange of scientific information and encourages new discoveries that foster economic growth. By allowing a better understanding of our history, it provides opportunities to learn lessons from the past, and it makes it easier to quash unfounded speculation about the Government's past actions. Reducing the amount of information in the classification system allows for better management and cost controls of that system and increases respect for the information that needs to stay protected. Greater access thus provides ground in which the public's faith in its government can flourish.
Chapter II addressed the problem of overclassification of information at the beginning of its life cycle. This chapter focuses on what happens at the end of that life cycle, discussing recent attempts to provide more public access as well as the barriers that persist for effective ways to declassify. It makes recommendations designed to ensure that, in making declassification decisions, agencies use resources efficiently, apply accurate data in making judgments about release, and interact effectively with the public. The Commission supports the appropriate protection of truly sensitive information while establishing wiser ways to handle the rest. In short, this chapter is about managing declassification consistent with principles of good government.
In recent years, agency task forces have searched for, reviewed, and declassified large volumes of records on issues involving past government actions about which there is great public interest. After passage of the President John F. Kennedy Assassination Records Collection Act of 1992 and the establishment of a Review Board to monitor implementation of the law, agencies undertook intensive searches for and reviews of relevant records. The result has been to make publicly available over three million pages of previously secret records related to that key event.
In response to the creation of a Senate select committee to investigate the fate of Americans who were prisoners of war or missing in action in past military conflicts, the Department of Defense (DoD) in 1991 established a Central Documentation Office that began a process of coordinating broad searches, declassification reviews, and public releases of records. In 1993, the DoD also established a task force to assist the Gulf War Illnesses Advisory Committee by locating, declassifying, and posting on an Internet site records that might help explain the physical ailments reported by veterans of the Persian Gulf War. Some critics have charged that neither of these two projects has yet released all relevant records. The Gulf War project also came under scrutiny when intelligence reports that had been placed on-line were removed but later reinstated after their removal drew complaints. Nevertheless, both have succeeded in making much more declassified information available to the public than would otherwise be the case.
Agencies have shown initiative in providing public access in other ways. In recent years, the State Department has worked closely with a statutorily created historical advisory committee to more regularly review, declassify, and publish records on key foreign policy events for its Foreign Relations of the United States series. In 1996, the Defense Department and the Central Intelligence Agency (CIA) each established formal working relationships with advisory groups of prominent scholars to obtain advice on their declassification efforts, although it is not yet clear what the continuing impact these citizen committees ultimately will have on those agencies' public access policies.
In addition, the Department of Energy (DoE) in 1993 began an "Openness Initiative" to increase public confidence in the DoE and to make more declassified information publicly available. The DoE also established an advisory committee in response to reports of government-sponsored human radiation experiments. In 1995, that advisory committee issued a comprehensive report and assembled over 1.6 million pages of relevant records from numerous sources, most of which had not been easily accessible before; these records are now available at the National Archives and on the Internet as well. Another consequence of the DoE's attempts at greater openness was that an environmental group that had been on the verge of suing the Department (and that had sued it in the past) decided to refrain from legal action and give the Department additional time to respond to the problems it had identified.
Skepticism about agency motives can also arise from the way in which an agency declassifies and publicly disseminates information. When agencies selectively declassify only a handful of records on an event but do not make entire files available, it can lead to the impression that the Government is more interested in self-justification of its actions than in a full airing of the historical record.
Secrecy is a tool that can help government officials reach policy goals, but too often a secret can become self-perpetuating even after the reason for maintaining it has been achieved or abandoned. Solving the problem of the growing backlog of classified documents, discussed in more detail below, requires the acceptance of declassification as a routine government activity. The dictionary defines "classify" as simply "to organize or arrange according to class or category." Thus, providing public access to government records that no longer need protection, or "declassifying," means finding sensible, cost-effective, and routine ways to separate the categories of materials no longer warranting protection from those needing to stay secret. One historian active in recent debates about the appropriate boundaries of government secrecy has observed that "the whole process of security classification itself is a Cold War artifact; we need to distinguish what of the process can be jettisoned and what we need to keep."4
Thus, applying risk management principles to declassification is closely tied to the type of information involved; not all classified information should be treated alike when it is being considered for release. For example, information that would encourage nuclear proliferation needs careful protection. However, a decades-old report analyzing a foreign country's political situation or in which policymakers are advised of possible options may not pose any risk to national security from public release. Evaluation of the potential harm from release based on current and realistic risk assessments is critical to managing declassification well.
Despite some successes in increasing public access, the vast majority of classified information, including many very old records that might provide key insights into our nation's history, remains inaccessible to the public. Sensible, cost-effective processes do not currently exist to distinguish between the material that would and that would not harm national security if it were released. Now, it simply is easier to classify information and keep it classified than to move it out of the system when it no longer requires protection.
