
[Back]

[Index]

[Next]
 [Back] |
 [Index] |
 [Next] | Operations Security |
INTELLIGENCE COLLECTION ACTIVITIES AND DISCIPLINES
Intelligence is the product resulting from the collection, collation, evaluation, analysis, integration, and interpretation of collected information.[1] It is a specialized information product that provides the United States or an adversary with information required to further its national interests. One of the most important functions of intelligence is the reduction of the ambiguity inherent in the observation of external activities. In the most obvious case, adversary intelligence organizations may seek information concerning military capabilities or other matters that directly threaten the national security of the United States. In other cases, adversary nations, or other groups, may seek information about U.S. diplomatic negotiating positions, economic programs, or proprietary information from U.S. corporations.
In each of these cases, the information sought may provide the adversary with an edge and might allow him to implement a well-developed strategy to reach his goals. In most cases, the development of an intelligence product involves collecting information from a number of different sources. In some cases, information may be disseminated immediately upon collection based upon operational necessity and potential impact on current operations. This type of raw intelligence is usually based on fragmentary information about fast-breaking events and may contain substantial inaccuracies or uncertainties that must be resolved through subsequent report and analysis. Finished intelligence products contain information that is compared, analyzed, and weighted to allow the development of conclusions. Finished intelligence is produced through analytical review in the intelligence process. The intelligence process confirms a fact or set of facts through a multiplicity of sources to reduce the chance of erroneous conclusions and susceptibility to deception.
Intelligence is divided into strategic and operational intelligence. Strategic intelligence provides policy makers with the information needed to make national policy or decisions of long-lasting importance. Strategic intelligence collection often requires integrating information concerning politics, military affairs, economics, societal interactions, and technological developments. It typically evolves over a long period of time and results in the development of intelligence studies and estimates. Operational intelligence is concerned with current or near-term events. It is used to determine the current and projected capability of a program or operation on an ongoing basis and does not result in long-term projections. Most intelligence activities support the development of operational intelligence. [2]
The intelligence cycle is the process through which intelligence is obtained, produced, and made available to users. In depicting this cycle, the United States Intelligence Community uses a five-step process. Other nations may describe this cycle differently; however, the process is largely the same. The steps in the intelligence cycle are depicted in the following illustration:
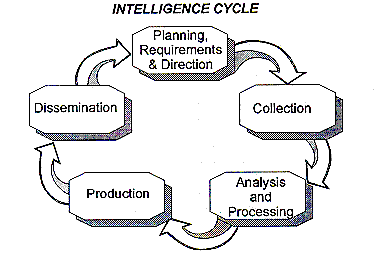
Planning and Direction. The first step in the cycle, planning and direction, involves the management of the entire intelligence effort, from the identification of a need for data to the final delivery of the intelligence product to the consumer. The process consists of identifying, prioritizing, and validating intelligence requirements, translating requirements into observables, preparing collection plans, issuing requests for information collection, production, and dissemination, and continuously monitoring the availability of collected data. In this step specific collection capabilities are tasked, based on the type of information required, the susceptibility of the targeted activity to various types of collection activity, and the availability of collection assets.
Collection. The second step, collection, includes both acquiring information and provisioning that information to processing and production elements. The collection process encompasses the management of various activities, including developing collection guidelines that ensure optimal use of available intelligence resources. Intelligence collection requirements are developed to meet the needs of potential consumers. Based upon identified intelligence, requirements collection activities are given specific taskings to collect information. These taskings are generally redundant and may use a number of different intelligence disciplines for collection activities. Tasking redundancy compensates for the potential loss or failure of a collection asset. It ensures that the failure of a collection asset is compensated for by duplicate or different assets capable of answering the collection need. The use of different types of collection systems contributes to redundancy. It also allows the collection of different types of information that can be used to confirm or disprove potential assessments. Collection operations depend on secure, rapid, redundant, and reliable communications to allow for data exchange and to provide opportunities for cross-cueing of assets and tip-off exchanges between assets. Once collected, information is correlated and forwarded for processing and production.
