
The False Hope of Nuclear Forensics? Assessing the Timeliness of Forensics Intelligence
Nuclear forensics is playing an increasing role in the conceptualization of U.S. deterrence strategy, formally integrated into policy in the 2006 National Strategy on Combatting Terrorism (NSCT). This policy linked terrorist groups and state sponsors in terms of retaliation, and called for the development of “rapid identification of the source and perpetrator of an attack,” through the bolstering of attribution via forensics capabilities.12 This indirect deterrence between terrorist groups and state sponsors was strengthened during the 2010 Nuclear Security Summit when nuclear forensics expanded into the international realm and was included in the short list of priorities for bolstering state and international capacity. However, while governments and the international community have continued to invest in capabilities and databases for tracking and characterizing the elemental signatures of nuclear material, the question persists as to the ability of nuclear forensics to contribute actionable intelligence in a post-detonation situation quickly enough, as to be useful in the typical time frame for retaliation to terrorist acts.
In the wake of a major terrorist attack resulting in significant casualties, the impetus for a country to respond quickly as a show of strength is critical.3 Because of this, a country is likely to retaliate based on other intelligence sources, as the data from a fully completed forensics characterization would be beyond the time frame necessary for a country’s show of force. To highlight the need for a quick response, a quantitative analysis of responses to major terrorist attacks will be presented in the following pages. This timeline will then be compared to a prospective timeline for forensics intelligence. Fundamentally, this analysis makes it clear that in the wake of a major nuclear terrorist attack, the need to respond quickly will trump the time required to adequately conduct nuclear forensics and characterize the origins of the nuclear material. As there have been no instances of nuclear terrorism, a scenario using chemical, biological, and radiological weapons will be used as a proxy for what would likely occur from a policy perspective in the event a nuclear device is used.
This article will examine existing literature, outline arguments, review technical attributes,4 examine the history of retaliation to terrorism, and discuss conclusions and policy recommendations. This analysis finds that the effective intelligence period for nuclear forensics is not immediate, optimistically producing results in ideal conditions between 21 and 90 days, if at all. The duration of 21 days is also based on pre-detonation conditions, and should be considered very, if not overly, optimistic. Further, empirical data collected and analyzed suggestions that the typical response to conventional terrorism was on average 22 days, with a median of 12 days, while terrorism that used chemical, biological, or radiological materials warranted quicker response – an average of 19 days and a median of 10 days. Policy and technical obstacles would restrict the effectiveness of nuclear forensics to successfully attribute the origin of a nuclear weapon following a terrorist attack before political demands would require assertive responses.
Literature
Discussions of nuclear forensics have increased in recent years. Non-technical scholarship has tended to focus on the ability of these processes to deter the use of nuclear weapons (in particular by terrorists), by eliminating the possibility of anonymity.5 Here, the deterrence framework is an indirect strategy, by which states signal guaranteed retribution for those who support the actions of an attacking nation or non-state actor. This approach requires the ability to provide credible evidence both as to the origin of material and to the political decision to transfer material to a non-state actor. As a result of insufficient data available on the world’s plutonium and uranium supply, as well as the historical record of the transit of material, nuclear forensics may not be able to provide stand-alone intelligence or evidence against a supplying country. However, scholars have largely assumed that the ‘smoking gun’ would be identifiable via nuclear forensics. Michael Miller, for example, argues that attribution would deter both state actors and terrorists from using nuclear weapons as anyone responsible will be identified via nuclear forensics.6 Keir Lieber and Daryl Press have echoed this position by arguing that attribution is fundamentally guaranteed due to the small number of possible suppliers of nuclear material and the high attribution rate for major terrorist attacks.7 There is an important oversight from both a technical and policy perspective in these types of arguments however.
First, the temporal component of nuclear forensics is largely ignored. The processes of forensics do not produce immediate results. While the length of time necessary to provide meaningful intelligence differs, it is unlikely that nuclear forensics will provide information as to the source of the device in the time frame required by policymakers, who in the wake of a terrorist attack will need to respond quickly and decisively. This is likely to decrease both the credibility of forensics information and its usefulness if the political demand requires a leader to act promptly.