Persistent declassification problems include:
Ensuring proper and timely public access to still-classified government records requires focus, discipline, and good records management. These fundamentals are particularly important given the impact of new technologies on the creation of records, making it all the more critical that the Government find sensible and cost-effective ways to act in this area. As some in government already recognize, the basic challenge is to simultaneously manage two transitions: from paper-based to electronic records systems, and from performing declassification on an ad hoc basis to doing so in systematic, efficient, and cost-effective ways.6 Recognizing these challenges is the first step but, as described below, most agencies have not yet begun to adequately address them.
However, when agencies perceive that implementation of these key elements is largely optional, experience has shown that the goal of promoting more effective declassification is not achieved. For example, Executive Order 12356 instructed that rather than assigning a date or event for declassification at the time a record was created, a new marking--"Originating Agency's Determination Required"--could be used. When OADR was applied to a record, no scheduled deadlines for declassification review applied. OADR soon became the default marking that classifiers across the Government used as a declassification instruction.7 By 1992, 95 percent of all documents classified that year were marked OADR.8 Executive Order 12356 also allowed, but did not require, systematic declassification. Agencies thus devoted few resources to it, contributing to a vast growth in the amount of classified records.
Table 1: Provisions in Past Executive Orders Promoting Public Access to Information Executive Orders PROVISIONS 10501 10964 11652 12065 12356 12958 Declassification date or event on document at time of classification YES YES YES YES Optional YES Portion marking of paragraphs in a document NO NO YES YES YES YES Balancing test of the public's right to know and need to protect NO NO NO YES NO NO Appeals or oversight structure YES NO YES YES YES YES Scheduled automatic declassification review or release NO YES YES YES NO YES Formal mandatory review procedures NO NO YES YES YES YES
Although agencies were required to submit declassification plans and proposals for the file series they intended to exempt from automatic release, not all submitted timely plans or provided many details about how they intend to implement the Order.
Moreover, without feedback on those plans from the National Security Council or the Information Security Oversight Office (to which the plans were submitted), agencies have proceeded to implement those plans as originally drafted even if they might not fully reflect the letter or spirit of the Order.
In addition, the Federal Bureau of Investigation (FBI) and the DoE received waivers from compliance with the automatic declassification provisions of the Order in exchange for their assurances that they would, on an expedited basis, undertake comprehensive reviews for possible release of their older records that are not classified pursuant to an executive order but nevertheless are unavailable to the public. However, to date no FBI records have been released under this agreement. The waiver for the FBI was based on its claim that privacy interests preclude public access to its older law enforcement records (although the Privacy Act does not apply to records that have been deposited at the National Archives, which is where many FBI records over 25 years old reside). The DoE's waiver was based on the fact that most of its records are not classified under an executive order but separately under the Atomic Energy Act. Thus, the FBI and the DoE have numerous records in which the public is interested that are not subject to the declassification provisions of this Order at all.
Declassification under the Order in other agencies is occurring slowly. Many agencies have chosen to start with their least sensitive records. Others are reviewing and declassifying their most sensitive documents first, reasoning that if the Order's five-year deadline is not met, the remaining records potentially subject to automatic declassification will present a lower risk of damage upon release. One year after the Order took effect, certain agencies had done almost nothing to comply with its declassification provisions. On the other hand, within a year after the Order was issued the Commerce Department already had reviewed and released nearly all of its classified records subject to the Order (although its situation is not completely comparable to that of other agencies subject to the Order because it classifies very little information in the first place).
The President's stated intent when signing Executive Order 12958 was that its provisions should result in "large-scale declassification [that] won't be dependent on the availability of individuals to conduct a line-by-line review." Nevertheless, most agencies indicate that they intend to implement the Order by doing the costly line-by-line review (discussed more fully later in this chapter) that the Order sought to avoid. This approach is driven in part by the discovery that file descriptions only vaguely or sometimes incorrectly describe the contents and their classification levels. It also is being used because line-by-line review is the only way most agencies have ever processed records for public release.
The primary experience most agencies have had with declassification has been through conducting line-by-line reviews of records in response to FOIA requests. The FOIA establishes a statutory right for any person to obtain copies of Federal agency records and is the primary vehicle for the public to obtain access to government records. Thirty years after its enactment, the FOIA's continuing significance and vitality stem from the legally enforceable rights it creates for requesters and the presumption of release that it establishes, limited only by the exemptions it provides that agencies may invoke to deny access.
However, requesters and agencies alike find the FOIA an imperfect tool for obtaining the declassification of records. Effective use of the FOIA requires considerable patience and, often, significant financial and legal resources. Problems posed by the FOIA's current use as a primary mechanism for declassifying records include:
In enacting the Electronic Freedom of Information Amendments (EFOIA), signed into law on October 2, 1996, the Congress and the President took a step toward improving agency responsiveness to FOIA requests. These amendments clarify that the Act applies to records in electronic as well as paper format, while also giving agencies relief from some of the Act's administrative requirements. In the words of one of the Act's sponsors, the EFOIA is intended to "deliver common-sense efficiency and government accountability to the American people."10 Still, because of the sheer volume of classified material that has accumulated in agencies over the years, these recent amendments will not wholly cure the FOIA's shortcomings for public access to classified records.