Processing. The third step, processing, is the conversion of collected information into a form suitable for the production of intelligence. In this process, incoming information is converted into formats that can be readily used by intelligence analysts in producing intelligence. Processing may include such activities as translation and reduction of intercepted messages into written format to permit detailed analysis and comparison with other information. Other types of processing include video production, photographic processing, and correlation of information collected by technical intelligence platforms.
Production. The fourth step, production, is the process of analyzing, evaluating, interpreting, and integrating raw data and information into finished intelligence products for known or anticipated purposes and applications. The product may be developed from a single source or from all-source collection and databases. To be effective, intelligence production must focus on the consumer's needs. It should be objective, timely, and most importantly accurate. As part of the production process, the analyst must eliminate information that is redundant, erroneous, or inapplicable to the intelligence requirement. As a result of the analytical effort, the analyst may determine that additional collection operations are required to fill in gaps left by previous collection or existing intelligence databases. The final intelligence product must provide the consumer with an understanding of the subject area, and draw analytical conclusions supported by available data.
Dissemination. The final step of the intelligence cycle is dissemination. Dissemination is the conveyance of intelligence to the consumer in a usable form. Intelligence can be provided to the consumer in a wide range of formats including verbal reports, written reports, imagery products, and intelligence databases. Dissemination can be accomplished through physical exchanges of data and through interconnected data and communications networks.[3]
The OPSEC program manager should be aware of the intelligence cycle for three reasons. First, this awareness allows the manager to play a role in the production of intelligence required to support his OPSEC program. The OPSEC program manager must be aware of the range of threats that confront his program, or he will not be able to implement countermeasures to deny the adversary access to data that may provide critical information. Knowledge of the intelligence cycle and the various Intelligence Community organizations allows the OPSEC program manager to determine how to access intelligence needed for conduct of the OPSEC process.
Second, knowledge of the intelligence cycle allows the OPSEC program manager to develop protective measures to thwart adversary collection activities. Knowledge of adversary intelligence planning derived through U.S. intelligence collection allows the OPSEC program manager to determine if his facility, operation, or program is targeted, or is likely to be targeted, by a particular adversary. Knowledge of an adversary's collection methods and patterns allows the program manager to develop effective countermeasures that hide or distort indicators.
Finally, a knowledge of the adversary's analytical biases can be used to develop deception programs that deceive the adversary by confirming erroneous perceptions. The following section of this handbook examines the various intelligence collection disciplines and considers their use by adversaries against the United States.
Several intelligence disciplines are used by adversaries to acquire information concerning the United States. These disciplines include human intelligence HUMINT), signals intelligence (SIGINT), imagery intelligence (IMINT), measurement and signatures intelligence (MASINT), and open source intelligence (OSINT). Each of these disciplines is used by adversaries against the United States to some degree. Most nations, and many subnational and private organizations, have HUMINT capabilities that they use to collect data on their adversaries and competitors.
Open source intelligence is successful in targeting the United States because of the openness of American society. Technical and professional journals are often lucrative sources for information concerning government and commercial activities in the United States. The growing number of on-line databases has increased the capacity of U.S. adversaries and competitors to develop tailored data products on U.S. government and industry activities by permitting them to review large quantities of information in very short periods of time. Search parameters used for these databases can be structured to extract only pertinent information for analysis.
Open source collection becomes more of a threat as more information becomes electronically accessible. OPSEC program managers must be aware of the potential for open source collection against their activities and must ensure that protective countermeasures are developed to prevent inadvertent compromise of program activities through publication of data in publicly available media.
Intelligence collection organizations may also use IMINT, SIGINT, and MASINT to gather data. These collection capabilities, however, are often limited by the technological capabilities of the intelligence organization. Historically, less technologically capable nations have been unable to gain access to information; however, this situation is changing. SIGINT technologies are proliferating throughout the world and are being sold by a wide variety of suppliers to nations that are known adversaries of the United States. Imagery products are becoming more readily available to non-traditional adversaries as commercial imagery products that approach the quality of intelligence collection systems become available for sale. MASINT, however, is still a relatively arcane collection discipline and only a limited number of nations have access to MASINT collection capabilities. The following sections discuss each of the collection disciplines and the type of information collected.