Secondly, the existence and size of a black-market for nuclear and radiological material is generally dismissed as a non-factor as it is assumed that a complex weapon provided by a state with nuclear weapon capacity is necessary. While it is acknowledged that a full-scale nuclear device capable of being deployed on a delivery device certainly requires advanced technical capacity that a terrorist organization would likely not have, a very crude weapon is possible. Devices such as a radiological dispersal device or a low yield nuclear device, or even a failed (fizzle) nuclear weapon, would still create a desirable outcome for a terrorist group in that panic, death, and devastating economic and societal consequences would ensue. Further, black market material could the ideal method of weaponization, as its characterization and origin-tracing would prove nearly impossible due to decoupling, and thus confusion, between perpetrator and originator.
It is evident that there is a gap between a robust technical understanding and arguments as to the viability and speed of nuclear forensics in providing actionable intelligence. This gap could lead to unrealistic expectations in times of crisis.
Technical Perspective
This section will outline the technologies, processes, and limitations of forensics in order to better inform its potential for contributing meaningful data in a crisis involving nuclear material. It should be noted that most open-source literature on the processes and capabilities of nuclear forensics come from a pre-detonation position, as specifics on post-denotation procedures and timelines are classified.8 This has resulted in the technical difficulties and inherent uncertainties in the conduct of forensic operations in a post-detonation situation being ignored. The following will attempt to extrapolate the details of the pre-detonation procedures into the post-detonation context in order to posit a potential time frame for intelligence retrieval.
Fundamentally, nuclear forensics is the analysis of nuclear or radiological material for the purposes of documenting the material’s characteristics and process history. With this information, and a database of material to compare the sample to, attribution of the origin of the material is possible.9 Following usage or attempted usage of a nuclear or radiological device, nuclear forensics would examine the known relationships between material characteristics and process history, seeking to correlate characterized material with known production history. While forensics encompasses the processes of analysis on recovered material, nuclear attribution is the process of identifying the source of nuclear or radioactive material, to determine the point of origin and routes of transit involving such material, and ultimately to contribute to the prosecution of those responsible.
Following a nuclear detonation, panic would likely prevail among the general populace and some first responders charged with helping those injured. Those tasked with collecting data from the site for forensic analysis would take time to deploy.10 While National Guard troops are able to respond to aid the population, specialized units are more dispersed throughout the country.11 Nuclear Emergency Support Teams, which would respond in the wake of a nuclear terror attack, are stationed at several of the national laboratories spread around the country. Depending on the location of the attack, response times may vary greatly. The responders’ first step would be to secure the site, as information required for attribution comes from both traditional forensics techniques (pictures, locating material, measurements, etc.) and the elemental forensics analysis of trace particles released from the detonation. At the site, responders would be able to determine almost immediately if it was indeed a full-scale nuclear detonation, a fizzle, or a radiological dispersal device. This is possible by assessing the level of damage and from the levels of radiation present, which can be determined with non-destructive assay techniques and dosimetry. Responders (through the use of gamma ray spectrometry and neutron detection) will be able to classify the type of material used if it is a nuclear device (plutonium versus uranium). With these factors assessed, radiation detectors would need to be deployed to carefully examine the blast site or fallout area to catalogue and extricate radioactive material for analysis. These materials would then need to be delivered to a laboratory capable of handling them.
Once samples arrive at the laboratories, characterization of the material will be undertaken to provide the full elemental analysis (isotopic and phase) of the radioactive material, including major, minor and trace constituents, and a variety of tools that can help classify into bulk analysis, imaging techniques, and microanalysis. Bulk analysis would provide elemental and isotopic composition on the material as a whole, and would enable the identification of trace material that would need to be further analyzed. Imaging tools capture the spatial and textural heterogeneities that are vital to fully characterizing a sample. Finally, microanalysis examines more granularly the individual components of the bulk material.