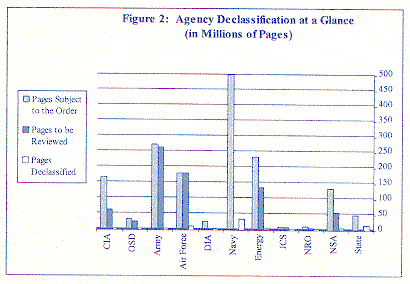
As Figure 2 illustrates, based on data provided by individual agencies, the Commission estimates that there are over 1.5 billion pages of records 25 years old and older still classified by the Federal Government.12 Of this amount, agencies currently plan to review less than one-half--approximately 719 million pages--under the automatic declassification provisions of the Order, meaning that agencies are exempting from automatic declassification over three quarters of a billion pages. A little over a year after Executive Order 12958 took effect, agencies had declassified about 57 million pages, less than one-tenth of what they had identified for review. Unless current agency plans change, public access to the hundreds of millions of exempted pages will occur either through the systematic declassification procedures required by Executive Order 12958 (which have yet to be established in most agencies), or through the current but inadequate system of individual requests filed under the Order's mandatory review process or the FOIA.

Although these numbers seem overwhelming, it is important to understand that they are only estimates based on initial surveys of the numbers of file boxes that appear to contain classified records. For example, unclassified records often are commingled with classified material when stored, or an entire box may be marked as classified even if it contains only a single classified document. In addition, many classified documents have numerous attachments that are themselves unclassified. Many older records are duplicates of others: copies may already have been declassified. Some file boxes turn out to be partly empty. Some boxes contain other items, such as shoes, plastic bags, office supplies, and drug samples. In one case, a file box was found to contain a mock hand grenade used for military exercises. While the review task facing agencies under Executive Order 12958 is significant, these insights into how records actually are stored indicate that agency estimates may overstate the amount of permanent records that needs to be reviewed. Thus, the ultimate declassification burden on agencies may turn out to be less onerous than the numbers currently suggest.
However, some who regularly create and use classified records understand that there is a life cycle for such materials; these officials acknowledge that there is a predictable "expiration date" for much classified information that can be determined when the information is created, based on experience with similar types of data. For example, certain portions of military plans requiring a high level of secrecy before an operation takes place often can be declassified shortly afterward because those elements of the plan have become common knowledge. Similarly, much information dealing with foreign policy may require initial classification because the matters discussed or identities of those involved are sensitive, but at some point in the future--ranging from months to years--the information may no longer need protection. In addition, even when declassification dates have been placed on records, they rarely have been enforced when that date has passed. Moreover, those markings can be invalidated by a future executive order, as occurred when Executive Order 12065 was replaced in 1982 by Executive Order 12356, causing the effort that had been expended under the previous Order to assign declassification dates essentially a waste of time and money.
Declassifying records without reviewing them line-by-line is commonly referred to as "bulk" declassification, a process often misunderstood to mean the release of records without any review of their content at all. A more accurate description of this process as it is used by trained archivists is "high-volume review." This approach involves the use of reliable survey techniques to accurately determine the contents of record groups and to assess whether they contain material that would damage national security if released. The age of the records, their subject matter, and the extent to which they were properly and accurately stored and indexed all contribute to how that review is conducted. In contrast to the costs associated with line-by-line review, the National Archives estimated that in 1992 the average cost to declassify using reliable sampling techniques was about seven cents per page.
Recent experience has shown that high-volume review for declassification can be a valid, reliable, and cost-effective way to process older historical records for potential public release. In 1994, President Clinton issued Executive Order 12937, ordering the declassification of millions of pages at the National Archives dating back to World War II and some as recent as the Vietnam War. After assessing the content and sensitivity of the records, the National Archives and agencies jointly identified and excluded from release file groups that contained highly sensitive material. Through this high volume review, 40 million pages were declassified, with no indication that any information still needing protection was inadvertently released in that process. Moreover, these materials were processed for release at an average cost of less than $400 per million pages--a fraction of a cent per page.14 In addition, as mentioned earlier in this chapter, Executive Order 12951's mandate to review and declassify satellite imagery is another vehicle by which classified materials that at one time were never expected to be viewed by the public are being made available in cost-effective ways that do not risk current methods of collecting sensitive information.
Resource issues have been a primary factor in the slow pace at which agencies have implemented automatic and systematic programs for declassification as required by Executive Order 12958. Many officials who were tasked by their agency to implement those provisions of the Order attribute their delay in doing so to their agency's failure to earmark new funds for this purpose. Moreover, congressional oversight committees have scrutinized agency budget requests and limited the amount that can be spent on declassification until the cost estimates on which those requests are based were adequately justified.