Human intelligence is derived from human sources.[4] To the public, HUMINT remains synonymous with espionage and clandestine activities, yet, in reality, most HUMINT collection is performed by overt collectors such as diplomats and military attaches. HUMINT is the oldest method for collecting information about a foreign power. Until the technical revolution of the mid to late twentieth century, HUMINT the primary source of intelligence for all governments. For most nations in the world, it remains the mainstay of their intelligence collection activities. HUMINT includes overt, sensitive, and clandestine activities and the individuals who exploit, control, supervise, or support these sources.
Overt activities are performed openly. Overt HUMINT collectors can include military attaches, diplomatic personnel, members of official delegations, and debriefers at refugee centers. Overt HUMINT activities may include: exploiting unclassified publications, conference materials, and Congressional hearings; operating interrogation centers for refugees and prisoners of war; and debriefing legal travelers who traveled to countries of interest to a nation's intelligence service. Sensitive HUMINT activities may depend upon the same methods as overt activities, however, the sponsor of the activity must be protected from disclosure. Disclosure of the sponsor's identity may result in political embarrassment, compromise of other intelligence operations, or security threats to the sponsoring nation.[5]
Clandestine HUMINT sources include agents who have been recruited or have volunteered to provided information to a foreign nation, and foreign nationals who successfully infiltrate an organization with a cover story. The latter cases are fairly rare, and generally come to the United States under the guise of being political refugees.[6] Once in the United States, they move into positions that allow them to gather political, technical, or economic information for their governments.
According to one estimate, over 100 countries currently conduct intelligence operations against the United States.[7] Adversary intelligence organizations place a high priority on the acquisition of scientific and technical information and target the United States because of its preeminence in many high-technology areas. The United States Government, American corporations, and U.S. universities have been targeted by intelligence organizations seeking scientific and technical intelligence. The United States hosts more science and technology (S&T) officials, defense attaches, and identified intelligence officers than any other industrialized nation in the world.
Intrusive on-site inspection activities required under some arms control agreements provide a significant opportunity for HUMINT collection at facilities of great importance to the national security of the United States. On-site inspection provisions are specified in the Treaty on Intermediate Range Nuclear Forces (INF), the Strategic Arms Reduction Treaty (START), the Bilateral Agreement between the United States and Russia on Chemical Weapons, and in the Treaty on Conventional Forces in Europe (CFE). In addition, the Peaceful Nuclear Explosions Treaty (PNET), the Threshold Test Ban Treaty (TTBT), and the Open Skies Treaty (OS) provide the opportunity to gather information from sensitive installations, even though no intrusive on-site inspections are permitted. These treaties provide for the use of technical collection capabilities to verify national declarations. The operation of these collection systems requires a significant number of support personnel, and some of these personnel are likely to be intelligence collectors. Intelligence collectors in onsite inspections will be accredited inspectors who are specially trained to collect specific types of data and enjoy diplomatic immunity. It is likely that these personnel will try to obtain intelligence through observation of facilities, elicitation of information from escorts and facility personnel, and collection of available documentation.
Even with the explosion of technical capabilities, HUMINT can still provide information that even the most proficient technical collectors cannot, such as access to internal memoranda and to compartmented information. Most importantly, human collectors can provide key insights into the intentions of an adversary, whereas technical collection systems are often limited to determining capabilities.[8] HUMINT can be used to reveal adversary plans and intentions, or uncover scientific and weapons developments before they are used or are detected by technical collection systems. HUMiNT can also provide documentary evidence such as blueprints of facilities, copies of adversary plans, or copies of diplomatic or policy documents. Finally, HUMINT is extremely cost effective compared with technical collection systems and does not require a significant technological production base for support.
Signals intelligence is derived from signal intercepts comprising, either individually or in combination, all communications intelligence (COMINT), electronic intelligence (ELlNT), and foreign instrumentation signals intelligence (FISINT), however transmitted.[9] COMINT, one of the primary SIG[NT disciplines, includes information derived from intercepted communications transmissions. COMINT targets voice and teleprinter traffic, video, Morse code traffic, or even facsimile messages. Assuming access is possible, COMINT can be collected from the air waves, cable, fiber optics, or any other transmission medium. ELINT includes the interception and analysis of noncommunications transmissions, such as radar. ELlNT is used to identify the location of an emitter, determine its characteristics, and infer the characteristics of supported systems. FISINT consists of intercepts of telemetry from an opponent's weapons systems as they are being tested. Telemetry units provide designers with information on a prototype's guidance system operation, fuel usage, staging, and other parameters vital for understanding operational characteristics. These data enable the designer to evaluate the performance of the prototype. However, if intercepted, they also provide an adversary with the ability to estimate the capability of the prototype.