The three-step process described above is critical to assessing the processes the material was exposed to and the origin of the material. The process, the tools used at each stage, and a rough sequencing of events is shown in Figure 1.12 This table, a working document produced by the IAEA, presents techniques and methods that would be used by forensics analysts as they proceed through the three-step process, from batch analysis to microanalysis. Each column represents a time frame in which a tool of nuclear forensics could be utilized by analysts. However, this is a pre-detonation scenario. While it does present a close representation of what would happen post-detonation, some of the techniques listed below would be expected to take longer. This is due to several factors such as the spread of the material, vaporization of key items, and safety requirements for handling radioactive material. These processes take time and deal with small amounts of material at a time which would require a multitude of microanalysis on a variety of elements.
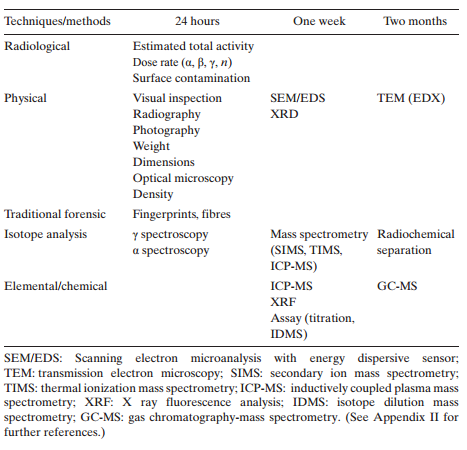
IAEA Suggested Sequence for Laboratory Techniques and Methods
It should also be noted that while nuclear forensics does employ developed best practices, it is not an exact science in that a process can be undertaken and definitive results. Rather, it is an iterative process, by which a deductive method of hypothesis building, testing, and retesting is used to guide analysis and extract conclusions. Analysts build hypotheses based on categorization of material, test these hypotheses against the available forensics data and initiate further investigation, and then interpret the results to include or remove actors from consideration. This can take several iterations. As such, while best practices and proven science drive analysis, the experience and quality of the analyst to develop well-informed hypotheses which can be used to focus more on the investigation is critical to success. A visual representation of the process is seen in Figure 2 below.13
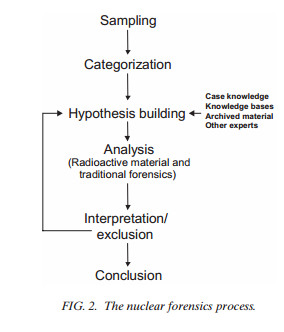
IAEA forensic analysis process
A net assessment by the Joint Working Group of the American Physical Society and the American Association for the Advancement of Science of the current status of nuclear forensics and the ability to successfully conduct attribution concluded that the technological expertise was progressing steadily, but greater cooperation and integration was necessary between agencies.14 They also provided a simplified timeline of events following a nuclear attack, which is seen in Figure 3.15 Miller also provides a more nuanced breakdown of questions that would arise in a post-detonation situation; however, it is the opinion of the author that his table overstates technical capacity following a detonation and uses optimistic estimates for intelligence.16
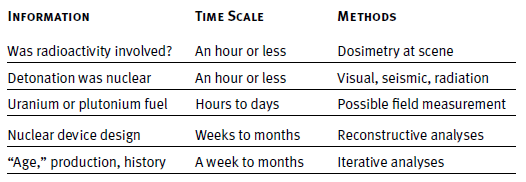
Nuclear forensics activities following a detonation
Many of the processes that provide the most insight simply take time to configure, run, and rerun. Gas chromatography-mass spectrometry, for instance, is able to detect and measure trace organic elements in a bulk sample, a very useful tool in attempting to identify potential origin via varying organics present.17 However, when the material is spread far (mostly vaporized or highly radioactive), it can take time to configure and run successfully. Thermal Ionization Mass Spectrometry (TIMS) allows for the measuring of multiple isotopes simultaneously, enabling ratios between isotope levels to be assessed.18 While critically important, this process takes time to prepare each sample, requiring purification in either a chemical or acid solution.