Yet resource availability alone does not explain why some agencies conduct successful declassification programs while others do not. Some agencies have shown that creative and effective implementation of declassification need not depend upon receipt of additional funds. For example, in August 1996, the Department of the Air Force won the Hammer Award (presented as part of the Clinton Administration's National Performance Review) for the efficient and creative implementation of its declassification program. It achieved these results not through an infusion of new funds but by finding the resources needed through other means, including using computers discarded by other offices, staffing the project with reservists, and developing internal computerized training and guidance.
New technologies hold promise as efficient tools for less costly declassification. The National Security Agency found that simply by implementing basic automation tools in its processing of POW/MIA documents, it saved over $330,000 in three and a half years, largely by replacing manual redaction with machine-aided processing.15 Some agencies, including the State Department, have for some time used computers to aid in declassification and in responding to FOIA requests; others continue to declassify pieces of paper laboriously by hand, using markers or tape to mask text. Many agencies have hired contractors to help them develop technological solutions for reviewing classified documents and, if necessary, redacting them for release, especially for records that exist in electronic, film, or other formats. However, much of this technology is either still in prototype, not fully operational, or is proprietary and cannot be shared with other agencies that would find it useful. Moreover, despite the allure of electronic wizardry, the most advanced technological solution is not always the most efficient and cost-effective one for declassifying.
There are also significant social and political costs when an agency does not routinely implement a means for public access to records that no longer need protection. Not only does the volume of classified documents that needs to be stored, accounted for, and protected continue to grow, but the costs associated with not understanding and learning from past events can be high. For example, historians have noted that it became increasingly difficult after the issuance of the 1982 Executive Order to get access to agency records from the 1940s and 1950s--the critical formative years of the Cold War. Currently, the Office of the Secretary of Defense has at least 30 million pages of records more than 25 years old.16 The Joint Staff has 4.7 million more pages of classified information from the 1940s and 1950s to be declassified.17 This backlog of materials means that it is likely to be some time before records from these offices are available to enhance public understanding of the past 50 years.
Current procedures for processing records with multiple equities are expensive and complex. An agency referring classified records to another agency for its review must make copies of the records and specially package and transport them in compliance with security procedures (which, depending on the records' classification levels, can range from sending them via registered mail to having them personally transferred to a government courier by a staff person with appropriate clearances). This process is repeated for every record that contains agency equities and can occur multiple times if a single document needs to be referred to more than one agency and also when that record is returned to the referring agency only partly declassified. At every step of this process, additional costs are incurred. Not only is the process burdensome and costly for agencies, but there are no deadlines by which agencies must respond to such referrals. The result can be lengthy delays before a review is completed and information released to the public (see box below).
A journalist who filed a FOIA request with the Department of State in 1984 seeking information on oil production in Saudi Arabia during the 1970s finally received a reply in 1993 -- nine years later. That reply consisted of a one-page chart that the State Department had retrieved and referred to the originating agency, the Department of Energy. In 1989, the DoE sent it to the Central Intelligence Agency for further review. It was then returned by the CIA to the DoE in 1993, and finally sent to the journalist with half of its numbers deleted and a notation on the document that it had actually been declassified in 1992. After nearly a decade of waiting, the journalist had long since moved on to another story.
Some encouraging steps toward more cooperative, creative ways to deal with agency equities have emerged from the implementation of automatic declassification under Executive Order 12958. Concern that its own equities might not be protected led the CIA to initiate the Remote Archive Capture project, designed to reproduce on CD-ROMs all classified documents at the presidential libraries for distribution to agencies likely to have equities in the records. Similarly, concerns that nuclear-related information classified under the Atomic Energy Act is embedded, but not identified as such, in documents that were classified under an executive order has prompted at the DoE an understanding of the need for interagency coordination and communication in declassification. The DoE has agreed to provide comprehensive guidance and training to other agencies to help them recognize such information and to speed resolution of any questions so that records containing such sensitive information can be processed more easily.
Thus, interagency use of accurate and up-to-date declassification guidance is one way to streamline the process of resolving agency equities. Some agencies already provide the National Archives with such guidance, and National Archives' officials, in turn, have encouraged agencies to share with each other any guidance they use in making declassification decisions. With some exceptions, agencies have been slow to embrace this approach, partly because some seem to be unfamiliar with using even their own agency's guides. This reluctance also seems due to a belief that others will not understand how to use the guides that do exist. However, the DoE's recent experience indicates that some types of information can be protected better if other agencies are better informed, through guides or through training, about how to recognize sensitive information.
The link between poor records management and the ability of agencies to provide access to the huge backlog of still-classified records became apparent as agencies began to take steps to comply with Executive Order 12958's automatic declassification requirements. For many agencies, it is impossible to retrieve information promptly, to make informed decisions about whether it needs continued protection, and to refer back to previous declassification decisions. Together, these result in duplicative and inconsistent releases of information.