Signals intelligence collection can be performed from a variety of platforms. Examples include overt ground collection sites, such as the Russian facility at Lourdes, Cuba; ships and aircraft; and covert locations inside the United States. SIGINT facilities can monitor transmissions from communications satellites, as well as terrestrial facilities. This is particularly important because many international transmissions originating in the United States depend on communications satellites for passage overseas. Communications satellites supporting the transmission of U.S. Government, private sector, and public communications include the International Maritime Satellite system ([NMARSAT), the International Telecommunications Satellite system (INTELSAT),and the European Satellite system (EUROSAT). International communications satellites are routinely monitored by foreign intelligence services, including the Russian and Chinese intelligence services. The majority of collection capabilities targeting the United States are either ground or sea based, and target line-of-site or satellite communication systems. Space-based collection systems can also collect COMINT, FISINT, and ELINT.[10]
MASINT is scientific and technical intelligence information obtained by quantitative and qualitative analysis of data derived from specific technical sensors for the purpose of identifying any distinctive features associated with the source emitter or sender. This information is then used to facilitate the subsequent identification or measurement of the same type of equipment. The term measurement refers primarily to the data collected for the purpose of obtaining finite metric parameters. The term signature refers primarily to data indicating the distinctive features of phenomena, equipment, or objects as they are sensed by the collection instrument. The signature is used to recognize the phenomenon, equipment, or object when its distinctive features are detected.
Examples of MASINT disciplines include radar intelligence (RAD[NT), infrared intelligence (IRINT), and nuclear intelligence (NUCINT). Because it works in different parts of the electromagnetic spectrum, MASINT detects information patterns not previously exploited by sensors. MASINT sensors collect information generally considered by the targeted nation to be peripheral in nature. As a result, these signatures are often not protected by any countermeasures.
IMINT is a product of imagery analysis. Imagery includes representations of objects reproduced electronically or by optical means on film, electronic display devices, or other media. Imagery can be derived from visual photography, radar sensors, infrared sensors, lasers, and electro-optics. IMINT includes the exploitation of data to detect, classify, and identify objects or organizations. It can be produced from either hard- or soft-copy (digital) imagery. Hard-copy imagery is synonymous with film, while soft-copy imagery is displayed on electronic terminals. Both types of imagery sources can be analyzed and interpreted for various purposes by different users.
At one time, the imagery intelligence threat was largely restricted to the former Soviet Union and later to the Russian Federation. This is no longer true. The proliferation of space-based imagery systems permits a much greater use of imagery products by nations that previously did not have access to them. Currently, imagery can be purchased from a variety of sensors. These systems include the Landsat multispectral imagery (MSI) system operated by the United States, the French SPOT MSI and pan-chromatic imaging system, the European Space Agency's ERS-1 synthetic aperture radar imaging system, and the Japanese JERS-1 multisensor imager.[11] Additionally, the Russians are selling 2-meter or better imagery from their spacebased reconnaissance systems. The commercial imagery market is likely to continue to grow at an exponential rate, and additional collection systems are currently being developed. These will include imaging systems produced by U.S. companies that will be capable of producing 1-meter resolution electro-optical digitized imagery. One meter imagery is sufficient to conduct technical analysis of terrain, determine key facilities in an urban area, and conduct detailed analyses of industrial facilities. Other nations such as France, Germany, Japan, and Canada are producing advanced imagery platforms that could be used to target sensitive facilities. Existing imagery systems and developmental commercial systems will be discussed in greater detail in Section 5. An additional factor that must be considered is the growing availability of sophisticated imagery work stations, and analytical tools. These capabilities will allow adversaries to conduct in-depth analysis for targeting and technical intelligence gathering.[12]
The 1992 Open Skies Treaty also poses an imagery collection threat. The treaty establishes a regime of unarmed aerial observation flights over the entire territory of its signatories. The treaty was negotiated between the members of NATO and the former Warsaw Pact as a means to promote openness and transparency of military forces and activities. Observation flights can be performed from aircraft provided by the observing nation, the observed nation, or a third participating party. Aircraft can be equipped with panoramic and framing cameras capable of a ground resolution of no better than 30 centimeters, video cameras with a ground resolution of no better than 30 centimeters, infrared line scanning devices with ground resolution of no better than 50 centimeters, and synthetic aperture radar systems with impulse response rate resolutions no better than 3 meters. Ground resolutions of 50 centimeters or less provide significant detailed information for an imagery analyst. Using the imagery derived from Open Skies flights analysts will be able to identify particular types of equipment by type and capability, and perform detailed analyses of rail, port, industrial, and military facilities.[13]