With this broad perspective in mind, how long would it take for actionable intelligence to be produced by a nuclear forensics laboratory following the detonation of a nuclear weapon? While Figure 1 puts output being produced in as little as one week, this would be high-level information and able to eliminate possible origins, but most likely not able to come to definitive conclusion. The estimates of Figure 3 (ranging from a week to months), are more likely as the iterative process of hypothesis testing and the obstacles leading up to the point at which the material arrives at the laboratory, would slow and hamper progress. Further, if the signatures of the material are not classified into a comprehensive database, though disperse efforts are underway, the difficulty in conclusively saying it is a particular actor increases.19 As such, an estimate of weeks to months, as is highlighted in Figures 4 and 5, is an appropriate time frame by which actionable intelligence would be available from nuclear forensics. The graphics below show the likely production times for definitive findings by the forensics processes and outlines a zone of effective intelligence production. How does this align with the time frame of retribution?
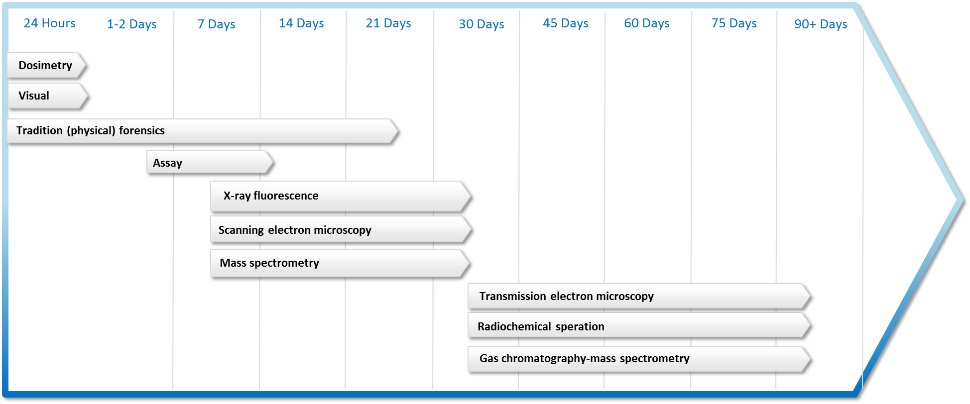
Nuclear forensics timeline (author-created figure, compiled from above cited IAEA reports and AAAS report}
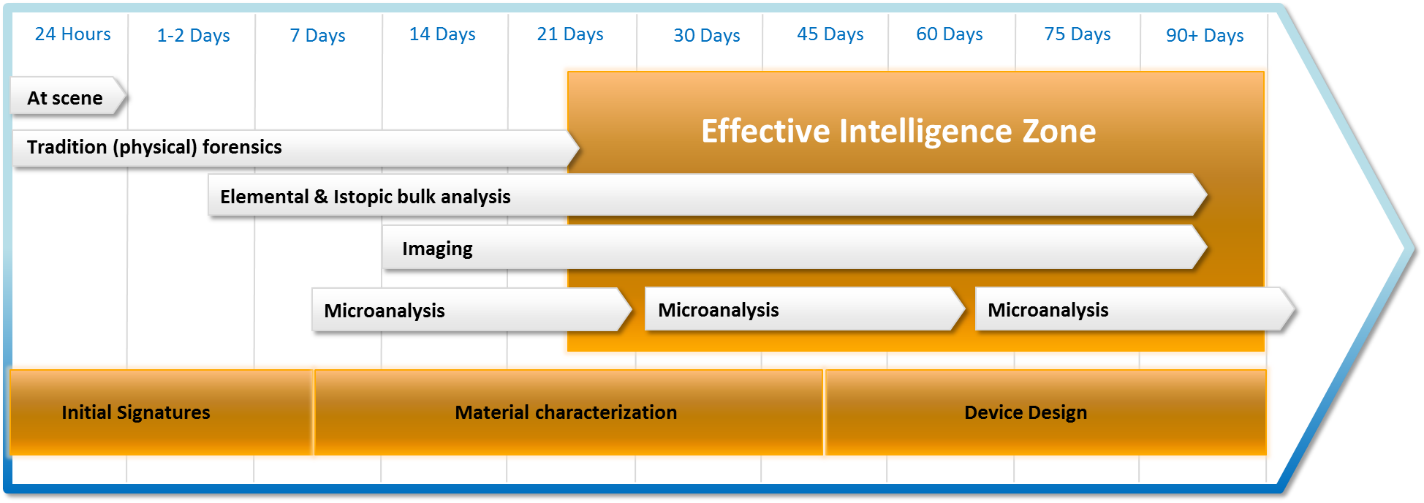
Effective Intelligence Zone (author-created figure, compiled from above cited IAEA reports and AAAS report.)