Lack of access to government records no longer needing protection is inextricably tied to the legacy of poor records management practices across the Government. Unorganized files and vague, unreliable, or nonexistent finding aids have impeded the task of locating and identifying documents subject to declassification under Executive Order 12958. Few agencies have devoted significant time, attention, and resources to good records management and to systematic declassification reviews of older records; as a result, many are unfamiliar with basic declassification techniques and do not have either personnel trained in these processes or an infrastructure to support effective and efficient declassification. As a consequence, agencies have been compelled to conduct a more complicated search for records than the Order's provisions seem to have anticipated. As one government official observed in connection with the issuance of Executive Order 12958, agencies "must integrate classification management more closely with information and records management. If we had been following that advice from the beginning, the tasks ahead of us would be far, far simpler to accomplish."20
Current and former government officials, scholars, and records management experts all cite the poor state of the Government's records management practices as a major impediment to declassifying the millions of pages of still-secret older records. Records management principles must also be clearly defined and implemented in order for agencies to manage records created using emerging technologies. If, as one report concluded, "the goal must be to reduce the volume of classified information before it arrives in the archives, not after," then the long-term solution is to make records management and declassification requirements a routine daily administrative practice, just as classification is now. 21
The Federal Records Act grants the National Archives substantial authority over government records management, but in the past it has not consistently exercised that authority. Under that law, the National Archives has the authority to require all agencies to review their records and to establish the conditions under which they must be turned over to the National Archives when they are no longer needed for current agency operations. The Archivist's consent also is required before any agency can destroy records. The primary mission of the National Archives is to ensure that the Government's permanently valuable records are kept and, where possible, made available to the public. In order to exercise these functions and ensure active coordination and oversight of agency declassification, storage, and disposition of Federal records, the National Archives must--although it has not always done so in the past--exert a strong leadership role within the Government. To do so requires the ongoing commitment of top leadership at the National Archives and also will require that it have adequate resources to exercise this function. In a strategic plan issued in July 1996, the National Archives already has indicated its intent to "work in partnership" with agencies to implement classification and declassification policies and to develop records management programs based on the information's life cycle. This approach can be a significant step toward improving the current state of records management in the Government. 22
In addition, many officials simply do not see public access as part of their agency's mission. As one agency employee noted in the context of explaining the attitude some officials have toward the FOIA, members of the public who request declassification often are considered "the enemy," those officials view the effort required to process requests as "a disruption" in their duties, and they feel that providing public access "is not what we get paid for."
However, the DoE has shown an awareness of the need to move beyond a solely security focus in declassification by commissioning a fundamental review to reevaluate standards for what can be declassified. Playing a major role in that process are professionals who have substantive program expertise, not just security officers. This fundamental review was undertaken with support from senior agency officials and included public input. It is a model mechanism other agencies could adopt, in which justifications for declassifying particular categories of information are publicly debated in a thoughtful way without compromising sensitive information, and attitudes toward declassification are reshaped through a comprehensive approach to forming an agency's public access policies.
Not only are agency records management programs weak, but seldom do the various offices involved in public access and declassification communicate or coordinate with each other, either because they are not organized under the same reporting structure or because of turf battles. In many agencies, several offices--including the records management staff, historian's staff, FOIA staff, security personnel, and public affairs officials--are all engaged in some aspect of declassification, but traditionally these persons have not regularly worked together or notified one another of their decisions. Declassification works best when coordination within an agency is maintained. Good communication among the different offices that handle classified information, and in some cases the centralization of these offices, can lead to cost savings and efficiency by eliminating redundant functions and better enabling offices to assist one another in making informed decisions.
Developing technologies are already playing a key role in aiding declassification and will continue to do so in the future. However, while some have begun to grapple with these issues, there are few coordinated efforts to share technical knowledge, to make systems interactive, or to use these systems across the Government in the most effective manner. Moreover, many agencies are spending large sums independently to obtain technology to assist them in declassification, some of which may prove ineffective or simply duplicative of what exists elsewhere.
Aside from the recent electronic FOIA amendments discussed earlier, the effect of technology on access to classified Federal records has received inadequate attention to date. The use of computers, photocopiers, and fax machines that easily create, copy, and transmit multiple copies of records is constantly growing, and the number of government records generated grows accordingly. Agency databases used for records management, declassification, and tracking of declassified information (where these functions exist) are not interoperable across the Government and sometimes not even within a particular agency. These databases also are not always constructed in ways that make them most useful. For example, the State Department maintains a database it shares with the presidential libraries, listing documents that are still classified; the database has not, however, in the past contained information that a library would find far more useful, such as lists of documents that have been reviewed and released.