Imagery provides significant benefits to an adversary collecting intelligence against the United States. First, properly mensurated imagery can provide geolocation accuracies for weapons systems targeting, or other intelligence collection platforms. Second, imagery allows activity to be detected, target characteristics studied in detail, and equipment and facilities enumerated. Third, large areas can be covered by imagery sensors for mapping of areas of key importances
Imagery also has limitations. Except for synthetic aperture radar, imagery quality is normally degraded by darkness and adverse weather. This allows the targeted organization to use these periods of time to conduct activities that they wish to go unobserved. If an organization is aware that it is being targeted by imagery systems, they can use camouflage, concealment, and deception (CC&D) techniques to obscure their activities or provide a misleading image to the observing party. Effective use of CC&D may result in the adversary drawing erroneous conclusions about the observed organization's capabilities and activities. Finally, imagery intelligence collection usually requires a technologically oriented infrastructure. While this requirement may be lessened to some extent in the future, effective use of imagery will still require well educated, technically competent analysts --- a capability that may be beyond some U.S. adversaries.
Open source intelligence involves the use of materials available to the public by intelligence agencies and other adversaries. Some analysts have estimated that the Soviet Union derived up to 90 percent of its intelligence from open source information. With the proliferation of electronic databases, it has become easier to collate large quantities of data, and structure information to meet the needs of the adversary collector. Open source information can often provide extremely valuable information concerning an organization's activities and capabilities. Frequently, open source material can provide information on organizational dynamics, technical processes, and research activities not available in any other form. When open source data is compiled, it is often possible to derive classified data or trade secrets. This is particularly true in the case of studies published in technical journals. A significant understanding of research and development efforts can often be derived by analyzing journal articles published by different members of a research organization. Finally, open source information is generally more timely and may be the only information available in the early stages of a crisis or emergency.
Open source intelligence collection does have limitations. Often articles in military or scientific journals represent a theoretical or desired capability rather than an actual capability. Censorship may also limit the publication of key data needed to arrive at a full understanding of an adversary's actions, or the press may be used as part of a conscious deception effort.
It is unclear to what extent foreign intelligence services are using computer hackers to obtain proprietary data or sensitive government information, or whether they have developed the capability to use computer intrusion techniques to disrupt telecommunications activities. The KGB did, however, sponsor computer intrusion activities by the Hannover Hackers, and there is no reason to believe that these efforts have ceased. The Hannover Hackers were able to access at least 28 Government computer systems, and obtain data from them. They sold this data to the KGB. While none of this data was classified, much of it was sensitive, and classified information could potentially be derived from comparing this information with other data. It has also been alleged that the KGB has been involved in similar efforts with other hacker groups and that these operations included the remote introduction of logic bombs and other malicious code. [16] There is little doubt that many foreign intelligence services could obtain hese capabilities if they wished.[17] The ability of a group of Dutch hackers to obtain sensitive information from U.S. Army, Navy, and Air Force computer networks during Operations Desert Shield and Desert Storm serves as an example of this potential for access. Between April 1990 and May 1991, this group was able to penetrate computer systems at 34 different facilities. The group obtained information on logistics operations, equipment movement schedules, and weapons development programs. Information from one of the penetrated computer systems directly supported Desert Shield/Desert Storm operations. In a review of this incident the General Accounting Office concluded that a foreign intelligence service would have been able to derive significant understanding of U.S. Operations in the Persian Gulf from the information that the Dutch hackers were able to extract from DoD information systems.[18]
The culmination of the intelligence cycle is the development of all source intelligence. All source intelligence incorporates information derived through HUMINT, SIGINT, IM[NT, MAS1NT, and OStNT. The intention of this type of effort is to develop reinforcing information and to use multiple sources to corroborate key data points. The advantage of an all source approach is that each of the intelligence disciplines is suited to collecting a particular type of data, which allows the intelligence organization to examine all facets of an intelligence target, and gain a better understanding of its operation. All source intelligence collection is the most formidable threat faced by the OPSEC program manager. Fortunately, only a few nations have the ability to mount such efforts. The following sections of this report examines the intelligence capabilities of adversary nations and groups.