Retaliation Data
How quickly do policymakers act in the wake of a terrorist attack? This question is largely unexplored in the social science literature. However, it is critical to establishing a baseline period in which nuclear forensics would likely need to be able to provide actionable intelligence following an attack. As such, an examination of the retaliatory time to major terrorist attacks will be examined to understand the time frame likely available to forensics analysts to contribute conclusions on materials recovered.
Major terrorist attacks were identified using the Study for Terrorism and Responses to Terrorism Global Terrorism Database.20 As such, the database was selected to return events that resulted in either 50 or more fatalities or over 100 injured. Also removed were cases occurring in Afghanistan or Iraq after 2001 and 2003 due to the indistinguishability of responses to terror attacks and normal operations of war within the data. This yielded 269 observations between 1990 and 2004. Cases that had immediate responses (same day) were excluded as this would indicate an ongoing armed conflict. Summary statistics for this data are as follows:
The identified terrorist events were then located in Gary King’s 10 Million Events data set21, which uses a proven data capture and classification method to catalogue events between 1990 and 2004. Government responses following the attack were then captured. Actions were restricted to only those where the government engaged the perpetrating group. This was done by capturing events classified as the following: missile attack, arrest, assassination, unconventional weapons, armed battle, bodily punishment, criminal arrests, human death, declare war, force used, artillery attack, hostage taking, torture, small arms attack, armed actions, suicide bombing, and vehicle bombing. This selection spans the spectrum of policy responses available to a country following a domestic terror attack that would demonstrate strength and resolve. Additionally, by utilizing a range of responses, it is possible to examine terrorism levied from domestic and international sources, thus enabling the consideration of both law enforcement and military actions. Speech acts, sanctions, and other policy actions that do not portray resolve and action were excluded, as they would typically occur within hours of an attack and would not be considered retaliation.
Undertaking this approached yielded retaliation dates for all observations. The summary statistics and basic outline of response time by tier of causalities are as follows:
Table 2: Summary Statistics Table 3: Casualties by Retaliation Quartile
Immediately, questions arise as to the relationship between retaliation time and destruction inflicted, as well as the time frame available to nuclear forensics analysts to provide intelligence before a response is required. With an average retaliation time of 22 days, this would fall within the 1-2 month time frame for complete analysis. Further, a median retaliation time of 12 days would put most laboratory analysis outside the bounds of being able to provide meaningful data. Figure 6 further highlights this by illustrating that within 30 days of a terrorist attack, 80 percent of incidents will have been responded to with force.