Most notably, the National Security Council played an active role in the drafting, coordination of agency and public input, and issuance of Executive Order 12958. Since then, however, it has paid little attention to agency implementation of the Order's declassification provisions. Declassification policies will only be as effective as the oversight of the agencies that implement those policies. That oversight must come from the Congress and the highest levels of the Executive Branch.
As the discussion above demonstrates, the Federal Government's process for dealing with information that no longer needs the protection of the classification system is badly in need of repair. It would be difficult, in fact, to devise a system that works less effectively and at a greater cost than the one now in place. The Commission makes three key recommendations, described below, to remedy the current situation and to avoid repeating past mistakes in the future.
The backlog of decades-old classified records described earlier in this chapter is due at least in part to defects in the way the Federal Government is organized to provide access. Declassification procedures are needed that take into account the fact that the resources available for it are finite. There are few incentives for agencies to declassify, little accountability for the ways in which they do provide access, and a lack of cost-effective, sensible procedures to accomplish the release of classified records that no longer need protection.
After examining the practices of a variety of agencies, the Commission concludes that declassification will work most efficiently and effectively when the direction of that activity is centrally coordinated. The process needs to be tied closely to an understanding of how records are kept, the context in which they were created, and how changing circumstances over time may (or may not) affect their continued need for protection. Those who declassify need to be motivated and to have the expertise, resources, and support to do their jobs well.
The Commission recommends the creation by statute of a central office--a National Declassification Center--at an existing Federal agency such as the National Archives and Records Administration to coordinate national declassification policy and activities. This Center would have the responsibility, authority, and funds sufficient to coordinate, oversee, and implement government declassification activities. The Center would monitor agency declassification programs and provide annual reports on their status to the Congress and the President.
This recommendation establishes within an existing agency a central coordination function lacking in the currently fragmented approach to agency declassification. The logical agency to administer the Center is the National Archives and Records Administration, which is already charged under the Federal Records Act with implementing many of the functions that this Center would perform. The National Archives has an understanding of how records are kept, what needs to be retained, and what can be discarded. The National Archives also can provide expert, educated, and cleared staff to review records; it has successfully done so in the past when agencies have provided sufficiently detailed guidance to do so, and at a minimal cost. (In 1995, the component of the National Archives responsible for declassification reviewed and released 111 million pages of permanently valuable records with a budget of only $2 million.) Because the National Archives has as its primary mission the management and public dissemination of federal records, it is an organization that could administer the Center.
An important aspect of the Center's coordination of declassification across the Executive Branch would be to facilitate exchange among agencies of detailed declassification guidance to resolve the equities concerns discussed earlier in this chapter. Certain categories of highly sensitive information, such as compartmented programs, human intelligence sources, and signals intelligence, could be generally exempted from declassification processing at the Center and from the sharing of declassification guidance except in circumstances where the agency head at his or her discretion may choose to do otherwise. Confidence in the Center's operations would also be enhanced by inclusion of a mechanism for agencies and the public to appeal declassification decisions made under the Center's direction. In creating the Interagency Security Classification Appeals Panel (ISCAP), Executive Order 12958 does provide an appeals mechanism for declassification decisions. However, the ISCAP operates currently in a limited fashion and does not reach all declassification activities across the government. An effective appeals mechanism made a part of the Center should have a broader reach that includes interagency appeals, FOIA requests, and other declassification projects undertaken by agencies.
The Center would perform a variety of services that would streamline declassification and assist agencies in processing records for release. It could, for example, coordinate search and review of records across agencies in response to particular public or congressional interest. However, this recommendation does not envision that the Center's primary function would be the compilation of specialized collections. Rather, the Center's mission would be to help direct government-wide declassification policy and to ensure that agencies follow basic records management and archival principles in implementing declassification. This would include efforts to keep file series intact in order to preserve the evidentiary value of the records and the historical context in which they were created.
Another key function of the Center would be to administer declassification functions on behalf of agencies, assuming the Center was provided resources sufficient to undertake that task. Agencies would be encouraged to send their classified records of permanent historical value to the Center for processing and public release. Thus, agencies would be able to take advantage of the Center's expertise while retaining substantive control over what is declassified through providing detailed guidance to be applied to the records that they send to the Center. Agencies would also be encouraged to detail employees to serve on interagency declassification review teams coordinated by the Center. These teams would, as appropriate based on the sensitivity of the records, conduct joint declassification reviews of records containing multiple agency equities that had been sent to the Center or were still housed at particular agencies.
The Center also would be responsible for establishing and coordinating agency pilot projects for records management and declassification review, especially those involving the use of new technologies. It could serve as a central government clearinghouse for procurement of, specifications for, and use of new declassification and archival storage and retrieval technologies. The Center would promote the coordinated use and sharing among agencies of new technologies, ensure greater interoperability, avoid the procurement of duplicative or proprietary systems, and employ new technologies that respond to researcher demand in cost-effective ways.