1 - Interagency OPSEC Support Staff, Compendium of OPSEC Terms, Greenbelt, MD: IOSS, April 1991.
2 - Bruce D. Berkowitz and Allan E. Goodman, StraJegic Intelligence for American National Security, Princeton, NJ: Princeton University Press, 1989.
3 - The Joint Staff, Doctrine for Intelligence Support to Joint Operations, Washington, DC: Office of the Joint Chiefs of Staff. June 30. 1991.
4 - Interagency OPSEC Support Staff, Compendium of OPSEC Terms, Greenbelt, MD: IOSS, April 1991.
5 - Air Force Pamphlet 200-18, Target Intelligence Handbook: Unclassif ed Targeting Principles, Washington, DC: Department of the Air Force, October 1, 1990.
6 - Suzanne Wood, Katherine L. Herbig, and Peter A. W. Lewis, American Espionage, 1945-1989, Monterey, CA: Defense Personnel Security Research and Education Center, 1990.
7 - Defense Science Board, Report of the Defense Science Board Summer Study Task Force on Information Architecture for the Battlefield, Washington, DC: Office of the Under Secretary of Defense for Acquisition and Technology, October 1994.
8 - Jeffrey Richelson, American Espionage and the Soviet Target, New York: William Morrow, 1987.
9 Intelligence Community Staff, Glossary of Intelligence Terms and Definitions, Washington, DC: ICS, June 1989.
10 - William Rosenau,"A Deafening Silence: U.S. Policy and the SIGINT Facility at Lourdes," Intelligence and National Security, 9:4 (October 1994), pp. 723-734.
11 - Pan chromatic systems produce black and white imagery. Multispectral systems capture selected visible and non-visible wavelengths of the electromagnetic spectrum to develop images that provide information not available from the visible spectrum alone. These images provide the means to determine soil porosity, moisture content, heat distribution patterns, structural density, and vegetation growth. Synthetic aperture radar (SAR) uses a radar antenna with a narrow beam to develop a high resolution image. SAR provides an all weather/day/night imaging capability. Electro-optic imagery differs from optical imagery in that the first uses an electrical system imaging system to obtain a digital image, and the second type is essentially a photographic system that uses film as a medium. The advantage of electro-optic imagery is that digitized imagery can be transmitted for near real-time analysis, and can be manipulated or enhanced to emphasize desired features.
12 - Daniel B. Sibbet, "Commercial Remote-Sensing," American Intelligence Journal, Spring/Summer 1993, p. 37, and Testimony of Robin Armani before the Senate Select Committee on Intelligence, Public Hearing on Commercial Remote Sensing, November 17. 1993.
13 - On-Site Inspection Agency, "Fact Sheet: The Open Skies Treaty," May 1993, and U.S. Arms Control and Disarmament Agency, Treaty on Open Skies (Official Text), April 10, 1992.
14 - Headquarters, U.S. Air Force, Target Intelligence Handbook: Unclassified Targeting Principles, Air Force Pamphlet 200-18, Volume 1, Washington, D.C., 1 October 1990, pp. 18-19.
15 - ibid.. P. 19.
16 - Peter Warren, "Technoterrorists: Growing Links Between Computer Technology and the Seedy Underworld of Terrorism, Organized Crime, and Spying." Computer Talk, June 19. 1989, D. 52.
17 - Interview: DISA Center for Information System Security, November 3, 1993.
18 - United States Senate, A Lesson of the Gulf War: National
Security Requires Computer Security, June 19, 1991, Subcommittee
on Government Information and Regulation, Committee on
Governmental Affairs, Washington, DC: USGPO.