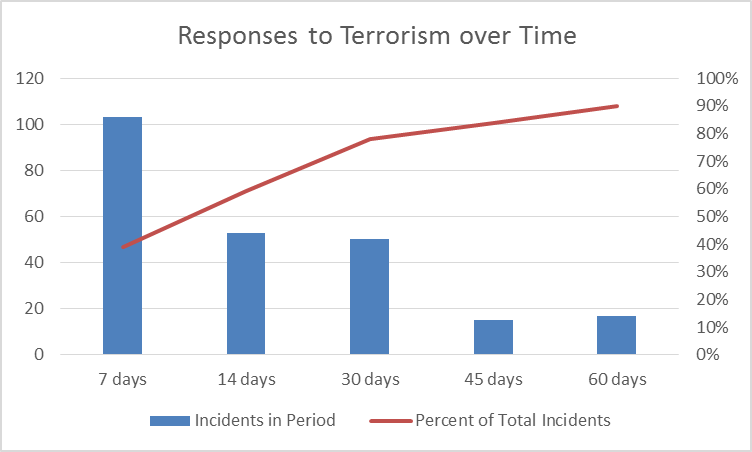
Response Time
One of the fundamental graphics presented in the Lieber and Press article shows that as the number of causalities in a terror attack increases, the likelihood of attribution increases correspondingly. This weakens their arguments for two reasons. First, forensics following a conventional attack would have significantly more data available than in the case of a nuclear attack, due to the destructive nature of the attack and the inability of responders to access certain locales. Secondly, a country that is attacked via unconventional means could arguably require a more resolute and quicker response. In looking at the data, the overall time to retaliation is 21.66 days. This number is significantly smaller when limited to unconventional weapons (19.04 days) and smaller still when the perpetrators are not clearly identified (18.8 days). This highlights the need for distinction between unconventional and conventional attacks, which Lieber and Press neglected in their quantitative section.
To further highlight the point that nuclear forensics may not meet the political demands put upon it in a post-detonation situation, Table 4 highlights the disconnect between conventional and unconventional attacks and existing threats. To reiterate, the term unconventional is used colloquially here as a substitute for CBRN weapons, and not unconventional tactics. In only 37 percent of the cases observed was the threat a known entity or attributed after the fact. This compares to 85 percent for conventional. In all of these attacks, retaliation did occur; allowing the conclusion that with the severity of an unconventional weapon and the unordinary fear that is likely to be produced that public outcry and a prompt response would be warranted regardless of attribution.
As the use of a nuclear weapon would result in a large number of deaths, the question as to whether or not higher levels of casualties influence response time is also of importance. However, no significant correlation is present between retaliation time and any of the other variables examined. Here, retaliation time (in days) was compared with binary variables for whether or not the perpetrators were known, if the facility was a government building or not, if the device used was a bomb or not, and if an unconventional device was used or not. Scale variables used include number of fatalities, injured, and the total casualties from the attack. Of particular note here is the negative correlation between unconventional attacks and effective attribution at time of response; this reemphasizes the above point on attribution prior to retaliation as being unnecessary following an unconventional attack.
Assessment
From this review, the ability of nuclear forensics to provide rapid, actionable intelligence in unlikely. While it is acknowledged that the process would produce gains along the way, an effective zone of intelligence production can be assumed between 21-90 days optimistically. This is highlighted in Figure 5 above, which aligns the effective zone with the processes that would likely provide definitive details. However, this does not align with the average (22 days) and median (12 days) time of response for conventional attacks. More importantly, unconventional attack responses fall well before this effective zone, with an average of 19 days and a median of 10. While the effective intelligence zone is close to these averages of these data points, the author remains skeptical that the techniques to be performed would produce viable data in a shorter time frame presented given the likely condition of the site and the length of time necessary for each run of each technique.22 This woasuld seem to support an argument that the working timelines for actionable data being outside the boundary of average retaliatory time. More examination is necessary to further narrow down the process times, a task plagued with difficulties due to material classification.ass
A secondary argument that can be made when thinking about unattributed terror attacks is that even without complete attribution, a state will retaliate against a known terror, cult, or insurgent organization following a terror attack to show strength and deter further attacks. This was shown to be the case in 34 of 54 observations (63 percent unattributed). While this number is remarkably high, all states were observed taking decisive action against a group. This would tend to negate the perspective that forensics will matter following an attack, as a state will respond more decisively to unconventional attacks than conventional whether attribution has been established or not.