Under this approach, agencies likely would need to devote fewer of their program resources to declassification. An initial outlay of funds would be required for the Center's start-up costs and ongoing activities. However, this investment should pay substantial dividends in future years, both in financial savings and with regard to the larger opportunity costs discussed earlier in this report that lack of access to information has generated in the past.
The Commission also believes that an important component of the Center would be a permanent advisory panel to provide for regular public input and advice on agency declassification priorities. This advisory panel could serve as a liaison both with other historical advisory groups established by individual agencies and with the public as well. Experience shows that advisory bodies created by statute and composed of distinguished scholars, researchers, and other members of the public can help expedite the release of records important to informed public debate on significant policy and historical issues. The active participation of advisory bodies can also bring credibility to agency declassification activities, especially those that may be vulnerable to charges that the agency is selectively declassifying only records that show it in a favorable light. The Center could also perform a support and coordination role with agency ombudsman offices, the establishment of which is discussed below.
Underlying many sources and methods claims is the fact that the secret being protected is not the content of the information itself, but instead how it was obtained. Yet the public and historians generally do not care how information was collected; they want to know how it was used and what decisions it informed. The National Security Act of 1947 requires that intelligence sources and methods are to be protected "from unauthorized disclosure." Over the years, this very general language has come to serve as a broad rationale for declining to declassify a vast range of information about the activities of intelligence agencies. Thus, sources and methods information is not treated like other types of classified information. In practice, the sources and methods rationale has become a vehicle for agencies to automatically keep information secret without engaging in the type of harm analysis required by executive orders as a prerequisite to keeping other kinds of information secret. The statutory requirement that sources and methods be protected thus appears at times to have been applied not in a thoughtful way but almost by rote.
The Commission recommends that the use of sources and methods as a basis for the continuing classification of intelligence information be clarified through issuance of an Intelligence Community directive by the Director of Central Intelligence, explaining the appropriate scope of that protection.
Clarifying the scope of and reasons for sources and methods protection would not put at risk information that is truly sensitive, but would remove the ability to apply this rationale to withhold automatically all information that could be construed as relating in any manner, however indirectly, to an intelligence source or method. This recommendation would not in any way diminish the authority of the Director of Central Intelligence to protect sources or methods. A directive could, for example, provide guidance that analysis and information drawn from open sources should not routinely be included in the scope of that protection. Such a directive would be consistent with and would preserve the intent of the National Security Act of 1947 that highly sensitive information--for example, human intelligence--is not placed in jeopardy but continues to get the protection it deserves.
A significant element currently missing from the declassification activities of many agencies is a vigorous, systematic declassification program. A program based on a comprehensive plan with established deadlines and benchmarks to measure performance would alleviate many of the problems discussed above. Other elements of a successful program include adherence to duration limits for protection of classified information (declassifying documents according to the date or event marked on a document and no later) and the compilation of a regularly updated database of all agency declassification guidance. Another key component is to prioritize records for declassification, based on public input, according to record groups and not according to topics. In the past, declassification by topic has been very costly, and it can skew understanding of the context in which the records were created.
The Commission recommends that agencies better structure their records management and systematic declassification programs to maximize access to records that are likely to be the subject of significant public interest.
Elements of this proposal should include:
Creating ombudsman offices in every agency that is involved in classification and declassification of information would promote more effective records management and access policies. Some agencies, such as the CIA, already use such an office to broker other types of complaints about internal agency action (in the CIA's case, to address charges that analysis has been politicized). Although the Joint Security Commission recommended the creation of an ombudsman function, it was seen only as applying to the classification of information and did not include a role for that office regarding declassification. Moreover, the JSC's more limited ombudsman recommendation has not been implemented to date.
As recommended here, the ombudsman office would be headed by a senior officer whose full-time job would be to oversee the process of classification and declassification and to deal with concerns about particular actions. This official would also be empowered to intervene in disputes between agencies and FOIA requesters before they escalate into expensive, time-consuming litigation. Thus, the ombudsman office would work closely with all agency personnel involved in the life cycle of information, including records managers, training officers, classifiers, declassifiers, FOIA officers, and general counsel offices. The office would be required to submit to the agency head regular reports on cases undertaken, activities observed, and the status of agency cooperation and compliance with relevant statutes, executive orders, and other directives.
_________________
1 "U.S. Spy Satellite Ready for Launch," New York Post (19 December 1996): 37.
2 For example, Oliver Stone's movie "JFK" and its allegations of agency involvement in President
Kennedy's assassination led to creation of the Assassination Records Review Board and
the declassification of over a million pages of agency records. Assertions of a cover-up of the
crash of extraterrestrial spacecraft in New Mexico in the 1940s led to declassification of records
about Department of Air Force activities in the area during that period. See Headquarters U.S.
Air Force, The Roswell Report: Fact versus Fiction in the New Mexico Desert, stock no. 008-
070-00697-9 (Washington, D.C.: Government Printing Office, 1995).