There are also strategic implications for indirect deterrent strategies as well. Indirect deterrence offers a bit more flexibility in the timing of results, but less so in the uncertainty of results, as it will critical in levying guilty claims against a third-party actor. Thus, nuclear forensics can be very useful, and perhaps even necessary, in indirect deterrent strategies if data is available to compare materials and a state is patient in waiting for the results; however, significant delays in intelligence or uncertainty in results may reduce the credibility of accusations and harm claims of guilt in the international context. From a strategic perspective, the emphasis in the United States policy regarding rapid identification that was discussed at the outset of the paper reflects optimism rather than reality.
Policy Recommendations
While nuclear forensics may not be able to contribute information quickly enough to guide policymakers in their retaliatory decision-making following terrorist attacks, nuclear forensics does have significant merit. Nuclear forensics will be able to rule people out. It will be able to guide decisions for addressing the environmental disaster. Forensics also has significant political importance, as it can be used in a post-hoc situation following retaliation to possibly justify any action taken. It will also continue to be important in pre-detonation interdiction situations, where it has been advanced and excelled to-date, providing valuable information on the trafficking of illicit materials.
However, realistic expectations are necessary and should be made known so that policymakers are able to plan accordingly. The public will demand quick action, requiring officials to produce tangible results. If delay is not possible, attribution may not be possible. To overcome this, ensuring policymakers are aware of the technical limitations and hurdles that are present in conducting forensics analysis of radioactive material would help to manage expectations.
To reduce analytical time and improve attribution success rates, further steps should be taken. Continuing to enlarge the IAEA database on nuclear material signatures is critical, as this will reduce analytical time and uncertainty, making more precise attribution possible. Additional resources for equipment, building up analytical capacity, and furthering cooperation among all states to ensure that signatures are catalogued and accessible is critical. The United States has taken great steps in improving the knowledge base on how nuclear forensics is conducted with fellowships and trainings available through the Department of Energy (DOE) and the Department of Homeland Security (DHS). While funding constraints are tight, expansion of these programs and targeted recruitment of highly-qualified students and individuals is key. Perhaps, these trainings and opportunities could be expanded to cover individuals that are trained to do analytical work, but is not their primary tasking – like a National Guard for nuclear forensics. DOE and other agencies have similar programs for response capacity during emergencies; bolstering analytical capacity for rapid ramp-up in case of emergency would help to reduce analytical time. However, while these programs may reduce time, some of the delay is inherent in the science. Technological advances in analytics may help, but in the short-term are unavailable. In sum, further work in developing the personnel and technological infrastructure for nuclear forensics is needed; in the meantime, prudence is necessary.
Philip Baxter is currently a PhD Candidate in the International Affairs, Science, and Technology program in the Sam Nunn School of International Affairs at Georgia Tech. He completed his BA in political science and history at Grove City College and a MA in public policy, focusing on national security policy, from George Mason University. Prior to joining the Sam Nunn School, Phil worked in international security related positions in the Washington, DC area, including serving as a researcher at the National Defense University and as a Nonproliferation Fellow at the National Nuclear Security Administration. His dissertation takes a network analysis approach in examining how scientific cooperation and tacit knowledge development impacts proliferation latency. More broadly, his research interests focus on international security issues, including deterrence theory, strategic stability, illicit trafficking, U.S.-China-Russia relations, and nuclear safeguards.
A military depot in central Belarus has recently been upgraded with additional security perimeters and an access point that indicate it could be intended for housing Russian nuclear warheads for Belarus’ Russia-supplied Iskander missile launchers.
The Indian government announced yesterday that it had conducted the first flight test of its Agni-5 ballistic missile “with Multiple Independently Targetable Re-Entry Vehicle (MIRV) technology.
While many are rightly concerned about Russia’s development of new nuclear-capable systems, fears of substantial nuclear increase may be overblown.
Despite modernization of Russian nuclear forces and warnings about an increase of especially shorter-range non-strategic warheads, we do not yet see such an increase as far as open sources indicate.