3 See Department of Defense Personnel Security Research Center, Public Attitudes Towards
Security and Counter-Espionage Matters In The Post Cold War Period, prepared by Tom W.
Smith, National Opinion Research Center, for the Security Awareness Area of the Personnel
Security Research Institutional Award Program (Monterey: November 1994).
4 Interview by Commission staff, 6 November 1995.
5 Dr. Alexander DiVolpi, statement at the Commission's Public Access Roundtable, National
Archives and Records Administration, Washington, DC, May 16, 1996 (describing problems he
and colleagues have encountered in publishing and discussing scientific information in the
public domain that the DoE later claimed was classified). See also Glenn T. Seaborg, "Secrecy
Runs Amok," Science (3 June 1994): 1410 (former chairman of the Atomic Energy Commission
discusses his experience with DoE assertions that his personal diary was classified and its
seizure of his personal papers even though he had previously sought and obtained verification
from the AEC that they contained no classified material).
6 See, e.g., Central Intelligence Agency, "CIA Briefing for the Commission on Protecting and
Reducing Government Secrecy" (18 August 1995, chart 3), on file with the Commission.
7 Department of State official, interview by Commission staff, 21 August 1996. That official
called OADR a potential "time bomb" because of its implicit requirement that every classified
document marked OADR -- no matter how innocuous or highly sensitive -- equally required
review by the originator before it could be declassified and released.
8 General Accounting Office, Classified Information: Volume Could Be Reduced by Changing
Retention Policy, GAO/NSIAD-93-127 (Washington, D.C.: Government Printing Office, May
1993), 16-17.
9 In 1992, the last year for which complied statistics are available, 575,424 FOIA requests were
filed and nearly $108.5 million spent to implement the law. "Costs Go Up But Requests Go
Down in 1993 Annual Reports," Access Reports (17 August 1994): 4-5.
10 House of Representatives, Rep. Randy Tate (R.-Washington) speaking for the Electronic
Freedom of Information Act Amendments of 1996, H.R. 3802, 104th Cong., 2d sess., Congressional
Record (17 September 1996), 142, pt. 128: H10450. Senator Patrick Leahy (D.-Vermont)
first introduced this bill in 1991, held hearings in 1992, and was one of its key proponents
through its final passage in 1996.
11 National Archives and Records Administration official, letter to Commission staff, 29 July
1996. One cubic foot is about 2,500-3,000 pages. (National Archives and Records Administration
official, telephone conversation with Commission staff, 29 July 1996.)
12 Data gathered by the Commission staff from government agencies on the numbers of pages
subject to declassification under Executive Order show the following:
Agencies Pages 25 years old Pages to be Pages declassified and older subject to reviewed for as of Executive Order declassification January 12958 (excluding exemptions) 1997 CIA 165,900,000 59,300,000 19,600 Defense, -Office of the Secretary 30,235,000 21,450,000 unknown after 476,104 pages reviewed -Army 270,000,000 same 0 -Air Force 176,495,000 same 7,503,781 -DIA 21,005,000 (not unavailable unavailable including 201,000 cans of aerial film) -Navy 500,000,000 unknown 33,120,000 Energy 230,000,000 132,000,000 1,600,000 JCS 4,675,625 same 570,000 NRO 6,500,000 1,300,000 0 NSA 129,300,000 53,300,000 1,900,000 State 45,000,000 unavailable 12,500,000 TOTAL 1,579,110,625 718,520,625 57,213,381
13 Department of the Navy, "Declassification Plan for Navy and Marine Corps Records Under
Executive Order 12958," (16 April 1996), on file with the Commission.
14 National Archives and Records Administration, Declassification Projects: Time & Cost To
Process 1,000,000 Pages (on file with the Commission).
15 National Security Agency, "Estimated Cost Saving for Declassification Effort" (9 February
1996, briefing sheet, on file with the Commission).
16 Department of Defense staff, telephone conversation with Commission staff, 24 September
1996.
17 Ibid.
18 Department of State officials, interview by Commission staff, 19 September 1995.
19 Defense Intelligence Agency officials, interview by Commission staff, 30 August 1995.
20 National Classification Management Society, "Virtual Interview With The Director, Information
Security Oversight Office,"Viewpoints1 (1995): 31.
21 Inspector General, Department of Defense, White Paper: Classification and Declassification
Within the Department of Defense (Washington, D.C.: Department of Defense, May 1995), ii.
22 National Archives and Records Administration, Ready Access To Essential Evidence: The
Strategic Plan Of The National Archives And Records Administration, 1997-2000, 13.
23 General Accounting Office, Environmental Data: Major Effort Is Needed to Improve NOAA's
Data Management and Archiving, GAO/IMTEC-91-11 (Washington, D.C.: Government
Printing Office, November 1990), 26-27.
24 Inspector General, DoD,White Paper, i.
Go Back to Top Page of the Commission Report
Proceed to Chapter Four